Network Design and Optimization: COMP712 Routing and Switching Report
VerifiedAdded on 2023/05/31
|10
|1781
|289
Report
AI Summary
This report focuses on optimizing a network, specifically addressing routing and switching essentials. It begins with an executive summary and introduction, outlining the need for improved network performance. The report delves into network design considerations, proposing enhancements such as adding routers for improved load balancing and easier network understanding. It also explores the implementation of VPN servers for enhanced security and remote access. The use of RIPng and IPv6 is evaluated, alongside the configuration of RIPng authentication to increase security. The report also examines the integration of network management tools, including firewalls, and compares different routing and switching features from various vendors. The conclusion recommends the use of firewalls, virtual servers, and reliable network components to ensure network efficiency and security. References are provided to support the analysis and recommendations.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ROUTING AND
SWITCHING
SWITCHING

Executive summary
In the current developing network technology routing plays a very important role especially in
the forwarding of packets from the source to destination. Different types of routers have different
features. In this paper we evaluate how we can use different types of routing protocols like
RIPng together with IPv6 in order to improve the performance of different types of network.
This paper discusses different features of protocols that are required in order to increase the
performance ability of the different types of protocols a that are implemented in any network in
order to provide efficient flow of packets within the network components .Use of RIP and IPv6
as a routing protocol is recommended due to the following reasons. RIP routing protocol uses
modified hops in establishing network distance and pushes information in the routing tables after
every 30 seconds unlike other routing protocols.
In the current developing network technology routing plays a very important role especially in
the forwarding of packets from the source to destination. Different types of routers have different
features. In this paper we evaluate how we can use different types of routing protocols like
RIPng together with IPv6 in order to improve the performance of different types of network.
This paper discusses different features of protocols that are required in order to increase the
performance ability of the different types of protocols a that are implemented in any network in
order to provide efficient flow of packets within the network components .Use of RIP and IPv6
as a routing protocol is recommended due to the following reasons. RIP routing protocol uses
modified hops in establishing network distance and pushes information in the routing tables after
every 30 seconds unlike other routing protocols.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table of Contents
Executive summary.........................................................................................................................1
Introduction......................................................................................................................................3
Network design................................................................................................................................3
VPN server...................................................................................................................................4
Configuring RIPng Authentication..............................................................................................5
Configuration of the link state protocols......................................................................................5
Network management tools.............................................................................................................6
Firewalls.......................................................................................................................................6
Routing and switching feature comparison.....................................................................................6
Conclusion and recommendation....................................................................................................7
Executive summary.........................................................................................................................1
Introduction......................................................................................................................................3
Network design................................................................................................................................3
VPN server...................................................................................................................................4
Configuring RIPng Authentication..............................................................................................5
Configuration of the link state protocols......................................................................................5
Network management tools.............................................................................................................6
Firewalls.......................................................................................................................................6
Routing and switching feature comparison.....................................................................................6
Conclusion and recommendation....................................................................................................7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Introduction
Routing is the process by which the best route is chosen among many routes in order to transmit
data between the source and the destination. The choice of routes depend on the routing
protocols that are implemented in any given network. The routing protocols utilizes different
metrics in order to select the best routes to transmit data. This paper describes how RIP with
IPv6 address can be improved in any given network topology in order to increase the
performance of any given network topology (Baran & Sosa 2017). Improvement of any given
network topology that is connected using RIPng protocols mainly targets the following features
of the protocol that is implemented in the network. The database request time, the response time
that the routing protocols offers, the security in the connection ports of the network.,IPv6 traffic
jitter and the end to end delay and response to communication. The following shows how
configuration in RIPng can be improved in the given network topology in order to improve the
performance of the network.
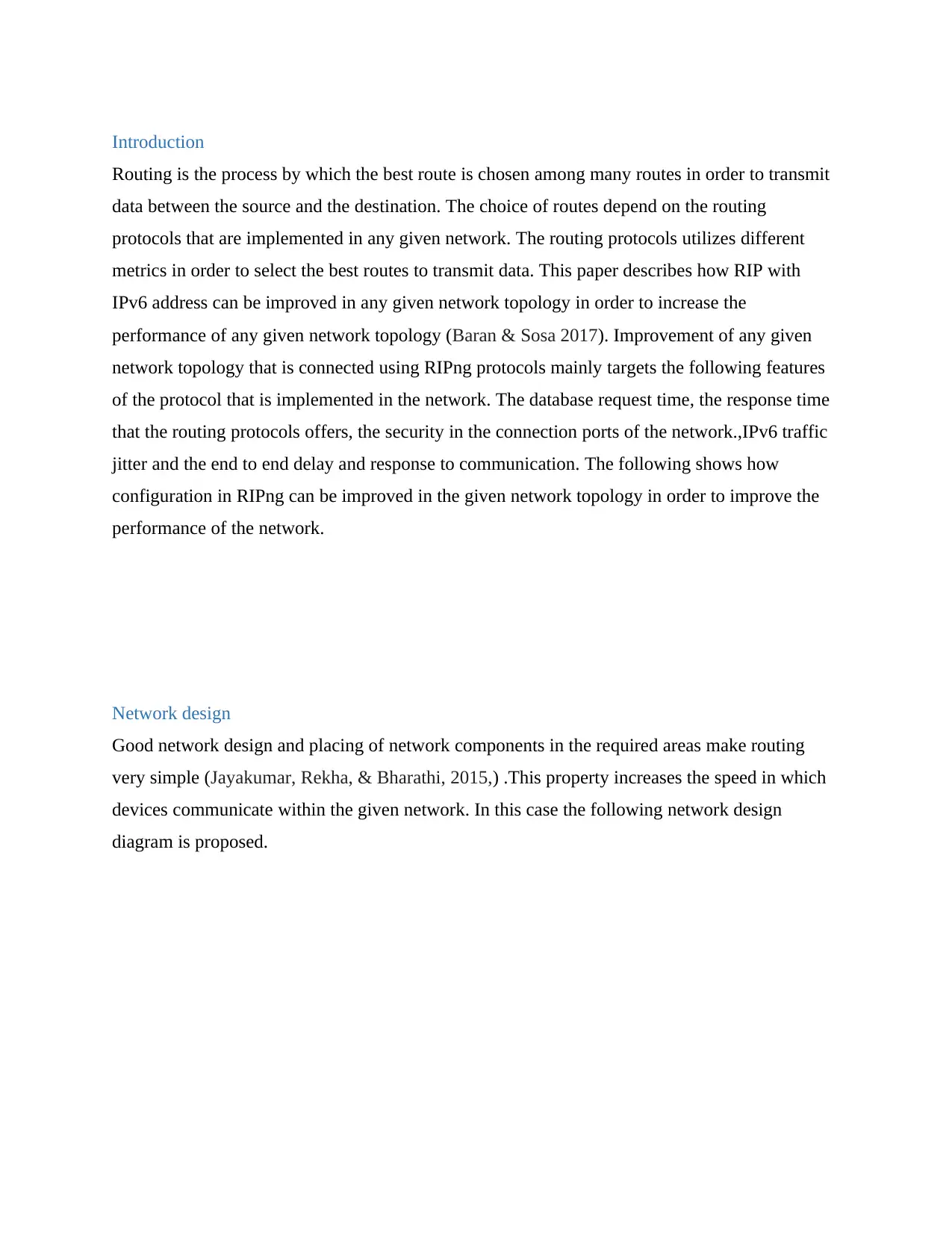
Network design
Good network design and placing of network components in the required areas make routing
very simple (Jayakumar, Rekha, & Bharathi, 2015,) .This property increases the speed in which
devices communicate within the given network. In this case the following network design
diagram is proposed.
Routing is the process by which the best route is chosen among many routes in order to transmit
data between the source and the destination. The choice of routes depend on the routing
protocols that are implemented in any given network. The routing protocols utilizes different
metrics in order to select the best routes to transmit data. This paper describes how RIP with
IPv6 address can be improved in any given network topology in order to increase the
performance of any given network topology (Baran & Sosa 2017). Improvement of any given
network topology that is connected using RIPng protocols mainly targets the following features
of the protocol that is implemented in the network. The database request time, the response time
that the routing protocols offers, the security in the connection ports of the network.,IPv6 traffic
jitter and the end to end delay and response to communication. The following shows how
configuration in RIPng can be improved in the given network topology in order to improve the
performance of the network.
Network design
Good network design and placing of network components in the required areas make routing
very simple (Jayakumar, Rekha, & Bharathi, 2015,) .This property increases the speed in which
devices communicate within the given network. In this case the following network design
diagram is proposed.
Adding one router to the previous topology will improve the performance of the previous
network. This because four routers have the following advantages in RIP routing. When four
routers are used to in the network configuration will be very easy since the topology can be
easily understood by the network engineers. Use of more routers promote load balancing in
network. This means that many routes will be available for data to flow within the network since
the existing routers installs routes with lower administrating level in the network.
VPN server
Configuring VPN servers to enable users to connect to the entire network remotely.
Implementation of VPN server will have the following advantages in the network. The network
will have improved security, it increases online safety when accessing resources through the
internet .It prevents a hackers from accessing the information this because the ISP’s that is in the
network will not be able to access user log’s that are created in the network. Use of VPN in any
network allows remote access to information thus users will be able to access from any location
increasing productivity. VPN is also used to reduce the cost of accessing the internet in any
given network. Lastly use of VPN service normally allows users to bypass restrictions in any
given network. This means that the network users will be able to access information in any
webserver while using the service without any restrictions.
network. This because four routers have the following advantages in RIP routing. When four
routers are used to in the network configuration will be very easy since the topology can be
easily understood by the network engineers. Use of more routers promote load balancing in
network. This means that many routes will be available for data to flow within the network since
the existing routers installs routes with lower administrating level in the network.
VPN server
Configuring VPN servers to enable users to connect to the entire network remotely.
Implementation of VPN server will have the following advantages in the network. The network
will have improved security, it increases online safety when accessing resources through the
internet .It prevents a hackers from accessing the information this because the ISP’s that is in the
network will not be able to access user log’s that are created in the network. Use of VPN in any
network allows remote access to information thus users will be able to access from any location
increasing productivity. VPN is also used to reduce the cost of accessing the internet in any
given network. Lastly use of VPN service normally allows users to bypass restrictions in any
given network. This means that the network users will be able to access information in any
webserver while using the service without any restrictions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Configuring RIPng Authentication
Use of RIPv2 in the network which supports RIP authentication of links before they are accessed
or activated to be alive. Authentication provides an additional layer of network security beyond
other security features that are included in the network (Wan, Kranakis, & Oorschot, 2014). This
features allows routers to authenticate each other while communicating using the same keys that
are configured in the network. This type of feature is not supported by RIPv1 of routing.
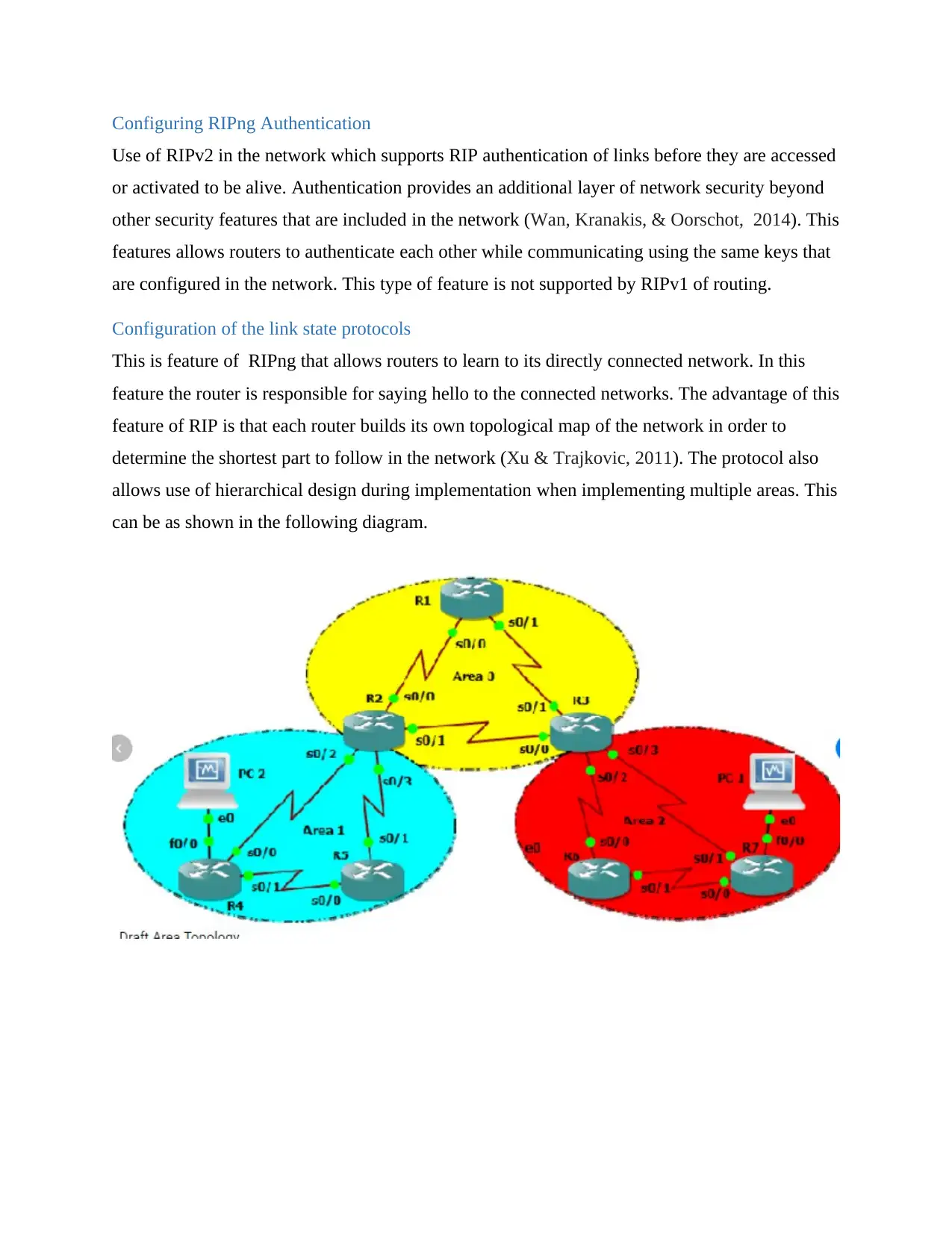
Configuration of the link state protocols
This is feature of RIPng that allows routers to learn to its directly connected network. In this
feature the router is responsible for saying hello to the connected networks. The advantage of this
feature of RIP is that each router builds its own topological map of the network in order to
determine the shortest part to follow in the network (Xu & Trajkovic, 2011). The protocol also
allows use of hierarchical design during implementation when implementing multiple areas. This
can be as shown in the following diagram.
Use of RIPv2 in the network which supports RIP authentication of links before they are accessed
or activated to be alive. Authentication provides an additional layer of network security beyond
other security features that are included in the network (Wan, Kranakis, & Oorschot, 2014). This
features allows routers to authenticate each other while communicating using the same keys that
are configured in the network. This type of feature is not supported by RIPv1 of routing.
Configuration of the link state protocols
This is feature of RIPng that allows routers to learn to its directly connected network. In this
feature the router is responsible for saying hello to the connected networks. The advantage of this
feature of RIP is that each router builds its own topological map of the network in order to
determine the shortest part to follow in the network (Xu & Trajkovic, 2011). The protocol also
allows use of hierarchical design during implementation when implementing multiple areas. This
can be as shown in the following diagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network management tools
This are the software and hardware components that are used in network implementation in order
for the network to perform efficiently as per the requirements. These are the tools that are used in
order to detect earliest failures in any network and improve them at early stage(Rawat, Kumar &
Gupta, 2014). The management tools that should be include in this network include server,
security and databases tool. The following is an example of the tools that should be included in
order to increase the performance of the network.
Firewalls
These are the systems that are used to prevent unauthorized access to or from private networks. It
will be implemented both as a hardware or a software. In this case the firewalls can be
implemented in each router in order to prevent unauthorized access the network (Verma &
Bhardwaj, 2016).
Other tools that should be included in the network include backup server for data backup in case
the main server fails. Implementation of the virtual server will also be very important in the
network
Routing and switching feature comparison
There are different types of switches from different vendors that are required in the network
implementation. This switches support different kind of features that are required in any
network.
Switches
Among the switches that should be implemented in any network are the switches from cisco,
Juniper network and Arista networks. An example of such network switch is the 16 slot cisco-
nexus switch 9500 that houses a lot of gigaEthernet ports up to 576.This switches have a lot of
ports and throughputs thus they are the best to be implemented in the network (Yi et al., 2014).
Routers
Routers are very essential in implementation of any network. There different types of routers that
are from different types of vendors with different specified characters that should be installed in
This are the software and hardware components that are used in network implementation in order
for the network to perform efficiently as per the requirements. These are the tools that are used in
order to detect earliest failures in any network and improve them at early stage(Rawat, Kumar &
Gupta, 2014). The management tools that should be include in this network include server,
security and databases tool. The following is an example of the tools that should be included in
order to increase the performance of the network.
Firewalls
These are the systems that are used to prevent unauthorized access to or from private networks. It
will be implemented both as a hardware or a software. In this case the firewalls can be
implemented in each router in order to prevent unauthorized access the network (Verma &
Bhardwaj, 2016).
Other tools that should be included in the network include backup server for data backup in case
the main server fails. Implementation of the virtual server will also be very important in the
network
Routing and switching feature comparison
There are different types of switches from different vendors that are required in the network
implementation. This switches support different kind of features that are required in any
network.
Switches
Among the switches that should be implemented in any network are the switches from cisco,
Juniper network and Arista networks. An example of such network switch is the 16 slot cisco-
nexus switch 9500 that houses a lot of gigaEthernet ports up to 576.This switches have a lot of
ports and throughputs thus they are the best to be implemented in the network (Yi et al., 2014).
Routers
Routers are very essential in implementation of any network. There different types of routers that
are from different types of vendors with different specified characters that should be installed in

this network. The net gear switch from Cisco and Juniper networks should be implemented in
this network dues to its high functionality and high number of ports that are present in it
Conclusion and recommendation
Since RIPng runs over IPv6, RIPng relies on the IP Authentication Header and the IP
Encapsulating Security Payload to ensure integrity and authentication/confidentiality of routing
exchanges. Network firewalls are also recommended to be added in the network in order to
increase the network security and prevent attackers from accessing the network. The virtual
server should also be included in the network in order to reduce the maintenance and increase the
functionality of the network. More so virtual server centralized management of the data in the
network thus making it easier for the network to be maintained. This also supports backing up of
data in case there is any data loss in the network. The selection of network components to be
used in network is very much essential. They determine the speed of the network and its
efficiency. The selected network components in any network should be highly related and from
trusted vendors in order for the network to be efficient throughout. The VPN server is also
implemented in the network in order to allow users to access the network privately from any
location.
this network dues to its high functionality and high number of ports that are present in it
Conclusion and recommendation
Since RIPng runs over IPv6, RIPng relies on the IP Authentication Header and the IP
Encapsulating Security Payload to ensure integrity and authentication/confidentiality of routing
exchanges. Network firewalls are also recommended to be added in the network in order to
increase the network security and prevent attackers from accessing the network. The virtual
server should also be included in the network in order to reduce the maintenance and increase the
functionality of the network. More so virtual server centralized management of the data in the
network thus making it easier for the network to be maintained. This also supports backing up of
data in case there is any data loss in the network. The selection of network components to be
used in network is very much essential. They determine the speed of the network and its
efficiency. The selected network components in any network should be highly related and from
trusted vendors in order for the network to be efficient throughout. The VPN server is also
implemented in the network in order to allow users to access the network privately from any
location.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Baran, B., & Sosa, R. (2017). A new approach for AntNet routing. In Computer
Communications
and Networks, 2000. Proceedings. Ninth International Conference on (pp. 303-308).
IEEE.
Jayakumar, M., Rekha, N. R. S., & Bharathi, B. (2015, March). A comparative study on RIP and
OSPF protocols. In Innovations in Information, Embedded and Communication Systems
(ICIIECS), 2015 International Conference on (pp. 1-5). IEEE.
Rawat, G. S., Kumar, D., & Gupta, S. C. (2014, October). An analysis of DYMO, FSR, ZRP and
RIP routing protocols using QUALNET. In Proceedings of the 2014 International
Conference on Interdisciplinary Advances in Applied Computing (p. 2). ACM.
Verma, A., & Bhardwaj, N. (2016). A review on routing information protocol (RIP) and open
shortest path first (OSPF) routing protocol. International Journal of Future Generation
Communication and Networking, 9(4), 161-170.
Wan, T., Kranakis, E., & van Oorschot, P. C. (2014, June). S-rip: A secure distance vector
routing protocol. In International Conference on Applied Cryptography and Network
Security(pp. 103-119). Springer, Berlin, Heidelberg.
Xu, D., & Trajkovic, L. (2011). Performance analysis of RIP, EIGRP, and OSPF using OPNET.
Yi, C., Abraham, J., Afanasyev, A., Wang, L., Zhang, B., & Zhang, L. (2014, September). On
the role of routing in named data networking. In Proceedings of the 1st ACM Conference
on Information-Centric Networking (pp. 27-36). ACM.
Baran, B., & Sosa, R. (2017). A new approach for AntNet routing. In Computer
Communications
and Networks, 2000. Proceedings. Ninth International Conference on (pp. 303-308).
IEEE.
Jayakumar, M., Rekha, N. R. S., & Bharathi, B. (2015, March). A comparative study on RIP and
OSPF protocols. In Innovations in Information, Embedded and Communication Systems
(ICIIECS), 2015 International Conference on (pp. 1-5). IEEE.
Rawat, G. S., Kumar, D., & Gupta, S. C. (2014, October). An analysis of DYMO, FSR, ZRP and
RIP routing protocols using QUALNET. In Proceedings of the 2014 International
Conference on Interdisciplinary Advances in Applied Computing (p. 2). ACM.
Verma, A., & Bhardwaj, N. (2016). A review on routing information protocol (RIP) and open
shortest path first (OSPF) routing protocol. International Journal of Future Generation
Communication and Networking, 9(4), 161-170.
Wan, T., Kranakis, E., & van Oorschot, P. C. (2014, June). S-rip: A secure distance vector
routing protocol. In International Conference on Applied Cryptography and Network
Security(pp. 103-119). Springer, Berlin, Heidelberg.
Xu, D., & Trajkovic, L. (2011). Performance analysis of RIP, EIGRP, and OSPF using OPNET.
Yi, C., Abraham, J., Afanasyev, A., Wang, L., Zhang, B., & Zhang, L. (2014, September). On
the role of routing in named data networking. In Proceedings of the 1st ACM Conference
on Information-Centric Networking (pp. 27-36). ACM.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




