Royal Holloway IY5502 Cryptography & Security Exam Solutions
VerifiedAdded on 2023/06/15
|33
|5553
|256
Quiz and Exam
AI Summary
This document contains solutions to past MSc examinations in Introduction to Cryptography and Security Mechanisms (IY5502) from Royal Holloway, University of London, covering the years 2013 to 2017. The solutions address questions related to cryptographic principles, security algorithms, key management, and various security mechanisms like GSM security, AES, and DES. Topics include true/false justifications, advantages and disadvantages of proprietary encryption algorithms, comparisons of different cipher modes like ECB and CTR, and discussions on the role of hash functions and digital signatures in ensuring data integrity and authenticity. The document provides detailed explanations and analysis relevant to understanding and applying cryptographic concepts in practical security scenarios.

Running head: INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Introduction to Cryptography and Security Mechanisms
Name of the Student
Name of the University
Author Note
Introduction to Cryptography and Security Mechanisms
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Table of Contents
MSc EXAMINATION 2013...............................................................................................3
Question 1........................................................................................................................3
Question 2........................................................................................................................5
Question 3........................................................................................................................7
MSc EXAMINATION 2014.............................................................................................10
Question 1......................................................................................................................10
Question 2......................................................................................................................11
Question 5......................................................................................................................13
MSc EXAMINATION 2015.............................................................................................16
Question 1......................................................................................................................16
Question 3......................................................................................................................17
Question 4......................................................................................................................19
MSc EXAMINATION 2016.............................................................................................22
Question 1......................................................................................................................22
Question 2......................................................................................................................24
Question 5......................................................................................................................25
MSc EXAMINATION 2017.............................................................................................27
Question 1......................................................................................................................27
Question 3......................................................................................................................28
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Table of Contents
MSc EXAMINATION 2013...............................................................................................3
Question 1........................................................................................................................3
Question 2........................................................................................................................5
Question 3........................................................................................................................7
MSc EXAMINATION 2014.............................................................................................10
Question 1......................................................................................................................10
Question 2......................................................................................................................11
Question 5......................................................................................................................13
MSc EXAMINATION 2015.............................................................................................16
Question 1......................................................................................................................16
Question 3......................................................................................................................17
Question 4......................................................................................................................19
MSc EXAMINATION 2016.............................................................................................22
Question 1......................................................................................................................22
Question 2......................................................................................................................24
Question 5......................................................................................................................25
MSc EXAMINATION 2017.............................................................................................27
Question 1......................................................................................................................27
Question 3......................................................................................................................28

2
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Question 5......................................................................................................................30
Bibliography......................................................................................................................32
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Question 5......................................................................................................................30
Bibliography......................................................................................................................32
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
MSc EXAMINATION 2013
Question 1
a) (i). False.
Cryptography provides a means of hiding information in such a way that an attacker or a
third party is prevented from reading or accessing the private messages.
(ii). True.
Encryption by default provides data integrity as an encrypted data can only be accessed
by the legitimate users. Therefore, it is not possible for an attacker to modify the data in ay way
thus maintaining the data integrity.
(iii). True.
Asymmetric keys or public keys tend to be longer than the symmetric keys as it involves
complex mathematical structures for encryption. Asymmetric key encryption makes use of key
sizes that are generally of 1024, 2048 and 4096 bits; while the symmetric key encryption mainly
uses keys of 128 bits, 192 bits and 256 bits.
(iv). True.
Error generally does not propagate through stream cipher as pseudorandom key stream is
generated in stream cipher. One of the major benefits of plain text is that if a single digit in
cipher is affected, the error does not propagate to the other parts.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
MSc EXAMINATION 2013
Question 1
a) (i). False.
Cryptography provides a means of hiding information in such a way that an attacker or a
third party is prevented from reading or accessing the private messages.
(ii). True.
Encryption by default provides data integrity as an encrypted data can only be accessed
by the legitimate users. Therefore, it is not possible for an attacker to modify the data in ay way
thus maintaining the data integrity.
(iii). True.
Asymmetric keys or public keys tend to be longer than the symmetric keys as it involves
complex mathematical structures for encryption. Asymmetric key encryption makes use of key
sizes that are generally of 1024, 2048 and 4096 bits; while the symmetric key encryption mainly
uses keys of 128 bits, 192 bits and 256 bits.
(iv). True.
Error generally does not propagate through stream cipher as pseudorandom key stream is
generated in stream cipher. One of the major benefits of plain text is that if a single digit in
cipher is affected, the error does not propagate to the other parts.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(v). True.
Caesar cipher is a type of substitution cipher, where the original message or plain text is
replaced by a corresponding letter after certain shifting in the alphabet. Therefore, it can certainly
be used as a one-time pad to send a letter of plain text.
(vi). False.
The value of d is the modular multiplicative inverse of e (modulo λ(n))
(vii). True.
In cryptography, HMAC is a message authentication code that involves a cryptographic
hash function along with a secret cryptographic key.
(viii). False.
Entity authentication protocol involves use of a private key for digitally signing a random
number generated.
(ix). True.
Quantum computers have the ability to surpass all the processing powers of today’s
computers and therefore it has the power to make encryption algorithms insecure. However, it
will take a decade more to build such computers.
(x) False.
WiFi protected access does not make use of hybrid encryption.
b) The pros and cons of deploying a proprietary encryption algorithm are as follows-
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(v). True.
Caesar cipher is a type of substitution cipher, where the original message or plain text is
replaced by a corresponding letter after certain shifting in the alphabet. Therefore, it can certainly
be used as a one-time pad to send a letter of plain text.
(vi). False.
The value of d is the modular multiplicative inverse of e (modulo λ(n))
(vii). True.
In cryptography, HMAC is a message authentication code that involves a cryptographic
hash function along with a secret cryptographic key.
(viii). False.
Entity authentication protocol involves use of a private key for digitally signing a random
number generated.
(ix). True.
Quantum computers have the ability to surpass all the processing powers of today’s
computers and therefore it has the power to make encryption algorithms insecure. However, it
will take a decade more to build such computers.
(x) False.
WiFi protected access does not make use of hybrid encryption.
b) The pros and cons of deploying a proprietary encryption algorithm are as follows-

5
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Pros
1. It keeps the encryption algorithm private.
2. Gives an access of the trade secrets such as additional cryptographic information.
3. It allows custom encryption options
Cons
1. The security level of the encryption largely depends on its design and hence it may not
be completely secure.
2. The security cannot be matched up to the level of mathematical algorithms.
Question 2
(a) A good cryptographic algorithm should incorporate different functions such as
message secrecy, message integrity, authentication and digital signatures. Furthermore, it is
essential to consider whether symmetric or asymmetric cryptography method is to be considered
for a chosen environment. Symmetric key cryptography provides additional layer of security.
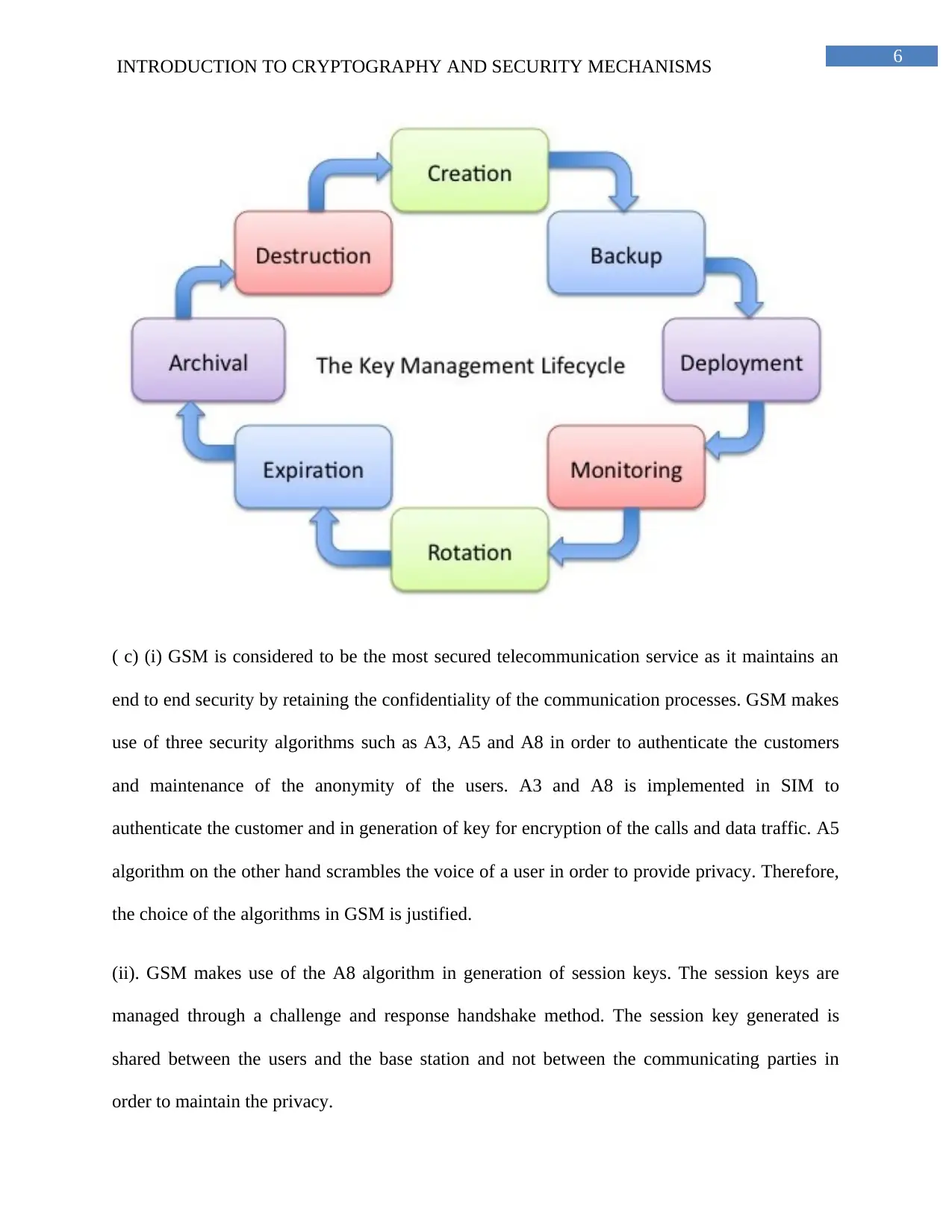
(b) A good cryptographic algorithm needs a good key management as it deals with
management and administration of the cryptographic keys. The operational phases of key
management include creation, backup, deployment, monitoring, expiration and destruction.
These phases are linked with each other and help in secure communication. Proper operation of
all the phases is essential for maintaining a good cryptographic algorithm.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
Pros
1. It keeps the encryption algorithm private.
2. Gives an access of the trade secrets such as additional cryptographic information.
3. It allows custom encryption options
Cons
1. The security level of the encryption largely depends on its design and hence it may not
be completely secure.
2. The security cannot be matched up to the level of mathematical algorithms.
Question 2
(a) A good cryptographic algorithm should incorporate different functions such as
message secrecy, message integrity, authentication and digital signatures. Furthermore, it is
essential to consider whether symmetric or asymmetric cryptography method is to be considered
for a chosen environment. Symmetric key cryptography provides additional layer of security.
(b) A good cryptographic algorithm needs a good key management as it deals with
management and administration of the cryptographic keys. The operational phases of key
management include creation, backup, deployment, monitoring, expiration and destruction.
These phases are linked with each other and help in secure communication. Proper operation of
all the phases is essential for maintaining a good cryptographic algorithm.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
( c) (i) GSM is considered to be the most secured telecommunication service as it maintains an
end to end security by retaining the confidentiality of the communication processes. GSM makes
use of three security algorithms such as A3, A5 and A8 in order to authenticate the customers
and maintenance of the anonymity of the users. A3 and A8 is implemented in SIM to
authenticate the customer and in generation of key for encryption of the calls and data traffic. A5
algorithm on the other hand scrambles the voice of a user in order to provide privacy. Therefore,
the choice of the algorithms in GSM is justified.
(ii). GSM makes use of the A8 algorithm in generation of session keys. The session keys are
managed through a challenge and response handshake method. The session key generated is
shared between the users and the base station and not between the communicating parties in
order to maintain the privacy.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
( c) (i) GSM is considered to be the most secured telecommunication service as it maintains an
end to end security by retaining the confidentiality of the communication processes. GSM makes
use of three security algorithms such as A3, A5 and A8 in order to authenticate the customers
and maintenance of the anonymity of the users. A3 and A8 is implemented in SIM to
authenticate the customer and in generation of key for encryption of the calls and data traffic. A5
algorithm on the other hand scrambles the voice of a user in order to provide privacy. Therefore,
the choice of the algorithms in GSM is justified.
(ii). GSM makes use of the A8 algorithm in generation of session keys. The session keys are
managed through a challenge and response handshake method. The session key generated is
shared between the users and the base station and not between the communicating parties in
order to maintain the privacy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(d). Apart from a good cryptographic algorithm and good key management, another
major element that is needed to be considered for security of a cryptosystem is access control,
which ensures only the authorized users are able to access a data.
Question 3
(a). The block size in AES is 128 bits and key size can be of 128 bits, 192 bits or 256 bits.
(b). In block cipher, padding is a process of making a data’s multiple of the block size
cipher if it is not by default. The block cipher needs a data to be exact multiple of the block size
and therefore, padding is essential. However, this can cause a problem as block cipher padding is
very much prone to the padding oracle attacks.
(c) In electronic code book cipher, the message is divided into a number of blocks and
every block is encrypted separately. It is the simplest mode of encryption.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(d). Apart from a good cryptographic algorithm and good key management, another
major element that is needed to be considered for security of a cryptosystem is access control,
which ensures only the authorized users are able to access a data.
Question 3
(a). The block size in AES is 128 bits and key size can be of 128 bits, 192 bits or 256 bits.
(b). In block cipher, padding is a process of making a data’s multiple of the block size
cipher if it is not by default. The block cipher needs a data to be exact multiple of the block size
and therefore, padding is essential. However, this can cause a problem as block cipher padding is
very much prone to the padding oracle attacks.
(c) In electronic code book cipher, the message is divided into a number of blocks and
every block is encrypted separately. It is the simplest mode of encryption.
8
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
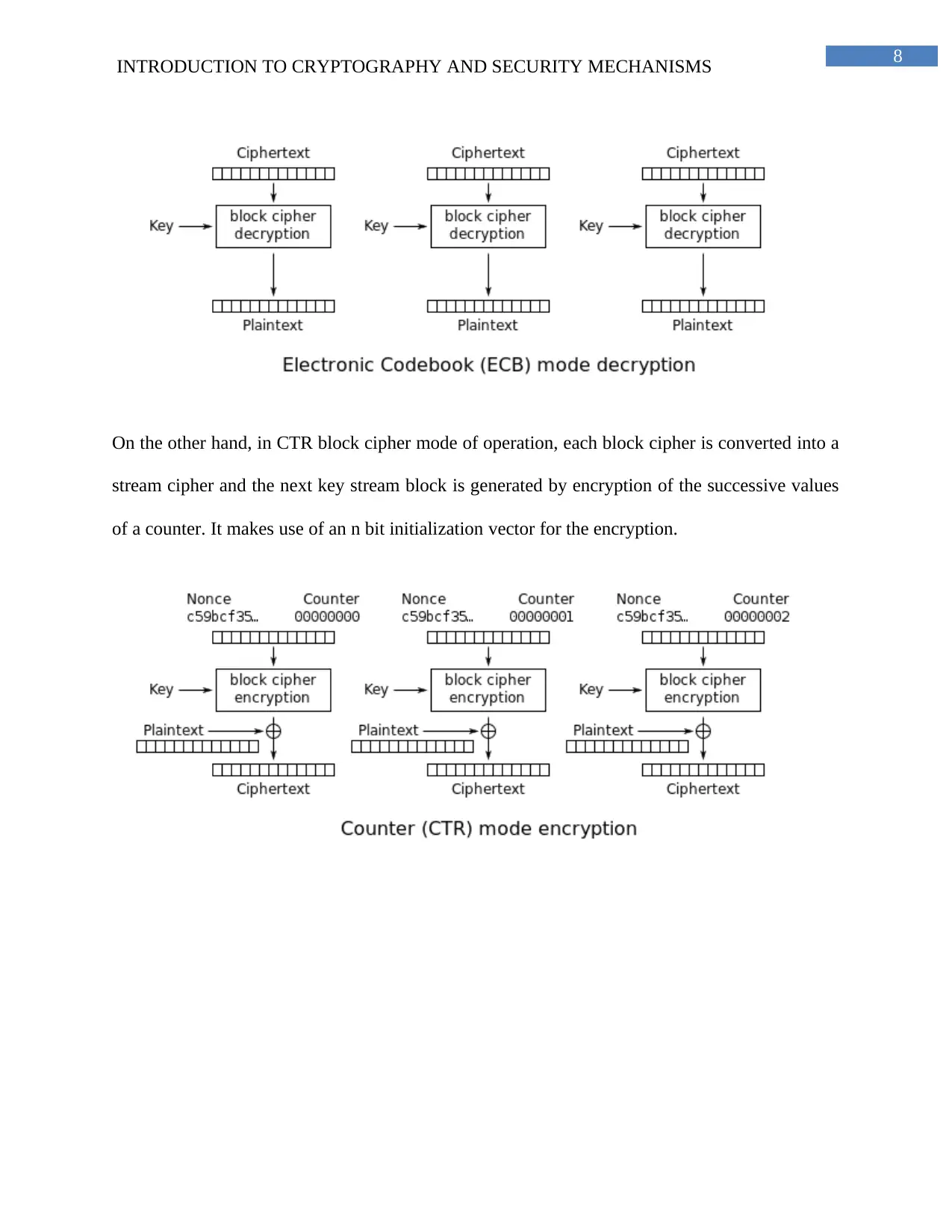
On the other hand, in CTR block cipher mode of operation, each block cipher is converted into a
stream cipher and the next key stream block is generated by encryption of the successive values
of a counter. It makes use of an n bit initialization vector for the encryption.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
On the other hand, in CTR block cipher mode of operation, each block cipher is converted into a
stream cipher and the next key stream block is generated by encryption of the successive values
of a counter. It makes use of an n bit initialization vector for the encryption.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(d). The comparison between ECB and CTR is as follows-
Perspective ECB CTR
Requirement for padding Requires padding Does not require padding
impact of a 1-bit transmission
error
Error does not have effect on
other blocks.
Have effects on other blocks, if
one block is damaged all the
subsequent cipher blocks are
damaged as well.
impact of loss of a block in the
communication channel
Does not have effects on other
block
Have profound effect on other
blocks
impact of a 1-bit computation
error in the encryption of a single
block
Since every block is encrypted
independently, it has no impact
on other blocks
Effects the subsequent blocks as
well
Implementation Issues It is not semantically secure No such implementation issues
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(d). The comparison between ECB and CTR is as follows-
Perspective ECB CTR
Requirement for padding Requires padding Does not require padding
impact of a 1-bit transmission
error
Error does not have effect on
other blocks.
Have effects on other blocks, if
one block is damaged all the
subsequent cipher blocks are
damaged as well.
impact of loss of a block in the
communication channel
Does not have effects on other
block
Have profound effect on other
blocks
impact of a 1-bit computation
error in the encryption of a single
block
Since every block is encrypted
independently, it has no impact
on other blocks
Effects the subsequent blocks as
well
Implementation Issues It is not semantically secure No such implementation issues
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
MSc EXAMINATION 2014
Question 1
(a) (i). True.
In public key cryptography, only one part of the key has to be kept secret and the
message is needed to be encrypted using the public key of the receiver.
(ii). True.
Digital signatures provide added assurance and evidence of data origin, its identity and
status.
(iii). True.
A side channel attack is mainly based on information gained from the physical
implementation of a system and not due to the weakness in implemented algorithm.
(iv). False
The key space of 128 bit AES is 2128, while that of 256 bit AEs is 2256.
(v). False.
CCB is not a standardized mode of operation of block cipher.
(vi). True.
Hash functions can be used for building other cryptographic primitives, for examples
MACs or message authentication codes are built from hash functions.
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
MSc EXAMINATION 2014
Question 1
(a) (i). True.
In public key cryptography, only one part of the key has to be kept secret and the
message is needed to be encrypted using the public key of the receiver.
(ii). True.
Digital signatures provide added assurance and evidence of data origin, its identity and
status.
(iii). True.
A side channel attack is mainly based on information gained from the physical
implementation of a system and not due to the weakness in implemented algorithm.
(iv). False
The key space of 128 bit AES is 2128, while that of 256 bit AEs is 2256.
(v). False.
CCB is not a standardized mode of operation of block cipher.
(vi). True.
Hash functions can be used for building other cryptographic primitives, for examples
MACs or message authentication codes are built from hash functions.

11
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(vii). False.
MACs are based on symmetric principles and therefore do not provide non repudiation.
(viii). True.
The authenticity problem in net banking is solved by one time pad system that generates
a private key randomly to encrypt and decrypt a message.
(ix). False.
There is certain security issues associated with the key pair establishment in public key
cryptography as the encryption is carried out using the public key of the receiver.
(x) True.
GSM is the secured cellular telecommunication system that authenticates the identity of
the subscriber with the help of challenge response mechanism.
(b). It is generally impossible for two messages to generate identical message digest and
therefore, cryptographic hash functions are often used to detect whether a message is altered.
This is done by computing the digest of a file called the base line digest. If at any point of time, a
digest differs from its baseline digest, it can be concluded that the file has been altered.
Therefore, hash functions are rightly used to provide data integrity as an attacker cannot make
any unauthorized change without being detected.
Question 2
(a). ECB is not generally recommended for encryption of long messages because –
INTRODUCTION TO CRYPTOGRAPHY AND SECURITY MECHANISMS
(vii). False.
MACs are based on symmetric principles and therefore do not provide non repudiation.
(viii). True.
The authenticity problem in net banking is solved by one time pad system that generates
a private key randomly to encrypt and decrypt a message.
(ix). False.
There is certain security issues associated with the key pair establishment in public key
cryptography as the encryption is carried out using the public key of the receiver.
(x) True.
GSM is the secured cellular telecommunication system that authenticates the identity of
the subscriber with the help of challenge response mechanism.
(b). It is generally impossible for two messages to generate identical message digest and
therefore, cryptographic hash functions are often used to detect whether a message is altered.
This is done by computing the digest of a file called the base line digest. If at any point of time, a
digest differs from its baseline digest, it can be concluded that the file has been altered.
Therefore, hash functions are rightly used to provide data integrity as an attacker cannot make
any unauthorized change without being detected.
Question 2
(a). ECB is not generally recommended for encryption of long messages because –
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



