Data Protection in SaaS HR Applications: Security Analysis
VerifiedAdded on 2022/12/23
|33
|2718
|65
Report
AI Summary
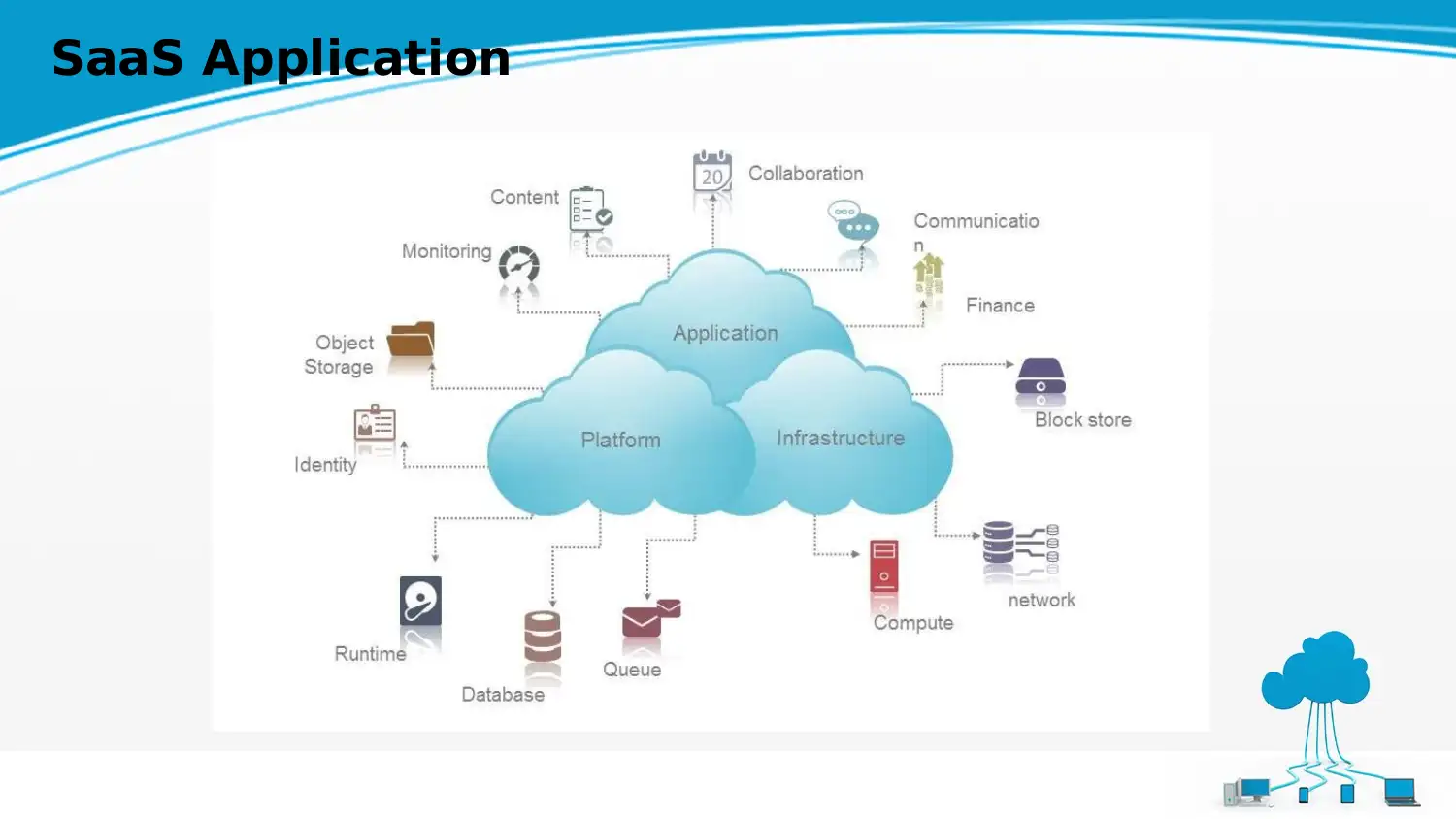
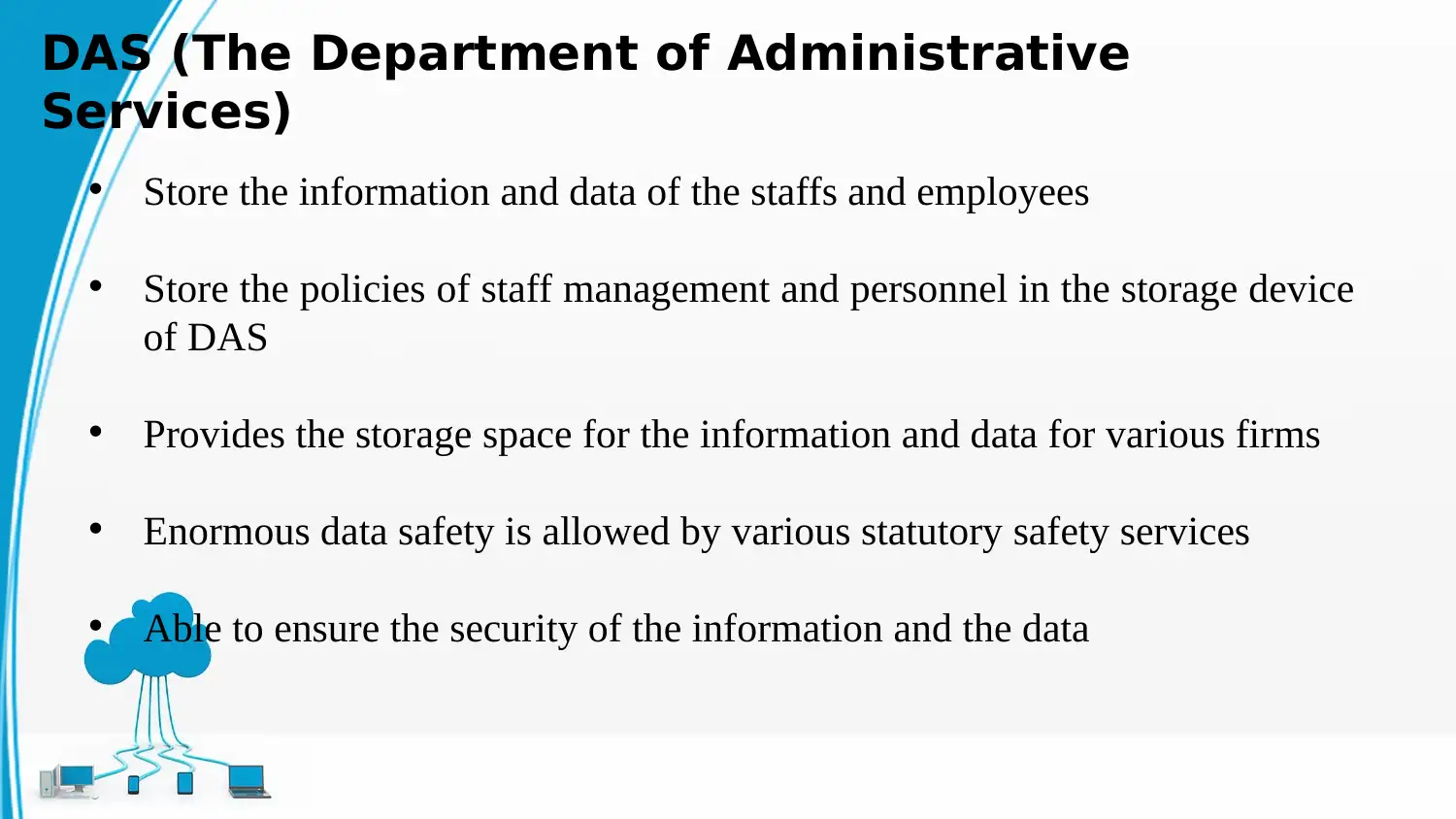
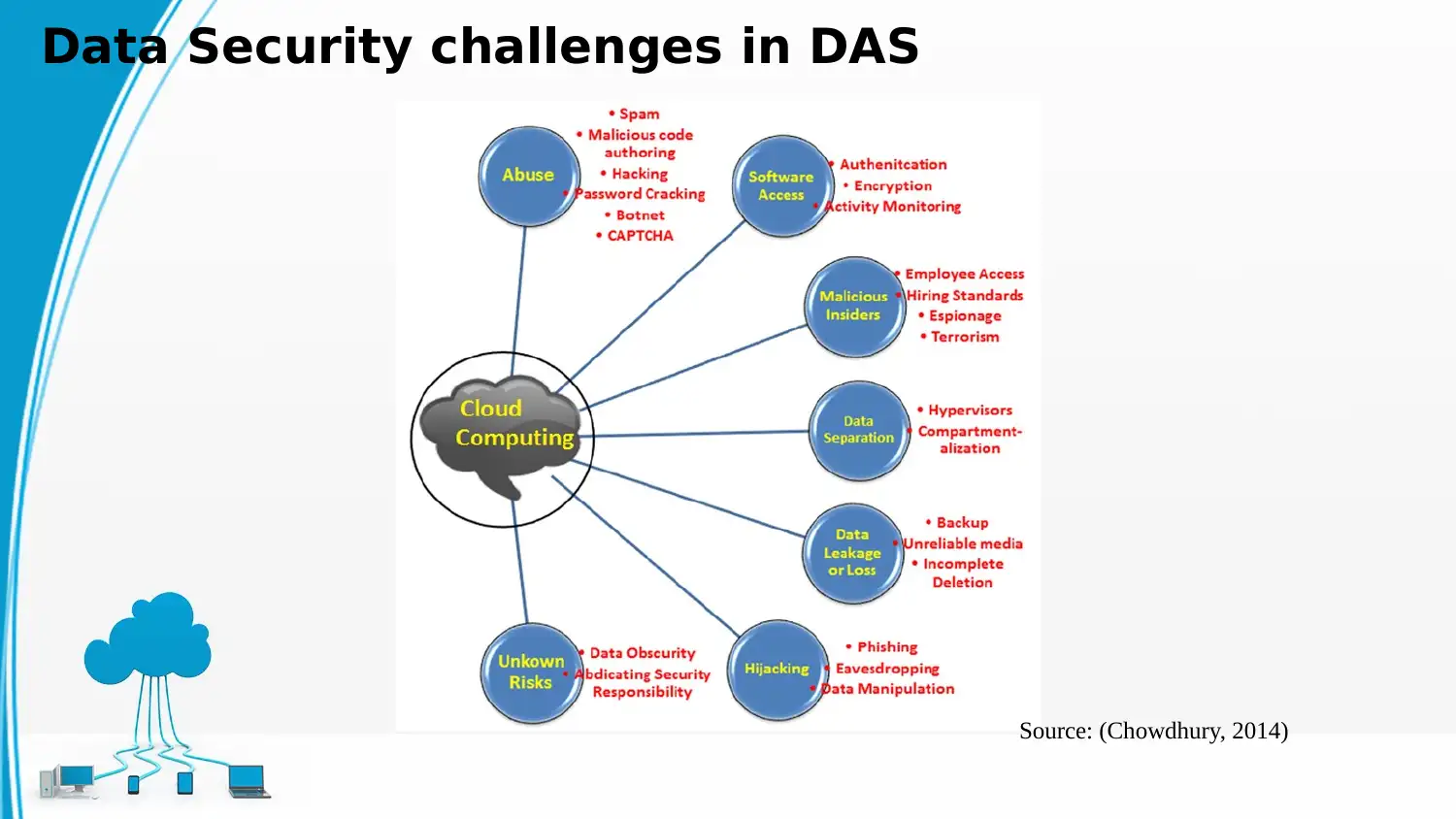
This report examines data protection strategies within cloud environments, focusing on SaaS applications used by the Department of Administrative Services (DAS) for HR and personnel management. It discusses the impacts of SaaS applications, including the protection of sensitive data using Cloud Access Security Brokers (CASBs), and analyzes operational solutions for SaaS applications, highlighting the importance of centralized management and policy enforcement. The report identifies data security challenges such as privilege abuse, database input injection, malware, and excessive rights, and proposes operational solutions for ensuring the privacy and security of employee data, addressing digital identity, data sensitivity, and data sovereignty. It further explores security and privacy implications for DAS, including identity governance, forensics and detection, manageability, encryption, standards, compliance, and management. The report concludes by emphasizing the importance of hazard leadership and the role of SaaS providers in mitigating security threats, referencing various studies and frameworks relevant to cloud security and data protection.
1 out of 33















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)