Cloud Security Report: Risks to Employee Data Security in SaaS
VerifiedAdded on 2020/03/07
|12
|2975
|261
Report
AI Summary
This report examines the cloud security risks and privacy concerns related to employee data, specifically within a Software as a Service (SaaS) environment. The report, prepared for the Department of Administrative Service (DAS) in Australia, assesses various security threats, including non-existent security architecture, unpatched software, phishing attacks, and poor configuration management. It also explores new threats arising from SaaS adoption, such as insider threats, poor passwords, and physical security vulnerabilities. The report analyzes the likelihood, impact, and priority of each risk, proposing preventive actions and contingency plans. Furthermore, it addresses privacy issues like computer monitoring, telephone monitoring, and internet usage monitoring, along with new privacy risks associated with SaaS, such as distant corporate control and data breaches. The report also discusses digital identity issues, provider solution challenges, and solution architecture considerations for ensuring data security and privacy. The severity of risks and threats to employee data security and privacy are thoroughly evaluated, providing a comprehensive overview of cloud security challenges and potential solutions for DAS.

Running head: Cloud Security
Cloud Security
Name of the student
Name of the University
Author Note
Cloud Security
Name of the student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD SECURITY
Table of Contents
Introduction:..........................................................................................................................................2
Security of Employee Data.................................................................................................................2
New Security Threat to Employee data(after moving to SaaS)..............................................................4
Severity of risk and threat to security employee data.......................................................................5
Privacy of Employee Data......................................................................................................................5
Existing privacy threats and risks to the privacy of employee data...................................................5
Severity of risk and threat toprivacy employee data........................................................................7
Digital Identity Issues.............................................................................................................................8
Provider Solution Issues and why?........................................................................................................8
Solution Architecture including security and Privacy.............................................................................9
Data Sensitivity......................................................................................................................................9
Conclusion:..........................................................................................................................................10
References:..........................................................................................................................................11
Table of Contents
Introduction:..........................................................................................................................................2
Security of Employee Data.................................................................................................................2
New Security Threat to Employee data(after moving to SaaS)..............................................................4
Severity of risk and threat to security employee data.......................................................................5
Privacy of Employee Data......................................................................................................................5
Existing privacy threats and risks to the privacy of employee data...................................................5
Severity of risk and threat toprivacy employee data........................................................................7
Digital Identity Issues.............................................................................................................................8
Provider Solution Issues and why?........................................................................................................8
Solution Architecture including security and Privacy.............................................................................9
Data Sensitivity......................................................................................................................................9
Conclusion:..........................................................................................................................................10
References:..........................................................................................................................................11
CLOUD SECURITY
Introduction:
Department of Administrative Service (DAS) is delivering various services for the different
departments of the state government in Australia. The data centre of the department of DAS is
delivering the services for the department.
A new service provider is being introduced to DAS to implement new program in the system that is
Software as a Service (Saas) which is a centrally hosted licensing model and software delivery. A
team has been introduced to deliver a risk management program that will identify the threats and
risks to the privacy and security of data of employee working in DAS. A severity matrix have also
been proposed to validate which risk is most critical, which needs least consideration and which can
cause medium impact to the privacy and security of the employees of DAS.
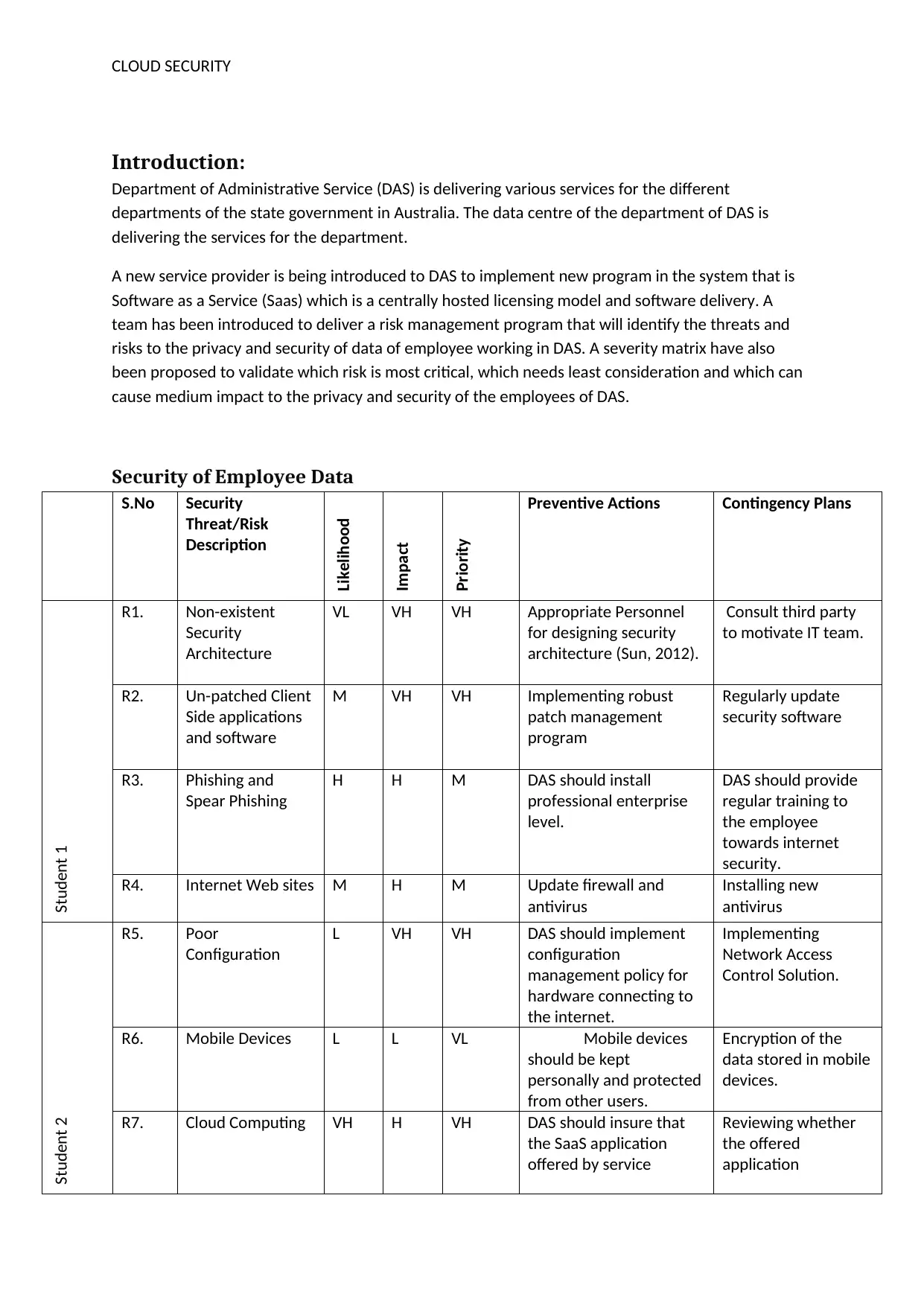
Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R1. Non-existent
Security
Architecture
VL VH VH Appropriate Personnel
for designing security
architecture (Sun, 2012).
Consult third party
to motivate IT team.
R2. Un-patched Client
Side applications
and software
M VH VH Implementing robust
patch management
program
Regularly update
security software
R3. Phishing and
Spear Phishing
H H M DAS should install
professional enterprise
level.
DAS should provide
regular training to
the employee
towards internet
security.
R4. Internet Web sites M H M Update firewall and
antivirus
Installing new
antivirus
R5. Poor
Configuration
L VH VH DAS should implement
configuration
management policy for
hardware connecting to
the internet.
Implementing
Network Access
Control Solution.
Student 2
R6. Mobile Devices L L VL Mobile devices
should be kept
personally and protected
from other users.
Encryption of the
data stored in mobile
devices.
R7. Cloud Computing VH H VH DAS should insure that
the SaaS application
offered by service
Reviewing whether
the offered
application
Introduction:
Department of Administrative Service (DAS) is delivering various services for the different
departments of the state government in Australia. The data centre of the department of DAS is
delivering the services for the department.
A new service provider is being introduced to DAS to implement new program in the system that is
Software as a Service (Saas) which is a centrally hosted licensing model and software delivery. A
team has been introduced to deliver a risk management program that will identify the threats and
risks to the privacy and security of data of employee working in DAS. A severity matrix have also
been proposed to validate which risk is most critical, which needs least consideration and which can
cause medium impact to the privacy and security of the employees of DAS.
Security of Employee Data
S.No Security
Threat/Risk
Description
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R1. Non-existent
Security
Architecture
VL VH VH Appropriate Personnel
for designing security
architecture (Sun, 2012).
Consult third party
to motivate IT team.
R2. Un-patched Client
Side applications
and software
M VH VH Implementing robust
patch management
program
Regularly update
security software
R3. Phishing and
Spear Phishing
H H M DAS should install
professional enterprise
level.
DAS should provide
regular training to
the employee
towards internet
security.
R4. Internet Web sites M H M Update firewall and
antivirus
Installing new
antivirus
R5. Poor
Configuration
L VH VH DAS should implement
configuration
management policy for
hardware connecting to
the internet.
Implementing
Network Access
Control Solution.
Student 2
R6. Mobile Devices L L VL Mobile devices
should be kept
personally and protected
from other users.
Encryption of the
data stored in mobile
devices.
R7. Cloud Computing VH H VH DAS should insure that
the SaaS application
offered by service
Reviewing whether
the offered
application
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
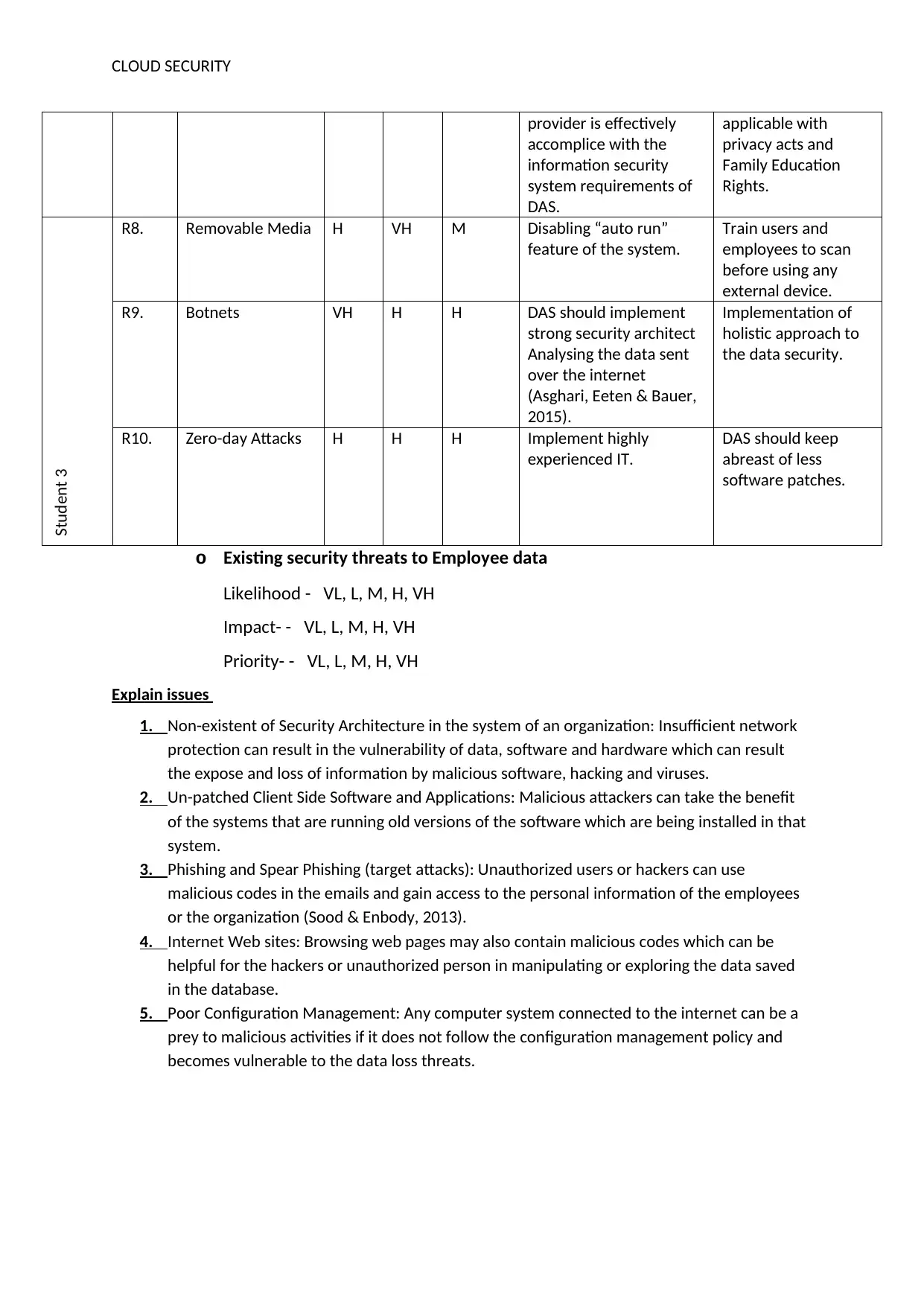
CLOUD SECURITY
provider is effectively
accomplice with the
information security
system requirements of
DAS.
applicable with
privacy acts and
Family Education
Rights.
Student 3
R8. Removable Media H VH M Disabling “auto run”
feature of the system.
Train users and
employees to scan
before using any
external device.
R9. Botnets VH H H DAS should implement
strong security architect
Analysing the data sent
over the internet
(Asghari, Eeten & Bauer,
2015).
Implementation of
holistic approach to
the data security.
R10. Zero-day Attacks H H H Implement highly
experienced IT.
DAS should keep
abreast of less
software patches.
o Existing security threats to Employee data
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Non-existent of Security Architecture in the system of an organization: Insufficient network
protection can result in the vulnerability of data, software and hardware which can result
the expose and loss of information by malicious software, hacking and viruses.
2. Un-patched Client Side Software and Applications: Malicious attackers can take the benefit
of the systems that are running old versions of the software which are being installed in that
system.
3. Phishing and Spear Phishing (target attacks): Unauthorized users or hackers can use
malicious codes in the emails and gain access to the personal information of the employees
or the organization (Sood & Enbody, 2013).
4. Internet Web sites: Browsing web pages may also contain malicious codes which can be
helpful for the hackers or unauthorized person in manipulating or exploring the data saved
in the database.
5. Poor Configuration Management: Any computer system connected to the internet can be a
prey to malicious activities if it does not follow the configuration management policy and
becomes vulnerable to the data loss threats.
provider is effectively
accomplice with the
information security
system requirements of
DAS.
applicable with
privacy acts and
Family Education
Rights.
Student 3
R8. Removable Media H VH M Disabling “auto run”
feature of the system.
Train users and
employees to scan
before using any
external device.
R9. Botnets VH H H DAS should implement
strong security architect
Analysing the data sent
over the internet
(Asghari, Eeten & Bauer,
2015).
Implementation of
holistic approach to
the data security.
R10. Zero-day Attacks H H H Implement highly
experienced IT.
DAS should keep
abreast of less
software patches.
o Existing security threats to Employee data
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Non-existent of Security Architecture in the system of an organization: Insufficient network
protection can result in the vulnerability of data, software and hardware which can result
the expose and loss of information by malicious software, hacking and viruses.
2. Un-patched Client Side Software and Applications: Malicious attackers can take the benefit
of the systems that are running old versions of the software which are being installed in that
system.
3. Phishing and Spear Phishing (target attacks): Unauthorized users or hackers can use
malicious codes in the emails and gain access to the personal information of the employees
or the organization (Sood & Enbody, 2013).
4. Internet Web sites: Browsing web pages may also contain malicious codes which can be
helpful for the hackers or unauthorized person in manipulating or exploring the data saved
in the database.
5. Poor Configuration Management: Any computer system connected to the internet can be a
prey to malicious activities if it does not follow the configuration management policy and
becomes vulnerable to the data loss threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
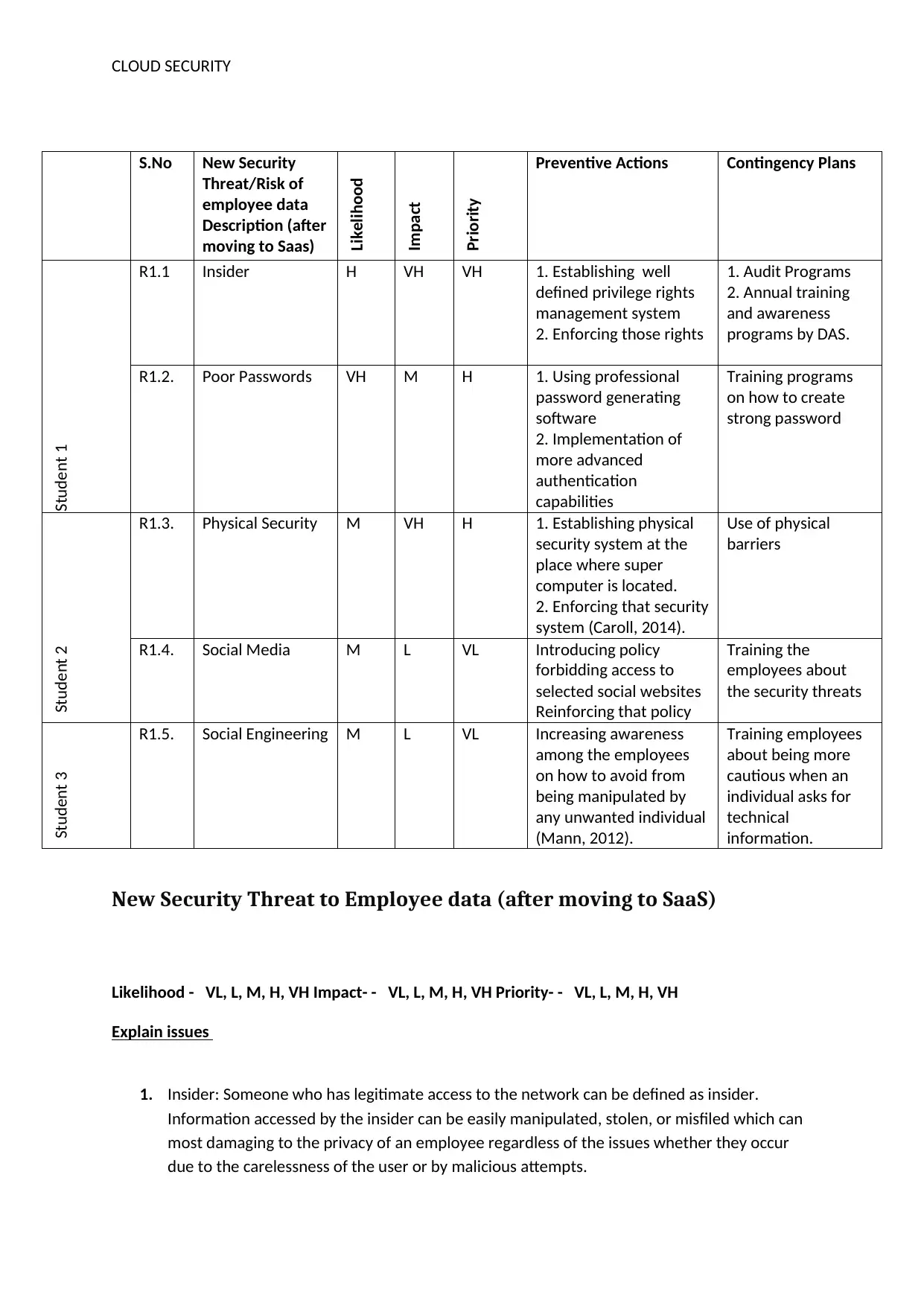
CLOUD SECURITY
S.No New Security
Threat/Risk of
employee data
Description (after
moving to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R1.1 Insider H VH VH 1. Establishing well
defined privilege rights
management system
2. Enforcing those rights
1. Audit Programs
2. Annual training
and awareness
programs by DAS.
R1.2. Poor Passwords VH M H 1. Using professional
password generating
software
2. Implementation of
more advanced
authentication
capabilities
Training programs
on how to create
strong password
Student 2
R1.3. Physical Security M VH H 1. Establishing physical
security system at the
place where super
computer is located.
2. Enforcing that security
system (Caroll, 2014).
Use of physical
barriers
R1.4. Social Media M L VL Introducing policy
forbidding access to
selected social websites
Reinforcing that policy
Training the
employees about
the security threats
Student 3
R1.5. Social Engineering M L VL Increasing awareness
among the employees
on how to avoid from
being manipulated by
any unwanted individual
(Mann, 2012).
Training employees
about being more
cautious when an
individual asks for
technical
information.
New Security Threat to Employee data (after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
Explain issues
1. Insider: Someone who has legitimate access to the network can be defined as insider.
Information accessed by the insider can be easily manipulated, stolen, or misfiled which can
most damaging to the privacy of an employee regardless of the issues whether they occur
due to the carelessness of the user or by malicious attempts.
S.No New Security
Threat/Risk of
employee data
Description (after
moving to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1
R1.1 Insider H VH VH 1. Establishing well
defined privilege rights
management system
2. Enforcing those rights
1. Audit Programs
2. Annual training
and awareness
programs by DAS.
R1.2. Poor Passwords VH M H 1. Using professional
password generating
software
2. Implementation of
more advanced
authentication
capabilities
Training programs
on how to create
strong password
Student 2
R1.3. Physical Security M VH H 1. Establishing physical
security system at the
place where super
computer is located.
2. Enforcing that security
system (Caroll, 2014).
Use of physical
barriers
R1.4. Social Media M L VL Introducing policy
forbidding access to
selected social websites
Reinforcing that policy
Training the
employees about
the security threats
Student 3
R1.5. Social Engineering M L VL Increasing awareness
among the employees
on how to avoid from
being manipulated by
any unwanted individual
(Mann, 2012).
Training employees
about being more
cautious when an
individual asks for
technical
information.
New Security Threat to Employee data (after moving to SaaS)
Likelihood - VL, L, M, H, VH Impact- - VL, L, M, H, VH Priority- - VL, L, M, H, VH
Explain issues
1. Insider: Someone who has legitimate access to the network can be defined as insider.
Information accessed by the insider can be easily manipulated, stolen, or misfiled which can
most damaging to the privacy of an employee regardless of the issues whether they occur
due to the carelessness of the user or by malicious attempts.
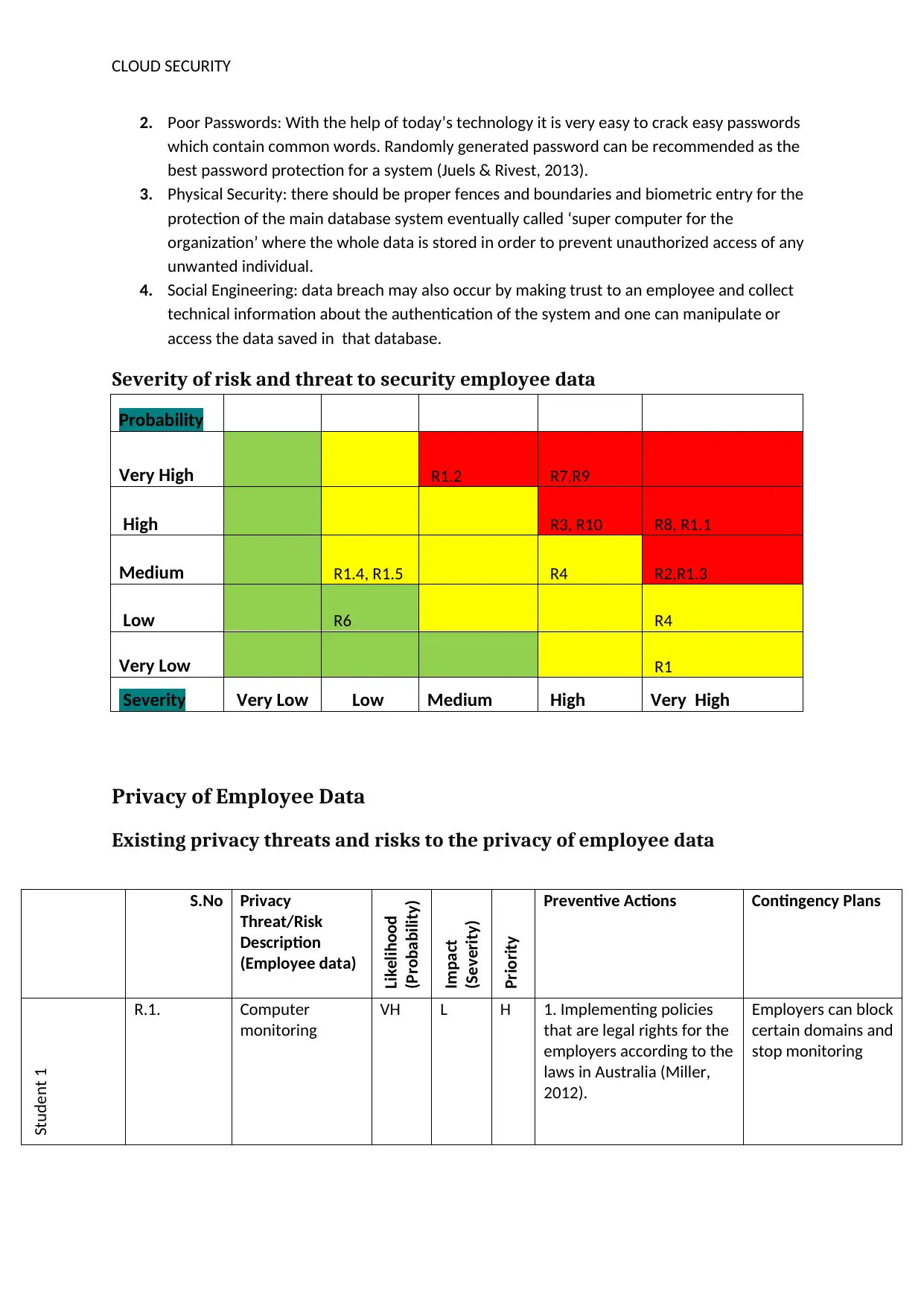
CLOUD SECURITY
2. Poor Passwords: With the help of today’s technology it is very easy to crack easy passwords
which contain common words. Randomly generated password can be recommended as the
best password protection for a system (Juels & Rivest, 2013).
3. Physical Security: there should be proper fences and boundaries and biometric entry for the
protection of the main database system eventually called ‘super computer for the
organization’ where the whole data is stored in order to prevent unauthorized access of any
unwanted individual.
4. Social Engineering: data breach may also occur by making trust to an employee and collect
technical information about the authentication of the system and one can manipulate or
access the data saved in that database.
Severity of risk and threat to security employee data
Probability
Very High R1.2 R7,R9
High R3, R10 R8, R1.1
Medium R1.4, R1.5 R4 R2,R1.3
Low R6 R4
Very Low R1
Severity Very Low Low Medium High Very High
Privacy of Employee Data
Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk
Description
(Employee data)
Likelihood
(Probability)
Impact
(Severity)
Priority
Preventive Actions Contingency Plans
Student 1
R.1. Computer
monitoring
VH L H 1. Implementing policies
that are legal rights for the
employers according to the
laws in Australia (Miller,
2012).
Employers can block
certain domains and
stop monitoring
2. Poor Passwords: With the help of today’s technology it is very easy to crack easy passwords
which contain common words. Randomly generated password can be recommended as the
best password protection for a system (Juels & Rivest, 2013).
3. Physical Security: there should be proper fences and boundaries and biometric entry for the
protection of the main database system eventually called ‘super computer for the
organization’ where the whole data is stored in order to prevent unauthorized access of any
unwanted individual.
4. Social Engineering: data breach may also occur by making trust to an employee and collect
technical information about the authentication of the system and one can manipulate or
access the data saved in that database.
Severity of risk and threat to security employee data
Probability
Very High R1.2 R7,R9
High R3, R10 R8, R1.1
Medium R1.4, R1.5 R4 R2,R1.3
Low R6 R4
Very Low R1
Severity Very Low Low Medium High Very High
Privacy of Employee Data
Existing privacy threats and risks to the privacy of employee data
S.No Privacy
Threat/Risk
Description
(Employee data)
Likelihood
(Probability)
Impact
(Severity)
Priority
Preventive Actions Contingency Plans
Student 1
R.1. Computer
monitoring
VH L H 1. Implementing policies
that are legal rights for the
employers according to the
laws in Australia (Miller,
2012).
Employers can block
certain domains and
stop monitoring
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CLOUD SECURITY
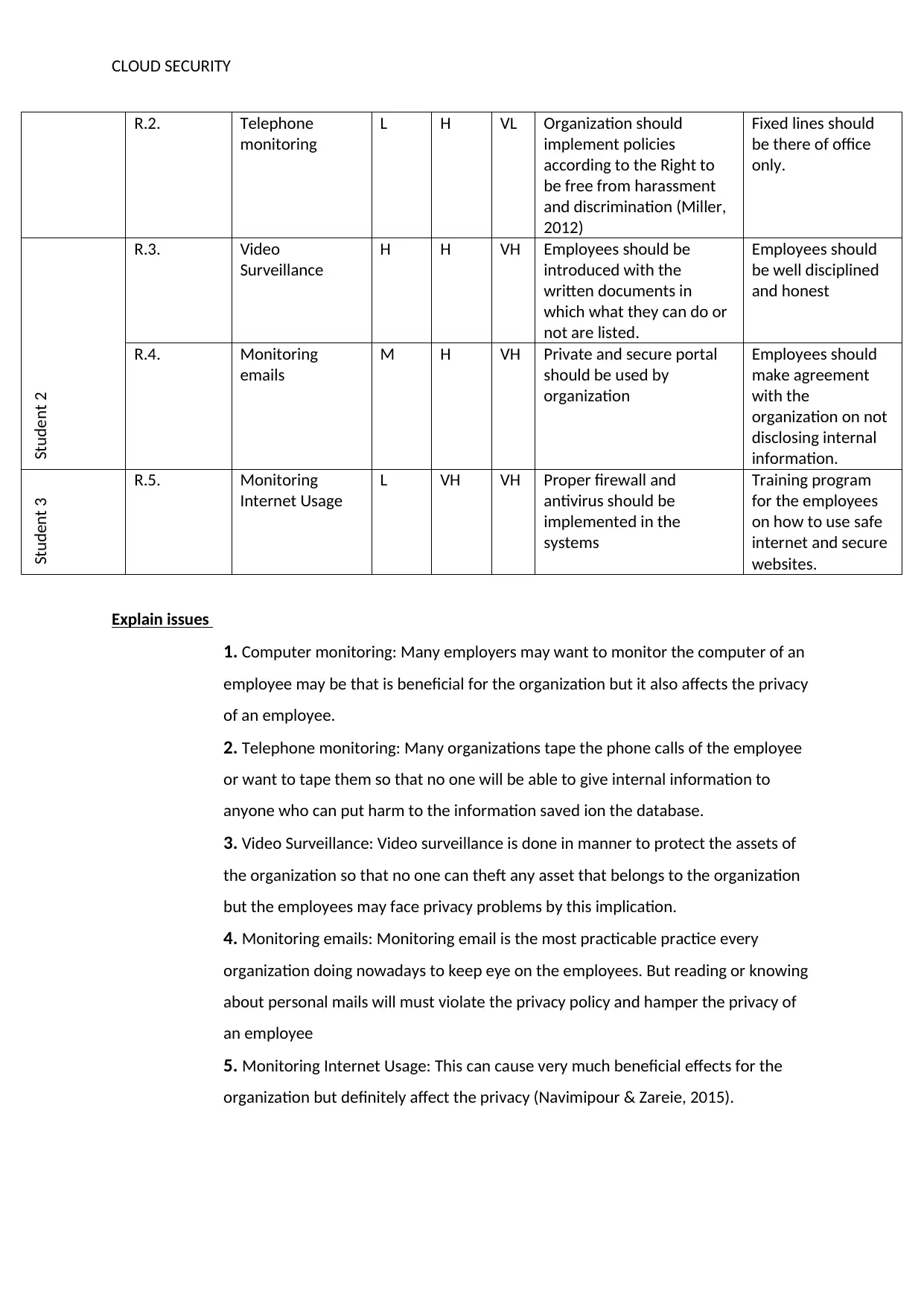
R.2. Telephone
monitoring
L H VL Organization should
implement policies
according to the Right to
be free from harassment
and discrimination (Miller,
2012)
Fixed lines should
be there of office
only.
Student 2
R.3. Video
Surveillance
H H VH Employees should be
introduced with the
written documents in
which what they can do or
not are listed.
Employees should
be well disciplined
and honest
R.4. Monitoring
emails
M H VH Private and secure portal
should be used by
organization
Employees should
make agreement
with the
organization on not
disclosing internal
information.
Student 3 R.5. Monitoring
Internet Usage
L VH VH Proper firewall and
antivirus should be
implemented in the
systems
Training program
for the employees
on how to use safe
internet and secure
websites.
Explain issues
1. Computer monitoring: Many employers may want to monitor the computer of an
employee may be that is beneficial for the organization but it also affects the privacy
of an employee.
2. Telephone monitoring: Many organizations tape the phone calls of the employee
or want to tape them so that no one will be able to give internal information to
anyone who can put harm to the information saved ion the database.
3. Video Surveillance: Video surveillance is done in manner to protect the assets of
the organization so that no one can theft any asset that belongs to the organization
but the employees may face privacy problems by this implication.
4. Monitoring emails: Monitoring email is the most practicable practice every
organization doing nowadays to keep eye on the employees. But reading or knowing
about personal mails will must violate the privacy policy and hamper the privacy of
an employee
5. Monitoring Internet Usage: This can cause very much beneficial effects for the
organization but definitely affect the privacy (Navimipour & Zareie, 2015).
R.2. Telephone
monitoring
L H VL Organization should
implement policies
according to the Right to
be free from harassment
and discrimination (Miller,
2012)
Fixed lines should
be there of office
only.
Student 2
R.3. Video
Surveillance
H H VH Employees should be
introduced with the
written documents in
which what they can do or
not are listed.
Employees should
be well disciplined
and honest
R.4. Monitoring
emails
M H VH Private and secure portal
should be used by
organization
Employees should
make agreement
with the
organization on not
disclosing internal
information.
Student 3 R.5. Monitoring
Internet Usage
L VH VH Proper firewall and
antivirus should be
implemented in the
systems
Training program
for the employees
on how to use safe
internet and secure
websites.
Explain issues
1. Computer monitoring: Many employers may want to monitor the computer of an
employee may be that is beneficial for the organization but it also affects the privacy
of an employee.
2. Telephone monitoring: Many organizations tape the phone calls of the employee
or want to tape them so that no one will be able to give internal information to
anyone who can put harm to the information saved ion the database.
3. Video Surveillance: Video surveillance is done in manner to protect the assets of
the organization so that no one can theft any asset that belongs to the organization
but the employees may face privacy problems by this implication.
4. Monitoring emails: Monitoring email is the most practicable practice every
organization doing nowadays to keep eye on the employees. But reading or knowing
about personal mails will must violate the privacy policy and hamper the privacy of
an employee
5. Monitoring Internet Usage: This can cause very much beneficial effects for the
organization but definitely affect the privacy (Navimipour & Zareie, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CLOUD SECURITY
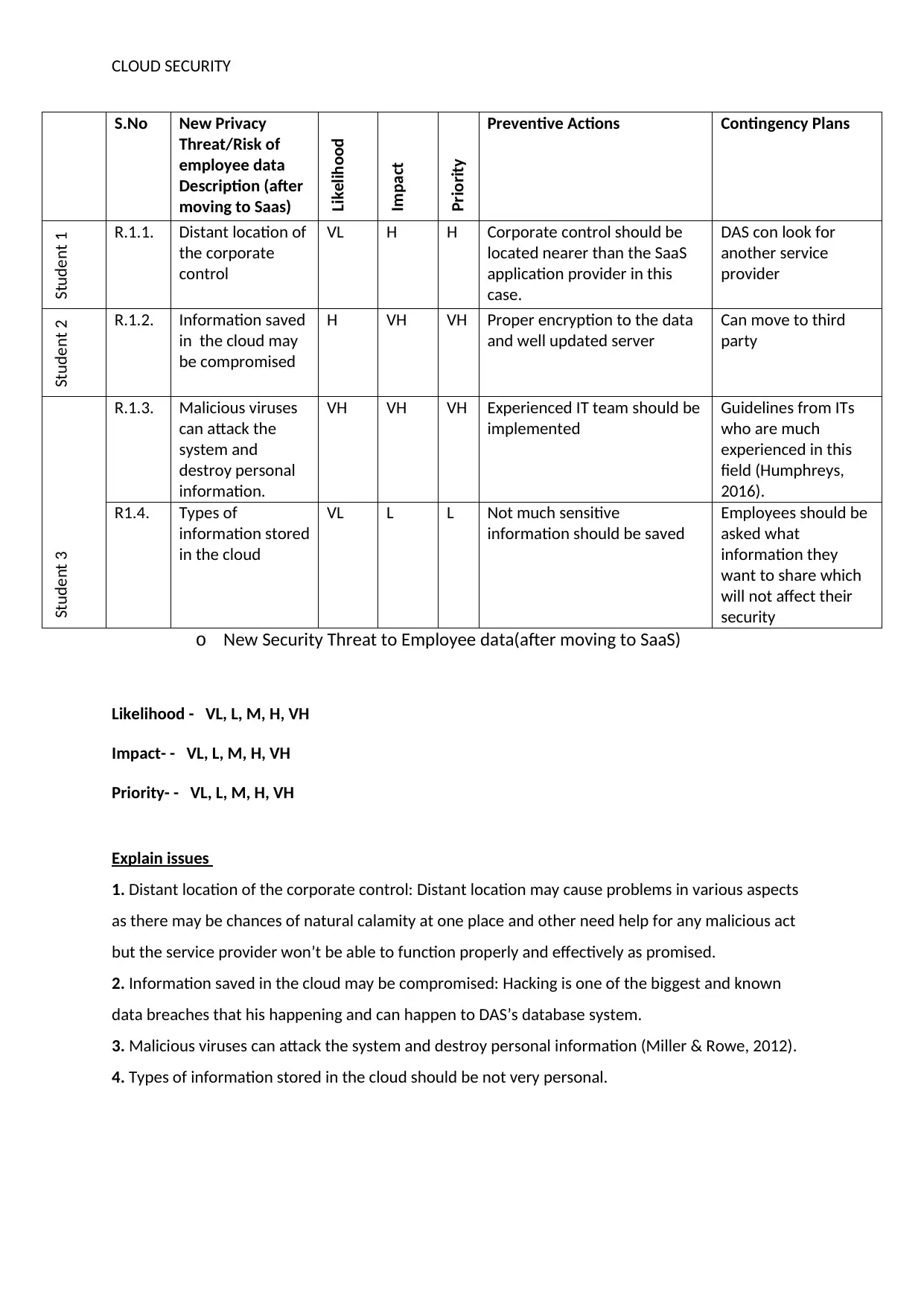
S.No New Privacy
Threat/Risk of
employee data
Description (after
moving to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1 R.1.1. Distant location of
the corporate
control
VL H H Corporate control should be
located nearer than the SaaS
application provider in this
case.
DAS con look for
another service
provider
Student 2 R.1.2. Information saved
in the cloud may
be compromised
H VH VH Proper encryption to the data
and well updated server
Can move to third
party
Student 3
R.1.3. Malicious viruses
can attack the
system and
destroy personal
information.
VH VH VH Experienced IT team should be
implemented
Guidelines from ITs
who are much
experienced in this
field (Humphreys,
2016).
R1.4. Types of
information stored
in the cloud
VL L L Not much sensitive
information should be saved
Employees should be
asked what
information they
want to share which
will not affect their
security
o New Security Threat to Employee data(after moving to SaaS)
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Distant location of the corporate control: Distant location may cause problems in various aspects
as there may be chances of natural calamity at one place and other need help for any malicious act
but the service provider won’t be able to function properly and effectively as promised.
2. Information saved in the cloud may be compromised: Hacking is one of the biggest and known
data breaches that his happening and can happen to DAS’s database system.
3. Malicious viruses can attack the system and destroy personal information (Miller & Rowe, 2012).
4. Types of information stored in the cloud should be not very personal.
S.No New Privacy
Threat/Risk of
employee data
Description (after
moving to Saas)
Likelihood
Impact
Priority
Preventive Actions Contingency Plans
Student 1 R.1.1. Distant location of
the corporate
control
VL H H Corporate control should be
located nearer than the SaaS
application provider in this
case.
DAS con look for
another service
provider
Student 2 R.1.2. Information saved
in the cloud may
be compromised
H VH VH Proper encryption to the data
and well updated server
Can move to third
party
Student 3
R.1.3. Malicious viruses
can attack the
system and
destroy personal
information.
VH VH VH Experienced IT team should be
implemented
Guidelines from ITs
who are much
experienced in this
field (Humphreys,
2016).
R1.4. Types of
information stored
in the cloud
VL L L Not much sensitive
information should be saved
Employees should be
asked what
information they
want to share which
will not affect their
security
o New Security Threat to Employee data(after moving to SaaS)
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Distant location of the corporate control: Distant location may cause problems in various aspects
as there may be chances of natural calamity at one place and other need help for any malicious act
but the service provider won’t be able to function properly and effectively as promised.
2. Information saved in the cloud may be compromised: Hacking is one of the biggest and known
data breaches that his happening and can happen to DAS’s database system.
3. Malicious viruses can attack the system and destroy personal information (Miller & Rowe, 2012).
4. Types of information stored in the cloud should be not very personal.
CLOUD SECURITY
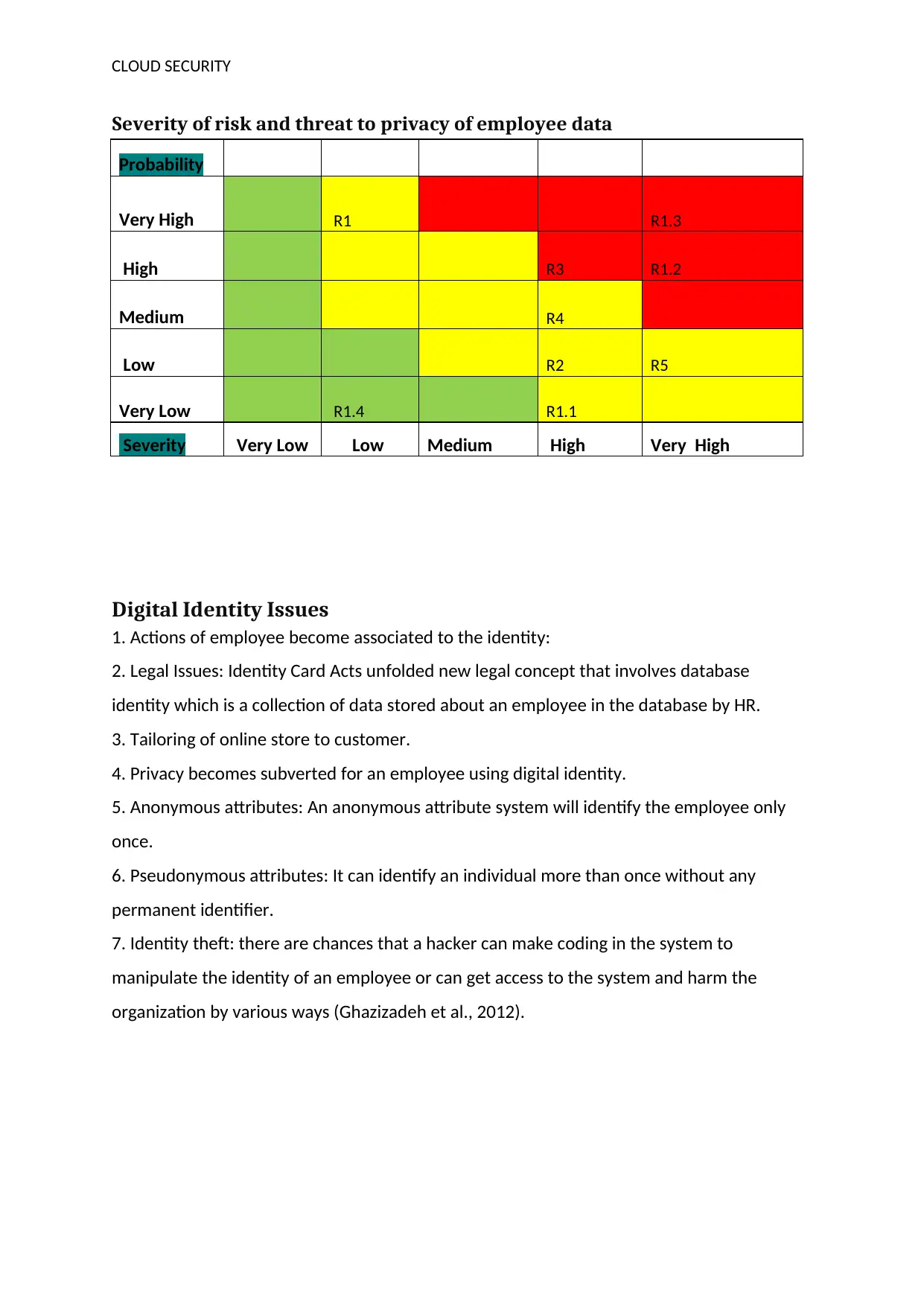
Severity of risk and threat to privacy of employee data
Probability
Very High R1 R1.3
High R3 R1.2
Medium R4
Low R2 R5
Very Low R1.4 R1.1
Severity Very Low Low Medium High Very High
Digital Identity Issues
1. Actions of employee become associated to the identity:
2. Legal Issues: Identity Card Acts unfolded new legal concept that involves database
identity which is a collection of data stored about an employee in the database by HR.
3. Tailoring of online store to customer.
4. Privacy becomes subverted for an employee using digital identity.
5. Anonymous attributes: An anonymous attribute system will identify the employee only
once.
6. Pseudonymous attributes: It can identify an individual more than once without any
permanent identifier.
7. Identity theft: there are chances that a hacker can make coding in the system to
manipulate the identity of an employee or can get access to the system and harm the
organization by various ways (Ghazizadeh et al., 2012).
Severity of risk and threat to privacy of employee data
Probability
Very High R1 R1.3
High R3 R1.2
Medium R4
Low R2 R5
Very Low R1.4 R1.1
Severity Very Low Low Medium High Very High
Digital Identity Issues
1. Actions of employee become associated to the identity:
2. Legal Issues: Identity Card Acts unfolded new legal concept that involves database
identity which is a collection of data stored about an employee in the database by HR.
3. Tailoring of online store to customer.
4. Privacy becomes subverted for an employee using digital identity.
5. Anonymous attributes: An anonymous attribute system will identify the employee only
once.
6. Pseudonymous attributes: It can identify an individual more than once without any
permanent identifier.
7. Identity theft: there are chances that a hacker can make coding in the system to
manipulate the identity of an employee or can get access to the system and harm the
organization by various ways (Ghazizadeh et al., 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CLOUD SECURITY
Provider Solution Issues and why?
1. The process could be highly private, in which DAS manages the HR and contract
managers: For any case which is irrelevant and not appropriate for the data stored
in the system, managers should look onto features and capabilities of DAS.
2. Applicant tracking: It considers managers capability of posting jobs for the
employees, applications and boarding latest employers.
3. HRMS software offered can have beneficial effects to the administration: This can
help in offering beneficial plans to the clients by varying easy managing of employee
enrollment.
4. Performance management: It is the ability to keep records of the aims of
employees and can manipulate them in manner to enhance the performance of an
organization (Uddin, Luva & hossain, 2012).
Solution Architecture including security and Privacy
Figure: Solution Architecture including security and privacy
(Source: Created by author)
Data Sensitivity
Sensitive data and issues related to sensitive data
Provider Solution Issues and why?
1. The process could be highly private, in which DAS manages the HR and contract
managers: For any case which is irrelevant and not appropriate for the data stored
in the system, managers should look onto features and capabilities of DAS.
2. Applicant tracking: It considers managers capability of posting jobs for the
employees, applications and boarding latest employers.
3. HRMS software offered can have beneficial effects to the administration: This can
help in offering beneficial plans to the clients by varying easy managing of employee
enrollment.
4. Performance management: It is the ability to keep records of the aims of
employees and can manipulate them in manner to enhance the performance of an
organization (Uddin, Luva & hossain, 2012).
Solution Architecture including security and Privacy
Figure: Solution Architecture including security and privacy
(Source: Created by author)
Data Sensitivity
Sensitive data and issues related to sensitive data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CLOUD SECURITY
There are various considerable issues of data sensitivity or jurisdiction in this case makes iot
crucial to list out each relevant consideration that can be implemented in data sensitivity
policies.
There are not same requirements for the protection of each data such as intellectual
property and financial records of the corporate of the DAS. It can be seen that the
availability of the data on which the business’s life and continuity was dependent are
critical. The spoofing and substituting of data or other malicious matters that can cause
system to behave improperly are the moment assuring data integrity.
Conclusion:
Based on the above report it can be concluded that the privacy and security issues in the
implementation of new SaaS program into DAS has been successfully examined based on
the severity matrix which is proposed above in the report. There are various risks in
implementing this new SaaS software in DAS which can seriously affect the organization but
it can be mitigated or completely eliminated by the measures discussed above. Data Control
location was established far away which can also result in various security and privacy
threats to the data of the employee saved in the HR database.
There are various considerable issues of data sensitivity or jurisdiction in this case makes iot
crucial to list out each relevant consideration that can be implemented in data sensitivity
policies.
There are not same requirements for the protection of each data such as intellectual
property and financial records of the corporate of the DAS. It can be seen that the
availability of the data on which the business’s life and continuity was dependent are
critical. The spoofing and substituting of data or other malicious matters that can cause
system to behave improperly are the moment assuring data integrity.
Conclusion:
Based on the above report it can be concluded that the privacy and security issues in the
implementation of new SaaS program into DAS has been successfully examined based on
the severity matrix which is proposed above in the report. There are various risks in
implementing this new SaaS software in DAS which can seriously affect the organization but
it can be mitigated or completely eliminated by the measures discussed above. Data Control
location was established far away which can also result in various security and privacy
threats to the data of the employee saved in the HR database.

CLOUD SECURITY
References:
Asghari, H., van Eeten, M. J., & Bauer, J. M. (2015). Economics of fighting botnets: Lessons from a
decade of mitigation. IEEE Security & Privacy, 13(5), 16-23.
Carroll, J. M. (2014). Computer security. Butterworth-Heinemann.
Ghazizadeh, E., Zamani, M., Khaleghparast, R., & Taherian, A. (2012, December). A trust based model
for federated identity architecture to mitigate identity theft. In Internet Technology And
Secured Transactions, 2012 International Conference for (pp. 376-381). IEEE.
Humphreys, E. (2016). Implementing the ISO/IEC 27001: 2013 ISMS Standard. Artech House.
Juels, A., & Rivest, R. L. (2013, November). Honeywords: Making password-cracking
detectable. In Proceedings of the 2013 ACM SIGSAC conference on Computer &
communications security (pp. 145-160). ACM.
Mann, M. I. (2012). Hacking the human: social engineering techniques and security
countermeasures. Gower Publishing, Ltd..
Miller, B., & Rowe, D. (2012, October). A survey SCADA of and critical infrastructure incidents.
In Proceedings of the 1st Annual conference on Research in information technology (pp. 51-
56). ACM.
Miller, K. W., Voas, J., & Hurlburt, G. F. (2012). BYOD: Security and privacy considerations. It
Professional, 14(5), 53-55.
Navimipour, N. J., & Zareie, B. (2015). A model for assessing the impact of e-learning systems on
employees’ satisfaction. Computers in Human Behavior, 53, 475-485.
Sood, A. K., & Enbody, R. J. (2013). Targeted cyberattacks: a superset of advanced persistent
threats. IEEE security & privacy, 11(1), 54-61.
Sun, X. (2012). A systematic approach for migrating enterprise networks(Doctoral dissertation,
Purdue University).
Uddin, M. J., Luva, R. H., & Hossain, S. M. M. (2012). Impact of organizational culture on employee
performance and productivity: a case study of telecommunication sector in
Bangladesh. International Journal of Business and Management, 8(2), 63.
References:
Asghari, H., van Eeten, M. J., & Bauer, J. M. (2015). Economics of fighting botnets: Lessons from a
decade of mitigation. IEEE Security & Privacy, 13(5), 16-23.
Carroll, J. M. (2014). Computer security. Butterworth-Heinemann.
Ghazizadeh, E., Zamani, M., Khaleghparast, R., & Taherian, A. (2012, December). A trust based model
for federated identity architecture to mitigate identity theft. In Internet Technology And
Secured Transactions, 2012 International Conference for (pp. 376-381). IEEE.
Humphreys, E. (2016). Implementing the ISO/IEC 27001: 2013 ISMS Standard. Artech House.
Juels, A., & Rivest, R. L. (2013, November). Honeywords: Making password-cracking
detectable. In Proceedings of the 2013 ACM SIGSAC conference on Computer &
communications security (pp. 145-160). ACM.
Mann, M. I. (2012). Hacking the human: social engineering techniques and security
countermeasures. Gower Publishing, Ltd..
Miller, B., & Rowe, D. (2012, October). A survey SCADA of and critical infrastructure incidents.
In Proceedings of the 1st Annual conference on Research in information technology (pp. 51-
56). ACM.
Miller, K. W., Voas, J., & Hurlburt, G. F. (2012). BYOD: Security and privacy considerations. It
Professional, 14(5), 53-55.
Navimipour, N. J., & Zareie, B. (2015). A model for assessing the impact of e-learning systems on
employees’ satisfaction. Computers in Human Behavior, 53, 475-485.
Sood, A. K., & Enbody, R. J. (2013). Targeted cyberattacks: a superset of advanced persistent
threats. IEEE security & privacy, 11(1), 54-61.
Sun, X. (2012). A systematic approach for migrating enterprise networks(Doctoral dissertation,
Purdue University).
Uddin, M. J., Luva, R. H., & Hossain, S. M. M. (2012). Impact of organizational culture on employee
performance and productivity: a case study of telecommunication sector in
Bangladesh. International Journal of Business and Management, 8(2), 63.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





