MBA Cloud Computing Research: SaaS Service & End-User Requirements
VerifiedAdded on 2021/04/19
|37
|7600
|24
Report
AI Summary
This research report, prepared for an MBA Cloud Computing course, investigates Software as a Service (SaaS). It explores the market readiness of SaaS, its relationship with cloud computing and big data, and the impact of mobile platforms. The study examines the research methodology, including the research philosophy, approach, design, data collection and analysis methods, and ethical considerations. The aim is to determine if SaaS provides genuine services to clients and meets end-user requirements. The report reviews existing literature on SaaS, cloud computing, and related topics. The study aims to explore the benefits of SaaS, recognize market demand, identify problems with customized cloud solutions, and assess whether SaaS meets end-user needs. The report anticipates findings and includes a detailed literature review, research methodology, and anticipated findings sections. The report also discusses the research structure and significance.
Running head: SOFTWARE AS A SERVICE
INDI
VIDUAL ASSIGNMENT
Students Names: Laxmanrao Nimmala,
Student Id 10352103
Course Tittle MBA-Cloud computing
Lecturer Name Gary Bernie
Module Code B9RS106
Module Tittle Research Methods-2
Number of Words 6648
Date of Submission 3rd January 2018
INDI
VIDUAL ASSIGNMENT
Students Names: Laxmanrao Nimmala,
Student Id 10352103
Course Tittle MBA-Cloud computing
Lecturer Name Gary Bernie
Module Code B9RS106
Module Tittle Research Methods-2
Number of Words 6648
Date of Submission 3rd January 2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOFTWARE AS A SERVICE
Table of Contents
1. Introduction..................................................................................................................................3
1.1 Background of the research...................................................................................................3
1.2 Research rationale..................................................................................................................4
1.3 Research aim..........................................................................................................................5
1.4 Research objectives...............................................................................................................5
1.5 Research questions.................................................................................................................6
1.6 Research significance............................................................................................................6
1.7 Research structure..................................................................................................................7
2. Literature Review........................................................................................................................8
2.1 Market Readiness of Saas......................................................................................................8
2.2 Cloud Computing and SaaS.................................................................................................10
2.3 Big Data and Cloud Computing..........................................................................................11
2.4 Mobile Platform usage.........................................................................................................13
2.5 Cloud Storage Methods.......................................................................................................14
3. Research Methodology..............................................................................................................16
3.1 Research philosophy............................................................................................................16
3.2 Research approach...............................................................................................................16
3.3 Research Design..................................................................................................................17
Table of Contents
1. Introduction..................................................................................................................................3
1.1 Background of the research...................................................................................................3
1.2 Research rationale..................................................................................................................4
1.3 Research aim..........................................................................................................................5
1.4 Research objectives...............................................................................................................5
1.5 Research questions.................................................................................................................6
1.6 Research significance............................................................................................................6
1.7 Research structure..................................................................................................................7
2. Literature Review........................................................................................................................8
2.1 Market Readiness of Saas......................................................................................................8
2.2 Cloud Computing and SaaS.................................................................................................10
2.3 Big Data and Cloud Computing..........................................................................................11
2.4 Mobile Platform usage.........................................................................................................13
2.5 Cloud Storage Methods.......................................................................................................14
3. Research Methodology..............................................................................................................16
3.1 Research philosophy............................................................................................................16
3.2 Research approach...............................................................................................................16
3.3 Research Design..................................................................................................................17

2SOFTWARE AS A SERVICE
3.4 Data collection method........................................................................................................17
3.5 Sampling method.................................................................................................................18
3.6 Data analysis techniques......................................................................................................19
3.7 Pilot Testing.........................................................................................................................19
3.8 Ethical considerations..........................................................................................................20
3.9 Research timeline.................................................................................................................20
3.10 Limitations.........................................................................................................................21
4. Anticipated findings...................................................................................................................22
Reference List................................................................................................................................23
3.4 Data collection method........................................................................................................17
3.5 Sampling method.................................................................................................................18
3.6 Data analysis techniques......................................................................................................19
3.7 Pilot Testing.........................................................................................................................19
3.8 Ethical considerations..........................................................................................................20
3.9 Research timeline.................................................................................................................20
3.10 Limitations.........................................................................................................................21
4. Anticipated findings...................................................................................................................22
Reference List................................................................................................................................23
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SOFTWARE AS A SERVICE
1. Introduction
Software as a service (SaaS) is sometimes referred to as on-demand-services to the
clients. SaaS is a software delivery and licensing model through which software can be accessed
as licensed via subscription (Baltes 2015). This study focuses mainly whether SaaS provides
genuine services to the clients and it also strives to find out whether SaaS is meeting the end
users’ requirements. In this proposal, aim, objectives and research questions will be given with
rationale. This research will try to find the market demand for SaaS software products among the
clients. In this study, scholarly articles based on SaaS and its market importance will be
reviewed. Data collection and data analysis process for the research will be explained.
1.1 Background of the research
The concept of SaaS came into technology with ASP (Application Service Providers)
model and in the year 2012, ASP started focusing on hosting and managing third-party
independent software. From that time, SaaS vendors began to develop their own software and
ASP started offering client-server application. As mentioned by Chu et al. (2014), acronym SaaS
allegedly first appeared in an article named ‘Strategic Backgrounder'. SaaS, cloud-based model
has no direct distribution and it does not have any physical need as it is not physically
distributed. This software is deployed instantaneously. SaaS is accessed by users through thin
client via a web browser. Many of the business application is now using SaaS application
software for office software, payroll processing, messaging software, CAD software,
virtualisation gamification and accounting. Of late, SaaS is incorporated into the strategy of
many leading enterprise software companies (Han et al. 2015). Like other traditional software,
SaaS does not have a perpetual license, however; SaaS gives price application for a subscription
1. Introduction
Software as a service (SaaS) is sometimes referred to as on-demand-services to the
clients. SaaS is a software delivery and licensing model through which software can be accessed
as licensed via subscription (Baltes 2015). This study focuses mainly whether SaaS provides
genuine services to the clients and it also strives to find out whether SaaS is meeting the end
users’ requirements. In this proposal, aim, objectives and research questions will be given with
rationale. This research will try to find the market demand for SaaS software products among the
clients. In this study, scholarly articles based on SaaS and its market importance will be
reviewed. Data collection and data analysis process for the research will be explained.
1.1 Background of the research
The concept of SaaS came into technology with ASP (Application Service Providers)
model and in the year 2012, ASP started focusing on hosting and managing third-party
independent software. From that time, SaaS vendors began to develop their own software and
ASP started offering client-server application. As mentioned by Chu et al. (2014), acronym SaaS
allegedly first appeared in an article named ‘Strategic Backgrounder'. SaaS, cloud-based model
has no direct distribution and it does not have any physical need as it is not physically
distributed. This software is deployed instantaneously. SaaS is accessed by users through thin
client via a web browser. Many of the business application is now using SaaS application
software for office software, payroll processing, messaging software, CAD software,
virtualisation gamification and accounting. Of late, SaaS is incorporated into the strategy of
many leading enterprise software companies (Han et al. 2015). Like other traditional software,
SaaS does not have a perpetual license, however; SaaS gives price application for a subscription
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SOFTWARE AS A SERVICE
fee. It can have a monthly fee or annual fee and SaaS application less costly than other enterprise
software. In recent time, the demand for SaaS is increasing among the organisations and its price
is based on usage parameter of the clients.
SaaS software mainly markets the products and services with freemium model and
marketers provide free services with limited functionality. Fees are charged after a period
enhancing the functionality for a larger scope. SaaS marketing is a B2B sale and it is
synonymous with long scale cycles. Software development is ever-evolving arena which needs
constant changes, setbacks and advances. USP of SaaS is information that is provided to the
clients and SaaS developers need to think in a way those clients are long-term. As opined by
Obal (2015), SaaS has great demand in market and buying process of SaaS software is
complicated and cost of implementation is higher also. Vendors of SaaS must go for product
transparency and there are two types of SaaS, full-service SaaS and Self-serve SaaS. Clients of
SaaS software can have many benefits through using SaaS application like high adoption as most
of the staffs are used to with internet and they are familiar with the concept. SaaS provides lower
initial cost and management does not need much IT infrastructure to install this. As suggested by
Chae and Park (2014), SaaS provides a painless upgrade to the clients and it has seamless
integration to meet specific needs.
1.2 Research rationale
SaaS software emphasises on service and as a product software must be flawless and
powerful. According to Safari and Hasanzadeh (2015), in SaaS software, service needs to be a
paragon of virtues and SaaS marketing plan depends on fully-integrated architecture in which all
aspects of business must be related to the support, product, marketing and revenue model. The
developer of SaaS keeps the marketing plan simple and the actual goal is to have a SaaS that can
fee. It can have a monthly fee or annual fee and SaaS application less costly than other enterprise
software. In recent time, the demand for SaaS is increasing among the organisations and its price
is based on usage parameter of the clients.
SaaS software mainly markets the products and services with freemium model and
marketers provide free services with limited functionality. Fees are charged after a period
enhancing the functionality for a larger scope. SaaS marketing is a B2B sale and it is
synonymous with long scale cycles. Software development is ever-evolving arena which needs
constant changes, setbacks and advances. USP of SaaS is information that is provided to the
clients and SaaS developers need to think in a way those clients are long-term. As opined by
Obal (2015), SaaS has great demand in market and buying process of SaaS software is
complicated and cost of implementation is higher also. Vendors of SaaS must go for product
transparency and there are two types of SaaS, full-service SaaS and Self-serve SaaS. Clients of
SaaS software can have many benefits through using SaaS application like high adoption as most
of the staffs are used to with internet and they are familiar with the concept. SaaS provides lower
initial cost and management does not need much IT infrastructure to install this. As suggested by
Chae and Park (2014), SaaS provides a painless upgrade to the clients and it has seamless
integration to meet specific needs.
1.2 Research rationale
SaaS software emphasises on service and as a product software must be flawless and
powerful. According to Safari and Hasanzadeh (2015), in SaaS software, service needs to be a
paragon of virtues and SaaS marketing plan depends on fully-integrated architecture in which all
aspects of business must be related to the support, product, marketing and revenue model. The
developer of SaaS keeps the marketing plan simple and the actual goal is to have a SaaS that can

5SOFTWARE AS A SERVICE
sell itself. SaaS developer can create more clients based on good products and killer support.
There are two types of SaaS, vertical SaaS and horizontal SaaS.
Among the clients, interest in SaaS has been grown and concern about SaaS security has
also been grown. In recent time, the client base of SaaS has been increased 28.6% in the first half
of 2017 and the total revenue touched $64 billion (Ironpaper.com 2017). Now, in public cloud,
SaaS technology gathers 68% market and last year, it increased almost 22%. On the contrary, the
issue of cost ownership is one such roadblock among potential SaaS clients. However, in recent
time, cloud networks are becoming more famous and it can be used as a strategic mission for
critical business operation. Cloud computing system is rooted in the traditional network system
and in large part of cloud computing, it allows virtualisation technology to permit the single
server to hold many machines with data from multiple customers. SaaS technology faces the
issue of identity management in the cloud and it is immature as it is related to the third-party
technology (Chamelian 2016). For instance, Google itself has Secure Data Connector which
connects customers’ data with Google’s business application. In some of the vendors, cloud
standards are weak as SAS 70 is auditing standard designed that shows service providers may
have sufficient control over data. SaaS vendors are secretive about the security process in SaaS
technology.
1.3 Research aim
The aim of the research is to explore whether the SaaS is providing a genuine service to
their clients and to know whether it is meeting end-user requirements.
1.4 Research objectives
To explore the benefits of genuine SaaS software product
sell itself. SaaS developer can create more clients based on good products and killer support.
There are two types of SaaS, vertical SaaS and horizontal SaaS.
Among the clients, interest in SaaS has been grown and concern about SaaS security has
also been grown. In recent time, the client base of SaaS has been increased 28.6% in the first half
of 2017 and the total revenue touched $64 billion (Ironpaper.com 2017). Now, in public cloud,
SaaS technology gathers 68% market and last year, it increased almost 22%. On the contrary, the
issue of cost ownership is one such roadblock among potential SaaS clients. However, in recent
time, cloud networks are becoming more famous and it can be used as a strategic mission for
critical business operation. Cloud computing system is rooted in the traditional network system
and in large part of cloud computing, it allows virtualisation technology to permit the single
server to hold many machines with data from multiple customers. SaaS technology faces the
issue of identity management in the cloud and it is immature as it is related to the third-party
technology (Chamelian 2016). For instance, Google itself has Secure Data Connector which
connects customers’ data with Google’s business application. In some of the vendors, cloud
standards are weak as SAS 70 is auditing standard designed that shows service providers may
have sufficient control over data. SaaS vendors are secretive about the security process in SaaS
technology.
1.3 Research aim
The aim of the research is to explore whether the SaaS is providing a genuine service to
their clients and to know whether it is meeting end-user requirements.
1.4 Research objectives
To explore the benefits of genuine SaaS software product
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SOFTWARE AS A SERVICE
To recognise the demand in present market for SaaS products
To point out problems of SaaS products that indulge the clients looking for customised
cloud solutions
To find out whether SaaS is meeting end users’ requirements
1.5 Research questions
Primary question
Does SaaS provide a genuine service to the clients meeting all end users’ requirements?
Secondary questions
Is SaaS creating genuine software products that are beneficial for individuals?
Does in the market present any demand for SaaS products?
Does the prevalence of SaaS products is causing any problems to their clients looking for
customised cloud solutions?
1.6 Research significance
This research topic will highlight the application of SaaS in the business environment and
the advantages of SaaS application for end users. Vendors of SaaS technology install the
application and then configure it for the clients. This research will be helpful for the future
readers who would get an idea about market benefits of SaaS technology. This study would aid
the SaaS clients as it this research will give thorough ideas about benefits of SaaS for
individuals. This research will be helpful for the marketers who are trying to use SaaS
technologies in their work to reduce the time of marketing. This study is important as it also
highlights the problems of clients regarding SaaS technologies.
To recognise the demand in present market for SaaS products
To point out problems of SaaS products that indulge the clients looking for customised
cloud solutions
To find out whether SaaS is meeting end users’ requirements
1.5 Research questions
Primary question
Does SaaS provide a genuine service to the clients meeting all end users’ requirements?
Secondary questions
Is SaaS creating genuine software products that are beneficial for individuals?
Does in the market present any demand for SaaS products?
Does the prevalence of SaaS products is causing any problems to their clients looking for
customised cloud solutions?
1.6 Research significance
This research topic will highlight the application of SaaS in the business environment and
the advantages of SaaS application for end users. Vendors of SaaS technology install the
application and then configure it for the clients. This research will be helpful for the future
readers who would get an idea about market benefits of SaaS technology. This study would aid
the SaaS clients as it this research will give thorough ideas about benefits of SaaS for
individuals. This research will be helpful for the marketers who are trying to use SaaS
technologies in their work to reduce the time of marketing. This study is important as it also
highlights the problems of clients regarding SaaS technologies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SOFTWARE AS A SERVICE
1.7 Research structure
Figure 1: Proposed structure of research
(Source: Self-developed)
Chapter One: Introduction
Chapter two: Literature Review
Chapter three: Research Methodology
Chapter four: Data findings and analysis
Chapter five: Conclusions and recommendations
1.7 Research structure
Figure 1: Proposed structure of research
(Source: Self-developed)
Chapter One: Introduction
Chapter two: Literature Review
Chapter three: Research Methodology
Chapter four: Data findings and analysis
Chapter five: Conclusions and recommendations

8SOFTWARE AS A SERVICE
2. Literature Review
There are many texts to be taken into consideration while understanding the issue of
Software as a Service in the contemporary market environment. The Software as a Service and
the and Cloud Computing is showing an exponential growth in the market and the rising use of
these services has given rise to a constant need of security among these platforms. There are
many studies considering the various issues that have risen due to the rise of cloud computing in
the market. The market scenario has changed due to the diverse needs of the mobile and digital
cloud platform users. The social situation of the market of cloud computing is studied in many
models. There are many studies, which are based on the changing scenarios of the market of
SaaS and the Security issues in Cloud Computing.
2.1 Market Readiness of SaaS
In the recent years, the Software as a Service has been pointed out as one of the major
growing industries in the modern market. According to Yang et al., 2015, despite the meteoritic
rise, that the number has seen through the decade there seems an issue of overall acceptance of
SaaS in the market. The use of SaaS lies in many operations such as outsourcing of large data
and various software services like email client and anti-virus software. There is still a hesitation
in the market regarding the acceptance of SaaS as a necessary raw material for the success of an
organization. The research considers many factors that account for the success of a service in a
business environment. It also points out the different services that can be used in the
organizations for a better and cost-effective data storage and software service options. Yang et
al., 2015, consider the different factors that should be considered to judge the maker readiness
and the conducive environment of the success of SaaS. Technological readinesses of the
2. Literature Review
There are many texts to be taken into consideration while understanding the issue of
Software as a Service in the contemporary market environment. The Software as a Service and
the and Cloud Computing is showing an exponential growth in the market and the rising use of
these services has given rise to a constant need of security among these platforms. There are
many studies considering the various issues that have risen due to the rise of cloud computing in
the market. The market scenario has changed due to the diverse needs of the mobile and digital
cloud platform users. The social situation of the market of cloud computing is studied in many
models. There are many studies, which are based on the changing scenarios of the market of
SaaS and the Security issues in Cloud Computing.
2.1 Market Readiness of SaaS
In the recent years, the Software as a Service has been pointed out as one of the major
growing industries in the modern market. According to Yang et al., 2015, despite the meteoritic
rise, that the number has seen through the decade there seems an issue of overall acceptance of
SaaS in the market. The use of SaaS lies in many operations such as outsourcing of large data
and various software services like email client and anti-virus software. There is still a hesitation
in the market regarding the acceptance of SaaS as a necessary raw material for the success of an
organization. The research considers many factors that account for the success of a service in a
business environment. It also points out the different services that can be used in the
organizations for a better and cost-effective data storage and software service options. Yang et
al., 2015, consider the different factors that should be considered to judge the maker readiness
and the conducive environment of the success of SaaS. Technological readinesses of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9SOFTWARE AS A SERVICE
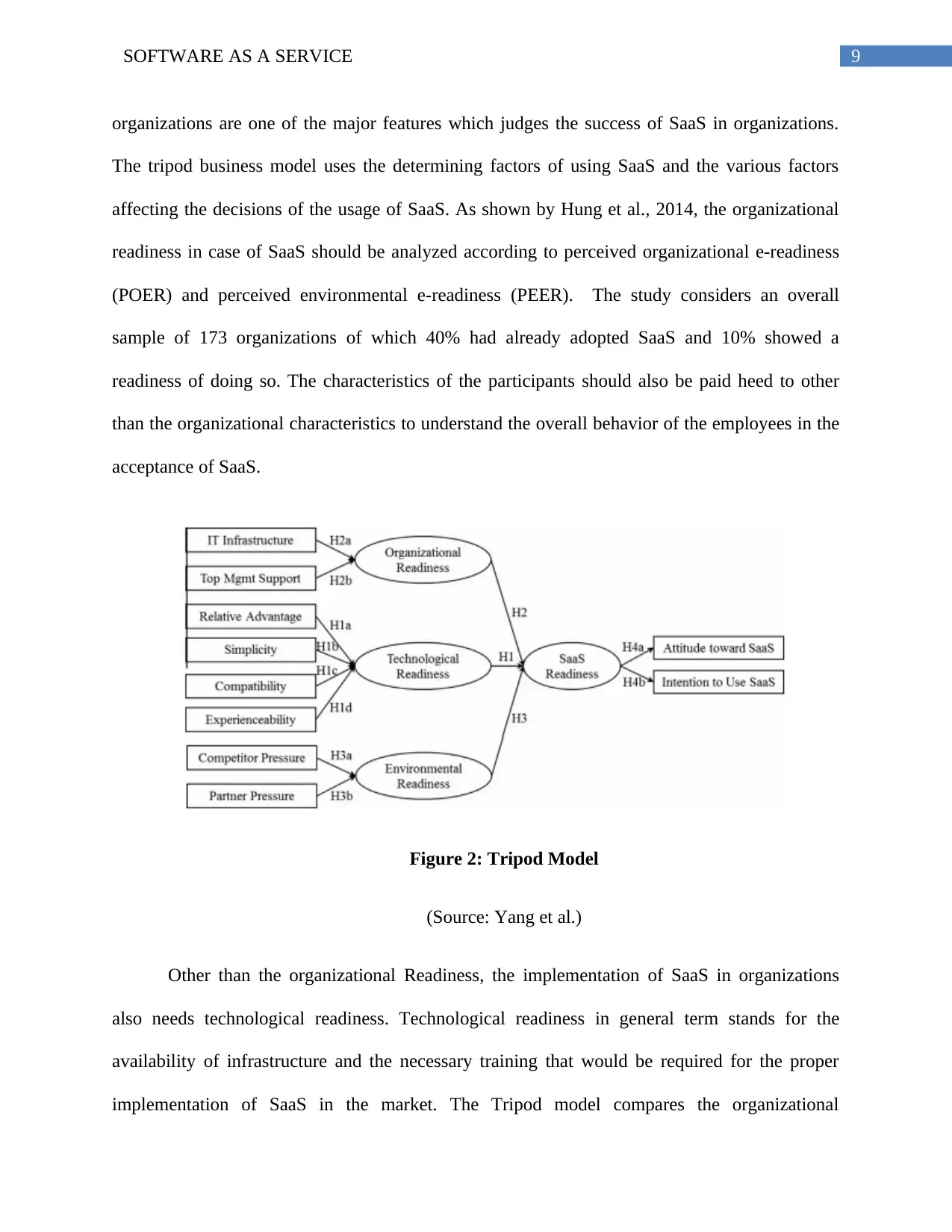
organizations are one of the major features which judges the success of SaaS in organizations.
The tripod business model uses the determining factors of using SaaS and the various factors
affecting the decisions of the usage of SaaS. As shown by Hung et al., 2014, the organizational
readiness in case of SaaS should be analyzed according to perceived organizational e-readiness
(POER) and perceived environmental e-readiness (PEER). The study considers an overall
sample of 173 organizations of which 40% had already adopted SaaS and 10% showed a
readiness of doing so. The characteristics of the participants should also be paid heed to other
than the organizational characteristics to understand the overall behavior of the employees in the
acceptance of SaaS.
Figure 2: Tripod Model
(Source: Yang et al.)
Other than the organizational Readiness, the implementation of SaaS in organizations
also needs technological readiness. Technological readiness in general term stands for the
availability of infrastructure and the necessary training that would be required for the proper
implementation of SaaS in the market. The Tripod model compares the organizational
organizations are one of the major features which judges the success of SaaS in organizations.
The tripod business model uses the determining factors of using SaaS and the various factors
affecting the decisions of the usage of SaaS. As shown by Hung et al., 2014, the organizational
readiness in case of SaaS should be analyzed according to perceived organizational e-readiness
(POER) and perceived environmental e-readiness (PEER). The study considers an overall
sample of 173 organizations of which 40% had already adopted SaaS and 10% showed a
readiness of doing so. The characteristics of the participants should also be paid heed to other
than the organizational characteristics to understand the overall behavior of the employees in the
acceptance of SaaS.
Figure 2: Tripod Model
(Source: Yang et al.)
Other than the organizational Readiness, the implementation of SaaS in organizations
also needs technological readiness. Technological readiness in general term stands for the
availability of infrastructure and the necessary training that would be required for the proper
implementation of SaaS in the market. The Tripod model compares the organizational
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SOFTWARE AS A SERVICE
technological and environmental readiness in a situation to test the readiness among participants
for effective implementation of SaaS. The research anyhow is limited to China and may not
provide a proper information of the importance of the global perspective of the implementation
of SaaS in various business models. The research also fails to take in to account a variety of
sources, like many highly positioned employees in the organizations, which may have led to
discrepancy in the final result. As pointed out by Almorsy, Grundy and Müller, 2016, the SaaS
has many safety issues and is vulnerable to cyber security threats, which is one of the main issues
stopping organizations from accepting it. The partner and the competitor pressure are also one of
the important factors, which stands as an hindrance in the acceptance of SaaS.
2.2 Cloud Computing and SaaS
According to Soofi et al., 2014, the rising popularity of the SaaS is due to the increasing
market requirement and the constantly increasing need of the internet based data storage and data
sharing in the present society. The exchange of the data and the storage of the information has
also shown a great increase in the number of hacking of accounts and the theft of information.
The constant change in the marketing environment helps in the increase of the demands of the
consumers but the security threats in the cloud computing service remains intact. There are a
number of ways to ensure the security of the data too, like the multiple layer security software,
which would increase the level of security in the online environment. The changes in the security
systems and their programming will help in the proper implementation of SaaS in the global
market, as it would increase the trust of the consumers in the products. The change in market
environment, which has seen a change in basic assumptions in the growing virtual digital
environment is due to the rising requirement of cloud computing. The changes due to the rising
demand of the cloud computing as an alternative data storage options have brought it under
technological and environmental readiness in a situation to test the readiness among participants
for effective implementation of SaaS. The research anyhow is limited to China and may not
provide a proper information of the importance of the global perspective of the implementation
of SaaS in various business models. The research also fails to take in to account a variety of
sources, like many highly positioned employees in the organizations, which may have led to
discrepancy in the final result. As pointed out by Almorsy, Grundy and Müller, 2016, the SaaS
has many safety issues and is vulnerable to cyber security threats, which is one of the main issues
stopping organizations from accepting it. The partner and the competitor pressure are also one of
the important factors, which stands as an hindrance in the acceptance of SaaS.
2.2 Cloud Computing and SaaS
According to Soofi et al., 2014, the rising popularity of the SaaS is due to the increasing
market requirement and the constantly increasing need of the internet based data storage and data
sharing in the present society. The exchange of the data and the storage of the information has
also shown a great increase in the number of hacking of accounts and the theft of information.
The constant change in the marketing environment helps in the increase of the demands of the
consumers but the security threats in the cloud computing service remains intact. There are a
number of ways to ensure the security of the data too, like the multiple layer security software,
which would increase the level of security in the online environment. The changes in the security
systems and their programming will help in the proper implementation of SaaS in the global
market, as it would increase the trust of the consumers in the products. The change in market
environment, which has seen a change in basic assumptions in the growing virtual digital
environment is due to the rising requirement of cloud computing. The changes due to the rising
demand of the cloud computing as an alternative data storage options have brought it under

11SOFTWARE AS A SERVICE
limelight and made it threat prone (Mohamed et al. 2012). The complexity of the cloud
computing algorithms and the lack of it among the general population has increased its threat in
the market place. The market requirements of the cloud computing have also led to an increase in
the constant supply newer and better services but the threat to the security of these serfvices
remains. Anomaly Detection System can also be used to increase the security in the cloud
computing systems, giving rise to incresred security in the cloud computing platforms. The cloud
computing services like Apple i-cloud and the Google Dropbox use two-step authentication to
ensure the security of the system. The use of SSL and secure https helps in ensuring the security
of the data stored in the cloud computing services (Sari 2015). The security threat is one of the
major concerns of the growing software industry and the methods of mitigation are being
constantly worked on.
2.3 Big Data and Cloud Computing
Hashem et al., 2015, have analyzed the importance of the rise of Big Data as the
important determinant of the rise of the cloud computing services. The rises of the constant
computing and the data usage have increased the issues of the big data. The big data in general
terms stand for the total amount of the data that in the digital terms that is too big to be handled
over the simple systems. The big data and the cloud computing systems are correlated to each
other as the big data arises due to the large amount of the virtual data and sizable data stored on
the cloud platforms. The data stored on the various platforms need to be analyzed and understood
for the information to be understood in the social and the digital environment. The overall
analysis of the data in comparison to the data traffic of the overall internet environment shows
most of the features that are implemented in cloud computing. The lack on the security of the
limelight and made it threat prone (Mohamed et al. 2012). The complexity of the cloud
computing algorithms and the lack of it among the general population has increased its threat in
the market place. The market requirements of the cloud computing have also led to an increase in
the constant supply newer and better services but the threat to the security of these serfvices
remains. Anomaly Detection System can also be used to increase the security in the cloud
computing systems, giving rise to incresred security in the cloud computing platforms. The cloud
computing services like Apple i-cloud and the Google Dropbox use two-step authentication to
ensure the security of the system. The use of SSL and secure https helps in ensuring the security
of the data stored in the cloud computing services (Sari 2015). The security threat is one of the
major concerns of the growing software industry and the methods of mitigation are being
constantly worked on.
2.3 Big Data and Cloud Computing
Hashem et al., 2015, have analyzed the importance of the rise of Big Data as the
important determinant of the rise of the cloud computing services. The rises of the constant
computing and the data usage have increased the issues of the big data. The big data in general
terms stand for the total amount of the data that in the digital terms that is too big to be handled
over the simple systems. The big data and the cloud computing systems are correlated to each
other as the big data arises due to the large amount of the virtual data and sizable data stored on
the cloud platforms. The data stored on the various platforms need to be analyzed and understood
for the information to be understood in the social and the digital environment. The overall
analysis of the data in comparison to the data traffic of the overall internet environment shows
most of the features that are implemented in cloud computing. The lack on the security of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




