SBM4304 IS Security & Risk Management: Applied Project on Atlassian
VerifiedAdded on 2023/06/04
|17
|4012
|187
Report
AI Summary
This report provides a comprehensive analysis of IT security and risk management within the context of Atlassian, an information technology organization. It delves into the working mechanisms of ransomware and suggests three tools for mitigation, explores threats against network routers and switches, and discusses strategies to ensure the reliability and availability of web services. The report also addresses methods for maintaining the confidentiality and integrity of staff email, prioritizes threats and security issues related to webmail and web servers, and proposes approaches to improve email server availability. Furthermore, it examines the impact of human factors and organizational issues on information security and risk management, recommends risk management strategies, and emphasizes the importance of log analysis. The report concludes with an overview of five network security devices, providing a holistic view of IT security practices within the organization.

Running head: IT SECURITY AND RISK MANAGEMENT
IT SECURITY AND RISK MANAGEMENT
Name of the Student
Name of the University
Author Note
IT SECURITY AND RISK MANAGEMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2IT SECURITY AND RISK MANAGEMENT
Table of Contents
1. Introduction..................................................................................................................................4
2. Ransomware malwares threads against organization Information systems................................4
a. working mechanism of ransomware........................................................................................4
b. Three tools to tackle the ransomware attack............................................................................5
3. Threats against network routers and switches.............................................................................5
How routers and switches are vulnerable to destruction and abuse............................................5
4. Discussion on how the organization can ensure the reliability and availability of the web........7
service..............................................................................................................................................7
5. The ways to ensure confidentiality and integrity of the staff email............................................7
6. Discussion and prioritize the threats and the possible types of malware and security................8
issues related to web mail and webserver........................................................................................8
7. Proposal of two approaches to improve the availability of email servers.................................10
8. Impact of human factors and organizational issues on IS-related security and risk..................11
management...................................................................................................................................11
Risk management recommendations.........................................................................................11
9. Use of logs.................................................................................................................................11
10. Details analysis of activity log.................................................................................................12
11. Five network security devices.................................................................................................12
Table of Contents
1. Introduction..................................................................................................................................4
2. Ransomware malwares threads against organization Information systems................................4
a. working mechanism of ransomware........................................................................................4
b. Three tools to tackle the ransomware attack............................................................................5
3. Threats against network routers and switches.............................................................................5
How routers and switches are vulnerable to destruction and abuse............................................5
4. Discussion on how the organization can ensure the reliability and availability of the web........7
service..............................................................................................................................................7
5. The ways to ensure confidentiality and integrity of the staff email............................................7
6. Discussion and prioritize the threats and the possible types of malware and security................8
issues related to web mail and webserver........................................................................................8
7. Proposal of two approaches to improve the availability of email servers.................................10
8. Impact of human factors and organizational issues on IS-related security and risk..................11
management...................................................................................................................................11
Risk management recommendations.........................................................................................11
9. Use of logs.................................................................................................................................11
10. Details analysis of activity log.................................................................................................12
11. Five network security devices.................................................................................................12

3IT SECURITY AND RISK MANAGEMENT
12. Conclusion...............................................................................................................................13
13. References................................................................................................................................14
12. Conclusion...............................................................................................................................13
13. References................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4IT SECURITY AND RISK MANAGEMENT
1. Introduction
The main objective to the report is to take into consideration different aspect which are
related to the security of the different devices which are connected to the internet. There can be
different types of intruder attack which can be included into the working of the organization. In
most of these situation it can be stated that if there are any type of intruder activity it can directly
decrease the quality which is related to the data which is stored in the server (Bichou, 2015). The
aspect of the reliability of the data can be directly be linked with the aspect of the integrity of the
data.
The organization which is selected in the sector is the Atlassian which is an information
technology organization which focus on the aspect of providing better security implication to the
different standard which is related to the concept.
2. Ransomware malwares threads against organization Information systems
a. Working mechanism of ransomware
The concept of ransomware can be considered as a malicious software that directly takes
control of the overall system and directly threatens the system. It can be stated as one of the most
common types of attack which is generated in the system or in the network. Ones there is an
attack relating to ransomware the data of the computer can be at stack. One of the common
working mechanism which is related to the working of the ransomware is the phishing spam. The
attack is mainly generated in the sector of an email which is generated from the attackers which
aim at the controlling of the system. Ones the email is accessed and then downloaded the system
would be consisting of the ransomware or the virus. The concept can also trick the user to take
control of the system and also generate an administrative access of the system.
1. Introduction
The main objective to the report is to take into consideration different aspect which are
related to the security of the different devices which are connected to the internet. There can be
different types of intruder attack which can be included into the working of the organization. In
most of these situation it can be stated that if there are any type of intruder activity it can directly
decrease the quality which is related to the data which is stored in the server (Bichou, 2015). The
aspect of the reliability of the data can be directly be linked with the aspect of the integrity of the
data.
The organization which is selected in the sector is the Atlassian which is an information
technology organization which focus on the aspect of providing better security implication to the
different standard which is related to the concept.
2. Ransomware malwares threads against organization Information systems
a. Working mechanism of ransomware
The concept of ransomware can be considered as a malicious software that directly takes
control of the overall system and directly threatens the system. It can be stated as one of the most
common types of attack which is generated in the system or in the network. Ones there is an
attack relating to ransomware the data of the computer can be at stack. One of the common
working mechanism which is related to the working of the ransomware is the phishing spam. The
attack is mainly generated in the sector of an email which is generated from the attackers which
aim at the controlling of the system. Ones the email is accessed and then downloaded the system
would be consisting of the ransomware or the virus. The concept can also trick the user to take
control of the system and also generate an administrative access of the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5IT SECURITY AND RISK MANAGEMENT
b. Three tools to tackle the ransomware attack
The organization which is taken into consideration which is the Atlassian uses different
types of tool relating to the attack which is generated from the ransomware attack. Few of the
tools which are used are discussed below:
Trend micro’s tool: This tool is directly designed for the aspect of detecting and getting
rid of the ‘lock screen’ ransomware. These type of ransomware directly blocks the user
from accessing the system or the PC. The main action which can be done in the sector is
the installation of the software by means of bypassing the malware by directly booting
the PC into the safe mode.
Avast anti ransomware tools: It can be stated here that there are different types of
activity which are majorly done in the sector of the working of the ransomware. In most
of the sector there should be an implementation of a decryption which are specially made
for certain type of ransomware.
AVG ransomware decryption tools: The concept of the AVG directly provides a
decryption tool which is related to the variety of the ransomware. On the other hand,
there is also an offering which is related to the lots of resources and the guide to engage
through the guide of typical attack of ransomware.
3. Threats against network routers and switches
How routers and switches are vulnerable to destruction and abuse.
Some of the threats which are related to the network router in the Atlassian organization are
stated below:
b. Three tools to tackle the ransomware attack
The organization which is taken into consideration which is the Atlassian uses different
types of tool relating to the attack which is generated from the ransomware attack. Few of the
tools which are used are discussed below:
Trend micro’s tool: This tool is directly designed for the aspect of detecting and getting
rid of the ‘lock screen’ ransomware. These type of ransomware directly blocks the user
from accessing the system or the PC. The main action which can be done in the sector is
the installation of the software by means of bypassing the malware by directly booting
the PC into the safe mode.
Avast anti ransomware tools: It can be stated here that there are different types of
activity which are majorly done in the sector of the working of the ransomware. In most
of the sector there should be an implementation of a decryption which are specially made
for certain type of ransomware.
AVG ransomware decryption tools: The concept of the AVG directly provides a
decryption tool which is related to the variety of the ransomware. On the other hand,
there is also an offering which is related to the lots of resources and the guide to engage
through the guide of typical attack of ransomware.
3. Threats against network routers and switches
How routers and switches are vulnerable to destruction and abuse.
Some of the threats which are related to the network router in the Atlassian organization are
stated below:

6IT SECURITY AND RISK MANAGEMENT
Masquerade attack: The attack which is seen in this sector is directly related to the
aspect of attackers manipulating the IP packets to falsify the IP addresses. The attack
which is related to the masquerades can be directly be used for gaining the unauthorized
access or to directly bogus the data into the network.
Session hijacking: The concept which is related to the aspect of the session hijacking can
be directly be related to the aspect when an attacker insert falsified IP packets after the
establishment of sessions via the concept if the sequence number of prediction, spoofing
and the alteration or any other types of methods (Kott & Arnold, 2015).
Rerouting attack: The aspect which is related to the concept of the rerouting attack can
be indicated in the sector of manipulating the updates of the router which would be
directly causing the traffic in the channel relating to the flow of the unauthorized
destination.
Some of the threats which are related to the switches in the Atlassian organization are stated
below:
MAC flooding: In the concept of the MAC flooding it can be stated that there is a flood
in the CAM table with the MAC addresses more than the limitation which is related to
the capacity of the switch. This aspect directly allows the switch to act as a hub which
directly gives the access of the attacker to sniff into the traffic.
DHCP spoofing: A DHCP snooping attacker directly listened for the DHCP request and
directly gives them the answer. This directly gives the IP address as a default gateway for
the client the attacker then directly becomes the “man in the middle”
Masquerade attack: The attack which is seen in this sector is directly related to the
aspect of attackers manipulating the IP packets to falsify the IP addresses. The attack
which is related to the masquerades can be directly be used for gaining the unauthorized
access or to directly bogus the data into the network.
Session hijacking: The concept which is related to the aspect of the session hijacking can
be directly be related to the aspect when an attacker insert falsified IP packets after the
establishment of sessions via the concept if the sequence number of prediction, spoofing
and the alteration or any other types of methods (Kott & Arnold, 2015).
Rerouting attack: The aspect which is related to the concept of the rerouting attack can
be indicated in the sector of manipulating the updates of the router which would be
directly causing the traffic in the channel relating to the flow of the unauthorized
destination.
Some of the threats which are related to the switches in the Atlassian organization are stated
below:
MAC flooding: In the concept of the MAC flooding it can be stated that there is a flood
in the CAM table with the MAC addresses more than the limitation which is related to
the capacity of the switch. This aspect directly allows the switch to act as a hub which
directly gives the access of the attacker to sniff into the traffic.
DHCP spoofing: A DHCP snooping attacker directly listened for the DHCP request and
directly gives them the answer. This directly gives the IP address as a default gateway for
the client the attacker then directly becomes the “man in the middle”
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7IT SECURITY AND RISK MANAGEMENT
VLAN based attack: This is when the attacker would be able to access the VLAN other
than its own sector. This can be done in a number of processes which is mainly the A-
Switch spoofing.
4. Discussion on how the organization can ensure the reliability and availability of the web
service.
Reliability
The aspect of the reliability in the concept can be directly be related to the aspect of the
different data which is stored in the concept. It can be stated here that most of the crucial data of
the organization are saved in the concept of the server. In most of the sector it should be taken
into consideration that the data which is stored are not altered and it can be taken into
consideration that the data which is retrieved is very much reliable
Availability
The data which is stored in the sever should be very much be available to be accessed
when it is required to do so. In most of the time it can be stated that there is problem related to
the access of the data which is majorly seen in the issue which is related to the linkage problem.
The situation can be stated as a very big problem for the organization due to the factor that they
would not be able to access the data when they would be requiring to do so. The data should be
very much being available for access whenever the organization would be needing the access and
the sector of the reliability of the data should also be included into the concept (Aven, 2016).
Direct access control mechanism should be included into the aspect of the working so that there
are no problem relating to the access sector of the data.
VLAN based attack: This is when the attacker would be able to access the VLAN other
than its own sector. This can be done in a number of processes which is mainly the A-
Switch spoofing.
4. Discussion on how the organization can ensure the reliability and availability of the web
service.
Reliability
The aspect of the reliability in the concept can be directly be related to the aspect of the
different data which is stored in the concept. It can be stated here that most of the crucial data of
the organization are saved in the concept of the server. In most of the sector it should be taken
into consideration that the data which is stored are not altered and it can be taken into
consideration that the data which is retrieved is very much reliable
Availability
The data which is stored in the sever should be very much be available to be accessed
when it is required to do so. In most of the time it can be stated that there is problem related to
the access of the data which is majorly seen in the issue which is related to the linkage problem.
The situation can be stated as a very big problem for the organization due to the factor that they
would not be able to access the data when they would be requiring to do so. The data should be
very much being available for access whenever the organization would be needing the access and
the sector of the reliability of the data should also be included into the concept (Aven, 2016).
Direct access control mechanism should be included into the aspect of the working so that there
are no problem relating to the access sector of the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8IT SECURITY AND RISK MANAGEMENT
5. The ways to ensure confidentiality and integrity of the staff email
The main aspect which can be related to the sector of integrity and confidentiality can be
stated as two of the major points which is related to securing of the email of the employee. It can
be stated that there are different types of approaches which can be implemented in the sector
which would be helping in the sector of the integrity and confidentiality of the data which is
stored in the email. One of the technique which can be implemented in the sector is the use of the
digital signature which can be used for the purpose of the authentication of the data. In steps
which are followed in the sector is the aspect of the generation of a secret keys which can be
directly be used when transferring of the message from the one end to another end. It can be
stated that it prevents the data from being altered or manipulated. The concept is applicable in
the sector of the sender authentication and the concept of the noon repudiation.
Another aspect which can be related to the concept is the encryption of the messages. The
concept can be very much beneficial in the sector of the working due to the factor that the
message can be seen by another person who has directly gained access to the mail. The process
which is followed in the sector is the encryption process and the decryption process. The process
which is related to the encryption and decryption can be done in a two level process which is
explained below.
Generation of key
Encryption using the process of RSA algorithm
Encryption using the concept of the random array method.
Decryption using the concept of the random array methods
Decryption using the RSA algorithm.
5. The ways to ensure confidentiality and integrity of the staff email
The main aspect which can be related to the sector of integrity and confidentiality can be
stated as two of the major points which is related to securing of the email of the employee. It can
be stated that there are different types of approaches which can be implemented in the sector
which would be helping in the sector of the integrity and confidentiality of the data which is
stored in the email. One of the technique which can be implemented in the sector is the use of the
digital signature which can be used for the purpose of the authentication of the data. In steps
which are followed in the sector is the aspect of the generation of a secret keys which can be
directly be used when transferring of the message from the one end to another end. It can be
stated that it prevents the data from being altered or manipulated. The concept is applicable in
the sector of the sender authentication and the concept of the noon repudiation.
Another aspect which can be related to the concept is the encryption of the messages. The
concept can be very much beneficial in the sector of the working due to the factor that the
message can be seen by another person who has directly gained access to the mail. The process
which is followed in the sector is the encryption process and the decryption process. The process
which is related to the encryption and decryption can be done in a two level process which is
explained below.
Generation of key
Encryption using the process of RSA algorithm
Encryption using the concept of the random array method.
Decryption using the concept of the random array methods
Decryption using the RSA algorithm.

9IT SECURITY AND RISK MANAGEMENT
6. Discussion and prioritize the threats and the possible types of malware and security
issues related to web mail and webserver
There can be different types of malware which are related to the concept of web mail and
the mail server. The malwares are explained below:
DoS threat: The damage which is related the DoS attack can be stated to be very much be
overstated. The sector can be applicable both in the sector of the send mail as well as the
unsent mails (DeAngelo & Stulz, 2015). The main sector which is related to the concept
of the prevention is that there should be limited possible connection to the server which is
related to the SMTP.
Stability of the server and the performance: In this concept it can be stated that whenever
the term performance and server, the aspect of the load balancing can be taken into
consideration. In most of the cases it can be stated that if the server was attacked and the
working is abounded there should be implementation of another plan which is known as
the reserve server.
Ignoring best practice: one of the most vital sector which can be related to the concept is
that there should not be saving of any crucial data in the network which can directly harm
the overall functionality of the server.
The security aspect which can be related to the concept are stated below:
Unauthorized access of the data: The data which is stored in the serve of the mail can be
accessed by anyone which is termed as unauthorized access. This can be termed as
security issue due to the factor that if the unauthorized access is made it can directly
6. Discussion and prioritize the threats and the possible types of malware and security
issues related to web mail and webserver
There can be different types of malware which are related to the concept of web mail and
the mail server. The malwares are explained below:
DoS threat: The damage which is related the DoS attack can be stated to be very much be
overstated. The sector can be applicable both in the sector of the send mail as well as the
unsent mails (DeAngelo & Stulz, 2015). The main sector which is related to the concept
of the prevention is that there should be limited possible connection to the server which is
related to the SMTP.
Stability of the server and the performance: In this concept it can be stated that whenever
the term performance and server, the aspect of the load balancing can be taken into
consideration. In most of the cases it can be stated that if the server was attacked and the
working is abounded there should be implementation of another plan which is known as
the reserve server.
Ignoring best practice: one of the most vital sector which can be related to the concept is
that there should not be saving of any crucial data in the network which can directly harm
the overall functionality of the server.
The security aspect which can be related to the concept are stated below:
Unauthorized access of the data: The data which is stored in the serve of the mail can be
accessed by anyone which is termed as unauthorized access. This can be termed as
security issue due to the factor that if the unauthorized access is made it can directly
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10IT SECURITY AND RISK MANAGEMENT
impact the overall functionality which is related to the organization and the crucial data
of the organization can go into the hand of the attackers.
Threat to data leakage: One of the most important sector which ca be related to the factor
of security is the data leakage (Safa, Von Solms & Furnell, 2016). Then main motive
which is behind the attackers in the sector of the access to the system would be gain the
personal data which is saved in the system. The main data which is tried to be achieved
rom the concept is the username, password and other personal details. The main
mitigation aspect which can be related to the concept is the SMTP, POP3 and IMAP
protocols should be directly be encrypted with the SSL/TLS.
7. Proposal of two approaches to improve the availability of email servers
Two different approach which are related to the improving of the availability of the email
server. The organization Atlassian can directly include the following strategies which would be
beneficial in the sector.
SPF record: The sender policy framework can be directly implemented in the sector
which would be directly enhancing the sector of the availability of the email server. On the other
hand, it can be also used for the sector of authentication as well. It directly helps the organization
to indulge into different factor of working which would be beneficial in the working of the
organization and in most of the cases it can directly alter the overall working which is seen in the
concept (Eriksson, 2017). The concept can be stated to be very much beneficial in the sector of
the implementation of the mail server.
impact the overall functionality which is related to the organization and the crucial data
of the organization can go into the hand of the attackers.
Threat to data leakage: One of the most important sector which ca be related to the factor
of security is the data leakage (Safa, Von Solms & Furnell, 2016). Then main motive
which is behind the attackers in the sector of the access to the system would be gain the
personal data which is saved in the system. The main data which is tried to be achieved
rom the concept is the username, password and other personal details. The main
mitigation aspect which can be related to the concept is the SMTP, POP3 and IMAP
protocols should be directly be encrypted with the SSL/TLS.
7. Proposal of two approaches to improve the availability of email servers
Two different approach which are related to the improving of the availability of the email
server. The organization Atlassian can directly include the following strategies which would be
beneficial in the sector.
SPF record: The sender policy framework can be directly implemented in the sector
which would be directly enhancing the sector of the availability of the email server. On the other
hand, it can be also used for the sector of authentication as well. It directly helps the organization
to indulge into different factor of working which would be beneficial in the working of the
organization and in most of the cases it can directly alter the overall working which is seen in the
concept (Eriksson, 2017). The concept can be stated to be very much beneficial in the sector of
the implementation of the mail server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
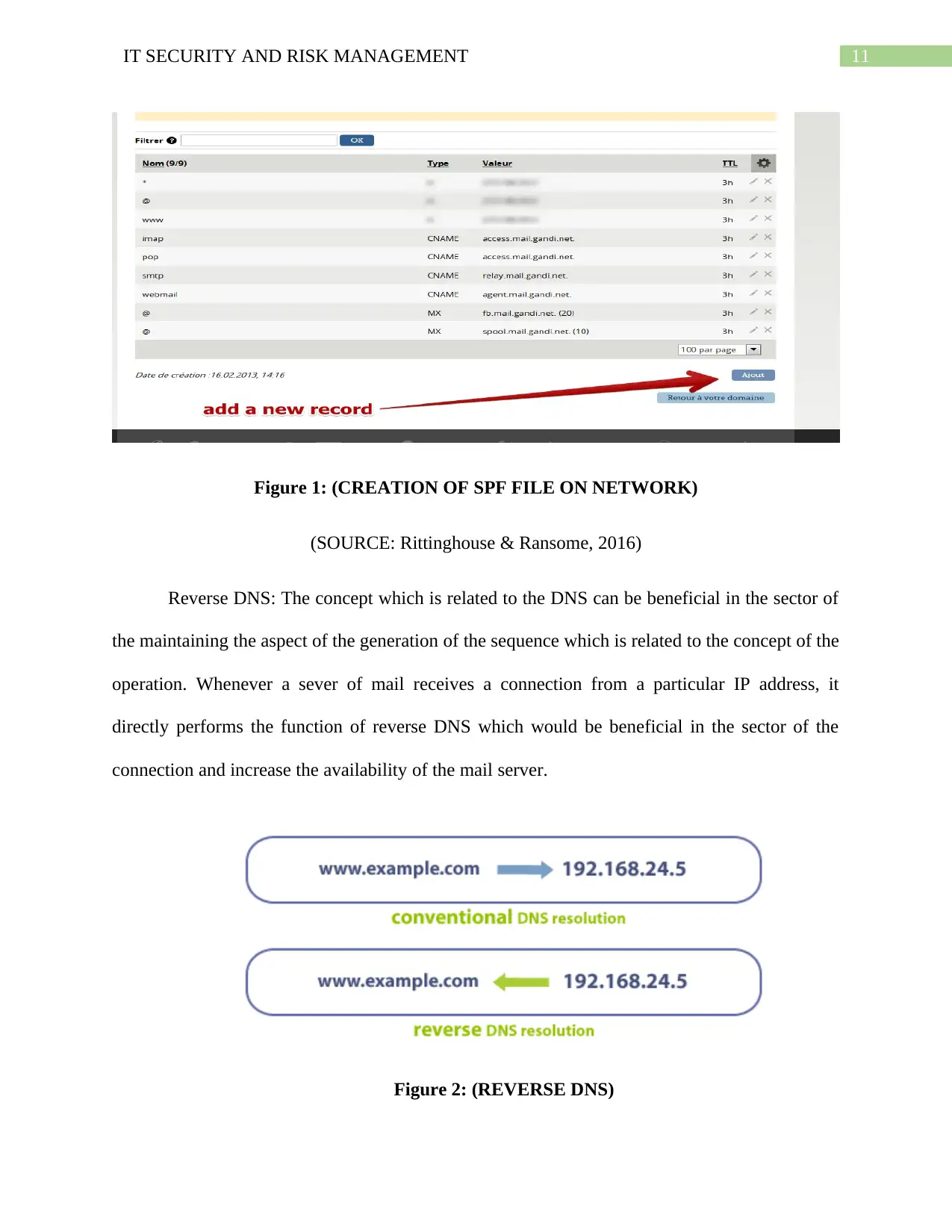
11IT SECURITY AND RISK MANAGEMENT
Figure 1: (CREATION OF SPF FILE ON NETWORK)
(SOURCE: Rittinghouse & Ransome, 2016)
Reverse DNS: The concept which is related to the DNS can be beneficial in the sector of
the maintaining the aspect of the generation of the sequence which is related to the concept of the
operation. Whenever a sever of mail receives a connection from a particular IP address, it
directly performs the function of reverse DNS which would be beneficial in the sector of the
connection and increase the availability of the mail server.
Figure 2: (REVERSE DNS)
Figure 1: (CREATION OF SPF FILE ON NETWORK)
(SOURCE: Rittinghouse & Ransome, 2016)
Reverse DNS: The concept which is related to the DNS can be beneficial in the sector of
the maintaining the aspect of the generation of the sequence which is related to the concept of the
operation. Whenever a sever of mail receives a connection from a particular IP address, it
directly performs the function of reverse DNS which would be beneficial in the sector of the
connection and increase the availability of the mail server.
Figure 2: (REVERSE DNS)

12IT SECURITY AND RISK MANAGEMENT
(SOURCE: Rittinghouse & Ransome, 2016)
8. Impact of human factors and organizational issues on IS-related security and risk
management
Risk management recommendations
The main aspect which is information of the security is that the employee should be very
much aware of the different aspects of the security (Rittinghouse & Ransome, 2016). Data
security is the factor which play an important role in the organization would be secured and how
the different aspects of the operation can be properly implemented. Taking into consideration the
employee it should be taken into consideration that training is given to the employee so that they
can easily indulge into the different aspect of the working which is seen in the sector of the
working.
The main recommendation which can be stated in this sector is stated below:
Recommendation 1: The employee should be informed of the different security policies
Recommendation 2: The employee should be well aware of what step has to be taken if there is
any situation of risk engaged in the working.
Recommendation 3: The employee should have a clear idea of the working which is related to
the context of the working which would be included into the concept of the working of the
organization.
9. Use of logs
The concept of log record can be very much beneficial in the sector of the getting the
overall track of the different activity which is related to the concept. In most of the cases it can
(SOURCE: Rittinghouse & Ransome, 2016)
8. Impact of human factors and organizational issues on IS-related security and risk
management
Risk management recommendations
The main aspect which is information of the security is that the employee should be very
much aware of the different aspects of the security (Rittinghouse & Ransome, 2016). Data
security is the factor which play an important role in the organization would be secured and how
the different aspects of the operation can be properly implemented. Taking into consideration the
employee it should be taken into consideration that training is given to the employee so that they
can easily indulge into the different aspect of the working which is seen in the sector of the
working.
The main recommendation which can be stated in this sector is stated below:
Recommendation 1: The employee should be informed of the different security policies
Recommendation 2: The employee should be well aware of what step has to be taken if there is
any situation of risk engaged in the working.
Recommendation 3: The employee should have a clear idea of the working which is related to
the context of the working which would be included into the concept of the working of the
organization.
9. Use of logs
The concept of log record can be very much beneficial in the sector of the getting the
overall track of the different activity which is related to the concept. In most of the cases it can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

