Report: Systems Design & Implementation for SBRU Resort Booking System
VerifiedAdded on 2021/04/17
|16
|3029
|64
Report
AI Summary
This report presents a comprehensive analysis of the SBRU resort booking system, focusing on its design and implementation. The report begins with an executive summary and an introduction outlining the need for a new system to cater to evolving student needs, incorporating social media features. It includes detailed class and interaction diagrams for booking reservations and adding resorts. A significant portion of the report is dedicated to security, emphasizing the importance of safeguarding against phishing, malware, and identity theft within the social networking subsystem. The security measures involve governance structures, two-step authentication, Geo fencing, and monitoring social media activity. A database schema is developed based on the ER diagrams, and a phased implementation approach using the Agile SCRUM framework is proposed, ensuring incremental improvements and continuous testing. The report also covers project management, with a specific focus on risk management, detailing potential risks such as cost and time overruns, failure to meet user requirements, and poor implementation, along with mitigation strategies. The report concludes with references to the sources used.

SYSTEMS DESIGN &
IMPLEMENTATION REPORT: SBRU RESORT BOOKING SYSTEM
Name
Date
IMPLEMENTATION REPORT: SBRU RESORT BOOKING SYSTEM
Name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

EXECUTIVE SUMMARY
This paper outlines a new design to be used by SBRU for students to book accommodation during
summer breaks and enable resorts to update their details on the system in real time. The use cases
and relations are captured in the class diagrams as well as in the interaction diagrams. Security of
the social networking subsystem is very critical; security to be ensured through a social use policy
for staff and for he users. Security features including firewalls, a record of users, network
monitoring, and encryption will be implemented, along with Geo fencing social subsystem use
areas to avoid unauthorized external use or Phishing. The preferred implementation plan is the the
phased system that enables incremental and gradual replacement of the old system, used with the
SCRUM Agile method. Risk management will be handled through a risk management plan; the
main identified risks include cost override, time override, failure to meet the user requirements,
poor implementation, and loss of stakeholder support
This paper outlines a new design to be used by SBRU for students to book accommodation during
summer breaks and enable resorts to update their details on the system in real time. The use cases
and relations are captured in the class diagrams as well as in the interaction diagrams. Security of
the social networking subsystem is very critical; security to be ensured through a social use policy
for staff and for he users. Security features including firewalls, a record of users, network
monitoring, and encryption will be implemented, along with Geo fencing social subsystem use
areas to avoid unauthorized external use or Phishing. The preferred implementation plan is the the
phased system that enables incremental and gradual replacement of the old system, used with the
SCRUM Agile method. Risk management will be handled through a risk management plan; the
main identified risks include cost override, time override, failure to meet the user requirements,
poor implementation, and loss of stakeholder support
Table of Contents
executive Summary..............................................................................................................................2
Introduction..........................................................................................................................................4
Task 1: Class Diagrams........................................................................................................................4
Task 2: Interaction Diagrams................................................................................................................7
Task 3: Security....................................................................................................................................8
Task 4: Database Schema...................................................................................................................10
Task 5: Implementation......................................................................................................................12
Task 6: Project Management..............................................................................................................14
References..........................................................................................................................................16
executive Summary..............................................................................................................................2
Introduction..........................................................................................................................................4
Task 1: Class Diagrams........................................................................................................................4
Task 2: Interaction Diagrams................................................................................................................7
Task 3: Security....................................................................................................................................8
Task 4: Database Schema...................................................................................................................10
Task 5: Implementation......................................................................................................................12
Task 6: Project Management..............................................................................................................14
References..........................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
SBRU is an online travel service that makes allows students to book vacations for college students;
students have used the service for decades, however, changes in technology have necessitated
changes to better meet student needs. Students can access the system and book rooms and SBRU
has a list of resorts that need to know their bookings of a weekly basis. In line with recent
technological developments, SBRU has opted to update its systems to include social media and this
requires a new design with several use cases. To create a new system for SBRU, this paper creates
class diagrams for booking reservations and adding a resort. The paper then creates interaction
diagrams for the same and then outlines how security for the new system will be achieved. A
database schema is then developed for the ER diagrams developed and a suitable strategy for
deployment proposed. The paper then concludes with a description of how the project management
will be undertaken, with a particular focus on risk management and how the risks will be mitigated
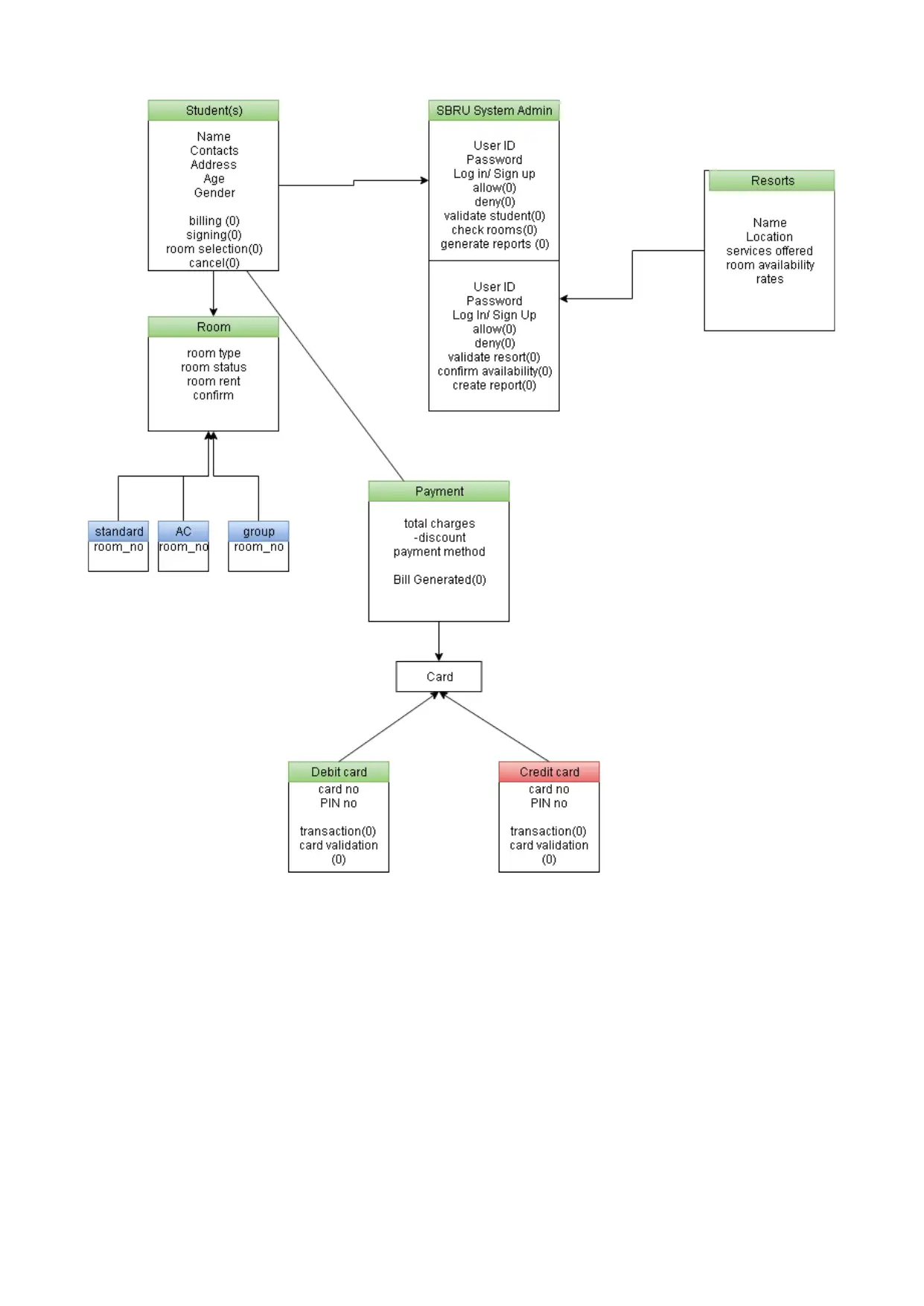
TASK 1: CLASS DIAGRAMS
SBRU is an online travel service that makes allows students to book vacations for college students;
students have used the service for decades, however, changes in technology have necessitated
changes to better meet student needs. Students can access the system and book rooms and SBRU
has a list of resorts that need to know their bookings of a weekly basis. In line with recent
technological developments, SBRU has opted to update its systems to include social media and this
requires a new design with several use cases. To create a new system for SBRU, this paper creates
class diagrams for booking reservations and adding a resort. The paper then creates interaction
diagrams for the same and then outlines how security for the new system will be achieved. A
database schema is then developed for the ER diagrams developed and a suitable strategy for
deployment proposed. The paper then concludes with a description of how the project management
will be undertaken, with a particular focus on risk management and how the risks will be mitigated
TASK 1: CLASS DIAGRAMS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
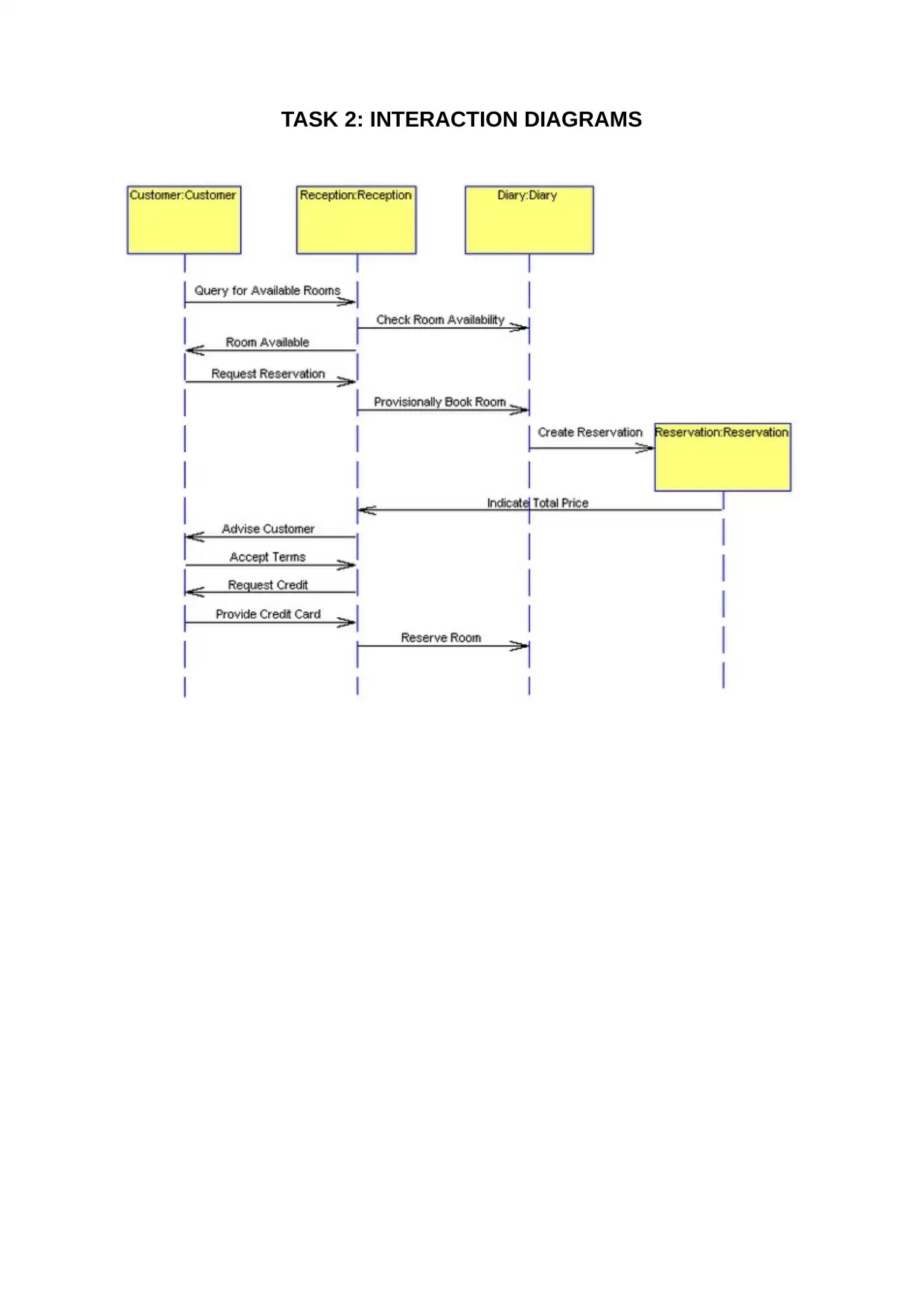
TASK 2: INTERACTION DIAGRAMS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
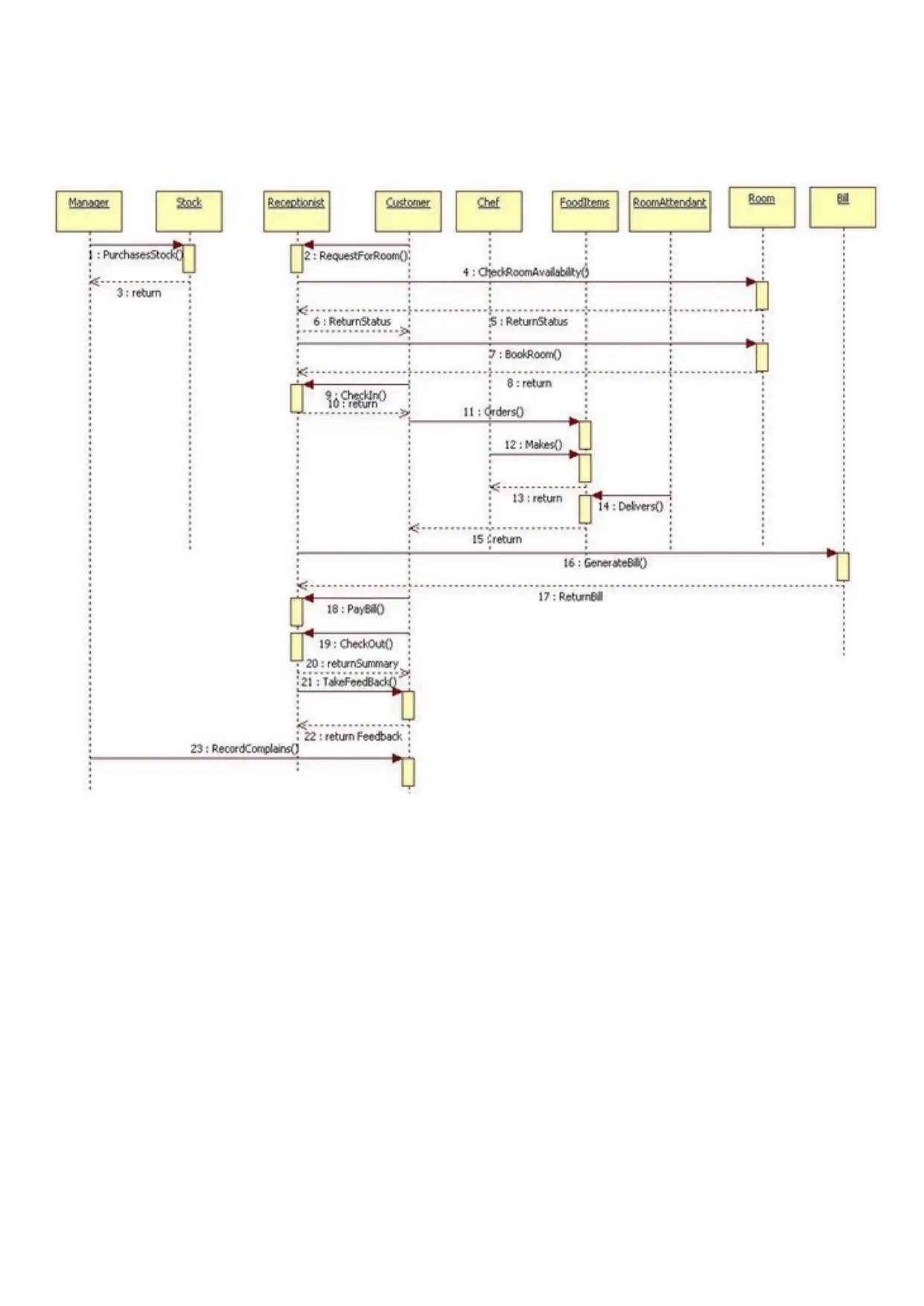

TASK 3: SECURITY
Security is a major concern, especially in the system where clients will be able to conduct
transactions and post personal information when using the SBRU system. The students and possibly
employees will be updating their social media status; given its rise as a means for interaction and
communication, especially when people are on vacation (Luo et al., 2009). Social media has
become the preferred communication channel for many people, and so students on the SBRU
system as well as employees and partners are going to use it frequently. The social networking
subsystem has inherent security risks including phishing and an effective platform for malware
attacks as well as identity theft attacks (Rathore et al., 2017), (Rosenblum, 2007). The first step in
ensuring the security of the system is to implement governance structures with regard to social
media use, both for students at the resort and employees as well as partners (the resorts). Business
data must be classified so that employees understand what sensitive information is and what can be
posted online; this is because internal weaknesses are likely to exacerbate social networking risks
(Fang and LeFevre, 2010). Further, the people that can access the classified and sensitive
information must be defined with access rights controlled through two step authentication. Further,
the policy must extend to the students on vacation that will be the biggest users of the social media
subsystem. Clear guidelines must be set on how they can create secure passwords (Hajli and Lin,
2014). SBRU should undertake effective monitoring and engage directly whenever there are brand
mentions on the social networking subsystem. The firm should keep track of all active social media
accounts and ensure they meet the set policies, including on passwords. When users log in, it is
likely they will leave the site open; the social networking accounts should be designed in such a
way that users are automatically logged out after a period of inactivity, especially when the accounts
are accessed from devices such as laptops, desktops, or public access points (Turban et al., 2017). A
robust policy for social media use will help avoid cases of human error and accidental posting of
sensitive information. Employees must be trained on what kind of information can be posted on the
social networking site for everyone else to see because one of the biggest challenges with social
media is that everyone connected can see a post or information. When students check in, their
mobile devices must be registered in the master list and the URL as well as identifying features
stored; this will ensure that malicious users are detected on time (Liang et al., 2014). The students
also need to have a security policy and be told what they can and can not post for their own security.
For instance, a student seeking some customer service through the social networking subsystem can
post their personal details such as names, or even credit card information; they should be advised
strongly against this. The subsystem should also be designed to reject such information being
visible to the rest of the users (Gupta, Agrawal and Yamaguchi, 2016). Further, when the students
Security is a major concern, especially in the system where clients will be able to conduct
transactions and post personal information when using the SBRU system. The students and possibly
employees will be updating their social media status; given its rise as a means for interaction and
communication, especially when people are on vacation (Luo et al., 2009). Social media has
become the preferred communication channel for many people, and so students on the SBRU
system as well as employees and partners are going to use it frequently. The social networking
subsystem has inherent security risks including phishing and an effective platform for malware
attacks as well as identity theft attacks (Rathore et al., 2017), (Rosenblum, 2007). The first step in
ensuring the security of the system is to implement governance structures with regard to social
media use, both for students at the resort and employees as well as partners (the resorts). Business
data must be classified so that employees understand what sensitive information is and what can be
posted online; this is because internal weaknesses are likely to exacerbate social networking risks
(Fang and LeFevre, 2010). Further, the people that can access the classified and sensitive
information must be defined with access rights controlled through two step authentication. Further,
the policy must extend to the students on vacation that will be the biggest users of the social media
subsystem. Clear guidelines must be set on how they can create secure passwords (Hajli and Lin,
2014). SBRU should undertake effective monitoring and engage directly whenever there are brand
mentions on the social networking subsystem. The firm should keep track of all active social media
accounts and ensure they meet the set policies, including on passwords. When users log in, it is
likely they will leave the site open; the social networking accounts should be designed in such a
way that users are automatically logged out after a period of inactivity, especially when the accounts
are accessed from devices such as laptops, desktops, or public access points (Turban et al., 2017). A
robust policy for social media use will help avoid cases of human error and accidental posting of
sensitive information. Employees must be trained on what kind of information can be posted on the
social networking site for everyone else to see because one of the biggest challenges with social
media is that everyone connected can see a post or information. When students check in, their
mobile devices must be registered in the master list and the URL as well as identifying features
stored; this will ensure that malicious users are detected on time (Liang et al., 2014). The students
also need to have a security policy and be told what they can and can not post for their own security.
For instance, a student seeking some customer service through the social networking subsystem can
post their personal details such as names, or even credit card information; they should be advised
strongly against this. The subsystem should also be designed to reject such information being
visible to the rest of the users (Gupta, Agrawal and Yamaguchi, 2016). Further, when the students
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

are using the social networking subsystem, it is important that the back end is designed to monitor
the geographic location of the user; all log ins, especially from non-traditional devices or locations
must be flagged and confirmation made if the said account holder accessed the account; otherwise it
should be immediately suspended to avoid further damage. SBRU can achieve this by creating a
master list of all URLs, account holder details, and passwords for administrators (Mohamed and
Ahmad, 2012). Scams involving phishing attacks on social media is a very big and real threat for
the social media sub system and this is another priority area for ensuring security. SBRU should
invest in a secure technology, and security should be incorporated right from the design phase.
Because the social networking subsystem will be hosted on its servers, the design should
incorporate a cloud backup in case of problems with the physical hosting servers. Further, the
hosting locations must have high level security implemented, including encryption of information in
the social networking site when in transport and even at rest (Huang and Benyoucef, 2013). SBRU
should implement basic security measures, including a firewall (physical and software) for the
social networking site host servers and install network monitoring tools and software to monitor use
and help identify malicious users pretending to be ‘friendly’ users (phishing attacks). The social
networking subsystem should have security and use policies set such that it cannot be accessed
outside of a given parameter by implementing strict Geo fencing measures; this will ensure
malicious users posing as legitimate users are unable t access and exploit the system from a remote
location (Henne, Szongott and Smith, 2013).
TASK 4: DATABASE SCHEMA
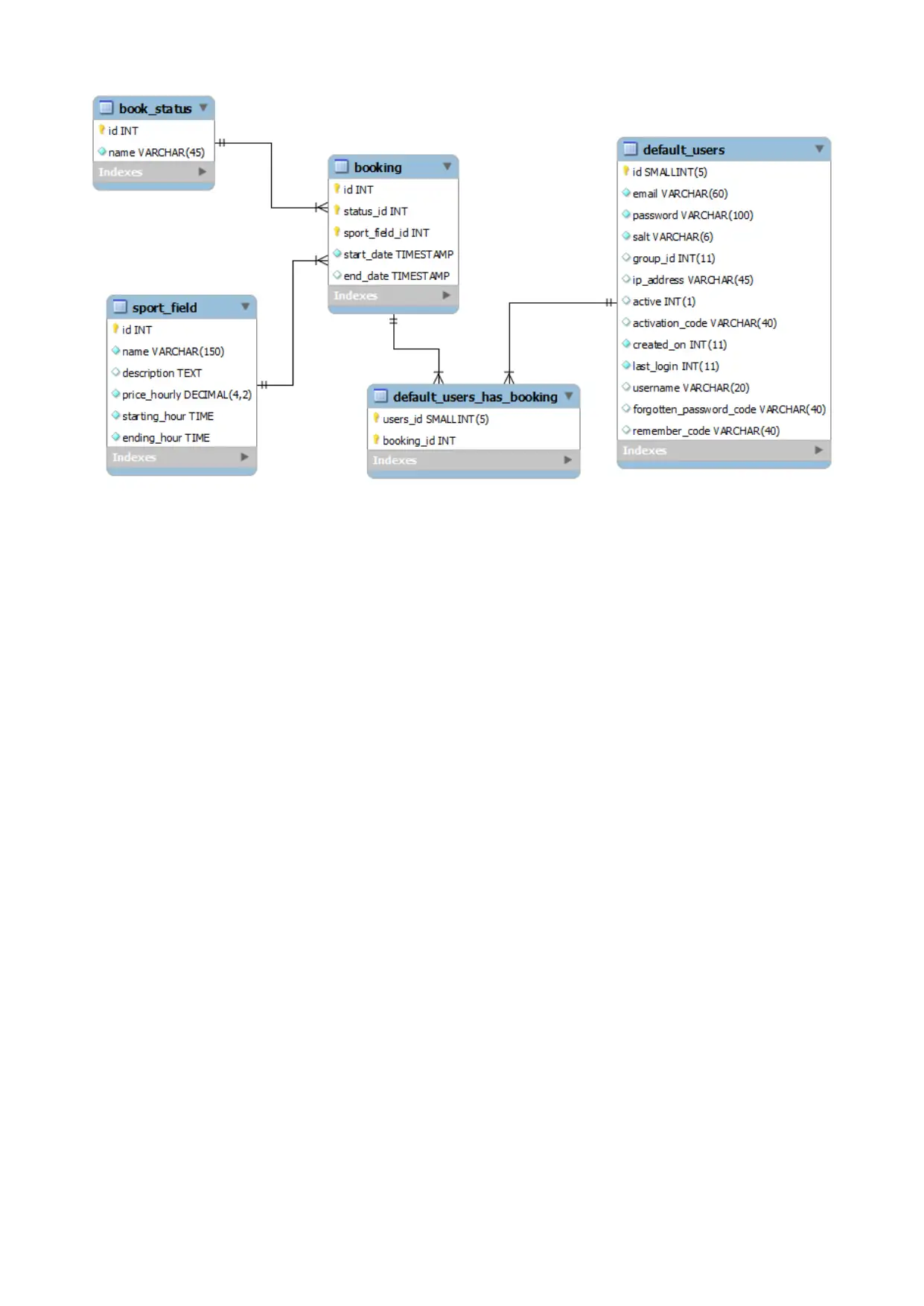
The schema is developed for the users booking a room based on the ER diagrams developed priorly
as shown below;
the geographic location of the user; all log ins, especially from non-traditional devices or locations
must be flagged and confirmation made if the said account holder accessed the account; otherwise it
should be immediately suspended to avoid further damage. SBRU can achieve this by creating a
master list of all URLs, account holder details, and passwords for administrators (Mohamed and
Ahmad, 2012). Scams involving phishing attacks on social media is a very big and real threat for
the social media sub system and this is another priority area for ensuring security. SBRU should
invest in a secure technology, and security should be incorporated right from the design phase.
Because the social networking subsystem will be hosted on its servers, the design should
incorporate a cloud backup in case of problems with the physical hosting servers. Further, the
hosting locations must have high level security implemented, including encryption of information in
the social networking site when in transport and even at rest (Huang and Benyoucef, 2013). SBRU
should implement basic security measures, including a firewall (physical and software) for the
social networking site host servers and install network monitoring tools and software to monitor use
and help identify malicious users pretending to be ‘friendly’ users (phishing attacks). The social
networking subsystem should have security and use policies set such that it cannot be accessed
outside of a given parameter by implementing strict Geo fencing measures; this will ensure
malicious users posing as legitimate users are unable t access and exploit the system from a remote
location (Henne, Szongott and Smith, 2013).
TASK 4: DATABASE SCHEMA
The schema is developed for the users booking a room based on the ER diagrams developed priorly
as shown below;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 5: IMPLEMENTATION
The development and implementation of the system must follow a systematic approach; the
development and testing will be done using the Agile SCRUM framework, in which the systems
will be designed, developed, and tested at the end of every sprint backlog and any issues identified
and rectified. The framework that best suits such a project requires incremental and continuous
improvement, especially with regard to functionality, performance, and security. An incremental
approach based on Agile SCRUM will ensure the final system and subsystems have as few faults
and problem as possible (Ambler, 2013). The best method to implement the system is using the
phased in conversion approach; implementation is a process in which the information system is
implemented in a way that makes it highly operational as desired. Implementation entails
construction a new system from scratch and adding it to an existing one, or at least having some
existing features retained. An effective implementation will enable the users to take over the system
operation and evaluates it. The development will follow an agile approach that will ensure frequent
testing and evaluation with the intended users. This will ensure new user requirements are identified
and any problems or challenges with its use also identified and resolved up front. Implementing a
new system such as proposed for SBRU is a form of change within an organization; change
implementation always faces resistance and so at the beginning during the planning phase, change
management strategies that are effective for the particular case should be used. This requires getting
views from staff on the proposed changes and having them involved, through effective leadership so
they take ownership of the system from start. This will ensure other interventions, such as
implementing security policies are well received and internalized. End user training will be
incorporated into the implementation of the system; users will be trained on the new system for
booking and how resorts can post and update information (Leffingwell and Reinertsen, 2012). The
training will also cover how to work with the new processes, maintain security, and troubleshoot
and solve basic problems. Implementation requires conversion as well; conversion refers to the
process of migrating to the new system from the old system. Conversion offers a system that is
understandable and structured to ensure communication between stakeholders is improved and that
the new system implementation is a success. A successful conversion will require a suitable
conversion plan that details all activities that must be undertaken during implementation of the new
system (Ford et al., 2010). The conversion plan anticipates any challenges or problems and
mitigates these upfront; it will form part of the overall risk management strategy. The conversion
plan will name all files to be converted, identify data requirements for developing new files during
conversion, and list all new procedures and documents required for successful implementation. The
plans also detail the controls for every activity and give responsibilities to a person for every
The development and implementation of the system must follow a systematic approach; the
development and testing will be done using the Agile SCRUM framework, in which the systems
will be designed, developed, and tested at the end of every sprint backlog and any issues identified
and rectified. The framework that best suits such a project requires incremental and continuous
improvement, especially with regard to functionality, performance, and security. An incremental
approach based on Agile SCRUM will ensure the final system and subsystems have as few faults
and problem as possible (Ambler, 2013). The best method to implement the system is using the
phased in conversion approach; implementation is a process in which the information system is
implemented in a way that makes it highly operational as desired. Implementation entails
construction a new system from scratch and adding it to an existing one, or at least having some
existing features retained. An effective implementation will enable the users to take over the system
operation and evaluates it. The development will follow an agile approach that will ensure frequent
testing and evaluation with the intended users. This will ensure new user requirements are identified
and any problems or challenges with its use also identified and resolved up front. Implementing a
new system such as proposed for SBRU is a form of change within an organization; change
implementation always faces resistance and so at the beginning during the planning phase, change
management strategies that are effective for the particular case should be used. This requires getting
views from staff on the proposed changes and having them involved, through effective leadership so
they take ownership of the system from start. This will ensure other interventions, such as
implementing security policies are well received and internalized. End user training will be
incorporated into the implementation of the system; users will be trained on the new system for
booking and how resorts can post and update information (Leffingwell and Reinertsen, 2012). The
training will also cover how to work with the new processes, maintain security, and troubleshoot
and solve basic problems. Implementation requires conversion as well; conversion refers to the
process of migrating to the new system from the old system. Conversion offers a system that is
understandable and structured to ensure communication between stakeholders is improved and that
the new system implementation is a success. A successful conversion will require a suitable
conversion plan that details all activities that must be undertaken during implementation of the new
system (Ford et al., 2010). The conversion plan anticipates any challenges or problems and
mitigates these upfront; it will form part of the overall risk management strategy. The conversion
plan will name all files to be converted, identify data requirements for developing new files during
conversion, and list all new procedures and documents required for successful implementation. The
plans also detail the controls for every activity and give responsibilities to a person for every
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





