Report on Intrusion Detection in SCADA using Gas Pipeline Datasets
VerifiedAdded on 2023/03/24
|39
|12934
|83
Report
AI Summary
This report investigates intrusion detection within Supervisory Control and Data Acquisition (SCADA) systems, focusing on the vulnerabilities introduced by increased connectivity in modern industrial control systems. It introduces two new datasets derived from network traffic captured on a gas pipeline to support the development and testing of Intrusion Detection Systems (IDS). The report details the background of SCADA systems, common threats, and existing datasets, highlighting the limitations of previous datasets like the Gao dataset. It describes the methodology used to collect the gas pipeline data, including the system setup, network transactions, and simulated attacks. The report further explains the structure of the datasets, including raw network transaction data and ARFF datasets, emphasizing the importance of payload information, network data, and labels for effective intrusion detection. Ultimately, the research aims to provide a valuable resource for researchers and industry professionals working to enhance the security of SCADA systems.

Intrusion
Detection on
SCADA
Detection on
SCADA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This report will use a new SCADA system to monitor and control industrial control
systems in many industries as well as economic sectors. There is a rise in the security concerns
due to this new found connectivity. To researchers and industry this thesis makes one primary
contribution. For SCADA system two datasets have been introduced. This has been introduced to
support the intrusion detection system. The network traffic captured on gas pipeline is included
in the dataset. In order to train and test proposed algorithms, IDS researcher lack in a common
framework.
This report will use a new SCADA system to monitor and control industrial control
systems in many industries as well as economic sectors. There is a rise in the security concerns
due to this new found connectivity. To researchers and industry this thesis makes one primary
contribution. For SCADA system two datasets have been introduced. This has been introduced to
support the intrusion detection system. The network traffic captured on gas pipeline is included
in the dataset. In order to train and test proposed algorithms, IDS researcher lack in a common
framework.

Table of Contents
Abstract............................................................................................................................................2
CHAPTER 1: INTRODUCTION....................................................................................................1
1.1 Background............................................................................................................................1
1.2 Research Contributions..........................................................................................................3
1.3 Organisation...........................................................................................................................4
CHAPTER 2: LITERATURE REVIEW.........................................................................................6
2.1 SCADA System Threats........................................................................................................6
2.2 Intrusion Detection................................................................................................................7
2.3 SCADA Datasets and test beds............................................................................................11
CHAPTER 3: GAS PIPELINE DATASET..................................................................................13
3.1 Introduction..........................................................................................................................13
3.2 Previous work......................................................................................................................13
3.3 Gas pipeline system.............................................................................................................14
3.4 Dataset Collection Methodology.........................................................................................15
3.5 Dataset Description..............................................................................................................17
3.5.1 Raw Dataset......................................................................................................................17
3.5.2 ARFF dataset....................................................................................................................19
CONCLUSION..............................................................................................................................33
REFERENCES..............................................................................................................................34
Abstract............................................................................................................................................2
CHAPTER 1: INTRODUCTION....................................................................................................1
1.1 Background............................................................................................................................1
1.2 Research Contributions..........................................................................................................3
1.3 Organisation...........................................................................................................................4
CHAPTER 2: LITERATURE REVIEW.........................................................................................6
2.1 SCADA System Threats........................................................................................................6
2.2 Intrusion Detection................................................................................................................7
2.3 SCADA Datasets and test beds............................................................................................11
CHAPTER 3: GAS PIPELINE DATASET..................................................................................13
3.1 Introduction..........................................................................................................................13
3.2 Previous work......................................................................................................................13
3.3 Gas pipeline system.............................................................................................................14
3.4 Dataset Collection Methodology.........................................................................................15
3.5 Dataset Description..............................................................................................................17
3.5.1 Raw Dataset......................................................................................................................17
3.5.2 ARFF dataset....................................................................................................................19
CONCLUSION..............................................................................................................................33
REFERENCES..............................................................................................................................34
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CHAPTER 1: INTRODUCTION
1.1 Background
The utilities that act very critical are being managed and controlled by the Supervisory
Control and Data Acquisitions (SCADA). There are various controlled systems involved which
includes the railroads, pipelines, power plants etc. Sometime before, these all systems were
excluded from the other various networks but now have been desegregated with the corporate
networks and the Internet. This integration with the various networks have maximized the
control of the organisations, thus savings have been also accounted up for the same. Various
security concerns are also needed to be analysed because of these new connections. The
susceptibility may exist in any of the system, if so, then it will permit the attackers to exploit the
data completely, thus having all the control over the SCADA systems. This control over can
cause breakdown in the hardware, thus harming the lives of the people.
The visualisation and control of the critical infrastructure systems have been controlled
by the SCADA systems. Four components have been used for the composition of these systems.
The first part contains the sensors and actuators, the second has programmable logic controllers
(PLCs), third is the supervisory control. Sensors are devices which collects the information about
a system. The state of the system is being controlled by the actuators which involves motor,
pump etc. PLCs has the responsibility of managing the collected data representing the state of
system. These controllers can also be considered as remote terminal units (RTUs). The master
terminal unit (MTU) interacts with these controls by managing and handling them. Various
protocols are there for carrying out whole communication such as Fieldbus, Profibus, Distributed
Network Protocol Version 3 (DNP3) and Modbus. Human machine interface (HMI) is
categorised as the final level. It is being used by an operator for representation of the MTU's
collected information. The role of an HMI is to manage the representation of the system along
with its sub systems. It also has another role of exchanging parameters within the SCADA
systems for continuing the interaction with the MTU. A simple SCADA system is represented
below:
1
1.1 Background
The utilities that act very critical are being managed and controlled by the Supervisory
Control and Data Acquisitions (SCADA). There are various controlled systems involved which
includes the railroads, pipelines, power plants etc. Sometime before, these all systems were
excluded from the other various networks but now have been desegregated with the corporate
networks and the Internet. This integration with the various networks have maximized the
control of the organisations, thus savings have been also accounted up for the same. Various
security concerns are also needed to be analysed because of these new connections. The
susceptibility may exist in any of the system, if so, then it will permit the attackers to exploit the
data completely, thus having all the control over the SCADA systems. This control over can
cause breakdown in the hardware, thus harming the lives of the people.
The visualisation and control of the critical infrastructure systems have been controlled
by the SCADA systems. Four components have been used for the composition of these systems.
The first part contains the sensors and actuators, the second has programmable logic controllers
(PLCs), third is the supervisory control. Sensors are devices which collects the information about
a system. The state of the system is being controlled by the actuators which involves motor,
pump etc. PLCs has the responsibility of managing the collected data representing the state of
system. These controllers can also be considered as remote terminal units (RTUs). The master
terminal unit (MTU) interacts with these controls by managing and handling them. Various
protocols are there for carrying out whole communication such as Fieldbus, Profibus, Distributed
Network Protocol Version 3 (DNP3) and Modbus. Human machine interface (HMI) is
categorised as the final level. It is being used by an operator for representation of the MTU's
collected information. The role of an HMI is to manage the representation of the system along
with its sub systems. It also has another role of exchanging parameters within the SCADA
systems for continuing the interaction with the MTU. A simple SCADA system is represented
below:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
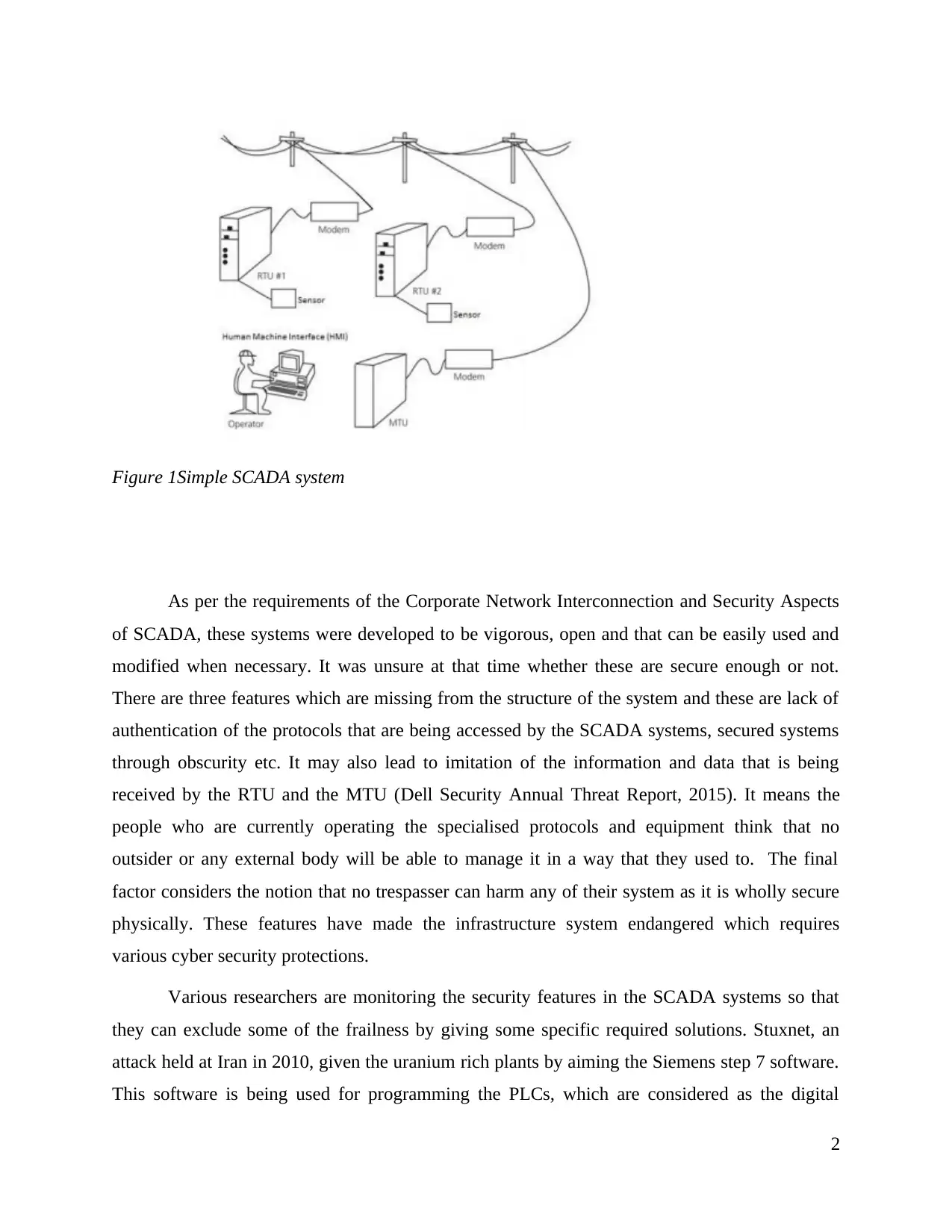
Figure 1Simple SCADA system
As per the requirements of the Corporate Network Interconnection and Security Aspects
of SCADA, these systems were developed to be vigorous, open and that can be easily used and
modified when necessary. It was unsure at that time whether these are secure enough or not.
There are three features which are missing from the structure of the system and these are lack of
authentication of the protocols that are being accessed by the SCADA systems, secured systems
through obscurity etc. It may also lead to imitation of the information and data that is being
received by the RTU and the MTU (Dell Security Annual Threat Report, 2015). It means the
people who are currently operating the specialised protocols and equipment think that no
outsider or any external body will be able to manage it in a way that they used to. The final
factor considers the notion that no trespasser can harm any of their system as it is wholly secure
physically. These features have made the infrastructure system endangered which requires
various cyber security protections.
Various researchers are monitoring the security features in the SCADA systems so that
they can exclude some of the frailness by giving some specific required solutions. Stuxnet, an
attack held at Iran in 2010, given the uranium rich plants by aiming the Siemens step 7 software.
This software is being used for programming the PLCs, which are considered as the digital
2
As per the requirements of the Corporate Network Interconnection and Security Aspects
of SCADA, these systems were developed to be vigorous, open and that can be easily used and
modified when necessary. It was unsure at that time whether these are secure enough or not.
There are three features which are missing from the structure of the system and these are lack of
authentication of the protocols that are being accessed by the SCADA systems, secured systems
through obscurity etc. It may also lead to imitation of the information and data that is being
received by the RTU and the MTU (Dell Security Annual Threat Report, 2015). It means the
people who are currently operating the specialised protocols and equipment think that no
outsider or any external body will be able to manage it in a way that they used to. The final
factor considers the notion that no trespasser can harm any of their system as it is wholly secure
physically. These features have made the infrastructure system endangered which requires
various cyber security protections.
Various researchers are monitoring the security features in the SCADA systems so that
they can exclude some of the frailness by giving some specific required solutions. Stuxnet, an
attack held at Iran in 2010, given the uranium rich plants by aiming the Siemens step 7 software.
This software is being used for programming the PLCs, which are considered as the digital
2

devices handling the industrial systems. The windows environment has been introduced with it
and initiated their search for the Siemen's software. There was a play book named How Stuxnet
is rewriting the cyber terrorism play book, after the identification of the software, Stuxnet was
free enough to have the required data and putting the system in a critical phase. Re writing
firmware and the ladder logic made this possible on PLC. This, further permits the attacker to
forcefully produce false responses towards PLC.
The SCADA system has also been attacked by another attacker, Flame which was able to
collect the surveillance information. Flame is also similar to Stuxnet in a way that it infects all
the systems that are windows based on only distinguishable fact between the both is that the
Flame does not focuses on doing any harm, rather it focuses on collecting and streaming of the
data to the control server (Boyer and Stuart, 2014). After that, the filtration takes place and the
outcomes can be represented to the operator at the end. This specific attack was being used in
Iran for acquiring information of other states.
Aurora, another event by Idaho National laboratory, was being represented to the
government to discuss about the seriousness of these ongoing attacks. It was being experienced
on a temporary basis in which it duplicated the controls of the power system. The control system
was targeted first by the attack and also tried to include and exclude the circuit breakers. Because
of a minor change in the operation cycle, a fully damaged generator was the last and their final
goal which would have caused a fatal condition of the phase. Instead, it has not been imitated in
real but they were successful in grabbing the attention of government. Also, they were able to
increase the development in industrial control system (ICS).
An Intrusion detection system (IDS) can help in detecting and alerting the operators so
that they can prevent the system from further damages. IDS act as very essential part of
providing security features in any system that is communication based. It seems perfect to
manage and analyse the further conditions. In SCADA systems, these are being trained with data
logs which demonstrates the actual traffic. Any dataset which can modify and improve the IDS
system which is required.
1.2 Research Contributions
A primary contribution has been made to the industry and the researches. This
contribution involves two data sets which can be used for replacement of a previous one. The
3
and initiated their search for the Siemen's software. There was a play book named How Stuxnet
is rewriting the cyber terrorism play book, after the identification of the software, Stuxnet was
free enough to have the required data and putting the system in a critical phase. Re writing
firmware and the ladder logic made this possible on PLC. This, further permits the attacker to
forcefully produce false responses towards PLC.
The SCADA system has also been attacked by another attacker, Flame which was able to
collect the surveillance information. Flame is also similar to Stuxnet in a way that it infects all
the systems that are windows based on only distinguishable fact between the both is that the
Flame does not focuses on doing any harm, rather it focuses on collecting and streaming of the
data to the control server (Boyer and Stuart, 2014). After that, the filtration takes place and the
outcomes can be represented to the operator at the end. This specific attack was being used in
Iran for acquiring information of other states.
Aurora, another event by Idaho National laboratory, was being represented to the
government to discuss about the seriousness of these ongoing attacks. It was being experienced
on a temporary basis in which it duplicated the controls of the power system. The control system
was targeted first by the attack and also tried to include and exclude the circuit breakers. Because
of a minor change in the operation cycle, a fully damaged generator was the last and their final
goal which would have caused a fatal condition of the phase. Instead, it has not been imitated in
real but they were successful in grabbing the attention of government. Also, they were able to
increase the development in industrial control system (ICS).
An Intrusion detection system (IDS) can help in detecting and alerting the operators so
that they can prevent the system from further damages. IDS act as very essential part of
providing security features in any system that is communication based. It seems perfect to
manage and analyse the further conditions. In SCADA systems, these are being trained with data
logs which demonstrates the actual traffic. Any dataset which can modify and improve the IDS
system which is required.
1.2 Research Contributions
A primary contribution has been made to the industry and the researches. This
contribution involves two data sets which can be used for replacement of a previous one. The
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Gao data set was not suitable for the research of the IDS. In the Mississippi State University's in
house SCADA gas pipeline, Network transactions within MTU and the RTU is the data collected
in the data set. For replication of the real attacks and the activities of the operators on the
pipeline of the gas, various new data sets were collected with the help of a novel framework.
When compared with a previous data set, it was found that all the issues that affected were
resolved.
Features have been categorised in three different forms which includes payload
information, network data and labels. The network data provides a specific technique for
intruding the detection structure for competing against. SCADA systems have various network
topologies which are already decided and there are repetitive nodes as well. These systems do
not act like Information technology (IT) networks. It acts conductive with the IDS and is
conscious enough to detect any abnormal activity. Another category compiles of the payload
information. It provides the data about the pipeline state of the gas, parameters etc. These factors
of the system are enough for understanding the level of performance and also it will be able to
monitor if it is present in critical state as well.
For the assessment of performance of the SCADA system, data sets are suggested to be
used in the aid researches with the help of original patterns of the SCADA attacks and operations
of the HMI as well. These systems have a longer life line so it fixes the interactions patterns also.
Then, these data sets are permitted to be used for utilizing SCADA IDS structures by giving
some general characteristics.
1.3 Organisation
The next chapter covers the threatening areas of the SCADA systems, critical
infrastructure systems for the IDS along with an evaluation of the test beds and data sets of the
SCADA. It will be properly defined in this chapter that what is the importance of these data sets
and how this can prove purposeful to the people around. Third chapter, will be sufficiently able
to demonstrate the pipeline system of the gas which helped the data sets to be created adding up
the methodologies and framework which is to be implemented as well. Further two sections of
the third chapter describe the two data sets which will be created. It includes the raw network
transaction data and the information that is being collected from the first. Along with all this,
another section in the chapter comprises of the data set that has been improvised from the earlier
4
house SCADA gas pipeline, Network transactions within MTU and the RTU is the data collected
in the data set. For replication of the real attacks and the activities of the operators on the
pipeline of the gas, various new data sets were collected with the help of a novel framework.
When compared with a previous data set, it was found that all the issues that affected were
resolved.
Features have been categorised in three different forms which includes payload
information, network data and labels. The network data provides a specific technique for
intruding the detection structure for competing against. SCADA systems have various network
topologies which are already decided and there are repetitive nodes as well. These systems do
not act like Information technology (IT) networks. It acts conductive with the IDS and is
conscious enough to detect any abnormal activity. Another category compiles of the payload
information. It provides the data about the pipeline state of the gas, parameters etc. These factors
of the system are enough for understanding the level of performance and also it will be able to
monitor if it is present in critical state as well.
For the assessment of performance of the SCADA system, data sets are suggested to be
used in the aid researches with the help of original patterns of the SCADA attacks and operations
of the HMI as well. These systems have a longer life line so it fixes the interactions patterns also.
Then, these data sets are permitted to be used for utilizing SCADA IDS structures by giving
some general characteristics.
1.3 Organisation
The next chapter covers the threatening areas of the SCADA systems, critical
infrastructure systems for the IDS along with an evaluation of the test beds and data sets of the
SCADA. It will be properly defined in this chapter that what is the importance of these data sets
and how this can prove purposeful to the people around. Third chapter, will be sufficiently able
to demonstrate the pipeline system of the gas which helped the data sets to be created adding up
the methodologies and framework which is to be implemented as well. Further two sections of
the third chapter describe the two data sets which will be created. It includes the raw network
transaction data and the information that is being collected from the first. Along with all this,
another section in the chapter comprises of the data set that has been improvised from the earlier
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

one. Then, at last there would be the last chapter compiling of the conclusions came from this
research.
5
research.
5
CHAPTER 2: LITERATURE REVIEW
2.1 SCADA System Threats
Using the SCADA network traffic, it has become easy and simple for the researchers to
study and develop IDS systems. These SCADA systems, day by day are becoming more unsafe
to the external parties and also have threatened the professionals as well. In the overview of
Security for Process Control, it has discussed the value of the industrial control systems by
including various challenges of the security of SCADA and also providing support and help to
have the outcomes of the challenges (Almalawi and et.al, 2014). Various types of security threats
are also included in the SCADA systems. In the Challenges and direction towards secure
communication, the issues regarding the security in the SCADA has been discussed along with
the smart grid technologies. It has been discussed in detail that these open standard protocols are
becoming endangered to various cyber-attacks. On isolated networks, these protocols have been
made, the security features have not been discussed there as they are not being connected to the
larger networks. According to Hong and Lee, there were some issues with the intrusion detection
systems also. For determining any abnormal activity in the system, it was asking for the various
network traffic patterns by which it can be able to find easily. There is a requirement of a data set
demonstrating the original SCADA system which must be including the peculiar traffic for
preparing the IDS that is being customized for applications of SCADA. As per Kang and et.al
(2009), it has involved various problems of the SCADA system. The table represented below
various attacks and the specific systems.
6
2.1 SCADA System Threats
Using the SCADA network traffic, it has become easy and simple for the researchers to
study and develop IDS systems. These SCADA systems, day by day are becoming more unsafe
to the external parties and also have threatened the professionals as well. In the overview of
Security for Process Control, it has discussed the value of the industrial control systems by
including various challenges of the security of SCADA and also providing support and help to
have the outcomes of the challenges (Almalawi and et.al, 2014). Various types of security threats
are also included in the SCADA systems. In the Challenges and direction towards secure
communication, the issues regarding the security in the SCADA has been discussed along with
the smart grid technologies. It has been discussed in detail that these open standard protocols are
becoming endangered to various cyber-attacks. On isolated networks, these protocols have been
made, the security features have not been discussed there as they are not being connected to the
larger networks. According to Hong and Lee, there were some issues with the intrusion detection
systems also. For determining any abnormal activity in the system, it was asking for the various
network traffic patterns by which it can be able to find easily. There is a requirement of a data set
demonstrating the original SCADA system which must be including the peculiar traffic for
preparing the IDS that is being customized for applications of SCADA. As per Kang and et.al
(2009), it has involved various problems of the SCADA system. The table represented below
various attacks and the specific systems.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
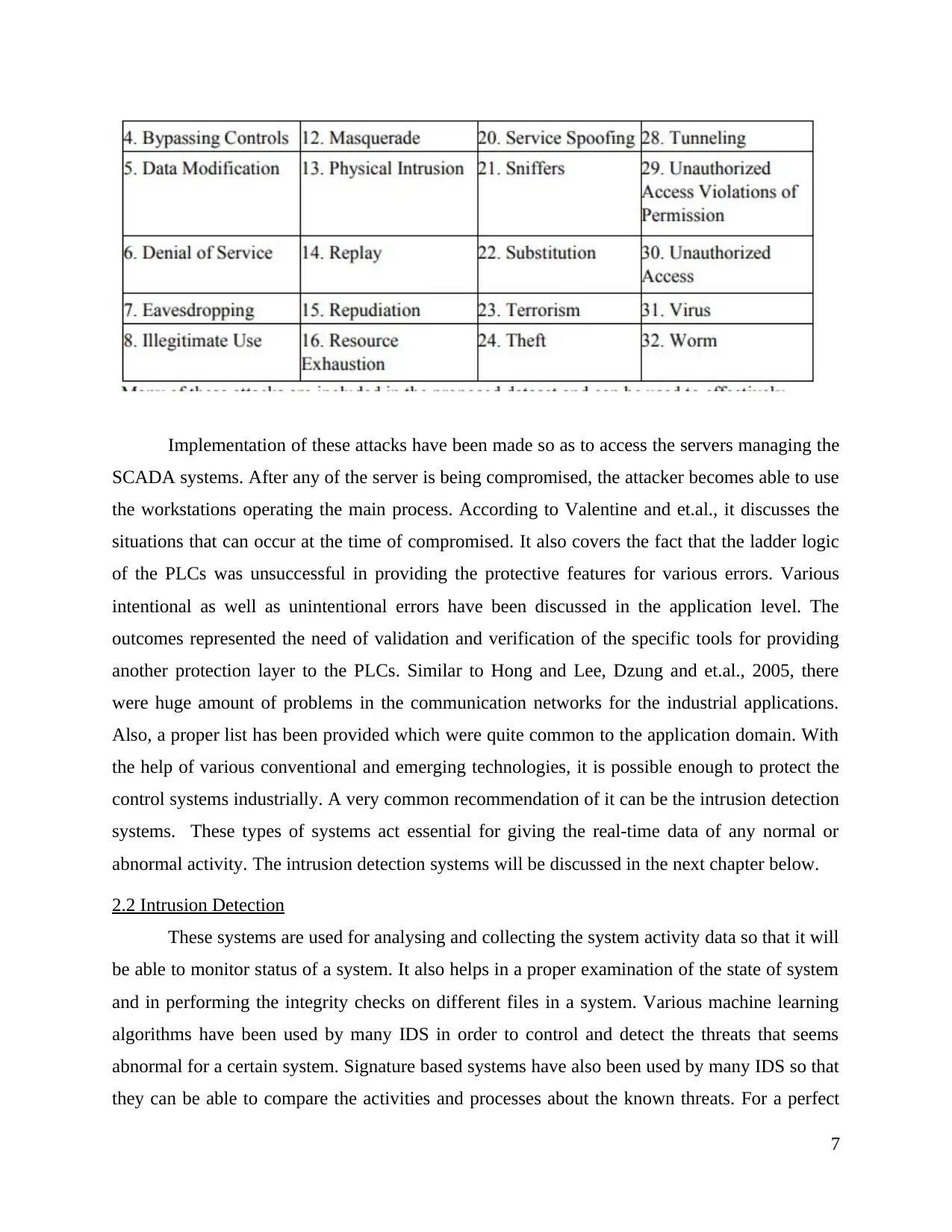
Implementation of these attacks have been made so as to access the servers managing the
SCADA systems. After any of the server is being compromised, the attacker becomes able to use
the workstations operating the main process. According to Valentine and et.al., it discusses the
situations that can occur at the time of compromised. It also covers the fact that the ladder logic
of the PLCs was unsuccessful in providing the protective features for various errors. Various
intentional as well as unintentional errors have been discussed in the application level. The
outcomes represented the need of validation and verification of the specific tools for providing
another protection layer to the PLCs. Similar to Hong and Lee, Dzung and et.al., 2005, there
were huge amount of problems in the communication networks for the industrial applications.
Also, a proper list has been provided which were quite common to the application domain. With
the help of various conventional and emerging technologies, it is possible enough to protect the
control systems industrially. A very common recommendation of it can be the intrusion detection
systems. These types of systems act essential for giving the real-time data of any normal or
abnormal activity. The intrusion detection systems will be discussed in the next chapter below.
2.2 Intrusion Detection
These systems are used for analysing and collecting the system activity data so that it will
be able to monitor status of a system. It also helps in a proper examination of the state of system
and in performing the integrity checks on different files in a system. Various machine learning
algorithms have been used by many IDS in order to control and detect the threats that seems
abnormal for a certain system. Signature based systems have also been used by many IDS so that
they can be able to compare the activities and processes about the known threats. For a perfect
7
SCADA systems. After any of the server is being compromised, the attacker becomes able to use
the workstations operating the main process. According to Valentine and et.al., it discusses the
situations that can occur at the time of compromised. It also covers the fact that the ladder logic
of the PLCs was unsuccessful in providing the protective features for various errors. Various
intentional as well as unintentional errors have been discussed in the application level. The
outcomes represented the need of validation and verification of the specific tools for providing
another protection layer to the PLCs. Similar to Hong and Lee, Dzung and et.al., 2005, there
were huge amount of problems in the communication networks for the industrial applications.
Also, a proper list has been provided which were quite common to the application domain. With
the help of various conventional and emerging technologies, it is possible enough to protect the
control systems industrially. A very common recommendation of it can be the intrusion detection
systems. These types of systems act essential for giving the real-time data of any normal or
abnormal activity. The intrusion detection systems will be discussed in the next chapter below.
2.2 Intrusion Detection
These systems are used for analysing and collecting the system activity data so that it will
be able to monitor status of a system. It also helps in a proper examination of the state of system
and in performing the integrity checks on different files in a system. Various machine learning
algorithms have been used by many IDS in order to control and detect the threats that seems
abnormal for a certain system. Signature based systems have also been used by many IDS so that
they can be able to compare the activities and processes about the known threats. For a perfect
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

detection system, all these features can be combined together and it will also help in providing an
efficient layer of protection from various attacks.
There are three components of an IDS and it includes the Network Intrusion Detection
systems (NIDS). It uses a signature based system for the determination of the various processes
and activities in the system that is everything within normal factors or it can be found in the
known attack's database. The activity is being reported to the administrator or operator in the
case where the NIDS has found a match of a signature. The NIDS helps in providing a warning.
Rather it does not prevent it from the on-going traffic ( Sugwon and Myongho, 2010). Another
component is considered as the Network node intrusion detection system (NNIDS) which seems
more effective for the interaction within a single bus system and a control station. Although, it is
quite similar to the NIDS, but it also gives analysis of the behaviour along with the pattern
recognition. An algorithm is necessary for each control set to work according to its specific
functions. There is a need for specialisation so that higher level of data security can be provided
to the systems. The sub system has the final copy of the security and the process is called as Host
Intrusion Detection System (HIDS). It has the responsibility to analyse the actual state of the
system, thus also can have various integrity checks on it. It helps them in determining whether
there is an abnormal activity or not that may affect the whole process. There has been seen a
lower variability in different states but the changes in the processes can be easily detected with
the help of an installed IDS.
As discussed, there have been a huge amount of limitations for the solutions of the IDS. It
can be false positive rate from the noise that has been produced in the general activities. It has
been introduced in the form of a packet or like a malfunctioning hardware. It can be further
analysed as quite abnormal and also reported as a threat to the available operator. These huge
amounts of false reports can have a negative impact on the overall effectiveness of the IDS. This
is because it can erase the threats, causing the ignorance of the warnings. There are various
problems with the IDS solutions but a very common is the regular need of upgrading the
signatures. It has been a major issue with the IDS solutions. Updating of every system is
essential but sometimes can be overlooked by the operators which can also cause some
vulnerable changes to the whole system. Another limitation of this can be considered as the fact
that any system with poor authentication and un identified protocols, cannot be secured by the
IDS. The reason behind it can be spoofing. It only creates problems where a system is recording
8
efficient layer of protection from various attacks.
There are three components of an IDS and it includes the Network Intrusion Detection
systems (NIDS). It uses a signature based system for the determination of the various processes
and activities in the system that is everything within normal factors or it can be found in the
known attack's database. The activity is being reported to the administrator or operator in the
case where the NIDS has found a match of a signature. The NIDS helps in providing a warning.
Rather it does not prevent it from the on-going traffic ( Sugwon and Myongho, 2010). Another
component is considered as the Network node intrusion detection system (NNIDS) which seems
more effective for the interaction within a single bus system and a control station. Although, it is
quite similar to the NIDS, but it also gives analysis of the behaviour along with the pattern
recognition. An algorithm is necessary for each control set to work according to its specific
functions. There is a need for specialisation so that higher level of data security can be provided
to the systems. The sub system has the final copy of the security and the process is called as Host
Intrusion Detection System (HIDS). It has the responsibility to analyse the actual state of the
system, thus also can have various integrity checks on it. It helps them in determining whether
there is an abnormal activity or not that may affect the whole process. There has been seen a
lower variability in different states but the changes in the processes can be easily detected with
the help of an installed IDS.
As discussed, there have been a huge amount of limitations for the solutions of the IDS. It
can be false positive rate from the noise that has been produced in the general activities. It has
been introduced in the form of a packet or like a malfunctioning hardware. It can be further
analysed as quite abnormal and also reported as a threat to the available operator. These huge
amounts of false reports can have a negative impact on the overall effectiveness of the IDS. This
is because it can erase the threats, causing the ignorance of the warnings. There are various
problems with the IDS solutions but a very common is the regular need of upgrading the
signatures. It has been a major issue with the IDS solutions. Updating of every system is
essential but sometimes can be overlooked by the operators which can also cause some
vulnerable changes to the whole system. Another limitation of this can be considered as the fact
that any system with poor authentication and un identified protocols, cannot be secured by the
IDS. The reason behind it can be spoofing. It only creates problems where a system is recording
8

pressure data. The above example can be compared with the Aurora attack which was developed
for a power system and made it a tough situation for the generator. In that attack, it was possible
enough to place the generator in about phase state. It could be proved very harmful to the system
as well. Out of huge limitations, the final one was with the analysis of the encrypted traffic. In
this, Inserting the packets deeply in an IDS are not possible. The traffic should be encrypted
before the occurrence of any attempt. There are issues in the processing times and also can affect
the IDS for performing in a real time. Instead of the fact that IDS consist of various limitations, it
still has an important role in providing proper security to the networks.
In computer networks and various virus software's, IDS are being commonly used. For
providing security to the personal computers and the web servers, these systems have an
essential role. Also, they are considering the field of research for ICS professionals. In SCADA
systems, there are various reasons for implementing IDS. A very common example of this can
be the dependence of highly critical structure on the specialised protocols which have been made
in accordance of the ease and reliability (Introduction to Industrial Control Networks, 2012). It
gives priority to these factors rather than giving to the security. These systems depend on the
operators and also requires automated approaches for proper monitoring the general activities of
the system. Various studies have been there to provide a much wider approach which are
sufficient for improving the security features has easily distributed to the system.
IDS have developed an approach that is to be implemented on the SCADA systems and it
was represented in an unsupervised anomaly based detections approach for integrity attacks on
the SCADA systems. It was proposed that a learning that is not a supervised algorithm, would
act best on the SCADA network. the theory has also been tested with the help of data and
information from a real or industrial system. It could be a water plant. There were many pre-
processing techniques which were used as the pre-processing techniques and they were
managing the input so that the improved results can come as an outcome. It also controlled the
noise factors that was within the data sets from the water plants. Then, it also has been proposed
that the data sets through the clustering algorithm was a behavioural analysis technique. It was
concluded that this this type of behavioural approach that represents the promising behaviour and
the ability to accomplish high detection results in the specific field. With the help of fixed width
algorithm, it was easy to achieve the maximum of the detection rate of 90% with a false
negativity of .01%. It is concern with a few factors such as the complexity and time of algorithm
9
for a power system and made it a tough situation for the generator. In that attack, it was possible
enough to place the generator in about phase state. It could be proved very harmful to the system
as well. Out of huge limitations, the final one was with the analysis of the encrypted traffic. In
this, Inserting the packets deeply in an IDS are not possible. The traffic should be encrypted
before the occurrence of any attempt. There are issues in the processing times and also can affect
the IDS for performing in a real time. Instead of the fact that IDS consist of various limitations, it
still has an important role in providing proper security to the networks.
In computer networks and various virus software's, IDS are being commonly used. For
providing security to the personal computers and the web servers, these systems have an
essential role. Also, they are considering the field of research for ICS professionals. In SCADA
systems, there are various reasons for implementing IDS. A very common example of this can
be the dependence of highly critical structure on the specialised protocols which have been made
in accordance of the ease and reliability (Introduction to Industrial Control Networks, 2012). It
gives priority to these factors rather than giving to the security. These systems depend on the
operators and also requires automated approaches for proper monitoring the general activities of
the system. Various studies have been there to provide a much wider approach which are
sufficient for improving the security features has easily distributed to the system.
IDS have developed an approach that is to be implemented on the SCADA systems and it
was represented in an unsupervised anomaly based detections approach for integrity attacks on
the SCADA systems. It was proposed that a learning that is not a supervised algorithm, would
act best on the SCADA network. the theory has also been tested with the help of data and
information from a real or industrial system. It could be a water plant. There were many pre-
processing techniques which were used as the pre-processing techniques and they were
managing the input so that the improved results can come as an outcome. It also controlled the
noise factors that was within the data sets from the water plants. Then, it also has been proposed
that the data sets through the clustering algorithm was a behavioural analysis technique. It was
concluded that this this type of behavioural approach that represents the promising behaviour and
the ability to accomplish high detection results in the specific field. With the help of fixed width
algorithm, it was easy to achieve the maximum of the detection rate of 90% with a false
negativity of .01%. It is concern with a few factors such as the complexity and time of algorithm
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 39
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

