Networking Project: Comparing OpenDaylight and Floodlight Controllers
VerifiedAdded on 2022/11/14
|53
|13550
|289
Project
AI Summary
This project analyzes Software Defined Network (SDN) controllers, specifically comparing OpenDaylight and Floodlight. The report investigates the architecture, efficiency, and features of these controllers, evaluating their performance based on factors like delay, loss, and network loads. The study utilizes Mininet to simulate network environments and assess Quality of Service (QoS) parameters. The findings indicate that OpenDaylight excels under lighter network loads, while Floodlight's performance improves with increased load, particularly concerning latency and packet loss. The project also reviews existing literature on SDN and controllers, and the report concludes with a discussion of the project's outcomes, including the identification of suitable controllers for various network scenarios. This research aims to provide insights for resolving data sharing challenges through network infrastructure and promoting the automation of network functions to propose cost-effective network solutions.

Running head: NETWORKING PROJECT
Networking Project
Name of the Student
Name of the University
Author’s Note
Networking Project
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKING PROJECT
Abstract
Software Defined Network is considered as a network architecture and controller is one of the
intelligent part of the network. The controllers are of different types such as Floodlight,
OpenDaylight, POX, NOX, Maestro, etc. The performance of the OpenDaylight and Floodlight
controller is evaluated based on the situation it can be applied and given in the report. The
efficiency, architecture and the features of the controllers are evaluated for comparing the
controllers with each other. The two controllers that are popular in the Software Defined
Network architecture is compared based on delay, loss and network loads for choosing the best
controller. The results of the comparison shows that the performance of the OpenDay light is
better than the Flood Light when there is less load on the network but the but the performance of
the Flood light improves with the increase in load in the network based on latency and packet
loss. In the other cases no significant differences are found in Floodlight and Openlight
controllers. The report is developed for resolving the different problems with sharing of large
volume of data using a network infrastructure. An analysis is made on the Software Defined
Network for the configuration of large computer networks and enabling a centralized control on
the network. The layers of the SDN i.e. Application, control and infrastructure is evaluated for
management and operation of the server and managing the request from different users. Different
articles are reviewed for getting the idea about the software defined network and its role in
reducing complexity of the network and discussed in the report. The support of SDN for
automation of the network function is evaluated and a cost effective network solution is proposed
that would support the distributed environment and allow sharing of data between different hosts
located in diverse geographical location. The software defined network can be created easily and
NETWORKING PROJECT
Abstract
Software Defined Network is considered as a network architecture and controller is one of the
intelligent part of the network. The controllers are of different types such as Floodlight,
OpenDaylight, POX, NOX, Maestro, etc. The performance of the OpenDaylight and Floodlight
controller is evaluated based on the situation it can be applied and given in the report. The
efficiency, architecture and the features of the controllers are evaluated for comparing the
controllers with each other. The two controllers that are popular in the Software Defined
Network architecture is compared based on delay, loss and network loads for choosing the best
controller. The results of the comparison shows that the performance of the OpenDay light is
better than the Flood Light when there is less load on the network but the but the performance of
the Flood light improves with the increase in load in the network based on latency and packet
loss. In the other cases no significant differences are found in Floodlight and Openlight
controllers. The report is developed for resolving the different problems with sharing of large
volume of data using a network infrastructure. An analysis is made on the Software Defined
Network for the configuration of large computer networks and enabling a centralized control on
the network. The layers of the SDN i.e. Application, control and infrastructure is evaluated for
management and operation of the server and managing the request from different users. Different
articles are reviewed for getting the idea about the software defined network and its role in
reducing complexity of the network and discussed in the report. The support of SDN for
automation of the network function is evaluated and a cost effective network solution is proposed
that would support the distributed environment and allow sharing of data between different hosts
located in diverse geographical location. The software defined network can be created easily and

2
NETWORKING PROJECT
it can help in creating new possibility for the organization with the standardization of different
activities.
Table of Contents
Introduction......................................................................................................................................3
Literature Review............................................................................................................................6
Project Methodology.....................................................................................................................12
Outcomes.......................................................................................................................................19
Discussion......................................................................................................................................35
Conclusion.....................................................................................................................................41
Reflection.......................................................................................................................................42
References......................................................................................................................................44
NETWORKING PROJECT
it can help in creating new possibility for the organization with the standardization of different
activities.
Table of Contents
Introduction......................................................................................................................................3
Literature Review............................................................................................................................6
Project Methodology.....................................................................................................................12
Outcomes.......................................................................................................................................19
Discussion......................................................................................................................................35
Conclusion.....................................................................................................................................41
Reflection.......................................................................................................................................42
References......................................................................................................................................44
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKING PROJECT
Introduction
There are different problems faced by the users while using the traditional network and
thus the programmable network was introduced such that the problems can be resolved easily
and the network can be evolved to the next level. The software defined network thus created a
revolution for the traditional network design and facilitate control of large device, topologies,
services, policies, traffic paths and APIs of the network. Software defined network is a
technology used for separating the control plane from the data plane of a network and forwarding
the network traffic (Truong, Lee & Ghamri-Doudane, 2015). It is used for enforcing
management based on network hardware and use of policy based management for the network.
The statistically defined network complexity can be reduced with the implementation of SDN
and thus help in automating the network functionality and use simpler provisioning and
managing the resources from different areas of the network. SDN can be used for supporting the
remote access and edge computing and helps in distribution of computing power to remote PCs
and moving the data center (Farhady, Lee & Nakao, 2015). The network can be complex or
dynamic and their management and configuration is a difficult task. The network can consist of
wide range of hardware devices such as firewall, switch, router, Access point, etc. It is the
responsibility of the network operator to configure the network hardware such that high level
network policy can be implemented in the system respond against different events such as
intrusion, load balancing, etc. For the application of the high level network policy in the network
device it is important to distribute them with the configuration. The network developed now a
days does not have any mechanism for automatically responding against different events that can
occur in the network (Baktir, Ozgovde & Ersoy, 2017). The network operators are responsible
for the implementation of complex and sophisticated policy with the combination of low level
NETWORKING PROJECT
Introduction
There are different problems faced by the users while using the traditional network and
thus the programmable network was introduced such that the problems can be resolved easily
and the network can be evolved to the next level. The software defined network thus created a
revolution for the traditional network design and facilitate control of large device, topologies,
services, policies, traffic paths and APIs of the network. Software defined network is a
technology used for separating the control plane from the data plane of a network and forwarding
the network traffic (Truong, Lee & Ghamri-Doudane, 2015). It is used for enforcing
management based on network hardware and use of policy based management for the network.
The statistically defined network complexity can be reduced with the implementation of SDN
and thus help in automating the network functionality and use simpler provisioning and
managing the resources from different areas of the network. SDN can be used for supporting the
remote access and edge computing and helps in distribution of computing power to remote PCs
and moving the data center (Farhady, Lee & Nakao, 2015). The network can be complex or
dynamic and their management and configuration is a difficult task. The network can consist of
wide range of hardware devices such as firewall, switch, router, Access point, etc. It is the
responsibility of the network operator to configure the network hardware such that high level
network policy can be implemented in the system respond against different events such as
intrusion, load balancing, etc. For the application of the high level network policy in the network
device it is important to distribute them with the configuration. The network developed now a
days does not have any mechanism for automatically responding against different events that can
occur in the network (Baktir, Ozgovde & Ersoy, 2017). The network operators are responsible
for the implementation of complex and sophisticated policy with the combination of low level
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORKING PROJECT
configuration for the devices using the CLI environment of the network device. The report
provides an in-depth analysis of the network problems and the technology that can be applied for
eliminating the problems. Configure and different mechanism of management can be applied in
the network for its improvement of the network and enable changes in the network, supporting
the configuration of network and providing centralized control and visibility of the network for
troubleshooting the issues (Cui, Yu & Yan, 2016). The implementation of the technologies help
in application of wide network policy in the network and identify the source of the error in the
network easily. We have created prototype of the software defined network for the demonstration
of its functionality and improve the network management. With the application of the software
defined network the maintenance cost of the network can be reduced and the network can be
secured from the external agents (Blenk et al., 2015). Different research paper on the software
defined network is evaluated for the creation of the report and identify the different areas the
technology can be applied.
The intelligent part of the network is the controller and the data plane works under the
instruction of the controller plane. There are two other components i.e. the southbound and the
northbound interfaces where the southbound interface is used for connecting the data plane
(switches) with the controller and the north bound interface is used for offering APIs to the
services and controlling the network (Wang et al., 2015). Open flow protocol can be
implemented to the southbound interface that helps in remote controlling the routers, access
points and switches. There are other protocols that is developed on the working principle of
OpenFlow protocol for example POX, NOX, OpenDaylight, Floodlight and Beacon. The
selection of the best controller is a complex task for the researcher and the network administrator
(Arslan, Sundaresan & Rangarajan, 2015). There are different existing researches that can be
NETWORKING PROJECT
configuration for the devices using the CLI environment of the network device. The report
provides an in-depth analysis of the network problems and the technology that can be applied for
eliminating the problems. Configure and different mechanism of management can be applied in
the network for its improvement of the network and enable changes in the network, supporting
the configuration of network and providing centralized control and visibility of the network for
troubleshooting the issues (Cui, Yu & Yan, 2016). The implementation of the technologies help
in application of wide network policy in the network and identify the source of the error in the
network easily. We have created prototype of the software defined network for the demonstration
of its functionality and improve the network management. With the application of the software
defined network the maintenance cost of the network can be reduced and the network can be
secured from the external agents (Blenk et al., 2015). Different research paper on the software
defined network is evaluated for the creation of the report and identify the different areas the
technology can be applied.
The intelligent part of the network is the controller and the data plane works under the
instruction of the controller plane. There are two other components i.e. the southbound and the
northbound interfaces where the southbound interface is used for connecting the data plane
(switches) with the controller and the north bound interface is used for offering APIs to the
services and controlling the network (Wang et al., 2015). Open flow protocol can be
implemented to the southbound interface that helps in remote controlling the routers, access
points and switches. There are other protocols that is developed on the working principle of
OpenFlow protocol for example POX, NOX, OpenDaylight, Floodlight and Beacon. The
selection of the best controller is a complex task for the researcher and the network administrator
(Arslan, Sundaresan & Rangarajan, 2015). There are different existing researches that can be

5
NETWORKING PROJECT
used for comparing the architecture of the controllers and its efficiency such as availability and
scalability. The feature parameters are also evaluated based on productivity, supported platform,
interface and language. The paper is created for comparing the protocols such as OpenDaylight
and Floodlight with the application of Mininet in SDN emulator based on QoS parameter such as
loss and delay in the network (Yan et al., 2015). The report is prepared for the comparison of
four OpenFlow network controlling that includes Beacon, Maestro, NOX and Floodlight on the
basis of architecture for a machine that have shared memory and multiple core. The main factors
causing the bottleneck for the system includes support of multiple core, partitioning of the
network including switch, task and packet batching. The design of the architecture contains a
static batching and switch partition that can be applied in Beacon, Floodlight and NOX and
application of adaptive and static queue batching in maestro (Tang et al., 2016). The results
evaluation of the performance displays that the design of the network with packet batching and
static switch partitioning provides the best performance for the controllers for a network having
high throughput. For the application that are sensitive to delay such as VOIP the packet and task
batching designs can be applied. The control messages are sent individually for the improvement
of the latency and performance of the network. The results are evaluated for proposing the
controller that have the best performance compared with the other available controllers (Haque
& Abu-Ghazaleh, 2016). There are other controllers also such as Floodlight and OpenDaylight
are compared with each other. The selection of the controller is a Multi Criteria Decision Making
problem because there are several properties present in the controller that are needed to be
considered for selecting it. For reaching the decision analytical hierarchical process can be
applied for getting prioritization based on pairs and applying integrated consistency mechanism.
The available interface, GUI, virtual switch support, REST API support and productivity
NETWORKING PROJECT
used for comparing the architecture of the controllers and its efficiency such as availability and
scalability. The feature parameters are also evaluated based on productivity, supported platform,
interface and language. The paper is created for comparing the protocols such as OpenDaylight
and Floodlight with the application of Mininet in SDN emulator based on QoS parameter such as
loss and delay in the network (Yan et al., 2015). The report is prepared for the comparison of
four OpenFlow network controlling that includes Beacon, Maestro, NOX and Floodlight on the
basis of architecture for a machine that have shared memory and multiple core. The main factors
causing the bottleneck for the system includes support of multiple core, partitioning of the
network including switch, task and packet batching. The design of the architecture contains a
static batching and switch partition that can be applied in Beacon, Floodlight and NOX and
application of adaptive and static queue batching in maestro (Tang et al., 2016). The results
evaluation of the performance displays that the design of the network with packet batching and
static switch partitioning provides the best performance for the controllers for a network having
high throughput. For the application that are sensitive to delay such as VOIP the packet and task
batching designs can be applied. The control messages are sent individually for the improvement
of the latency and performance of the network. The results are evaluated for proposing the
controller that have the best performance compared with the other available controllers (Haque
& Abu-Ghazaleh, 2016). There are other controllers also such as Floodlight and OpenDaylight
are compared with each other. The selection of the controller is a Multi Criteria Decision Making
problem because there are several properties present in the controller that are needed to be
considered for selecting it. For reaching the decision analytical hierarchical process can be
applied for getting prioritization based on pairs and applying integrated consistency mechanism.
The available interface, GUI, virtual switch support, REST API support and productivity
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKING PROJECT
condition is used for the comparison of OpenDaylight and Floodlight (Akyildiz, Wang & Lin,
2015). From the result of the comparison it has been found that for the priority vector case Ryu
achieves the best value and OpenDaylight, Floodlight, Pox and Trema has the result next to Ryu
(Yan & Yu, 2015). The floodlight and the OpenDaylight have the clos result and can be used as
replacement of Ryu.
Literature Review
There are many works of different authors who have compared the SDN controllers and
used Floodlight ad OpenDaylight for the comparison with achieving similar result. The
controllers are applied in different fields such as cloud computing, multimedia, QoS for
measuring their performance. The performance of the controllers are analyzed based on the
parameters of QoS with the use of Mininet (Wood et al., 2015). The OpenDaylight and
Floodlight is reviewed in this section providing a short introduction of both the controllers.
The floodlight controller is based on Beacon controller developed from Stanford
University and works with the combination of virtual and physical OpenFlow switch. The
controller have some unique feature like apache license, modular, asynchronous framework for
application, event driven, java based and utilization of synchronized lock. The management of
topology is important for the controller and can be applied for the discovery of openflow and non
openflow endpoint. The device management is also important and it includes tracking of IP and
MAC address, computation of best path, developing web access infrastructure, storage of
counter, big data and quantum for interoperating the different agents for providing support to
OpeFlow (Rawat & Reddy, 2016). The components of the Floodlight are loadable services and
the service provider acts as core module for handling the input and output that are received and
send to switch. The module can also be used for translating OpenFlow message in floodlight
NETWORKING PROJECT
condition is used for the comparison of OpenDaylight and Floodlight (Akyildiz, Wang & Lin,
2015). From the result of the comparison it has been found that for the priority vector case Ryu
achieves the best value and OpenDaylight, Floodlight, Pox and Trema has the result next to Ryu
(Yan & Yu, 2015). The floodlight and the OpenDaylight have the clos result and can be used as
replacement of Ryu.
Literature Review
There are many works of different authors who have compared the SDN controllers and
used Floodlight ad OpenDaylight for the comparison with achieving similar result. The
controllers are applied in different fields such as cloud computing, multimedia, QoS for
measuring their performance. The performance of the controllers are analyzed based on the
parameters of QoS with the use of Mininet (Wood et al., 2015). The OpenDaylight and
Floodlight is reviewed in this section providing a short introduction of both the controllers.
The floodlight controller is based on Beacon controller developed from Stanford
University and works with the combination of virtual and physical OpenFlow switch. The
controller have some unique feature like apache license, modular, asynchronous framework for
application, event driven, java based and utilization of synchronized lock. The management of
topology is important for the controller and can be applied for the discovery of openflow and non
openflow endpoint. The device management is also important and it includes tracking of IP and
MAC address, computation of best path, developing web access infrastructure, storage of
counter, big data and quantum for interoperating the different agents for providing support to
OpeFlow (Rawat & Reddy, 2016). The components of the Floodlight are loadable services and
the service provider acts as core module for handling the input and output that are received and
send to switch. The module can also be used for translating OpenFlow message in floodlight
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORKING PROJECT
event. In the controller there are REST APIs that can be used to get and set the state of
controller, notification system of an event, pass that emits Java event (Hakiri et al., 2015). There
are also different sample of application containing learning hub, switch application and pusher,
load balancing and firewall.
The OpenDaylight project was formed in the year 2013 by the Linux foundation and the
project is concerned with creation of a de facto northbound API standard for the management of
the south bound protocols for example OpenFlow, 12RS, NETCONF and its programming. The
controller have different features such as Java based, support multiple protocol and plugin and
modularity. It also has the support of programming of OSGI and REST bidirectional protocol
that provides the support of running different application in the same space of address in the
controller (Zhou et al., 2016). The requests from internal and external sources are mapped using
the service abstraction layer for providing plugin for the southbound and building upon the basic
level of service abstraction for getting higher service levels. The capability of the plugin is
important for providing service to the features. There are other built in services that are offered
by OpenDaylight such as discovery and abstraction of topology, NETCONF, 12RS, OpenFlow
(Wickboldt et al., 2015). The following table is used for comparing each of the two protocols.
NETWORKING PROJECT
event. In the controller there are REST APIs that can be used to get and set the state of
controller, notification system of an event, pass that emits Java event (Hakiri et al., 2015). There
are also different sample of application containing learning hub, switch application and pusher,
load balancing and firewall.
The OpenDaylight project was formed in the year 2013 by the Linux foundation and the
project is concerned with creation of a de facto northbound API standard for the management of
the south bound protocols for example OpenFlow, 12RS, NETCONF and its programming. The
controller have different features such as Java based, support multiple protocol and plugin and
modularity. It also has the support of programming of OSGI and REST bidirectional protocol
that provides the support of running different application in the same space of address in the
controller (Zhou et al., 2016). The requests from internal and external sources are mapped using
the service abstraction layer for providing plugin for the southbound and building upon the basic
level of service abstraction for getting higher service levels. The capability of the plugin is
important for providing service to the features. There are other built in services that are offered
by OpenDaylight such as discovery and abstraction of topology, NETCONF, 12RS, OpenFlow
(Wickboldt et al., 2015). The following table is used for comparing each of the two protocols.

8
NETWORKING PROJECT
With the use of Mininet a virtual network is created and Software define network is
implemented in it. The Mininet team uses it for running the controllers, hosts and switches in the
virtual environment for a single computer. The default network created using Mininet have a
OpenFlow switch and it connects with an OpenFlow controller and two hosts (Bertaux et al.,
2015). The hosts connected in the Mininet would be able to run commands of different file
system in Linux, e.g. ipref command can be used for getting the details of bandwidth
consumption between server and client, topo command can be used for creating topologies with
python API and creating customized virtual network. There are different common predefined
network topologies created in Mininet and can be termed as single topology, linear topology and
tree topology (Ali et al., 2015). In the single topology three hosts named H1, H2 and H3 are
connected with a switch S1, in the linear topology the hosts are connected with separate switch
S1, S2 and S3 and each of the switch are connected using serial connection. In the tree topology
a switch S1 is connected with two switch S2 and S5. The switch S2 is connected with S3 and S4
NETWORKING PROJECT
With the use of Mininet a virtual network is created and Software define network is
implemented in it. The Mininet team uses it for running the controllers, hosts and switches in the
virtual environment for a single computer. The default network created using Mininet have a
OpenFlow switch and it connects with an OpenFlow controller and two hosts (Bertaux et al.,
2015). The hosts connected in the Mininet would be able to run commands of different file
system in Linux, e.g. ipref command can be used for getting the details of bandwidth
consumption between server and client, topo command can be used for creating topologies with
python API and creating customized virtual network. There are different common predefined
network topologies created in Mininet and can be termed as single topology, linear topology and
tree topology (Ali et al., 2015). In the single topology three hosts named H1, H2 and H3 are
connected with a switch S1, in the linear topology the hosts are connected with separate switch
S1, S2 and S3 and each of the switch are connected using serial connection. In the tree topology
a switch S1 is connected with two switch S2 and S5. The switch S2 is connected with S3 and S4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORKING PROJECT
in parallel and the host H1 and H2 are connected with S3, H3 and H4 is connected to switch S4.
The switch S6 and S7 is connected to switch S5 and H5 and H6 is connected with S6 and host
H7 and H8 is connected with switch S7.
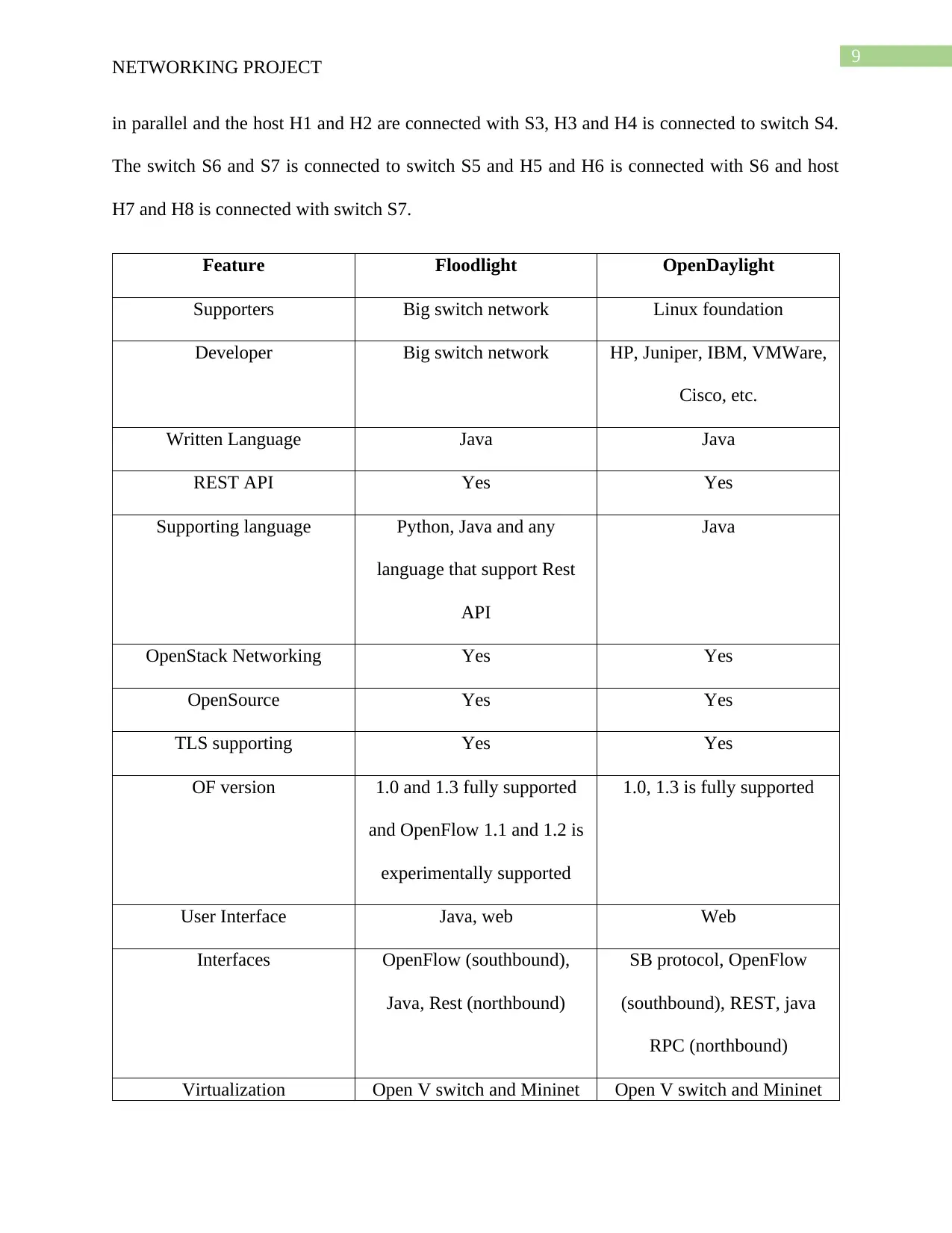
Feature Floodlight OpenDaylight
Supporters Big switch network Linux foundation
Developer Big switch network HP, Juniper, IBM, VMWare,
Cisco, etc.
Written Language Java Java
REST API Yes Yes
Supporting language Python, Java and any
language that support Rest
API
Java
OpenStack Networking Yes Yes
OpenSource Yes Yes
TLS supporting Yes Yes
OF version 1.0 and 1.3 fully supported
and OpenFlow 1.1 and 1.2 is
experimentally supported
1.0, 1.3 is fully supported
User Interface Java, web Web
Interfaces OpenFlow (southbound),
Java, Rest (northbound)
SB protocol, OpenFlow
(southbound), REST, java
RPC (northbound)
Virtualization Open V switch and Mininet Open V switch and Mininet
NETWORKING PROJECT
in parallel and the host H1 and H2 are connected with S3, H3 and H4 is connected to switch S4.
The switch S6 and S7 is connected to switch S5 and H5 and H6 is connected with S6 and host
H7 and H8 is connected with switch S7.
Feature Floodlight OpenDaylight
Supporters Big switch network Linux foundation
Developer Big switch network HP, Juniper, IBM, VMWare,
Cisco, etc.
Written Language Java Java
REST API Yes Yes
Supporting language Python, Java and any
language that support Rest
API
Java
OpenStack Networking Yes Yes
OpenSource Yes Yes
TLS supporting Yes Yes
OF version 1.0 and 1.3 fully supported
and OpenFlow 1.1 and 1.2 is
experimentally supported
1.0, 1.3 is fully supported
User Interface Java, web Web
Interfaces OpenFlow (southbound),
Java, Rest (northbound)
SB protocol, OpenFlow
(southbound), REST, java
RPC (northbound)
Virtualization Open V switch and Mininet Open V switch and Mininet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORKING PROJECT
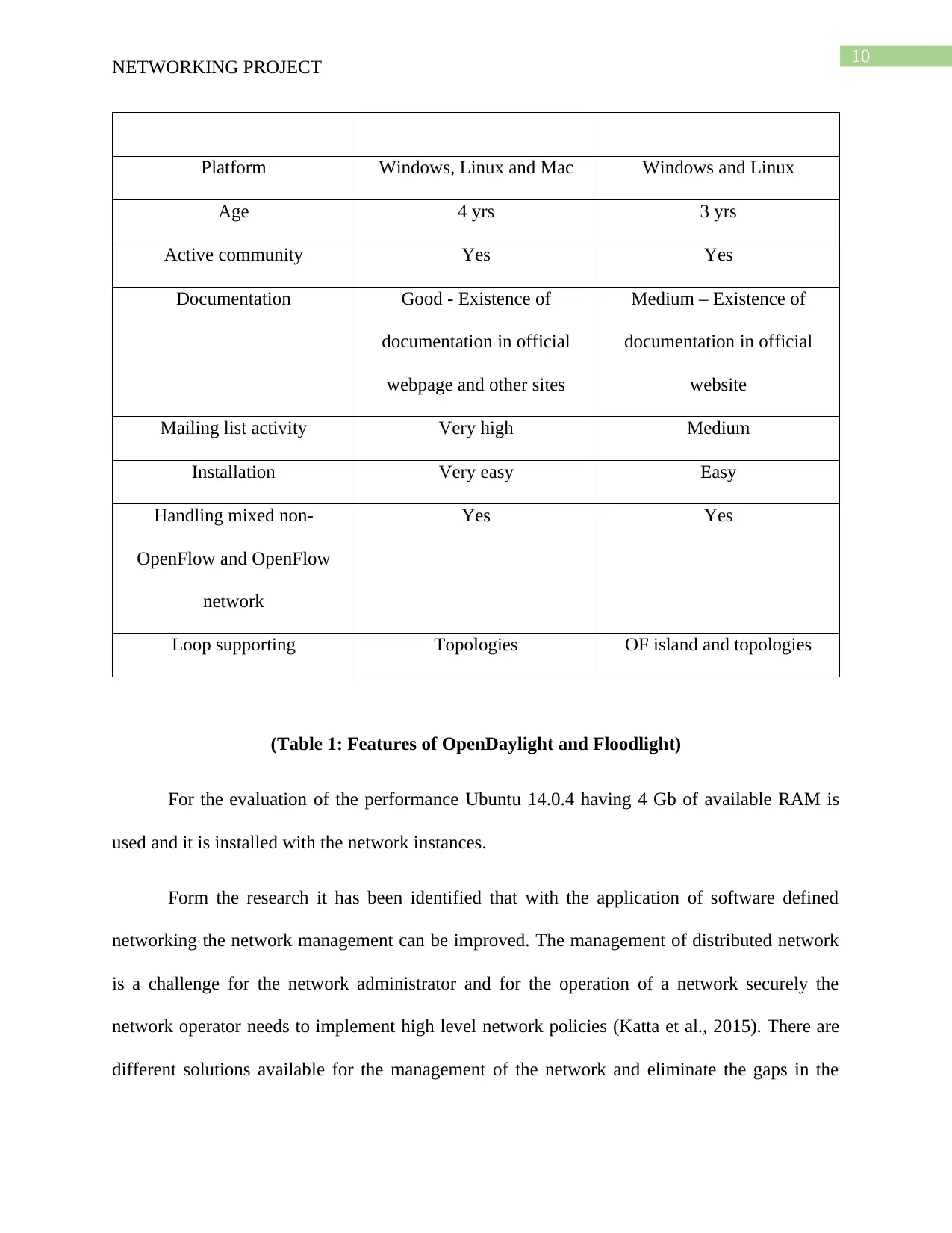
Platform Windows, Linux and Mac Windows and Linux
Age 4 yrs 3 yrs
Active community Yes Yes
Documentation Good - Existence of
documentation in official
webpage and other sites
Medium – Existence of
documentation in official
website
Mailing list activity Very high Medium
Installation Very easy Easy
Handling mixed non-
OpenFlow and OpenFlow
network
Yes Yes
Loop supporting Topologies OF island and topologies
(Table 1: Features of OpenDaylight and Floodlight)
For the evaluation of the performance Ubuntu 14.0.4 having 4 Gb of available RAM is
used and it is installed with the network instances.
Form the research it has been identified that with the application of software defined
networking the network management can be improved. The management of distributed network
is a challenge for the network administrator and for the operation of a network securely the
network operator needs to implement high level network policies (Katta et al., 2015). There are
different solutions available for the management of the network and eliminate the gaps in the
NETWORKING PROJECT
Platform Windows, Linux and Mac Windows and Linux
Age 4 yrs 3 yrs
Active community Yes Yes
Documentation Good - Existence of
documentation in official
webpage and other sites
Medium – Existence of
documentation in official
website
Mailing list activity Very high Medium
Installation Very easy Easy
Handling mixed non-
OpenFlow and OpenFlow
network
Yes Yes
Loop supporting Topologies OF island and topologies
(Table 1: Features of OpenDaylight and Floodlight)
For the evaluation of the performance Ubuntu 14.0.4 having 4 Gb of available RAM is
used and it is installed with the network instances.
Form the research it has been identified that with the application of software defined
networking the network management can be improved. The management of distributed network
is a challenge for the network administrator and for the operation of a network securely the
network operator needs to implement high level network policies (Katta et al., 2015). There are
different solutions available for the management of the network and eliminate the gaps in the

11
NETWORKING PROJECT
network. The application of SDN helps in introduction of new possibility for the configuration
and management of network. Different articles are reviewed for identification of the problems in
network management based on frequently changing the state and condition of the network,
supporting the network hardware device configuration and getting high level visibility of the
network for troubleshooting and diagnosing the network problem (Duan & Wang, 2015). As a
network controller Procera can be used since it follows the rules of software defined networking
for forwarding the data traffic and updating the low level network routing tables based on the
network policy. The network policy is translated by the network controller such that actual
packet forwarding can be done to the different network devices. The controller helps in
establishment of a connection with the switch capable of OpenFlow protocol with the application
of OpenFlow protocol (Karakus & Durresi, 2017). The network controller helps in insertion,
deletion and modification of the packet forwarding rules in the network switch with the help of
the connection. The packet in and switch join event is used by the controller for taking the packet
forwarding decision. Procera is used as a control framework of the network for expressing the
network policies and reacting against different network policies with the help of functional
programming languages. The Procera can act as an intermediate bond between the network
configurations and the network policies. For expressing the network policies that are event
driven a control domain is set is offered by procera that helps in setting certain conditions and
assigning appropriate actions to forward the packets based on the conditions (Dong et al., 2015).
The application of additional control domain can increase the flexibility of the network operator
and development of a reactive policy for the network. The network operator can also integrate
the control domains such that the quality of the network policy can be improved and automate
some of the operations of the network eliminating the need to rely on event triggered scripts that
NETWORKING PROJECT
network. The application of SDN helps in introduction of new possibility for the configuration
and management of network. Different articles are reviewed for identification of the problems in
network management based on frequently changing the state and condition of the network,
supporting the network hardware device configuration and getting high level visibility of the
network for troubleshooting and diagnosing the network problem (Duan & Wang, 2015). As a
network controller Procera can be used since it follows the rules of software defined networking
for forwarding the data traffic and updating the low level network routing tables based on the
network policy. The network policy is translated by the network controller such that actual
packet forwarding can be done to the different network devices. The controller helps in
establishment of a connection with the switch capable of OpenFlow protocol with the application
of OpenFlow protocol (Karakus & Durresi, 2017). The network controller helps in insertion,
deletion and modification of the packet forwarding rules in the network switch with the help of
the connection. The packet in and switch join event is used by the controller for taking the packet
forwarding decision. Procera is used as a control framework of the network for expressing the
network policies and reacting against different network policies with the help of functional
programming languages. The Procera can act as an intermediate bond between the network
configurations and the network policies. For expressing the network policies that are event
driven a control domain is set is offered by procera that helps in setting certain conditions and
assigning appropriate actions to forward the packets based on the conditions (Dong et al., 2015).
The application of additional control domain can increase the flexibility of the network operator
and development of a reactive policy for the network. The network operator can also integrate
the control domains such that the quality of the network policy can be improved and automate
some of the operations of the network eliminating the need to rely on event triggered scripts that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 53
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





