Network Design Report: Seagull International Network Setup and Design
VerifiedAdded on 2022/11/16
|9
|1245
|317
Report
AI Summary
This report presents a comprehensive network design solution for Seagull International, a growing business with 50 employees across two locations, planning to move into a new office in Sydney. The report begins with a network diagram outlining the office setup, detailing the placement of workstations, routers, and servers. It then discusses the selection of operating systems, recommending Windows 10 for employees and Microsoft Server 2016 for network management. The report emphasizes the importance of secure operating systems, especially for sales employees, and suggests the use of Virtual Private Networks (VPNs) for remote access. Furthermore, it explores the implementation of leased lines and IPBX for efficient data transfer and telephone services, along with the integration of Wi-Fi security measures, including WEP and WPA. The report also covers the use of Class C IP addresses to manage the network, dividing it into subnets for improved security and efficient resource allocation. The report provides details on IP address ranges and subnet masks for different departments, ensuring a secure and organized network infrastructure.

Running Head: Network Design 0
Network Design
Report
Student name
9/16/2019
Network Design
Report
Student name
9/16/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Design 1
Table of Contents
Topic-1.............................................................................................................................................1
Topic-2.............................................................................................................................................1
Topic-3.............................................................................................................................................1
Topic-4.............................................................................................................................................1
Topic-5.............................................................................................................................................1
Topic-6.............................................................................................................................................1
Table of Contents
Topic-1.............................................................................................................................................1
Topic-2.............................................................................................................................................1
Topic-3.............................................................................................................................................1
Topic-4.............................................................................................................................................1
Topic-5.............................................................................................................................................1
Topic-6.............................................................................................................................................1
Network Design 2
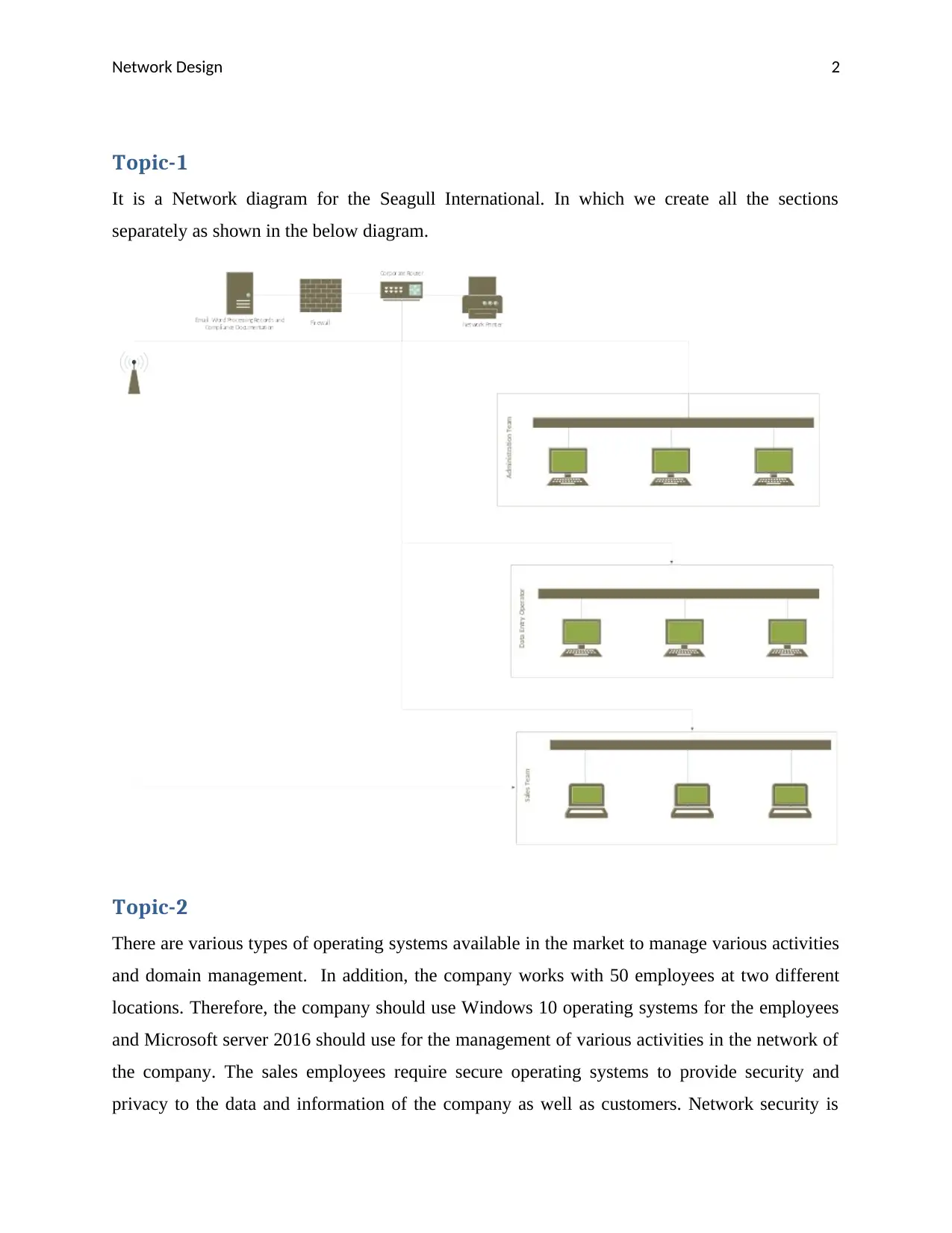
Topic-1
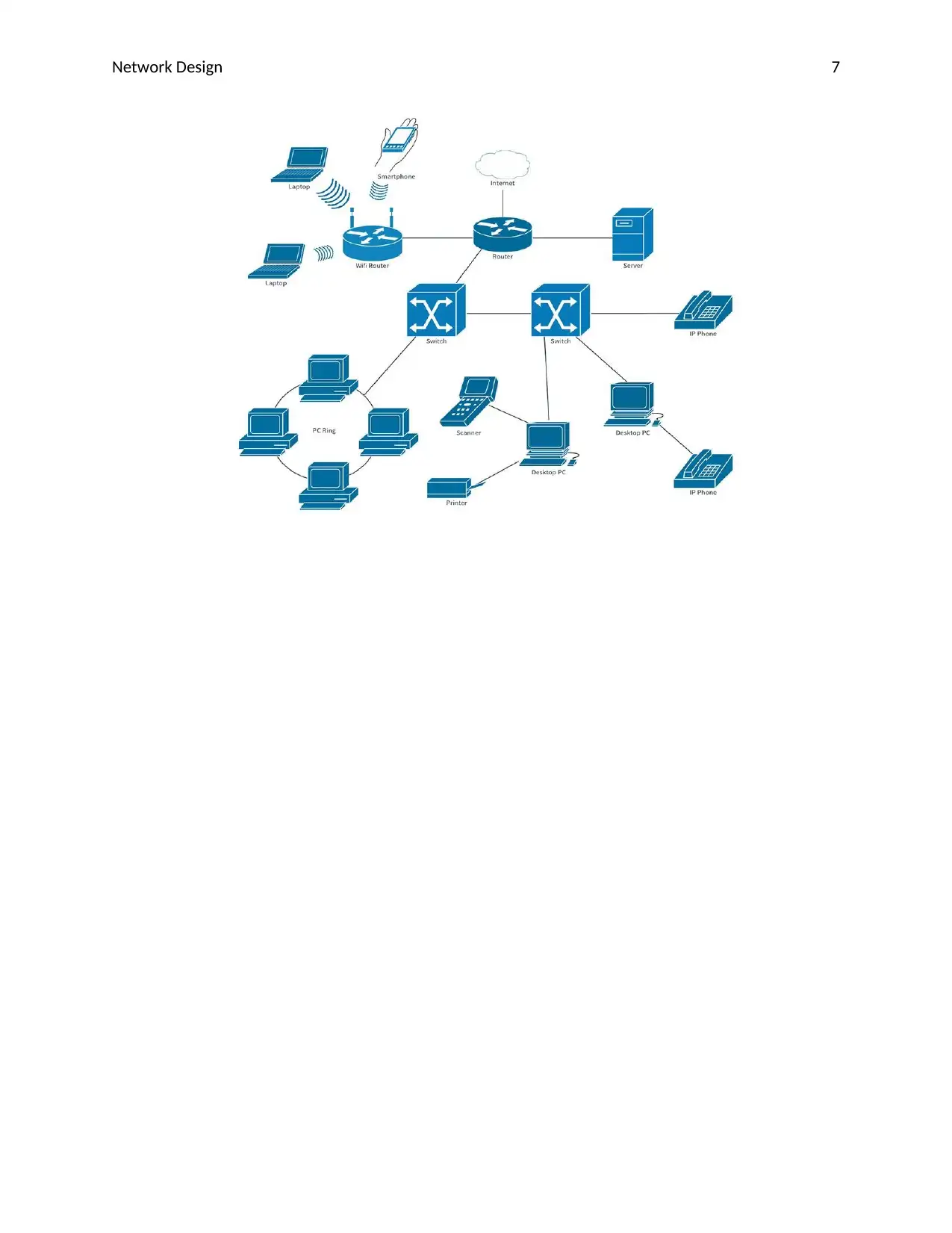
It is a Network diagram for the Seagull International. In which we create all the sections
separately as shown in the below diagram.
Topic-2
There are various types of operating systems available in the market to manage various activities
and domain management. In addition, the company works with 50 employees at two different
locations. Therefore, the company should use Windows 10 operating systems for the employees
and Microsoft server 2016 should use for the management of various activities in the network of
the company. The sales employees require secure operating systems to provide security and
privacy to the data and information of the company as well as customers. Network security is
Topic-1
It is a Network diagram for the Seagull International. In which we create all the sections
separately as shown in the below diagram.
Topic-2
There are various types of operating systems available in the market to manage various activities
and domain management. In addition, the company works with 50 employees at two different
locations. Therefore, the company should use Windows 10 operating systems for the employees
and Microsoft server 2016 should use for the management of various activities in the network of
the company. The sales employees require secure operating systems to provide security and
privacy to the data and information of the company as well as customers. Network security is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Design 3
good in the Windows 10 operating systems. A secure network is necessary for data and
information security (Tanenbaum, 2014).
Moreover, Windows 10 is upgraded systems, which provide security to the data of company and
it will work for long-term as well. It needs fewer maintenance costs as well as less security and
privacy issues.
Topic-3
The sales team members can use Virtual Private Network (VPN) of the company to access the
network of the company from their laptops from another location. The company can use team
viewer and other remote application software to manage all the things in a proper manner. It can
be possible using server as well. The company must provide a secure connection to remotely
access the sale team computer systems. VPN provides a secure connection the authorized
persons to access the different services of their organisations, such as network access, database
access, and many others. VPN is the best solution for remote access services in an organisation
(Sunshine, 2013). A network must be secure from different types of cyber-attacks, such as
phishing, social engineering, and many others (Cowley, 2012).
Moreover, the sales teams can access the network from both points, one is VPN and another is a
Wi-Fi connection. They must require Wi-Fi passwords to access a secure connection. It will
manage security of the network.
Topic-4
The company must use a leased line of more than 1Gbps connection to provide fast access to
data and information from various computer systems. IPBX can be used for the telephonic
service for the data entry team and administrative staff members. The company can also use
broadband and ADSL connection to manage their internet and telephone services at different
locations. In addition, computer network is the best way to provide various services (Mitchell,
2018). Internet service providers provide secure connection to the company to manage their other
services in a proper manner (Forouzan, 2007).
good in the Windows 10 operating systems. A secure network is necessary for data and
information security (Tanenbaum, 2014).
Moreover, Windows 10 is upgraded systems, which provide security to the data of company and
it will work for long-term as well. It needs fewer maintenance costs as well as less security and
privacy issues.
Topic-3
The sales team members can use Virtual Private Network (VPN) of the company to access the
network of the company from their laptops from another location. The company can use team
viewer and other remote application software to manage all the things in a proper manner. It can
be possible using server as well. The company must provide a secure connection to remotely
access the sale team computer systems. VPN provides a secure connection the authorized
persons to access the different services of their organisations, such as network access, database
access, and many others. VPN is the best solution for remote access services in an organisation
(Sunshine, 2013). A network must be secure from different types of cyber-attacks, such as
phishing, social engineering, and many others (Cowley, 2012).
Moreover, the sales teams can access the network from both points, one is VPN and another is a
Wi-Fi connection. They must require Wi-Fi passwords to access a secure connection. It will
manage security of the network.
Topic-4
The company must use a leased line of more than 1Gbps connection to provide fast access to
data and information from various computer systems. IPBX can be used for the telephonic
service for the data entry team and administrative staff members. The company can also use
broadband and ADSL connection to manage their internet and telephone services at different
locations. In addition, computer network is the best way to provide various services (Mitchell,
2018). Internet service providers provide secure connection to the company to manage their other
services in a proper manner (Forouzan, 2007).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Design 4
Moreover, the ADSL connection provides telephone connection to manage internal and external
phone calls. It reduces cost of overall connection as well.
Topic-5
Wireless LAN security is crucial, as the Sales Team will use Wi-Fi when they will be in the
office. Provide appropriate Network Security solutions for wireless LAN of this company. There
are various techniques to secure the Wi-Fi connection from servers and routers. There are
cryptography and authentication techniques available in the server as well as in Wi-Fi routers,
which can restrict the unauthorized access of network and data. Wi-Fi connection requires more
security as outsides access the network, which can be harmful to the company’s data and
information (Kenneth C. Mansfield & Antonakos, 2009). Moreover, network security is handled
by firewalls in an easy way (Gapiński, 2014). However, IP addressing will provide more
security to the network. Therefore, no one can access the network of the company (Blanchet ,
2010).
Wi-Fi connection is available for the guest and sales team only. Therefore, the company can take
competitive advantage of this service in the market. it will improve customer satisfaction. In
addition, Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA) can be used for
the security of the network.
Topic-6
We can take class C IP addresses to manage the whole network, as we have three departments,
which are data entry, administrative, and sales department. Therefore, we require three subnets to
divide all the departments to improve the security of the network.
In addition, there are many benefits to class C addressing. The company manages up to 62-
computer system in a subnet, company has 18, 22, and 12 members in admin, sales and data
entry office respectively.
Moreover, the company can use proper security in different sub-networks using advanced
concepts of networking. In addition, the company can provide high level of security to the
information assets of the company.
Moreover, the ADSL connection provides telephone connection to manage internal and external
phone calls. It reduces cost of overall connection as well.
Topic-5
Wireless LAN security is crucial, as the Sales Team will use Wi-Fi when they will be in the
office. Provide appropriate Network Security solutions for wireless LAN of this company. There
are various techniques to secure the Wi-Fi connection from servers and routers. There are
cryptography and authentication techniques available in the server as well as in Wi-Fi routers,
which can restrict the unauthorized access of network and data. Wi-Fi connection requires more
security as outsides access the network, which can be harmful to the company’s data and
information (Kenneth C. Mansfield & Antonakos, 2009). Moreover, network security is handled
by firewalls in an easy way (Gapiński, 2014). However, IP addressing will provide more
security to the network. Therefore, no one can access the network of the company (Blanchet ,
2010).
Wi-Fi connection is available for the guest and sales team only. Therefore, the company can take
competitive advantage of this service in the market. it will improve customer satisfaction. In
addition, Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA) can be used for
the security of the network.
Topic-6
We can take class C IP addresses to manage the whole network, as we have three departments,
which are data entry, administrative, and sales department. Therefore, we require three subnets to
divide all the departments to improve the security of the network.
In addition, there are many benefits to class C addressing. The company manages up to 62-
computer system in a subnet, company has 18, 22, and 12 members in admin, sales and data
entry office respectively.
Moreover, the company can use proper security in different sub-networks using advanced
concepts of networking. In addition, the company can provide high level of security to the
information assets of the company.
Network Design 5
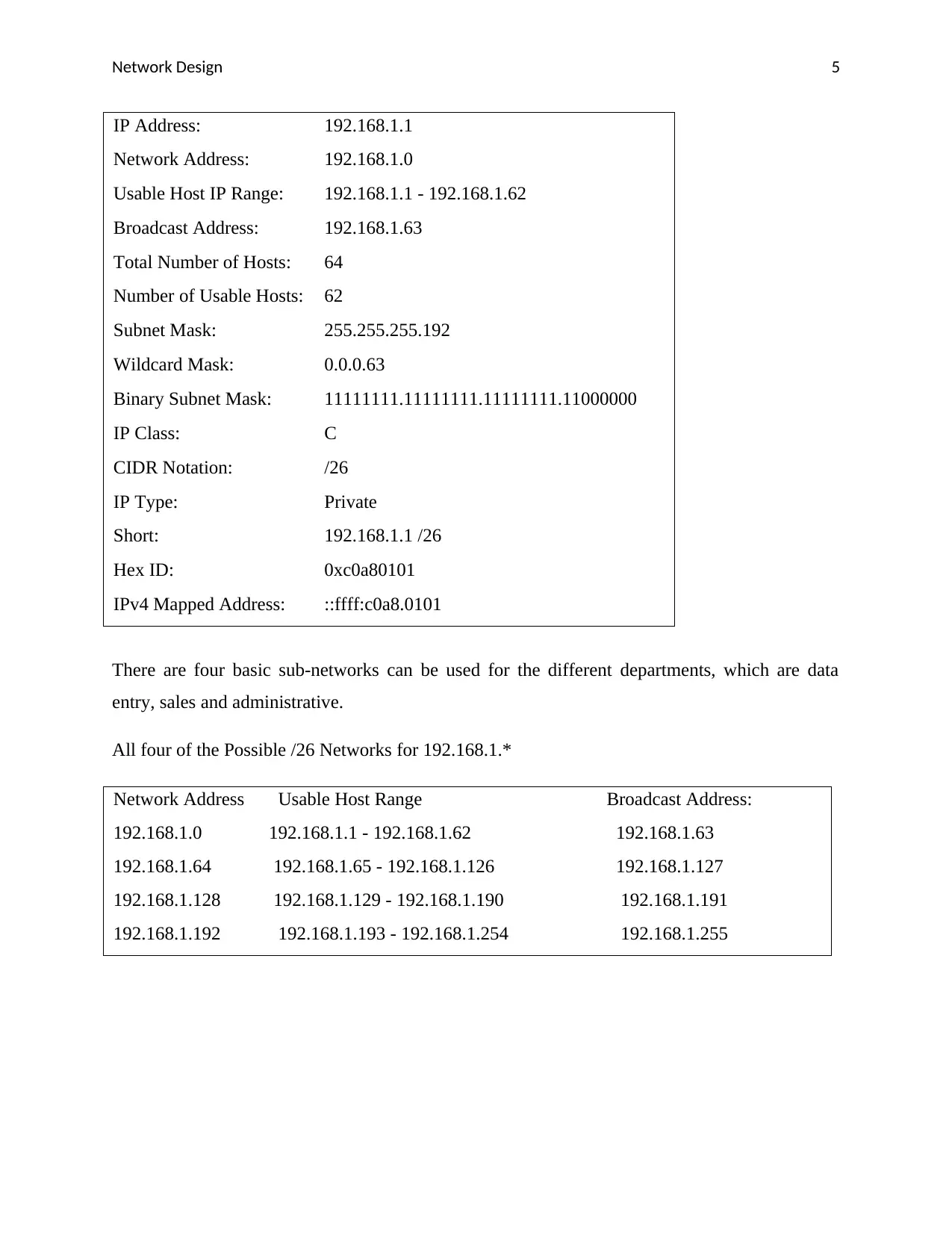
IP Address: 192.168.1.1
Network Address: 192.168.1.0
Usable Host IP Range: 192.168.1.1 - 192.168.1.62
Broadcast Address: 192.168.1.63
Total Number of Hosts: 64
Number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Short: 192.168.1.1 /26
Hex ID: 0xc0a80101
IPv4 Mapped Address: ::ffff:c0a8.0101
There are four basic sub-networks can be used for the different departments, which are data
entry, sales and administrative.
All four of the Possible /26 Networks for 192.168.1.*
Network Address Usable Host Range Broadcast Address:
192.168.1.0 192.168.1.1 - 192.168.1.62 192.168.1.63
192.168.1.64 192.168.1.65 - 192.168.1.126 192.168.1.127
192.168.1.128 192.168.1.129 - 192.168.1.190 192.168.1.191
192.168.1.192 192.168.1.193 - 192.168.1.254 192.168.1.255
IP Address: 192.168.1.1
Network Address: 192.168.1.0
Usable Host IP Range: 192.168.1.1 - 192.168.1.62
Broadcast Address: 192.168.1.63
Total Number of Hosts: 64
Number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Short: 192.168.1.1 /26
Hex ID: 0xc0a80101
IPv4 Mapped Address: ::ffff:c0a8.0101
There are four basic sub-networks can be used for the different departments, which are data
entry, sales and administrative.
All four of the Possible /26 Networks for 192.168.1.*
Network Address Usable Host Range Broadcast Address:
192.168.1.0 192.168.1.1 - 192.168.1.62 192.168.1.63
192.168.1.64 192.168.1.65 - 192.168.1.126 192.168.1.127
192.168.1.128 192.168.1.129 - 192.168.1.190 192.168.1.191
192.168.1.192 192.168.1.193 - 192.168.1.254 192.168.1.255
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Design 6
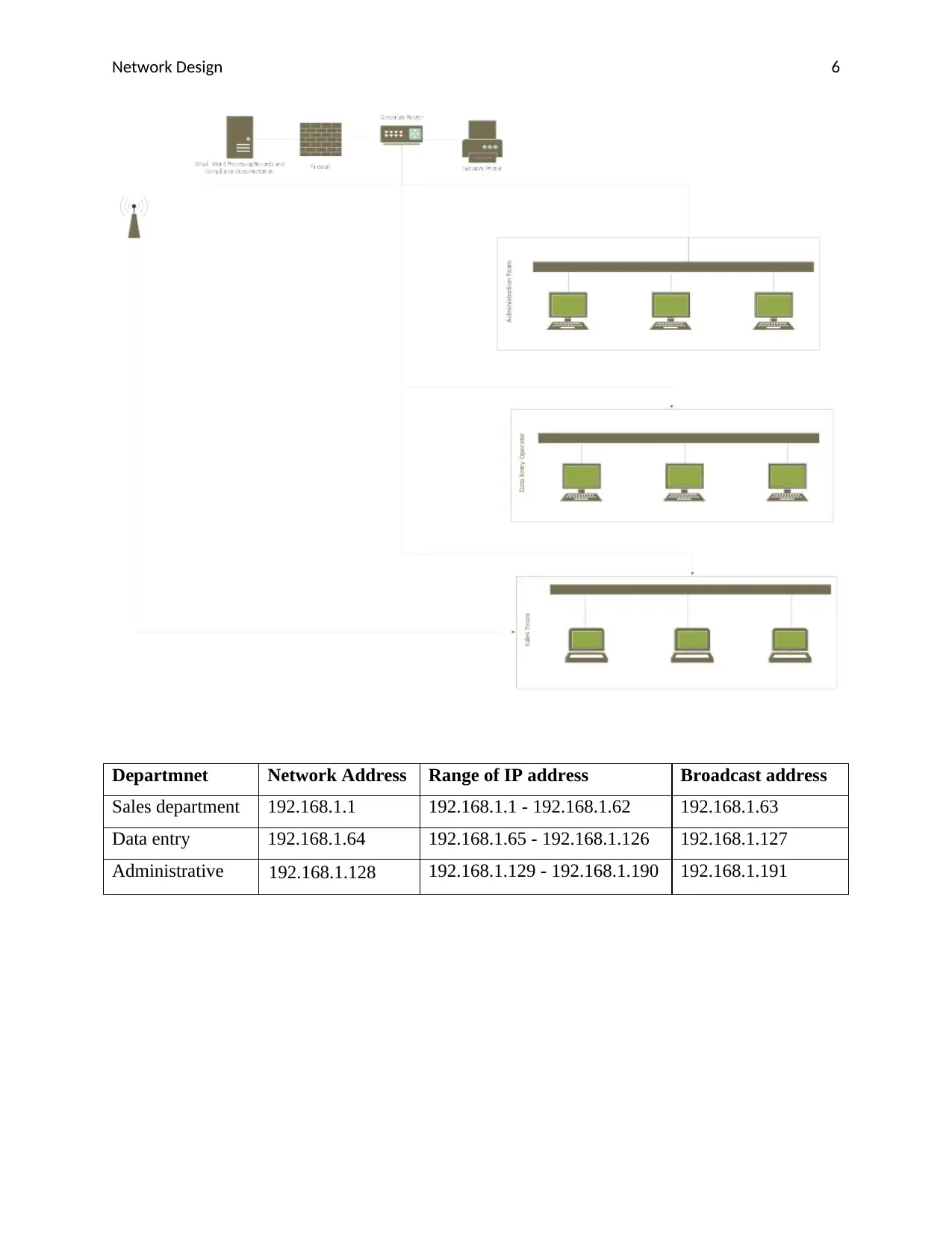
Departmnet Network Address Range of IP address Broadcast address
Sales department 192.168.1.1 192.168.1.1 - 192.168.1.62 192.168.1.63
Data entry 192.168.1.64 192.168.1.65 - 192.168.1.126 192.168.1.127
Administrative 192.168.1.128 192.168.1.129 - 192.168.1.190 192.168.1.191
Departmnet Network Address Range of IP address Broadcast address
Sales department 192.168.1.1 192.168.1.1 - 192.168.1.62 192.168.1.63
Data entry 192.168.1.64 192.168.1.65 - 192.168.1.126 192.168.1.127
Administrative 192.168.1.128 192.168.1.129 - 192.168.1.190 192.168.1.191
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Design 7

Network Design 8
References
Blanchet , M., 2010. IP network node and middleware for establishing connectivity to both the
IPv4 and IPv6 networks.. Washington, Patent No. 7,657,642.
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Gapiński, A., 2014. Strategies for Computer Networks Security. Kwartalnik Nauk o
Przedsiębiorstwie, Volume 3, pp. 59-65.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
Mitchell, B., 2018. What Is Computer Networking?. [Online]
Available at: https://www.lifewire.com/what-is-computer-networking-816249
[Accessed 16 January 2019].
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
References
Blanchet , M., 2010. IP network node and middleware for establishing connectivity to both the
IPv4 and IPv6 networks.. Washington, Patent No. 7,657,642.
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Gapiński, A., 2014. Strategies for Computer Networks Security. Kwartalnik Nauk o
Przedsiębiorstwie, Volume 3, pp. 59-65.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
Mitchell, B., 2018. What Is Computer Networking?. [Online]
Available at: https://www.lifewire.com/what-is-computer-networking-816249
[Accessed 16 January 2019].
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




