SEC Risk Assessment & Incident Response Plan Based on NIST SP 800-61
VerifiedAdded on 2023/06/10
|21
|3465
|363
Report
AI Summary
This report presents a business risk assessment and incident response plan, focusing on the Securities and Exchange Commission (SEC). It identifies hazard categories (purposeful threats, unintentional errors, and environmental disruptions) and uses the SEC's 2012 FISMA assessment as a case study. The assessment evaluates progressive monitoring management, configuration, access management, risk management, safety training, and contingency planning. Key findings include the need for improved continuous monitoring, baseline configurations, and a formal project plan for Personal Identity Verification. The report includes an incident response paper developed using NIST’s SP 800-61, defining roles, training, plan testing, incident notification, reporting/tracking, and procedures for addressing specific security risks like hacking.

BUSINESS RISK ASSEMENT
Name
Subject:
Date of Submission
1 | P a g e
Name
Subject:
Date of Submission
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Hazard Categories.......................................................................................................................................3
Evaluation Criteria.......................................................................................................................................4
Outcomes....................................................................................................................................................4
Risk level......................................................................................................................................................6
Recommended corrective actions...............................................................................................................7
INCIDENT RESPONSE PAPER........................................................................................................................7
Risk: Hacking:...........................................................................................................................................8
Risk assessment tool................................................................................................................................8
References...................................................................................................................................................9
2 | P a g e
Introduction.................................................................................................................................................3
Hazard Categories.......................................................................................................................................3
Evaluation Criteria.......................................................................................................................................4
Outcomes....................................................................................................................................................4
Risk level......................................................................................................................................................6
Recommended corrective actions...............................................................................................................7
INCIDENT RESPONSE PAPER........................................................................................................................7
Risk: Hacking:...........................................................................................................................................8
Risk assessment tool................................................................................................................................8
References...................................................................................................................................................9
2 | P a g e
Introduction
Risks are inevitable parts of any business organization in its operations and daily business
activities, this therefore creates a need of assessing the risk in terms of its impacts to the
profitability and performance of the respective business organization.
Conferring to Ready.gov, peril valuations spot prospective problems, however a business impact
analysis ascertains how these problems might affect a actual business. Since these two tasks go
hand-in-hand, it is useful to pronounce them together.
Hazard Categories.
Threat Origination
Category
Type Identifier
Threats launched purposefully P
Threats created by unintentional human or
machine errors U
Threats caused by environmental agents or
disruptions E
From the above table, the hazard categories are shown given identifiers each, Threats denoted by
P are malicious which are purposefully launched by ill-intended individuals.
Threats denoted by U are those that could be termed as miscelenoiuos having been launched
unintended by human or machine errors in the event of duty delivery.
The E threats are also not intended for but are as a result of natural disasters which cannot be
possibly avoided but it is wise to be included in the business plans during financing the business
operations.
3 | P a g e
Risks are inevitable parts of any business organization in its operations and daily business
activities, this therefore creates a need of assessing the risk in terms of its impacts to the
profitability and performance of the respective business organization.
Conferring to Ready.gov, peril valuations spot prospective problems, however a business impact
analysis ascertains how these problems might affect a actual business. Since these two tasks go
hand-in-hand, it is useful to pronounce them together.
Hazard Categories.
Threat Origination
Category
Type Identifier
Threats launched purposefully P
Threats created by unintentional human or
machine errors U
Threats caused by environmental agents or
disruptions E
From the above table, the hazard categories are shown given identifiers each, Threats denoted by
P are malicious which are purposefully launched by ill-intended individuals.
Threats denoted by U are those that could be termed as miscelenoiuos having been launched
unintended by human or machine errors in the event of duty delivery.
The E threats are also not intended for but are as a result of natural disasters which cannot be
possibly avoided but it is wise to be included in the business plans during financing the business
operations.
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Using the Securities and Exchange Commission (SEC) agency, below is the risk assessment:
Goals. The main objective of the 2012 FISMA assessment was to assess the SEC’s systems and
to give the OIG with input to the SEC’s response.
The assessment comprised of the following;
Progressive monitoring management.
Management configuration.
Point and access management.
Risk management.
Safety training.
Breakthrough and plan actions.
Management remotely.
Contingency planning.
Contractor systems.
Safety planning.
From the tentative risks in the above table, the probability of risks P and E occurring is very
minimal therefore we majorly concentrated on the risk U (Quinsey et.al 2010).
Evaluation Criteria.
The evaluation was based on the following;
1.The systems inventory and its quality.
2.The enterprise security architecture
3.Data and boundary protection.
4.The network security protocols
Outcomes.
The review concluded that OIT did not exhaustively conduct and document progressive
monitoring inline with certain NIST requirements. Progressive or continuous monitoring is the
process whereby organizations develop a clear strategy and implements a program for the
continuous supervision of security and safety control effectiveness. This comprises of potential
4 | P a g e
Goals. The main objective of the 2012 FISMA assessment was to assess the SEC’s systems and
to give the OIG with input to the SEC’s response.
The assessment comprised of the following;
Progressive monitoring management.
Management configuration.
Point and access management.
Risk management.
Safety training.
Breakthrough and plan actions.
Management remotely.
Contingency planning.
Contractor systems.
Safety planning.
From the tentative risks in the above table, the probability of risks P and E occurring is very
minimal therefore we majorly concentrated on the risk U (Quinsey et.al 2010).
Evaluation Criteria.
The evaluation was based on the following;
1.The systems inventory and its quality.
2.The enterprise security architecture
3.Data and boundary protection.
4.The network security protocols
Outcomes.
The review concluded that OIT did not exhaustively conduct and document progressive
monitoring inline with certain NIST requirements. Progressive or continuous monitoring is the
process whereby organizations develop a clear strategy and implements a program for the
continuous supervision of security and safety control effectiveness. This comprises of potential
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
need to change or beef up a control set taking into consideration any actual or proposed changes
to the information system or its operating environs ( Assessment, P. R. 2009).
Penetration testing and loophole scanning on a continuous basis and provided NIT with its test
reports, however it was deduced that penetration testing is not sufficient enough to satisfy
continuous monitoring strategy requirements as stipulated by the SP in NIST publication(SP
800-137)
It was also noticed that some areas were not tested, between year certification and accreditation
(C&A) assessment sequence or on the continuous basis for grave safety controls. Due to this,
OIT’s progressive monitoring program required enlargements with respect to its assessing
process and performance consequently.
It was also eminent that OIT top management is entirely in compliance with FISMA and
requirements and guidelines. In spite of all these compliances, OIT failed to define baseline
(Lim,et.al 2012) configurations and there is no compliance configuration too either. In addition
to these drawbacks, OIT has not given a go ahead formal project plan to Personal Identity
Verification
and has not been implemented as technical solution link. This is to cater threats under categories
P and U.
The assessment of the SEC’s risk management strategy deduced that it does not fully address the
requirements needed for a comprehensive administrative hierarchy and the organization overall
safety risk management. Further, risk from a scheme and business process aspects are not catered
for in the assessments as identified in the NIST SP 800-37 Rev.1.2.3 as consequence
Of not updating the risk management strategy to tackle the NIST guidelines.
The result of all these drawbacks is that SEC is possibly exposed to a lot of risks as business
operation.
ID Threat Name Description Typical impact to the data systems.
T1 cat
P
Hacking It is an
intentional
Confidentiality
obviously tempered
The integrity is
also messed up
5 | P a g e
to the information system or its operating environs ( Assessment, P. R. 2009).
Penetration testing and loophole scanning on a continuous basis and provided NIT with its test
reports, however it was deduced that penetration testing is not sufficient enough to satisfy
continuous monitoring strategy requirements as stipulated by the SP in NIST publication(SP
800-137)
It was also noticed that some areas were not tested, between year certification and accreditation
(C&A) assessment sequence or on the continuous basis for grave safety controls. Due to this,
OIT’s progressive monitoring program required enlargements with respect to its assessing
process and performance consequently.
It was also eminent that OIT top management is entirely in compliance with FISMA and
requirements and guidelines. In spite of all these compliances, OIT failed to define baseline
(Lim,et.al 2012) configurations and there is no compliance configuration too either. In addition
to these drawbacks, OIT has not given a go ahead formal project plan to Personal Identity
Verification
and has not been implemented as technical solution link. This is to cater threats under categories
P and U.
The assessment of the SEC’s risk management strategy deduced that it does not fully address the
requirements needed for a comprehensive administrative hierarchy and the organization overall
safety risk management. Further, risk from a scheme and business process aspects are not catered
for in the assessments as identified in the NIST SP 800-37 Rev.1.2.3 as consequence
Of not updating the risk management strategy to tackle the NIST guidelines.
The result of all these drawbacks is that SEC is possibly exposed to a lot of risks as business
operation.
ID Threat Name Description Typical impact to the data systems.
T1 cat
P
Hacking It is an
intentional
Confidentiality
obviously tempered
The integrity is
also messed up
5 | P a g e
threat launched
malicious
personnel to
remotely break
in the data
systems.
with having
disclosed the
confidential
information.
with
T2 cat
U.
Errors Unintentional
threat usually
launched in the
event daily
operations.
The
confidentiality
though not
guaranteed but
can be kept
anonymously.
The integrity is
so not lost as in
the occurrence
of other threats.
T3 cat
E
Typhoon Occurs from the
massive sea
winds .
The impact here is
massive and its
usually physical, this
is not likely to occur
due to the
organization’s
location in the far
areas from massive
water bodies.
T4 cat
P
Bombing Intentional
attack launched
by use of
explosives
Massive impact of
total destruction of
the organization’s
premises.
T5 cat
U,P &
E
Communication
failures.
Can be as a
result of human
errors,
intentional
errors or as a
The impact is
evident as the
operations can
never run
smooth without
6 | P a g e
malicious
personnel to
remotely break
in the data
systems.
with having
disclosed the
confidential
information.
with
T2 cat
U.
Errors Unintentional
threat usually
launched in the
event daily
operations.
The
confidentiality
though not
guaranteed but
can be kept
anonymously.
The integrity is
so not lost as in
the occurrence
of other threats.
T3 cat
E
Typhoon Occurs from the
massive sea
winds .
The impact here is
massive and its
usually physical, this
is not likely to occur
due to the
organization’s
location in the far
areas from massive
water bodies.
T4 cat
P
Bombing Intentional
attack launched
by use of
explosives
Massive impact of
total destruction of
the organization’s
premises.
T5 cat
U,P &
E
Communication
failures.
Can be as a
result of human
errors,
intentional
errors or as a
The impact is
evident as the
operations can
never run
smooth without
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
result of natural
disaster.
communication.
T6 cat
P
Emanating
issues.
Majorly
revolves around
the cybercrime
issues such as
evesdropping.
The
confidentiality
of the
organization’s
sensitive
information is
tempered with.
T7 cat
P & U
Data disclosure. This can be
intentional or
unintentional
depending on
the
circumstance.
Confidentiality
is also put to
test here.
T8 cat
U
Data Entry
Error
Human
inattention,
lack of
knowledge,
and failure to
cross-check
system
activities
could
contribute to
errors
becoming
integrated and
ingrained in
automated
Modification
7 | P a g e
disaster.
communication.
T6 cat
P
Emanating
issues.
Majorly
revolves around
the cybercrime
issues such as
evesdropping.
The
confidentiality
of the
organization’s
sensitive
information is
tempered with.
T7 cat
P & U
Data disclosure. This can be
intentional or
unintentional
depending on
the
circumstance.
Confidentiality
is also put to
test here.
T8 cat
U
Data Entry
Error
Human
inattention,
lack of
knowledge,
and failure to
cross-check
system
activities
could
contribute to
errors
becoming
integrated and
ingrained in
automated
Modification
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
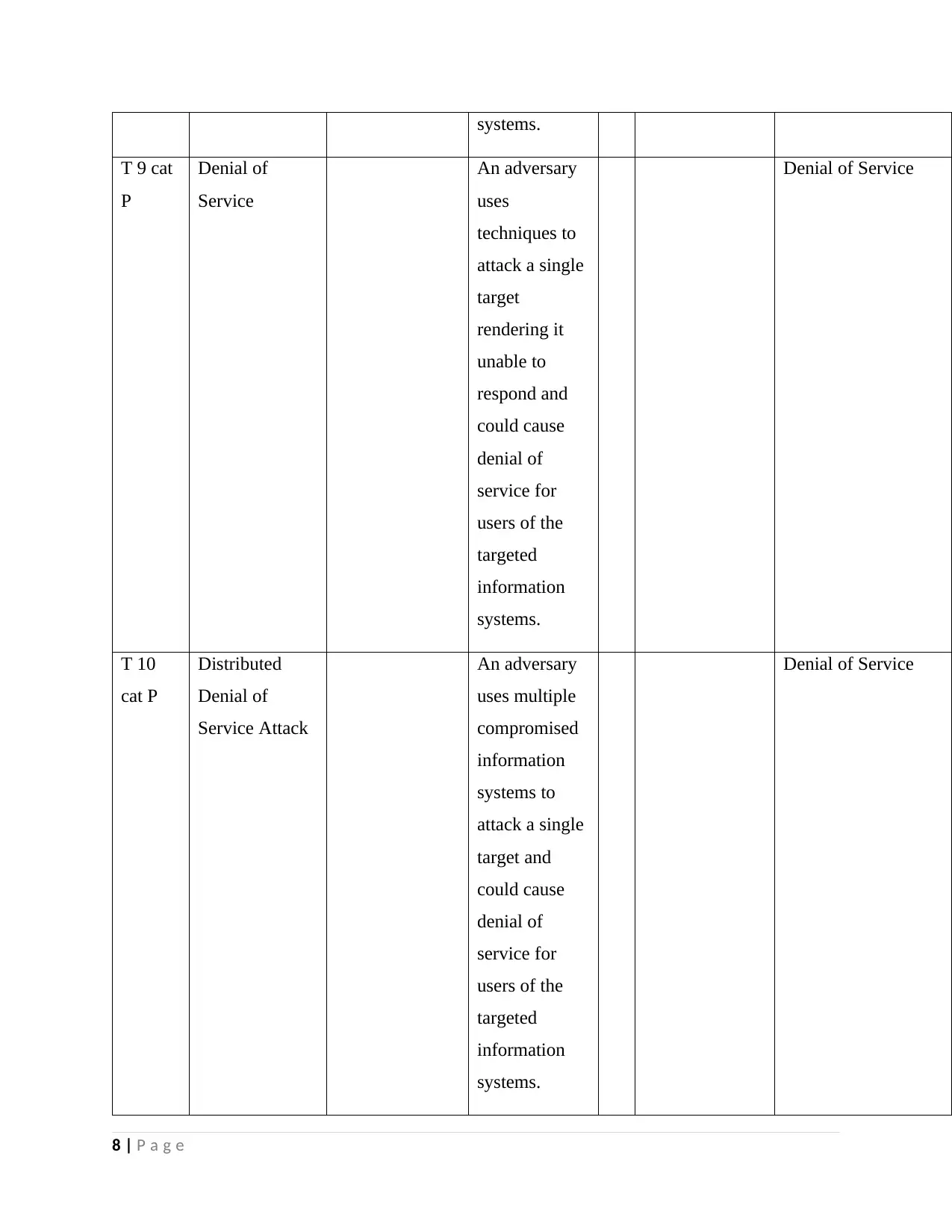
systems.
T 9 cat
P
Denial of
Service
An adversary
uses
techniques to
attack a single
target
rendering it
unable to
respond and
could cause
denial of
service for
users of the
targeted
information
systems.
Denial of Service
T 10
cat P
Distributed
Denial of
Service Attack
An adversary
uses multiple
compromised
information
systems to
attack a single
target and
could cause
denial of
service for
users of the
targeted
information
systems.
Denial of Service
8 | P a g e
T 9 cat
P
Denial of
Service
An adversary
uses
techniques to
attack a single
target
rendering it
unable to
respond and
could cause
denial of
service for
users of the
targeted
information
systems.
Denial of Service
T 10
cat P
Distributed
Denial of
Service Attack
An adversary
uses multiple
compromised
information
systems to
attack a single
target and
could cause
denial of
service for
users of the
targeted
information
systems.
Denial of Service
8 | P a g e
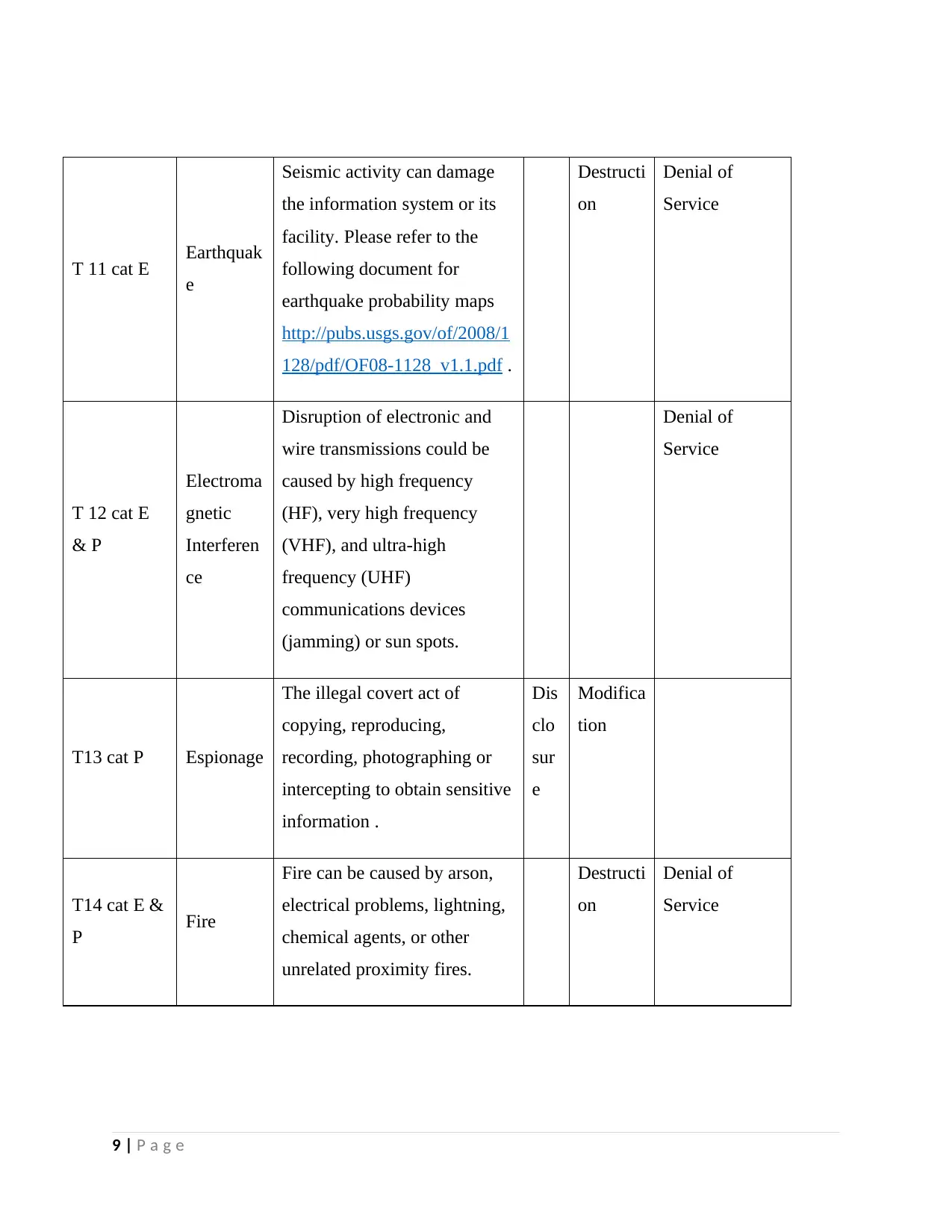
T 11 cat E Earthquak
e
Seismic activity can damage
the information system or its
facility. Please refer to the
following document for
earthquake probability maps
http://pubs.usgs.gov/of/2008/1
128/pdf/OF08-1128_v1.1.pdf .
Destructi
on
Denial of
Service
T 12 cat E
& P
Electroma
gnetic
Interferen
ce
Disruption of electronic and
wire transmissions could be
caused by high frequency
(HF), very high frequency
(VHF), and ultra-high
frequency (UHF)
communications devices
(jamming) or sun spots.
Denial of
Service
T13 cat P Espionage
The illegal covert act of
copying, reproducing,
recording, photographing or
intercepting to obtain sensitive
information .
Dis
clo
sur
e
Modifica
tion
T14 cat E &
P Fire
Fire can be caused by arson,
electrical problems, lightning,
chemical agents, or other
unrelated proximity fires.
Destructi
on
Denial of
Service
9 | P a g e
e
Seismic activity can damage
the information system or its
facility. Please refer to the
following document for
earthquake probability maps
http://pubs.usgs.gov/of/2008/1
128/pdf/OF08-1128_v1.1.pdf .
Destructi
on
Denial of
Service
T 12 cat E
& P
Electroma
gnetic
Interferen
ce
Disruption of electronic and
wire transmissions could be
caused by high frequency
(HF), very high frequency
(VHF), and ultra-high
frequency (UHF)
communications devices
(jamming) or sun spots.
Denial of
Service
T13 cat P Espionage
The illegal covert act of
copying, reproducing,
recording, photographing or
intercepting to obtain sensitive
information .
Dis
clo
sur
e
Modifica
tion
T14 cat E &
P Fire
Fire can be caused by arson,
electrical problems, lightning,
chemical agents, or other
unrelated proximity fires.
Destructi
on
Denial of
Service
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
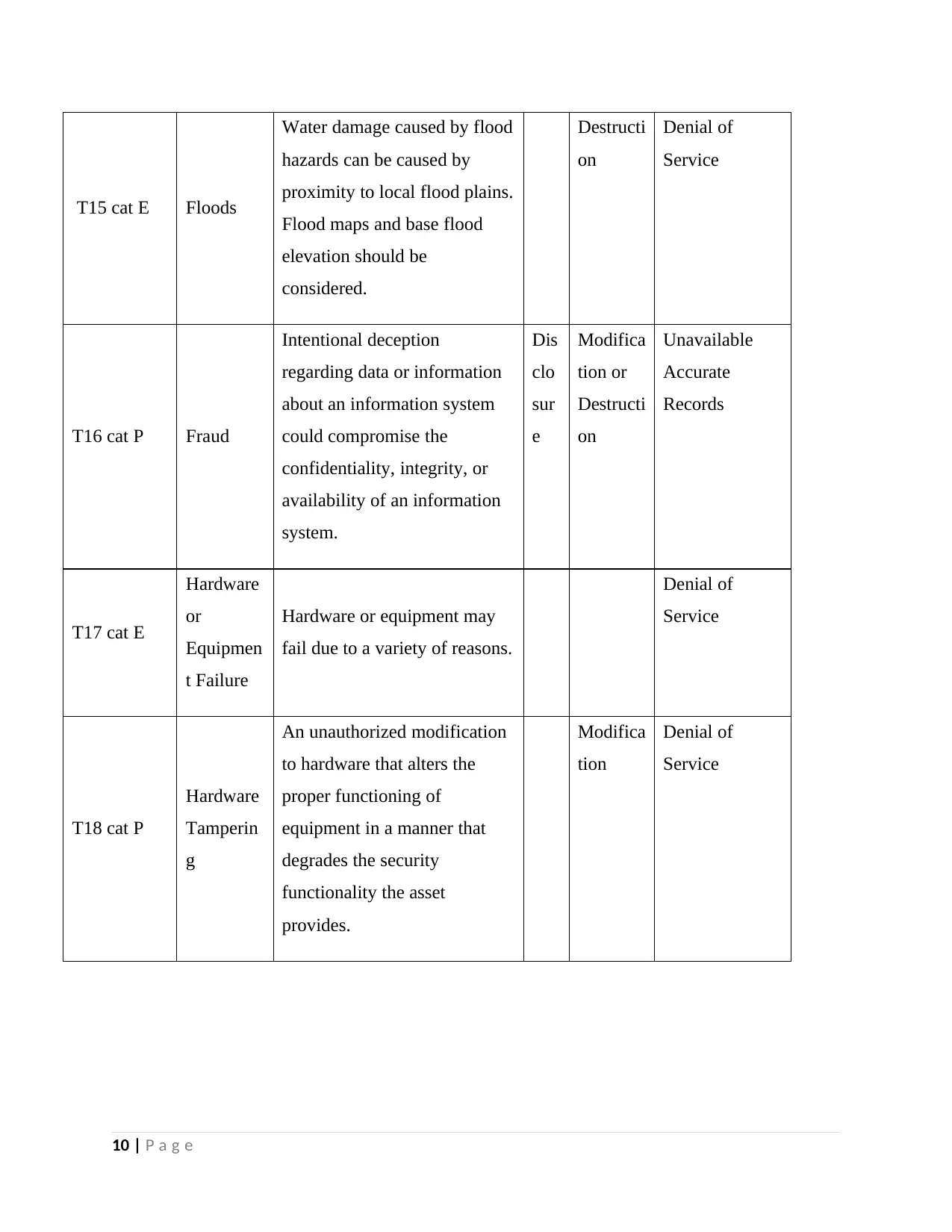
T15 cat E Floods
Water damage caused by flood
hazards can be caused by
proximity to local flood plains.
Flood maps and base flood
elevation should be
considered.
Destructi
on
Denial of
Service
T16 cat P Fraud
Intentional deception
regarding data or information
about an information system
could compromise the
confidentiality, integrity, or
availability of an information
system.
Dis
clo
sur
e
Modifica
tion or
Destructi
on
Unavailable
Accurate
Records
T17 cat E
Hardware
or
Equipmen
t Failure
Hardware or equipment may
fail due to a variety of reasons.
Denial of
Service
T18 cat P
Hardware
Tamperin
g
An unauthorized modification
to hardware that alters the
proper functioning of
equipment in a manner that
degrades the security
functionality the asset
provides.
Modifica
tion
Denial of
Service
10 | P a g e
Water damage caused by flood
hazards can be caused by
proximity to local flood plains.
Flood maps and base flood
elevation should be
considered.
Destructi
on
Denial of
Service
T16 cat P Fraud
Intentional deception
regarding data or information
about an information system
could compromise the
confidentiality, integrity, or
availability of an information
system.
Dis
clo
sur
e
Modifica
tion or
Destructi
on
Unavailable
Accurate
Records
T17 cat E
Hardware
or
Equipmen
t Failure
Hardware or equipment may
fail due to a variety of reasons.
Denial of
Service
T18 cat P
Hardware
Tamperin
g
An unauthorized modification
to hardware that alters the
proper functioning of
equipment in a manner that
degrades the security
functionality the asset
provides.
Modifica
tion
Denial of
Service
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
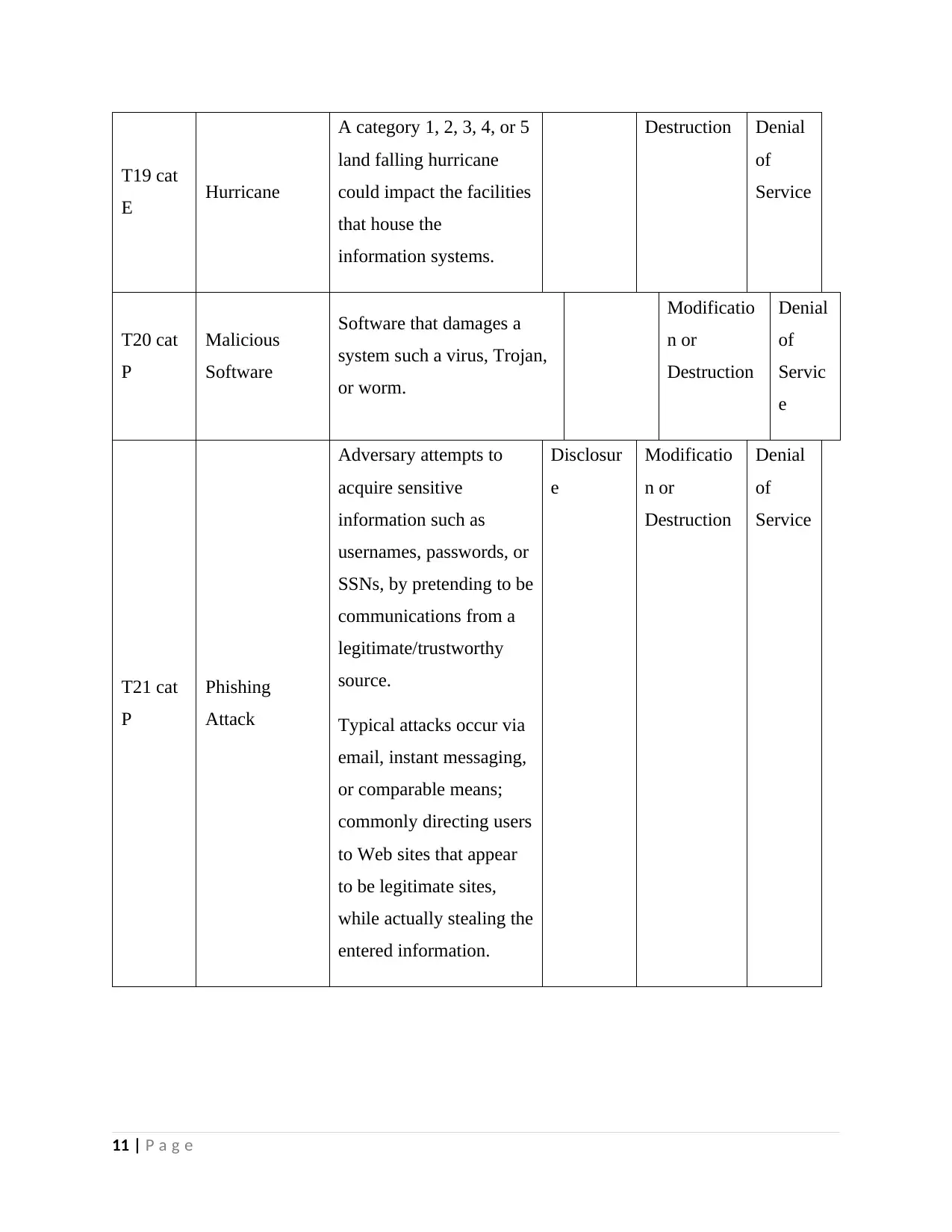
T19 cat
E Hurricane
A category 1, 2, 3, 4, or 5
land falling hurricane
could impact the facilities
that house the
information systems.
Destruction Denial
of
Service
T20 cat
P
Malicious
Software
Software that damages a
system such a virus, Trojan,
or worm.
Modificatio
n or
Destruction
Denial
of
Servic
e
T21 cat
P
Phishing
Attack
Adversary attempts to
acquire sensitive
information such as
usernames, passwords, or
SSNs, by pretending to be
communications from a
legitimate/trustworthy
source.
Typical attacks occur via
email, instant messaging,
or comparable means;
commonly directing users
to Web sites that appear
to be legitimate sites,
while actually stealing the
entered information.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Service
11 | P a g e
E Hurricane
A category 1, 2, 3, 4, or 5
land falling hurricane
could impact the facilities
that house the
information systems.
Destruction Denial
of
Service
T20 cat
P
Malicious
Software
Software that damages a
system such a virus, Trojan,
or worm.
Modificatio
n or
Destruction
Denial
of
Servic
e
T21 cat
P
Phishing
Attack
Adversary attempts to
acquire sensitive
information such as
usernames, passwords, or
SSNs, by pretending to be
communications from a
legitimate/trustworthy
source.
Typical attacks occur via
email, instant messaging,
or comparable means;
commonly directing users
to Web sites that appear
to be legitimate sites,
while actually stealing the
entered information.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Service
11 | P a g e
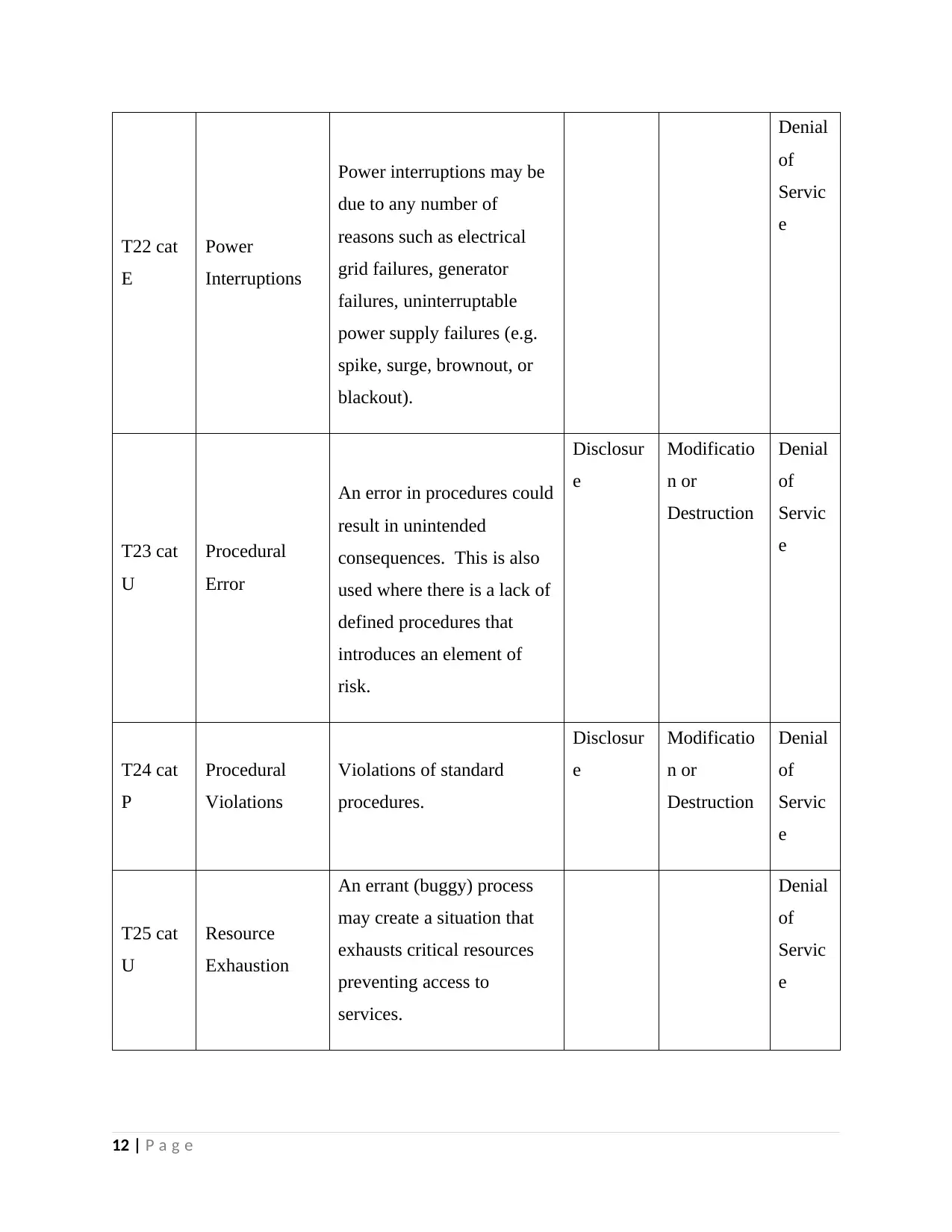
T22 cat
E
Power
Interruptions
Power interruptions may be
due to any number of
reasons such as electrical
grid failures, generator
failures, uninterruptable
power supply failures (e.g.
spike, surge, brownout, or
blackout).
Denial
of
Servic
e
T23 cat
U
Procedural
Error
An error in procedures could
result in unintended
consequences. This is also
used where there is a lack of
defined procedures that
introduces an element of
risk.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Servic
e
T24 cat
P
Procedural
Violations
Violations of standard
procedures.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Servic
e
T25 cat
U
Resource
Exhaustion
An errant (buggy) process
may create a situation that
exhausts critical resources
preventing access to
services.
Denial
of
Servic
e
12 | P a g e
E
Power
Interruptions
Power interruptions may be
due to any number of
reasons such as electrical
grid failures, generator
failures, uninterruptable
power supply failures (e.g.
spike, surge, brownout, or
blackout).
Denial
of
Servic
e
T23 cat
U
Procedural
Error
An error in procedures could
result in unintended
consequences. This is also
used where there is a lack of
defined procedures that
introduces an element of
risk.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Servic
e
T24 cat
P
Procedural
Violations
Violations of standard
procedures.
Disclosur
e
Modificatio
n or
Destruction
Denial
of
Servic
e
T25 cat
U
Resource
Exhaustion
An errant (buggy) process
may create a situation that
exhausts critical resources
preventing access to
services.
Denial
of
Servic
e
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.