Secure Asset Management's MIS: Data Handling, Ethics and Business
VerifiedAdded on 2023/06/08
|16
|4461
|493
Report
AI Summary
This report provides a comprehensive analysis of Secure Asset Management's Management Information System (MIS), focusing on the interconnection of its various business units, including production, sales, marketing, and research and development. It delves into the different types of data utilized within the organization, differentiating between operational, tactical, and strategic data, and explores the technologies and products associated with operational databases and CRM. Furthermore, the report discusses data warehousing, data mining, and data analytics options, including cloud-based and outsourced data management platforms, as well as web-based and mobile application access. Finally, it summarizes key ethical, legal, and professional concerns related to information handling and security within Secure Asset Management. Desklib provides access to this assignment and many other solved assignments and past papers for students.

Management
Information System
Information System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Content
INTRODUCTION ........................................................................................................................3
Task-1..............................................................................................................................................3
Describe how the business units of Secure Asset Management are interconnected....................3
Task 2..............................................................................................................................................5
Explain the key concept and differences between: operational, tactical and strategic data........5
Task 3..............................................................................................................................................7
Operational database and CRM technologies and products........................................................7
Data warehousing, data mining and data analytics (‘big data’) options......................................8
Cloud based and out-sourced data management platforms and services.....................................9
Access of platforms on web-based and mobile applications ......................................................9
Task 4............................................................................................................................................10
Summary of key concerns about ethical, legal and professional implications associated with
information handling and security.............................................................................................10
CONCLUSION............................................................................................................................11
REFERENCES............................................................................................................................12
INTRODUCTION ........................................................................................................................3
Task-1..............................................................................................................................................3
Describe how the business units of Secure Asset Management are interconnected....................3
Task 2..............................................................................................................................................5
Explain the key concept and differences between: operational, tactical and strategic data........5
Task 3..............................................................................................................................................7
Operational database and CRM technologies and products........................................................7
Data warehousing, data mining and data analytics (‘big data’) options......................................8
Cloud based and out-sourced data management platforms and services.....................................9
Access of platforms on web-based and mobile applications ......................................................9
Task 4............................................................................................................................................10
Summary of key concerns about ethical, legal and professional implications associated with
information handling and security.............................................................................................10
CONCLUSION............................................................................................................................11
REFERENCES............................................................................................................................12

INTRODUCTION
Management information system is the system of the company that is used by the
management in order to operate their business in an appropriate manner. this also assist in taking
strategic and comparative decisions for the growth of the business. This also leads to have full
control over the organisation with the help of visualisation(Lloyd, 2020). The growth of
information management is very high as there are various advance technology which are
developed in the market and helps the company to operate the business in an effective manner.
MIS are basically based on technology within the organisation with the sole aim in order to
collect the information from the various source in order to have the better decisions to them. It
also enables an organisation to understand the needs and desire of the customer in the market
which help the company to work as per the market demand to their potential customers. This is
helpful for the top level executives of an organisation as it helps them to take better and valuable
decisions within the company. For tis respective report, secure Asset Management is the chosen
business which is headquartered is in London and they are operating in storing sensitive
corporate data such as internal accounts, auditing reports, staff and salary data, bank-ups &
archives of operational data, corporate strategy data and more. This report will cover the
interrelation of various business units. This also provide the discussion related to the roles and
responsibilities of Secure Asset Management’s data warehousing. This also further analyse the
key concern about the ethical, professional and legal implication associated with the security and
data handling.
Task-1
Describe how the business units of Secure Asset Management are interconnected.
As the management of the company has performed various business with the help of various
department that also enables the extensive growth and sale for the company. They also
establishing effective interrelation among various units of business that leads to attains the goals
and objectives in the market in an appropriate manner(Manoharan and et. al., 2020). with the
help of proper data and the information various department helps them to take corrective
decisions and operate their business in an effective manner. An interconnected system as it
relates to the business technological functions is one where the software is shared and easily
Management information system is the system of the company that is used by the
management in order to operate their business in an appropriate manner. this also assist in taking
strategic and comparative decisions for the growth of the business. This also leads to have full
control over the organisation with the help of visualisation(Lloyd, 2020). The growth of
information management is very high as there are various advance technology which are
developed in the market and helps the company to operate the business in an effective manner.
MIS are basically based on technology within the organisation with the sole aim in order to
collect the information from the various source in order to have the better decisions to them. It
also enables an organisation to understand the needs and desire of the customer in the market
which help the company to work as per the market demand to their potential customers. This is
helpful for the top level executives of an organisation as it helps them to take better and valuable
decisions within the company. For tis respective report, secure Asset Management is the chosen
business which is headquartered is in London and they are operating in storing sensitive
corporate data such as internal accounts, auditing reports, staff and salary data, bank-ups &
archives of operational data, corporate strategy data and more. This report will cover the
interrelation of various business units. This also provide the discussion related to the roles and
responsibilities of Secure Asset Management’s data warehousing. This also further analyse the
key concern about the ethical, professional and legal implication associated with the security and
data handling.
Task-1
Describe how the business units of Secure Asset Management are interconnected.
As the management of the company has performed various business with the help of various
department that also enables the extensive growth and sale for the company. They also
establishing effective interrelation among various units of business that leads to attains the goals
and objectives in the market in an appropriate manner(Manoharan and et. al., 2020). with the
help of proper data and the information various department helps them to take corrective
decisions and operate their business in an effective manner. An interconnected system as it
relates to the business technological functions is one where the software is shared and easily
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

transparent between various departments. This linking of the system helps the staff members to
adjust to the last minute changes and allows effective coordination between different groups.
Figure 1: Management information system, 2006
Structure chart of SAM
Production department
This is the department in which the production of products and services are being
performed. This is one of the significant and value business unit as the entire success of the
failure of the company is depends upon the quality of the products and services offered to the
large group of potential customer (Drobyazko and et. al., 2019). This department play significant
role as the production of commodities also decide the cost of the same. So when the company is
using the traditional methods of production then it leads to occur huge cost and impact the
overall operations of the company. It is vital for the production department to use the innovative
and advance methods and techniques in order to maintain the cost and the quality of the product.
Secure Asset Management is providing technological assistance to the various business clients
which basically includes the production of hardware i.e., computer systems, laptops and various
types of software. Production department needs the technical mind and the technology. They
further require an effective communication system so that they can operate and pass the right
information to the concern person within the given span of time.
Sales department
This is the department which is engage with the sales of products and services of an
organisation in the large market(Han and Kim, 2019). They basically have the direct contact with
the client as they are dealing in selling products and services in the target market. Employees
who are operating in this department, needs integrated set of skills so that they can attract the
adjust to the last minute changes and allows effective coordination between different groups.
Figure 1: Management information system, 2006
Structure chart of SAM
Production department
This is the department in which the production of products and services are being
performed. This is one of the significant and value business unit as the entire success of the
failure of the company is depends upon the quality of the products and services offered to the
large group of potential customer (Drobyazko and et. al., 2019). This department play significant
role as the production of commodities also decide the cost of the same. So when the company is
using the traditional methods of production then it leads to occur huge cost and impact the
overall operations of the company. It is vital for the production department to use the innovative
and advance methods and techniques in order to maintain the cost and the quality of the product.
Secure Asset Management is providing technological assistance to the various business clients
which basically includes the production of hardware i.e., computer systems, laptops and various
types of software. Production department needs the technical mind and the technology. They
further require an effective communication system so that they can operate and pass the right
information to the concern person within the given span of time.
Sales department
This is the department which is engage with the sales of products and services of an
organisation in the large market(Han and Kim, 2019). They basically have the direct contact with
the client as they are dealing in selling products and services in the target market. Employees
who are operating in this department, needs integrated set of skills so that they can attract the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

large group of customer at marketplace. In context to Secure Asset Management, they need to
provide needful resources and funds to the sale department so that they can better perform the
operations of the company in an appropriate manner. they need to establish effective
communication channels among such department which help them to share the number of
information within the organisation in the target market(Ikramov, Mamajonov and Toshpulatov,
2019). They basically have the direct contact with the products and services as they are also
operating products and services and offering them to their potential customers.
Marketing department
It is the business unit which is operating its business in advertising the products and
services to the target audience. In relation to Secure Asset Management, they are getting
technological support in order to advertise their products and services to their target market. It is
vital for the other business unit to have the better communication with the sales and market unit
so that they can be aware about the current and emerging market trends(Kravets and et. al.,
2018).
Research and development
This is the department which is concern for the innovation and advance by opting the
new technology and techniques from the large market. They continuously focus on getting some
innovation in their business so that they can retain in the market for long period of time and
ensure higher profitability and growth. The researcher of Secure Asset Management technology
and assisting their client with better services(Ferraris and et. al. 2018).
provide needful resources and funds to the sale department so that they can better perform the
operations of the company in an appropriate manner. they need to establish effective
communication channels among such department which help them to share the number of
information within the organisation in the target market(Ikramov, Mamajonov and Toshpulatov,
2019). They basically have the direct contact with the products and services as they are also
operating products and services and offering them to their potential customers.
Marketing department
It is the business unit which is operating its business in advertising the products and
services to the target audience. In relation to Secure Asset Management, they are getting
technological support in order to advertise their products and services to their target market. It is
vital for the other business unit to have the better communication with the sales and market unit
so that they can be aware about the current and emerging market trends(Kravets and et. al.,
2018).
Research and development
This is the department which is concern for the innovation and advance by opting the
new technology and techniques from the large market. They continuously focus on getting some
innovation in their business so that they can retain in the market for long period of time and
ensure higher profitability and growth. The researcher of Secure Asset Management technology
and assisting their client with better services(Ferraris and et. al. 2018).
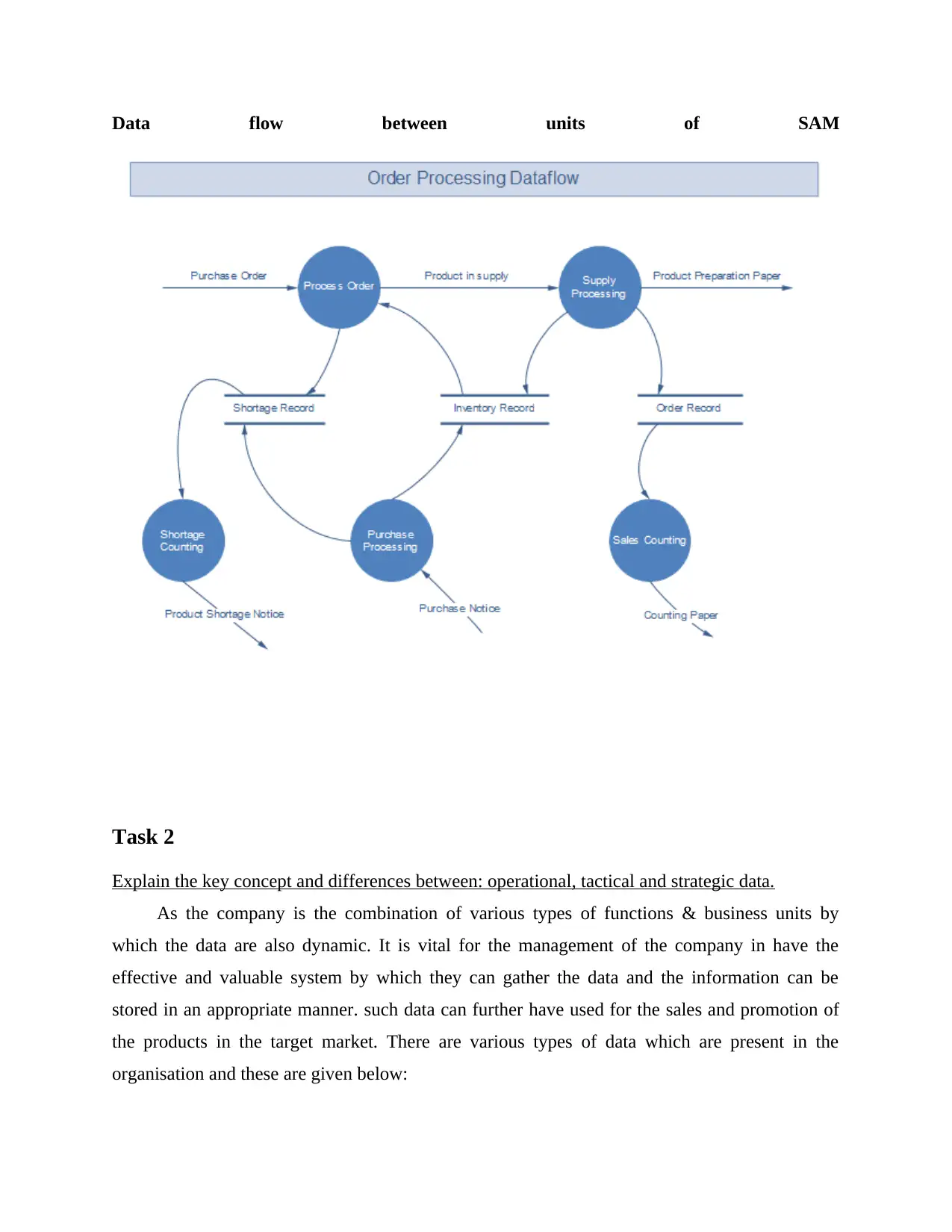
Data flow between units of SAM
Task 2
Explain the key concept and differences between: operational, tactical and strategic data.
As the company is the combination of various types of functions & business units by
which the data are also dynamic. It is vital for the management of the company in have the
effective and valuable system by which they can gather the data and the information can be
stored in an appropriate manner. such data can further have used for the sales and promotion of
the products in the target market. There are various types of data which are present in the
organisation and these are given below:
Task 2
Explain the key concept and differences between: operational, tactical and strategic data.
As the company is the combination of various types of functions & business units by
which the data are also dynamic. It is vital for the management of the company in have the
effective and valuable system by which they can gather the data and the information can be
stored in an appropriate manner. such data can further have used for the sales and promotion of
the products in the target market. There are various types of data which are present in the
organisation and these are given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Operational data
This is basically connected to the type of data that is being generated within the company
with the help of regular business operations. There are various events and transactions which are
conducting within the organisation that includes the purchase inventory and so on. It is note that
the frequency of such transactions are very high that also enables the management that create
confusing environment(Chouki and et. al., 2022). It is clear that when the data get deleted then it
hurdles the audit of the company and create problem for the company as well. This is the
obligation to all the business unit to maintain records of the data by which it can be recertified
for the effective analysis. This is vital for the management of the company that they applied
effective information management within the organisation which create effective data
management within the company. In consideration to Secure Asset Management, they are
operating its business in various nations which create effective data within the organisation and
they are providing various amount of data(Soni and Singh, 2021). As the various business unit
that are discussed in the task-1 that includes the marketing, production and so on. There are
number of customers in these type of companies which creates lots of data that is to be managed
by the company.
Tactical data
The management of the company has enables the management to secure their data in the
organisation. It basically related to such type of data which has to be protected from the
disclosure and modification for the limited period of time. There are various types of data which
are available within the organisation and it is vital for the betterment from the third party to
access the changes. Management information system of the company helps in giving various
This is basically connected to the type of data that is being generated within the company
with the help of regular business operations. There are various events and transactions which are
conducting within the organisation that includes the purchase inventory and so on. It is note that
the frequency of such transactions are very high that also enables the management that create
confusing environment(Chouki and et. al., 2022). It is clear that when the data get deleted then it
hurdles the audit of the company and create problem for the company as well. This is the
obligation to all the business unit to maintain records of the data by which it can be recertified
for the effective analysis. This is vital for the management of the company that they applied
effective information management within the organisation which create effective data
management within the company. In consideration to Secure Asset Management, they are
operating its business in various nations which create effective data within the organisation and
they are providing various amount of data(Soni and Singh, 2021). As the various business unit
that are discussed in the task-1 that includes the marketing, production and so on. There are
number of customers in these type of companies which creates lots of data that is to be managed
by the company.
Tactical data
The management of the company has enables the management to secure their data in the
organisation. It basically related to such type of data which has to be protected from the
disclosure and modification for the limited period of time. There are various types of data which
are available within the organisation and it is vital for the betterment from the third party to
access the changes. Management information system of the company helps in giving various
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
types of securing functions that leads to save the data in an appropriate manner. This basically
includes the data which are used by the top level management and they can used the management
information system in order preserve the data and the information.
Strategic data
It is the data which helps in framing the strategic and the effective decisions of the
company by which they can grow its business in the international market(Antonelli, 2019). In
context to Secure Asset Management, there are basically four type of data that is used by the
business such as descriptive data, diagnostic data, predicative data and prescriptive data. With
this, company can ensure the effective management of the data by which they can have smooth
running of the business. Strategic data also keeps marketers in tune with the trends which helps
create in-demand products and appealing advertisements. This is the data which is being used to
frame the strategy in order to operate the business for the smooth running of the business in the
company. This data is being used by the manager and can be middle level of the company in
order to take the various decisions within the company. They can use the point of sale software
in order to make the sale summary and many more.
Classification of information systems:
Characteristics Operational Tactical Strategic
Nature of data Highly structured Some unstructured
data
Highly unstructured
Accuracy Highly Accurate data Some subjective data Highly subjective data
Typical user Fist-line supervisors Middle managers Top management
Level of decision Task oriented Oriented for control
and allocation of
resources
Goal oriented
They basically make the floe of data from top level management to the middle level
management with the help of ERP portals of the employees so that they can ensure the overall
working of them and make the decisions accordingly for the further development. They are also
using email methods in order to pass the data and the information to the users to have the better
data to their customer and the company(Susanto and Almunawar, 2018).
includes the data which are used by the top level management and they can used the management
information system in order preserve the data and the information.
Strategic data
It is the data which helps in framing the strategic and the effective decisions of the
company by which they can grow its business in the international market(Antonelli, 2019). In
context to Secure Asset Management, there are basically four type of data that is used by the
business such as descriptive data, diagnostic data, predicative data and prescriptive data. With
this, company can ensure the effective management of the data by which they can have smooth
running of the business. Strategic data also keeps marketers in tune with the trends which helps
create in-demand products and appealing advertisements. This is the data which is being used to
frame the strategy in order to operate the business for the smooth running of the business in the
company. This data is being used by the manager and can be middle level of the company in
order to take the various decisions within the company. They can use the point of sale software
in order to make the sale summary and many more.
Classification of information systems:
Characteristics Operational Tactical Strategic
Nature of data Highly structured Some unstructured
data
Highly unstructured
Accuracy Highly Accurate data Some subjective data Highly subjective data
Typical user Fist-line supervisors Middle managers Top management
Level of decision Task oriented Oriented for control
and allocation of
resources
Goal oriented
They basically make the floe of data from top level management to the middle level
management with the help of ERP portals of the employees so that they can ensure the overall
working of them and make the decisions accordingly for the further development. They are also
using email methods in order to pass the data and the information to the users to have the better
data to their customer and the company(Susanto and Almunawar, 2018).

Task 3
Operational database and CRM technologies and products
Operational Database refers to the system of database management which stores and processes
the data in the real time. The operational data base system is basically a software which is
designed in a way for easily defining, modifying, retrieving and managing the data in real time.
Mean while the database rely on the batch processing, systems of operational database are
oriented to the real time, operations of transactions(Baruffaldi, Accorsi, and Manzini, 2018).
They are based on SQL and NoSQL for the source of warehouses of data. In context of Secure
Asset Management company they use operational data base for updating data at real time. These
kinds of databases allows the users for doing more than archiving data(Hariyati, Tjahjadi and
Soewarno, 2019).
CRM is the technology for the management of firms relationship and interactions with the
potential consumers and consumers(Singh and et.al., 2020). Secure Asset Management firm uses
CRM as it helps them to stay connected to the consumers, process streamline and enhance the
profits. Here are some CRM products-
Web services and services oriented Architecture- Secure Asset Management use this
as it provides the increased flexibility. It is more adaptable in changing more reference to
the process of business. It allows them to work across all the applications in the firm.
Speech applications- Secure Asset Management use this as it decreases the cost and
boosts the transactions amount in the firm even without increasing the count. Application
like VoiceXML aids them in cutting costs and consumer satisfaction.
Data warehousing, data mining and data analytics (‘big data’) options
Data warehouse- It is the central repository of information which is analysed for making the
better decisions. Data flow in the data warehouse from the systems of transactions, relational
databases on regular bases. Here are some options used by Secure Asset Management-
Snowflake- It is the famous and very easy in using warehouses. It is the contemporary
warehouses of data, where the flexibility is the primary selling points. Its a cloud agnostic
as it can be deployed any where consisting Azure, AWS etc(Stover, 2019).
Operational database and CRM technologies and products
Operational Database refers to the system of database management which stores and processes
the data in the real time. The operational data base system is basically a software which is
designed in a way for easily defining, modifying, retrieving and managing the data in real time.
Mean while the database rely on the batch processing, systems of operational database are
oriented to the real time, operations of transactions(Baruffaldi, Accorsi, and Manzini, 2018).
They are based on SQL and NoSQL for the source of warehouses of data. In context of Secure
Asset Management company they use operational data base for updating data at real time. These
kinds of databases allows the users for doing more than archiving data(Hariyati, Tjahjadi and
Soewarno, 2019).
CRM is the technology for the management of firms relationship and interactions with the
potential consumers and consumers(Singh and et.al., 2020). Secure Asset Management firm uses
CRM as it helps them to stay connected to the consumers, process streamline and enhance the
profits. Here are some CRM products-
Web services and services oriented Architecture- Secure Asset Management use this
as it provides the increased flexibility. It is more adaptable in changing more reference to
the process of business. It allows them to work across all the applications in the firm.
Speech applications- Secure Asset Management use this as it decreases the cost and
boosts the transactions amount in the firm even without increasing the count. Application
like VoiceXML aids them in cutting costs and consumer satisfaction.
Data warehousing, data mining and data analytics (‘big data’) options
Data warehouse- It is the central repository of information which is analysed for making the
better decisions. Data flow in the data warehouse from the systems of transactions, relational
databases on regular bases. Here are some options used by Secure Asset Management-
Snowflake- It is the famous and very easy in using warehouses. It is the contemporary
warehouses of data, where the flexibility is the primary selling points. Its a cloud agnostic
as it can be deployed any where consisting Azure, AWS etc(Stover, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Google Big Query- It is the offering to data warehouse industry and is completely based
out of cloud and is very easy in use. Secure Asset Management uses it for its analytic
capabilities offering insights, predictions and intelligence features which makes it a long
term and scalable solution.
Data mining- It is the process of extraction and discovering of patterns in the huge sets of data
which involves the methods at interaction of machine learning. Some of the options used by
Secure Asset Management are-
Integrate.io- It provides the platform which has functionalities for integrating,
procedure and preparation of data for the analytics. Secure Asset Management uses this
platform for making the opportunities with aid of this without even investing in hardware,
personnel etc.
Rapidminer- It is the predictive system for analysis and written in JAVA programming
language. Secure Asset Management uses it in a wide range of applications like training,
education, machine learning etc.
Big data analytics- It is the use of advanced techniques of analytics against the big sets of data
which includes the semi structured and structured from the various sources. Some of the option
are explained-
3Q Digital- Secure Asset Management use it as it blends the search engine, video and
mobile marketing. It perfects the channels of marketing by studying data on transactions,
behaviour of consumers etc. It allows the firm in distinguishing among the ineffective and
effective ad impressions on small level. It offers a complete suite of services and
solutions which help in transforming the existing performance into substantial growth. It
also provides an end to end solution which starts from planning & analytics and finishes
on delivery & management.
DISQO- Secure Asset Management takes help from this for measuring brand and
experience of consumer. It also aids in research specialization and marketing efforts by
tracking the performance and result(Guha and Kumar, 2018).
out of cloud and is very easy in use. Secure Asset Management uses it for its analytic
capabilities offering insights, predictions and intelligence features which makes it a long
term and scalable solution.
Data mining- It is the process of extraction and discovering of patterns in the huge sets of data
which involves the methods at interaction of machine learning. Some of the options used by
Secure Asset Management are-
Integrate.io- It provides the platform which has functionalities for integrating,
procedure and preparation of data for the analytics. Secure Asset Management uses this
platform for making the opportunities with aid of this without even investing in hardware,
personnel etc.
Rapidminer- It is the predictive system for analysis and written in JAVA programming
language. Secure Asset Management uses it in a wide range of applications like training,
education, machine learning etc.
Big data analytics- It is the use of advanced techniques of analytics against the big sets of data
which includes the semi structured and structured from the various sources. Some of the option
are explained-
3Q Digital- Secure Asset Management use it as it blends the search engine, video and
mobile marketing. It perfects the channels of marketing by studying data on transactions,
behaviour of consumers etc. It allows the firm in distinguishing among the ineffective and
effective ad impressions on small level. It offers a complete suite of services and
solutions which help in transforming the existing performance into substantial growth. It
also provides an end to end solution which starts from planning & analytics and finishes
on delivery & management.
DISQO- Secure Asset Management takes help from this for measuring brand and
experience of consumer. It also aids in research specialization and marketing efforts by
tracking the performance and result(Guha and Kumar, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud based and out-sourced data management platforms and services
Cloud data management is a method of managing the data across the various cloud platforms.
The cloud facility helps in storing data for disaster recovery, backup and other long term
archiving. The Secure Asset Management uses these cloud platforms to store data in both
software and hardware products. The services which are used by the organisation are
Infrastructure-as-a-Service, Platforms-as-a-Service and Software-as-a-Service(Szymkowiak, A.
and et. al., 2021). Cloud resource management requires complex policies and decisions for multi-
objective optimisation. Secure Asset Management uses outsourcing data management which
helps in tapping into a huge pool of talent of skilled and experienced professionals. In this way,
the business will be able to pay more attention on the other essential policies of the company.
Access of platforms on web-based and mobile applications
A web based application can be defined as a program which is accessed over a connection of
networks using HTTP instead of existing within a memory of the device. Secure Asset
Management uses these platforms for availing various benefits such as customization of different
devices, integration with other systems and removal of various issues of maintenance. It helps
the company in increasing scalability and flexibility of the operations of the business(Taylor and
Joshi, 2019). These different platforms should provide access to the mobile applications and
other web-based systems.
Task 4
Summary of key concerns about ethical, legal and professional implications associated with
information handling and security.
Hacking is the misconduct which is done by the people for the unfair means in order to
make their work easy. This leads to steal the money of the individual or the company and can
open the credit card with the another user name ans so on.
There is certain task which needs to control and do not forget of their coping with and
manipulating the data and information with inside the employer. There are certain guidelines that
the authorise of reputed united states of America changed to their commercial enterprises
Cloud data management is a method of managing the data across the various cloud platforms.
The cloud facility helps in storing data for disaster recovery, backup and other long term
archiving. The Secure Asset Management uses these cloud platforms to store data in both
software and hardware products. The services which are used by the organisation are
Infrastructure-as-a-Service, Platforms-as-a-Service and Software-as-a-Service(Szymkowiak, A.
and et. al., 2021). Cloud resource management requires complex policies and decisions for multi-
objective optimisation. Secure Asset Management uses outsourcing data management which
helps in tapping into a huge pool of talent of skilled and experienced professionals. In this way,
the business will be able to pay more attention on the other essential policies of the company.
Access of platforms on web-based and mobile applications
A web based application can be defined as a program which is accessed over a connection of
networks using HTTP instead of existing within a memory of the device. Secure Asset
Management uses these platforms for availing various benefits such as customization of different
devices, integration with other systems and removal of various issues of maintenance. It helps
the company in increasing scalability and flexibility of the operations of the business(Taylor and
Joshi, 2019). These different platforms should provide access to the mobile applications and
other web-based systems.
Task 4
Summary of key concerns about ethical, legal and professional implications associated with
information handling and security.
Hacking is the misconduct which is done by the people for the unfair means in order to
make their work easy. This leads to steal the money of the individual or the company and can
open the credit card with the another user name ans so on.
There is certain task which needs to control and do not forget of their coping with and
manipulating the data and information with inside the employer. There are certain guidelines that
the authorise of reputed united states of America changed to their commercial enterprises

corporations for the safety rights. Furthermore, the general data protection regulation is appeared
as this this the toughest safety regulation within the globe.
Ethical- It is the linked with the one values & practises which is being performed
with the sole aim of personnel of the company in the given time period in their
tremendous behaviour for various folks and the interest of the company. This is the
responsibility of the managers that they do not take longer records of the business to
any outsider or the competitive organisation(Antonelli, 2019). This is the duty of the
manager they can enhance its powerful records rea groups that has exception of being
morale within the company and ensure the right coaching to the employees. This is
also recommended to the Secure Asset Management that they can accompanied the
policies & laws which are appeal as moral in records control and handling. This is
important for the merchandising within the company that the employees are operating
within the company has the clear thoughts and directs in order to have the full control
over the given situation of an organisation.
Legal- There are various polices that are being framed by the authorise that can be
advanced with the authorise of the reputable firms to be accompanied through the
enterprise on the given subject of the information managing & control. These are the
guidelines and the polices are being fashioned for the safety purpose of the client
from the terrible and malpractice of the company to their employees.Give us an example
taken from GDPR and try to criticise it
The given record capture by the company consist of non-public records and the
records of banking of the customer that can be utilised by any of the hacker and the
take gain of it(Alfalah, 2018). This is the obligation of the managers of the enterprises
to put their effects of such polices and law of their company by which all the hazard
data and the information can be safe from being hacked. In relation to the Secure
Asset Management, they are developing diverse needs and the regulations on
premises of the presidency law by which the employees in formation managing and
control within the company.
Professional- This is the aspect which can be import for the agency for the
achievement of the commercial business. Employees behave professionally within
various business operations so that they can have the appropriate working within the
as this this the toughest safety regulation within the globe.
Ethical- It is the linked with the one values & practises which is being performed
with the sole aim of personnel of the company in the given time period in their
tremendous behaviour for various folks and the interest of the company. This is the
responsibility of the managers that they do not take longer records of the business to
any outsider or the competitive organisation(Antonelli, 2019). This is the duty of the
manager they can enhance its powerful records rea groups that has exception of being
morale within the company and ensure the right coaching to the employees. This is
also recommended to the Secure Asset Management that they can accompanied the
policies & laws which are appeal as moral in records control and handling. This is
important for the merchandising within the company that the employees are operating
within the company has the clear thoughts and directs in order to have the full control
over the given situation of an organisation.
Legal- There are various polices that are being framed by the authorise that can be
advanced with the authorise of the reputable firms to be accompanied through the
enterprise on the given subject of the information managing & control. These are the
guidelines and the polices are being fashioned for the safety purpose of the client
from the terrible and malpractice of the company to their employees.Give us an example
taken from GDPR and try to criticise it
The given record capture by the company consist of non-public records and the
records of banking of the customer that can be utilised by any of the hacker and the
take gain of it(Alfalah, 2018). This is the obligation of the managers of the enterprises
to put their effects of such polices and law of their company by which all the hazard
data and the information can be safe from being hacked. In relation to the Secure
Asset Management, they are developing diverse needs and the regulations on
premises of the presidency law by which the employees in formation managing and
control within the company.
Professional- This is the aspect which can be import for the agency for the
achievement of the commercial business. Employees behave professionally within
various business operations so that they can have the appropriate working within the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




