In-Depth Report: Secure Communication via Wi-Fi Protected Access
VerifiedAdded on 2023/06/15
|12
|782
|60
Report
AI Summary
This report provides an overview of Wi-Fi Protected Access (WPA) as a security standard for wireless communication. It discusses the objectives, functionality, advantages, and disadvantages of WPA, comparing it with other security technologies like WEP and WPA2. The report also explores the future of WPA, highlighting its effectiveness with Advanced Encryption Standard AES encryption and the Cipher Block Chaining Message Authentication Code Protocol (CCMP). It concludes that WPA is effective for authentication and key distribution, particularly for home users and small businesses, with the 4-way handshake playing a crucial role in authenticating the client access point and establishing TKIP encryption keys. Desklib offers a wealth of resources, including similar reports and solved assignments, to aid students in their studies.

Secure
Communications
Wi-Fi Protected access
Eli, Jama, Saumya &
Waheed
Communications
Wi-Fi Protected access
Eli, Jama, Saumya &
Waheed
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
• The Wi-fi Protected Access is mainly the security standard that is set
for handling the users of computing the devices. (Au, 2016)
• It is mainly equipped with a proper wireless internet connection that is
mainly to improve the security standards and the sophisticated data
encryption.
• The Wi-fi Protected Access is mainly the security standard that is set
for handling the users of computing the devices. (Au, 2016)
• It is mainly equipped with a proper wireless internet connection that is
mainly to improve the security standards and the sophisticated data
encryption.

Objective
WPA: WPA is mainly for handling the message integrity
check, with extended initialisation vector and re-keying
mechanism.
How does it work: It works on the Remote
Authentication Dial in User Service with access to the
device credentials so that the users can be
authenticated before they are connected to the network.
Where is it used: configuring security on home
networks, office etc.
Pros & Cons: It provides a better and stronger user
authentication like RADIUS to authenticate the user. The
WPA: WPA is mainly for handling the message integrity
check, with extended initialisation vector and re-keying
mechanism.
How does it work: It works on the Remote
Authentication Dial in User Service with access to the
device credentials so that the users can be
authenticated before they are connected to the network.
Where is it used: configuring security on home
networks, office etc.
Pros & Cons: It provides a better and stronger user
authentication like RADIUS to authenticate the user. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

What is WPA
•It is a security protocol which has been for creating a
secured wireless network.
•They tend to offer the improvement with handling
security keys and working on the systems on the
beginning and end of data transfer. (Linkola et al.,
2016).
•The standards are set for using the temporal key
integrity protocol that prevents the intruders from
creating own encryption key to match by secured
network.
•It is a security protocol which has been for creating a
secured wireless network.
•They tend to offer the improvement with handling
security keys and working on the systems on the
beginning and end of data transfer. (Linkola et al.,
2016).
•The standards are set for using the temporal key
integrity protocol that prevents the intruders from
creating own encryption key to match by secured
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
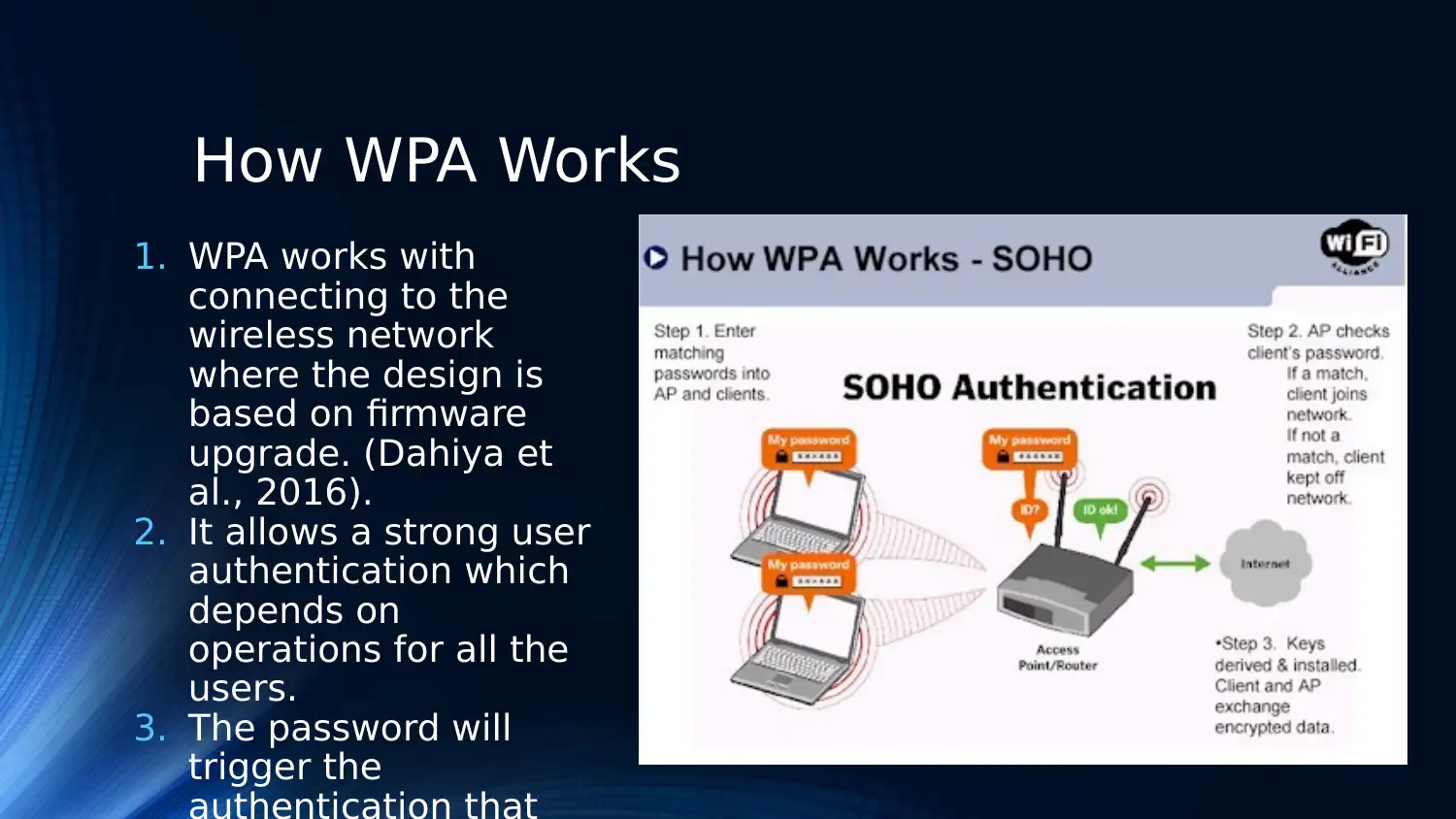
How WPA Works
1. WPA works with
connecting to the
wireless network
where the design is
based on firmware
upgrade. (Dahiya et
al., 2016).
2. It allows a strong user
authentication which
depends on
operations for all the
users.
3. The password will
trigger the
1. WPA works with
connecting to the
wireless network
where the design is
based on firmware
upgrade. (Dahiya et
al., 2016).
2. It allows a strong user
authentication which
depends on
operations for all the
users.
3. The password will
trigger the

What forms of communication is it
used in
•It is used in Wi-Fi Wireless Communication
•Extensible Authentication Protocol (EAP)
•wired communications
•Routers, web servers, and BSs.
•Prepaid telephone services
•Email
•Interactive chat, communication
•Games
used in
•It is used in Wi-Fi Wireless Communication
•Extensible Authentication Protocol (EAP)
•wired communications
•Routers, web servers, and BSs.
•Prepaid telephone services
•Interactive chat, communication
•Games
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Advantages of WPA
a. It is simple to use
b. A proper mobility is also ensured.
c. The personalized forms.
d. Easy to carry and handle. (Zhan et al., 2016)
e. The increased sales have made it more demanding
for the people.
f. Time saving as well.
a. It is simple to use
b. A proper mobility is also ensured.
c. The personalized forms.
d. Easy to carry and handle. (Zhan et al., 2016)
e. The increased sales have made it more demanding
for the people.
f. Time saving as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Disadvantages of WPA
a. It tends to consume more of battery life.
b. There are very small screens for the display and here
the speed of access is also a major disadvantage.
c. There are issues related to the pricing and availability
d. A major lack is in the user habit (Dahiya et al., 2016).
e. less memory.
a. It tends to consume more of battery life.
b. There are very small screens for the display and here
the speed of access is also a major disadvantage.
c. There are issues related to the pricing and availability
d. A major lack is in the user habit (Dahiya et al., 2016).
e. less memory.

Comparison to other security
technologies
a. Wired Equivalent Privacy: It works on 802.11 with
handling the easy hacking due to the 24 bit initiation
vector and weak authentication. Less used.
b. WPA (Wi-Fi Protected Access): It includes the
standards to address the major flaws of WEP where
the personal and enterprise is covered in this.
c. WPA2: It woks on the current standards and new
hardware.
technologies
a. Wired Equivalent Privacy: It works on 802.11 with
handling the easy hacking due to the 24 bit initiation
vector and weak authentication. Less used.
b. WPA (Wi-Fi Protected Access): It includes the
standards to address the major flaws of WEP where
the personal and enterprise is covered in this.
c. WPA2: It woks on the current standards and new
hardware.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The future of WPA
a. It has been effective for Advanced Encryption
Standard AES encryption is set with the Cipher Block
Chaining Message Authentication Code Protocol (CCMP)
in Counter Mode.
b. The CCMP tends to generate a message with the
integrity code with non-repudiation and integrity.
c. It also offers a higher level of security with stronger
encryption with creation of unique session keys on every
association to the client.
a. It has been effective for Advanced Encryption
Standard AES encryption is set with the Cipher Block
Chaining Message Authentication Code Protocol (CCMP)
in Counter Mode.
b. The CCMP tends to generate a message with the
integrity code with non-repudiation and integrity.
c. It also offers a higher level of security with stronger
encryption with creation of unique session keys on every
association to the client.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusions
•WAP works on authentication and key distribution with
home users and small business. (Au et al., 2016).
•The 4-way handshake helps in authenticating the client
access point, establishing and installing the TKIP
encryption keys.
•WAP works on authentication and key distribution with
home users and small business. (Au et al., 2016).
•The 4-way handshake helps in authenticating the client
access point, establishing and installing the TKIP
encryption keys.

References
•Zhan, G. and Wong, A.H.K., 2017, January. Consumer
Adoption of Wi-Fi Network: The Role of Security Knowledge,
Perceived Threat and Security Measures. In Proceedings of
the 8th International Conference on E-Education, E-
Business, E-Management and E-Learning(pp. 1-5). ACM.
•Dahiya, M. and Gill, S., 2016. Performance Evaluation of
Feed Forward Neural Network for Wired Equivalent
Privacy/Wi-Fi Protected Access Protocols. Indian Journal of
Science and Technology, 9(31).
•Linkola, J.P., Caldwell, C.E. and Hassan, O., T-Mobile Usa,
Inc., 2016. System and method for selectively provisioning
telecommunications services between an access point and a
telecommunications network using a subscriber identifier.
U.S. Patent 9,363,740.
•
•Zhan, G. and Wong, A.H.K., 2017, January. Consumer
Adoption of Wi-Fi Network: The Role of Security Knowledge,
Perceived Threat and Security Measures. In Proceedings of
the 8th International Conference on E-Education, E-
Business, E-Management and E-Learning(pp. 1-5). ACM.
•Dahiya, M. and Gill, S., 2016. Performance Evaluation of
Feed Forward Neural Network for Wired Equivalent
Privacy/Wi-Fi Protected Access Protocols. Indian Journal of
Science and Technology, 9(31).
•Linkola, J.P., Caldwell, C.E. and Hassan, O., T-Mobile Usa,
Inc., 2016. System and method for selectively provisioning
telecommunications services between an access point and a
telecommunications network using a subscriber identifier.
U.S. Patent 9,363,740.
•
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





