Implementing Secure Communication with TLS/SSL Protocols
VerifiedAdded on 2020/04/13
|15
|2543
|38
AI Summary
This report investigates the intricacies of implementing SSL/TLS protocols to establish secure communication channels across computer networks. The analysis begins with a historical perspective on SSL's evolution into TLS, highlighting the essential cryptographic mechanisms employed by these protocols. A critical examination of public-key cryptography is conducted to understand its significance in facilitating secure key exchanges and data encryption. Furthermore, the paper addresses common threats like man-in-the-middle attacks, exploring preventive strategies embedded within SSL/TLS frameworks. Practical implementation aspects are illustrated with references to contemporary tools such as BOSS (Building Operating System Services) that utilize these protocols for enhanced security. The assignment encapsulates theoretical concepts alongside real-world applications, demonstrating how SSL/TLS contribute to robust network security.

Running head: OPERATING SYSTEM AND CONCURRENCY
Operating System and Concurrency
Name of the student:
Name of the University:
Author note:
Operating System and Concurrency
Name of the student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATING SYSTEM AND CONCURRENCY
Table of Contents
2.5 Program Report..........................................................................................................................3
1. The Tunnel Program................................................................................................................3
A..............................................................................................................................................3
B...............................................................................................................................................3
C...............................................................................................................................................3
D..............................................................................................................................................4
3. OS Theory and Concepts.............................................................................................................5
2. OS Abstraction and Process Management...............................................................................5
A..............................................................................................................................................5
B...............................................................................................................................................5
3. Security....................................................................................................................................7
A..............................................................................................................................................7
B...............................................................................................................................................7
C...............................................................................................................................................8
Appendix 1.....................................................................................................................................10
Table of Contents
2.5 Program Report..........................................................................................................................3
1. The Tunnel Program................................................................................................................3
A..............................................................................................................................................3
B...............................................................................................................................................3
C...............................................................................................................................................3
D..............................................................................................................................................4
3. OS Theory and Concepts.............................................................................................................5
2. OS Abstraction and Process Management...............................................................................5
A..............................................................................................................................................5
B...............................................................................................................................................5
3. Security....................................................................................................................................7
A..............................................................................................................................................7
B...............................................................................................................................................7
C...............................................................................................................................................8
Appendix 1.....................................................................................................................................10

OPERATING SYSTEM AND CONCURRENCY
2.5 Program Report
1. The Tunnel Program
A.
A monitor is a high-level process of abstraction, which gives an effective and convenient
mechanism for process synchronization. It encourages that at a time, only a single process can
remain active in the monitor. This is known as mutual exclusion. This program uses monitor to
ensure that no two cars travel in opposite direction in the tunnel at the same time.
B.
Mutex is used in this process. It creates a monitor (Hung, Chauhan and Garg 2016). The
monitor, with the help of pthread library functions like lock(), cond_wait(), cond_signal() and
unlock() ensures that no two cars travel in opposite direction in the tunnel at the same time.
Whenever an approaching car encounters a car already inside the tunnel travelling in the opposite
direction, it calls the wait() and the thread goes to halt until the signal() is passed on condition
that opposite direction’s thread count is zero. Assertion is also made to ensure the condition is
satisfied throughout the program.
C.
Whenever the thread count on the same direction is found to be 3, the cond_wait() is
called by locking on to the mutex. This thread is only allowed to proceed when one of the
threads is released in the tunnel_exit(). The assertion made is ‘assert(n_in_tunnel[dir] <= 3);’.
2.5 Program Report
1. The Tunnel Program
A.
A monitor is a high-level process of abstraction, which gives an effective and convenient
mechanism for process synchronization. It encourages that at a time, only a single process can
remain active in the monitor. This is known as mutual exclusion. This program uses monitor to
ensure that no two cars travel in opposite direction in the tunnel at the same time.
B.
Mutex is used in this process. It creates a monitor (Hung, Chauhan and Garg 2016). The
monitor, with the help of pthread library functions like lock(), cond_wait(), cond_signal() and
unlock() ensures that no two cars travel in opposite direction in the tunnel at the same time.
Whenever an approaching car encounters a car already inside the tunnel travelling in the opposite
direction, it calls the wait() and the thread goes to halt until the signal() is passed on condition
that opposite direction’s thread count is zero. Assertion is also made to ensure the condition is
satisfied throughout the program.
C.
Whenever the thread count on the same direction is found to be 3, the cond_wait() is
called by locking on to the mutex. This thread is only allowed to proceed when one of the
threads is released in the tunnel_exit(). The assertion made is ‘assert(n_in_tunnel[dir] <= 3);’.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPERATING SYSTEM AND CONCURRENCY
This ensures that there will never be more than 3 cars in the same direction inside the tunnel, or
otherwise the program will exit with an error message.
D.
A deadlock is a situation where one or more processes keep waiting for shared resources
whereas they are being continually accessed by other processes. Here, it is made sure that no
more than 6 cars can travel in a direction through the tunnel, if the waitingFlag is made true. This
takes away resources from the process of a particular direction by making it to wait on condition.
Further it grants access to the opposite process and locks on to the tunnel mutex. Assertions is
also made to ensure the condition is satisfied throughout the program.
This ensures that there will never be more than 3 cars in the same direction inside the tunnel, or
otherwise the program will exit with an error message.
D.
A deadlock is a situation where one or more processes keep waiting for shared resources
whereas they are being continually accessed by other processes. Here, it is made sure that no
more than 6 cars can travel in a direction through the tunnel, if the waitingFlag is made true. This
takes away resources from the process of a particular direction by making it to wait on condition.
Further it grants access to the opposite process and locks on to the tunnel mutex. Assertions is
also made to ensure the condition is satisfied throughout the program.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATING SYSTEM AND CONCURRENCY
3. OS Theory and Concepts
2. OS Abstraction and Process Management
A.
A Hardware Abstraction Layer or HAL is a group of codes that serves as an abstraction
layer between the computer’s hardware and software. Its main purpose is to act as a device driver
interface that helps the software modules to interact with the hardware. A computer may
integrate the HAL into the OS kernel or the respective device drivers in order to provide a
uniform hardware interaction interface for the applications. This helps the OS to operate
regardless of the hardware configuration beneath (Dawson-Haggerty et al. 2013).
Numerous processors, devices, disks and much more are now an integrated and important
part of the modern computing system. It is therefore the Operating System’s task to manage their
allocation. The allocation is however not just random. The OS needs to uniformly and orderly
allocate these resources to the processes that seek for them (Silberschatz et al. 2012).
LINUX, Mac OS, Windows NT and 2000 are few examples of Operating Systems that
act as HAL and a Resource Manager as well.
B.
The Operating System follows the steps below in order to achieve context switching
between processes:
3. OS Theory and Concepts
2. OS Abstraction and Process Management
A.
A Hardware Abstraction Layer or HAL is a group of codes that serves as an abstraction
layer between the computer’s hardware and software. Its main purpose is to act as a device driver
interface that helps the software modules to interact with the hardware. A computer may
integrate the HAL into the OS kernel or the respective device drivers in order to provide a
uniform hardware interaction interface for the applications. This helps the OS to operate
regardless of the hardware configuration beneath (Dawson-Haggerty et al. 2013).
Numerous processors, devices, disks and much more are now an integrated and important
part of the modern computing system. It is therefore the Operating System’s task to manage their
allocation. The allocation is however not just random. The OS needs to uniformly and orderly
allocate these resources to the processes that seek for them (Silberschatz et al. 2012).
LINUX, Mac OS, Windows NT and 2000 are few examples of Operating Systems that
act as HAL and a Resource Manager as well.
B.
The Operating System follows the steps below in order to achieve context switching
between processes:
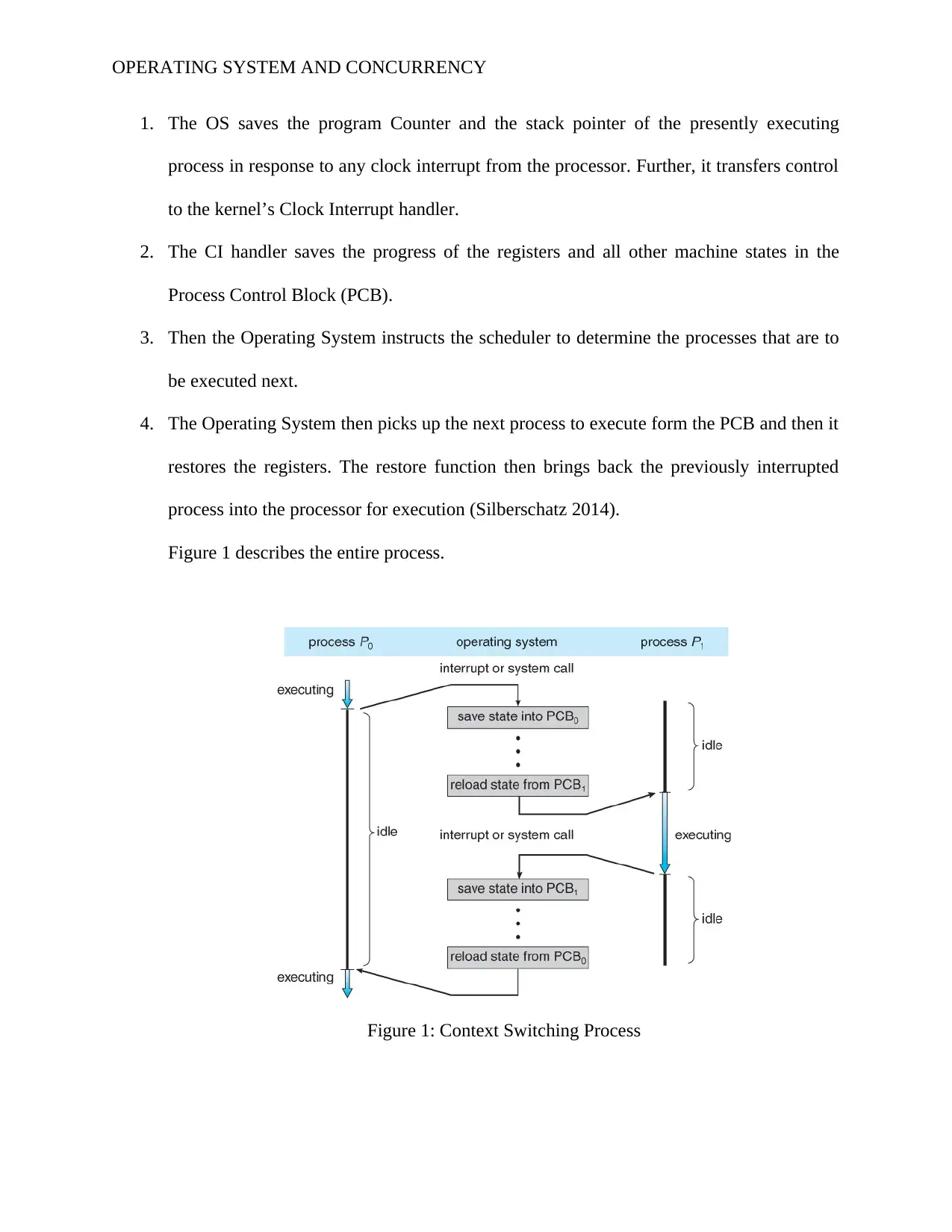
OPERATING SYSTEM AND CONCURRENCY
1. The OS saves the program Counter and the stack pointer of the presently executing
process in response to any clock interrupt from the processor. Further, it transfers control
to the kernel’s Clock Interrupt handler.
2. The CI handler saves the progress of the registers and all other machine states in the
Process Control Block (PCB).
3. Then the Operating System instructs the scheduler to determine the processes that are to
be executed next.
4. The Operating System then picks up the next process to execute form the PCB and then it
restores the registers. The restore function then brings back the previously interrupted
process into the processor for execution (Silberschatz 2014).
Figure 1 describes the entire process.
Figure 1: Context Switching Process
1. The OS saves the program Counter and the stack pointer of the presently executing
process in response to any clock interrupt from the processor. Further, it transfers control
to the kernel’s Clock Interrupt handler.
2. The CI handler saves the progress of the registers and all other machine states in the
Process Control Block (PCB).
3. Then the Operating System instructs the scheduler to determine the processes that are to
be executed next.
4. The Operating System then picks up the next process to execute form the PCB and then it
restores the registers. The restore function then brings back the previously interrupted
process into the processor for execution (Silberschatz 2014).
Figure 1 describes the entire process.
Figure 1: Context Switching Process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPERATING SYSTEM AND CONCURRENCY
3. Security
A.
The Secure Socket Layer (SSL) ensures that the following security concerns are not
violated:
Protection of data in the midst of the transmission between processes or web server OS.
Maintaining data authenticity while the processes are communicating.
The Secure Socket Layer provides a process for the encryption and authentication of data
being communicated between processes running on client and server OS. The SSL technology
makes use of both Public and Symmetric Key in order to secure the connection in between the
two machines, servers or processes. The SSL further has two sup-protocols namely the
Handshake Protocol and the Record Protocol.
The Handshake Protocol explains what cryptographic systems are to be used during
communication. It also deals with the negotiation between hosts or processes regarding the
exchange of keys as cryptographic material or for ensuring the authentication of data in
transmission (Bhargavan et al. 2013).
The Record Protocol states how the communicating processes would exchange data using
the SSL. This specifies how the data is needed to be encrypted, verified and decrypted back on
receive (Panwar and Kumar 2012).
B.
3. Security
A.
The Secure Socket Layer (SSL) ensures that the following security concerns are not
violated:
Protection of data in the midst of the transmission between processes or web server OS.
Maintaining data authenticity while the processes are communicating.
The Secure Socket Layer provides a process for the encryption and authentication of data
being communicated between processes running on client and server OS. The SSL technology
makes use of both Public and Symmetric Key in order to secure the connection in between the
two machines, servers or processes. The SSL further has two sup-protocols namely the
Handshake Protocol and the Record Protocol.
The Handshake Protocol explains what cryptographic systems are to be used during
communication. It also deals with the negotiation between hosts or processes regarding the
exchange of keys as cryptographic material or for ensuring the authentication of data in
transmission (Bhargavan et al. 2013).
The Record Protocol states how the communicating processes would exchange data using
the SSL. This specifies how the data is needed to be encrypted, verified and decrypted back on
receive (Panwar and Kumar 2012).
B.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATING SYSTEM AND CONCURRENCY
As the term Symmetric suggests, symmetry is maintained in the cryptography process
that is run by the Symmetric Keys. In this system, both the senders and receivers share a
common or single key for both encryption and decryption. This system is faster and simpler to
implement. However, the key must be exchanged between the processes in a secured and secret
manner. They are also known as secret-key cryptography.
On the other hand, Public key encryption makes use of two keys, a public key that is
needed for the encryption purpose and another private key to decrypt those data or messages.
The drawback of the symmetric key process is however overcome in this process. The public key
can be transmitted without necessary security measures and the private decryption key needs no
transmission at all, as this is only necessary at the receiver end. It is also known as Asymmetric
Cryptography (Salomaa 2013).
Data Encryption Standard (DES) is the most common Symmetric Key system and
Cramer–Shoup cryptosystem is an example of Public Key cryptography.
C.
A man-in-the-middle attack, commonly abbreviated as MiTM attack is a type of cyber
threat, which involves malicious actors or processes who inserts themselves into the system
while there is a conversation going on between two processes. Through this attack, the
intermediate actors intercept, send and receive data that was not meant for them.
MiTM attacks threat the SSL system in way where it is unpredictable. The Wrap Up
MiTM attack on an SSL is one of the deadliest attacks of all. It harms the network or the process
communication by converting the most secured servers into a completely insecure one. No party
would ever know if the encryption key has got stolen as the attacker keeps sending fake keys to
As the term Symmetric suggests, symmetry is maintained in the cryptography process
that is run by the Symmetric Keys. In this system, both the senders and receivers share a
common or single key for both encryption and decryption. This system is faster and simpler to
implement. However, the key must be exchanged between the processes in a secured and secret
manner. They are also known as secret-key cryptography.
On the other hand, Public key encryption makes use of two keys, a public key that is
needed for the encryption purpose and another private key to decrypt those data or messages.
The drawback of the symmetric key process is however overcome in this process. The public key
can be transmitted without necessary security measures and the private decryption key needs no
transmission at all, as this is only necessary at the receiver end. It is also known as Asymmetric
Cryptography (Salomaa 2013).
Data Encryption Standard (DES) is the most common Symmetric Key system and
Cramer–Shoup cryptosystem is an example of Public Key cryptography.
C.
A man-in-the-middle attack, commonly abbreviated as MiTM attack is a type of cyber
threat, which involves malicious actors or processes who inserts themselves into the system
while there is a conversation going on between two processes. Through this attack, the
intermediate actors intercept, send and receive data that was not meant for them.
MiTM attacks threat the SSL system in way where it is unpredictable. The Wrap Up
MiTM attack on an SSL is one of the deadliest attacks of all. It harms the network or the process
communication by converting the most secured servers into a completely insecure one. No party
would ever know if the encryption key has got stolen as the attacker keeps sending fake keys to

OPERATING SYSTEM AND CONCURRENCY
the receiver. This is known as SSL Hijacking. Another threat is the SSL Stripping, where the
attacker rips off the encryption and sends the unencrypted version to the receiver (Pateriya and
Kumar 2012).
The steps to stay secure against such attacks are:
Upgrade System & Server Configurations.
Spot HTTP Secured (HTTPS).
Avoid accessing open WiFi hotspots.
Strengthen personal system security.
the receiver. This is known as SSL Hijacking. Another threat is the SSL Stripping, where the
attacker rips off the encryption and sends the unencrypted version to the receiver (Pateriya and
Kumar 2012).
The steps to stay secure against such attacks are:
Upgrade System & Server Configurations.
Spot HTTP Secured (HTTPS).
Avoid accessing open WiFi hotspots.
Strengthen personal system security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPERATING SYSTEM AND CONCURRENCY
Appendix 1
#include <assert.h>
#include <pthread.h>
#include <semaphore.h>
#include "tunnel_controller.h"
#include "console.h"
static int n_in_tunnel[2];
static unsigned long n_total[2];
static int countSame=3, flagOppo=1, temp=3;
static int rc, waitingFlag, passing;
static pthread_mutex_t tunnel = PTHREAD_MUTEX_INITIALIZER;
static pthread_cond_t oppo = PTHREAD_COND_INITIALIZER;
static pthread_cond_t same = PTHREAD_COND_INITIALIZER;
/**
* @brief controls entry to the tunnel
* @param dir the direction of travel when entering
*/
void enter_tunnel(direction_t dir) {
rc = pthread_mutex_init(&same, NULL) ;
assert ( rc == 0 ) ;
Appendix 1
#include <assert.h>
#include <pthread.h>
#include <semaphore.h>
#include "tunnel_controller.h"
#include "console.h"
static int n_in_tunnel[2];
static unsigned long n_total[2];
static int countSame=3, flagOppo=1, temp=3;
static int rc, waitingFlag, passing;
static pthread_mutex_t tunnel = PTHREAD_MUTEX_INITIALIZER;
static pthread_cond_t oppo = PTHREAD_COND_INITIALIZER;
static pthread_cond_t same = PTHREAD_COND_INITIALIZER;
/**
* @brief controls entry to the tunnel
* @param dir the direction of travel when entering
*/
void enter_tunnel(direction_t dir) {
rc = pthread_mutex_init(&same, NULL) ;
assert ( rc == 0 ) ;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPERATING SYSTEM AND CONCURRENCY
rc = pthread_mutex_init(&oppo, NULL) ;
assert ( rc == 0 ) ;
if(n_in_tunnel[opposite(dir)]==0){ //ensures that there are no cars travelling the tunnel in
the opposite direction.
if(n_in_tunnel[dir]==2){
rc=pthread_mutex_lock(&tunnel); //locks the mutex after the entry of the
3rd car if 2 cars are already travelling in the tunnel.
assert(rc==0);
while(n_in_tunnel[dir]>2){
pthread_cond_wait(&same, tunnel); //thread waits till number of
cars in tunnel is not 2 only by locking onto the 'same' condition.
}
while(passing>=6){
pthread_cond_wait(&oppo, tunnel); //thread waits till number of
cars in tunnel is not less than 6, by locking onto the 'oppo' condition.
}
}
}
else{
rc=pthread_mutex_lock(&tunnel);
(waitingFlag==0) ? passing += n_in_tunnel[opposite(dir)]; //adds the number of
cars in the tunnel travelling in the opposite direction while a car comes and has to wait.
while(n_in_tunnel[opposite(dir)]!=0){
waitingFlag=1; //sets off flag in order to notify waiting state.
pthread_cond_wait(&oppo, tunnel); //thread waits till opposite direction
cars are all out of the tunnel.
rc = pthread_mutex_init(&oppo, NULL) ;
assert ( rc == 0 ) ;
if(n_in_tunnel[opposite(dir)]==0){ //ensures that there are no cars travelling the tunnel in
the opposite direction.
if(n_in_tunnel[dir]==2){
rc=pthread_mutex_lock(&tunnel); //locks the mutex after the entry of the
3rd car if 2 cars are already travelling in the tunnel.
assert(rc==0);
while(n_in_tunnel[dir]>2){
pthread_cond_wait(&same, tunnel); //thread waits till number of
cars in tunnel is not 2 only by locking onto the 'same' condition.
}
while(passing>=6){
pthread_cond_wait(&oppo, tunnel); //thread waits till number of
cars in tunnel is not less than 6, by locking onto the 'oppo' condition.
}
}
}
else{
rc=pthread_mutex_lock(&tunnel);
(waitingFlag==0) ? passing += n_in_tunnel[opposite(dir)]; //adds the number of
cars in the tunnel travelling in the opposite direction while a car comes and has to wait.
while(n_in_tunnel[opposite(dir)]!=0){
waitingFlag=1; //sets off flag in order to notify waiting state.
pthread_cond_wait(&oppo, tunnel); //thread waits till opposite direction
cars are all out of the tunnel.

OPERATING SYSTEM AND CONCURRENCY
}
}
n_in_tunnel[dir] += 1;
if(waitingFlag==1)
passing += 1; //keeps count of the number of cars entering or already in the tunnel
when there is cars waiting in opposite direction.
lcd_write_at(4+dir, 0, "In tunnel (%s) : %2d", (dir == NORTH) ? "NORTH" : "SOUTH",
n_in_tunnel[dir]); //Display
assert(n_in_tunnel[opposite(dir)] == 0); //assert that there are no two cars travelling in
opposite directions.
assert(n_in_tunnel[dir] <= 3); //assert that there are no three cars travelling in same directions.
assert(passing<=6); //assert that there are no more than 6 cars travelling in opposite directions,
while a car is in await.
}
/**
* @brief controls exit from the tunnel
* @param dir the direction of travel when leaving
*/
void exit_tunnel(direction_t dir) {
if(waitingFlag==1){
if(countOppo==6){
}
}
}
n_in_tunnel[dir] += 1;
if(waitingFlag==1)
passing += 1; //keeps count of the number of cars entering or already in the tunnel
when there is cars waiting in opposite direction.
lcd_write_at(4+dir, 0, "In tunnel (%s) : %2d", (dir == NORTH) ? "NORTH" : "SOUTH",
n_in_tunnel[dir]); //Display
assert(n_in_tunnel[opposite(dir)] == 0); //assert that there are no two cars travelling in
opposite directions.
assert(n_in_tunnel[dir] <= 3); //assert that there are no three cars travelling in same directions.
assert(passing<=6); //assert that there are no more than 6 cars travelling in opposite directions,
while a car is in await.
}
/**
* @brief controls exit from the tunnel
* @param dir the direction of travel when leaving
*/
void exit_tunnel(direction_t dir) {
if(waitingFlag==1){
if(countOppo==6){
}
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.