Network Proposal: Implementing Layer 2 & 3 Services for Security
VerifiedAdded on 2023/04/25
|10
|1844
|188
Report
AI Summary
This report proposes a network solution for an organization, focusing on security and performance. It details the implementation of a client-server architecture, VLANs, and a DMZ for enhanced security. The proposal includes technical details for configuring network devices with redundant links, ensuring high availability. It also covers naming conventions, Layer 2 and Layer 3 design considerations, and the use of protocols like Rapid Spanning Tree Protocol and trunking. The report emphasizes the importance of network management and intrusion detection systems for maintaining a secure and efficient network, highlighting the need for redundant links to minimize network failures. Desklib provides access to similar solved assignments and past papers for students.

Running head: NETWORK PROPOSAL PAPER
Network Proposal Paper
Name of the Student
Name of the University
Author’s Note
Network Proposal Paper
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK PROPOSAL PAPER
Executive Summary
Client server architecture is needed to be followed for sharing of information between the
hosts and the servers connected in the local area network. The client server architecture
allows the user to access the same database to store same information and the network is
needed to be subnetted for connecting the servers into different VLAN and improving the
performance of the network. A layer 3 switch is installed in the network and configured as a
core device for connecting with the access level devices and transmitting data traffic in the
network. A DMZ zone is created for the network for adding a layer of security and reduce the
vulnerability of the network.
NETWORK PROPOSAL PAPER
Executive Summary
Client server architecture is needed to be followed for sharing of information between the
hosts and the servers connected in the local area network. The client server architecture
allows the user to access the same database to store same information and the network is
needed to be subnetted for connecting the servers into different VLAN and improving the
performance of the network. A layer 3 switch is installed in the network and configured as a
core device for connecting with the access level devices and transmitting data traffic in the
network. A DMZ zone is created for the network for adding a layer of security and reduce the
vulnerability of the network.

2
NETWORK PROPOSAL PAPER
Table of Contents
Introduction................................................................................................................................3
Network Diagram.......................................................................................................................3
Technical Details........................................................................................................................4
Conclusion..................................................................................................................................6
Bibliography...............................................................................................................................7
NETWORK PROPOSAL PAPER
Table of Contents
Introduction................................................................................................................................3
Network Diagram.......................................................................................................................3
Technical Details........................................................................................................................4
Conclusion..................................................................................................................................6
Bibliography...............................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK PROPOSAL PAPER
Introduction
The report is developed for developing a network solution for the organization and an
analysis is made on the requirement and the current framework of the business organization
for the development of the network solution. The number of hosts and servers connected on
each of the subnet its needed to be identified for development of the IP address plan and
development of the client server architecture for interconnecting each of the department. The
issues and challenges with the client server system is also needed to be identified and the
proposed network solution is audited for enabling discretionary control on the network and
enabling authorization and identification of the users to access the network framework. The
technical details of the network are documented in the report that would help the stakeholders
to identify the protocols and technology used for configuration of the network and increasing
the efficiency of the current network framework of the organization.
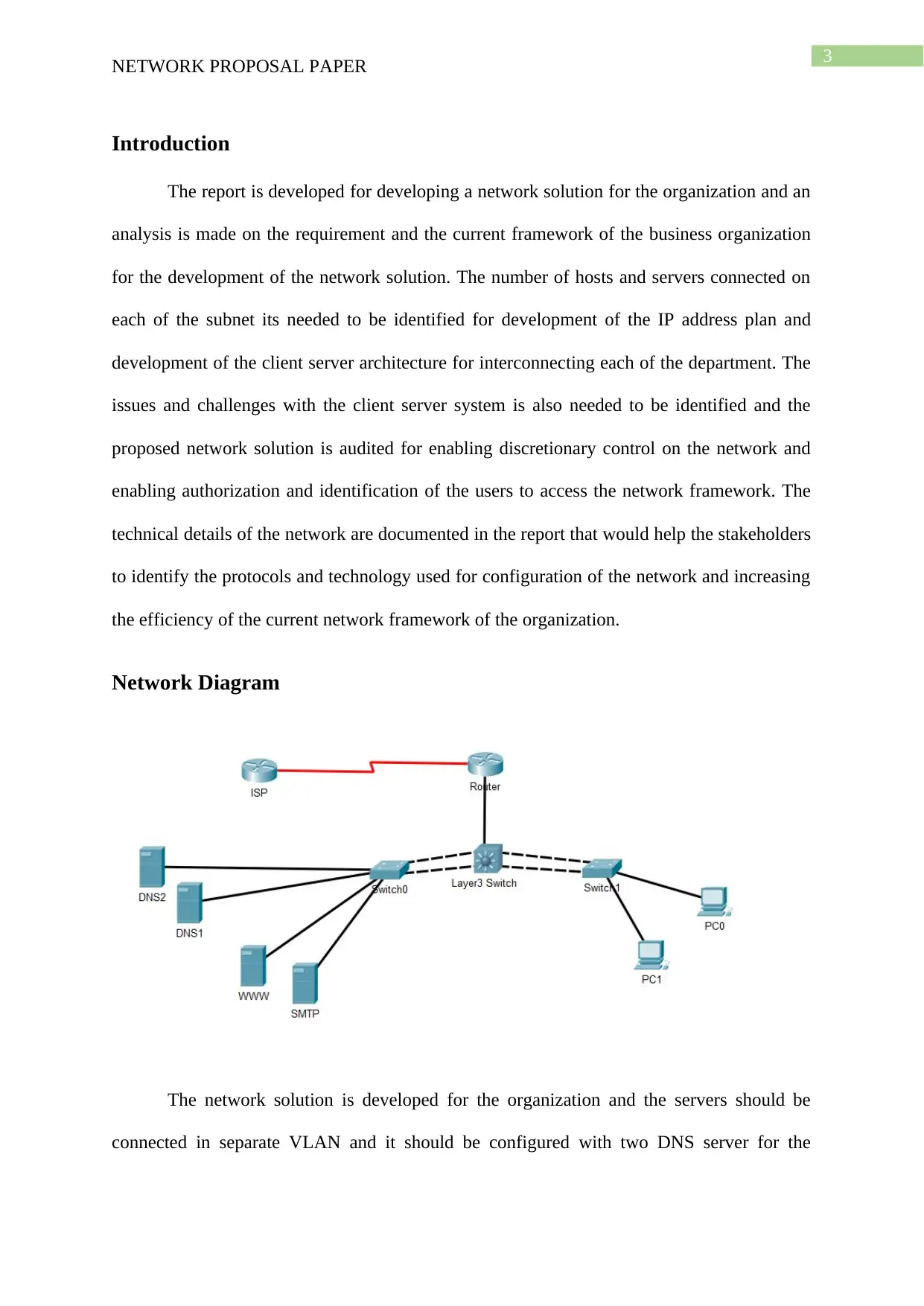
Network Diagram
The network solution is developed for the organization and the servers should be
connected in separate VLAN and it should be configured with two DNS server for the
NETWORK PROPOSAL PAPER
Introduction
The report is developed for developing a network solution for the organization and an
analysis is made on the requirement and the current framework of the business organization
for the development of the network solution. The number of hosts and servers connected on
each of the subnet its needed to be identified for development of the IP address plan and
development of the client server architecture for interconnecting each of the department. The
issues and challenges with the client server system is also needed to be identified and the
proposed network solution is audited for enabling discretionary control on the network and
enabling authorization and identification of the users to access the network framework. The
technical details of the network are documented in the report that would help the stakeholders
to identify the protocols and technology used for configuration of the network and increasing
the efficiency of the current network framework of the organization.
Network Diagram
The network solution is developed for the organization and the servers should be
connected in separate VLAN and it should be configured with two DNS server for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK PROPOSAL PAPER
internal and the external network. A SMTP server should also be configured for the
management of internal communication using email. The links should be configures as
EtherChannel for increasing the availability of bandwidth for each of the VLAN and
increasing the performance of the network. The router is also needed to be configured with
ACL for restricting and allowing access of the users to different parts of the network. The
network is also needed to be verified with pinging from different location before deployment
of the network.
Technical Details
Top Down Approach
Advantages:
The goals and requirement of the organization should be analysed for the
identification of network application requirement and servers for meeting the potential
future needs of the organization.
The network design is needed to be incorporated with the requirement of the
organization
Disadvantages:
It needs initial requirement analysis for determination of specific requirement and
ensuring that the specific service and application has been considered.
It also needs incorporation of the organizational requirement
Bottom Up Approach
Advantages
There is a need of quick response for the design request and facilitating the design
which is based on the previous network design of the organization
NETWORK PROPOSAL PAPER
internal and the external network. A SMTP server should also be configured for the
management of internal communication using email. The links should be configures as
EtherChannel for increasing the availability of bandwidth for each of the VLAN and
increasing the performance of the network. The router is also needed to be configured with
ACL for restricting and allowing access of the users to different parts of the network. The
network is also needed to be verified with pinging from different location before deployment
of the network.
Technical Details
Top Down Approach
Advantages:
The goals and requirement of the organization should be analysed for the
identification of network application requirement and servers for meeting the potential
future needs of the organization.
The network design is needed to be incorporated with the requirement of the
organization
Disadvantages:
It needs initial requirement analysis for determination of specific requirement and
ensuring that the specific service and application has been considered.
It also needs incorporation of the organizational requirement
Bottom Up Approach
Advantages
There is a need of quick response for the design request and facilitating the design
which is based on the previous network design of the organization

5
NETWORK PROPOSAL PAPER
It is a faster approach when compared with top down approach because the
development works on implementation of the project work in the existing
environment.
Disadvantage
It may result in inappropriate design of the network
Using this approach some of the application and services that are necessary may not
be considered and that leads the network design not meeting the requirement of the
organization.
It may be required to be redesigned for aligning the needs of the organization for
meeting the future growth of the organization.
Naming Conventions
Naming conventions should be used for the network device installed in the network
for providing different service to the users connected in the network. The devices should be
named following the name of the department such that the network administrator does not
face any difficulty for troubleshooting the complexity of the network. The switch should be
named with department and floor name of the and the wireless router should be named with
the department.
Layer 2 Design
The design of the network should be made following the VLAN Rapid Spanning Tree
Protocol Design and trunking protocol should be used allowing the switch to transfer the
VLAN information to the other switch connected in the network. The layer three switch
installed in the core layer of the network should be configured with VTP server for
transferring the VLAN information to the client switch connected in the network. IEEE
802.1Q standard should be followed for the wireless network and the router should be
NETWORK PROPOSAL PAPER
It is a faster approach when compared with top down approach because the
development works on implementation of the project work in the existing
environment.
Disadvantage
It may result in inappropriate design of the network
Using this approach some of the application and services that are necessary may not
be considered and that leads the network design not meeting the requirement of the
organization.
It may be required to be redesigned for aligning the needs of the organization for
meeting the future growth of the organization.
Naming Conventions
Naming conventions should be used for the network device installed in the network
for providing different service to the users connected in the network. The devices should be
named following the name of the department such that the network administrator does not
face any difficulty for troubleshooting the complexity of the network. The switch should be
named with department and floor name of the and the wireless router should be named with
the department.
Layer 2 Design
The design of the network should be made following the VLAN Rapid Spanning Tree
Protocol Design and trunking protocol should be used allowing the switch to transfer the
VLAN information to the other switch connected in the network. The layer three switch
installed in the core layer of the network should be configured with VTP server for
transferring the VLAN information to the client switch connected in the network. IEEE
802.1Q standard should be followed for the wireless network and the router should be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK PROPOSAL PAPER
configured with DHCP configuration such that the hosts connected in the VLAN are
automatically allocated with the subnet IP address for the department.
The network design should be made with connecting the network devices with
redundant link such that if any one of the link is broken the network does not collapse and the
second link can be used for reaching the destination address. A guest network should be
created for allowing the visitors to access the network without compromising the network
security.
Conclusion
From the above report it can be concluded that the implementation of the client server
architecture in the current framework of the network helps in meeting the needs of the
organization. It provides service for the management of data traffic in the network and
redundant link is needed to be used for reducing the network failure and increasing
availability of the network. The network is developed with the addition of building block
component and the network is divided into three layers i.e. core, distribution and access layer.
Network management system is needed to be implemented for management of faults and
measuring the performance of the network. An intrusion detection system is needed to be
applied such that it can be used for detection of vulnerability and working on the security
concern for developing the network following the requirement of the organization. The
routers should be configured following the technology and protocols used for the
development of the network framework and the fast Ethernet ports should be sub divided
following the subnet plan and the number of VLANs used for the configuration of the
network.
NETWORK PROPOSAL PAPER
configured with DHCP configuration such that the hosts connected in the VLAN are
automatically allocated with the subnet IP address for the department.
The network design should be made with connecting the network devices with
redundant link such that if any one of the link is broken the network does not collapse and the
second link can be used for reaching the destination address. A guest network should be
created for allowing the visitors to access the network without compromising the network
security.
Conclusion
From the above report it can be concluded that the implementation of the client server
architecture in the current framework of the network helps in meeting the needs of the
organization. It provides service for the management of data traffic in the network and
redundant link is needed to be used for reducing the network failure and increasing
availability of the network. The network is developed with the addition of building block
component and the network is divided into three layers i.e. core, distribution and access layer.
Network management system is needed to be implemented for management of faults and
measuring the performance of the network. An intrusion detection system is needed to be
applied such that it can be used for detection of vulnerability and working on the security
concern for developing the network following the requirement of the organization. The
routers should be configured following the technology and protocols used for the
development of the network framework and the fast Ethernet ports should be sub divided
following the subnet plan and the number of VLANs used for the configuration of the
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK PROPOSAL PAPER
Bibliography
Che, M., Kuboki, T., & Kato, K. (2017, November). Proposal of cost-efficient and low-
complexity platform for software defined visible light communication. In Microoptics
Conference (MOC), 2017 22nd (pp. 330-331). IEEE.
Chen, C., Song, X., & Jiang, S. (2018, November). Focal Loss for Region Proposal Network.
In Chinese Conference on Pattern Recognition and Computer Vision (PRCV) (pp.
368-380). Springer, Cham.
Chen, G., Zou, Y., & Zhang, C. (2019, January). STMP: Spatial Temporal Multi-level
Proposal Network for Activity Detection. In International Conference on Multimedia
Modeling(pp. 29-41). Springer, Cham.
Dai, J., He, K., Li, Y., Ren, S., & Sun, J. (2016, October). Instance-sensitive fully
convolutional networks. In European Conference on Computer Vision (pp. 534-549).
Springer, Cham.
Dai, J., Li, Y., He, K., & Sun, J. (2016). R-fcn: Object detection via region-based fully
convolutional networks. In Advances in neural information processing systems (pp.
379-387).
Han, G., Zhang, X., & Li, C. (2017, November). Revisiting Faster R-CNN: A Deeper Look at
Region Proposal Network. In International Conference on Neural Information
Processing(pp. 14-24). Springer, Cham.
Kong, T., Yao, A., Chen, Y., & Sun, F. (2016). Hypernet: Towards accurate region proposal
generation and joint object detection. In Proceedings of the IEEE conference on
computer vision and pattern recognition (pp. 845-853).
NETWORK PROPOSAL PAPER
Bibliography
Che, M., Kuboki, T., & Kato, K. (2017, November). Proposal of cost-efficient and low-
complexity platform for software defined visible light communication. In Microoptics
Conference (MOC), 2017 22nd (pp. 330-331). IEEE.
Chen, C., Song, X., & Jiang, S. (2018, November). Focal Loss for Region Proposal Network.
In Chinese Conference on Pattern Recognition and Computer Vision (PRCV) (pp.
368-380). Springer, Cham.
Chen, G., Zou, Y., & Zhang, C. (2019, January). STMP: Spatial Temporal Multi-level
Proposal Network for Activity Detection. In International Conference on Multimedia
Modeling(pp. 29-41). Springer, Cham.
Dai, J., He, K., Li, Y., Ren, S., & Sun, J. (2016, October). Instance-sensitive fully
convolutional networks. In European Conference on Computer Vision (pp. 534-549).
Springer, Cham.
Dai, J., Li, Y., He, K., & Sun, J. (2016). R-fcn: Object detection via region-based fully
convolutional networks. In Advances in neural information processing systems (pp.
379-387).
Han, G., Zhang, X., & Li, C. (2017, November). Revisiting Faster R-CNN: A Deeper Look at
Region Proposal Network. In International Conference on Neural Information
Processing(pp. 14-24). Springer, Cham.
Kong, T., Yao, A., Chen, Y., & Sun, F. (2016). Hypernet: Towards accurate region proposal
generation and joint object detection. In Proceedings of the IEEE conference on
computer vision and pattern recognition (pp. 845-853).

8
NETWORK PROPOSAL PAPER
Li, S., Takahashi, S., Yamada, K., Takagi, M., & Sasaki, J. (2017, September). A Proposal of
the Tourism Course Recommendation System (TCRS) for Foreign Tourists by Using
Photo Data in Social Network Service. In New Trends in Intelligent Software
Methodologies, Tools and Techniques: Proceedings of the 16th International
Conference SoMeT_17(Vol. 297, p. 331). IOS Press.
Liang, X., Lin, L., Wei, Y., Shen, X., Yang, J., & Yan, S. (2018). Proposal-Free Network for
Instance-Level Object Segmentation. IEEE Transactions on Pattern Analysis and
Machine Intelligence, 40(12), 2978-2991.
Ren, S., He, K., Girshick, R., & Sun, J. (2015). Faster r-cnn: Towards real-time object
detection with region proposal networks. In Advances in neural information
processing systems (pp. 91-99).
Ren, S., He, K., Girshick, R., & Sun, J. (2017). Faster R-CNN: towards real-time object
detection with region proposal networks. IEEE Transactions on Pattern Analysis &
Machine Intelligence, (6), 1137-1149.
Tian, Z., Huang, W., He, T., He, P., & Qiao, Y. (2016, October). Detecting text in natural
image with connectionist text proposal network. In European conference on computer
vision (pp. 56-72). Springer, Cham.
Wang, C., Zheng, H., Yu, Z., Zheng, Z., Gu, Z., & Zheng, B. (2018). Discriminative Region
Proposal Adversarial Networks for High-Quality Image-to-Image Translation.
In Proceedings of the European Conference on Computer Vision (ECCV) (pp. 770-
785).
Xia, C., Zhang, C., Yang, T., Li, Y., Du, N., Wu, X., ... & Philip, S. Y. (2018). Multi-Grained
Entity Proposal Network for Named Entity Recognition.
NETWORK PROPOSAL PAPER
Li, S., Takahashi, S., Yamada, K., Takagi, M., & Sasaki, J. (2017, September). A Proposal of
the Tourism Course Recommendation System (TCRS) for Foreign Tourists by Using
Photo Data in Social Network Service. In New Trends in Intelligent Software
Methodologies, Tools and Techniques: Proceedings of the 16th International
Conference SoMeT_17(Vol. 297, p. 331). IOS Press.
Liang, X., Lin, L., Wei, Y., Shen, X., Yang, J., & Yan, S. (2018). Proposal-Free Network for
Instance-Level Object Segmentation. IEEE Transactions on Pattern Analysis and
Machine Intelligence, 40(12), 2978-2991.
Ren, S., He, K., Girshick, R., & Sun, J. (2015). Faster r-cnn: Towards real-time object
detection with region proposal networks. In Advances in neural information
processing systems (pp. 91-99).
Ren, S., He, K., Girshick, R., & Sun, J. (2017). Faster R-CNN: towards real-time object
detection with region proposal networks. IEEE Transactions on Pattern Analysis &
Machine Intelligence, (6), 1137-1149.
Tian, Z., Huang, W., He, T., He, P., & Qiao, Y. (2016, October). Detecting text in natural
image with connectionist text proposal network. In European conference on computer
vision (pp. 56-72). Springer, Cham.
Wang, C., Zheng, H., Yu, Z., Zheng, Z., Gu, Z., & Zheng, B. (2018). Discriminative Region
Proposal Adversarial Networks for High-Quality Image-to-Image Translation.
In Proceedings of the European Conference on Computer Vision (ECCV) (pp. 770-
785).
Xia, C., Zhang, C., Yang, T., Li, Y., Du, N., Wu, X., ... & Philip, S. Y. (2018). Multi-Grained
Entity Proposal Network for Named Entity Recognition.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK PROPOSAL PAPER
NETWORK PROPOSAL PAPER
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




