Comprehensive Report on Secure Encryption Technologies and Security
VerifiedAdded on 2024/05/17
|15
|586
|240
Report
AI Summary
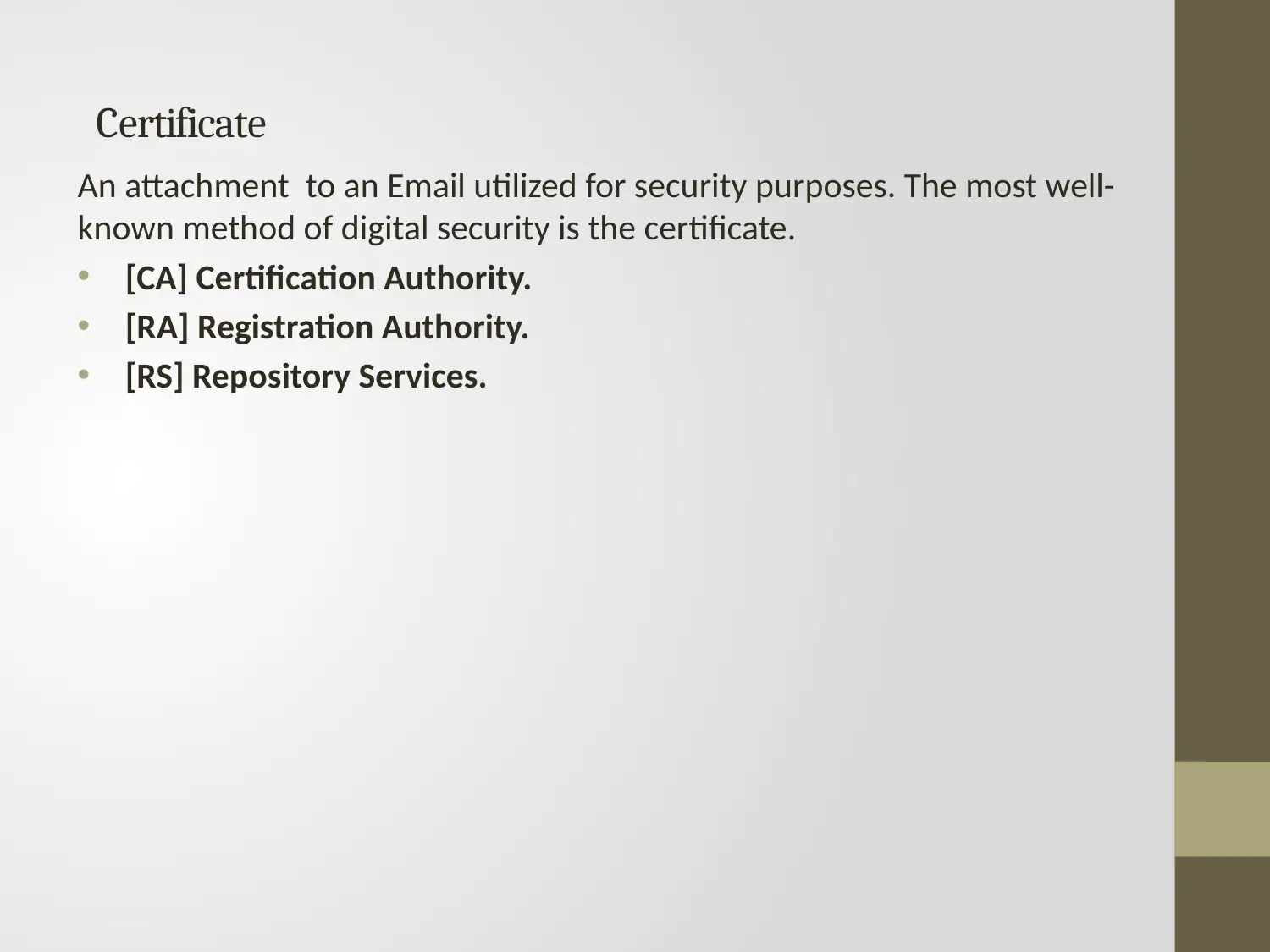
This report provides an overview of secure encryption technologies, focusing on certificates, asymmetric and symmetric key algorithms, and encryption strength. It discusses various encryption types, including secret key, public key, and hash key cryptography, along with functions like access control permissions and digital signatures. The report also examines message digest algorithms, public key infrastructure, and outline replay security. Key security threats such as eavesdropping, data interception, and falsification are identified, followed by an explanation of the Transmission Control Protocol and its layers. Finally, the document outlines security issues related to administration, compliance, vulnerability management, and legal aspects, as well as challenges posed by the broadcast nature of wireless communication and limitations in computational power. The report also touches upon wired equivalent privacy, Wi-Fi protected access, and other relevant topics.
1 out of 15

















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)