Network Security Design: Threats, Devices, and Algorithms
VerifiedAdded on 2020/06/05
|14
|2642
|221
Report
AI Summary
This report provides a comprehensive overview of secure network design, addressing the evolving landscape of B2B interactions and the challenges posed by mobile devices, Web 2.0, and smart computing. It delves into various network security threats, including worms, Trojans, and denial-of-service attacks, categorizing them as resource and logic attacks. The report examines network security devices like firewalls, VPNs, and intrusion detection systems, providing a detailed classification of these devices. It further explores the components needed to build a secure network, such as cables, routers, and firewalls. The report then classifies network security devices into various categories and also covers cryptographic algorithm metrics, discussing authentication, non-repudiation, privacy, and integrity. Finally, the report highlights symmetric cryptography, the most common form of cryptography, and its use in securing data transmission.

Secure Network Design
Submitted By:
Date:
Submitted By:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Several security and danger professionals seek in order to implement fine-grained defense controls that
period traditional boundaries plus perimeters for their institutions. Businesses today have got global
features and lots of trusted partners that will constantly access their own business resources. Issue
weren’t challenging sufficient, partners can now gain access to corporate information plus resources via
completely new such as mobile devices, Web and methods 2.0 technologies. In addition, the particular
advancement of Intelligent Important Infrastructure technology that are vertical, particular, and that
increase information-sharing between bodily products, such as sensors plus core IT techniques, will
create a totally new companion atmosphere. With the developing nature of business-to-business (B2B)
interactions, the safety controls need to progress as well. Forrester views four tiers associated with
access control rising in the B2B environment: application, information, system, and physical. Safety
professionals need to consist of these access settings in their strategy to create a comprehensive B2B
protection structures.
Several security and danger professionals seek in order to implement fine-grained defense controls that
period traditional boundaries plus perimeters for their institutions. Businesses today have got global
features and lots of trusted partners that will constantly access their own business resources. Issue
weren’t challenging sufficient, partners can now gain access to corporate information plus resources via
completely new such as mobile devices, Web and methods 2.0 technologies. In addition, the particular
advancement of Intelligent Important Infrastructure technology that are vertical, particular, and that
increase information-sharing between bodily products, such as sensors plus core IT techniques, will
create a totally new companion atmosphere. With the developing nature of business-to-business (B2B)
interactions, the safety controls need to progress as well. Forrester views four tiers associated with
access control rising in the B2B environment: application, information, system, and physical. Safety
professionals need to consist of these access settings in their strategy to create a comprehensive B2B
protection structures.

Introduction
The current B2B interactions shall no longer be bounded merely by a conventional network perimeter or
even limited to traditional techniques of data trade and communication. The brand new B2B
atmosphere associated with partners, companies, providers, and extra 3rd parties is, actually
unbounded, and details flows much more freely. As a total outcome, many of our traditional regulates
to secure B2B connections are no longer adequate. Listed below are key inflection factors that challenge
the current B2B security structures: · Mobile devices plus Web 2. 0 have got introduced new methods to
conduct business relationships. Companies are interacting with their particular partners in a lot more ad
hoc however cost effective way. It’s not unusual today to have corporation transactions and interactions
“on the go” with the use of mobile items and interactive press using Web 2.0 applications. 1 The
particular dynamic character from the content poses brand new risks that are particular to Web plus
application security. Cloud marketing promotions are a new way to broaden applications to B2B
partners. The particular cloud is a persuasive selection that your corporation can’t ignore intended for
extending resources in order to B2B clients, yet as a risk plus security professional, it is your job to
ensure that protection and personal privacy worries are recognized. · Smart Computing may breed more
complex interactions. Smart Computing can be the particular new era of integrated equipment, software
program, and system techniques that provide the systems with current awareness of the real world. A
few Smart Computing technologies will help several from the public and personal initiatives around the
world aimed at making important infrastructure of the towns smarter. For example, Wise Grid and
Sensible City projects which make use of Smart Processing technologies are rolling out there across the
world. 4 With all the advent of these sensible technologies, businesses may have complex and pervasive
partner relationships, many of them nontraditional in character. For instance, resources can be your
next technical partner as intelligent grid initiatives turns out. Security and danger assessment and
administration become really vital in this connected atmosphere as cyber threats plus data
confidentiality needs increase.
The current B2B interactions shall no longer be bounded merely by a conventional network perimeter or
even limited to traditional techniques of data trade and communication. The brand new B2B
atmosphere associated with partners, companies, providers, and extra 3rd parties is, actually
unbounded, and details flows much more freely. As a total outcome, many of our traditional regulates
to secure B2B connections are no longer adequate. Listed below are key inflection factors that challenge
the current B2B security structures: · Mobile devices plus Web 2. 0 have got introduced new methods to
conduct business relationships. Companies are interacting with their particular partners in a lot more ad
hoc however cost effective way. It’s not unusual today to have corporation transactions and interactions
“on the go” with the use of mobile items and interactive press using Web 2.0 applications. 1 The
particular dynamic character from the content poses brand new risks that are particular to Web plus
application security. Cloud marketing promotions are a new way to broaden applications to B2B
partners. The particular cloud is a persuasive selection that your corporation can’t ignore intended for
extending resources in order to B2B clients, yet as a risk plus security professional, it is your job to
ensure that protection and personal privacy worries are recognized. · Smart Computing may breed more
complex interactions. Smart Computing can be the particular new era of integrated equipment, software
program, and system techniques that provide the systems with current awareness of the real world. A
few Smart Computing technologies will help several from the public and personal initiatives around the
world aimed at making important infrastructure of the towns smarter. For example, Wise Grid and
Sensible City projects which make use of Smart Processing technologies are rolling out there across the
world. 4 With all the advent of these sensible technologies, businesses may have complex and pervasive
partner relationships, many of them nontraditional in character. For instance, resources can be your
next technical partner as intelligent grid initiatives turns out. Security and danger assessment and
administration become really vital in this connected atmosphere as cyber threats plus data
confidentiality needs increase.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
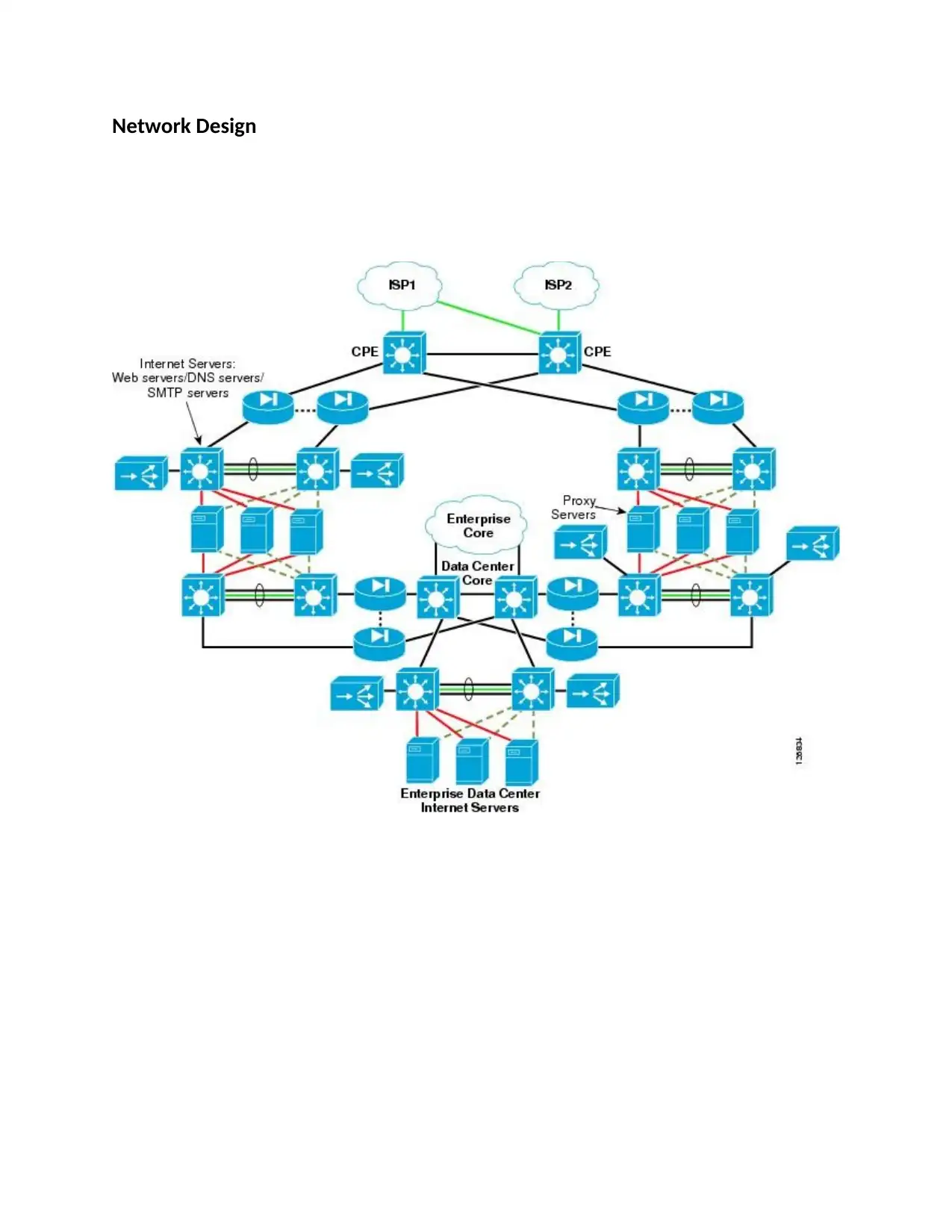
Network Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Security Threats
Earthworms, Trojan mounts, and two, in addition known as refusal associated with service types of
assaults in many cases are utilized malevolently to remove plus consume a given network’s resources.
Within instances, terribly configured website hosts plus accompanying computers act like risks in order
to network security, since they do eat up obtainable resources for not good reason.
Logic episodes
The majority of security experts team the various risks to system protection in one of 2 significant
categories. Possibly they might be thinking reference or approaches.
Resource attacks
The second group associated with network safety dangers are reference episodes. This kind of assaults
are primarily created in order to overwhelm essential program resources like RAM, usually and CPU
resources. This is mainly accomplished via dispatching a lot of forged IP and demands bouts to the
network included even.
Trojan horse Infections
A Trojan Equine displays to be adware and spyware which is certainly not personal replicating. Typically,
this type of viruses is cunning extremely, in that they will seem like these are carrying out a desirable
task for that customer. In reality though really, they are making probable unlawful access onto the user
within question’s computer system. The term only comes from the Trojan infections Horse story within
Homer’s Iliad through Greek mythology.
Worms
Computer worms are usually computer program spyware that are self-replicating usually. They will
utilize the particular pc network in order to mail copies of on their own to other personal computers
utilizing the specific network. They are numerous by means of computer bacterial infections in that
although they are not needed to be attached to any kind of current programs.
Earthworms, Trojan mounts, and two, in addition known as refusal associated with service types of
assaults in many cases are utilized malevolently to remove plus consume a given network’s resources.
Within instances, terribly configured website hosts plus accompanying computers act like risks in order
to network security, since they do eat up obtainable resources for not good reason.
Logic episodes
The majority of security experts team the various risks to system protection in one of 2 significant
categories. Possibly they might be thinking reference or approaches.
Resource attacks
The second group associated with network safety dangers are reference episodes. This kind of assaults
are primarily created in order to overwhelm essential program resources like RAM, usually and CPU
resources. This is mainly accomplished via dispatching a lot of forged IP and demands bouts to the
network included even.
Trojan horse Infections
A Trojan Equine displays to be adware and spyware which is certainly not personal replicating. Typically,
this type of viruses is cunning extremely, in that they will seem like these are carrying out a desirable
task for that customer. In reality though really, they are making probable unlawful access onto the user
within question’s computer system. The term only comes from the Trojan infections Horse story within
Homer’s Iliad through Greek mythology.
Worms
Computer worms are usually computer program spyware that are self-replicating usually. They will
utilize the particular pc network in order to mail copies of on their own to other personal computers
utilizing the specific network. They are numerous by means of computer bacterial infections in that
although they are not needed to be attached to any kind of current programs.
There are several types of network attacks.
1. Spoofing.
2. Sniffing.
3. Mapping.
4. Hijacking.
5. Trojans.
6. DoS and DDoS.
7. Social engineering.
1. Spoofing.
2. Sniffing.
3. Mapping.
4. Hijacking.
5. Trojans.
6. DoS and DDoS.
7. Social engineering.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security network devices
Make sure of network security is one of the most essential times intended for safe plus correct working
from the pc systems additionally networks. The operational program safety includes guarantee from the
limited entry to delicate information, the particular protection from illegal accessibility, risks and
possible protection threats, plus enhancement of system performance. It is crucial to guard the network
in different real way of its get access to factors, the most important factors within network security are
encryption usually, reliable security passwords, using antivirus software program and modern superior
network security products.
There are few sorts of program safety gadgets:
o Active gadgets: firewalls, antivirus checking gadgets, content blocking devices, which often
prevent the surplus traffic.
o Passive devices, such as intrusion identification appliances, which identify in addition record on
unwanted website visitors usually.
o Preventative devices: transmission testing devices and weaknesses evaluation appliances, which
examine the networks plus identify possible safety problems.
o Unified Risk management (UTM) gadgets, such as firewalls, articles filtering, which work as
helpful safety devices.
To build up a network we want a variety of equipment including the following:
Cables plus connectors - this particular hyperlink the computer systems along, printers, web servers
together with other gear on your system.
The particular router - This particular manages network visitors, ensuring devices might communicate
with each other through every wireless plus " cable " connections, plus offers net connection.
The particular wireless entry point (optional) - This can extend your own personal Wi-Fi network if the
router is incapable associated with providing safety in some parts of home.
An online hyperlink - This may be the faster fiber link or dedicated rented selection.
Make sure of network security is one of the most essential times intended for safe plus correct working
from the pc systems additionally networks. The operational program safety includes guarantee from the
limited entry to delicate information, the particular protection from illegal accessibility, risks and
possible protection threats, plus enhancement of system performance. It is crucial to guard the network
in different real way of its get access to factors, the most important factors within network security are
encryption usually, reliable security passwords, using antivirus software program and modern superior
network security products.
There are few sorts of program safety gadgets:
o Active gadgets: firewalls, antivirus checking gadgets, content blocking devices, which often
prevent the surplus traffic.
o Passive devices, such as intrusion identification appliances, which identify in addition record on
unwanted website visitors usually.
o Preventative devices: transmission testing devices and weaknesses evaluation appliances, which
examine the networks plus identify possible safety problems.
o Unified Risk management (UTM) gadgets, such as firewalls, articles filtering, which work as
helpful safety devices.
To build up a network we want a variety of equipment including the following:
Cables plus connectors - this particular hyperlink the computer systems along, printers, web servers
together with other gear on your system.
The particular router - This particular manages network visitors, ensuring devices might communicate
with each other through every wireless plus " cable " connections, plus offers net connection.
The particular wireless entry point (optional) - This can extend your own personal Wi-Fi network if the
router is incapable associated with providing safety in some parts of home.
An online hyperlink - This may be the faster fiber link or dedicated rented selection.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
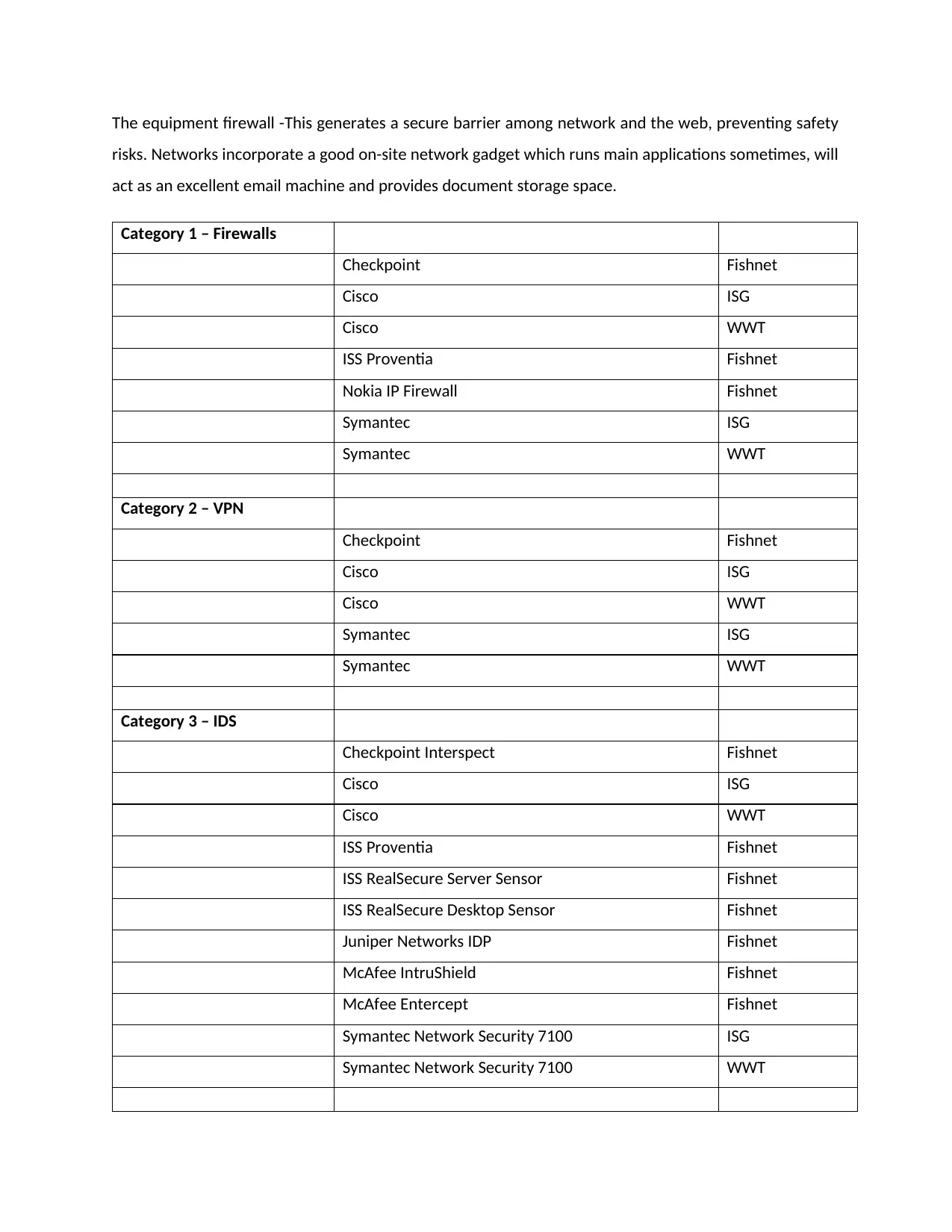
The equipment firewall -This generates a secure barrier among network and the web, preventing safety
risks. Networks incorporate a good on-site network gadget which runs main applications sometimes, will
act as an excellent email machine and provides document storage space.
Category 1 – Firewalls
Checkpoint Fishnet
Cisco ISG
Cisco WWT
ISS Proventia Fishnet
Nokia IP Firewall Fishnet
Symantec ISG
Symantec WWT
Category 2 – VPN
Checkpoint Fishnet
Cisco ISG
Cisco WWT
Symantec ISG
Symantec WWT
Category 3 – IDS
Checkpoint Interspect Fishnet
Cisco ISG
Cisco WWT
ISS Proventia Fishnet
ISS RealSecure Server Sensor Fishnet
ISS RealSecure Desktop Sensor Fishnet
Juniper Networks IDP Fishnet
McAfee IntruShield Fishnet
McAfee Entercept Fishnet
Symantec Network Security 7100 ISG
Symantec Network Security 7100 WWT
risks. Networks incorporate a good on-site network gadget which runs main applications sometimes, will
act as an excellent email machine and provides document storage space.
Category 1 – Firewalls
Checkpoint Fishnet
Cisco ISG
Cisco WWT
ISS Proventia Fishnet
Nokia IP Firewall Fishnet
Symantec ISG
Symantec WWT
Category 2 – VPN
Checkpoint Fishnet
Cisco ISG
Cisco WWT
Symantec ISG
Symantec WWT
Category 3 – IDS
Checkpoint Interspect Fishnet
Cisco ISG
Cisco WWT
ISS Proventia Fishnet
ISS RealSecure Server Sensor Fishnet
ISS RealSecure Desktop Sensor Fishnet
Juniper Networks IDP Fishnet
McAfee IntruShield Fishnet
McAfee Entercept Fishnet
Symantec Network Security 7100 ISG
Symantec Network Security 7100 WWT
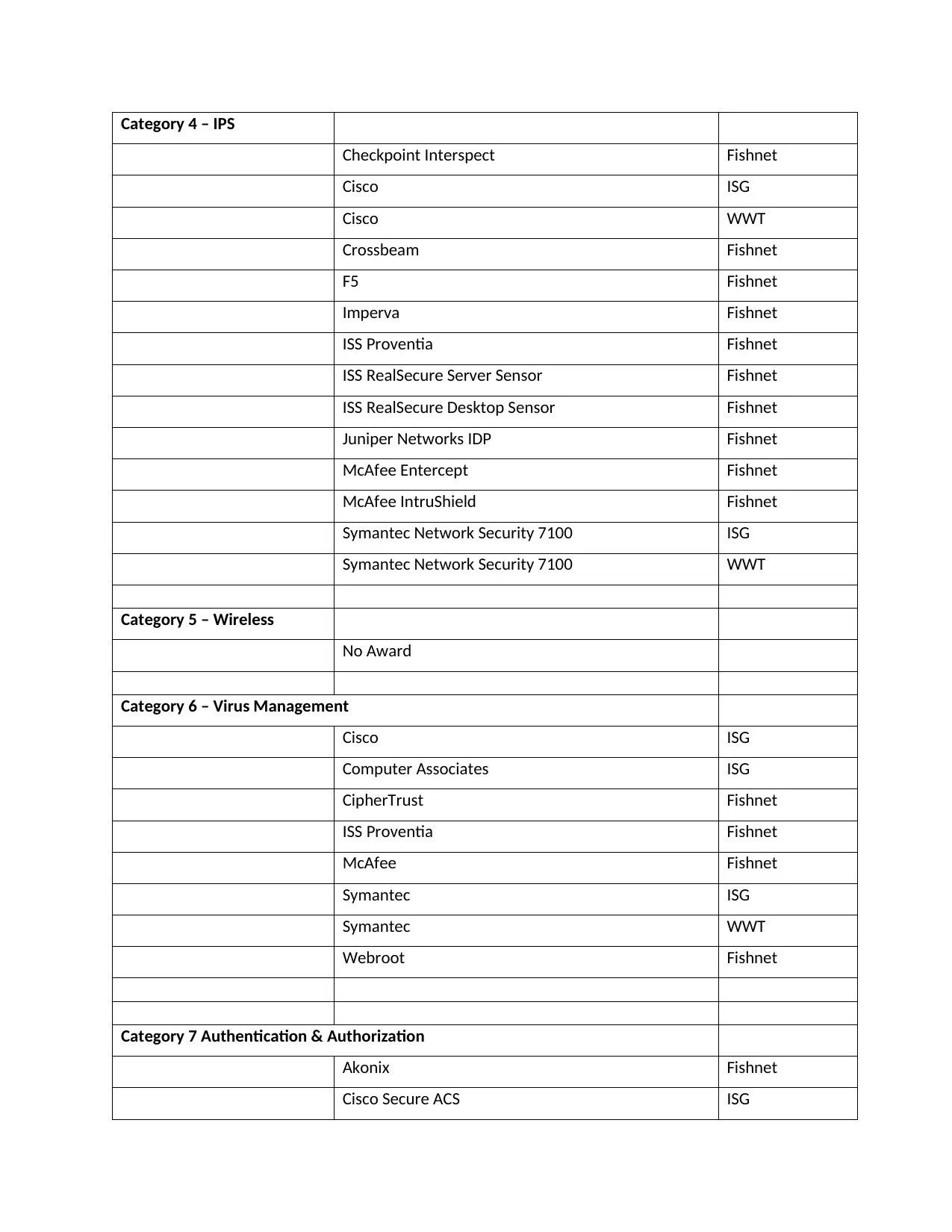
Category 4 – IPS
Checkpoint Interspect Fishnet
Cisco ISG
Cisco WWT
Crossbeam Fishnet
F5 Fishnet
Imperva Fishnet
ISS Proventia Fishnet
ISS RealSecure Server Sensor Fishnet
ISS RealSecure Desktop Sensor Fishnet
Juniper Networks IDP Fishnet
McAfee Entercept Fishnet
McAfee IntruShield Fishnet
Symantec Network Security 7100 ISG
Symantec Network Security 7100 WWT
Category 5 – Wireless
No Award
Category 6 – Virus Management
Cisco ISG
Computer Associates ISG
CipherTrust Fishnet
ISS Proventia Fishnet
McAfee Fishnet
Symantec ISG
Symantec WWT
Webroot Fishnet
Category 7 Authentication & Authorization
Akonix Fishnet
Cisco Secure ACS ISG
Checkpoint Interspect Fishnet
Cisco ISG
Cisco WWT
Crossbeam Fishnet
F5 Fishnet
Imperva Fishnet
ISS Proventia Fishnet
ISS RealSecure Server Sensor Fishnet
ISS RealSecure Desktop Sensor Fishnet
Juniper Networks IDP Fishnet
McAfee Entercept Fishnet
McAfee IntruShield Fishnet
Symantec Network Security 7100 ISG
Symantec Network Security 7100 WWT
Category 5 – Wireless
No Award
Category 6 – Virus Management
Cisco ISG
Computer Associates ISG
CipherTrust Fishnet
ISS Proventia Fishnet
McAfee Fishnet
Symantec ISG
Symantec WWT
Webroot Fishnet
Category 7 Authentication & Authorization
Akonix Fishnet
Cisco Secure ACS ISG
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
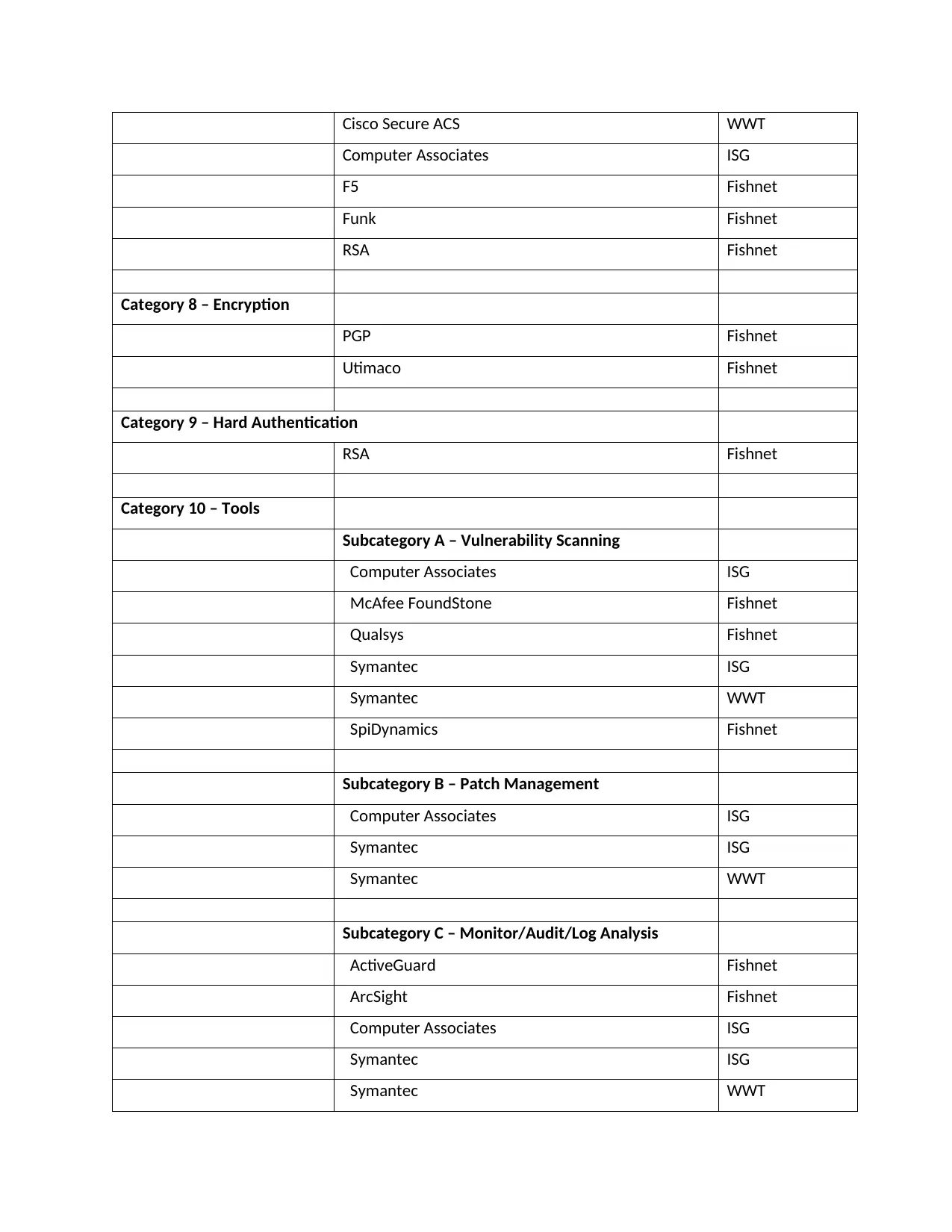
Cisco Secure ACS WWT
Computer Associates ISG
F5 Fishnet
Funk Fishnet
RSA Fishnet
Category 8 – Encryption
PGP Fishnet
Utimaco Fishnet
Category 9 – Hard Authentication
RSA Fishnet
Category 10 – Tools
Subcategory A – Vulnerability Scanning
Computer Associates ISG
McAfee FoundStone Fishnet
Qualsys Fishnet
Symantec ISG
Symantec WWT
SpiDynamics Fishnet
Subcategory B – Patch Management
Computer Associates ISG
Symantec ISG
Symantec WWT
Subcategory C – Monitor/Audit/Log Analysis
ActiveGuard Fishnet
ArcSight Fishnet
Computer Associates ISG
Symantec ISG
Symantec WWT
Computer Associates ISG
F5 Fishnet
Funk Fishnet
RSA Fishnet
Category 8 – Encryption
PGP Fishnet
Utimaco Fishnet
Category 9 – Hard Authentication
RSA Fishnet
Category 10 – Tools
Subcategory A – Vulnerability Scanning
Computer Associates ISG
McAfee FoundStone Fishnet
Qualsys Fishnet
Symantec ISG
Symantec WWT
SpiDynamics Fishnet
Subcategory B – Patch Management
Computer Associates ISG
Symantec ISG
Symantec WWT
Subcategory C – Monitor/Audit/Log Analysis
ActiveGuard Fishnet
ArcSight Fishnet
Computer Associates ISG
Symantec ISG
Symantec WWT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
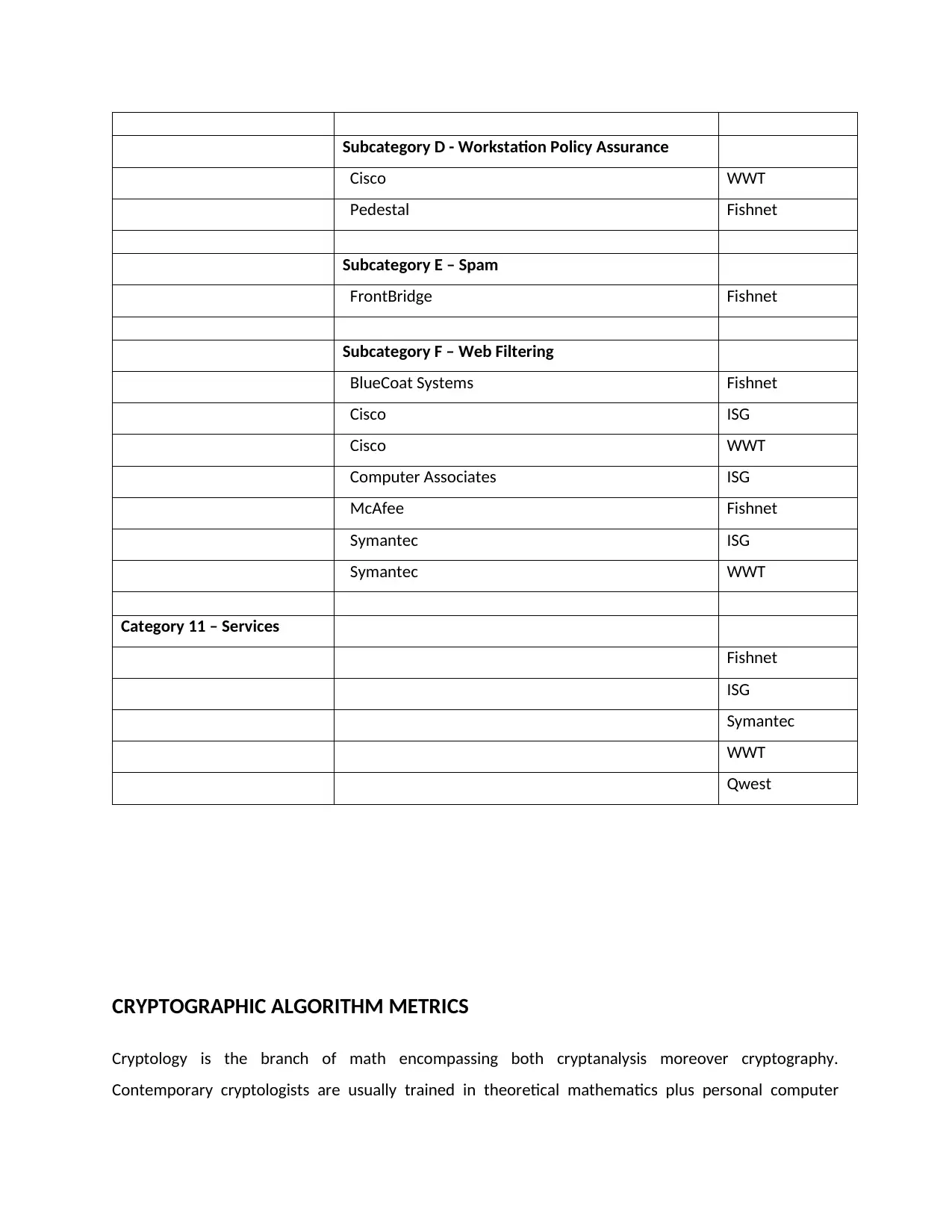
Subcategory D - Workstation Policy Assurance
Cisco WWT
Pedestal Fishnet
Subcategory E – Spam
FrontBridge Fishnet
Subcategory F – Web Filtering
BlueCoat Systems Fishnet
Cisco ISG
Cisco WWT
Computer Associates ISG
McAfee Fishnet
Symantec ISG
Symantec WWT
Category 11 – Services
Fishnet
ISG
Symantec
WWT
Qwest
CRYPTOGRAPHIC ALGORITHM METRICS
Cryptology is the branch of math encompassing both cryptanalysis moreover cryptography.
Contemporary cryptologists are usually trained in theoretical mathematics plus personal computer
Cisco WWT
Pedestal Fishnet
Subcategory E – Spam
FrontBridge Fishnet
Subcategory F – Web Filtering
BlueCoat Systems Fishnet
Cisco ISG
Cisco WWT
Computer Associates ISG
McAfee Fishnet
Symantec ISG
Symantec WWT
Category 11 – Services
Fishnet
ISG
Symantec
WWT
Qwest
CRYPTOGRAPHIC ALGORITHM METRICS
Cryptology is the branch of math encompassing both cryptanalysis moreover cryptography.
Contemporary cryptologists are usually trained in theoretical mathematics plus personal computer

technology. The particular artwork and science associated with maintaining messages secure is usually
cryptography, in fact it is practiced by cryptographers basically. Cryptanalysts are experts associated
with cryptanalysis, the particular science plus artwork associated with breaking cipher text; that is,
seeing plaintext with the cryptographic disguise. Cryptology provides the difficulty not contained in
normal academic disciplines: the benefits of continuous relationship of cryptography and cryptanalysis.
This discussion begins with a challenge via cryptographers that starts every single cycle with an
announcement from the new algorithm design and also a response from the cryptanalysts who also else
try to expose defects within the design, which is much more difficult than designing the techniques in
the first place usually. The result is really a beneficial competitive process which will produces “strong”
cryptography.
Whenever examining your specs plus risks, you need to select which of these four functions should be
employed to protect your details.
Authentication
Using a cryptographic system, you can easily set up the identity linked to the remote user (or system). A
typical example could be the SSL certificate of an internet machine providing proof towards the
customer that he or she is coupled towards the correct server.
Non-Repudiation
The idea of non-repudiation is very important for economic or web commerce programs. Often,
cryptographic equipment is needed to prove that a special consumer has made a deal demand. It must
not be feasible for the customer to refute his as well as her activities.
Privacy
Additionally, the biggest concern is to maintain information private. Cryptographic strategies were
originally created to work in this ability. Be it security passwords sent during a connect to the internet
cryptography, in fact it is practiced by cryptographers basically. Cryptanalysts are experts associated
with cryptanalysis, the particular science plus artwork associated with breaking cipher text; that is,
seeing plaintext with the cryptographic disguise. Cryptology provides the difficulty not contained in
normal academic disciplines: the benefits of continuous relationship of cryptography and cryptanalysis.
This discussion begins with a challenge via cryptographers that starts every single cycle with an
announcement from the new algorithm design and also a response from the cryptanalysts who also else
try to expose defects within the design, which is much more difficult than designing the techniques in
the first place usually. The result is really a beneficial competitive process which will produces “strong”
cryptography.
Whenever examining your specs plus risks, you need to select which of these four functions should be
employed to protect your details.
Authentication
Using a cryptographic system, you can easily set up the identity linked to the remote user (or system). A
typical example could be the SSL certificate of an internet machine providing proof towards the
customer that he or she is coupled towards the correct server.
Non-Repudiation
The idea of non-repudiation is very important for economic or web commerce programs. Often,
cryptographic equipment is needed to prove that a special consumer has made a deal demand. It must
not be feasible for the customer to refute his as well as her activities.
Privacy
Additionally, the biggest concern is to maintain information private. Cryptographic strategies were
originally created to work in this ability. Be it security passwords sent during a connect to the internet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





