Secure Software Development: SDLC, Methodologies, Analysis and Tools
VerifiedAdded on 2023/06/12
|15
|2894
|482
Report
AI Summary
This report provides a comprehensive overview of secure software development, focusing on integrating security practices into the Software Development Life Cycle (SDLC). It explores various methodologies, including the Waterfall model, and discusses the importance of security requirements, design considerations, secure coding practices, and thorough testing. The report reviews existing literature on secure software development, emphasizing the need for clear strategies and guidelines at each stage of the SDLC. It also highlights the use of tools for managing security requirements and conducting risk analysis. Ultimately, the report advocates for a software security framework that incorporates best security practices into the SDLC to address security vulnerabilities and improve the overall security posture of software applications. Desklib provides access to similar solved assignments for students.

SECURE SOFTWARE DEVELOPMENT
Name:
Subject:
Code:
1 | P a g e
Name:
Subject:
Code:
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1.0Introduction...............................................................................................................................3
1.1 Background..............................................................................................................................3
1.2 Statement of the problem........................................................................................................4
2.0LITERATURE REVIEW........................................................................................................5
2.1 Overview and analysis of the related work............................................................................5
2.2 Conclusion.............................................................................................................................7
3.0METHODOLOGY...................................................................................................................8
3.1 Software Development Life Cycle (SDLC)...........................................................................8
3.1.1 The Waterfall Methodology.........................................................................................9
3.2 Analysis and design tools.....................................................................................................10
3.3 System Testing and validation.............................................................................................11
References......................................................................................................................................13
2 | P a g e
1.0Introduction...............................................................................................................................3
1.1 Background..............................................................................................................................3
1.2 Statement of the problem........................................................................................................4
2.0LITERATURE REVIEW........................................................................................................5
2.1 Overview and analysis of the related work............................................................................5
2.2 Conclusion.............................................................................................................................7
3.0METHODOLOGY...................................................................................................................8
3.1 Software Development Life Cycle (SDLC)...........................................................................8
3.1.1 The Waterfall Methodology.........................................................................................9
3.2 Analysis and design tools.....................................................................................................10
3.3 System Testing and validation.............................................................................................11
References......................................................................................................................................13
2 | P a g e

CHAPTER ONE
1.0 Introduction.
Security is a fundamental intrigue theme in Information Technologies these days, and is
viewed as a Quality Attribute of a System by programming building . Starting here of view, a
few activities, similar to strategies, models and devices, have been proposed keeping in mind the
end goal to include building and plan choices through the Software Development Life Cycle
(SDLC)1. A number of these activities mean to help programming engineers to identify security
dangers, for example, Attack Trees, the elicitation of security necessities with Misuse Cases, and
the definition of security objectives as in Secure Tropos, while others permit programming
architects to moderate these security dangers or fulfill security prerequisites, by reusing security
plan choices or supporting the basic leadership process2. Be that as it may, the effect of these
strategies, techniques and models is difficult to evaluate, considering the idea of programming
advancement process, the absence of norms to gauge programming security from the perspective
of the product engineer, and the di culty of defining security prerequisites in a successful, clearffi
and unambiguous way.
.
1 Apvrille, Axelle, and Makan Pourzandi. "Secure software development by example." IEEE
Security & Privacy 3, no. 4 (2010): 10-17.
2 De Win, Bart, Riccardo Scandariato, Koen Buyens, Johan Grégoire, and Wouter Joosen. "On
the secure software development process: CLASP, SDL and Touchpoints
compared." Information and software technology 51, no. 7 (2009): 1152-1171
3 | P a g e
1.0 Introduction.
Security is a fundamental intrigue theme in Information Technologies these days, and is
viewed as a Quality Attribute of a System by programming building . Starting here of view, a
few activities, similar to strategies, models and devices, have been proposed keeping in mind the
end goal to include building and plan choices through the Software Development Life Cycle
(SDLC)1. A number of these activities mean to help programming engineers to identify security
dangers, for example, Attack Trees, the elicitation of security necessities with Misuse Cases, and
the definition of security objectives as in Secure Tropos, while others permit programming
architects to moderate these security dangers or fulfill security prerequisites, by reusing security
plan choices or supporting the basic leadership process2. Be that as it may, the effect of these
strategies, techniques and models is difficult to evaluate, considering the idea of programming
advancement process, the absence of norms to gauge programming security from the perspective
of the product engineer, and the di culty of defining security prerequisites in a successful, clearffi
and unambiguous way.
.
1 Apvrille, Axelle, and Makan Pourzandi. "Secure software development by example." IEEE
Security & Privacy 3, no. 4 (2010): 10-17.
2 De Win, Bart, Riccardo Scandariato, Koen Buyens, Johan Grégoire, and Wouter Joosen. "On
the secure software development process: CLASP, SDL and Touchpoints
compared." Information and software technology 51, no. 7 (2009): 1152-1171
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.1 Background
As innovation progresses, application conditions turn out to be more mind boggling and
application improvement security turns out to be all the more difficult. Applications,
frameworks, and systems are continually under different security assaults, for example, noxious
code or disavowal of administration3. Vulnerabilities of security are contained in applications
that might be presented by programming engineers either purposefully or indiscreetly.
Programming, natural, and equipment controls are needed in spite of the fact that they
can't keep issues made as a result of programming practices that are poor. Utilizing point of
confinement and grouping checks to approve clients' information will enhance the nature of
information. Despite the fact that software engineers may take after prescribed procedures, an
application can in any case flop because of unusual conditions and in this manner should deal
with sudden disappointments effectively by first logging all the data it can catch in planning for
evaluating. Administrative overhead and relative cost increases with increase in security.
1.2 Statement of the problem
The developing Internet availability of PCs and systems and the comparing client reliance on
arrange empowered administrations, (for example, email and Web-based exchanges) have
expanded the quantity of assault vectors and the simplicity with which an assault can be made.
This puts programming at more serious hazard. Another hazard territory influencing
programming security is how much frameworks acknowledge updates and expansions with the
goal that the abilities that the framework offers can develop incrementally. Extensible
3 Apvrille, Axelle, and Makan Pourzandi. "Secure software development by example." IEEE
Security & Privacy 3, no. 4 (2010): 10-17.
4 | P a g e
As innovation progresses, application conditions turn out to be more mind boggling and
application improvement security turns out to be all the more difficult. Applications,
frameworks, and systems are continually under different security assaults, for example, noxious
code or disavowal of administration3. Vulnerabilities of security are contained in applications
that might be presented by programming engineers either purposefully or indiscreetly.
Programming, natural, and equipment controls are needed in spite of the fact that they
can't keep issues made as a result of programming practices that are poor. Utilizing point of
confinement and grouping checks to approve clients' information will enhance the nature of
information. Despite the fact that software engineers may take after prescribed procedures, an
application can in any case flop because of unusual conditions and in this manner should deal
with sudden disappointments effectively by first logging all the data it can catch in planning for
evaluating. Administrative overhead and relative cost increases with increase in security.
1.2 Statement of the problem
The developing Internet availability of PCs and systems and the comparing client reliance on
arrange empowered administrations, (for example, email and Web-based exchanges) have
expanded the quantity of assault vectors and the simplicity with which an assault can be made.
This puts programming at more serious hazard. Another hazard territory influencing
programming security is how much frameworks acknowledge updates and expansions with the
goal that the abilities that the framework offers can develop incrementally. Extensible
3 Apvrille, Axelle, and Makan Pourzandi. "Secure software development by example." IEEE
Security & Privacy 3, no. 4 (2010): 10-17.
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

frameworks are alluring on the grounds that they accommodate the expansion of new highlights
and administrations. A last programming security chance zone is the unbridled development in
the size and many-sided quality of programming frameworks, (for example, the Microsoft
Windows working framework).
5 | P a g e
and administrations. A last programming security chance zone is the unbridled development in
the size and many-sided quality of programming frameworks, (for example, the Microsoft
Windows working framework).
5 | P a g e

CHAPTER TWO
2.0LITERATURE REVIEW
2.1 Overview and analysis of the related work.
Related work such as that of outlined the content that should be contained in the
requirement of the system while other scholars such as 4 among others emphasized on the
methodology and technical issues. Development of software with high quality involves a lot of
labor. Activities that are dedicated to security are involved which are left out in the traditional
SDLC. On the other hand stressed on the essence of requirements of the security at each stage of
the software development since majority of the developers are not trained in regard to the
security of the software. The model that has been proposed suggests that, engineers should elicit
the requirements of the security using various methods5. After completing the elicitation of the
requirements, the designing phase follows.
Vulnerabilities of the security are distinguished, recorded, and sent to the advancement group.
Engineers will think about all vulnerabilities and plan their relief design amid the plan stage. The
testing group then gets the created programming along with the documentation, all together to
4 Gregoire, Johan, Koen Buyens, Bart De Win, Riccardo Scandariato, and Wouter Joosen. "On
the secure software development process: CLASP and SDL compared." In Proceedings of the
Third International Workshop on Software Engineering for Secure Systems, p. 1. IEEE
Computer Society, 2010.
5 Futcher, Lynn, and Rossouw von Solms. "Guidelines for secure software development."
In Proceedings of the 2008 annual research conference of the South African Institute of
Computer Scientists and Information Technologists on IT research in developing countries:
riding the wave of technology, pp. 56-65. ACM, 2008.
6 | P a g e
2.0LITERATURE REVIEW
2.1 Overview and analysis of the related work.
Related work such as that of outlined the content that should be contained in the
requirement of the system while other scholars such as 4 among others emphasized on the
methodology and technical issues. Development of software with high quality involves a lot of
labor. Activities that are dedicated to security are involved which are left out in the traditional
SDLC. On the other hand stressed on the essence of requirements of the security at each stage of
the software development since majority of the developers are not trained in regard to the
security of the software. The model that has been proposed suggests that, engineers should elicit
the requirements of the security using various methods5. After completing the elicitation of the
requirements, the designing phase follows.
Vulnerabilities of the security are distinguished, recorded, and sent to the advancement group.
Engineers will think about all vulnerabilities and plan their relief design amid the plan stage. The
testing group then gets the created programming along with the documentation, all together to
4 Gregoire, Johan, Koen Buyens, Bart De Win, Riccardo Scandariato, and Wouter Joosen. "On
the secure software development process: CLASP and SDL compared." In Proceedings of the
Third International Workshop on Software Engineering for Secure Systems, p. 1. IEEE
Computer Society, 2010.
5 Futcher, Lynn, and Rossouw von Solms. "Guidelines for secure software development."
In Proceedings of the 2008 annual research conference of the South African Institute of
Computer Scientists and Information Technologists on IT research in developing countries:
riding the wave of technology, pp. 56-65. ACM, 2008.
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

find plan and improvement bugs. Toward the finish of the procedure, the product is prepared for
organization.
In accordance with 6 who suggested a tool for the management of the requirements of a
secure software. The tool, referred to as Tool for Secure Software Requirements, is intended to
oversee hazard examination, framework prerequisites, framework and undertaking security,
client and gathering limitations, encoded databases and traceability. Secure Software
Requirements tool has four segments: Planner, Modeler, Prover and Documenter. The Planner
module consolidates peril examination and investigation of the errand, that will be valuable in
dissecting the product security.
The Modeler supports system illustrating, designing, and affirmation. The Prover offers
clever organization theory, capable reasoning, confirm support, and hypothesis exhibiting for
check of logical models. The Documenter bolsters control ordering, basic perspectives,
specialized archive altering, and gives an interface to outside apparatuses. It likewise deals with a
focal archive database, which utilizes slope figure encryption and decoding security procedures
to give security to the database security. McGraw ( focused on that security ought to be expressly
characterized at the necessities level.
Security prerequisites ought to cover both utilitarian security and new security highlights.
Characterizing misuse cases that depict the framework's conduct under assault is a decent
methodology to cover the developing security space. This ought to likewise require express
examination of what ought to be secured, who to ensure against, and for to what extent
programming engineers ought to record every one of their presumptions and distinguish
6 Daud, Malik Imran. "Secure software development model: A guide for secure software life
cycle." In Proceedings of the international MultiConference of Engineers and Computer
Scientists, vol. 1, pp. 17-19. 2010.
7 | P a g e
organization.
In accordance with 6 who suggested a tool for the management of the requirements of a
secure software. The tool, referred to as Tool for Secure Software Requirements, is intended to
oversee hazard examination, framework prerequisites, framework and undertaking security,
client and gathering limitations, encoded databases and traceability. Secure Software
Requirements tool has four segments: Planner, Modeler, Prover and Documenter. The Planner
module consolidates peril examination and investigation of the errand, that will be valuable in
dissecting the product security.
The Modeler supports system illustrating, designing, and affirmation. The Prover offers
clever organization theory, capable reasoning, confirm support, and hypothesis exhibiting for
check of logical models. The Documenter bolsters control ordering, basic perspectives,
specialized archive altering, and gives an interface to outside apparatuses. It likewise deals with a
focal archive database, which utilizes slope figure encryption and decoding security procedures
to give security to the database security. McGraw ( focused on that security ought to be expressly
characterized at the necessities level.
Security prerequisites ought to cover both utilitarian security and new security highlights.
Characterizing misuse cases that depict the framework's conduct under assault is a decent
methodology to cover the developing security space. This ought to likewise require express
examination of what ought to be secured, who to ensure against, and for to what extent
programming engineers ought to record every one of their presumptions and distinguish
6 Daud, Malik Imran. "Secure software development model: A guide for secure software life
cycle." In Proceedings of the international MultiConference of Engineers and Computer
Scientists, vol. 1, pp. 17-19. 2010.
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

conceivable assaults7. Also, chance examination must be performed to find and rank dangers
with the goal that moderation control can be started. Outer audit of the plan is frequently
important .
With respect to the code, we ought to center around execution imperfections, particularly
those that static investigation instruments can find. Code survey is a fundamental practice for
accomplishing secure programming however is just piece of the arrangement. Security testing
should cover two procedures: (i) testing security usefulness with practical testing methods; and
(ii) chance construct security testing situated in light of assault examples and danger models8. A
security test arrange for that can be followed back to necessities, and that utilizations the two
techniques, can be viewed as a decent testing arrangement. Entrance testing is helpful also, on
the off chance that it thinks about the product engineering.
2.2 Conclusion
The exploration has distinguished different essential components as security strategies,
forms being rehearsed, and devices utilized inside the SDLC through the survey of the writing.
The proof assembled from the field demonstrates the absence of clear strategy and rules that are
set up at the task administration level inside each period of the SDLC. In such manner, proposals
7 Futcher, Lynn, and Rossouw von Solms. "Guidelines for secure software development."
In Proceedings of the 2008 annual research conference of the South African Institute of
Computer Scientists and Information Technologists on IT research in developing countries:
riding the wave of technology, pp. 56-65. ACM, 2008.
8 Khan, Muhammad Umair Ahmed, and Mohammad Zulkernine. "Quantifying security in secure
software development phases." In Computer Software and Applications, 2008. COMPSAC'08.
32nd Annual IEEE International, pp. 955-960. IEEE, 2008.
8 | P a g e
with the goal that moderation control can be started. Outer audit of the plan is frequently
important .
With respect to the code, we ought to center around execution imperfections, particularly
those that static investigation instruments can find. Code survey is a fundamental practice for
accomplishing secure programming however is just piece of the arrangement. Security testing
should cover two procedures: (i) testing security usefulness with practical testing methods; and
(ii) chance construct security testing situated in light of assault examples and danger models8. A
security test arrange for that can be followed back to necessities, and that utilizations the two
techniques, can be viewed as a decent testing arrangement. Entrance testing is helpful also, on
the off chance that it thinks about the product engineering.
2.2 Conclusion
The exploration has distinguished different essential components as security strategies,
forms being rehearsed, and devices utilized inside the SDLC through the survey of the writing.
The proof assembled from the field demonstrates the absence of clear strategy and rules that are
set up at the task administration level inside each period of the SDLC. In such manner, proposals
7 Futcher, Lynn, and Rossouw von Solms. "Guidelines for secure software development."
In Proceedings of the 2008 annual research conference of the South African Institute of
Computer Scientists and Information Technologists on IT research in developing countries:
riding the wave of technology, pp. 56-65. ACM, 2008.
8 Khan, Muhammad Umair Ahmed, and Mohammad Zulkernine. "Quantifying security in secure
software development phases." In Computer Software and Applications, 2008. COMPSAC'08.
32nd Annual IEEE International, pp. 955-960. IEEE, 2008.
8 | P a g e

and confirmation were assembled to evoke the genuine exercises that are proper for
incorporation at each period of the SDLC.
To accomplish the primary research objective, a software security system is proposed and
approved keeping in mind the end goal to consolidate best security rehearses into the SDLC. By
use of the the recommended demonstrate, the SDLC can be represented and security can be fused
in various stages; thus, different security issues and issues can be overwhelmed with
substantially before. This examination contributes altogether to information and practices by
proposing a model that enables specialists to proceed with its advancement and check in various
settings9. Also, chiefs and designers can utilize the model to build programming that is more
secure and all around arranged ahead of schedule in the advancement procedure.
CHAPTER THREE
9 Khan, Muhammad Umair Ahmed, and Mohammad Zulkernine. "Quantifying security in secure
software development phases." In Computer Software and Applications, 2008. COMPSAC'08.
32nd Annual IEEE International, pp. 955-960. IEEE, 2008.
9 | P a g e
incorporation at each period of the SDLC.
To accomplish the primary research objective, a software security system is proposed and
approved keeping in mind the end goal to consolidate best security rehearses into the SDLC. By
use of the the recommended demonstrate, the SDLC can be represented and security can be fused
in various stages; thus, different security issues and issues can be overwhelmed with
substantially before. This examination contributes altogether to information and practices by
proposing a model that enables specialists to proceed with its advancement and check in various
settings9. Also, chiefs and designers can utilize the model to build programming that is more
secure and all around arranged ahead of schedule in the advancement procedure.
CHAPTER THREE
9 Khan, Muhammad Umair Ahmed, and Mohammad Zulkernine. "Quantifying security in secure
software development phases." In Computer Software and Applications, 2008. COMPSAC'08.
32nd Annual IEEE International, pp. 955-960. IEEE, 2008.
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
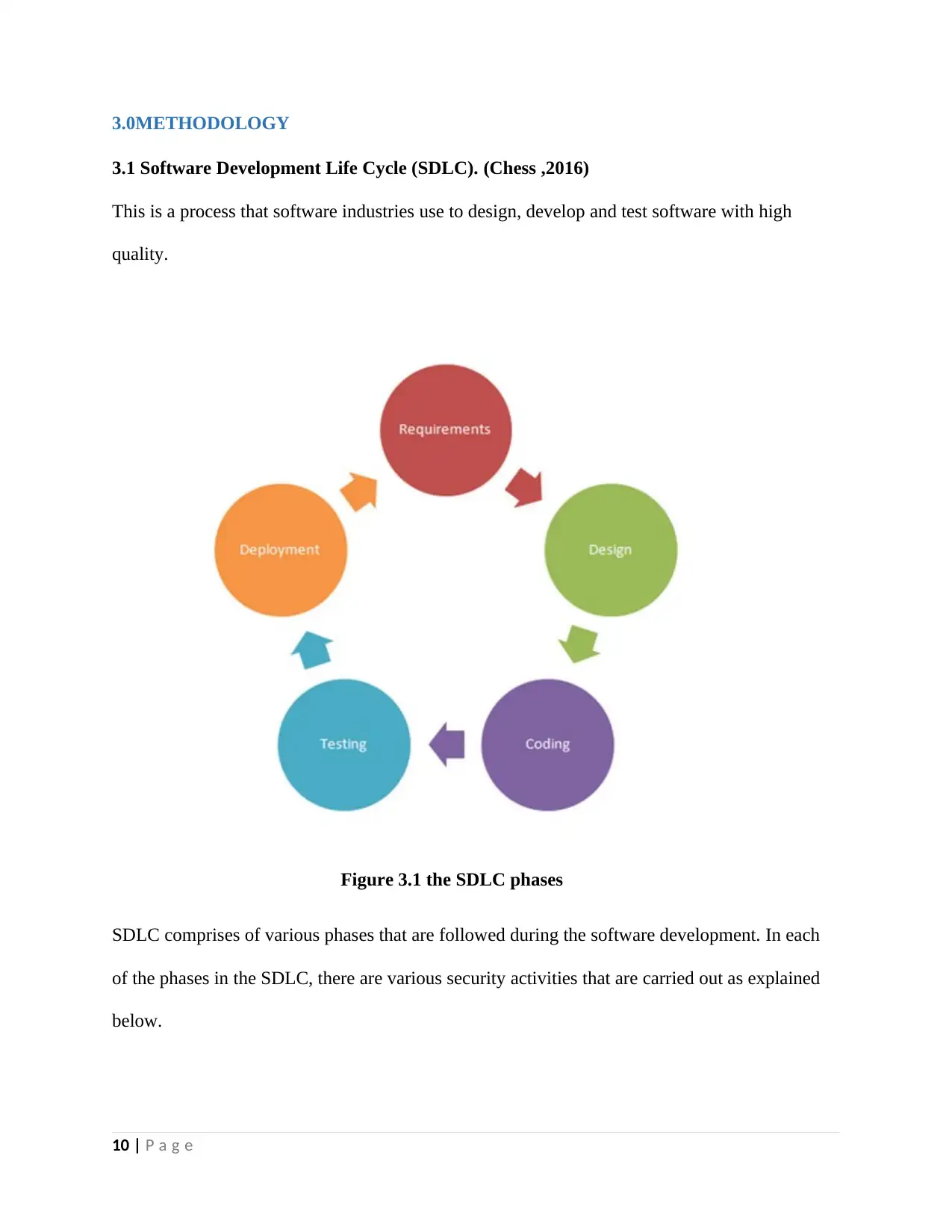
3.0METHODOLOGY
3.1 Software Development Life Cycle (SDLC). (Chess ,2016)
This is a process that software industries use to design, develop and test software with high
quality.
Figure 3.1 the SDLC phases
SDLC comprises of various phases that are followed during the software development. In each
of the phases in the SDLC, there are various security activities that are carried out as explained
below.
10 | P a g e
3.1 Software Development Life Cycle (SDLC). (Chess ,2016)
This is a process that software industries use to design, develop and test software with high
quality.
Figure 3.1 the SDLC phases
SDLC comprises of various phases that are followed during the software development. In each
of the phases in the SDLC, there are various security activities that are carried out as explained
below.
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Requirement gathering: a record of the expected response of the software to be developed
is done here. In this phase, security requirements, phase gates and assessment of risk are
carried out to enhance the security of the software.
Design: a blueprint is developed in this phase. It is used by the developers for the
development of the code. The requirements of the design based on the security
perspective are identified, reviews of the design and architecture are made and finally
modeling of threat is done.
Coding: source code is developed based on the blueprint made in the design phase. Best
practices of coding are done together with the performance of static analysis.
Testing: after the completion of coding, various tests are carried out on the software
developed to ensure that its working properly. If any issues are found, they are fixed
before or after deployment of the software. Software vulnerability and fuzzing are done
here.
Deployment: deployment of the software is done in the server used for production. The
deployment can be carried out on the client premise if the software was developed for the
client. The server and network configuration reviews are carried out in this phase.
3.1.1 The Waterfall Methodology (Pohl,2016)
This is an unbending direct model which encompasses of successive phases which in this
case includes Requirements, Design, Implementation, Verification and Maintenance whereby
unmistakable purposes are skilled. In every stage mentioned above, the activities carried out
must be 100% done afore going to the subsequent phase, habitually no procedure is there for
backtracking to modify the task.
11 | P a g e
is done here. In this phase, security requirements, phase gates and assessment of risk are
carried out to enhance the security of the software.
Design: a blueprint is developed in this phase. It is used by the developers for the
development of the code. The requirements of the design based on the security
perspective are identified, reviews of the design and architecture are made and finally
modeling of threat is done.
Coding: source code is developed based on the blueprint made in the design phase. Best
practices of coding are done together with the performance of static analysis.
Testing: after the completion of coding, various tests are carried out on the software
developed to ensure that its working properly. If any issues are found, they are fixed
before or after deployment of the software. Software vulnerability and fuzzing are done
here.
Deployment: deployment of the software is done in the server used for production. The
deployment can be carried out on the client premise if the software was developed for the
client. The server and network configuration reviews are carried out in this phase.
3.1.1 The Waterfall Methodology (Pohl,2016)
This is an unbending direct model which encompasses of successive phases which in this
case includes Requirements, Design, Implementation, Verification and Maintenance whereby
unmistakable purposes are skilled. In every stage mentioned above, the activities carried out
must be 100% done afore going to the subsequent phase, habitually no procedure is there for
backtracking to modify the task.
11 | P a g e
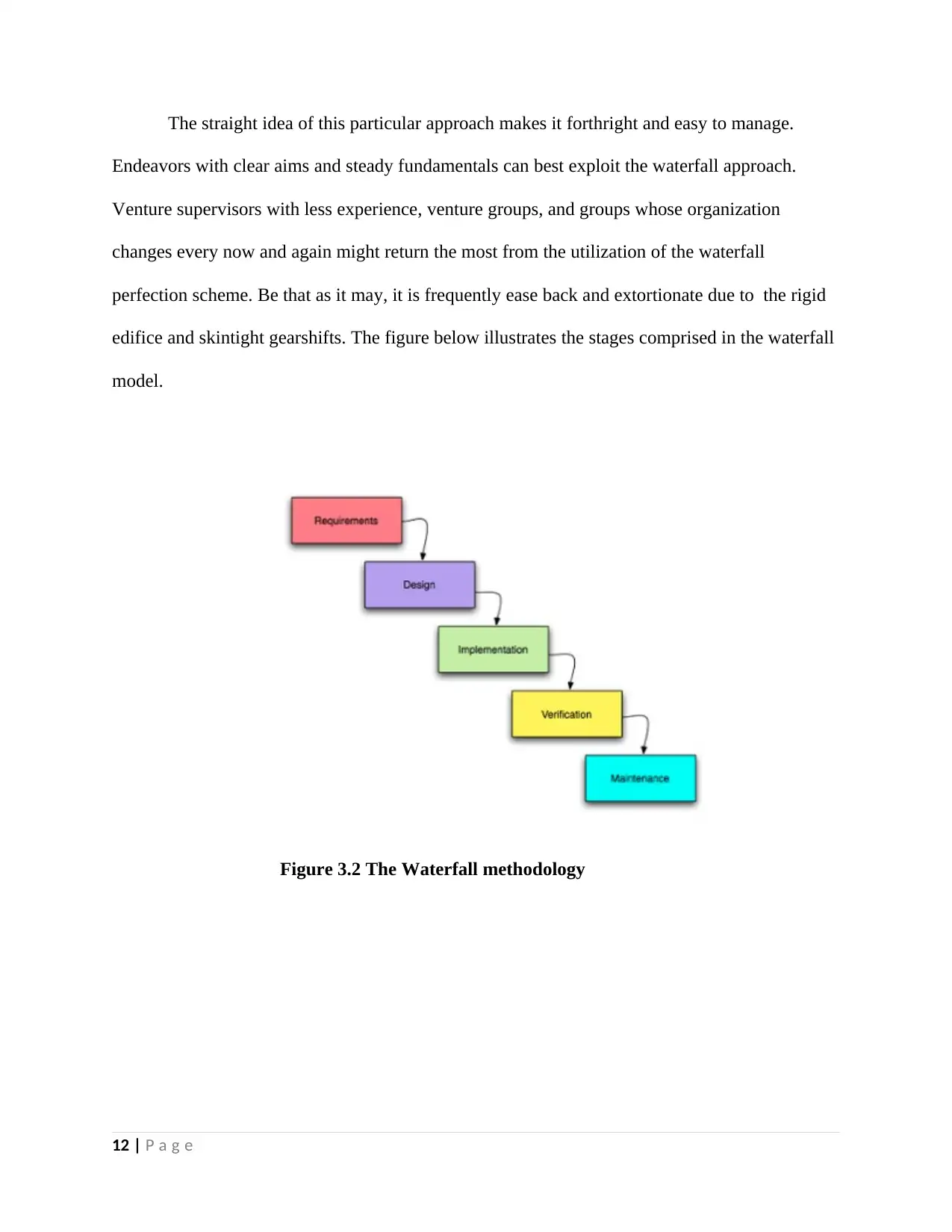
The straight idea of this particular approach makes it forthright and easy to manage.
Endeavors with clear aims and steady fundamentals can best exploit the waterfall approach.
Venture supervisors with less experience, venture groups, and groups whose organization
changes every now and again might return the most from the utilization of the waterfall
perfection scheme. Be that as it may, it is frequently ease back and extortionate due to the rigid
edifice and skintight gearshifts. The figure below illustrates the stages comprised in the waterfall
model.
Figure 3.2 The Waterfall methodology
12 | P a g e
Endeavors with clear aims and steady fundamentals can best exploit the waterfall approach.
Venture supervisors with less experience, venture groups, and groups whose organization
changes every now and again might return the most from the utilization of the waterfall
perfection scheme. Be that as it may, it is frequently ease back and extortionate due to the rigid
edifice and skintight gearshifts. The figure below illustrates the stages comprised in the waterfall
model.
Figure 3.2 The Waterfall methodology
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





