University Business Analytics: Security and Privacy Concerns
VerifiedAdded on 2022/08/26
|12
|2575
|15
Report
AI Summary
This report provides a comprehensive overview of security and privacy concerns within the realm of business analytics. It delves into the challenges posed by the evolving digital landscape and the increasing volume of data collected and analyzed. The report examines various facets of security, including Hadoop security, cloud security, auditing and monitoring, key management, and data security. It highlights the vulnerabilities and threats associated with each area, such as the limitations of traditional security measures and the risks of data breaches. The report also explores the importance of regulations and balanced approaches to ensure both the right to analytics for corporations and the privacy of individuals. Furthermore, it discusses the significance of auditing and monitoring, key management, and privacy-preserving data publishing and mining techniques to mitigate risks and protect sensitive information. Overall, the report emphasizes the need for a holistic approach to security and privacy in analytics, encompassing management, infrastructure, data quality, and policies.

Running head: BUSINESS ANALYTICS
BUSINESS ANALYTICS
Name of the Student:
Name of the University:
Author Note:
BUSINESS ANALYTICS
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BUSINESS ANALYTICS
Table of Contents
Literature Review.......................................................................................................................2
Security and Privacy Concerns in Analytics..........................................................................2
Hadoop Security.....................................................................................................................3
Cloud Security........................................................................................................................5
Auditing and Monitoring........................................................................................................6
Key Management...................................................................................................................7
Data Security..........................................................................................................................9
References................................................................................................................................10
Table of Contents
Literature Review.......................................................................................................................2
Security and Privacy Concerns in Analytics..........................................................................2
Hadoop Security.....................................................................................................................3
Cloud Security........................................................................................................................5
Auditing and Monitoring........................................................................................................6
Key Management...................................................................................................................7
Data Security..........................................................................................................................9
References................................................................................................................................10

2BUSINESS ANALYTICS
Literature Review
Security and Privacy Concerns in Analytics
Traditional privacy and security approaches are not capable of total addressing
changes which are used by analytics to digital world, which ranges from quantity of data
which is collected and stored for manipulation. The security measures like complicated
algorithm of encryption, firewalls, intrusion detection system and access control limitations
could be broken as well as anonymised data is identified and also associated with certain
users in malicious use. New regulations are proposed specifically to address challenges which
analytics have introduced to privacy of the individuals, aggregation and inference that makes
this possible in re-identifying the individuals after there is removal of identifiers from the
dataset [1]. Though there are certain cases where regulations that are previously defined
might result in violation of privacy like retention of the data of email for certain period of
time that simply leaves door open for violations of privacy.
However, old dilemma called security triangle is faced that states that as the tougher
security measures as employed, the functionality of the systems are affected. For instance, if
specific regulation limits access of corporations for analysing and manipulating raw data, the
corporation would not enhance the business. Hence, it is required in proposing balanced
approach for the analytics and regulations which ensures right of corporation to analytics
along with privacy of individual [2]. In nutshell, overall ecosystem of analytics from
management to infrastructure to trust integrity data quality and policies should be revisited
and examined with relation to privacy and security concerns. There is need of comprehensive
research in thoroughly identifying and addressing the concerns. It should be made sure that
the security measures are placed into every technologies that are developed for analytics, like
technologies for auditing and monitoring processes, data provenance, applications and
Literature Review
Security and Privacy Concerns in Analytics
Traditional privacy and security approaches are not capable of total addressing
changes which are used by analytics to digital world, which ranges from quantity of data
which is collected and stored for manipulation. The security measures like complicated
algorithm of encryption, firewalls, intrusion detection system and access control limitations
could be broken as well as anonymised data is identified and also associated with certain
users in malicious use. New regulations are proposed specifically to address challenges which
analytics have introduced to privacy of the individuals, aggregation and inference that makes
this possible in re-identifying the individuals after there is removal of identifiers from the
dataset [1]. Though there are certain cases where regulations that are previously defined
might result in violation of privacy like retention of the data of email for certain period of
time that simply leaves door open for violations of privacy.
However, old dilemma called security triangle is faced that states that as the tougher
security measures as employed, the functionality of the systems are affected. For instance, if
specific regulation limits access of corporations for analysing and manipulating raw data, the
corporation would not enhance the business. Hence, it is required in proposing balanced
approach for the analytics and regulations which ensures right of corporation to analytics
along with privacy of individual [2]. In nutshell, overall ecosystem of analytics from
management to infrastructure to trust integrity data quality and policies should be revisited
and examined with relation to privacy and security concerns. There is need of comprehensive
research in thoroughly identifying and addressing the concerns. It should be made sure that
the security measures are placed into every technologies that are developed for analytics, like
technologies for auditing and monitoring processes, data provenance, applications and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3BUSINESS ANALYTICS
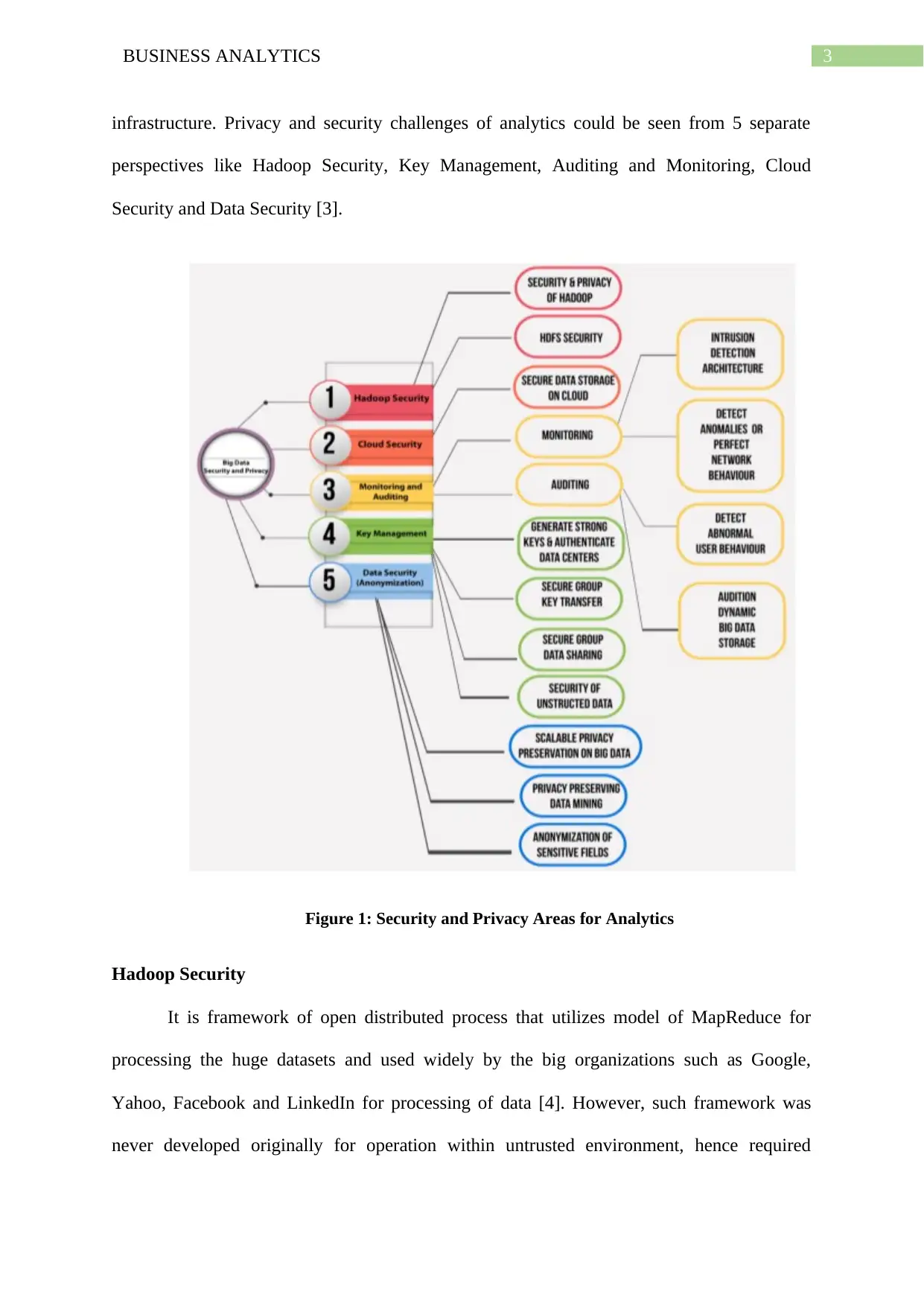
infrastructure. Privacy and security challenges of analytics could be seen from 5 separate
perspectives like Hadoop Security, Key Management, Auditing and Monitoring, Cloud
Security and Data Security [3].
Figure 1: Security and Privacy Areas for Analytics
Hadoop Security
It is framework of open distributed process that utilizes model of MapReduce for
processing the huge datasets and used widely by the big organizations such as Google,
Yahoo, Facebook and LinkedIn for processing of data [4]. However, such framework was
never developed originally for operation within untrusted environment, hence required
infrastructure. Privacy and security challenges of analytics could be seen from 5 separate
perspectives like Hadoop Security, Key Management, Auditing and Monitoring, Cloud
Security and Data Security [3].
Figure 1: Security and Privacy Areas for Analytics
Hadoop Security
It is framework of open distributed process that utilizes model of MapReduce for
processing the huge datasets and used widely by the big organizations such as Google,
Yahoo, Facebook and LinkedIn for processing of data [4]. However, such framework was
never developed originally for operation within untrusted environment, hence required
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BUSINESS ANALYTICS
measures for security were never incorporated. Lack of appropriate security protection within
several technologies for analytics like Hadoop, Pig, Hive, Mahout, Cassandra, MapReduce
and Twitter Strom has turned the infrastructure into security challenge for analytics.
However against every shortcomings within security, Hadoop got great interest and
was chosen as a primary platform for analytics, making this compulsory in figuring out ways
by which required security precautions could be added, as the data that is stored within the
cloud is targeted by the hacker. Hadoop’s two main security weaknesses are mentioned and
the techniques which could be used to develop Hadoop system to ensure privacy and security
of data are discussed.
HDFS Security: It is distributed file system of Hadoop that possesses three major
components such as secondary name node, name node and data node. Many replicas
for every block of the data is created by HDFS in order for ensuring quick response
time and availability [5]. However, certain issues are there for HDFS with regards to
authentication to which Kerberos’s use is suggested for allowing nodes to prove the
identity to each other. Another issue which is faced by HDFS is with respect to
unavailability of naming nodes for which there is suggestion of use of additional
name node which could be accessed if anything occurs to master name node.
Administrator grants access to slave node if condition which is mentioned in Name
Node Security Enhance (NNSE) holds.
Hadoop Privacy and Security: A way through which users’ secure access to data
stored within cloud is provided, is by authentication of user before giving access to
the name node, within the mechanism both name node and user create hash function
by using algorithms like SHA-256, comparison among hash value that is generated
by user and sent by user is performed name node and gives access if values are
correct [6]. The Trust Mechanism gives access to the data nodes. Other commonly
measures for security were never incorporated. Lack of appropriate security protection within
several technologies for analytics like Hadoop, Pig, Hive, Mahout, Cassandra, MapReduce
and Twitter Strom has turned the infrastructure into security challenge for analytics.
However against every shortcomings within security, Hadoop got great interest and
was chosen as a primary platform for analytics, making this compulsory in figuring out ways
by which required security precautions could be added, as the data that is stored within the
cloud is targeted by the hacker. Hadoop’s two main security weaknesses are mentioned and
the techniques which could be used to develop Hadoop system to ensure privacy and security
of data are discussed.
HDFS Security: It is distributed file system of Hadoop that possesses three major
components such as secondary name node, name node and data node. Many replicas
for every block of the data is created by HDFS in order for ensuring quick response
time and availability [5]. However, certain issues are there for HDFS with regards to
authentication to which Kerberos’s use is suggested for allowing nodes to prove the
identity to each other. Another issue which is faced by HDFS is with respect to
unavailability of naming nodes for which there is suggestion of use of additional
name node which could be accessed if anything occurs to master name node.
Administrator grants access to slave node if condition which is mentioned in Name
Node Security Enhance (NNSE) holds.
Hadoop Privacy and Security: A way through which users’ secure access to data
stored within cloud is provided, is by authentication of user before giving access to
the name node, within the mechanism both name node and user create hash function
by using algorithms like SHA-256, comparison among hash value that is generated
by user and sent by user is performed name node and gives access if values are
correct [6]. The Trust Mechanism gives access to the data nodes. Other commonly

5BUSINESS ANALYTICS
used and easy is ensuring safety of data and limit the unauthorised access by
performing decryption and encryption by using Random Encryption Algorithms such
as AES, RSA, IDEA, RC6, Rinjdael and Triple DES.
Cloud Security
It is used widely in analytics for several advantages, this mainly provides as real-time
or on-demand availability of service, resources sharing and widespread access. However
cloud computing’s use in analytics comes with several security issues as the technology
consists of multiple principals and areas such as resource sharing, networking, virtualization.,
databases and operating systems [7]. Hence, security challenges of the technologies and
systems are applicable also in cloud computing. A major issue with cloud is securing the
stored data. Hence, providers of cloud service have suggested several secure ways to share
analytics over platform of cloud. The providers give assurance that issues are not faced by the
clients such as theft or loss of data that is caused due to user impersonation. The challenges of
cloud security are divided into few categories:
Authentication level: Security issues of authentication level include areas such as
methods of authentication like administrative permission of nodes, authentication of
applications, logging and the techniques that are used in decryption and encryption.
Network Level: Security issues and protocol of network level include areas such as
distributed data and nodes and internode communications [8]. Hence it is suggested
that every network communications should be encrypted by Secure Sockets Layer
(SSL) for security of the packets.
Data Level: Security issues of data level include area such as distributed data
protection for assuring integrity and availability of data. It is essential in having at
least three separate Back-Up servers, if main server is not available for technical
problems.
used and easy is ensuring safety of data and limit the unauthorised access by
performing decryption and encryption by using Random Encryption Algorithms such
as AES, RSA, IDEA, RC6, Rinjdael and Triple DES.
Cloud Security
It is used widely in analytics for several advantages, this mainly provides as real-time
or on-demand availability of service, resources sharing and widespread access. However
cloud computing’s use in analytics comes with several security issues as the technology
consists of multiple principals and areas such as resource sharing, networking, virtualization.,
databases and operating systems [7]. Hence, security challenges of the technologies and
systems are applicable also in cloud computing. A major issue with cloud is securing the
stored data. Hence, providers of cloud service have suggested several secure ways to share
analytics over platform of cloud. The providers give assurance that issues are not faced by the
clients such as theft or loss of data that is caused due to user impersonation. The challenges of
cloud security are divided into few categories:
Authentication level: Security issues of authentication level include areas such as
methods of authentication like administrative permission of nodes, authentication of
applications, logging and the techniques that are used in decryption and encryption.
Network Level: Security issues and protocol of network level include areas such as
distributed data and nodes and internode communications [8]. Hence it is suggested
that every network communications should be encrypted by Secure Sockets Layer
(SSL) for security of the packets.
Data Level: Security issues of data level include area such as distributed data
protection for assuring integrity and availability of data. It is essential in having at
least three separate Back-Up servers, if main server is not available for technical
problems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BUSINESS ANALYTICS
Auditing and Monitoring
Auditing and Monitoring is integral part for management of network security that
helps service providers in preventing the security breaches through checking traffic of
network and by using information that is acquired for adjusting and applying specific
security measures [9]. Network monitoring focuses mainly on studying and collecting
events for detecting the intrusions. Network auditing could be considered as measurable
and systematic security policy that has huge impact over network security.
Network Auditing: There are few challenges when it is about data availability and
integrity of analytics. While availability of analytics could be achieved easily by
keeping several replicas for assuring fast and easy access, it might create few
issues with integrity of data.
Network Monitoring: Factors are there which should be analysed if the Intrusion
Detection and Prevention Architecture is successfully applied for monitoring total
network system, few of areas should be included within monitoring process are
DNS and HTTP traffic, data collected by honeypots that are laid as trap for the
intruders and records of IP flow. Data is stored and processed by Intrusion
Detection System (IDS) by using Malicious Likelihood Metrics for finding out if
flow, domain name or packets are affected, in that case, process or action would
be immediately stopped [10].
Auditing and Monitoring
Auditing and Monitoring is integral part for management of network security that
helps service providers in preventing the security breaches through checking traffic of
network and by using information that is acquired for adjusting and applying specific
security measures [9]. Network monitoring focuses mainly on studying and collecting
events for detecting the intrusions. Network auditing could be considered as measurable
and systematic security policy that has huge impact over network security.
Network Auditing: There are few challenges when it is about data availability and
integrity of analytics. While availability of analytics could be achieved easily by
keeping several replicas for assuring fast and easy access, it might create few
issues with integrity of data.
Network Monitoring: Factors are there which should be analysed if the Intrusion
Detection and Prevention Architecture is successfully applied for monitoring total
network system, few of areas should be included within monitoring process are
DNS and HTTP traffic, data collected by honeypots that are laid as trap for the
intruders and records of IP flow. Data is stored and processed by Intrusion
Detection System (IDS) by using Malicious Likelihood Metrics for finding out if
flow, domain name or packets are affected, in that case, process or action would
be immediately stopped [10].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BUSINESS ANALYTICS
Figure 2: Classification of Analytics
Key Management
Privacy and security enhancement of analytics come with separate challenges as
dynamic generation of key for analytics is not enough efficient by using latest cryptographic
techniques. Within mobile security, users of data centre could be located everywhere that
makes this necessary in having certain system of key management for simultaneously
securing channel and data used for the transmission among nodes [11]. For solving this issue,
effective Quantum Cryptography is required by data centres by using algorithm of Grover for
proper approaches of authentication for enhancing privacy and security with much lees
complexity within data centres. Though Quantum model’s use could increase efficiency and
security of the system. It is crucial in remembering that communications in analytics need
protocols of Secure Group Key Transfer for withstanding the attacks, hence using the online
key generation based on Diffie Hellman Key Agreement.
Another aspect is Secure Group Data Sharing to which there is use of Conditional
Proxy Re-Encryption (CPRE) for enabling sensitive data’s group sharing without exposing
Figure 2: Classification of Analytics
Key Management
Privacy and security enhancement of analytics come with separate challenges as
dynamic generation of key for analytics is not enough efficient by using latest cryptographic
techniques. Within mobile security, users of data centre could be located everywhere that
makes this necessary in having certain system of key management for simultaneously
securing channel and data used for the transmission among nodes [11]. For solving this issue,
effective Quantum Cryptography is required by data centres by using algorithm of Grover for
proper approaches of authentication for enhancing privacy and security with much lees
complexity within data centres. Though Quantum model’s use could increase efficiency and
security of the system. It is crucial in remembering that communications in analytics need
protocols of Secure Group Key Transfer for withstanding the attacks, hence using the online
key generation based on Diffie Hellman Key Agreement.
Another aspect is Secure Group Data Sharing to which there is use of Conditional
Proxy Re-Encryption (CPRE) for enabling sensitive data’s group sharing without exposing
8BUSINESS ANALYTICS
actual content key for decryption to the people. Latest scheme to secure group data sharing
over cloud is introduced that is much more efficient and compatible with analytics known as
Outsourcing CPRE scheme (O-CPRE) that decreases user overhead. Analytics could be
divided broadly into two types such as unstructured and structured and it is tougher in
assuring Security for Unstructured Data. In such approach, the data is clustered, filtered,
reviewed and classified based on sensitivity level and type, then there is creation of certain
data nodes within the database [12]. For providing security to the data nodes, there was
design of security suite that incorporates separate security algorithms and standards with type
of the data node. In such stage, most appropriate algorithm should be assigned with data
nodes depending on data type and the sensitivity level and requirements from the security
suite.
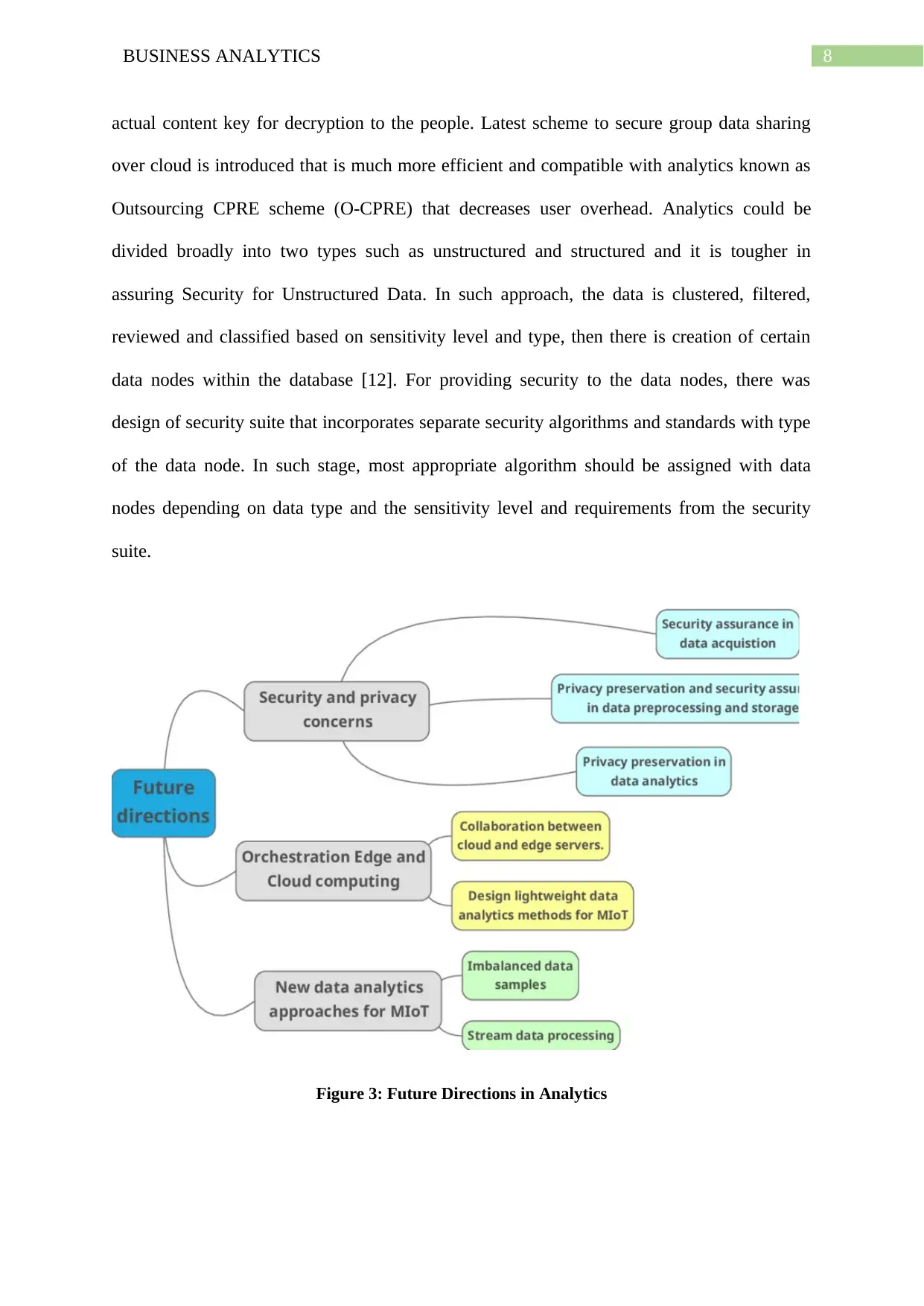
Figure 3: Future Directions in Analytics
actual content key for decryption to the people. Latest scheme to secure group data sharing
over cloud is introduced that is much more efficient and compatible with analytics known as
Outsourcing CPRE scheme (O-CPRE) that decreases user overhead. Analytics could be
divided broadly into two types such as unstructured and structured and it is tougher in
assuring Security for Unstructured Data. In such approach, the data is clustered, filtered,
reviewed and classified based on sensitivity level and type, then there is creation of certain
data nodes within the database [12]. For providing security to the data nodes, there was
design of security suite that incorporates separate security algorithms and standards with type
of the data node. In such stage, most appropriate algorithm should be assigned with data
nodes depending on data type and the sensitivity level and requirements from the security
suite.
Figure 3: Future Directions in Analytics
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BUSINESS ANALYTICS
Data Security
Data harvesting and collection for analytics has raised numerous eyebrows with
regards to right of privacy for the user. One important responsibility for data publishers is
assuring privacy and security of data. Privacy Preserving Data Publishing (PPDP) discusses
way in where data could be published when making sure right to privacy of user. This is
becoming much tougher for data publishers in masking Personally Identifiable Information
(PII) for speed where there is sharing of data, there is dire need for devising the policies
where organizations are responsible in ensuring anonymization and also secure transfer of
personal data of users. Though after performing process of anonymization, ways are there
where user could be re-identified. For avoiding such issue, K-Anonymity based Metrics are
used for masking sensitive fields [13]. There is removal of personal identifiers from the usage
logs for protecting privacy of the users. Sensitive fields’ anonymization is achieved through
use of the symmetric key encryption of AES that is stored within HDFS.
Privacy Preserving Data Mining (PPDM) is other subject which gained traction as for
increased usage of the privacy concerns of analytics. It is essential in gaining privacy without
even compromising mining accuracy or data content [14]. Hence, it is advised to use
Adaptive Utility based Anonymization algorithm for addressing risk of the disclosure of data
without affecting the classification accuracy. Huge volume and scalability is other reason that
the methods of anonymization are not successful in masking the sensitive information when it
is about analytics. Hence, use of Hybrid Top-Down and Bottom-Up Subtree Anonymization
model for increasing method’s scalability capability.
Data Security
Data harvesting and collection for analytics has raised numerous eyebrows with
regards to right of privacy for the user. One important responsibility for data publishers is
assuring privacy and security of data. Privacy Preserving Data Publishing (PPDP) discusses
way in where data could be published when making sure right to privacy of user. This is
becoming much tougher for data publishers in masking Personally Identifiable Information
(PII) for speed where there is sharing of data, there is dire need for devising the policies
where organizations are responsible in ensuring anonymization and also secure transfer of
personal data of users. Though after performing process of anonymization, ways are there
where user could be re-identified. For avoiding such issue, K-Anonymity based Metrics are
used for masking sensitive fields [13]. There is removal of personal identifiers from the usage
logs for protecting privacy of the users. Sensitive fields’ anonymization is achieved through
use of the symmetric key encryption of AES that is stored within HDFS.
Privacy Preserving Data Mining (PPDM) is other subject which gained traction as for
increased usage of the privacy concerns of analytics. It is essential in gaining privacy without
even compromising mining accuracy or data content [14]. Hence, it is advised to use
Adaptive Utility based Anonymization algorithm for addressing risk of the disclosure of data
without affecting the classification accuracy. Huge volume and scalability is other reason that
the methods of anonymization are not successful in masking the sensitive information when it
is about analytics. Hence, use of Hybrid Top-Down and Bottom-Up Subtree Anonymization
model for increasing method’s scalability capability.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BUSINESS ANALYTICS
References
[1] Y. Gahi, M. Guennoun and H.T. Mouftah, “Big data analytics: Security and privacy
challenges”, In 2016 IEEE Symposium on Computers and Communication (ISCC)
(pp. 952-957). IEEE, 2016
[2] D.S. Terzi, R. Terzi and S. Sagiroglu, “December. A survey on security and privacy
issues in big data”, In 2015 10th International Conference for Internet Technology
and Secured Transactions (ICITST) (pp. 202-207). IEEE, 2015
[3] B. Thuraisingham, “Big data security and privacy”, In Proceedings of the 5th ACM
Conference on Data and Application Security and Privacy (pp. 279-280), 2015
[4] C.A. Ardagna, P. Ceravolo and E. Damiani, “Big data analytics as-a-service: Issues
and challenges”, In 2016 IEEE International Conference on Big Data (Big Data) (pp.
3638-3644). IEEE, 2016
[5] J. Hu and A.V. Vasilakos, “Energy big data analytics and security: challenges and
opportunities”, IEEE Transactions on Smart Grid, 7(5), pp.2423-2436, 2016
[6] K. Abouelmehdi, A. Beni-Hssane, H. Khaloufi and M. Saadi, “Big data security and
privacy in healthcare: A Review”, Procedia Computer Science, 113, pp.73-80, 2017
[7] R.P. Minch, “Location privacy in the Era of the Internet of Things and Big Data
analytics”, In 2015 48th Hawaii International Conference on System Sciences (pp.
1521-1530). IEEE, 2015
[8] M. Khalil and M. Ebner, "Learning analytics: principles and constraints”, In
EdMedia+ Innovate Learning (pp. 1789-1799). Association for the Advancement of
Computing in Education (AACE), 2015
[9] K. Abouelmehdi, A. Beni-Hessane and H. Khaloufi, “Big healthcare data: preserving
security and privacy”, Journal of Big Data, 5(1), p.1, 2018
References
[1] Y. Gahi, M. Guennoun and H.T. Mouftah, “Big data analytics: Security and privacy
challenges”, In 2016 IEEE Symposium on Computers and Communication (ISCC)
(pp. 952-957). IEEE, 2016
[2] D.S. Terzi, R. Terzi and S. Sagiroglu, “December. A survey on security and privacy
issues in big data”, In 2015 10th International Conference for Internet Technology
and Secured Transactions (ICITST) (pp. 202-207). IEEE, 2015
[3] B. Thuraisingham, “Big data security and privacy”, In Proceedings of the 5th ACM
Conference on Data and Application Security and Privacy (pp. 279-280), 2015
[4] C.A. Ardagna, P. Ceravolo and E. Damiani, “Big data analytics as-a-service: Issues
and challenges”, In 2016 IEEE International Conference on Big Data (Big Data) (pp.
3638-3644). IEEE, 2016
[5] J. Hu and A.V. Vasilakos, “Energy big data analytics and security: challenges and
opportunities”, IEEE Transactions on Smart Grid, 7(5), pp.2423-2436, 2016
[6] K. Abouelmehdi, A. Beni-Hssane, H. Khaloufi and M. Saadi, “Big data security and
privacy in healthcare: A Review”, Procedia Computer Science, 113, pp.73-80, 2017
[7] R.P. Minch, “Location privacy in the Era of the Internet of Things and Big Data
analytics”, In 2015 48th Hawaii International Conference on System Sciences (pp.
1521-1530). IEEE, 2015
[8] M. Khalil and M. Ebner, "Learning analytics: principles and constraints”, In
EdMedia+ Innovate Learning (pp. 1789-1799). Association for the Advancement of
Computing in Education (AACE), 2015
[9] K. Abouelmehdi, A. Beni-Hessane and H. Khaloufi, “Big healthcare data: preserving
security and privacy”, Journal of Big Data, 5(1), p.1, 2018

11BUSINESS ANALYTICS
[10] M. Chowdhury, A. Apon and K. Dey, “Data analytics for intelligent transportation
systems”, Elsevier, 2017
[11] H. Drachsler and W. Greller, “Privacy and analytics: it's a DELICATE issue a
checklist for trusted learning analytics”, In Proceedings of the sixth international
conference on learning analytics & knowledge (pp. 89-98). ACM, 2016
[12] C.W. Tsai, C.F. Lai, H.C. Chao and A.V. Vasilakos, “Big data analytics: a survey”,
Journal of Big data, 2(1), p.21, 2015
13] K. Prema and A.V. Sriharsha, “Differential Privacy in Big Data Analytics for Haptic
Applications”, Technology, 8(3), pp.11-19, 2017
[14] X. Liu, S. Zhu, W. Wang and J. Liu, “Alde: privacy risk analysis of analytics libraries
in the android ecosystem”, In International Conference on Security and Privacy in
Communication Systems (pp. 655-672). Springer, Cham, 2016
[10] M. Chowdhury, A. Apon and K. Dey, “Data analytics for intelligent transportation
systems”, Elsevier, 2017
[11] H. Drachsler and W. Greller, “Privacy and analytics: it's a DELICATE issue a
checklist for trusted learning analytics”, In Proceedings of the sixth international
conference on learning analytics & knowledge (pp. 89-98). ACM, 2016
[12] C.W. Tsai, C.F. Lai, H.C. Chao and A.V. Vasilakos, “Big data analytics: a survey”,
Journal of Big data, 2(1), p.21, 2015
13] K. Prema and A.V. Sriharsha, “Differential Privacy in Big Data Analytics for Haptic
Applications”, Technology, 8(3), pp.11-19, 2017
[14] X. Liu, S. Zhu, W. Wang and J. Liu, “Alde: privacy risk analysis of analytics libraries
in the android ecosystem”, In International Conference on Security and Privacy in
Communication Systems (pp. 655-672). Springer, Cham, 2016
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





