Security Audit: Vulnerabilities, Controls, Safeguards for Assets
VerifiedAdded on 2022/09/01
|12
|2717
|30
Report
AI Summary
This document presents an audit report focusing on the security of six assets, identifying common vulnerabilities and exposures related to cash, prepaid expenses, marketable securities, inventory, accounts receivable, accounts payable, and tangible assets. The report discusses the importance of information security risk management, highlighting the need for continuous monitoring and adaptation due to evolving threats and functional changes. It reviews controls and policies, emphasizing the role of protective measures and countermeasures in mitigating risks. The audit simulation includes discussions on approaching asset simulation, threat characteristics, and valid safeguards that could be implemented to address the findings. The report concludes with an independent auditor's assessment of the security controls and safeguards of the company's assets, underlining management's responsibility in maintaining a secure environment.

Running head: AUDITING
Auditing
Name:
Institution:
Date:
Auditing
Name:
Institution:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
AUDIT
Group Discussion #1:
a) Identification of the four vulnerabilities for the various assets
Vulnerability is the threat that can exploit a weak asset. The component itself does not
cause damage because a threat without vulnerability is not dangerous to the organization. It is
however necessary to monitor the vulnerabilities so as to identify the ones that are able to use
new threats in instances where there are functional changes for the assets. In this paper, on
the basis of a common vulnerability assessment system that allows us to determine a
qualitative indicator of vulnerability of information systems taking into account
environmental factors, a risk assessment technique for various types of cloud deployment is
presented. Information risk management, determining the applicability of cloud services to an
organization is impossible without understanding the context in which the organization
operates and the consequences of the possible types of threats that it may encounter as a
result of its activities (Alles, Brennan, Kogan, & Vasarhelyi, 2018).. The article proposes an
approach to risk assessment, used when choosing the most appropriate option for configuring
the cloud computing environment from the point of view of security requirements. The
application of a risk assessment methodology for various types of cloud deployment will help
to identify the coefficient of resistance to possible attacks and to correlate the amount of
damage with the total cost of the entire IT infrastructure of the organization.
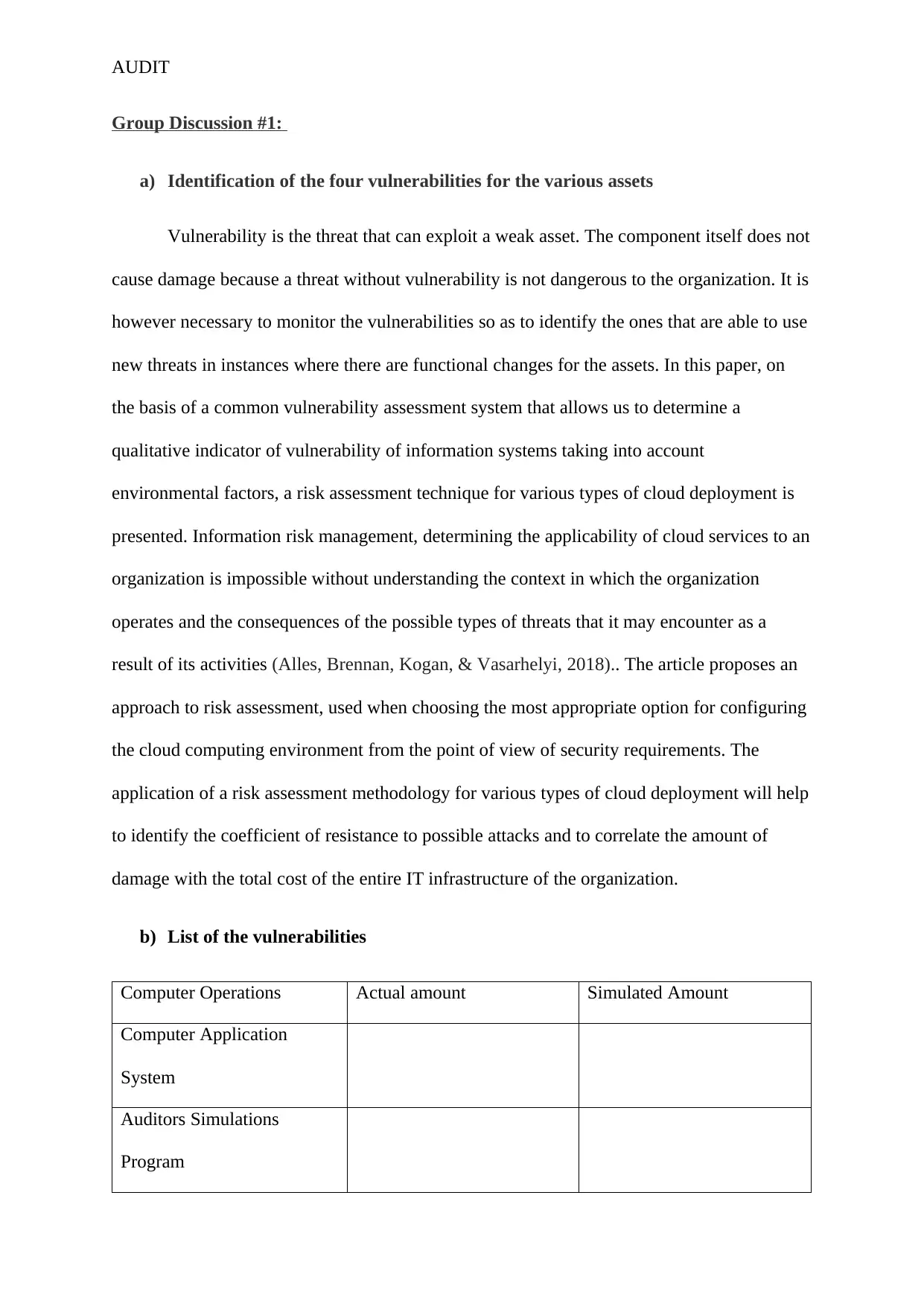
b) List of the vulnerabilities
Computer Operations Actual amount Simulated Amount
Computer Application
System
Auditors Simulations
Program
Group Discussion #1:
a) Identification of the four vulnerabilities for the various assets
Vulnerability is the threat that can exploit a weak asset. The component itself does not
cause damage because a threat without vulnerability is not dangerous to the organization. It is
however necessary to monitor the vulnerabilities so as to identify the ones that are able to use
new threats in instances where there are functional changes for the assets. In this paper, on
the basis of a common vulnerability assessment system that allows us to determine a
qualitative indicator of vulnerability of information systems taking into account
environmental factors, a risk assessment technique for various types of cloud deployment is
presented. Information risk management, determining the applicability of cloud services to an
organization is impossible without understanding the context in which the organization
operates and the consequences of the possible types of threats that it may encounter as a
result of its activities (Alles, Brennan, Kogan, & Vasarhelyi, 2018).. The article proposes an
approach to risk assessment, used when choosing the most appropriate option for configuring
the cloud computing environment from the point of view of security requirements. The
application of a risk assessment methodology for various types of cloud deployment will help
to identify the coefficient of resistance to possible attacks and to correlate the amount of
damage with the total cost of the entire IT infrastructure of the organization.
b) List of the vulnerabilities
Computer Operations Actual amount Simulated Amount
Computer Application
System
Auditors Simulations
Program
AUDIT
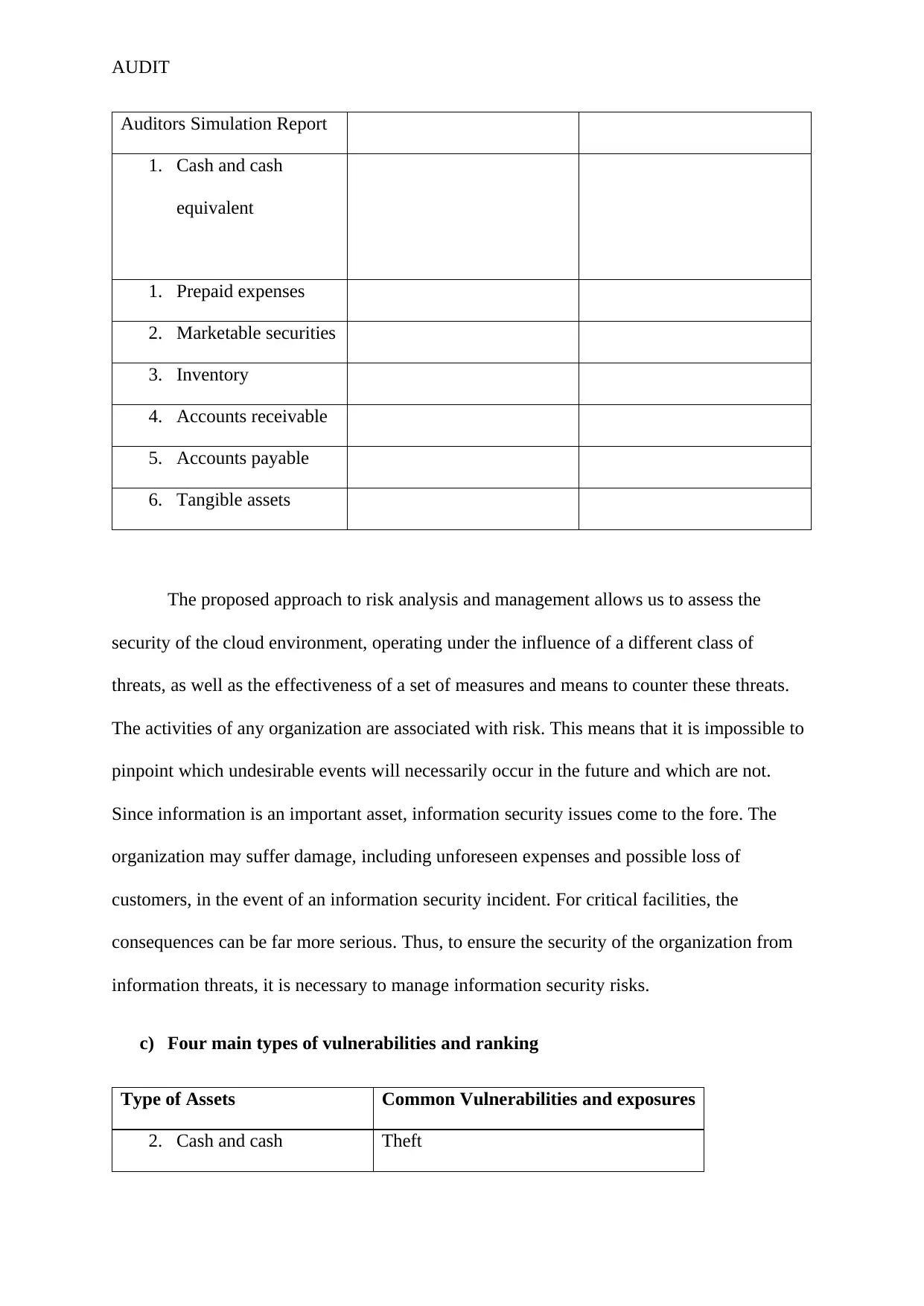
Auditors Simulation Report
1. Cash and cash
equivalent
1. Prepaid expenses
2. Marketable securities
3. Inventory
4. Accounts receivable
5. Accounts payable
6. Tangible assets
The proposed approach to risk analysis and management allows us to assess the
security of the cloud environment, operating under the influence of a different class of
threats, as well as the effectiveness of a set of measures and means to counter these threats.
The activities of any organization are associated with risk. This means that it is impossible to
pinpoint which undesirable events will necessarily occur in the future and which are not.
Since information is an important asset, information security issues come to the fore. The
organization may suffer damage, including unforeseen expenses and possible loss of
customers, in the event of an information security incident. For critical facilities, the
consequences can be far more serious. Thus, to ensure the security of the organization from
information threats, it is necessary to manage information security risks.
c) Four main types of vulnerabilities and ranking
Type of Assets Common Vulnerabilities and exposures
2. Cash and cash Theft
Auditors Simulation Report
1. Cash and cash
equivalent
1. Prepaid expenses
2. Marketable securities
3. Inventory
4. Accounts receivable
5. Accounts payable
6. Tangible assets
The proposed approach to risk analysis and management allows us to assess the
security of the cloud environment, operating under the influence of a different class of
threats, as well as the effectiveness of a set of measures and means to counter these threats.
The activities of any organization are associated with risk. This means that it is impossible to
pinpoint which undesirable events will necessarily occur in the future and which are not.
Since information is an important asset, information security issues come to the fore. The
organization may suffer damage, including unforeseen expenses and possible loss of
customers, in the event of an information security incident. For critical facilities, the
consequences can be far more serious. Thus, to ensure the security of the organization from
information threats, it is necessary to manage information security risks.
c) Four main types of vulnerabilities and ranking
Type of Assets Common Vulnerabilities and exposures
2. Cash and cash Theft
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AUDIT
equivalent
7. Prepaid expenses Data destruction
8. Marketable securities Data exposure
9. Inventory Data modification
10. Accounts receivable
11. Accounts payable
12. Tangible assets
Group Discussion #2:
a) Review the 3 controls/policies
A protective measure can be effective in mitigating the risks associated with a threat
that uses an asset vulnerability group. The risk is considered acceptable, and no measures are
implemented even in the presence of a threat and if the asset is vulnerable. A safeguard group
can be effective in reducing the risks associated with a group of threats that exploit the
vulnerability of an asset.. Security model Information security risk management process The
information security risk management process can be applied both to the entire organization
and to any part of it (division or information system). This process should be continuous,
since over time the security of the object weakens due to changes in the functionality of the
components and the emergence of new threats. Therefore, at all stages of the risk
management process, it is necessary to document the results obtained. In general, risk
management refers to a process that includes a context, assessment, processing and
monitoring of risks
b) Simulation report against controls of the group
equivalent
7. Prepaid expenses Data destruction
8. Marketable securities Data exposure
9. Inventory Data modification
10. Accounts receivable
11. Accounts payable
12. Tangible assets
Group Discussion #2:
a) Review the 3 controls/policies
A protective measure can be effective in mitigating the risks associated with a threat
that uses an asset vulnerability group. The risk is considered acceptable, and no measures are
implemented even in the presence of a threat and if the asset is vulnerable. A safeguard group
can be effective in reducing the risks associated with a group of threats that exploit the
vulnerability of an asset.. Security model Information security risk management process The
information security risk management process can be applied both to the entire organization
and to any part of it (division or information system). This process should be continuous,
since over time the security of the object weakens due to changes in the functionality of the
components and the emergence of new threats. Therefore, at all stages of the risk
management process, it is necessary to document the results obtained. In general, risk
management refers to a process that includes a context, assessment, processing and
monitoring of risks
b) Simulation report against controls of the group
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AUDIT
This component harms the organization by exploiting the vulnerabilities of its assets.
There are a large number of different classifications of threats, however, it is important to
understand that they can be not only targeted, but also random. The last security component
under consideration is countermeasures, that is, actions that can ensure security against the
threat. The choice of necessary countermeasures determines the effectiveness of measures to
ensure information security. The interconnection of security components shows how assets
can be exposed to threats (Chan, & Vasarhelyi, 2018).. These relationships are the five most
common scenarios: There is an asset vulnerability, but no threats are known that can exploit
it. A protective measure can be effective in reducing the risks associated with a threat that
could exploit the vulnerability of an asset.
The last security component under consideration is countermeasures, that is, actions
that can ensure security against the threat. The choice of necessary countermeasures
determines the effectiveness of measures to ensure information security. The interconnection
of security components shows how assets can be exposed to threats. These relationships are
the five most common scenarios: There is an asset vulnerability, but no threats are known that
can exploit it. A protective measure can be effective in reducing the risks associated with a
threat that could exploit the vulnerability of an asset.
Group Discussion #3:
a) Valid safeguards that could be implemented to address the findings from
audit
This component harms the organization by exploiting the vulnerabilities of its assets.
There are a large number of different classifications of threats, however, it is important to
understand that they can be not only targeted, but also random. The last security component
under consideration is countermeasures, that is, actions that can ensure security against the
threat. The choice of necessary countermeasures determines the effectiveness of measures to
ensure information security. The interconnection of security components shows how assets
can be exposed to threats (Chan, & Vasarhelyi, 2018).. These relationships are the five most
common scenarios: There is an asset vulnerability, but no threats are known that can exploit
it. A protective measure can be effective in reducing the risks associated with a threat that
could exploit the vulnerability of an asset.
The last security component under consideration is countermeasures, that is, actions
that can ensure security against the threat. The choice of necessary countermeasures
determines the effectiveness of measures to ensure information security. The interconnection
of security components shows how assets can be exposed to threats. These relationships are
the five most common scenarios: There is an asset vulnerability, but no threats are known that
can exploit it. A protective measure can be effective in reducing the risks associated with a
threat that could exploit the vulnerability of an asset.
Group Discussion #3:
a) Valid safeguards that could be implemented to address the findings from
audit

AUDIT
A safeguard group can be effective in reducing the risks associated with a group of
threats that exploit the vulnerability of an asset. A protective measure can be effective in
mitigating the risks associated with a threat that uses an asset vulnerability group. The risk is
considered acceptable, and no measures are implemented even in the presence of a threat and
if the asset is vulnerable.For each threat, a decision must be made: accept the risk, reduce the
risk or transfer the risk. Accepting risk means realizing it, accepting its ability and continuing
to act as before. Applicable for threats with low damage and low probability of occurrence.
To reduce risk means to introduce additional measures and means of protection,
conduct staff training, etc. That is, carry out deliberate work to reduce risk. In this case, it is
necessary to quantify the effectiveness of additional measures and remedies. All costs
incurred by the organization, from the purchase of protective equipment to commissioning
(including installation, configuration, training, maintenance, etc.), must not exceed the
amount of damage from the implementation of the threat.
To transfer risk means to transfer the consequences of the risk to a third party, for example,
through insurance.
As a result of a quantitative risk assessment, the following should be determined:
value of assets in monetary terms; A complete list of all IS threats with damage from a single
incident for each threat; frequency of implementation of each threat; potential damage from
each threat;
Recommended security measures, countermeasures and actions for each threat.
Now it is necessary to evaluate expertly how often such a situation may arise (taking into
account the intensity of operation, the quality of power supply, etc.)
A safeguard group can be effective in reducing the risks associated with a group of
threats that exploit the vulnerability of an asset. A protective measure can be effective in
mitigating the risks associated with a threat that uses an asset vulnerability group. The risk is
considered acceptable, and no measures are implemented even in the presence of a threat and
if the asset is vulnerable.For each threat, a decision must be made: accept the risk, reduce the
risk or transfer the risk. Accepting risk means realizing it, accepting its ability and continuing
to act as before. Applicable for threats with low damage and low probability of occurrence.
To reduce risk means to introduce additional measures and means of protection,
conduct staff training, etc. That is, carry out deliberate work to reduce risk. In this case, it is
necessary to quantify the effectiveness of additional measures and remedies. All costs
incurred by the organization, from the purchase of protective equipment to commissioning
(including installation, configuration, training, maintenance, etc.), must not exceed the
amount of damage from the implementation of the threat.
To transfer risk means to transfer the consequences of the risk to a third party, for example,
through insurance.
As a result of a quantitative risk assessment, the following should be determined:
value of assets in monetary terms; A complete list of all IS threats with damage from a single
incident for each threat; frequency of implementation of each threat; potential damage from
each threat;
Recommended security measures, countermeasures and actions for each threat.
Now it is necessary to evaluate expertly how often such a situation may arise (taking into
account the intensity of operation, the quality of power supply, etc.)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AUDIT
An analysis of information security risks by a qualitative method should be carried out with
the involvement of employees with experience and competencies in the area in which threats
are considered.
How to conduct a qualitative risk assessment:
1. Determine the value of information assets.
The asset value can be determined by the level of criticality (consequences) in case of
violation of the security characteristics (confidentiality, integrity, availability) of the
information asset.
2. Determine the likelihood of the threat in relation to the information asset.
To assess the likelihood of a threat, a three-level quality scale can be used (low, medium,
high).
3. Determine the level of possibility of successful implementation of the threat, taking into
account the current state of information security, implemented measures and means of
protection (Hall, (2015)..
A three-level quality scale (low, medium, high) can also be used to assess the level of
possibility of implementing a threat. The importance of the possibility of implementing a
threat shows how feasible the successful implementation of the threat is.
4. To draw a conclusion about the level of risk on the basis of the value of the information
asset, the probability of the threat, the possibility of the threat.
To determine the level of risk, you can use a five-point or ten-point scale. (Lins, Schneider, &
Sunyaev, 2016)..
An analysis of information security risks by a qualitative method should be carried out with
the involvement of employees with experience and competencies in the area in which threats
are considered.
How to conduct a qualitative risk assessment:
1. Determine the value of information assets.
The asset value can be determined by the level of criticality (consequences) in case of
violation of the security characteristics (confidentiality, integrity, availability) of the
information asset.
2. Determine the likelihood of the threat in relation to the information asset.
To assess the likelihood of a threat, a three-level quality scale can be used (low, medium,
high).
3. Determine the level of possibility of successful implementation of the threat, taking into
account the current state of information security, implemented measures and means of
protection (Hall, (2015)..
A three-level quality scale (low, medium, high) can also be used to assess the level of
possibility of implementing a threat. The importance of the possibility of implementing a
threat shows how feasible the successful implementation of the threat is.
4. To draw a conclusion about the level of risk on the basis of the value of the information
asset, the probability of the threat, the possibility of the threat.
To determine the level of risk, you can use a five-point or ten-point scale. (Lins, Schneider, &
Sunyaev, 2016)..
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AUDIT
The next step is to identify existing controls. An understanding is formed of what is
already in the organization and how effective it is. Then, threats and vulnerabilities are
identified. The results are issued in the form of two documents: a list of threats and a list of
vulnerabilities. The last element of this stage is the identification of consequences, which
consists in compiling a list of scenarios of information security incidents with their
consequences for the organization. Often, when conducting a high-level risk assessment
based on the results of a meeting with the parties involved, this list of scenarios is formed,
based on which a detailed risk assessment is carried out. Risk analysis - the process of
studying the nature of the risk and determining the level of risk. This stage includes an
assessment of the severity of the consequences and their corresponding probabilities. In turn,
the probability value includes both the probability of the threat occurring and the probability
that the threat uses the vulnerability of the asset to cause damage. The methods used in risk
analysis can be quantitative, qualitative, or mixed (Groomer, & Murthy, 2018). Depending on
the needs of the organization and the availability of reliable data, the degree of detail of the
analysis is determined. In practice, a qualitative assessment is often used first to obtain
general information about the level of risk. Later, it may be necessary to carry out a more in-
depth analysis, as a result of which a quantitative risk assessment will be applied. When
assessing the severity of the consequences, data on the asset value table are taken into
account, as well as damage assessment results.
Group Submission
Simulate an audit of the information system : Description of how the group
would approach the simulation of the Assets
The next step is to identify existing controls. An understanding is formed of what is
already in the organization and how effective it is. Then, threats and vulnerabilities are
identified. The results are issued in the form of two documents: a list of threats and a list of
vulnerabilities. The last element of this stage is the identification of consequences, which
consists in compiling a list of scenarios of information security incidents with their
consequences for the organization. Often, when conducting a high-level risk assessment
based on the results of a meeting with the parties involved, this list of scenarios is formed,
based on which a detailed risk assessment is carried out. Risk analysis - the process of
studying the nature of the risk and determining the level of risk. This stage includes an
assessment of the severity of the consequences and their corresponding probabilities. In turn,
the probability value includes both the probability of the threat occurring and the probability
that the threat uses the vulnerability of the asset to cause damage. The methods used in risk
analysis can be quantitative, qualitative, or mixed (Groomer, & Murthy, 2018). Depending on
the needs of the organization and the availability of reliable data, the degree of detail of the
analysis is determined. In practice, a qualitative assessment is often used first to obtain
general information about the level of risk. Later, it may be necessary to carry out a more in-
depth analysis, as a result of which a quantitative risk assessment will be applied. When
assessing the severity of the consequences, data on the asset value table are taken into
account, as well as damage assessment results.
Group Submission
Simulate an audit of the information system : Description of how the group
would approach the simulation of the Assets

AUDIT
The main features that characterize the threat: source, frequency of occurrence,
harmful effect. As a component of security, risk is the ability of a threat to exploit the
vulnerability of an asset to harm an organization. Risk is characterized by a combination of
the probability of an information security incident and the consequences of such an incident.
It is important to understand that risk is never completely eliminated. Acceptance of residual
risk is part of the conclusion that the security level meets the organization's needs. The
system can develop and implement an effective security program, but lose sight of any asset,
as a result of which the actual protection of the organization from information security threats
will differ from the established one. The degree of detail for this phase is based on safety
objectives. The next security component under consideration is the threat.
Individual portion
AUDIT REPORT
Audit Report : Independent Auditors Report on the Security of Six Assets.
To the
Board of Management
ABC Company
This is an audit report on the security controls and safeguards of the assets of the
company. The six assets include;
Assets Common Vulnerabilities and exposures
Cash and cash
equivalent
Theft
The main features that characterize the threat: source, frequency of occurrence,
harmful effect. As a component of security, risk is the ability of a threat to exploit the
vulnerability of an asset to harm an organization. Risk is characterized by a combination of
the probability of an information security incident and the consequences of such an incident.
It is important to understand that risk is never completely eliminated. Acceptance of residual
risk is part of the conclusion that the security level meets the organization's needs. The
system can develop and implement an effective security program, but lose sight of any asset,
as a result of which the actual protection of the organization from information security threats
will differ from the established one. The degree of detail for this phase is based on safety
objectives. The next security component under consideration is the threat.
Individual portion
AUDIT REPORT
Audit Report : Independent Auditors Report on the Security of Six Assets.
To the
Board of Management
ABC Company
This is an audit report on the security controls and safeguards of the assets of the
company. The six assets include;
Assets Common Vulnerabilities and exposures
Cash and cash
equivalent
Theft
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AUDIT
Prepaid expenses Data destruction
Marketable securities Data exposure
Inventory Data modification
Accounts receivable
Accounts payable
Tangible assets
Management Responsibility
The most obvious criterion is the financial loss that the organization will incur if the
information security incident is successfully implemented. However, it is important to
understand that this criterion reflects only part of the “big picture” of the consequences. For
example, for critical facilities, in addition to financial losses, it is also necessary to take into
account environmental consequences. In this regard, at this stage, all the necessary criteria are
included in the damage assessment table in order to comprehensively cover the main types of
consequences for the organization, taking into account its activities. As an example, consider
the most common criteria: financial loss and loss of reputation of the organization. To include
them in the damage assessment table, it is necessary to refer to the scale of damage
assessment criteria established at the stage of the risk management context. The values of this
scale in the example are arbitrary and depend on the characteristics of the organization.
Auditors Responsibility
How to quantify risks?
1. Determine the value of information assets in monetary terms.
Prepaid expenses Data destruction
Marketable securities Data exposure
Inventory Data modification
Accounts receivable
Accounts payable
Tangible assets
Management Responsibility
The most obvious criterion is the financial loss that the organization will incur if the
information security incident is successfully implemented. However, it is important to
understand that this criterion reflects only part of the “big picture” of the consequences. For
example, for critical facilities, in addition to financial losses, it is also necessary to take into
account environmental consequences. In this regard, at this stage, all the necessary criteria are
included in the damage assessment table in order to comprehensively cover the main types of
consequences for the organization, taking into account its activities. As an example, consider
the most common criteria: financial loss and loss of reputation of the organization. To include
them in the damage assessment table, it is necessary to refer to the scale of damage
assessment criteria established at the stage of the risk management context. The values of this
scale in the example are arbitrary and depend on the characteristics of the organization.
Auditors Responsibility
How to quantify risks?
1. Determine the value of information assets in monetary terms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AUDIT
2. To quantify the potential damage from the implementation of each threat in relation to each
information asset.
Answers to the questions “What part of the value of the asset will be the damage from the
realization of each threat?”, “What is the cost of damage in monetary terms from a single
incident when this threat is realized to this asset?”
3. Determine the likelihood of each of the threats of information security.
To do this, you can use statistics, surveys of employees and stakeholders. In the process of
determining the probability, calculate the frequency of incidents related to the
implementation of the IS threat under consideration for the control period (for example, for
one year).
4. Determine the total potential damage from each threat in relation to each asset for the
control period (for one year).
Opinion
The opinion on assets security can either be qualified, unqualified or an adverse opinion. This
is based on the security levels and the transparency of the financials from the assets. The
value is calculated by multiplying the one-time damage from the threat realization by the
frequency of the threat realization.
Yours Faithfully
HHM Auditors
2. To quantify the potential damage from the implementation of each threat in relation to each
information asset.
Answers to the questions “What part of the value of the asset will be the damage from the
realization of each threat?”, “What is the cost of damage in monetary terms from a single
incident when this threat is realized to this asset?”
3. Determine the likelihood of each of the threats of information security.
To do this, you can use statistics, surveys of employees and stakeholders. In the process of
determining the probability, calculate the frequency of incidents related to the
implementation of the IS threat under consideration for the control period (for example, for
one year).
4. Determine the total potential damage from each threat in relation to each asset for the
control period (for one year).
Opinion
The opinion on assets security can either be qualified, unqualified or an adverse opinion. This
is based on the security levels and the transparency of the financials from the assets. The
value is calculated by multiplying the one-time damage from the threat realization by the
frequency of the threat realization.
Yours Faithfully
HHM Auditors

AUDIT
References
Alles, M., Brennan, G., Kogan, A., & Vasarhelyi, M. A. (2018). Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald
Publishing Limited.
Chan, D. Y., & Vasarhelyi, M. A. (2018). Innovation and practice of continuous auditing.
In Continuous Auditing: Theory and Application (pp. 271-283). Emerald Publishing
Limited.
Groomer, S. M., & Murthy, U. S. (2018). Continuous auditing of database applications: An
embedded audit module approach. In Continuous Auditing: Theory and
Application (pp. 105-124). Emerald Publishing Limited.
Hall, J. A. (2015). Information technology auditing. Cengage Learning.
Lins, S., Schneider, S., & Sunyaev, A. (2016). Trust is good, control is better: Creating secure
clouds by continuous auditing. IEEE Transactions on Cloud Computing, 6(3), 890-
903.
References
Alles, M., Brennan, G., Kogan, A., & Vasarhelyi, M. A. (2018). Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald
Publishing Limited.
Chan, D. Y., & Vasarhelyi, M. A. (2018). Innovation and practice of continuous auditing.
In Continuous Auditing: Theory and Application (pp. 271-283). Emerald Publishing
Limited.
Groomer, S. M., & Murthy, U. S. (2018). Continuous auditing of database applications: An
embedded audit module approach. In Continuous Auditing: Theory and
Application (pp. 105-124). Emerald Publishing Limited.
Hall, J. A. (2015). Information technology auditing. Cengage Learning.
Lins, S., Schneider, S., & Sunyaev, A. (2016). Trust is good, control is better: Creating secure
clouds by continuous auditing. IEEE Transactions on Cloud Computing, 6(3), 890-
903.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




