Information Security: CIA Triad, Biometrics and Cryptography
VerifiedAdded on 2023/06/13
|8
|1576
|270
Homework Assignment
AI Summary
This assignment delves into various aspects of information security, starting with an explanation of the CIA triad and its application in safeguarding data privacy, particularly concerning PIN numbers and data encryption techniques. It explores ATM security, calculating the probability of guessing a PIN with limited attempts using permutation and combination concepts. The assignment further discusses the advantages and disadvantages of biometric systems, including issues like recognition failures and data breaches, suggesting solutions such as multi-layer authentication and regular software updates. It also defines false positives and false negatives in biometric systems and their potential impacts on organizational security. Finally, the assignment includes a practical decryption exercise using substitution and Caesar ciphers to decode an encrypted message related to processor speed, demonstrating cryptographic principles. Desklib provides access to past papers and solved assignments for students seeking further assistance.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................4
References............................................................................................................................7
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................4
Answer to Question 5:.........................................................................................................4
References............................................................................................................................7

2INFORMATION SECURITY
Answer to Question 1:
CIA triad can be considered nothing but a guide, which can be used for taking the
security measures related to the information. Information security can be directly be related to
the concept of how the different security measures can be implemented with the concept of the
data. In this scenario, the privacy aspect is related to the confidentiality taking into consideration
the PIN number (Haque, Nasrollahi & Moeslund, 2015). The concept of PIN number is that it is
a set of number, which can be used for the personal identification, which can be used for the
purpose of transaction. The main aim of the aspect is the safeguard the data from any type of
intrusion so that it can be saved in a secured manner. Safeguarding the data can sometimes
require special type of training. Data encryption can be considered one of the technology, which
can be used which can be implemented to keep the data safe.
Answer to Question 2:
The entire keyboard of the ATM machine consist of ten keys (0 to 9). In the scenario, it is
seen that the thief has broken five keys and the keys, which are available to him, are five keys.
The PIN number consist of combination of four numbers (Alsaadi, 2015). The concept, which is
applied to the aspect in order to find out the number of tries, is the permutation and combination
concept.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
From the above equation, it can be stated that the possible outcome is 120. According to
the rules of the ATM security, a user can indulge into a maximum of three tries. After the third
try, the card would be blocked. Therefore, the thief also has three tries to get the right PIN into
the system.
Answer to Question 1:
CIA triad can be considered nothing but a guide, which can be used for taking the
security measures related to the information. Information security can be directly be related to
the concept of how the different security measures can be implemented with the concept of the
data. In this scenario, the privacy aspect is related to the confidentiality taking into consideration
the PIN number (Haque, Nasrollahi & Moeslund, 2015). The concept of PIN number is that it is
a set of number, which can be used for the personal identification, which can be used for the
purpose of transaction. The main aim of the aspect is the safeguard the data from any type of
intrusion so that it can be saved in a secured manner. Safeguarding the data can sometimes
require special type of training. Data encryption can be considered one of the technology, which
can be used which can be implemented to keep the data safe.
Answer to Question 2:
The entire keyboard of the ATM machine consist of ten keys (0 to 9). In the scenario, it is
seen that the thief has broken five keys and the keys, which are available to him, are five keys.
The PIN number consist of combination of four numbers (Alsaadi, 2015). The concept, which is
applied to the aspect in order to find out the number of tries, is the permutation and combination
concept.
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
From the above equation, it can be stated that the possible outcome is 120. According to
the rules of the ATM security, a user can indulge into a maximum of three tries. After the third
try, the card would be blocked. Therefore, the thief also has three tries to get the right PIN into
the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
Answer to Question 3:
In the technology, which is related to the biometric system, there are many advantage
which can be received but on the other hand there are also different types of problem which can
be encountered. Some of the example of the problem are stated below:
One of the biggest problem, which can be seen in the technology, is the recognition of the
person. It is sometimes seen that that a person is not recognized by the system as a result of
which they are not given the permission of access. It can make life hectic when the concept is
implemented into any organization.
Another problem, which can be encountered, is that false detection of the individual. It can
be seen that many a times the identification of another person is taken into account. In this
aspect, a person can perform different types of unethical practices with the identification of
another person.
The biometric system usually stores the personal information of the user in such a case if an
intruder gets into the system they would be able to get the personal information of the user
and use it for their own personal. This can be directly harmful for the user (Haque, M. A.,
Nasrollahi & Moeslund, 2015). In most of the cases the security the machine would be the
only factor which would be involved. It can be harmful from the point of view of the
organization and the user as well.
There are certain steps, which can be included into the concept of the biometric such as
multilayer authentication, which helps securing the identity of a person, and enhanced security
measures, which would be securing the data of the user from intruders. There can be also
Answer to Question 3:
In the technology, which is related to the biometric system, there are many advantage
which can be received but on the other hand there are also different types of problem which can
be encountered. Some of the example of the problem are stated below:
One of the biggest problem, which can be seen in the technology, is the recognition of the
person. It is sometimes seen that that a person is not recognized by the system as a result of
which they are not given the permission of access. It can make life hectic when the concept is
implemented into any organization.
Another problem, which can be encountered, is that false detection of the individual. It can
be seen that many a times the identification of another person is taken into account. In this
aspect, a person can perform different types of unethical practices with the identification of
another person.
The biometric system usually stores the personal information of the user in such a case if an
intruder gets into the system they would be able to get the personal information of the user
and use it for their own personal. This can be directly harmful for the user (Haque, M. A.,
Nasrollahi & Moeslund, 2015). In most of the cases the security the machine would be the
only factor which would be involved. It can be harmful from the point of view of the
organization and the user as well.
There are certain steps, which can be included into the concept of the biometric such as
multilayer authentication, which helps securing the identity of a person, and enhanced security
measures, which would be securing the data of the user from intruders. There can be also
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
personal attacks, which can be harmful from the point of view of the actual user (Alsaadi, 2015).
The system should be always updated with the later software so that the security measures in the
aspect can be dealt quite easily and would be involving the latest patch of the software security
(Deokar, S. R Wakode, 2017).
Answer to Question 4:
The concept of false negative is a situation when the user is not recognized by the system.
When the concept of biometric is implemented within a system and the user is not identified it
can create different types of problem in the scenario. It can be very much problem if the user is
not identified in a proper time framework. On the other hand the false positive aspect is when the
identification is done but of some other individual. In this case, a person can indulge into some
sort of unethical activity by using the name or identification of another person. On an
organizational system it can have a bad impact on the overall working of the system and can
result in the shutting down of the over infrastructure (Ali & Afzal, 2017).
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
personal attacks, which can be harmful from the point of view of the actual user (Alsaadi, 2015).
The system should be always updated with the later software so that the security measures in the
aspect can be dealt quite easily and would be involving the latest patch of the software security
(Deokar, S. R Wakode, 2017).
Answer to Question 4:
The concept of false negative is a situation when the user is not recognized by the system.
When the concept of biometric is implemented within a system and the user is not identified it
can create different types of problem in the scenario. It can be very much problem if the user is
not identified in a proper time framework. On the other hand the false positive aspect is when the
identification is done but of some other individual. In this case, a person can indulge into some
sort of unethical activity by using the name or identification of another person. On an
organizational system it can have a bad impact on the overall working of the system and can
result in the shutting down of the over infrastructure (Ali & Afzal, 2017).
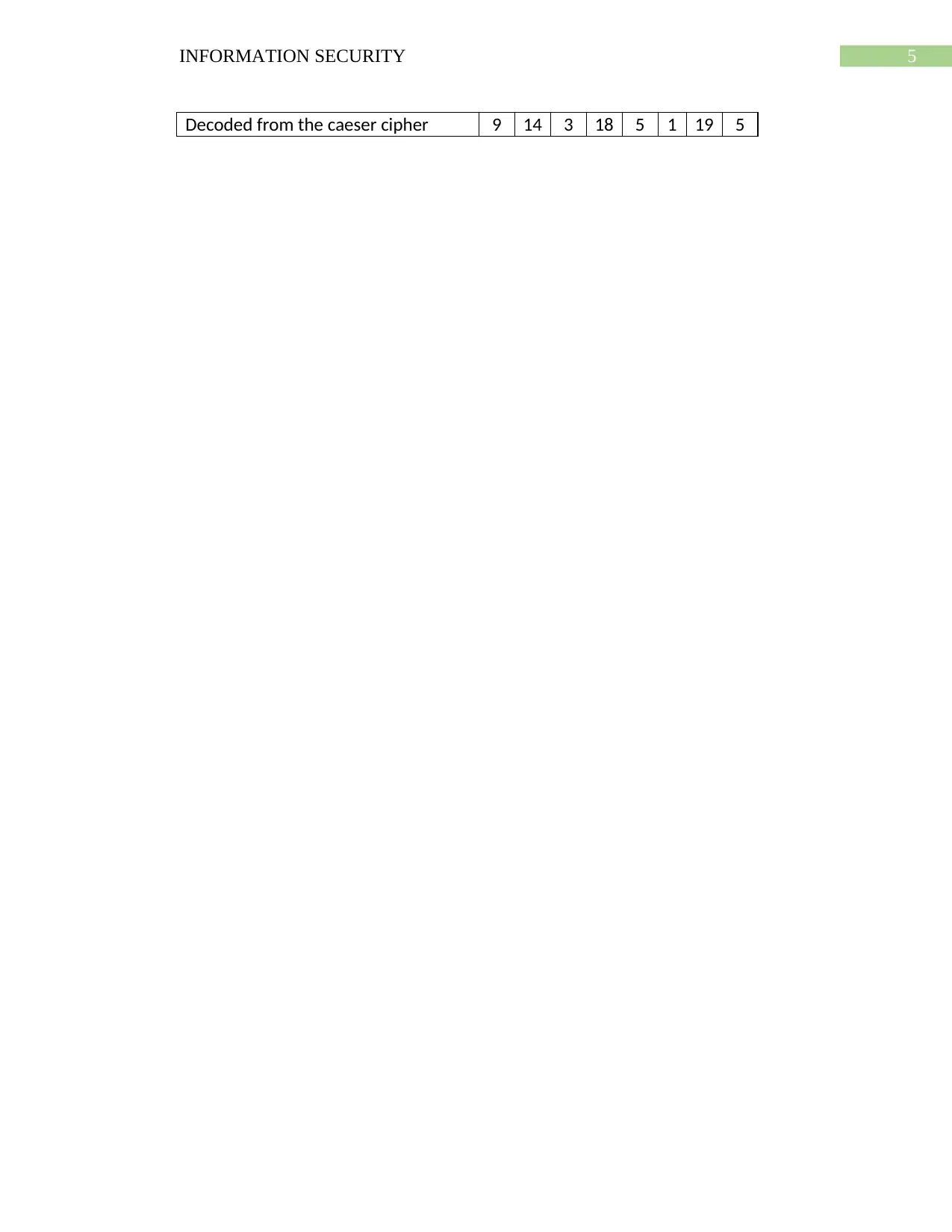
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
5INFORMATION SECURITY
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY
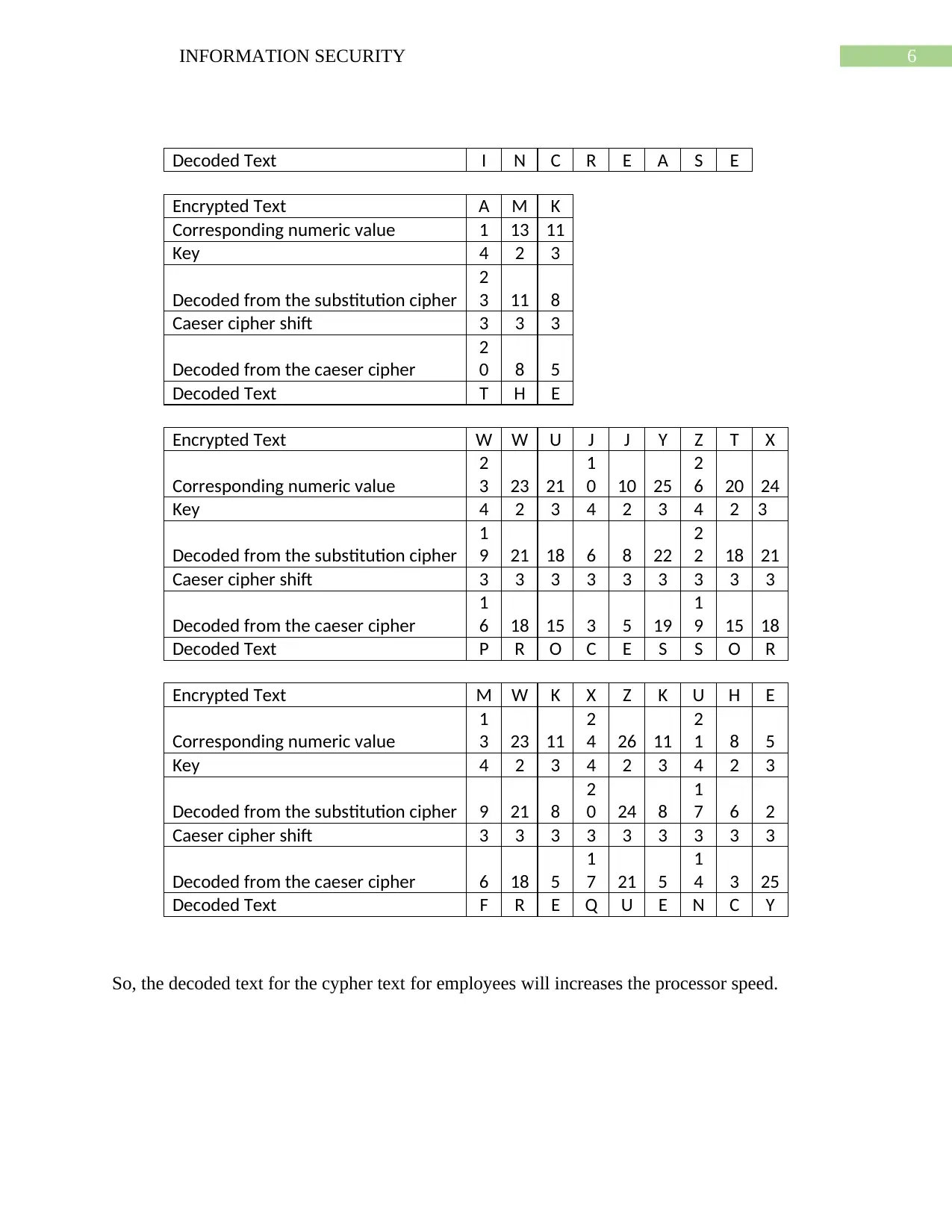
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
So, the decoded text for the cypher text for employees will increases the processor speed.
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
So, the decoded text for the cypher text for employees will increases the processor speed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
References
Ali, A., & Afzal, M. M. (2017). Database Security: Threats and Solutions. International Journal
of Engineering Inventions, 6(2), 25-27.
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.
References
Ali, A., & Afzal, M. M. (2017). Database Security: Threats and Solutions. International Journal
of Engineering Inventions, 6(2), 25-27.
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



