Comprehensive Report: Computer Security, Asynchronous I/O, Sony PSN
VerifiedAdded on 2020/10/23
|10
|3282
|261
Report
AI Summary
This report delves into the realm of information security, examining computer security breaches that occurred between April 2015 and August 2018, including the Facebook-Cambridge Analytica data scandal. It explores the problems, causes, and potential solutions to these breaches, highlighting the impact of data loss and the increasing sophistication of cyberattacks. The report also investigates asynchronous I/O activity and memory protection schemes, such as base/bounds and paging, and discusses the 2011 Sony PlayStation Network outage, analyzing the event's impact and causes. The report presents a comprehensive overview of information security challenges and provides insights into safeguarding data against malicious intent.

Research essay and case
study
study
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
PART A...........................................................................................................................................1
1) Web for news on security breaches of computer which occurred during April-August 2015-
2018. Prepare report and focus on what problem was, how, why it occurred and what are
effective solutions...................................................................................................................1
2) Asynchronous I/O activity is problem with many memory protection schemes, consisting
base/bounds and paging..........................................................................................................3
PART B............................................................................................................................................5
1) 2011 Sony PlayStation Network outage case.....................................................................5
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8
.........................................................................................................................................................8
INTRODUCTION...........................................................................................................................1
PART A...........................................................................................................................................1
1) Web for news on security breaches of computer which occurred during April-August 2015-
2018. Prepare report and focus on what problem was, how, why it occurred and what are
effective solutions...................................................................................................................1
2) Asynchronous I/O activity is problem with many memory protection schemes, consisting
base/bounds and paging..........................................................................................................3
PART B............................................................................................................................................5
1) 2011 Sony PlayStation Network outage case.....................................................................5
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8
.........................................................................................................................................................8
INTRODUCTION
Information security refers to practice of preventing an unauthorized access, disclosure,
modification, use and recording of information. Data or information can be in the form of
physical or electronic. The main purpose to design Information security is to protect an integrity,
confidentiality and also availability of data with any malicious intentions. Under this, mention
report will be discuss about the computer security beaches which occurred and focus on problem
and their solutions (Datoo, 2018). There will be discussion about the asynchronous input and
output activity with several memory protection schemes. The case of 2011 Sony PlayStation
Network on web will be mention in this given report in detailed manner.
PART A
1) Web for news on security breaches of computer which occurred during April-August 2015-
2018. Prepare report and focus on what problem was, how, why it occurred and what are
effective solutions
Data breach scandals are problems for major organizations all around the world. As the
loss of personal data of the users can be used by the hacker for any illegal activities without their
permission. This is happening because of increase in numbers of skilful hackers to get the
personal data without permission to full-fill personal needs. Companies like Google, Facebook,
Domino's Pizza, and many more which are well known for their securities has also been
witnessed for data breaches. Some of the big data breaches occurred between April-August
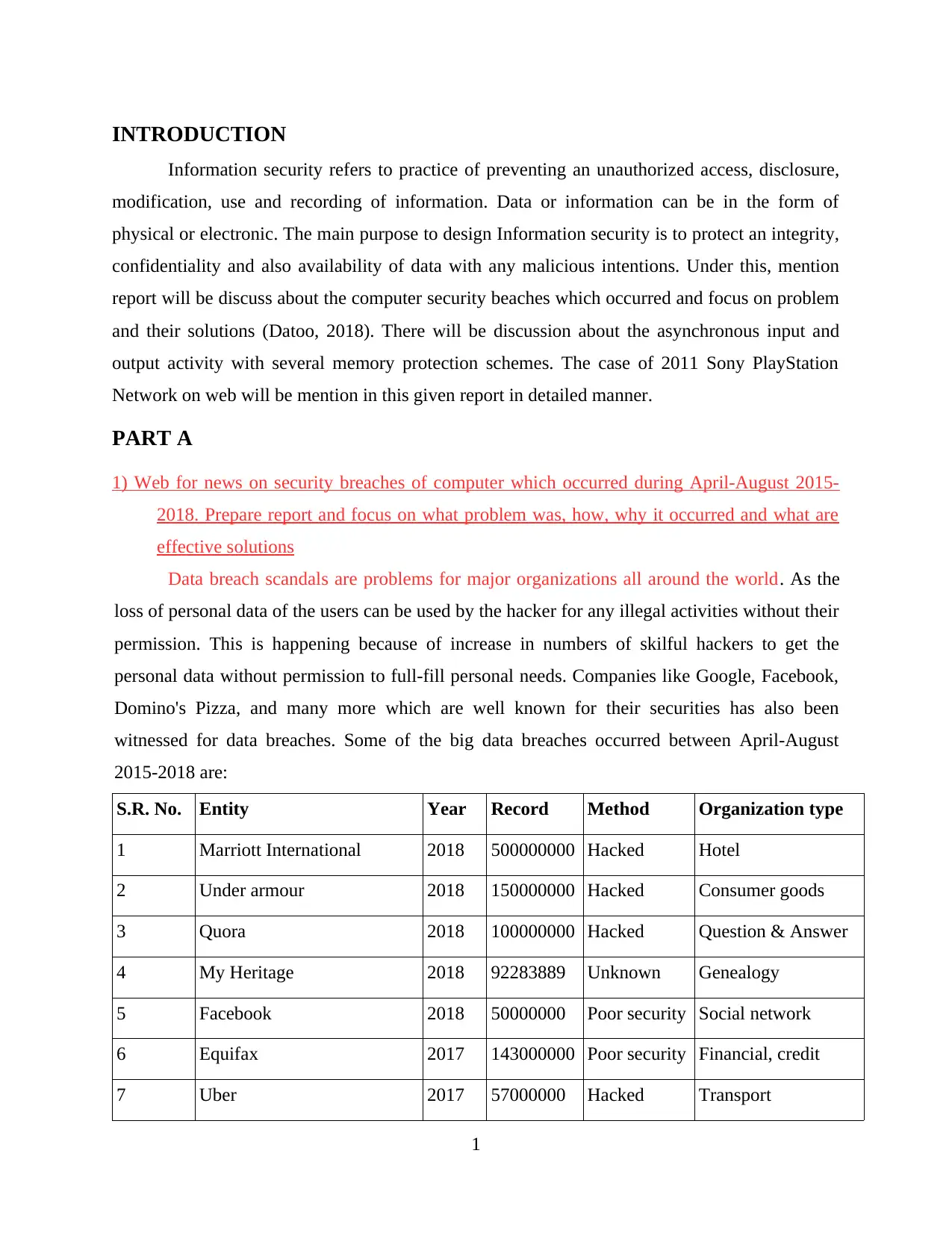
2015-2018 are:
S.R. No. Entity Year Record Method Organization type
1 Marriott International 2018 500000000 Hacked Hotel
2 Under armour 2018 150000000 Hacked Consumer goods
3 Quora 2018 100000000 Hacked Question & Answer
4 My Heritage 2018 92283889 Unknown Genealogy
5 Facebook 2018 50000000 Poor security Social network
6 Equifax 2017 143000000 Poor security Financial, credit
7 Uber 2017 57000000 Hacked Transport
1
Information security refers to practice of preventing an unauthorized access, disclosure,
modification, use and recording of information. Data or information can be in the form of
physical or electronic. The main purpose to design Information security is to protect an integrity,
confidentiality and also availability of data with any malicious intentions. Under this, mention
report will be discuss about the computer security beaches which occurred and focus on problem
and their solutions (Datoo, 2018). There will be discussion about the asynchronous input and
output activity with several memory protection schemes. The case of 2011 Sony PlayStation
Network on web will be mention in this given report in detailed manner.
PART A
1) Web for news on security breaches of computer which occurred during April-August 2015-
2018. Prepare report and focus on what problem was, how, why it occurred and what are
effective solutions
Data breach scandals are problems for major organizations all around the world. As the
loss of personal data of the users can be used by the hacker for any illegal activities without their
permission. This is happening because of increase in numbers of skilful hackers to get the
personal data without permission to full-fill personal needs. Companies like Google, Facebook,
Domino's Pizza, and many more which are well known for their securities has also been
witnessed for data breaches. Some of the big data breaches occurred between April-August
2015-2018 are:
S.R. No. Entity Year Record Method Organization type
1 Marriott International 2018 500000000 Hacked Hotel
2 Under armour 2018 150000000 Hacked Consumer goods
3 Quora 2018 100000000 Hacked Question & Answer
4 My Heritage 2018 92283889 Unknown Genealogy
5 Facebook 2018 50000000 Poor security Social network
6 Equifax 2017 143000000 Poor security Financial, credit
7 Uber 2017 57000000 Hacked Transport
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
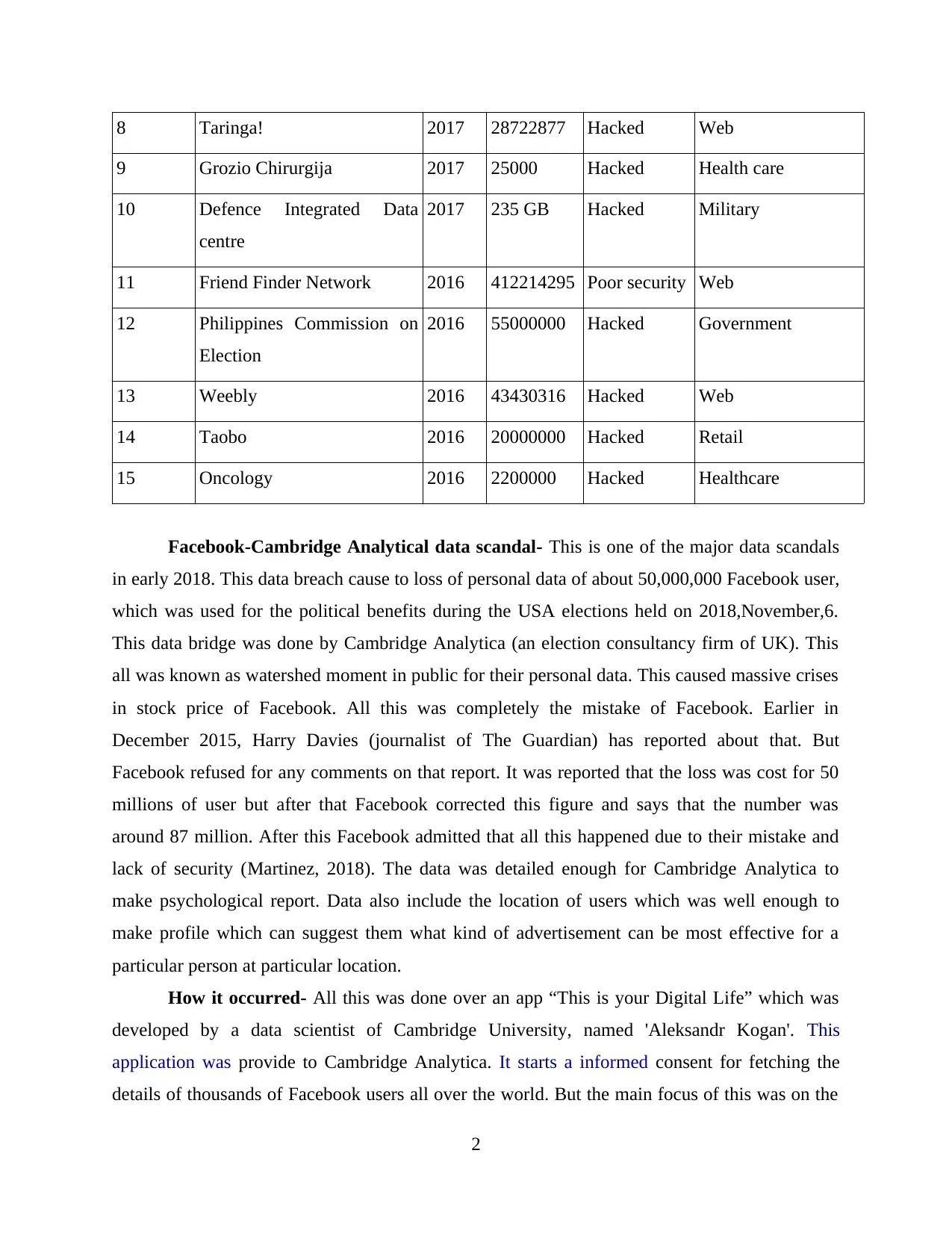
8 Taringa! 2017 28722877 Hacked Web
9 Grozio Chirurgija 2017 25000 Hacked Health care
10 Defence Integrated Data
centre
2017 235 GB Hacked Military
11 Friend Finder Network 2016 412214295 Poor security Web
12 Philippines Commission on
Election
2016 55000000 Hacked Government
13 Weebly 2016 43430316 Hacked Web
14 Taobo 2016 20000000 Hacked Retail
15 Oncology 2016 2200000 Hacked Healthcare
Facebook-Cambridge Analytical data scandal- This is one of the major data scandals
in early 2018. This data breach cause to loss of personal data of about 50,000,000 Facebook user,
which was used for the political benefits during the USA elections held on 2018,November,6.
This data bridge was done by Cambridge Analytica (an election consultancy firm of UK). This
all was known as watershed moment in public for their personal data. This caused massive crises
in stock price of Facebook. All this was completely the mistake of Facebook. Earlier in
December 2015, Harry Davies (journalist of The Guardian) has reported about that. But
Facebook refused for any comments on that report. It was reported that the loss was cost for 50
millions of user but after that Facebook corrected this figure and says that the number was
around 87 million. After this Facebook admitted that all this happened due to their mistake and
lack of security (Martinez, 2018). The data was detailed enough for Cambridge Analytica to
make psychological report. Data also include the location of users which was well enough to
make profile which can suggest them what kind of advertisement can be most effective for a
particular person at particular location.
How it occurred- All this was done over an app “This is your Digital Life” which was
developed by a data scientist of Cambridge University, named 'Aleksandr Kogan'. This
application was provide to Cambridge Analytica. It starts a informed consent for fetching the
details of thousands of Facebook users all over the world. But the main focus of this was on the
2
9 Grozio Chirurgija 2017 25000 Hacked Health care
10 Defence Integrated Data
centre
2017 235 GB Hacked Military
11 Friend Finder Network 2016 412214295 Poor security Web
12 Philippines Commission on
Election
2016 55000000 Hacked Government
13 Weebly 2016 43430316 Hacked Web
14 Taobo 2016 20000000 Hacked Retail
15 Oncology 2016 2200000 Hacked Healthcare
Facebook-Cambridge Analytical data scandal- This is one of the major data scandals
in early 2018. This data breach cause to loss of personal data of about 50,000,000 Facebook user,
which was used for the political benefits during the USA elections held on 2018,November,6.
This data bridge was done by Cambridge Analytica (an election consultancy firm of UK). This
all was known as watershed moment in public for their personal data. This caused massive crises
in stock price of Facebook. All this was completely the mistake of Facebook. Earlier in
December 2015, Harry Davies (journalist of The Guardian) has reported about that. But
Facebook refused for any comments on that report. It was reported that the loss was cost for 50
millions of user but after that Facebook corrected this figure and says that the number was
around 87 million. After this Facebook admitted that all this happened due to their mistake and
lack of security (Martinez, 2018). The data was detailed enough for Cambridge Analytica to
make psychological report. Data also include the location of users which was well enough to
make profile which can suggest them what kind of advertisement can be most effective for a
particular person at particular location.
How it occurred- All this was done over an app “This is your Digital Life” which was
developed by a data scientist of Cambridge University, named 'Aleksandr Kogan'. This
application was provide to Cambridge Analytica. It starts a informed consent for fetching the
details of thousands of Facebook users all over the world. But the main focus of this was on the
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

users from USA only who agreed the permission to complete survey only for academic use.
However, Facebook not just only allow the app to collect personal information of those user who
have agreed for the survey, but also allows to excess the information of all of those who uses the
Facebook social network. This is how Cambridge Analytica able to fetch data of millions of
users over Facebook.
Why it occurred- This was occurred to make more attractive political promotional
activities according to an individual. This all was done to know the interest of an individual and
along with their locations. Cambridge Analytica was able to do that due to lack of security over
the excess granted for the applications and websites which come under the Facebook's program.
It reduces the security level for the user's data and make very easy for any outsider to break the
internal security of Facebook (Richterich, 2018).
Possible solutions to prevent this- To prevent the users from more loss of data,
Facebook owner Mark Zuckerberg started a feature in the application as well as in the website.
Under this, at the place of news feed a link was given, by clicking on which user will redirected
to a page. At that page user will get the list of permissions they have granted to the applications
and websites. As well also they will come to know about the websites and pages they have been
logged in using Facebook. Above that also the users which get affected by this receives a
notification that 'We have banned the website “This is your Digital Life”. It did this due to
misused of information on Facebook through sharing it with firm known as Cambridge
Analytica'.
To prevent this in future, Facebook have to take some measures like, they can make their
internal security stronger. They also can verifies the applications and websites which run under
them, and also which need log in via Facebook that they are secure or not in the prospectives of
user data (Sumpter, 2018).
2) Asynchronous I/O activity is problem with many memory protection schemes, consisting
base/bounds and paging
In computer science, asynchronous I/O Activity is a type of I/O processing that allow
other processing to proceed before transmission has ended. Input and output activities on system
can extremely moderate as compared to data processing. Protection of memory is the process to
affect memory access rights on system, and is component of most modern instruction set
architecture and operating systems. The main role of protecting memory is to save process from
3
However, Facebook not just only allow the app to collect personal information of those user who
have agreed for the survey, but also allows to excess the information of all of those who uses the
Facebook social network. This is how Cambridge Analytica able to fetch data of millions of
users over Facebook.
Why it occurred- This was occurred to make more attractive political promotional
activities according to an individual. This all was done to know the interest of an individual and
along with their locations. Cambridge Analytica was able to do that due to lack of security over
the excess granted for the applications and websites which come under the Facebook's program.
It reduces the security level for the user's data and make very easy for any outsider to break the
internal security of Facebook (Richterich, 2018).
Possible solutions to prevent this- To prevent the users from more loss of data,
Facebook owner Mark Zuckerberg started a feature in the application as well as in the website.
Under this, at the place of news feed a link was given, by clicking on which user will redirected
to a page. At that page user will get the list of permissions they have granted to the applications
and websites. As well also they will come to know about the websites and pages they have been
logged in using Facebook. Above that also the users which get affected by this receives a
notification that 'We have banned the website “This is your Digital Life”. It did this due to
misused of information on Facebook through sharing it with firm known as Cambridge
Analytica'.
To prevent this in future, Facebook have to take some measures like, they can make their
internal security stronger. They also can verifies the applications and websites which run under
them, and also which need log in via Facebook that they are secure or not in the prospectives of
user data (Sumpter, 2018).
2) Asynchronous I/O activity is problem with many memory protection schemes, consisting
base/bounds and paging
In computer science, asynchronous I/O Activity is a type of I/O processing that allow
other processing to proceed before transmission has ended. Input and output activities on system
can extremely moderate as compared to data processing. Protection of memory is the process to
affect memory access rights on system, and is component of most modern instruction set
architecture and operating systems. The main role of protecting memory is to save process from
3

accessing memory which has not been assigned to it. This prevent other processes and the
operating system from getting affected by running processes. Asynchronous I/O is a input/
output process that allow to the other processing to implement before the finished transmission.
It incorporate mechanical devices that move physically. Mainly it is a simple approach that
would be start the access and wait for complete. Operating system provides a key feature of
relocation, which is also important environment for multi-user (Bratterud and et. al., 2015).
Having two or more than two user, no one can determine in advance where the implementation
of a program will get loaded. To resolves the issue starting and base address are solution for
provided by the relocation registers. Base address is use to redeem all address inside programs.
Base register are known as variable fence register. Fence register do not provide an upper bound
but not lower one. To study how much spaces are allocated and to examine overflow into
forbidden section an upper bound can be very useful. To handle this problem another register is
generally attached. Bound register is second register, which is upper address limit. Every time
the base address is required to be under program address because the address is attached to the
content of base register (Dulloor and et. al., 2014). Using this technique saves a program address
to get changed through other user. When implementation alters from one user program to other,
the content of base and bound register get changed by the operating system to consider the
correct address place for that user. It is a part of extensive arrangement known as context switch.
A user can be protected without any external user's fault by using a pair of base/bound register.
Base/bound checking only verifies which each address is inside users address range, so the
program still can get influenced due to incorrect addresses inside a user's address range.
To solve this problem, other pairs of base/bound registers can be use. Out of which one
for instructions or code of program, and second for range of data. After which, executed fetched
code get checked as well as relocated with the first pair, and with second pair data accesses are
relocated and checked (Silberschatz, Gagne and Galvin, 2018). Using two pair of registers can
maximize the effect of data-operating commands to the data space but do not block all program
faults. Another important reward is offered by the pairs of registers: the skill to break a program
into two segments that can be relocated individually. Two or more pairs of registers can only get
utilized due to these two features: one for instructions, one for read-only data, and one for
alterable data values. Two pair of registers are limit for design of computer, otherwise this
concept can be expanded. For further registers pair, something in machine code must indicate
4
operating system from getting affected by running processes. Asynchronous I/O is a input/
output process that allow to the other processing to implement before the finished transmission.
It incorporate mechanical devices that move physically. Mainly it is a simple approach that
would be start the access and wait for complete. Operating system provides a key feature of
relocation, which is also important environment for multi-user (Bratterud and et. al., 2015).
Having two or more than two user, no one can determine in advance where the implementation
of a program will get loaded. To resolves the issue starting and base address are solution for
provided by the relocation registers. Base address is use to redeem all address inside programs.
Base register are known as variable fence register. Fence register do not provide an upper bound
but not lower one. To study how much spaces are allocated and to examine overflow into
forbidden section an upper bound can be very useful. To handle this problem another register is
generally attached. Bound register is second register, which is upper address limit. Every time
the base address is required to be under program address because the address is attached to the
content of base register (Dulloor and et. al., 2014). Using this technique saves a program address
to get changed through other user. When implementation alters from one user program to other,
the content of base and bound register get changed by the operating system to consider the
correct address place for that user. It is a part of extensive arrangement known as context switch.
A user can be protected without any external user's fault by using a pair of base/bound register.
Base/bound checking only verifies which each address is inside users address range, so the
program still can get influenced due to incorrect addresses inside a user's address range.
To solve this problem, other pairs of base/bound registers can be use. Out of which one
for instructions or code of program, and second for range of data. After which, executed fetched
code get checked as well as relocated with the first pair, and with second pair data accesses are
relocated and checked (Silberschatz, Gagne and Galvin, 2018). Using two pair of registers can
maximize the effect of data-operating commands to the data space but do not block all program
faults. Another important reward is offered by the pairs of registers: the skill to break a program
into two segments that can be relocated individually. Two or more pairs of registers can only get
utilized due to these two features: one for instructions, one for read-only data, and one for
alterable data values. Two pair of registers are limit for design of computer, otherwise this
concept can be expanded. For further registers pair, something in machine code must indicate
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

relocation set is to be used to address the instructions operands. Two or more data spaces can be
defined by each instruction while having more than two pairs. But with only two pairs, decision
can be automated : code with one pair, data range with the other.
PART B
1) 2011 Sony PlayStation Network outage case
Sony is Japanese multinational conglomerate organisation. It diversified its business that
consists of professional and consumer electronics, entertainment, financial services and gaming.
It owns largest entertainment, biggest video game console business in all over the world. This
company provide its services in whole world. It is parent firm of Sony Group and also
Electronics business unit (Alomari and et. al., 2012). It is engaged in the business by various
components like for an instance electronics, financial services, motion pictures, and music. In
addition to this, there is a case happened related to Sony PlayStation Network outage in year
2011.
What was the problem?
2011 Sony PlayStation Network outage case was result of “external intrusion” on
PlayStation Network of Sony, under which personal details of more than 77 million accounts
were to be compromised. Online service of Sony for PSP game machines and PlayStation 3 as
well as PC online games. Under this, Sony company has been targeted through Anonymous
group hackers. Anonymous is decentralised international group of hacktivist which are known
for different DDoS cyber attacks against many of the government agencies. Anonymous has
been critical of Japan based entertainment and PS3's closed operating system unlocked through
American hacker (Ko, Kirchberg and Lee, 2011). Sony discovered that among 17 and 19 April,
“unauthorized and illegal person”, got access to names, email address, usernames, address,
passwords, security related questions, logins and many other personal details of people. For
download software, online games, music and films, there was need to PlayStation members to
submit their personal and credit card details. The data was hacked more than 77m of users.
About hacking of personal details, organisation is starting to emailing those people which might
affected. On the other hand, an intrusion is one of biggest ever in credit card store. PlayStation
Network of Sony is one of biggest credit card hotels as comparison to Apple iTunes, Amazon,
PayPal etc. Under this, after 7 days of the speculation- ridden downtime, finally Sony company
5
defined by each instruction while having more than two pairs. But with only two pairs, decision
can be automated : code with one pair, data range with the other.
PART B
1) 2011 Sony PlayStation Network outage case
Sony is Japanese multinational conglomerate organisation. It diversified its business that
consists of professional and consumer electronics, entertainment, financial services and gaming.
It owns largest entertainment, biggest video game console business in all over the world. This
company provide its services in whole world. It is parent firm of Sony Group and also
Electronics business unit (Alomari and et. al., 2012). It is engaged in the business by various
components like for an instance electronics, financial services, motion pictures, and music. In
addition to this, there is a case happened related to Sony PlayStation Network outage in year
2011.
What was the problem?
2011 Sony PlayStation Network outage case was result of “external intrusion” on
PlayStation Network of Sony, under which personal details of more than 77 million accounts
were to be compromised. Online service of Sony for PSP game machines and PlayStation 3 as
well as PC online games. Under this, Sony company has been targeted through Anonymous
group hackers. Anonymous is decentralised international group of hacktivist which are known
for different DDoS cyber attacks against many of the government agencies. Anonymous has
been critical of Japan based entertainment and PS3's closed operating system unlocked through
American hacker (Ko, Kirchberg and Lee, 2011). Sony discovered that among 17 and 19 April,
“unauthorized and illegal person”, got access to names, email address, usernames, address,
passwords, security related questions, logins and many other personal details of people. For
download software, online games, music and films, there was need to PlayStation members to
submit their personal and credit card details. The data was hacked more than 77m of users.
About hacking of personal details, organisation is starting to emailing those people which might
affected. On the other hand, an intrusion is one of biggest ever in credit card store. PlayStation
Network of Sony is one of biggest credit card hotels as comparison to Apple iTunes, Amazon,
PayPal etc. Under this, after 7 days of the speculation- ridden downtime, finally Sony company
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

announced that PlayStation Network outage because of massive hack that exposed names, email,
birthdays, security questions, credit card details of all users which use PlayStation network.
Who were affected and how?
From this incident, people who used the PlayStation Network were more affected
because their personal as well as financial details all were hacked. Sony warned its all users to
look for telephone scams or mail to lodge “fraud alert” with the credit bureaus such as Equifax
and Ezperian. The credit card details get leaked after this scandal. Sony also faced questions
regarding to their clear image of having tight securities. The believe of gamers over Sony was
reducing day by day in the prospectives of their personal detail. This time was the golden period
for many companies to release their online games in the market and attract the distributed gamers
from all over the world. “Portal2” was really the key game released at that time. This all was the
big problem for Sony.
How was the attack carried out?
In history of Sony, it has strong security related to protect data and information of
customers. But for this outage, no appropriate reason has not been find out. According to some
researches data breaches is the reason for this outage. It was assumed that Anonymous came to
know about some weakness of Play Station Network (Rodgers, 2011). After which it was very
easy for the hackers to enter into the hole of SQL by the injection attack. The another reason
which can be a cause of that outage could be the recent release of custom PlayStation3 firmware
build called Rebug. Due to which PS3 turns into a developer unit and activates a slew of features
which cannot be access normally by a customer. Rebug firmware provides the console a trusted
access to Sony's internal developer network. According to the report once the gamer is on the
internal, trusted network, a range of new hackers are available, along with the fake credit details
on Play Station Network. By installing the custom Firmware, it is easy to access the breached
data base having customer details. It is possible that Sony's security mechanisms simply did not
account for an internal attack from a trusted network and without some trusted agents functional
network cannot be created.
What could have been done to prevent the attack?
To prevent the system from these types of intrusions, some steps can be taken are-
1. Temporarily turn off the Play Station Network and Qriocity services.
2. Hire an external and recognised firm for the full investigation into what happened
6
birthdays, security questions, credit card details of all users which use PlayStation network.
Who were affected and how?
From this incident, people who used the PlayStation Network were more affected
because their personal as well as financial details all were hacked. Sony warned its all users to
look for telephone scams or mail to lodge “fraud alert” with the credit bureaus such as Equifax
and Ezperian. The credit card details get leaked after this scandal. Sony also faced questions
regarding to their clear image of having tight securities. The believe of gamers over Sony was
reducing day by day in the prospectives of their personal detail. This time was the golden period
for many companies to release their online games in the market and attract the distributed gamers
from all over the world. “Portal2” was really the key game released at that time. This all was the
big problem for Sony.
How was the attack carried out?
In history of Sony, it has strong security related to protect data and information of
customers. But for this outage, no appropriate reason has not been find out. According to some
researches data breaches is the reason for this outage. It was assumed that Anonymous came to
know about some weakness of Play Station Network (Rodgers, 2011). After which it was very
easy for the hackers to enter into the hole of SQL by the injection attack. The another reason
which can be a cause of that outage could be the recent release of custom PlayStation3 firmware
build called Rebug. Due to which PS3 turns into a developer unit and activates a slew of features
which cannot be access normally by a customer. Rebug firmware provides the console a trusted
access to Sony's internal developer network. According to the report once the gamer is on the
internal, trusted network, a range of new hackers are available, along with the fake credit details
on Play Station Network. By installing the custom Firmware, it is easy to access the breached
data base having customer details. It is possible that Sony's security mechanisms simply did not
account for an internal attack from a trusted network and without some trusted agents functional
network cannot be created.
What could have been done to prevent the attack?
To prevent the system from these types of intrusions, some steps can be taken are-
1. Temporarily turn off the Play Station Network and Qriocity services.
2. Hire an external and recognised firm for the full investigation into what happened
6

3. Take quick steps for security enhancement and increase the strength of infrastructure of
network through re-building system to give stronger protection to the data base and
personal information.
Some steps Sony is taking to prevent outage conditions in future-
Sony is hiring a Chief Information Security Officer.
It will help Sony to insert new efforts in the security including addition of software
monitoring and defend attacks (Sangani, 2011).
CONCLUSION
It has been concluded from above mention report that Information security is helpful in
prevent the information as well as data of customers from any kind of unauthorized activities. In
this mention report studied about the Facebook-Cambridge Analytica data scandal. There has
been discussion about the arisen of issue and solution to prevent from problems. Asynchronous
I/O activity is problem with many memory protection schemes has been discussed here. In this
given report also studied regarding the 2011 Sony PlayStation Network outage case in which all
personal and credit card details data of PlayStation Network has been hacked.
7
network through re-building system to give stronger protection to the data base and
personal information.
Some steps Sony is taking to prevent outage conditions in future-
Sony is hiring a Chief Information Security Officer.
It will help Sony to insert new efforts in the security including addition of software
monitoring and defend attacks (Sangani, 2011).
CONCLUSION
It has been concluded from above mention report that Information security is helpful in
prevent the information as well as data of customers from any kind of unauthorized activities. In
this mention report studied about the Facebook-Cambridge Analytica data scandal. There has
been discussion about the arisen of issue and solution to prevent from problems. Asynchronous
I/O activity is problem with many memory protection schemes has been discussed here. In this
given report also studied regarding the 2011 Sony PlayStation Network outage case in which all
personal and credit card details data of PlayStation Network has been hacked.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books & Journals
Alomari, E. and et. al., 2012. Botnet-based distributed denial of service (DDoS) attacks on web
servers: classification and art. arXiv preprint arXiv:1208.0403.
Bratterud, A. and et. al., 2015, November. IncludeOS: A minimal, resource efficient unikernel
for cloud services. In Cloud Computing Technology and Science (CloudCom), 2015
IEEE 7th International Conference on (pp. 250-257). IEEE.
Datoo, A., 2018. Data in the post-GDPR world. Computer Fraud & Security. 2018(9). pp.17-18.
Dulloor, S. R., and et. al., 2014, April. System software for persistent memory. In Proceedings
of the Ninth European Conference on Computer Systems (p. 15). ACM.
Ko, R. K., Kirchberg, M. and Lee, B. S., 2011, August. From system-centric to data-centric
logging-accountability, trust & security in cloud computing. In Defense Science
Research Conference and Expo (DSR). 2011 (pp. 1-4). IEEE.
Martinez, A. G., 2018. Chaos monkeys: Obscene fortune and random failure in Silicon Valley.
HarperCollins Publishers.
Richterich, A., 2018. How Data-Driven Research Fuelled the Cambridge Analytica Controversy.
Partecipazione e conflitto. 11(2). pp.528-543.
Rodgers, M., 2011. Once more,'undo'the breach. CIO, (Jul/Aug 2011), p.66.
Sangani, K., 2011. Sony security laid bare. Engineering & Technology. 6(8). pp.74-77.
Silberschatz, A., Gagne, G. and Galvin, P.B., 2018. Operating system concepts. Wiley.
Sumpter, D., 2018. Outnumbered: From Facebook and Google to Fake News and Filter-bubbles
The Algorithms That Control Our Lives (featuring Cambridge Analytica).
Online
PlayStation Network hackers access data of 77 million users. 2018. [Online]. Available through:
<https://www.theguardian.com/technology/2011/apr/26/playstation-network-hackers-
data>.
8
Books & Journals
Alomari, E. and et. al., 2012. Botnet-based distributed denial of service (DDoS) attacks on web
servers: classification and art. arXiv preprint arXiv:1208.0403.
Bratterud, A. and et. al., 2015, November. IncludeOS: A minimal, resource efficient unikernel
for cloud services. In Cloud Computing Technology and Science (CloudCom), 2015
IEEE 7th International Conference on (pp. 250-257). IEEE.
Datoo, A., 2018. Data in the post-GDPR world. Computer Fraud & Security. 2018(9). pp.17-18.
Dulloor, S. R., and et. al., 2014, April. System software for persistent memory. In Proceedings
of the Ninth European Conference on Computer Systems (p. 15). ACM.
Ko, R. K., Kirchberg, M. and Lee, B. S., 2011, August. From system-centric to data-centric
logging-accountability, trust & security in cloud computing. In Defense Science
Research Conference and Expo (DSR). 2011 (pp. 1-4). IEEE.
Martinez, A. G., 2018. Chaos monkeys: Obscene fortune and random failure in Silicon Valley.
HarperCollins Publishers.
Richterich, A., 2018. How Data-Driven Research Fuelled the Cambridge Analytica Controversy.
Partecipazione e conflitto. 11(2). pp.528-543.
Rodgers, M., 2011. Once more,'undo'the breach. CIO, (Jul/Aug 2011), p.66.
Sangani, K., 2011. Sony security laid bare. Engineering & Technology. 6(8). pp.74-77.
Silberschatz, A., Gagne, G. and Galvin, P.B., 2018. Operating system concepts. Wiley.
Sumpter, D., 2018. Outnumbered: From Facebook and Google to Fake News and Filter-bubbles
The Algorithms That Control Our Lives (featuring Cambridge Analytica).
Online
PlayStation Network hackers access data of 77 million users. 2018. [Online]. Available through:
<https://www.theguardian.com/technology/2011/apr/26/playstation-network-hackers-
data>.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



