ITC 571 Final Report: Security Issues in Content Delivery Networks
VerifiedAdded on 2020/03/16
|27
|6989
|70
Report
AI Summary
This report, prepared for ITC 571, focuses on the critical challenges of Content Delivery Network (CDN) security within the context of small business organizations. The study begins by identifying the primary threats and risks associated with data and information security in CDNs, emphasizing the limitations of existing models. It reviews the background and significance of the project, highlighting the security protocols and services. A comprehensive literature review explores the concepts, scalability, security, reliability, responsiveness, and performance aspects of CDNs. The methodology section details the descriptive research design, data collection methods (questionnaires, interviews, and observations), and the sample population. The core of the report proposes a new mathematical model designed to mitigate identified vulnerabilities. The model aims to enhance security standards, improve server speeds, and minimize threats. The report details the model's justifications, improvements over previous models, and practical applications, including considerations for CDN engineers and clients. The findings of the report provide recommendations for resolving issues and improving CDN security.

Guidelines for the final report of ITC 571
Title Security in Contents Distribution Networks, CDN .
Table of Contents
(on a separate
page)
Abstract
(200~250 maxium)
(on a separate
page)
This study aims to identify the challenges faced by the CDN in the
organisation and proposing a mode to mitigate these challenges in
the business organisation. The risks and threats related to data and
information in the system has been a key challenge to organisation.
The methods used in the study are cost-effective. The data has been
collected form online books and journals with proper security. There
has been four components on the data security including the users,
the publishers, the third party and distributor.
This study focuses on the threats and risks involved in the CDN
security mode; The previous model has been modified with new
proposed model that have mitigate the issues and limitations involved
in previous model. The use of new theories have helped in
understanding basic vulnerabilities of previous model. This study
describes about the end-to-end user connection involved in security
measures provided by the CDN in small business organisation. The
data collection method have helped in collecting data related to the
topic from questionnaires and interviews. The analysis of data have
helped in obtaining the findings from the study of the topic.
Many drawbacks are found in the current model of CDN. The study
1
Title Security in Contents Distribution Networks, CDN .
Table of Contents
(on a separate
page)
Abstract
(200~250 maxium)
(on a separate
page)
This study aims to identify the challenges faced by the CDN in the
organisation and proposing a mode to mitigate these challenges in
the business organisation. The risks and threats related to data and
information in the system has been a key challenge to organisation.
The methods used in the study are cost-effective. The data has been
collected form online books and journals with proper security. There
has been four components on the data security including the users,
the publishers, the third party and distributor.
This study focuses on the threats and risks involved in the CDN
security mode; The previous model has been modified with new
proposed model that have mitigate the issues and limitations involved
in previous model. The use of new theories have helped in
understanding basic vulnerabilities of previous model. This study
describes about the end-to-end user connection involved in security
measures provided by the CDN in small business organisation. The
data collection method have helped in collecting data related to the
topic from questionnaires and interviews. The analysis of data have
helped in obtaining the findings from the study of the topic.
Many drawbacks are found in the current model of CDN. The study
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

has able to identify the issues and propose a new model for
mitigating those drawbacks. Some recommendations are provided in
the study that might help in resolving the issues in the CDN.
1. Introduction
(500-600 maximum)
1.1. Background to the report
The security of data and information in the CDN have been an
alarming issue discussed in the study. The security of the data in
business organisation is an important aspect. The security protocols
and services provided by CDN has been focused in the study.
1.2. Issues and previous solutions
The issues and challenges in providing security by CDN ti business
organisation has been identified in the research. The cyber-attacks
has been a common reason in data loss for the company in the
market. The security of data and information in the CDN of Akamai
Company has been key issue in the market [1]. This study focuses on
the limitations of the CDN to secure data and information in company.
The technology used in the CDN has been properly discussed in the
study. The security breach in the CDN has been a major issue
focused in the study. This study expands knowledge related to the
security schemes used in CDN.
1.3. Significance of the project
This study highlights the gaps identified from the previous literature
review. Different gaps and limitations has been identified from the
current model of CDN. This study has helped in proposing new model
2
mitigating those drawbacks. Some recommendations are provided in
the study that might help in resolving the issues in the CDN.
1. Introduction
(500-600 maximum)
1.1. Background to the report
The security of data and information in the CDN have been an
alarming issue discussed in the study. The security of the data in
business organisation is an important aspect. The security protocols
and services provided by CDN has been focused in the study.
1.2. Issues and previous solutions
The issues and challenges in providing security by CDN ti business
organisation has been identified in the research. The cyber-attacks
has been a common reason in data loss for the company in the
market. The security of data and information in the CDN of Akamai
Company has been key issue in the market [1]. This study focuses on
the limitations of the CDN to secure data and information in company.
The technology used in the CDN has been properly discussed in the
study. The security breach in the CDN has been a major issue
focused in the study. This study expands knowledge related to the
security schemes used in CDN.
1.3. Significance of the project
This study highlights the gaps identified from the previous literature
review. Different gaps and limitations has been identified from the
current model of CDN. This study has helped in proposing new model
2

with resolved solutions for the limitations. The evaluation focused on
data from the origin and through the channels that it reaches the end
user being secure and safe. The model limits human management
and increased performance, scalability and reliability. The model
focused also on the key actors, the original data publishers, the
customer, and the systems role in the flow and distribution of
information via the internet.
1.4. Aims
The aim of the study is to assess potential network security threats
for CDN users and to assess the effectiveness of the policy issues in
safeguarding the web users. The purpose of the research is:
o To identify the threats included in use of CDN in small
businesses.
o To analyze the role of government and web users to
promote security in CDN
o To propose strategies for improving security in CDN.
2.Literature Review
(LR)
2.1 Concept
The use of various models in providing the security to data and
information in the business organisation [2]. The CDN have been
used to overcome different inherent challenges of Internet perceived
over the Quality of Service in the business organisation. A CDN
helped in replicating the content of the origin of cache servers in the
market. The business organisation in the market have to be alert
3
data from the origin and through the channels that it reaches the end
user being secure and safe. The model limits human management
and increased performance, scalability and reliability. The model
focused also on the key actors, the original data publishers, the
customer, and the systems role in the flow and distribution of
information via the internet.
1.4. Aims
The aim of the study is to assess potential network security threats
for CDN users and to assess the effectiveness of the policy issues in
safeguarding the web users. The purpose of the research is:
o To identify the threats included in use of CDN in small
businesses.
o To analyze the role of government and web users to
promote security in CDN
o To propose strategies for improving security in CDN.
2.Literature Review
(LR)
2.1 Concept
The use of various models in providing the security to data and
information in the business organisation [2]. The CDN have been
used to overcome different inherent challenges of Internet perceived
over the Quality of Service in the business organisation. A CDN
helped in replicating the content of the origin of cache servers in the
market. The business organisation in the market have to be alert
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

about the security of the data and information of company [3]. The
CDN combines both low and high level computing technologies in the
business organisation. The Content Delivery Networks helps in
improving the performance of network by maximizing the bandwidth
and shortening the latency. The CDN has a combination of content-
delivery, distribution, request-routing and accounting infrastructure
[4]. The accounting infrastructure helps in maintaining the logs of
clients and access them for mitigating issues in their network. This
help in enabling the data centres and Internet Service providers. A
CDN is a collection of network elements that helps in maintaining the
security of the data and information in the business organisation. The
data and information are centralized that helps in managing data in a
proper manner [5]. A CDN helps in providing an enhanced
performance by caching the content over the internet and storing over
the servers in database. This helps in maintaining a huge storage
capacity of data and information. On the other hand, there is a huge
risk of data breach over the internet due ti the Cyber-attacks. The
cyber-attacks has been prominent over the internet that causes data
loss in the business organisation [6].
Over the last decades, there has been a huge change in the concept
and application of the CDN in the business organisation. The growth
if the Internet technology has helped in enhancing the network traffic
over the internet [7]. The increase in the traffic of the internet has
caused many malicious activities over the internet.
2.2 Factors affecting business goals
Scalability
4
CDN combines both low and high level computing technologies in the
business organisation. The Content Delivery Networks helps in
improving the performance of network by maximizing the bandwidth
and shortening the latency. The CDN has a combination of content-
delivery, distribution, request-routing and accounting infrastructure
[4]. The accounting infrastructure helps in maintaining the logs of
clients and access them for mitigating issues in their network. This
help in enabling the data centres and Internet Service providers. A
CDN is a collection of network elements that helps in maintaining the
security of the data and information in the business organisation. The
data and information are centralized that helps in managing data in a
proper manner [5]. A CDN helps in providing an enhanced
performance by caching the content over the internet and storing over
the servers in database. This helps in maintaining a huge storage
capacity of data and information. On the other hand, there is a huge
risk of data breach over the internet due ti the Cyber-attacks. The
cyber-attacks has been prominent over the internet that causes data
loss in the business organisation [6].
Over the last decades, there has been a huge change in the concept
and application of the CDN in the business organisation. The growth
if the Internet technology has helped in enhancing the network traffic
over the internet [7]. The increase in the traffic of the internet has
caused many malicious activities over the internet.
2.2 Factors affecting business goals
Scalability
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The principle business objective of a CDN is to accomplish
adaptability. Scalability depicts to the capacity of the framework to
extend to deal with new and a lot of information, clients and
exchanges with no huge decrease in execution. To extend in a
worldwide scale, CDNs need to put time and expenses in
provisioning extra system associations and frameworks [8]. It
incorporates provisioning assets powerfully to address streak swarms
and shifting activity. A CDN should go about as a safeguard for
activity by consequently giving limit on-request to meet the
necessities of crowds. This capacity permits a
CDN to maintain a strategic distance from expensive over-
provisioning of assets and to give elite to each client.
Security
One of the significant worries of a CDN is to give potential security
solutions for confidential, high-esteem content [9]. Security is the
assurance of substance against unapproved access and change.
Without appropriate security control, a CDN stage is liable to digital
misrepresentation, distributed denial of service (DDoS) attacks,
viruses, and other undesirable interruptions that can degrade
business [10]. A CDN goes for meeting the stringent prerequisites of
physical, arrange, programming, information and procedural security.
Once the security prerequisites are addressed, a CDN can wipe out
the requirement for exorbitant equipment and committed part to
secure substance and exchanges [11]. In understanding to the
5
adaptability. Scalability depicts to the capacity of the framework to
extend to deal with new and a lot of information, clients and
exchanges with no huge decrease in execution. To extend in a
worldwide scale, CDNs need to put time and expenses in
provisioning extra system associations and frameworks [8]. It
incorporates provisioning assets powerfully to address streak swarms
and shifting activity. A CDN should go about as a safeguard for
activity by consequently giving limit on-request to meet the
necessities of crowds. This capacity permits a
CDN to maintain a strategic distance from expensive over-
provisioning of assets and to give elite to each client.
Security
One of the significant worries of a CDN is to give potential security
solutions for confidential, high-esteem content [9]. Security is the
assurance of substance against unapproved access and change.
Without appropriate security control, a CDN stage is liable to digital
misrepresentation, distributed denial of service (DDoS) attacks,
viruses, and other undesirable interruptions that can degrade
business [10]. A CDN goes for meeting the stringent prerequisites of
physical, arrange, programming, information and procedural security.
Once the security prerequisites are addressed, a CDN can wipe out
the requirement for exorbitant equipment and committed part to
secure substance and exchanges [11]. In understanding to the
5

security issues, a CDN battle against some other potential hazard
concerns including disavowal of-benefit assaults or different noxious
movement that may intrude on business.
Reliability, Responsiveness and Performance
Reliability refers to when an administration is accessible and what
are the limits on benefit blackouts that might be normal. A CDN
supplier can enhance customer access to particular substance
through conveying it from numerous areas [12]. For this, a fault
tolerant system with fitting burden-adjusting instrument is to be
executed. Responsiveness infers, while notwithstanding conceivable
blackouts, how soon an administration would begin playing out the
ordinary course of operation. The reaction time saw ordinarily
describes execution of a CDN by the end-clients [13]. Moderate
reaction time is the single most noteworthy supporter of clients'
surrendering Web locales and procedures. The unwavering quality
furthermore, execution of a CDN is influenced by the dispersed
substance area and directing component, and additionally by
information replication and storing systems. Consequently, a CDN
utilizes reserving and gushing to upgrade execution particularly for
conveyance of media content [14]. A CDN facilitating a Web website
likewise concentrates on giving quick and solid administration since it
fortifies the message that the organization is dependable and client
centred.
3. Methodology
(Depending on the
3.1. Design
The study has focused on clear objective and methodology. The research has used
6
concerns including disavowal of-benefit assaults or different noxious
movement that may intrude on business.
Reliability, Responsiveness and Performance
Reliability refers to when an administration is accessible and what
are the limits on benefit blackouts that might be normal. A CDN
supplier can enhance customer access to particular substance
through conveying it from numerous areas [12]. For this, a fault
tolerant system with fitting burden-adjusting instrument is to be
executed. Responsiveness infers, while notwithstanding conceivable
blackouts, how soon an administration would begin playing out the
ordinary course of operation. The reaction time saw ordinarily
describes execution of a CDN by the end-clients [13]. Moderate
reaction time is the single most noteworthy supporter of clients'
surrendering Web locales and procedures. The unwavering quality
furthermore, execution of a CDN is influenced by the dispersed
substance area and directing component, and additionally by
information replication and storing systems. Consequently, a CDN
utilizes reserving and gushing to upgrade execution particularly for
conveyance of media content [14]. A CDN facilitating a Web website
likewise concentrates on giving quick and solid administration since it
fortifies the message that the organization is dependable and client
centred.
3. Methodology
(Depending on the
3.1. Design
The study has focused on clear objective and methodology. The research has used
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

nature of the report)
(~500)
descriptive deign for having a clear perspective of the topic. The data has been
collected using interviews, questionnaires and observations. The questionnaires
are both open ended and close ended for various small businesses.
3.2. Method
The tools that are used in the collection of data and information have
ensured relevant to the research topic. The questionnaires were sent
through email to various small companies and follow up was
conducted [15]. The sample population was a simple random
sampling. The companies chosen for the study intends to be a small
or medium level having minimum cost for using CDN security
network. Interviews are conducted within the IT field. The interviews
are conducted with one-to-one platforms physically and online video
conferencing Telephone calls are also used with video calls that
helps in increasing the range of data collection. Observations are
done on company visit, website analysis and system review [16]. This
have helped in gathering relevant data and information related to the
topic of the study.
3/4. A proposed/ an
enhanced/
improved model
4.1 Justifications for the new model
The new model has derived from the limitation of the previous model.
The limitations are removed in the new model that helps in providing
enhanced security to data and information of business organisation
[17]. The model permits the CDN engineers and clients decide the
frameworks that works adequately as far as security and expenses.
The procedure uncovered for high security in a CDN framework does
7
(~500)
descriptive deign for having a clear perspective of the topic. The data has been
collected using interviews, questionnaires and observations. The questionnaires
are both open ended and close ended for various small businesses.
3.2. Method
The tools that are used in the collection of data and information have
ensured relevant to the research topic. The questionnaires were sent
through email to various small companies and follow up was
conducted [15]. The sample population was a simple random
sampling. The companies chosen for the study intends to be a small
or medium level having minimum cost for using CDN security
network. Interviews are conducted within the IT field. The interviews
are conducted with one-to-one platforms physically and online video
conferencing Telephone calls are also used with video calls that
helps in increasing the range of data collection. Observations are
done on company visit, website analysis and system review [16]. This
have helped in gathering relevant data and information related to the
topic of the study.
3/4. A proposed/ an
enhanced/
improved model
4.1 Justifications for the new model
The new model has derived from the limitation of the previous model.
The limitations are removed in the new model that helps in providing
enhanced security to data and information of business organisation
[17]. The model permits the CDN engineers and clients decide the
frameworks that works adequately as far as security and expenses.
The procedure uncovered for high security in a CDN framework does
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

not really mean high expenses [18]. Different factors, for example,
speed and time impact costs. The model can be utilized by
organizations in deciding the CDN design to apply in light of the
results wants and the level of security required [19]. In a CDN
situation, fundamental relationship for content conveyance is among
customer, surrogates and starting point servers [20]. A customer may
speak with surrogate server for demands expected for at least one-
inception servers. Where a surrogate is not utilized, the customer
discusses specifically with source server. The correspondence
between a client and surrogate happens in a straightforward way, as
though the correspondence is with planned root server [21].
Surrogate serves customer demands from its nearby reserve or goes
about as a portal to beginning server. The relationship among
customer, surrogates and the birthplace server [22]. CDNs can be
framed utilizing a system approach, where rationale is conveyed in
the organize components to forward movement to servers that are fit
for serving customer demands [23]. Other than these connections,
storing proxy inside a CDN may speak with each other. An
intermediary store is an application-layer arrange benefit for reserving
Web objects.
Intermediary stores can be at the same time gotten to and shared by
numerous clients. A key refinement between the CDN intermediary
stores and ISP-worked reserves is that the previous serve content
just for certain substance supplier, to be specific CDN clients, while
the last store content from all Web destinations.
8
speed and time impact costs. The model can be utilized by
organizations in deciding the CDN design to apply in light of the
results wants and the level of security required [19]. In a CDN
situation, fundamental relationship for content conveyance is among
customer, surrogates and starting point servers [20]. A customer may
speak with surrogate server for demands expected for at least one-
inception servers. Where a surrogate is not utilized, the customer
discusses specifically with source server. The correspondence
between a client and surrogate happens in a straightforward way, as
though the correspondence is with planned root server [21].
Surrogate serves customer demands from its nearby reserve or goes
about as a portal to beginning server. The relationship among
customer, surrogates and the birthplace server [22]. CDNs can be
framed utilizing a system approach, where rationale is conveyed in
the organize components to forward movement to servers that are fit
for serving customer demands [23]. Other than these connections,
storing proxy inside a CDN may speak with each other. An
intermediary store is an application-layer arrange benefit for reserving
Web objects.
Intermediary stores can be at the same time gotten to and shared by
numerous clients. A key refinement between the CDN intermediary
stores and ISP-worked reserves is that the previous serve content
just for certain substance supplier, to be specific CDN clients, while
the last store content from all Web destinations.
8

4.2 Introduce and explain the model, clearly indicating which
areas or aspects have been improved or added.
The model created is mathematical and it mirrors the real working of
the servers in this manner it is anything but difficult to test it [24]. The
model however is restricted to innovative innovation use, as the
frameworks should be enhanced to accomplish the superior rate. The
model in this manner should be imitated to a genuine server to set up
the legitimacy of the model practically speaking [25]. It has able to
improve the development of security standards for businesses and
enhanced speeds in the servers functioning. The model have helped
in minimizing the threats and security of data and information in
business organisation. The new model have able to transform the
working criteria of previous model in the business organisation. The
model permits the CDN system to distinguish false clicks revealed by
merchants unless the customer and the intermediary conspire [26].
The complex appropriated design of a CDN models distinctive
connections between its constituent segments. In this area, to
recognize the connections that exist in the replication and reserving
condition of a CDN [27]. These connections include parts, for
example, customers, surrogates, starting point server, intermediary
stores and other organize components. These parts convey to repeat
and store content inside a CDN. Replication includes making and
keeping up copy duplicate of some substance on various PC
framework. It normally includes driving substance from the starting
point server to the imitation servers. Then again, storing includes
9
areas or aspects have been improved or added.
The model created is mathematical and it mirrors the real working of
the servers in this manner it is anything but difficult to test it [24]. The
model however is restricted to innovative innovation use, as the
frameworks should be enhanced to accomplish the superior rate. The
model in this manner should be imitated to a genuine server to set up
the legitimacy of the model practically speaking [25]. It has able to
improve the development of security standards for businesses and
enhanced speeds in the servers functioning. The model have helped
in minimizing the threats and security of data and information in
business organisation. The new model have able to transform the
working criteria of previous model in the business organisation. The
model permits the CDN system to distinguish false clicks revealed by
merchants unless the customer and the intermediary conspire [26].
The complex appropriated design of a CDN models distinctive
connections between its constituent segments. In this area, to
recognize the connections that exist in the replication and reserving
condition of a CDN [27]. These connections include parts, for
example, customers, surrogates, starting point server, intermediary
stores and other organize components. These parts convey to repeat
and store content inside a CDN. Replication includes making and
keeping up copy duplicate of some substance on various PC
framework. It normally includes driving substance from the starting
point server to the imitation servers. Then again, storing includes
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

putting away cacheable reactions keeping in mind the end goal to
lessen the reaction time and system data transmission utilization on
future, proportionate solicitations [28]. Similarly, the convention tried
can be utilized to examine security dangers and give an approach to
address CDN security issues. Such a calculation would enhance
information security and data wellbeing.
4.3 Highlight some strengths of the model compared to previous
models.
There are various backgrounds on which the new model is beneficial
than the previous model [29]. The bandwidth if the new model has
been increased than the previous model that helps in capturing a
wider range of data packets over the internet. The delivery network of
the computing system has been enhanced in the model [30]. The use
of the updated security protocols have helped in maintaining security
of data and information of business organisation. The static contents
of geographically servers have helped in maintaining the location of
the servers properly. This helped in securing the data and information
of business organisation at a particular place. The model have
helped in minimizing the threats and security of data and information
in business organisation. The new model have able to improve the
SEO strategies of the business organisation. The slow loading of the
websites has been removed by enhancing the efficiency of transfer
rate of data packets [31]. It has able to improve the development of
security standards for businesses and enhanced speeds in the
servers functioning.
10
lessen the reaction time and system data transmission utilization on
future, proportionate solicitations [28]. Similarly, the convention tried
can be utilized to examine security dangers and give an approach to
address CDN security issues. Such a calculation would enhance
information security and data wellbeing.
4.3 Highlight some strengths of the model compared to previous
models.
There are various backgrounds on which the new model is beneficial
than the previous model [29]. The bandwidth if the new model has
been increased than the previous model that helps in capturing a
wider range of data packets over the internet. The delivery network of
the computing system has been enhanced in the model [30]. The use
of the updated security protocols have helped in maintaining security
of data and information of business organisation. The static contents
of geographically servers have helped in maintaining the location of
the servers properly. This helped in securing the data and information
of business organisation at a particular place. The model have
helped in minimizing the threats and security of data and information
in business organisation. The new model have able to improve the
SEO strategies of the business organisation. The slow loading of the
websites has been removed by enhancing the efficiency of transfer
rate of data packets [31]. It has able to improve the development of
security standards for businesses and enhanced speeds in the
servers functioning.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4/5.
Implementation of
the model
The new model has been implemented in various business
organisation in the market. This new model have helped in
enhancing the security of the data and information in the business
organisation.
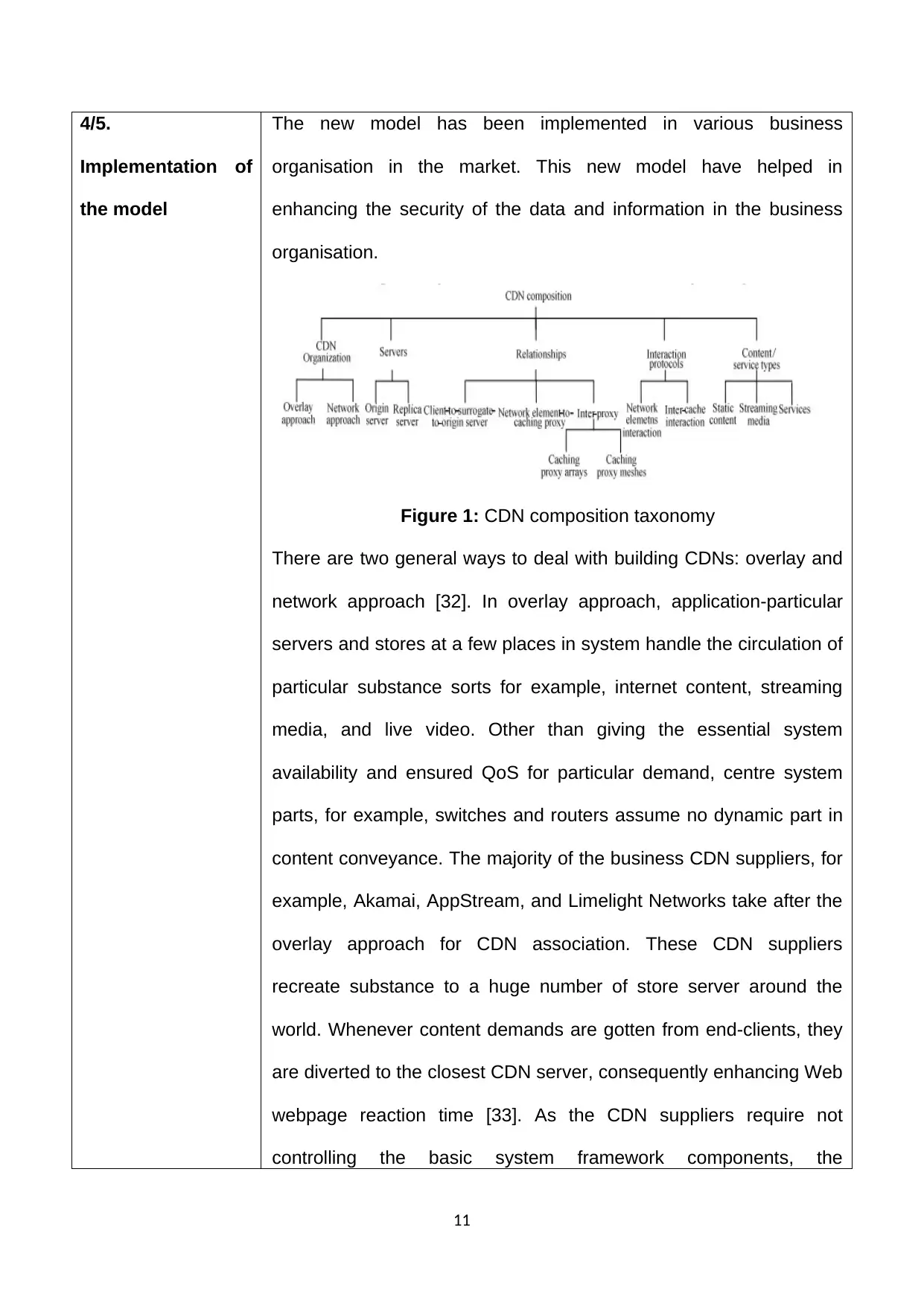
Figure 1: CDN composition taxonomy
There are two general ways to deal with building CDNs: overlay and
network approach [32]. In overlay approach, application-particular
servers and stores at a few places in system handle the circulation of
particular substance sorts for example, internet content, streaming
media, and live video. Other than giving the essential system
availability and ensured QoS for particular demand, centre system
parts, for example, switches and routers assume no dynamic part in
content conveyance. The majority of the business CDN suppliers, for
example, Akamai, AppStream, and Limelight Networks take after the
overlay approach for CDN association. These CDN suppliers
recreate substance to a huge number of store server around the
world. Whenever content demands are gotten from end-clients, they
are diverted to the closest CDN server, consequently enhancing Web
webpage reaction time [33]. As the CDN suppliers require not
controlling the basic system framework components, the
11
Implementation of
the model
The new model has been implemented in various business
organisation in the market. This new model have helped in
enhancing the security of the data and information in the business
organisation.
Figure 1: CDN composition taxonomy
There are two general ways to deal with building CDNs: overlay and
network approach [32]. In overlay approach, application-particular
servers and stores at a few places in system handle the circulation of
particular substance sorts for example, internet content, streaming
media, and live video. Other than giving the essential system
availability and ensured QoS for particular demand, centre system
parts, for example, switches and routers assume no dynamic part in
content conveyance. The majority of the business CDN suppliers, for
example, Akamai, AppStream, and Limelight Networks take after the
overlay approach for CDN association. These CDN suppliers
recreate substance to a huge number of store server around the
world. Whenever content demands are gotten from end-clients, they
are diverted to the closest CDN server, consequently enhancing Web
webpage reaction time [33]. As the CDN suppliers require not
controlling the basic system framework components, the
11
administration is streamlined in an overlay approach and it opens
open doors for new administrations. In the system approach, the
system parts including switches and switches are furnished with code
for distinguishing particular application sorts and for sending the
solicitations in light of predefined approaches. Cases of this
approach incorporate gadgets that divert content solicitations to
nearby stores or change movement coming to server farms to
particular servers enhanced to serve particular substance sorts [34].
Some CDN including Akamai, Mirror Image utilize both system and
overlay approach for CDN association. In such case, a system
component including switch, can act at front end of server cultivate
and diverts substance demand to an adjacent application-particular
surrogate server.
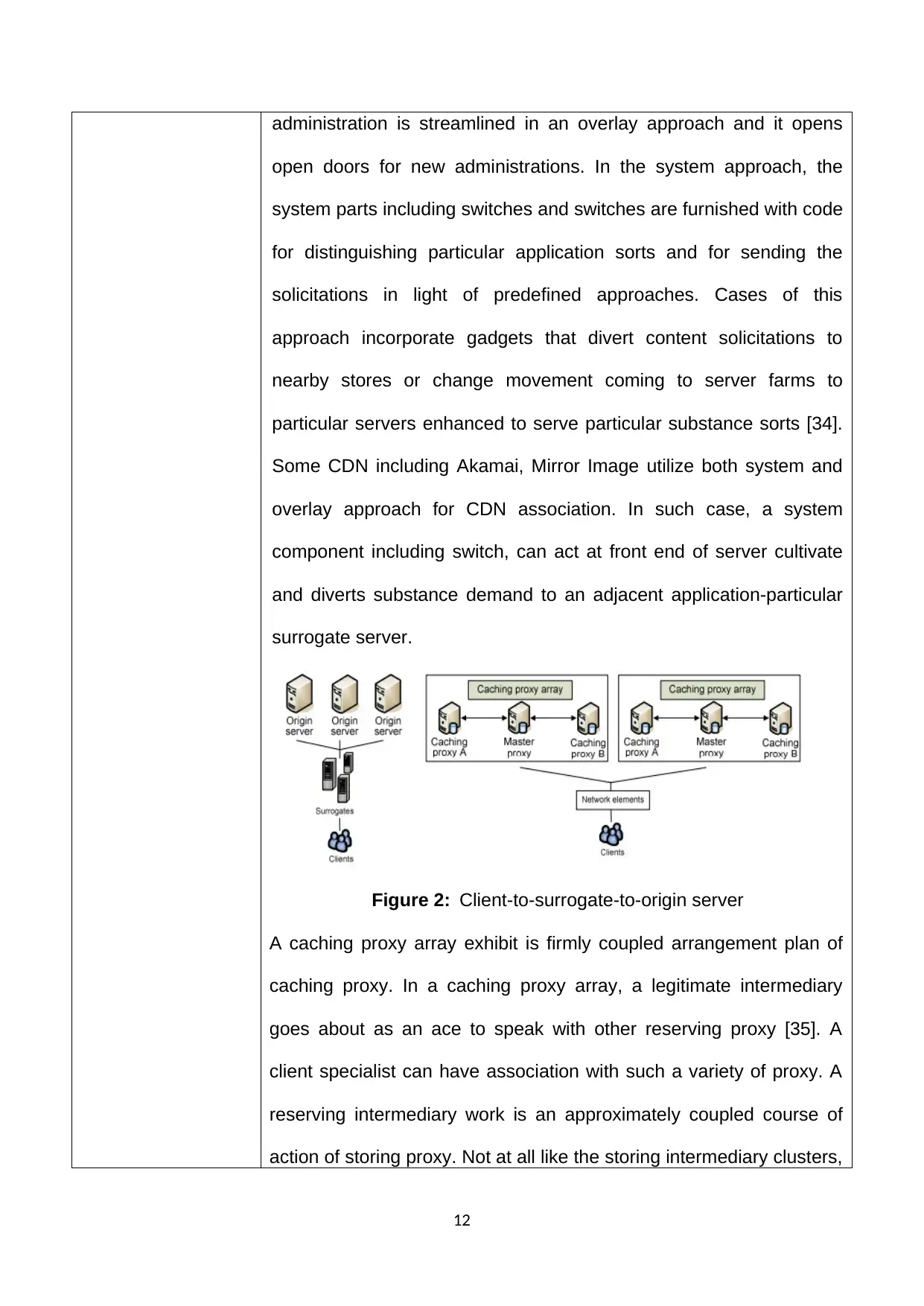
Figure 2: Client-to-surrogate-to-origin server
A caching proxy array exhibit is firmly coupled arrangement plan of
caching proxy. In a caching proxy array, a legitimate intermediary
goes about as an ace to speak with other reserving proxy [35]. A
client specialist can have association with such a variety of proxy. A
reserving intermediary work is an approximately coupled course of
action of storing proxy. Not at all like the storing intermediary clusters,
12
open doors for new administrations. In the system approach, the
system parts including switches and switches are furnished with code
for distinguishing particular application sorts and for sending the
solicitations in light of predefined approaches. Cases of this
approach incorporate gadgets that divert content solicitations to
nearby stores or change movement coming to server farms to
particular servers enhanced to serve particular substance sorts [34].
Some CDN including Akamai, Mirror Image utilize both system and
overlay approach for CDN association. In such case, a system
component including switch, can act at front end of server cultivate
and diverts substance demand to an adjacent application-particular
surrogate server.
Figure 2: Client-to-surrogate-to-origin server
A caching proxy array exhibit is firmly coupled arrangement plan of
caching proxy. In a caching proxy array, a legitimate intermediary
goes about as an ace to speak with other reserving proxy [35]. A
client specialist can have association with such a variety of proxy. A
reserving intermediary work is an approximately coupled course of
action of storing proxy. Not at all like the storing intermediary clusters,
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





