Cloud Computing Security and Privacy: A Research Proposal
VerifiedAdded on 2023/01/19
|8
|1975
|27
Project
AI Summary
This project proposal delves into the critical domain of cloud computing security and privacy. It begins with an introduction to tenant clouds and their advantages, emphasizing the importance of secure data storage for individuals and organizations. The proposal outlines the aim to study security and privacy concerns in public tenant clouds, along with specific objectives, research questions, and a detailed methodology. The research design employs an exploratory approach with an inductive research approach, utilizing secondary data collection and thematic data analysis. Ethical considerations are also addressed. Expected outcomes include insights into preventive software and devices to enhance data security, analysis of threats, and the identification of factors affecting cloud safety. The project includes a time and activity plan and addresses potential risks associated with the research process. References to relevant books and journals are also provided, offering a comprehensive overview of the topic.

Proposal- Cloud Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION-300....................................................................................................................3
AIM AND OBJECTIVES]..............................................................................................................4
Aim-.............................................................................................................................................4
Objectives-...................................................................................................................................4
RESEARCH QUESTIONS.............................................................................................................4
METHODS......................................................................................................................................4
EXPECTED OUTCOMES-300.......................................................................................................5
TIME AND ACTIVITY PLAN.......................................................................................................6
RISK MANAGEMENT...................................................................................................................6
REFERENCES................................................................................................................................7
INTRODUCTION-300....................................................................................................................3
AIM AND OBJECTIVES]..............................................................................................................4
Aim-.............................................................................................................................................4
Objectives-...................................................................................................................................4
RESEARCH QUESTIONS.............................................................................................................4
METHODS......................................................................................................................................4
EXPECTED OUTCOMES-300.......................................................................................................5
TIME AND ACTIVITY PLAN.......................................................................................................6
RISK MANAGEMENT...................................................................................................................6
REFERENCES................................................................................................................................7

INTRODUCTION-300
The tenant is a cloud that is owned by a single person. It also can be takes as a cloud
computing architecture that allows the user to share their resources with in their limitations. The
information and data stores on this network is not accessible to other users (Kalaiprasath,
Elankavi and Udayakumar, 2017). There are different people around the world using clouds to
store their personal and private information. In the 21st century it is one of the best service that
allows the user to store their data on virtual network to keep it safe and secure for long time.
These services are provided by different service providers with certain charges. Some services
providing this cloud storage for free. There no physical limit of cloud data storage.
Cloud storage is beneficiary for different organization and people who have large data to
store, and they do not possess that much physical devices to store that data. This technology is
useful for business organization who have a lot of data to handle. They can use this clouds to
keep backup for their data. This is how individual person and an organization can use tenant
cloud to keep back up of their data for future use. There are different advantages of cloud
storage. It is basically classified in two categories. One is single cloud and other is multi Tenant
clouds. Both are same in function and main different is in their architecture. The architecture is
based on the number of users for a single cloud.
There are many benefits of both single and multi tenant clouds, that can help the
organization to meet their storage related demand. There is no limitation in the storage capability
and user can store large size data on cloud just by purchasing the cloud slot or package. Cloud
storage can help the user to save cost that required in the purchase of the storage devices. If due
to any failure if user lost their data then they can recover their data which is stored on clouds
(Singh and Chatterjee, 2017). The cloud storage is accessible to all mobile locations. User only
need computer and internet to access data from the cloud storage. There are different type of
protection is provided in the cloud storage to keep data safe from any cyber attack. These are
some advantages of tenant cloud. But there are some threats are associated with the use of cloud
storage. The main concern related to the cloud storage are associated with security and privacy of
data.
Security and private is major problem in the cloud storage. On the regular basis hackers
and cyber criminal use to infect the user cloud storage with viruses to stole and over write the
information. Criminals have offensive practices that can harm the data and information of user
The tenant is a cloud that is owned by a single person. It also can be takes as a cloud
computing architecture that allows the user to share their resources with in their limitations. The
information and data stores on this network is not accessible to other users (Kalaiprasath,
Elankavi and Udayakumar, 2017). There are different people around the world using clouds to
store their personal and private information. In the 21st century it is one of the best service that
allows the user to store their data on virtual network to keep it safe and secure for long time.
These services are provided by different service providers with certain charges. Some services
providing this cloud storage for free. There no physical limit of cloud data storage.
Cloud storage is beneficiary for different organization and people who have large data to
store, and they do not possess that much physical devices to store that data. This technology is
useful for business organization who have a lot of data to handle. They can use this clouds to
keep backup for their data. This is how individual person and an organization can use tenant
cloud to keep back up of their data for future use. There are different advantages of cloud
storage. It is basically classified in two categories. One is single cloud and other is multi Tenant
clouds. Both are same in function and main different is in their architecture. The architecture is
based on the number of users for a single cloud.
There are many benefits of both single and multi tenant clouds, that can help the
organization to meet their storage related demand. There is no limitation in the storage capability
and user can store large size data on cloud just by purchasing the cloud slot or package. Cloud
storage can help the user to save cost that required in the purchase of the storage devices. If due
to any failure if user lost their data then they can recover their data which is stored on clouds
(Singh and Chatterjee, 2017). The cloud storage is accessible to all mobile locations. User only
need computer and internet to access data from the cloud storage. There are different type of
protection is provided in the cloud storage to keep data safe from any cyber attack. These are
some advantages of tenant cloud. But there are some threats are associated with the use of cloud
storage. The main concern related to the cloud storage are associated with security and privacy of
data.
Security and private is major problem in the cloud storage. On the regular basis hackers
and cyber criminal use to infect the user cloud storage with viruses to stole and over write the
information. Criminals have offensive practices that can harm the data and information of user
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

which is stored in the virtual storage. These are some challenges to the Tenant cloud storage
which are need to address to make it more secure and useful for consumer. This research will be
providing the brief information of privacy and security concerns of tenant clouds. The research
will be discussing importance of privacy and security in cloud computing. Various methods will
be considered in the research that can help the service providers and user to improve the privacy
and security of their data.
AIM AND OBJECTIVES]
Aim-
To study the privacy and security concerns in Public Tenant clouds.
Objectives-
1. To learn importance of privacy and security in Tenant clouds.
2. To learn the different security concerns in tenant clouds.
3. To evaluate different methods to improve security and privacy in tenant clouds.
RESEARCH QUESTIONS
Question 1. How security and privacy is important in Tenant clouds.?
Question 2. What are main security concerns in tenant cloud?
Question 3. Which methods or technologies can be used to improve security and privacy of
tenant clouds?
METHODS
There are different type of approaches can be used in the research work (Ørngreen and
Levinsen, 2017). This is important to use specific approach in research work to make the work
and information effective for the readers.
Research Design- A particular design is required to use for the research. This is important to use
the different components of research report in effective and logical method to prevent the
unusual discussion in result and address particular topic (Mackey and Gass, 2015). This research
will be using exploratory approach because there are different solutions are required for the issue
of security and privacy in tenant Clouds. This will be most suitable approach for the research
because it will help user to collect information in effective way.
Research Approach- It can be classified as a outlining plan for the research which can be used
by researcher to perform whole research work (Ledford and Gast, 2018). The plan or approach
which are need to address to make it more secure and useful for consumer. This research will be
providing the brief information of privacy and security concerns of tenant clouds. The research
will be discussing importance of privacy and security in cloud computing. Various methods will
be considered in the research that can help the service providers and user to improve the privacy
and security of their data.
AIM AND OBJECTIVES]
Aim-
To study the privacy and security concerns in Public Tenant clouds.
Objectives-
1. To learn importance of privacy and security in Tenant clouds.
2. To learn the different security concerns in tenant clouds.
3. To evaluate different methods to improve security and privacy in tenant clouds.
RESEARCH QUESTIONS
Question 1. How security and privacy is important in Tenant clouds.?
Question 2. What are main security concerns in tenant cloud?
Question 3. Which methods or technologies can be used to improve security and privacy of
tenant clouds?
METHODS
There are different type of approaches can be used in the research work (Ørngreen and
Levinsen, 2017). This is important to use specific approach in research work to make the work
and information effective for the readers.
Research Design- A particular design is required to use for the research. This is important to use
the different components of research report in effective and logical method to prevent the
unusual discussion in result and address particular topic (Mackey and Gass, 2015). This research
will be using exploratory approach because there are different solutions are required for the issue
of security and privacy in tenant Clouds. This will be most suitable approach for the research
because it will help user to collect information in effective way.
Research Approach- It can be classified as a outlining plan for the research which can be used
by researcher to perform whole research work (Ledford and Gast, 2018). The plan or approach
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

that will selected for research is based on the nature of research problem addressed by the
researcher. To conduct research on security and privacy issue topic the best approach is inductive
approach. Because this will provide better opportunity to research to find the answers for
questions.
Research Type- To find the answers For the particular research question researcher need to
collect different type of data. The type of research is based on what kind of result and conclusion
need to be concluded (Taylor, Bogdan and DeVault, 2015). For this research quantitative
approach can be used because in this research it is required to analyse different suggestion of
authors.
Research Philosophy- All the researches that are performed by different researcher, are
completed with certain mindset and beliefs. The results of research are based on the thinking
possessed by the researcher (Attia and Edge, 2017). For this research work realism research
philosophy can be used. Because the scientific results are required in process, this approach will
be more effective
Data Collection- To analyse the different perspectives of authors various kind of data is
collected to perform research (Dumay and Cai, 2015.). Because in this process researcher need to
use different technical books and journal, Secondary data collection will be the best suitable
approach for this research work.
Data Analysis- In a research work various kind of data is collected to generate more precise and
accurate result and conclusion (McCusker and Gunaydin, 2015). Because in this research the
secondary data collection approach is used. The data collected in research will be in form of
suggestion and theoretical explanation. To analyse this kind of data thematic data analysis
approach will be more effective.
Ethical Consideration- There are various consideration are need to be taken while performing
the research work. This is important to consider these ethical consideration to make the report
right and precise (King and Mackey, 2016). Tom make the report ethical authorized and
authenticate sources are used in research.
EXPECTED OUTCOMES-300
The expected outcomes of this research will be related to some preventive software and
devices that can help the service provider and user to improve the security and privacy of their
data. This research will analyse the different threat that can cause this security and privacy
researcher. To conduct research on security and privacy issue topic the best approach is inductive
approach. Because this will provide better opportunity to research to find the answers for
questions.
Research Type- To find the answers For the particular research question researcher need to
collect different type of data. The type of research is based on what kind of result and conclusion
need to be concluded (Taylor, Bogdan and DeVault, 2015). For this research quantitative
approach can be used because in this research it is required to analyse different suggestion of
authors.
Research Philosophy- All the researches that are performed by different researcher, are
completed with certain mindset and beliefs. The results of research are based on the thinking
possessed by the researcher (Attia and Edge, 2017). For this research work realism research
philosophy can be used. Because the scientific results are required in process, this approach will
be more effective
Data Collection- To analyse the different perspectives of authors various kind of data is
collected to perform research (Dumay and Cai, 2015.). Because in this process researcher need to
use different technical books and journal, Secondary data collection will be the best suitable
approach for this research work.
Data Analysis- In a research work various kind of data is collected to generate more precise and
accurate result and conclusion (McCusker and Gunaydin, 2015). Because in this research the
secondary data collection approach is used. The data collected in research will be in form of
suggestion and theoretical explanation. To analyse this kind of data thematic data analysis
approach will be more effective.
Ethical Consideration- There are various consideration are need to be taken while performing
the research work. This is important to consider these ethical consideration to make the report
right and precise (King and Mackey, 2016). Tom make the report ethical authorized and
authenticate sources are used in research.
EXPECTED OUTCOMES-300
The expected outcomes of this research will be related to some preventive software and
devices that can help the service provider and user to improve the security and privacy of their
data. This research will analyse the different threat that can cause this security and privacy
issues. The research will analyse different factors which can affect the safety and privacy of the
cloud. As per the research question in the first part research will analyse the importance of
security and safety consideration in tenant clouds. On the basis of research work this research
will analyse the various methods that can used in the security and privacy firewall of user to
prevent any kind of attack on the system. This is how research will derive answers for the
research aim and objectives. The research methodology will provide a brief of approaches that
are used in the research work. Data analysis process will provide specific results and solution for
the issues related to the data security and privacy in the cloud storages.
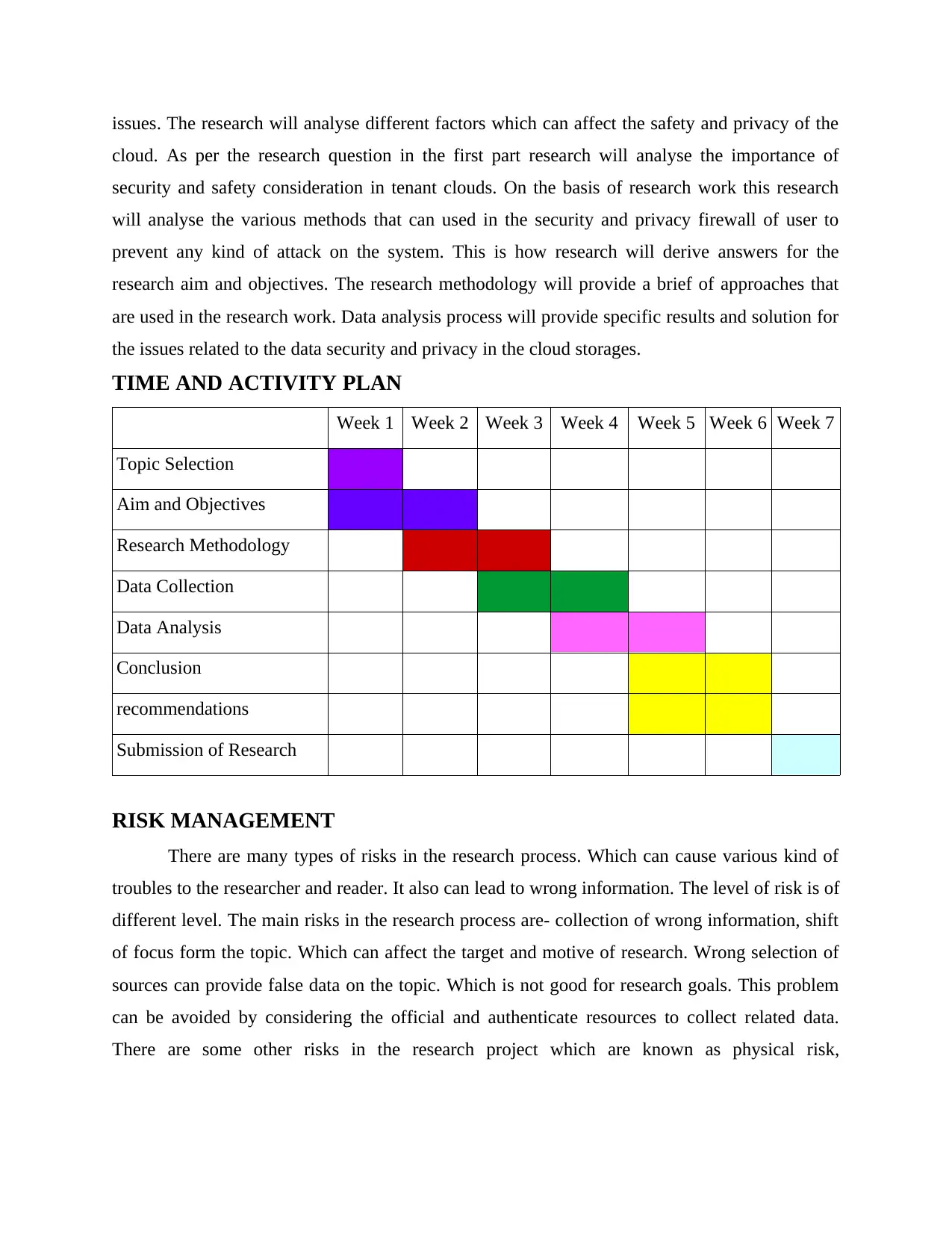
TIME AND ACTIVITY PLAN
Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7
Topic Selection
Aim and Objectives
Research Methodology
Data Collection
Data Analysis
Conclusion
recommendations
Submission of Research
RISK MANAGEMENT
There are many types of risks in the research process. Which can cause various kind of
troubles to the researcher and reader. It also can lead to wrong information. The level of risk is of
different level. The main risks in the research process are- collection of wrong information, shift
of focus form the topic. Which can affect the target and motive of research. Wrong selection of
sources can provide false data on the topic. Which is not good for research goals. This problem
can be avoided by considering the official and authenticate resources to collect related data.
There are some other risks in the research project which are known as physical risk,
cloud. As per the research question in the first part research will analyse the importance of
security and safety consideration in tenant clouds. On the basis of research work this research
will analyse the various methods that can used in the security and privacy firewall of user to
prevent any kind of attack on the system. This is how research will derive answers for the
research aim and objectives. The research methodology will provide a brief of approaches that
are used in the research work. Data analysis process will provide specific results and solution for
the issues related to the data security and privacy in the cloud storages.
TIME AND ACTIVITY PLAN
Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7
Topic Selection
Aim and Objectives
Research Methodology
Data Collection
Data Analysis
Conclusion
recommendations
Submission of Research
RISK MANAGEMENT
There are many types of risks in the research process. Which can cause various kind of
troubles to the researcher and reader. It also can lead to wrong information. The level of risk is of
different level. The main risks in the research process are- collection of wrong information, shift
of focus form the topic. Which can affect the target and motive of research. Wrong selection of
sources can provide false data on the topic. Which is not good for research goals. This problem
can be avoided by considering the official and authenticate resources to collect related data.
There are some other risks in the research project which are known as physical risk,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

psychological risks, social risks and legal risks. This all types of risk can be avoided by prepare
better plan and method for research.
better plan and method for research.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journal
Attia, M. and Edge, J., 2017. Be (com) ing a reflexive researcher: a developmental approach to
research methodology. Open Review of Educational Research. 4(1). pp.33-45.
Dumay, J. and Cai, L., 2015. Using content analysis as a research methodology for investigating
intellectual capital disclosure: a critique. Journal of Intellectual Capital. 16(1). pp.121-
155.
Kalaiprasath, R., Elankavi, R. and Udayakumar, D.R., 2017. Cloud. Security and Compliance-A
Semantic Approach in End to End Security. International Journal Of Mechanical
Engineering And Technology (Ijmet). 8(5). pp.987-994.
King, K.A. and Mackey, A., 2016. Research methodology in second language studies: Trends,
concerns, and new directions. The Modern Language Journal. 100(S1). pp.209-227.
Ledford, J.R. and Gast, D.L., 2018. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion. 30(7). pp.537-542.
Ørngreen, R. and Levinsen, K., 2017. Workshops as a Research Methodology. Electronic
Journal of E-learning. 15(1). pp.70-81.
Singh, A. and Chatterjee, K., 2017. Cloud security issues and challenges: A survey. Journal of
Network and Computer Applications. 79. pp.88-115.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
Books and Journal
Attia, M. and Edge, J., 2017. Be (com) ing a reflexive researcher: a developmental approach to
research methodology. Open Review of Educational Research. 4(1). pp.33-45.
Dumay, J. and Cai, L., 2015. Using content analysis as a research methodology for investigating
intellectual capital disclosure: a critique. Journal of Intellectual Capital. 16(1). pp.121-
155.
Kalaiprasath, R., Elankavi, R. and Udayakumar, D.R., 2017. Cloud. Security and Compliance-A
Semantic Approach in End to End Security. International Journal Of Mechanical
Engineering And Technology (Ijmet). 8(5). pp.987-994.
King, K.A. and Mackey, A., 2016. Research methodology in second language studies: Trends,
concerns, and new directions. The Modern Language Journal. 100(S1). pp.209-227.
Ledford, J.R. and Gast, D.L., 2018. Single case research methodology: Applications in special
education and behavioral sciences. Routledge.
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion. 30(7). pp.537-542.
Ørngreen, R. and Levinsen, K., 2017. Workshops as a Research Methodology. Electronic
Journal of E-learning. 15(1). pp.70-81.
Singh, A. and Chatterjee, K., 2017. Cloud security issues and challenges: A survey. Journal of
Network and Computer Applications. 79. pp.88-115.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research methods: A
guidebook and resource. John Wiley & Sons.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





