COSC2651 - Security in Computing and IT Assignment: OUA SP4 2019
VerifiedAdded on 2022/08/18
|7
|2956
|17
Homework Assignment
AI Summary
This document presents a comprehensive solution to a Security in Computing and IT assignment. It begins by exploring various techniques for deciphering encrypted messages, including brute force, dictionary attacks, and rainbow tables, along with estimations of decryption times based on hardware capabilities and key lengths. The solution then delves into methods to enhance security, such as salt inclusion and complex passwords, while also discussing factors that can make decryption easier. The assignment further examines the risks associated with storing user credentials in plain text and the significance of hashing algorithms. It provides detailed explanations of hashing, rainbow tables, and key stretching techniques, as well as various password cracking methods and their prevention. The document also includes a comparison of MD5, SHA-0, SHA-1, SHA-2, and SHA-3 hashing algorithms, discussing their applications, vulnerabilities, and the importance of padding in encryption. Finally, it offers insights into securing employee credentials using SHA-3 and protecting data against various attacks.

Running head: Security in Computing and IT
Security in Computing and IT
Name of the Student
Name of the University
Authors note
Security in Computing and IT
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY IN COMPUTING AND IT
Task 1
A
In order to decipher the message, we can use the brute force, rainbow table, dictionary attack in order to decrypt the message with the
public key. In case of BruteForce attack, intruder or attacker uses different possible keys / passwords as well as checks with the passwords in
order to check if any one of them returns correct plaintext from the decrypted message. This is often denoted as exhaustive key search. Required
amount of time is calculated with proportion to size of used secret key. Maximum number of attempts used is calculate as 2keysize where the
number of bits is considered as key size. In case of dictionary attack, it is attempted to guess the unknown key to decrypt the message through
the use of the well-known phrases.
B
For the automated techniques the time required for decryption mainly depends on the length of the keys even with the use of the current
high-end consumer hardware which includes AMD Ryzen 7 1800X running at 3.6GHz. While considering consumer hardware in order to
decrypt the intercepted message most effective and required hardware is graphics card or the GPU. As while considering the and trying too many
changed encryption keys at the same time the graphics cards that are able to execute threads in parallel manner are ideal. Therefore, depending
on the
As an example, it can be stated that with varying length of the key’s bits, following table is estimated;
Key length Estimated Time to decrypt
10 1Second or less
20 20 seconds
40 250 days
64 12000 years.
In the similar manner, if it is considered that the encryption key is 2048-RSA key, then the time required to decrypt the message will be
6.5 quadrillion years approximately.
C
Use of the salt inclusion techniques or keyword stretching can help in making the decryption process harder for the intruder. Salt is
random data that can be used while using the cryptography function along with plain text password at the time of hashing the passwords. In case
of Salt inclusion technique random string of characters is added with the key in the encryption process. While using the salts it is recommended
to use a salt that consist of a combination of letters, numbers as well as symbols.
D
Complex passwords and encryption technique such as SHA-512 can improve the security of the protected data. Therefore, exclusion of
the use of the strong keys for the encryption process as well as parallel processing with multiple techniques can enhance the forceful
decryption process /attacks faster as well as easier. Lack of the strong passwords and salts will help attacker to break the encryption minimum
amount of time with the matching hash and plain text passwords.
Task 2
A
If the organization is storing the user ID and passwords in plain text in database then in case of database breach then it will be easier for
hackers/ intruders to easily access to user credentials including their password. Therefore, it can be stated users/people who frequently utilize
same passwords on different sites are can get into trouble and may lead to economic loss and stolen identity of the users (Sahu and Ansari
2017). With the other vulnerabilities at the application end that allows SQL injection like attacks then the intruders does not even have to access
in the database in order to get the passwords that are stored in plain text.
Task 1
A
In order to decipher the message, we can use the brute force, rainbow table, dictionary attack in order to decrypt the message with the
public key. In case of BruteForce attack, intruder or attacker uses different possible keys / passwords as well as checks with the passwords in
order to check if any one of them returns correct plaintext from the decrypted message. This is often denoted as exhaustive key search. Required
amount of time is calculated with proportion to size of used secret key. Maximum number of attempts used is calculate as 2keysize where the
number of bits is considered as key size. In case of dictionary attack, it is attempted to guess the unknown key to decrypt the message through
the use of the well-known phrases.
B
For the automated techniques the time required for decryption mainly depends on the length of the keys even with the use of the current
high-end consumer hardware which includes AMD Ryzen 7 1800X running at 3.6GHz. While considering consumer hardware in order to
decrypt the intercepted message most effective and required hardware is graphics card or the GPU. As while considering the and trying too many
changed encryption keys at the same time the graphics cards that are able to execute threads in parallel manner are ideal. Therefore, depending
on the
As an example, it can be stated that with varying length of the key’s bits, following table is estimated;
Key length Estimated Time to decrypt
10 1Second or less
20 20 seconds
40 250 days
64 12000 years.
In the similar manner, if it is considered that the encryption key is 2048-RSA key, then the time required to decrypt the message will be
6.5 quadrillion years approximately.
C
Use of the salt inclusion techniques or keyword stretching can help in making the decryption process harder for the intruder. Salt is
random data that can be used while using the cryptography function along with plain text password at the time of hashing the passwords. In case
of Salt inclusion technique random string of characters is added with the key in the encryption process. While using the salts it is recommended
to use a salt that consist of a combination of letters, numbers as well as symbols.
D
Complex passwords and encryption technique such as SHA-512 can improve the security of the protected data. Therefore, exclusion of
the use of the strong keys for the encryption process as well as parallel processing with multiple techniques can enhance the forceful
decryption process /attacks faster as well as easier. Lack of the strong passwords and salts will help attacker to break the encryption minimum
amount of time with the matching hash and plain text passwords.
Task 2
A
If the organization is storing the user ID and passwords in plain text in database then in case of database breach then it will be easier for
hackers/ intruders to easily access to user credentials including their password. Therefore, it can be stated users/people who frequently utilize
same passwords on different sites are can get into trouble and may lead to economic loss and stolen identity of the users (Sahu and Ansari
2017). With the other vulnerabilities at the application end that allows SQL injection like attacks then the intruders does not even have to access
in the database in order to get the passwords that are stored in plain text.

2SECURITY IN COMPUTING AND IT
Furthermore, while transmitting the plain text passwords that are stored in the databases through the non-SSL based transmission
channel also can lead to vulnerability that can be exploited using eavesdropping technique or network sniffing tools such as Wireshark.
Moreover, this user credentials are also vulnerable to the MITM attacks.
SSL stripping is another type of attack that can be utilized in order view or retrieve plain text passwords of the users that are flowing
through SSL encrypted channel. Most of the breached authentication/ password data mainly originates from employee espionage. Furthermore,
database backups are vulnerable to attacks by the hackers/intruders. Hackers can gain access to the backup servers in order to get access to the
passwords that are saved in plain text format. It is also possible that developers get the passwords from a database as the response against their
queries made to the server.
B
Hashing is one of the important functions in cryptography that helps in transformation of some specific fixed data into another data that
have fixed length through the use of a specific mathematical process. Hashing includes mapping of original data that may be of any size to some
specific fixed length data through the utilization of a hash table. After this the output data is stored in digest. In terms of security it can be stated
that reconstruction of the initial input data from the digest is virtually impossible from the resulting output even though the attacker has the
information about the used hash function in the process.
C
In the password cracking or key decryption process, the rainbow table is considered as the database which is helpful in gaining the
authentication through the creation of matching password hash for an user. The rainbow table uses a precomputed dictionary containing
plaintext passwords along with the corresponding hash. This table or dictionary is helpful in finding out which plaintext password in the table is
producing the particular hash that matches with the specific user password. Here it can be mentioned that as more than one password or text in
the table can be responsible for producing the same hash, therefore with the passwords that generates the same hash the authentication process
can be passed by the hackers.
Whenever any attacker is able to gains access to password database of any application, utilizing rainbow tables they can get the hashed
passwords. After this from the rainbow table the attacker then gets the possible plain text passwords matching with each hash and finally can use
then in order to get access to an users account.
The attacks backed by the rainbow table can be prevented through the use of the salt techniques while saving the password in the
database. Salt is random part of data which is provided to hash function along with plain text password at the time of hashing the passwords.
Utilization of the of the salt in the hashing process is helpful in the ensuing that each and every password generates unique hash value and
therefore use of the rainbow table in the password cracking attack that principally depends on the logic that the more than one text password
can generate similar hash values can be obviously prevented by adding the salt.
One more technique that can help in preventing the precomputed hash attacks is Key stretching while hashing the passwords before
storing them. In this technique the password, used salt as well as other transitional hash values are passed through the hash function numerous
times in order to improve the computation time which is required in order to hash provided password (Sahu and Ansari 2017). Another
alternative approach to mitigate the risk of rainbow table attacks is key strengthening. In this approach, the password or key is extended through
the use of random salt. In the next stage the salt is securely deleted. After the completion of this technique it enforces both the legitimate user
and the attackers to carry out brute-force search approach in order to search the salt value.
MD5, SHA1 and other variants are the password hashing function that generates a digest from the actual content. MD5 and SHA1 are
outdated password hashing algorithms and most rainbow tables used to crack passwords are built to target applications and systems using these
hashing methods. Consider using more modern hashing methods like SHA2 (Long 2019).
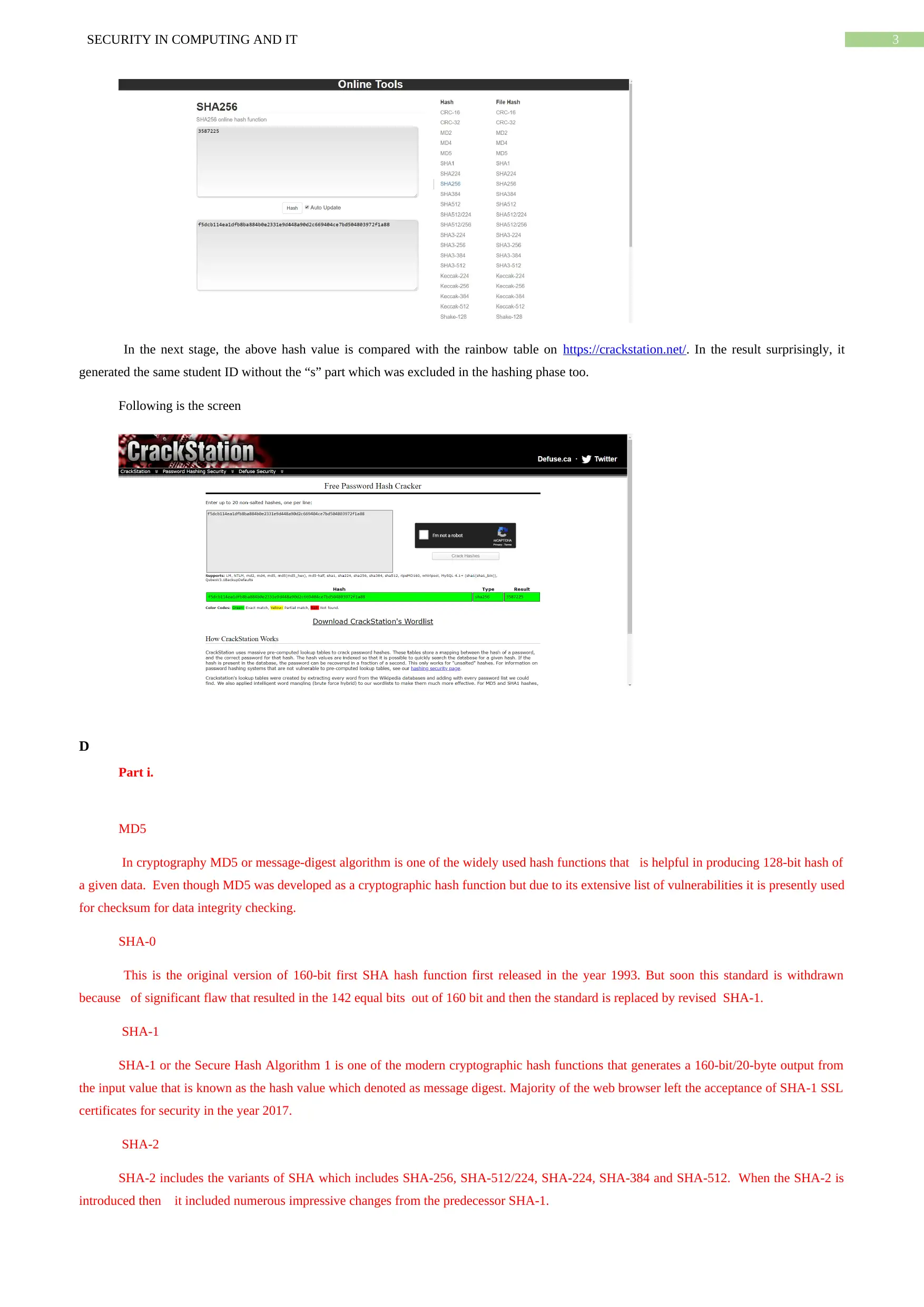
My student ID is s3587225
Now considering the numerical part we get the following
f5dcb114ea1dfb8ba884b0e2331e9d448a90d2c669404ce7bd504803972f1a88
url used: https://emn178.github.io/online-tools/sha256.html
Furthermore, while transmitting the plain text passwords that are stored in the databases through the non-SSL based transmission
channel also can lead to vulnerability that can be exploited using eavesdropping technique or network sniffing tools such as Wireshark.
Moreover, this user credentials are also vulnerable to the MITM attacks.
SSL stripping is another type of attack that can be utilized in order view or retrieve plain text passwords of the users that are flowing
through SSL encrypted channel. Most of the breached authentication/ password data mainly originates from employee espionage. Furthermore,
database backups are vulnerable to attacks by the hackers/intruders. Hackers can gain access to the backup servers in order to get access to the
passwords that are saved in plain text format. It is also possible that developers get the passwords from a database as the response against their
queries made to the server.
B
Hashing is one of the important functions in cryptography that helps in transformation of some specific fixed data into another data that
have fixed length through the use of a specific mathematical process. Hashing includes mapping of original data that may be of any size to some
specific fixed length data through the utilization of a hash table. After this the output data is stored in digest. In terms of security it can be stated
that reconstruction of the initial input data from the digest is virtually impossible from the resulting output even though the attacker has the
information about the used hash function in the process.
C
In the password cracking or key decryption process, the rainbow table is considered as the database which is helpful in gaining the
authentication through the creation of matching password hash for an user. The rainbow table uses a precomputed dictionary containing
plaintext passwords along with the corresponding hash. This table or dictionary is helpful in finding out which plaintext password in the table is
producing the particular hash that matches with the specific user password. Here it can be mentioned that as more than one password or text in
the table can be responsible for producing the same hash, therefore with the passwords that generates the same hash the authentication process
can be passed by the hackers.
Whenever any attacker is able to gains access to password database of any application, utilizing rainbow tables they can get the hashed
passwords. After this from the rainbow table the attacker then gets the possible plain text passwords matching with each hash and finally can use
then in order to get access to an users account.
The attacks backed by the rainbow table can be prevented through the use of the salt techniques while saving the password in the
database. Salt is random part of data which is provided to hash function along with plain text password at the time of hashing the passwords.
Utilization of the of the salt in the hashing process is helpful in the ensuing that each and every password generates unique hash value and
therefore use of the rainbow table in the password cracking attack that principally depends on the logic that the more than one text password
can generate similar hash values can be obviously prevented by adding the salt.
One more technique that can help in preventing the precomputed hash attacks is Key stretching while hashing the passwords before
storing them. In this technique the password, used salt as well as other transitional hash values are passed through the hash function numerous
times in order to improve the computation time which is required in order to hash provided password (Sahu and Ansari 2017). Another
alternative approach to mitigate the risk of rainbow table attacks is key strengthening. In this approach, the password or key is extended through
the use of random salt. In the next stage the salt is securely deleted. After the completion of this technique it enforces both the legitimate user
and the attackers to carry out brute-force search approach in order to search the salt value.
MD5, SHA1 and other variants are the password hashing function that generates a digest from the actual content. MD5 and SHA1 are
outdated password hashing algorithms and most rainbow tables used to crack passwords are built to target applications and systems using these
hashing methods. Consider using more modern hashing methods like SHA2 (Long 2019).
My student ID is s3587225
Now considering the numerical part we get the following
f5dcb114ea1dfb8ba884b0e2331e9d448a90d2c669404ce7bd504803972f1a88
url used: https://emn178.github.io/online-tools/sha256.html
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SECURITY IN COMPUTING AND IT
In the next stage, the above hash value is compared with the rainbow table on https://crackstation.net/. In the result surprisingly, it
generated the same student ID without the “s” part which was excluded in the hashing phase too.
Following is the screen
D
Part i.
MD5
In cryptography MD5 or message-digest algorithm is one of the widely used hash functions that is helpful in producing 128-bit hash of
a given data. Even though MD5 was developed as a cryptographic hash function but due to its extensive list of vulnerabilities it is presently used
for checksum for data integrity checking.
SHA-0
This is the original version of 160-bit first SHA hash function first released in the year 1993. But soon this standard is withdrawn
because of significant flaw that resulted in the 142 equal bits out of 160 bit and then the standard is replaced by revised SHA-1.
SHA-1
SHA-1 or the Secure Hash Algorithm 1 is one of the modern cryptographic hash functions that generates a 160-bit/20-byte output from
the input value that is known as the hash value which denoted as message digest. Majority of the web browser left the acceptance of SHA-1 SSL
certificates for security in the year 2017.
SHA-2
SHA-2 includes the variants of SHA which includes SHA-256, SHA-512/224, SHA-224, SHA-384 and SHA-512. When the SHA-2 is
introduced then it included numerous impressive changes from the predecessor SHA-1.
In the next stage, the above hash value is compared with the rainbow table on https://crackstation.net/. In the result surprisingly, it
generated the same student ID without the “s” part which was excluded in the hashing phase too.
Following is the screen
D
Part i.
MD5
In cryptography MD5 or message-digest algorithm is one of the widely used hash functions that is helpful in producing 128-bit hash of
a given data. Even though MD5 was developed as a cryptographic hash function but due to its extensive list of vulnerabilities it is presently used
for checksum for data integrity checking.
SHA-0
This is the original version of 160-bit first SHA hash function first released in the year 1993. But soon this standard is withdrawn
because of significant flaw that resulted in the 142 equal bits out of 160 bit and then the standard is replaced by revised SHA-1.
SHA-1
SHA-1 or the Secure Hash Algorithm 1 is one of the modern cryptographic hash functions that generates a 160-bit/20-byte output from
the input value that is known as the hash value which denoted as message digest. Majority of the web browser left the acceptance of SHA-1 SSL
certificates for security in the year 2017.
SHA-2
SHA-2 includes the variants of SHA which includes SHA-256, SHA-512/224, SHA-224, SHA-384 and SHA-512. When the SHA-2 is
introduced then it included numerous impressive changes from the predecessor SHA-1.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY IN COMPUTING AND IT
The SHA-2 included six hash functions that generates the digests with 224, 256, 384 and 512 bits. In case of the SHA-256, SHA-512,
the hash functions were able to compute hash with 32-bit and 64-bit words. In the computing process both the functions utilized different
additive constants as well as shift amounts for generating the digest where as their structures virtually identical.
SHA-3
SHA-3 is the latest SHA cryptography standard released in the year 2015 by NIST (National Institute of Standards and Technology).
This cryptography function is internally changed when compared to the MD5 structure SHA-1 and SHA-2 structure. Even though NIST is not
going to withdraw SHA-2 but the SHA-3 can be substituted for SHA-2 in the current applications whenever required or necessary. Change or
substitution to the SHA-3 will be able to expressively improve robustness of the complete hash algorithm toolkit.
Part ii.
In case of MD5, data can be secured from the unintentional corruption through the transmission channel. Presently this method is
suitable for different non-cryptographic use cases such as determining the partition in a disk or a particular key inside the partitioned database.
On the other hand, some of the extensively used security applications/ protocols such as SSH, TLS, SSL, PGP, S/MIME still supports SHA-1.
For SHA2, only difference is the number of rounds that are utilized in generating the digest. Initially the adoption of the SHA-2 was not easy due
to the lack of support for SHA-2 on different widely used operating system and collision in the generated digests were not found ( Long 2019).
Lastly compared to the previous, algorithms, in order to ensure that the input message is evenly divided into different r-bit blocks the padding in
the encryption is important. The block transformation techniques used in the SHA-3 is the Keccak-f. This considers the permutation of XOR,
AND as well as NOT operations. This algorithm is designed in such way that they can be easily implemented in both platforms’
software/hardware. In the year 2016, the team that developed SHA-3 functions as well as Keccak algorithms again announced the faster reduced-
rounds from to 12 and 14 rounds reduced from 24 in case of SHA-3 (Sahu and Ansari 2017).
Part iii.
For the encrypted message as in provided for Task 2, the SHA3 can be utilized in order to secure the stored credentials of the employees
to store them with better encryption and security that does not have any record of hash collision. In this way the data can be protected from the
intruders or attackers from different attacks with the help of high configurations systems.
Task 3
A
Even after the changes in the security of the data accessibility in the year 2018 due to the Cambridge Analytica expose, in the year 2019
there is again a reported breach to the user database by the app developers through the abuse of the Group API. According to the reports,
after 2018, Facebook made changes in the APIs’ that were developed for the developers in order to access specific data through using them and
restricting access to other information through the Groups API.
B
The Group API’s were mainly developed for the app developers so that they can integrate their applications in much more tightly manner
while maintaining the overall Facebook experience for the user. Unfortunately, due to the few loopholes in the API, app developers had access to
the user’s personal information in an improper way. Initially, Facebook intended to provide the data related to name of the Group, user
count of that specific Group, posts related to the specific Group. If any of the users of the users chose to, then they can opt-in to the options
to make the available their profile pictures different other profile information (Lindsey 2019). Where in this scenario, the developers were able
to access to the personal details such as names, profile pictures those who were involved in the group activity (of the users who may not have
opt in for the same while joining in the group). Reportedly through this Illegal scraping of Facebook API lead to 267 million user IDs, phone
numbers, and names are expose from the Elasticsearch Cluster.
C
According to head of platform partnerships Konstantinos Papamiltiadis of Facebook, it is stated that in their investigation it is found that
100 of the partners were able to access this restricted group’s members data and out of them 11 partners accessed user data through the use of
this API in last 60 days. The organization also claims that, in their investigation they have not found any evidence of exploitation and abuse of
The SHA-2 included six hash functions that generates the digests with 224, 256, 384 and 512 bits. In case of the SHA-256, SHA-512,
the hash functions were able to compute hash with 32-bit and 64-bit words. In the computing process both the functions utilized different
additive constants as well as shift amounts for generating the digest where as their structures virtually identical.
SHA-3
SHA-3 is the latest SHA cryptography standard released in the year 2015 by NIST (National Institute of Standards and Technology).
This cryptography function is internally changed when compared to the MD5 structure SHA-1 and SHA-2 structure. Even though NIST is not
going to withdraw SHA-2 but the SHA-3 can be substituted for SHA-2 in the current applications whenever required or necessary. Change or
substitution to the SHA-3 will be able to expressively improve robustness of the complete hash algorithm toolkit.
Part ii.
In case of MD5, data can be secured from the unintentional corruption through the transmission channel. Presently this method is
suitable for different non-cryptographic use cases such as determining the partition in a disk or a particular key inside the partitioned database.
On the other hand, some of the extensively used security applications/ protocols such as SSH, TLS, SSL, PGP, S/MIME still supports SHA-1.
For SHA2, only difference is the number of rounds that are utilized in generating the digest. Initially the adoption of the SHA-2 was not easy due
to the lack of support for SHA-2 on different widely used operating system and collision in the generated digests were not found ( Long 2019).
Lastly compared to the previous, algorithms, in order to ensure that the input message is evenly divided into different r-bit blocks the padding in
the encryption is important. The block transformation techniques used in the SHA-3 is the Keccak-f. This considers the permutation of XOR,
AND as well as NOT operations. This algorithm is designed in such way that they can be easily implemented in both platforms’
software/hardware. In the year 2016, the team that developed SHA-3 functions as well as Keccak algorithms again announced the faster reduced-
rounds from to 12 and 14 rounds reduced from 24 in case of SHA-3 (Sahu and Ansari 2017).
Part iii.
For the encrypted message as in provided for Task 2, the SHA3 can be utilized in order to secure the stored credentials of the employees
to store them with better encryption and security that does not have any record of hash collision. In this way the data can be protected from the
intruders or attackers from different attacks with the help of high configurations systems.
Task 3
A
Even after the changes in the security of the data accessibility in the year 2018 due to the Cambridge Analytica expose, in the year 2019
there is again a reported breach to the user database by the app developers through the abuse of the Group API. According to the reports,
after 2018, Facebook made changes in the APIs’ that were developed for the developers in order to access specific data through using them and
restricting access to other information through the Groups API.
B
The Group API’s were mainly developed for the app developers so that they can integrate their applications in much more tightly manner
while maintaining the overall Facebook experience for the user. Unfortunately, due to the few loopholes in the API, app developers had access to
the user’s personal information in an improper way. Initially, Facebook intended to provide the data related to name of the Group, user
count of that specific Group, posts related to the specific Group. If any of the users of the users chose to, then they can opt-in to the options
to make the available their profile pictures different other profile information (Lindsey 2019). Where in this scenario, the developers were able
to access to the personal details such as names, profile pictures those who were involved in the group activity (of the users who may not have
opt in for the same while joining in the group). Reportedly through this Illegal scraping of Facebook API lead to 267 million user IDs, phone
numbers, and names are expose from the Elasticsearch Cluster.
C
According to head of platform partnerships Konstantinos Papamiltiadis of Facebook, it is stated that in their investigation it is found that
100 of the partners were able to access this restricted group’s members data and out of them 11 partners accessed user data through the use of
this API in last 60 days. The organization also claims that, in their investigation they have not found any evidence of exploitation and abuse of
5SECURITY IN COMPUTING AND IT
the accessed data by those partners. In response to this incident Facebook replied that, their developers are working on the bug that made access
to the developers to this data.
In order to avoid the same kind attacks, it is important to enforce storing API security. This can be achieved by enforcement of strict
authentication and authorization permissions for the developers. The API Gateways should be able to effectively manage the authentication of
the users/developers in order to provide better service orchestration. Whenever there is issue of making the personal identifiable data or similar
kind of the critical data then it is important to place more fine-grained authorization stages while allowing the access to the data such as Group
API.
the accessed data by those partners. In response to this incident Facebook replied that, their developers are working on the bug that made access
to the developers to this data.
In order to avoid the same kind attacks, it is important to enforce storing API security. This can be achieved by enforcement of strict
authentication and authorization permissions for the developers. The API Gateways should be able to effectively manage the authentication of
the users/developers in order to provide better service orchestration. Whenever there is issue of making the personal identifiable data or similar
kind of the critical data then it is important to place more fine-grained authorization stages while allowing the access to the data such as Group
API.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY IN COMPUTING AND IT
Bibliography
Mansour, A.H., 2017. Encryption and Decryption Analysis of the RSA Digital Signature Based on MD5 and SHA Hash Functions Using Strong
Prime. Journal of Soft Computing and Decision Support Systems, 4(1), pp.7-15.
Perriam, J., Birkbak, A. and Freeman, A., 2019. Digital methods in a post-API environment. International Journal of Social Research
Methodology, pp.1-14.
Russell, N.C., Schaub, F., McDonald, A. and Sierra-Rocafort, W., 2019. APIs and Your Privacy. Available at SSRN 3328825.
Sahu, R. and Ansari, M.S., 2017. Securing messages from brute force attack by combined approach of honey encryption and
blowfish. International Journal, 4.
Siriwardena, P., 2020. Designing Security for APIs. In Advanced API Security (pp. 33-67). Apress, Berkeley, CA.
Lindsey, N. (2019). Another Facebook Privacy Breach, This One Involving Developers. [online] CPO Magazine. Available at:
https://www.cpomagazine.com/data-privacy/another-facebook-privacy-breach-this-one-involving-developers/ [Accessed 10 Feb. 2020].
Ahmed, A.M., Ahmed, S.H. and Ahmed, O.H., 2017, April. Enhancing 3D-playfair algorithm to support all the existing characters and increase
the resistanceto brute force and frequency analysis attacks. In 2017 International Conference on Current Research in Computer Science and
Information Technology (ICCIT) (pp. 81-85). IEEE.
Long, S., 2019, October. A Comparative Analysis of the Application of Hashing Encryption Algorithms for MD5, SHA-1, and SHA-512.
In Journal of Physics: Conference Series (Vol. 1314, No. 1, p. 012210). IOP Publishing.
Bibliography
Mansour, A.H., 2017. Encryption and Decryption Analysis of the RSA Digital Signature Based on MD5 and SHA Hash Functions Using Strong
Prime. Journal of Soft Computing and Decision Support Systems, 4(1), pp.7-15.
Perriam, J., Birkbak, A. and Freeman, A., 2019. Digital methods in a post-API environment. International Journal of Social Research
Methodology, pp.1-14.
Russell, N.C., Schaub, F., McDonald, A. and Sierra-Rocafort, W., 2019. APIs and Your Privacy. Available at SSRN 3328825.
Sahu, R. and Ansari, M.S., 2017. Securing messages from brute force attack by combined approach of honey encryption and
blowfish. International Journal, 4.
Siriwardena, P., 2020. Designing Security for APIs. In Advanced API Security (pp. 33-67). Apress, Berkeley, CA.
Lindsey, N. (2019). Another Facebook Privacy Breach, This One Involving Developers. [online] CPO Magazine. Available at:
https://www.cpomagazine.com/data-privacy/another-facebook-privacy-breach-this-one-involving-developers/ [Accessed 10 Feb. 2020].
Ahmed, A.M., Ahmed, S.H. and Ahmed, O.H., 2017, April. Enhancing 3D-playfair algorithm to support all the existing characters and increase
the resistanceto brute force and frequency analysis attacks. In 2017 International Conference on Current Research in Computer Science and
Information Technology (ICCIT) (pp. 81-85). IEEE.
Long, S., 2019, October. A Comparative Analysis of the Application of Hashing Encryption Algorithms for MD5, SHA-1, and SHA-512.
In Journal of Physics: Conference Series (Vol. 1314, No. 1, p. 012210). IOP Publishing.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




