Security in Computing and IT Assignment Solution - OUA SP4 2019
VerifiedAdded on 2022/08/24
|13
|2776
|33
Homework Assignment
AI Summary
This assignment solution for Security in Computing and IT (COSC2651/CPT251) addresses various aspects of information security. Task 1 explores decryption techniques for an intercepted encrypted message, including Caesar and transportation ciphers, estimating decryption times, and methods to increase or decrease decryption difficulty. Task 2 focuses on password security, discussing the risks of storing passwords in plain text, the use of hashing (SHA256), rainbow tables, and comparisons of MD5 and SHA algorithms. Task 3 analyzes a real-world data breach incident involving Elastic Search, detailing the nature of the breach, the methods used by attackers, and the potential preventative measures that could have been implemented by the affected organization to mitigate the data breach.

Running head: Security in Computing and IT
Security in Computing and IT
Name of the Student
Name of the University
Author Note
Security in Computing and IT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security in Computing and IT 1
Table of Contents
Task 1:........................................................................................................................................2
Task 2:........................................................................................................................................3
Task 3:........................................................................................................................................6
Task 4:........................................................................................................................................9
References:...............................................................................................................................11
Table of Contents
Task 1:........................................................................................................................................2
Task 2:........................................................................................................................................3
Task 3:........................................................................................................................................6
Task 4:........................................................................................................................................9
References:...............................................................................................................................11

2Security in Computing and IT
Task 1:
a)
Caesar cipher: For passing an encrypted message from one to pther person, this is the first
needed thing for both of the parties that they need to be having a key for the cipher for
encrypting the message as well as the receiver can decrypt the message. For the Caesar
cipher, the key is basically a number of characters for shifting the cipher alphabet.
Example.
Plain text: This is a secret message.
The shift: 3
Cipher text: Wklv lv d vhfuhw phvvdjh.
Transportation cipher: The decryption with the help of columnar transportation is very
much similar to the encryption. It follows a simple rule to mix up the characters the
characters of the plain text for forming the cipher text.
Example:
Let, there is a key: GERMAN
Plain text: defend the east wall of the castle
It can be written that:
G E R M A N
d e f e n d
t h e e a s
t w a l l o
f t h e c a
s t l e x x
Task 1:
a)
Caesar cipher: For passing an encrypted message from one to pther person, this is the first
needed thing for both of the parties that they need to be having a key for the cipher for
encrypting the message as well as the receiver can decrypt the message. For the Caesar
cipher, the key is basically a number of characters for shifting the cipher alphabet.
Example.
Plain text: This is a secret message.
The shift: 3
Cipher text: Wklv lv d vhfuhw phvvdjh.
Transportation cipher: The decryption with the help of columnar transportation is very
much similar to the encryption. It follows a simple rule to mix up the characters the
characters of the plain text for forming the cipher text.
Example:
Let, there is a key: GERMAN
Plain text: defend the east wall of the castle
It can be written that:
G E R M A N
d e f e n d
t h e e a s
t w a l l o
f t h e c a
s t l e x x
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3Security in Computing and IT
Encryption: For encryption the columns need to be reordered alphabetically. Such that:
A E G M N R
n e d e d f
a h t e s e
l w t l o a
c t f e a h
x t s e x l
Cipher text is: nalcx ehwtt dttfs eelee dsoax feahl.
b)
For several scenarios the decryption time can more than 48 hours such as for AES decryption.
However for high end systems the time can be less such as for columner transposition the
time for decryption can be less than 60 seconds.
c)
For making the decryption process harder the user can use two combined cryptographic
methods. As that will be kind of two locks in a door but with different protocols. By
implementing two different algorithm combinely the encryption will be more strong and it
will make the decryption process harder.
d)
By understanding about the algorithms and decryption techniques properly, the process of
decryption will be faster. The most important thing for decryption is the key. If, the user will
be unaware about the keys, then there will be difficulties in decryption. However, after
known proper keys and technique the user will be able to decrypt the cipher text successfully.
Task 2:
The student ID is: 3833235
Encryption: For encryption the columns need to be reordered alphabetically. Such that:
A E G M N R
n e d e d f
a h t e s e
l w t l o a
c t f e a h
x t s e x l
Cipher text is: nalcx ehwtt dttfs eelee dsoax feahl.
b)
For several scenarios the decryption time can more than 48 hours such as for AES decryption.
However for high end systems the time can be less such as for columner transposition the
time for decryption can be less than 60 seconds.
c)
For making the decryption process harder the user can use two combined cryptographic
methods. As that will be kind of two locks in a door but with different protocols. By
implementing two different algorithm combinely the encryption will be more strong and it
will make the decryption process harder.
d)
By understanding about the algorithms and decryption techniques properly, the process of
decryption will be faster. The most important thing for decryption is the key. If, the user will
be unaware about the keys, then there will be difficulties in decryption. However, after
known proper keys and technique the user will be able to decrypt the cipher text successfully.
Task 2:
The student ID is: 3833235
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4Security in Computing and IT
SHA256 hash: fa2e4977325f3ddc7eafe8f0dc029b6c656457180d2e9635cbe1f8cf6de647d1
a)
This is bad practice to store the password in the form of plain text that s existed in the
database because anyone who has access to the database can easily read all the passwords of
the users without any problem. The password which is stored in the form of plain text then it
is a risk for the organization as well as the users. Suppose a hacker gains access to the
database then the hacker misuse the password of the user account, which is the big problem
for the organization and the users. Companies like Google, Github, Facebook and other
companies currently storing the
password in the plain text in the database.
b)
Hashing is used to protect the data against tempering. Hashing create different values from
the text and string by using a function to protect the plain text from the unusual access.
Hashing can be used to prevent the above problem because it is used to convert plain text and
string by using some mathematical function which generates values that can be used to store
the data in the database. It can be an also helpful method to sort the key values from the
database more efficiently because it is used to index the data of the database which helps to
increase the speed of data retrieval from the database.
c)
The rainbow table is basically a precomputed table that is used to revise the cryptographic
hash functions, basically for cracking the password hashes. The rainbow tables are effective
and fast for cracking passwords as each of the passwords is hashed to the similar way.
SHA256 hash: fa2e4977325f3ddc7eafe8f0dc029b6c656457180d2e9635cbe1f8cf6de647d1
a)
This is bad practice to store the password in the form of plain text that s existed in the
database because anyone who has access to the database can easily read all the passwords of
the users without any problem. The password which is stored in the form of plain text then it
is a risk for the organization as well as the users. Suppose a hacker gains access to the
database then the hacker misuse the password of the user account, which is the big problem
for the organization and the users. Companies like Google, Github, Facebook and other
companies currently storing the
password in the plain text in the database.
b)
Hashing is used to protect the data against tempering. Hashing create different values from
the text and string by using a function to protect the plain text from the unusual access.
Hashing can be used to prevent the above problem because it is used to convert plain text and
string by using some mathematical function which generates values that can be used to store
the data in the database. It can be an also helpful method to sort the key values from the
database more efficiently because it is used to index the data of the database which helps to
increase the speed of data retrieval from the database.
c)
The rainbow table is basically a precomputed table that is used to revise the cryptographic
hash functions, basically for cracking the password hashes. The rainbow tables are effective
and fast for cracking passwords as each of the passwords is hashed to the similar way.
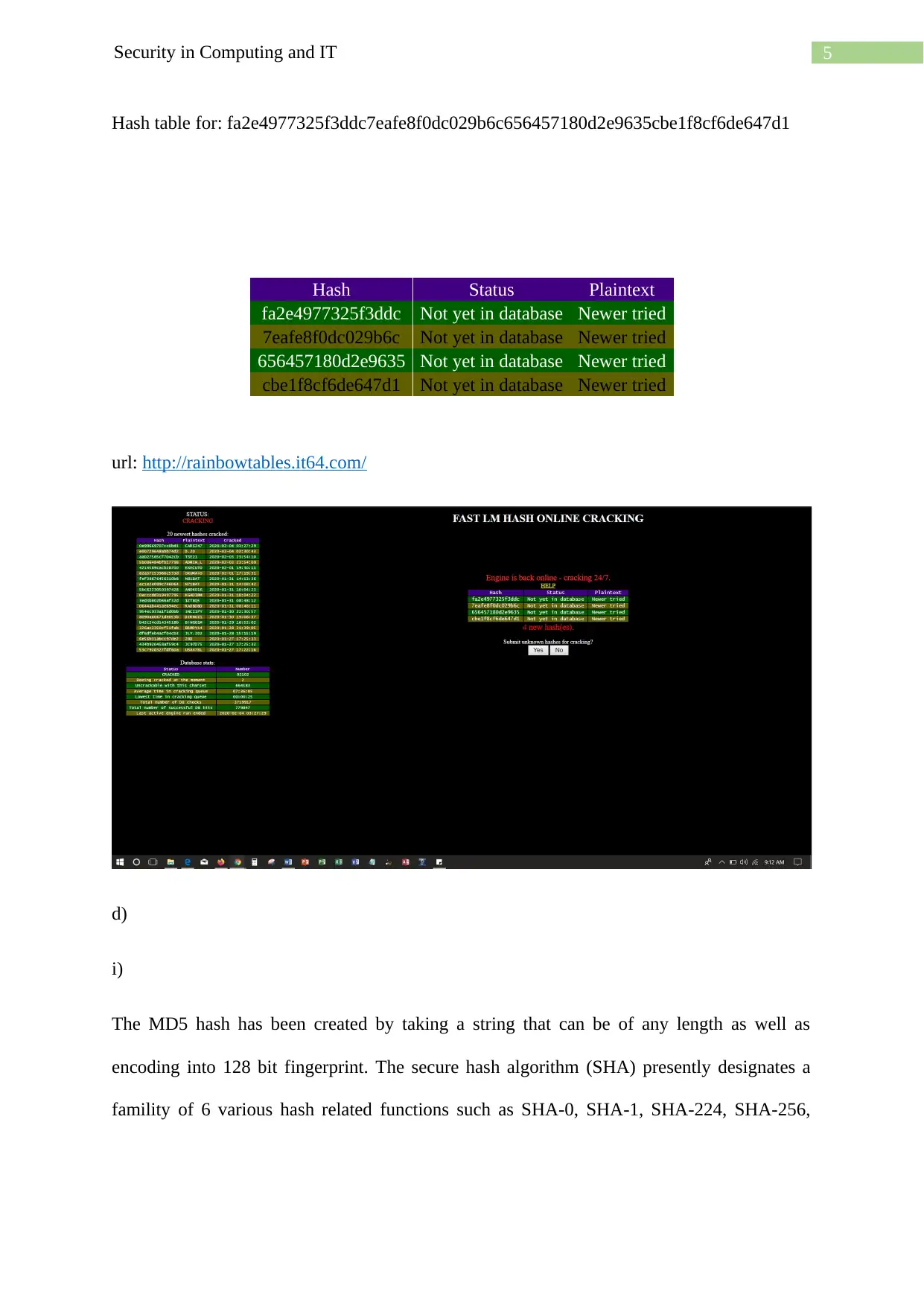
5Security in Computing and IT
Hash table for: fa2e4977325f3ddc7eafe8f0dc029b6c656457180d2e9635cbe1f8cf6de647d1
Hash Status Plaintext
fa2e4977325f3ddc Not yet in database Newer tried
7eafe8f0dc029b6c Not yet in database Newer tried
656457180d2e9635 Not yet in database Newer tried
cbe1f8cf6de647d1 Not yet in database Newer tried
url: http://rainbowtables.it64.com/
d)
i)
The MD5 hash has been created by taking a string that can be of any length as well as
encoding into 128 bit fingerprint. The secure hash algorithm (SHA) presently designates a
famility of 6 various hash related functions such as SHA-0, SHA-1, SHA-224, SHA-256,
Hash table for: fa2e4977325f3ddc7eafe8f0dc029b6c656457180d2e9635cbe1f8cf6de647d1
Hash Status Plaintext
fa2e4977325f3ddc Not yet in database Newer tried
7eafe8f0dc029b6c Not yet in database Newer tried
656457180d2e9635 Not yet in database Newer tried
cbe1f8cf6de647d1 Not yet in database Newer tried
url: http://rainbowtables.it64.com/
d)
i)
The MD5 hash has been created by taking a string that can be of any length as well as
encoding into 128 bit fingerprint. The secure hash algorithm (SHA) presently designates a
famility of 6 various hash related functions such as SHA-0, SHA-1, SHA-224, SHA-256,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6Security in Computing and IT
SHA-384, and SHA-512 which was published by the American National Institute of
Standards and Technology (NIST).
ii)
The secure hash algorithm (SHA) is having 6 various hash related functions such as SHA-0,
SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512 which was published by the American
National Institute of Standards and Technology (NIST). SHA-0, SHA-1, SHA-2, SHA-3 are
4 different versions of the algorithm. It can be said that SHA-1 is the successor SHA-0 and so
on. On the other side, MD5 message digest algorithm I used widely hash function for
producing a 128 bit hash value.
iii)
Yes, they are suitable for the database problem above as the MD5 hash has been created by
taking a string that can be of any length as well as encoding into 128 bit fingerprint and the
SHA algorithm can also be useful for the scenario.
Task 3:
a)
In January in the year 2019, ZDnet reported that an online group of casino leaked
information on more than 108 million bets that consisted of details about the personal
information, withdrawals and deposits of the customers. The data got leaked from a Server of
Elastic Search that was left uncovered and without a password (Solomon 2019). The Elastic
Search is a search engine that has various features like it is portable and is of very high grade
and the various organizations install it in order to improve the data indexing of web
SHA-384, and SHA-512 which was published by the American National Institute of
Standards and Technology (NIST).
ii)
The secure hash algorithm (SHA) is having 6 various hash related functions such as SHA-0,
SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512 which was published by the American
National Institute of Standards and Technology (NIST). SHA-0, SHA-1, SHA-2, SHA-3 are
4 different versions of the algorithm. It can be said that SHA-1 is the successor SHA-0 and so
on. On the other side, MD5 message digest algorithm I used widely hash function for
producing a 128 bit hash value.
iii)
Yes, they are suitable for the database problem above as the MD5 hash has been created by
taking a string that can be of any length as well as encoding into 128 bit fingerprint and the
SHA algorithm can also be useful for the scenario.
Task 3:
a)
In January in the year 2019, ZDnet reported that an online group of casino leaked
information on more than 108 million bets that consisted of details about the personal
information, withdrawals and deposits of the customers. The data got leaked from a Server of
Elastic Search that was left uncovered and without a password (Solomon 2019). The Elastic
Search is a search engine that has various features like it is portable and is of very high grade
and the various organizations install it in order to improve the data indexing of web
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Security in Computing and IT
applications and abilities of search. Justin Paine, who was the security researcher found out
the server and he also found out that the data of the user consisted of a lot of information
those were sensitive, such as addresses, real names, phone numbers, email addresses, and
many more personal information. ZDnet also reported that they were not sure about the time
the server was left exposed and the number of user who were affected, if anyone else
accessed the server and if the customers got notifications that their personal information was
accessed or exposed. The researchers said that Elastic Search Server, which is a technology
that is utilised in order to power the functions of search and it, was leaking about 73 GB data
and it was also seen that various databases were cached in the memory of the server. Inside
the database, the researcher found about 5 million records that include personal data of the
citizens of US (Gudivada, Ramaswamy and Srinivasan 2018). The Elastic Search server also
had a database that was cached which was named yellow pages and it consisted of additional
2 million records and it was found out to be business entries. These records consisted of more
information. The researcher reported to the ZDnet that he was not able to recognise the owner
of the server but based on the information he believed that the data belonged to the Canadian
Data Firm.
b)
The Elastic Search is a search engine that has various functionalities like portability
and it is of high grade. In order to exploit the search engine, password breaking was used. A
group of hackers cracked the password of the search engine and it was left exposed for many
hours. This was dangerous because it consisted of personal information of the clients and that
included the ban account details and withdrawals of the customers (Delgado 2018). A group
of hackers initiated the infiltration of the search engine. They cracked the password of Elastic
Search that included personal information of various customers and it was highly risky. It
also consisted on a database that had information of the business entities. Their motivation
applications and abilities of search. Justin Paine, who was the security researcher found out
the server and he also found out that the data of the user consisted of a lot of information
those were sensitive, such as addresses, real names, phone numbers, email addresses, and
many more personal information. ZDnet also reported that they were not sure about the time
the server was left exposed and the number of user who were affected, if anyone else
accessed the server and if the customers got notifications that their personal information was
accessed or exposed. The researchers said that Elastic Search Server, which is a technology
that is utilised in order to power the functions of search and it, was leaking about 73 GB data
and it was also seen that various databases were cached in the memory of the server. Inside
the database, the researcher found about 5 million records that include personal data of the
citizens of US (Gudivada, Ramaswamy and Srinivasan 2018). The Elastic Search server also
had a database that was cached which was named yellow pages and it consisted of additional
2 million records and it was found out to be business entries. These records consisted of more
information. The researcher reported to the ZDnet that he was not able to recognise the owner
of the server but based on the information he believed that the data belonged to the Canadian
Data Firm.
b)
The Elastic Search is a search engine that has various functionalities like portability
and it is of high grade. In order to exploit the search engine, password breaking was used. A
group of hackers cracked the password of the search engine and it was left exposed for many
hours. This was dangerous because it consisted of personal information of the clients and that
included the ban account details and withdrawals of the customers (Delgado 2018). A group
of hackers initiated the infiltration of the search engine. They cracked the password of Elastic
Search that included personal information of various customers and it was highly risky. It
also consisted on a database that had information of the business entities. Their motivation

8Security in Computing and IT
was to hack Elastic Search and to take all the information that was contained in the Elastic
Search. It consisted of about 50 million entries and the other database consisted of about 2o
million records. These records consisted of mainly personal information like first name, last
name, residential address, email address, state, IP address, phone number and many more.
No, the hackers were not recognised and they were not caught (Khan et al 2019). The
researcher of the security breach could not recognise the hackers and they didn’t even know
whether the customers know that their account was hacked. It was a massive data breach and
millions of data was breached from Elastic Search.
c)
The good news was that the server was taken down eventually. The precise date when
the server was protected is not known and it was closed after the data breach was discovered
by the researcher. The researcher of security has given a copy of the data that was leaked.
This was not the first time that Elastic Search has exposed the records of the customers and
the personal information of the Organization (Chatterjee et al 2019). In January there were
two companies named FitMetrix and Industries of Sao Paulo has suffered these kinds of data
breach. The cause of these data breach is that the administrators of the servers do not set up
strong passwords for the servers and after that they are left uncovered on the internet. In the
internet everyone can see the data and download the data that is cached inside it.
The company could have set strong passwords for the Elastic Search servers so that the
hackers do not enter the servers and then access the sensitive information about the company
and the customers and the employees those are related to the company. The organization
should have proper firewalls in its systems so that the hackers do not enter the systems
through the network. The hackers sometimes enter the system and the network through the
advertisement (Koch and Adeleye 2019). The organization should have appropriate adware
was to hack Elastic Search and to take all the information that was contained in the Elastic
Search. It consisted of about 50 million entries and the other database consisted of about 2o
million records. These records consisted of mainly personal information like first name, last
name, residential address, email address, state, IP address, phone number and many more.
No, the hackers were not recognised and they were not caught (Khan et al 2019). The
researcher of the security breach could not recognise the hackers and they didn’t even know
whether the customers know that their account was hacked. It was a massive data breach and
millions of data was breached from Elastic Search.
c)
The good news was that the server was taken down eventually. The precise date when
the server was protected is not known and it was closed after the data breach was discovered
by the researcher. The researcher of security has given a copy of the data that was leaked.
This was not the first time that Elastic Search has exposed the records of the customers and
the personal information of the Organization (Chatterjee et al 2019). In January there were
two companies named FitMetrix and Industries of Sao Paulo has suffered these kinds of data
breach. The cause of these data breach is that the administrators of the servers do not set up
strong passwords for the servers and after that they are left uncovered on the internet. In the
internet everyone can see the data and download the data that is cached inside it.
The company could have set strong passwords for the Elastic Search servers so that the
hackers do not enter the servers and then access the sensitive information about the company
and the customers and the employees those are related to the company. The organization
should have proper firewalls in its systems so that the hackers do not enter the systems
through the network. The hackers sometimes enter the system and the network through the
advertisement (Koch and Adeleye 2019). The organization should have appropriate adware
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9Security in Computing and IT
installed in the systems so that the hackers do not enter the system through the
advertisements.
There are various types’ approaches that could have been used by the employees of
the company so as for minimizing the impact of data breach in the organization. About 50
million data of the customer were leaked from the servers of the Elastic Search and about 20
million records of business entries were leaked from Elastic Search (Cheng, Liu and Yao
2017). The organization should follow several approaches so that data breach does not occur
in the organization. The organization should keep the backup of the data that are sensitive and
the data of the customers. The organization should train the employees of the organization
about the data breaches so that when data breaches occur they can lessen the impact of the
data breach on the organization. The organization must keep the system secure from with the
help of antivirus, anti malware; anti ransomware and firewalls so that the hackers cannot
enter the system through the network and they cannot install ransomware or malware inside
the system. The software of security must be kept up to date by the organization so that if any
emergency occurs then the upgraded software will minimize the impact of data breach or any
attack from the hackers (Karyda and Mitrou 2016). These methods will help the organization
to minimize the impact of data breach in the organization and also the safety measures will
lessen the attacks of hackers in the organization so that the sensitive information do not get
accessed and the customer data do not get leaked as it will be of great harm to the
organization.
Task 4:
3833235 mod 3 = 0.
Question 4.0:
installed in the systems so that the hackers do not enter the system through the
advertisements.
There are various types’ approaches that could have been used by the employees of
the company so as for minimizing the impact of data breach in the organization. About 50
million data of the customer were leaked from the servers of the Elastic Search and about 20
million records of business entries were leaked from Elastic Search (Cheng, Liu and Yao
2017). The organization should follow several approaches so that data breach does not occur
in the organization. The organization should keep the backup of the data that are sensitive and
the data of the customers. The organization should train the employees of the organization
about the data breaches so that when data breaches occur they can lessen the impact of the
data breach on the organization. The organization must keep the system secure from with the
help of antivirus, anti malware; anti ransomware and firewalls so that the hackers cannot
enter the system through the network and they cannot install ransomware or malware inside
the system. The software of security must be kept up to date by the organization so that if any
emergency occurs then the upgraded software will minimize the impact of data breach or any
attack from the hackers (Karyda and Mitrou 2016). These methods will help the organization
to minimize the impact of data breach in the organization and also the safety measures will
lessen the attacks of hackers in the organization so that the sensitive information do not get
accessed and the customer data do not get leaked as it will be of great harm to the
organization.
Task 4:
3833235 mod 3 = 0.
Question 4.0:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10Security in Computing and IT
Packet filter: This works in the network layer of the OSI model. It can apply the set of rules
on every packets as well as on the basis of the outcome, it will decide about forwarding or
discarding the packet. Threats: spyware, ransomware, CPU/resource stealing.
X.509 certificates: The X.509 certificates is basically a digital certificate which utilizes the
widely accepted international X.509 public key infrastructure (PKI) for verifying that the
public key is belonging to the computer, user or to the service for identifying contained
within the certificate. Threats: poisoned search results, person in the middle attack.
Sandboxing: The sandboxing is basically strategy of software management which isolates
the applications from the critical resources of system and other kind of programs. This offers
extra layers of security which prevents harmful apps and malware from negative affect to the
system.
Threats: phishing, person in the middle attack.
Encryption: The encryption is the procedure to encode an information or message in such a
way that the authorised user only will be able to access the information or message. Without
proper authorisation the users will not be able to access the information. Threats: key loggers,
clickjacking, phishing, password cracking.
Packet filter: This works in the network layer of the OSI model. It can apply the set of rules
on every packets as well as on the basis of the outcome, it will decide about forwarding or
discarding the packet. Threats: spyware, ransomware, CPU/resource stealing.
X.509 certificates: The X.509 certificates is basically a digital certificate which utilizes the
widely accepted international X.509 public key infrastructure (PKI) for verifying that the
public key is belonging to the computer, user or to the service for identifying contained
within the certificate. Threats: poisoned search results, person in the middle attack.
Sandboxing: The sandboxing is basically strategy of software management which isolates
the applications from the critical resources of system and other kind of programs. This offers
extra layers of security which prevents harmful apps and malware from negative affect to the
system.
Threats: phishing, person in the middle attack.
Encryption: The encryption is the procedure to encode an information or message in such a
way that the authorised user only will be able to access the information or message. Without
proper authorisation the users will not be able to access the information. Threats: key loggers,
clickjacking, phishing, password cracking.

11Security in Computing and IT
References:
Chatterjee, S., Gao, X., Sarkar, S. and Uzmanoglu, C., 2019. Reacting to the scope of a data
breach: The differential role of fear and anger. Journal of Business Research, 101, pp.183-
193.
Cheng, L., Liu, F. and Yao, D., 2017. Enterprise data breach: causes, challenges, prevention,
and future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5), p.e1211.
Delgado, P., 2018. Developing an Adaptive Threat Hunting Solution: The Elasticsearch
Stack (Doctoral dissertation).
Gudivada, V.N., Ramaswamy, S. and Srinivasan, S., 2018. Data Management Issues in
Cyber-Physical Systems. In Transportation Cyber-Physical Systems (pp. 173-200). Elsevier.
Kaplan, D., Powell, J. and Woller, T., 2016. AMD memory encryption. White paper.
Karyda, M. and Mitrou, L., 2016. Data Breach Notification: Issues and Challenges for
Security Management. In MCIS (p. 60).
Khan, F.S., Kim, J.H., Moore, R.L. and Mathiassen, L., 2019. Data Breach Risks and
Resolutions: A Literature Synthesis.
Koch, H. and Adeleye, N., 2019. Psychological Injury, Cyber Crime and Data Breach
Damages. The Expert Witness Journal, (26), pp.53-55.
Solomon, F.I., 2019, February. Securing Websites & Webapplications Using Data Analytics.
In 2019 International Conference on Computational Intelligence in Data Science
(ICCIDS) (pp. 1-4). IEEE.
References:
Chatterjee, S., Gao, X., Sarkar, S. and Uzmanoglu, C., 2019. Reacting to the scope of a data
breach: The differential role of fear and anger. Journal of Business Research, 101, pp.183-
193.
Cheng, L., Liu, F. and Yao, D., 2017. Enterprise data breach: causes, challenges, prevention,
and future directions. Wiley Interdisciplinary Reviews: Data Mining and Knowledge
Discovery, 7(5), p.e1211.
Delgado, P., 2018. Developing an Adaptive Threat Hunting Solution: The Elasticsearch
Stack (Doctoral dissertation).
Gudivada, V.N., Ramaswamy, S. and Srinivasan, S., 2018. Data Management Issues in
Cyber-Physical Systems. In Transportation Cyber-Physical Systems (pp. 173-200). Elsevier.
Kaplan, D., Powell, J. and Woller, T., 2016. AMD memory encryption. White paper.
Karyda, M. and Mitrou, L., 2016. Data Breach Notification: Issues and Challenges for
Security Management. In MCIS (p. 60).
Khan, F.S., Kim, J.H., Moore, R.L. and Mathiassen, L., 2019. Data Breach Risks and
Resolutions: A Literature Synthesis.
Koch, H. and Adeleye, N., 2019. Psychological Injury, Cyber Crime and Data Breach
Damages. The Expert Witness Journal, (26), pp.53-55.
Solomon, F.I., 2019, February. Securing Websites & Webapplications Using Data Analytics.
In 2019 International Conference on Computational Intelligence in Data Science
(ICCIDS) (pp. 1-4). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





