Security Consultation Report and Guidelines for SCU Information System
VerifiedAdded on 2022/08/17
|20
|3793
|9
Report
AI Summary
This report provides a security consultation for Southern Cross University (SCU), addressing key aspects of information system security. It begins with a BYOD (Bring Your Own Device) risk assessment, identifying critical components of the university's information system, including corporate financial data, human information, and proprietary software. The assessment includes defining risk appetite, identifying threats and vulnerabilities, and conducting both qualitative and quantitative risk assessments. The report then delves into certificate-based authentication, comparing its working principles to password-based authentication. Finally, the report concludes with anti-spam guidelines, defining spam characteristics, providing examples, and offering instructions for both users and IT administrators. The report aims to enhance SCU's overall security posture by providing a comprehensive framework for managing risks and implementing effective security measures.

Running head: SECURITY CONSULTATION REPORT AND GUIDELINE
Security Consultation Report and Guideline
Name of the Student
Name of the University
Author note
Security Consultation Report and Guideline
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY CONSULTATION REPORT AND GUIDELINE
Table of Contents
1. Introduction..................................................................................................................................3
Task 1: BYOD Risk Assessment.....................................................................................................3
1.1 Critical Components for the University Information System................................................3
1.2 BYOD Risk Assessment Introduction...................................................................................4
1.3 Objective/Purpose of BYOD Risk Assessment.....................................................................4
1.4 Scope of Risk Assessment.....................................................................................................5
1.5 Define risk appetite................................................................................................................5
1.6 Threats and Vulnerabilities identification and TVA.............................................................5
1.7 Risk Assessment (Qualitative/quantitative)...........................................................................8
Task 2: Certificate-Based Authentication........................................................................................8
2.1 Introduction............................................................................................................................8
2.2 Working principle of Password-based authentication scheme..............................................9
2.3 Certificate-based authentication scheme.............................................................................11
2.4 Working principle of Certificate-based authentication scheme...........................................11
2.5 Comparison of the password-based and certificate–based Authentication.........................13
2.6 Conclusion...........................................................................................................................13
Task 3: Anti-spam Guideline.........................................................................................................14
3.1 Definition and characteristics of Spam................................................................................14
3.2 Representative Examples of Spam......................................................................................14
Table of Contents
1. Introduction..................................................................................................................................3
Task 1: BYOD Risk Assessment.....................................................................................................3
1.1 Critical Components for the University Information System................................................3
1.2 BYOD Risk Assessment Introduction...................................................................................4
1.3 Objective/Purpose of BYOD Risk Assessment.....................................................................4
1.4 Scope of Risk Assessment.....................................................................................................5
1.5 Define risk appetite................................................................................................................5
1.6 Threats and Vulnerabilities identification and TVA.............................................................5
1.7 Risk Assessment (Qualitative/quantitative)...........................................................................8
Task 2: Certificate-Based Authentication........................................................................................8
2.1 Introduction............................................................................................................................8
2.2 Working principle of Password-based authentication scheme..............................................9
2.3 Certificate-based authentication scheme.............................................................................11
2.4 Working principle of Certificate-based authentication scheme...........................................11
2.5 Comparison of the password-based and certificate–based Authentication.........................13
2.6 Conclusion...........................................................................................................................13
Task 3: Anti-spam Guideline.........................................................................................................14
3.1 Definition and characteristics of Spam................................................................................14
3.2 Representative Examples of Spam......................................................................................14

2SECURITY CONSULTATION REPORT AND GUIDELINE
3.3 Instructions for Spam Handling (users)...............................................................................15
3.4 Instructions for Spam Handling (IT admin)........................................................................15
4. Conclusion.................................................................................................................................16
References......................................................................................................................................17
3.3 Instructions for Spam Handling (users)...............................................................................15
3.4 Instructions for Spam Handling (IT admin)........................................................................15
4. Conclusion.................................................................................................................................16
References......................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY CONSULTATION REPORT AND GUIDELINE
1. Introduction
The discussion is based on understanding the various aspects in relation to the
understanding over the implementation procedure of the BYOD policy that would be
implemented in Southern Cross University. In the present situation, the discussion is focused
over the emerging and contemporary threats that are being rising within the university due to low
forms of security strategies. Different situations of threats include the risk of data breaches from
the university database system. A proper lack of policy would be considered as negative towards
the implementation of proper measures taken for implementing better security of the embedded
systems (Ortbach, Walter and Öksüz 2015). Attacks from spam also affects the reputation of the
university and leads towards disastrous impacts.
The following parts of the discussion would be focused over the assessment of risks with
the process of implementation of BYOD policy for the information system (IS) for SCU. The
guidelines would be based on assessment of risks that would have affected the IS maintained for
the university. The next part of the discussion would be based on a report focusing on the
assessment of risks and recommending towards the implementation of a Certificate-based
Authentication system. The concluding part of the discussion would be focused on a guideline
discussing the Spam Act 2003 and further would include situations of spam and instructions
based on minimizing the spam threats.
Task 1: BYOD Risk Assessment
1.1 Critical Components for the University Information System
The assets of the university information system includes:
1. Introduction
The discussion is based on understanding the various aspects in relation to the
understanding over the implementation procedure of the BYOD policy that would be
implemented in Southern Cross University. In the present situation, the discussion is focused
over the emerging and contemporary threats that are being rising within the university due to low
forms of security strategies. Different situations of threats include the risk of data breaches from
the university database system. A proper lack of policy would be considered as negative towards
the implementation of proper measures taken for implementing better security of the embedded
systems (Ortbach, Walter and Öksüz 2015). Attacks from spam also affects the reputation of the
university and leads towards disastrous impacts.
The following parts of the discussion would be focused over the assessment of risks with
the process of implementation of BYOD policy for the information system (IS) for SCU. The
guidelines would be based on assessment of risks that would have affected the IS maintained for
the university. The next part of the discussion would be based on a report focusing on the
assessment of risks and recommending towards the implementation of a Certificate-based
Authentication system. The concluding part of the discussion would be focused on a guideline
discussing the Spam Act 2003 and further would include situations of spam and instructions
based on minimizing the spam threats.
Task 1: BYOD Risk Assessment
1.1 Critical Components for the University Information System
The assets of the university information system includes:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY CONSULTATION REPORT AND GUIDELINE
1. Corporate Financial Data – The financial data of the university is considered to be
highly critical in nature and thus it helps in determining several statistics based on determining
the business growth of the university. It also helps in determining the statistical pattern for the
number of students, performance metrics and others.
2. Human Information – This would include the detailed records of students, teachers
and other employees working within the university (AlHogail 2015). These are considered as
major critical assets of the university and hence they would need to be secured.
3. Proprietary Software – The university would have a dedicated and proprietary
software that would maintain the records of each employee and students while performing other
functions.
1.2 BYOD Risk Assessment Introduction
BYOD is defined as the collaboration of concepts, technologies and policies that would
be set for employees based on which they would be able to access their different IT resources.
With the proliferation of the IT impact on university, the introduction of BYOD policy is widely
considered (Tanimoto et al. 2016). The discussion in this paper would discuss over the risk
assessment process based on BYOD. It would also evaluate the risk management method.
1.3 Objective/Purpose of BYOD Risk Assessment
The purpose of performing the BYOD Risk Assessment is based on understanding the
various areas of risks and determining appropriate strategies focusing over mitigating them for
the benefit for the university.
1. Corporate Financial Data – The financial data of the university is considered to be
highly critical in nature and thus it helps in determining several statistics based on determining
the business growth of the university. It also helps in determining the statistical pattern for the
number of students, performance metrics and others.
2. Human Information – This would include the detailed records of students, teachers
and other employees working within the university (AlHogail 2015). These are considered as
major critical assets of the university and hence they would need to be secured.
3. Proprietary Software – The university would have a dedicated and proprietary
software that would maintain the records of each employee and students while performing other
functions.
1.2 BYOD Risk Assessment Introduction
BYOD is defined as the collaboration of concepts, technologies and policies that would
be set for employees based on which they would be able to access their different IT resources.
With the proliferation of the IT impact on university, the introduction of BYOD policy is widely
considered (Tanimoto et al. 2016). The discussion in this paper would discuss over the risk
assessment process based on BYOD. It would also evaluate the risk management method.
1.3 Objective/Purpose of BYOD Risk Assessment
The purpose of performing the BYOD Risk Assessment is based on understanding the
various areas of risks and determining appropriate strategies focusing over mitigating them for
the benefit for the university.
5SECURITY CONSULTATION REPORT AND GUIDELINE
1.4 Scope of Risk Assessment
The scope of the process for risk assessment is based on discussing over the most
appropriate process for determining the areas from which risks can approach towards the project.
The scope also includes the ways in which the risks could be mitigated and the most probable
ways in which the risks could be mitigated from the plan of the project.
1.5 Define risk appetite
Risk appetite can be defined as certain risks levels that could be tolerated at SCU and
thus the university should be prepared for accepting them through which they would be able to
meet to their objectives. The risk appetite also represents a certain balance that is maintained
between the several benefits based on innovation and their related threats, which would
inevitably change.
1.6 Threats and Vulnerabilities identification and TVA
2. Public Exposure – There might be a susceptibility to eavesdropping and man-in-the-
middle attacks posed at public hotspot points that might be operated by remote networking
workers.
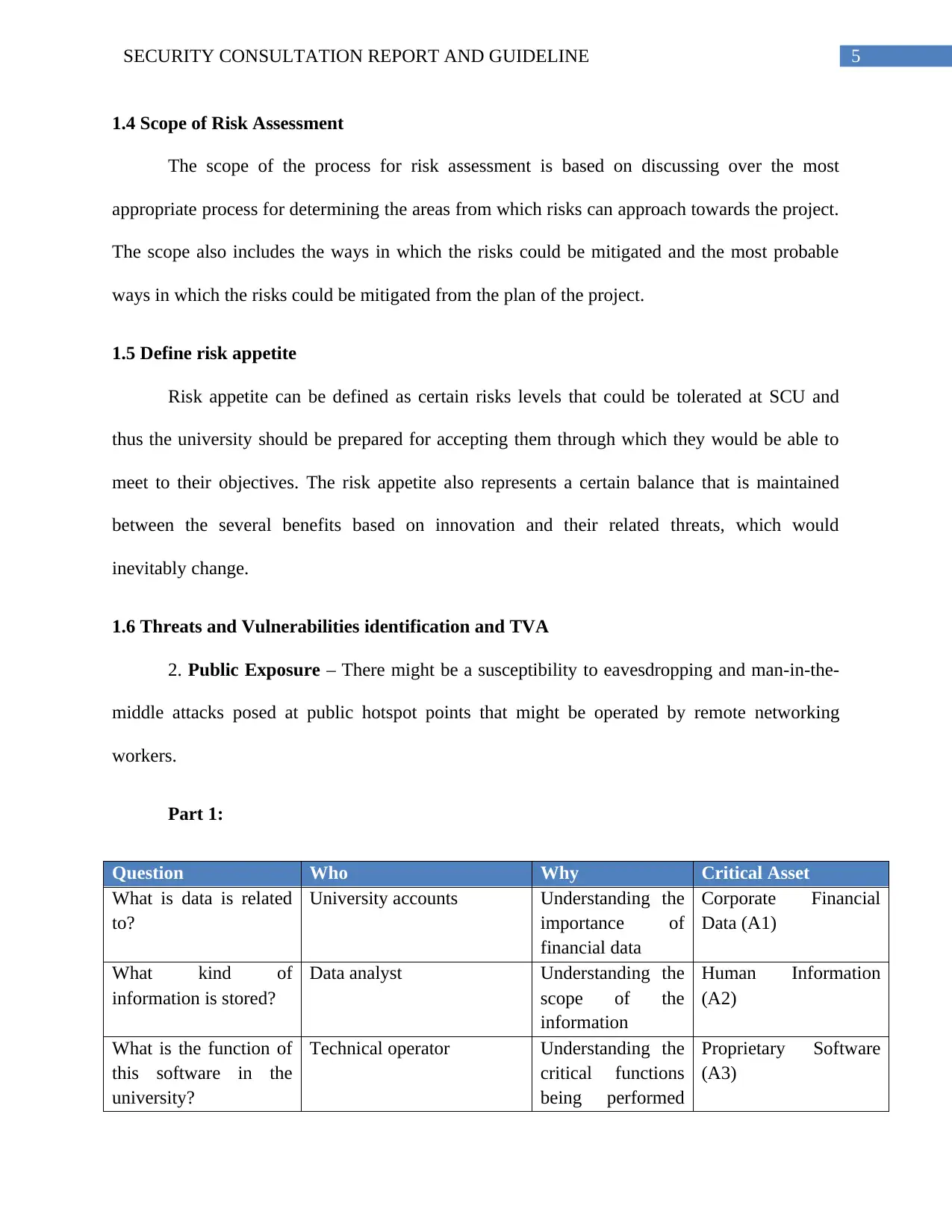
Part 1:
Question Who Why Critical Asset
What is data is related
to?
University accounts Understanding the
importance of
financial data
Corporate Financial
Data (A1)
What kind of
information is stored?
Data analyst Understanding the
scope of the
information
Human Information
(A2)
What is the function of
this software in the
university?
Technical operator Understanding the
critical functions
being performed
Proprietary Software
(A3)
1.4 Scope of Risk Assessment
The scope of the process for risk assessment is based on discussing over the most
appropriate process for determining the areas from which risks can approach towards the project.
The scope also includes the ways in which the risks could be mitigated and the most probable
ways in which the risks could be mitigated from the plan of the project.
1.5 Define risk appetite
Risk appetite can be defined as certain risks levels that could be tolerated at SCU and
thus the university should be prepared for accepting them through which they would be able to
meet to their objectives. The risk appetite also represents a certain balance that is maintained
between the several benefits based on innovation and their related threats, which would
inevitably change.
1.6 Threats and Vulnerabilities identification and TVA
2. Public Exposure – There might be a susceptibility to eavesdropping and man-in-the-
middle attacks posed at public hotspot points that might be operated by remote networking
workers.
Part 1:
Question Who Why Critical Asset
What is data is related
to?
University accounts Understanding the
importance of
financial data
Corporate Financial
Data (A1)
What kind of
information is stored?
Data analyst Understanding the
scope of the
information
Human Information
(A2)
What is the function of
this software in the
university?
Technical operator Understanding the
critical functions
being performed
Proprietary Software
(A3)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SECURITY CONSULTATION REPORT AND GUIDELINE
by the software
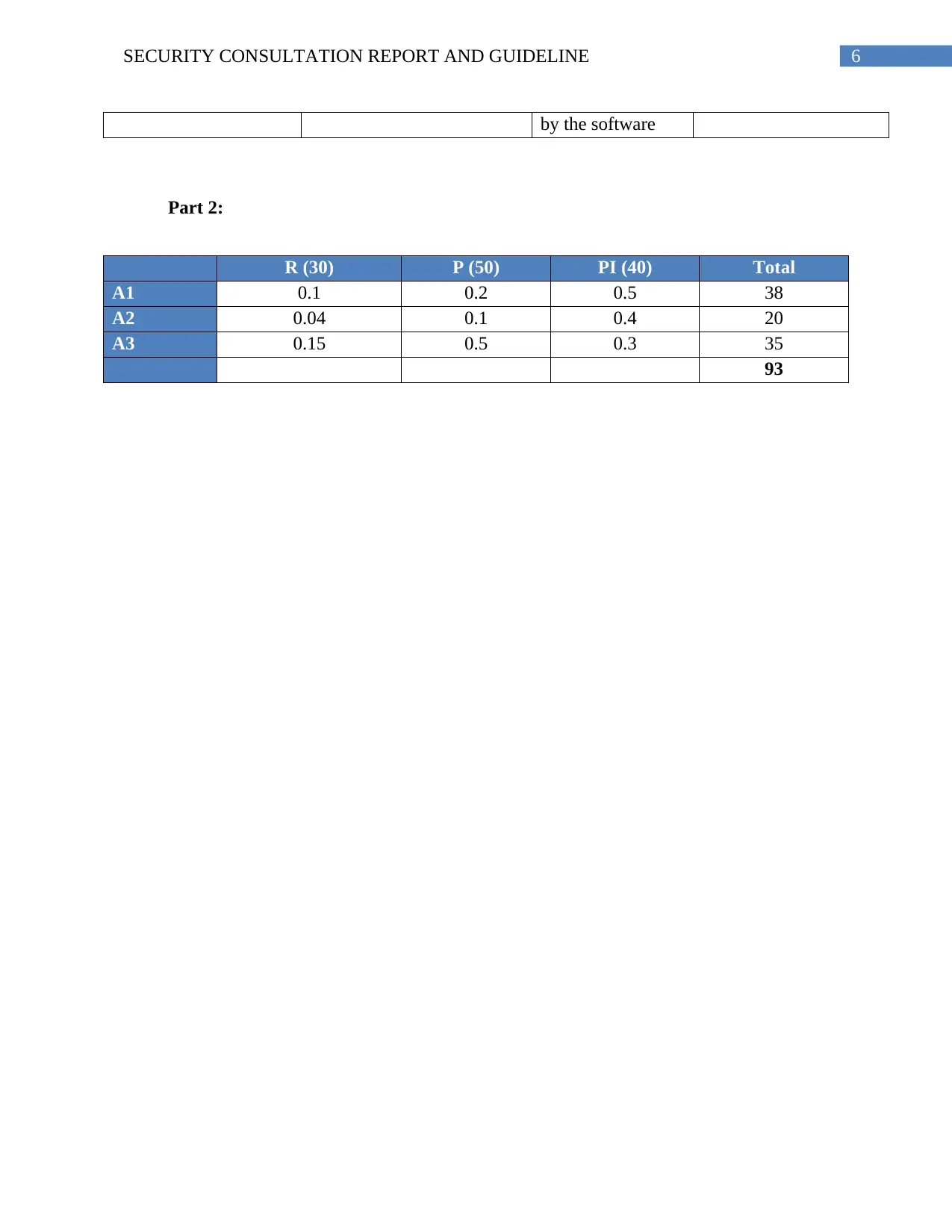
Part 2:
R (30) P (50) PI (40) Total
A1 0.1 0.2 0.5 38
A2 0.04 0.1 0.4 20
A3 0.15 0.5 0.3 35
93
by the software
Part 2:
R (30) P (50) PI (40) Total
A1 0.1 0.2 0.5 38
A2 0.04 0.1 0.4 20
A3 0.15 0.5 0.3 35
93
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SECURITY CONSULTATION REPORT AND GUIDELINE
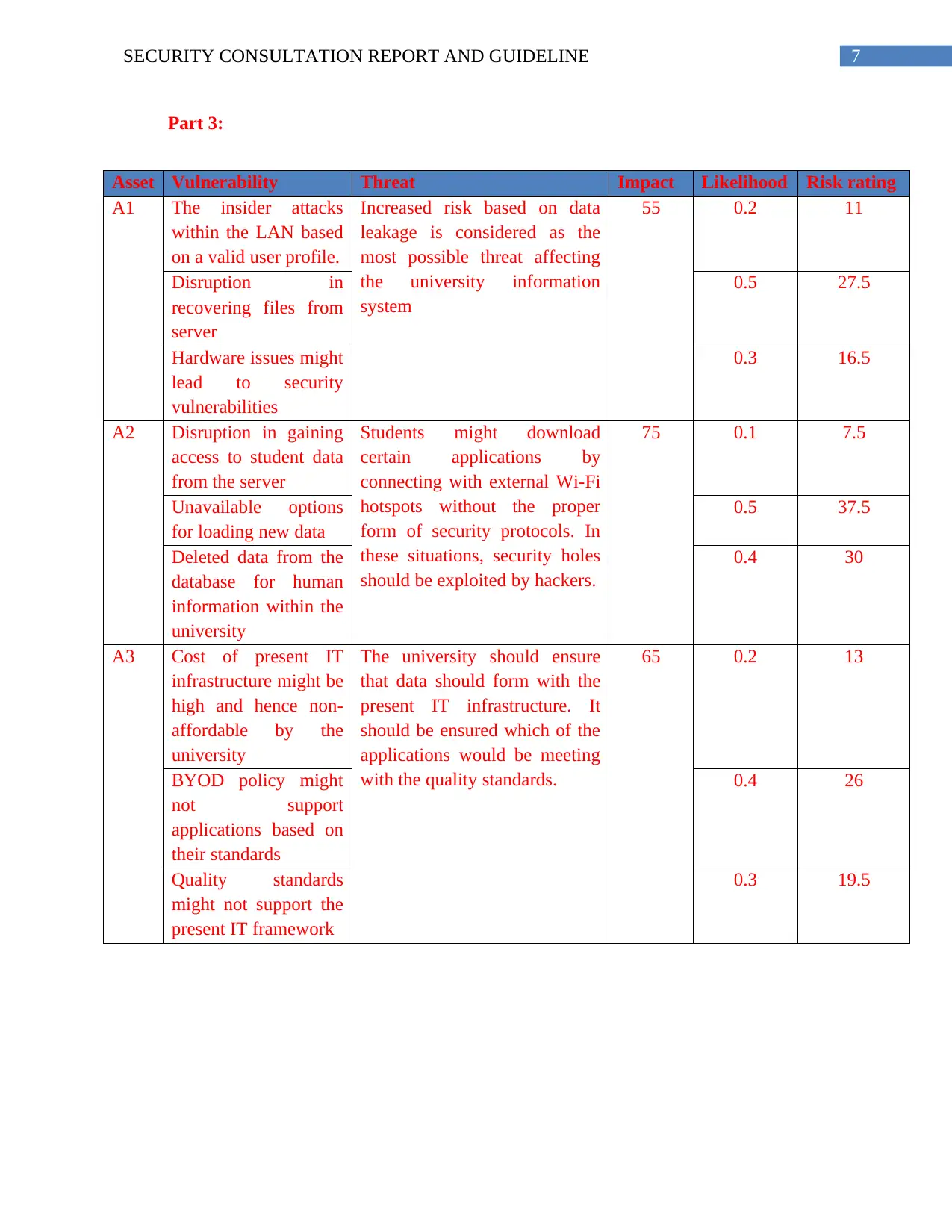
Part 3:
Asset Vulnerability Threat Impact Likelihood Risk rating
A1 The insider attacks
within the LAN based
on a valid user profile.
Increased risk based on data
leakage is considered as the
most possible threat affecting
the university information
system
55 0.2 11
Disruption in
recovering files from
server
0.5 27.5
Hardware issues might
lead to security
vulnerabilities
0.3 16.5
A2 Disruption in gaining
access to student data
from the server
Students might download
certain applications by
connecting with external Wi-Fi
hotspots without the proper
form of security protocols. In
these situations, security holes
should be exploited by hackers.
75 0.1 7.5
Unavailable options
for loading new data
0.5 37.5
Deleted data from the
database for human
information within the
university
0.4 30
A3 Cost of present IT
infrastructure might be
high and hence non-
affordable by the
university
The university should ensure
that data should form with the
present IT infrastructure. It
should be ensured which of the
applications would be meeting
with the quality standards.
65 0.2 13
BYOD policy might
not support
applications based on
their standards
0.4 26
Quality standards
might not support the
present IT framework
0.3 19.5
Part 3:
Asset Vulnerability Threat Impact Likelihood Risk rating
A1 The insider attacks
within the LAN based
on a valid user profile.
Increased risk based on data
leakage is considered as the
most possible threat affecting
the university information
system
55 0.2 11
Disruption in
recovering files from
server
0.5 27.5
Hardware issues might
lead to security
vulnerabilities
0.3 16.5
A2 Disruption in gaining
access to student data
from the server
Students might download
certain applications by
connecting with external Wi-Fi
hotspots without the proper
form of security protocols. In
these situations, security holes
should be exploited by hackers.
75 0.1 7.5
Unavailable options
for loading new data
0.5 37.5
Deleted data from the
database for human
information within the
university
0.4 30
A3 Cost of present IT
infrastructure might be
high and hence non-
affordable by the
university
The university should ensure
that data should form with the
present IT infrastructure. It
should be ensured which of the
applications would be meeting
with the quality standards.
65 0.2 13
BYOD policy might
not support
applications based on
their standards
0.4 26
Quality standards
might not support the
present IT framework
0.3 19.5

8SECURITY CONSULTATION REPORT AND GUIDELINE
1.7 Risk Assessment (Qualitative/quantitative)
The risks based on the information system implemented within the university could be
assessed using a qualitative approach. Under this approach, the different risks would be
discussed, analysed, selection of risk responses and monitoring processes.
In this case, the 5-step approach would be followed based on understanding the various
aspects of risks and determination of strategies based on their mitigation. These are as follows:
1. Step 1 – In the primary step, the risk situations should be identified.
2. Step 2 – It should be determined about the persons who would be responsible for the
situations of risks.
3. Step 3 – Based on understanding of the risk situations and the persons responsible for
the risk, the precautionary steps would be taken for mitigating them.
4. Step 4 – After the risk situations have been understood, the results would be record in
this step.
5. Step 5 – Regular review over assessments should be performed. More frequent
reviews would be considered as a necessary process in the workplace based on determining the
conditions of change.
Task 2: Certificate-Based Authentication
2.1 Introduction
The certificate-based authentication is recognized as a digital certificate for identification
of a user or machine before granting certain level of access to an application or resource (Verma,
1.7 Risk Assessment (Qualitative/quantitative)
The risks based on the information system implemented within the university could be
assessed using a qualitative approach. Under this approach, the different risks would be
discussed, analysed, selection of risk responses and monitoring processes.
In this case, the 5-step approach would be followed based on understanding the various
aspects of risks and determination of strategies based on their mitigation. These are as follows:
1. Step 1 – In the primary step, the risk situations should be identified.
2. Step 2 – It should be determined about the persons who would be responsible for the
situations of risks.
3. Step 3 – Based on understanding of the risk situations and the persons responsible for
the risk, the precautionary steps would be taken for mitigating them.
4. Step 4 – After the risk situations have been understood, the results would be record in
this step.
5. Step 5 – Regular review over assessments should be performed. More frequent
reviews would be considered as a necessary process in the workplace based on determining the
conditions of change.
Task 2: Certificate-Based Authentication
2.1 Introduction
The certificate-based authentication is recognized as a digital certificate for identification
of a user or machine before granting certain level of access to an application or resource (Verma,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY CONSULTATION REPORT AND GUIDELINE
Kumar and Sinha 2016). The method of certificate-based authentication represents the
deployment and coordination of different traditional methods that includes password and
username.
The following parts of the discussion would discuss on the work principles of the
password-based authentication scheme and certificate-based authentication. It also highlights on
the comparison presented between the certificate-based authentication with the password-based
authentication system.
2.2 Working principle of Password-based authentication scheme
The working principle of the scheme based on password-based authentication is based on
the process of identification and authorization. Simple method of password authentication helps
in offering an easy process based on performing authentication of users. In the password
authentication process, the concerned user should be able to supply a certain password to each of
the available servers (Wang and Xu 2017). The administrator would maintain a track over the
user name and unique password for each individual user on different servers.
The various steps involved behind the principle of working for the password-based
authentication scheme have being represented in the following picture.
Kumar and Sinha 2016). The method of certificate-based authentication represents the
deployment and coordination of different traditional methods that includes password and
username.
The following parts of the discussion would discuss on the work principles of the
password-based authentication scheme and certificate-based authentication. It also highlights on
the comparison presented between the certificate-based authentication with the password-based
authentication system.
2.2 Working principle of Password-based authentication scheme
The working principle of the scheme based on password-based authentication is based on
the process of identification and authorization. Simple method of password authentication helps
in offering an easy process based on performing authentication of users. In the password
authentication process, the concerned user should be able to supply a certain password to each of
the available servers (Wang and Xu 2017). The administrator would maintain a track over the
user name and unique password for each individual user on different servers.
The various steps involved behind the principle of working for the password-based
authentication scheme have being represented in the following picture.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY CONSULTATION REPORT AND GUIDELINE
(Figure 1: The Working Principle for the Password-based authentication system)
(Source: Wang and Xu 2017)
The principle of working for the password-based authentication system is discussed in the
following steps.
1. In the initial stage, the user would enter their name and password. The client
application should make use of the entered name for retrieving the Distinguished Name (DN).
2. In the second step, the client would send the DN and saved user passwords through the
internal network.
3. The server would match the password received from client-side with the pre-stored
password.
4. After determination over the authenticity of the password, the server would be able to
determine whether the specified user would be permitted for accessing any particular resource
(Moon et al. 2016). After this, the server would provide permission to the client for accessing the
request resource.
(Figure 1: The Working Principle for the Password-based authentication system)
(Source: Wang and Xu 2017)
The principle of working for the password-based authentication system is discussed in the
following steps.
1. In the initial stage, the user would enter their name and password. The client
application should make use of the entered name for retrieving the Distinguished Name (DN).
2. In the second step, the client would send the DN and saved user passwords through the
internal network.
3. The server would match the password received from client-side with the pre-stored
password.
4. After determination over the authenticity of the password, the server would be able to
determine whether the specified user would be permitted for accessing any particular resource
(Moon et al. 2016). After this, the server would provide permission to the client for accessing the
request resource.

11SECURITY CONSULTATION REPORT AND GUIDELINE
2.3 Certificate-based authentication scheme
This scheme makes use of a public key cryptography and digital certificate for the
purpose of authenticating any individual user. A digital approved certificate comprises of an
electronic form, which would comprise of a public key, digital signature, identification data and
the digital signature that would be approved by a certified authority (Mandal and Deepti 2017).
This would be derived from the private key that would belong to the certification authority.
Whenever a user would sign in within a server, they would be obligated to offer their
digital certificate, which would comprise a public key and signature derived from the authority
of certification. The server would compare the validity for the digital signature. It would also
verify whether the digital certificate would be issued by a certification authority (Almadhoun et
al. 2018). After the completion of the entire process, the server would be able to authenticate the
user based on a public-key cryptography based on confirming whether the designated user has
gained possession for the private key that would be in close association with the digital
certificate.
2.4 Working principle of Certificate-based authentication scheme
The certificate-based authentication process requires SSL based on performing
authentication. The certificate-based process would primarily assume that the client would be
connected to the server. The steps of authentication have been discussed in the following picture:
2.3 Certificate-based authentication scheme
This scheme makes use of a public key cryptography and digital certificate for the
purpose of authenticating any individual user. A digital approved certificate comprises of an
electronic form, which would comprise of a public key, digital signature, identification data and
the digital signature that would be approved by a certified authority (Mandal and Deepti 2017).
This would be derived from the private key that would belong to the certification authority.
Whenever a user would sign in within a server, they would be obligated to offer their
digital certificate, which would comprise a public key and signature derived from the authority
of certification. The server would compare the validity for the digital signature. It would also
verify whether the digital certificate would be issued by a certification authority (Almadhoun et
al. 2018). After the completion of the entire process, the server would be able to authenticate the
user based on a public-key cryptography based on confirming whether the designated user has
gained possession for the private key that would be in close association with the digital
certificate.
2.4 Working principle of Certificate-based authentication scheme
The certificate-based authentication process requires SSL based on performing
authentication. The certificate-based process would primarily assume that the client would be
connected to the server. The steps of authentication have been discussed in the following picture:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





