University Report: Security and Privacy of Employee Data Analysis
VerifiedAdded on 2022/10/02
|25
|6301
|272
Report
AI Summary
This report examines the security and privacy of employee data within the context of an Australian state government's shift to a "Shared Services" model using SaaS. It identifies and assesses various security and privacy threats, including data integrity issues, secrecy concerns, availability challenges, malware risks, and data injection attacks. The report further explores new security threats that arise from the transition to SaaS, such as data breaches, data loss, lack of transparency, identity theft, and uncertainty regarding data location. Each threat is analyzed in terms of likelihood, impact, and priority, with corresponding preventive actions and contingency plans. The report also addresses existing and new privacy threats, offering a comprehensive risk assessment to safeguard employee data in the evolving technological landscape. The report provides a detailed analysis of the various security and privacy risks associated with employee data, both before and after the transition to a SaaS model. It offers a thorough overview of the threats and the potential impact on the organization. The report also offers preventive measures and contingency plans to address these threats.

Running head: SECURITY AND PRIVACY OF EMPLOYEE DATA
Security and Privacy of Employee Data
Name of the Student:
Name of the university:
Author note:
Security and Privacy of Employee Data
Name of the Student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2SECURITY AND PRIVACY OF EMPLOYEE DATA
Introduction:
The state government of Australia receives a number of services from an
organization known as the department of Administrative Services or DAS. This service provider
provided them with many services that included management, payroll, tendering and many more.
There were a few risk that were identified in this system for which the DAS Company wanted to
shift the information to the cloud as “shared services” (McIlwraith, 2016) Shared Services works
with the help of SaaS model of the cloud computing technology. Though there are many
advantages of developing cloud access to the users, there are few constraints of using them too.
This report discuss all about the privacy and the security threats that the organization’s users can
face when a whole information system is shifted from minor data centers to clouds. They are
then put into the risk management register for the assessment of their priority (Haney et al,
2017). The priority level shows how much importance the issue has and how early does it needed
to be fixated.
Introduction:
The state government of Australia receives a number of services from an
organization known as the department of Administrative Services or DAS. This service provider
provided them with many services that included management, payroll, tendering and many more.
There were a few risk that were identified in this system for which the DAS Company wanted to
shift the information to the cloud as “shared services” (McIlwraith, 2016) Shared Services works
with the help of SaaS model of the cloud computing technology. Though there are many
advantages of developing cloud access to the users, there are few constraints of using them too.
This report discuss all about the privacy and the security threats that the organization’s users can
face when a whole information system is shifted from minor data centers to clouds. They are
then put into the risk management register for the assessment of their priority (Haney et al,
2017). The priority level shows how much importance the issue has and how early does it needed
to be fixated.
3SECURITY AND PRIVACY OF EMPLOYEE DATA
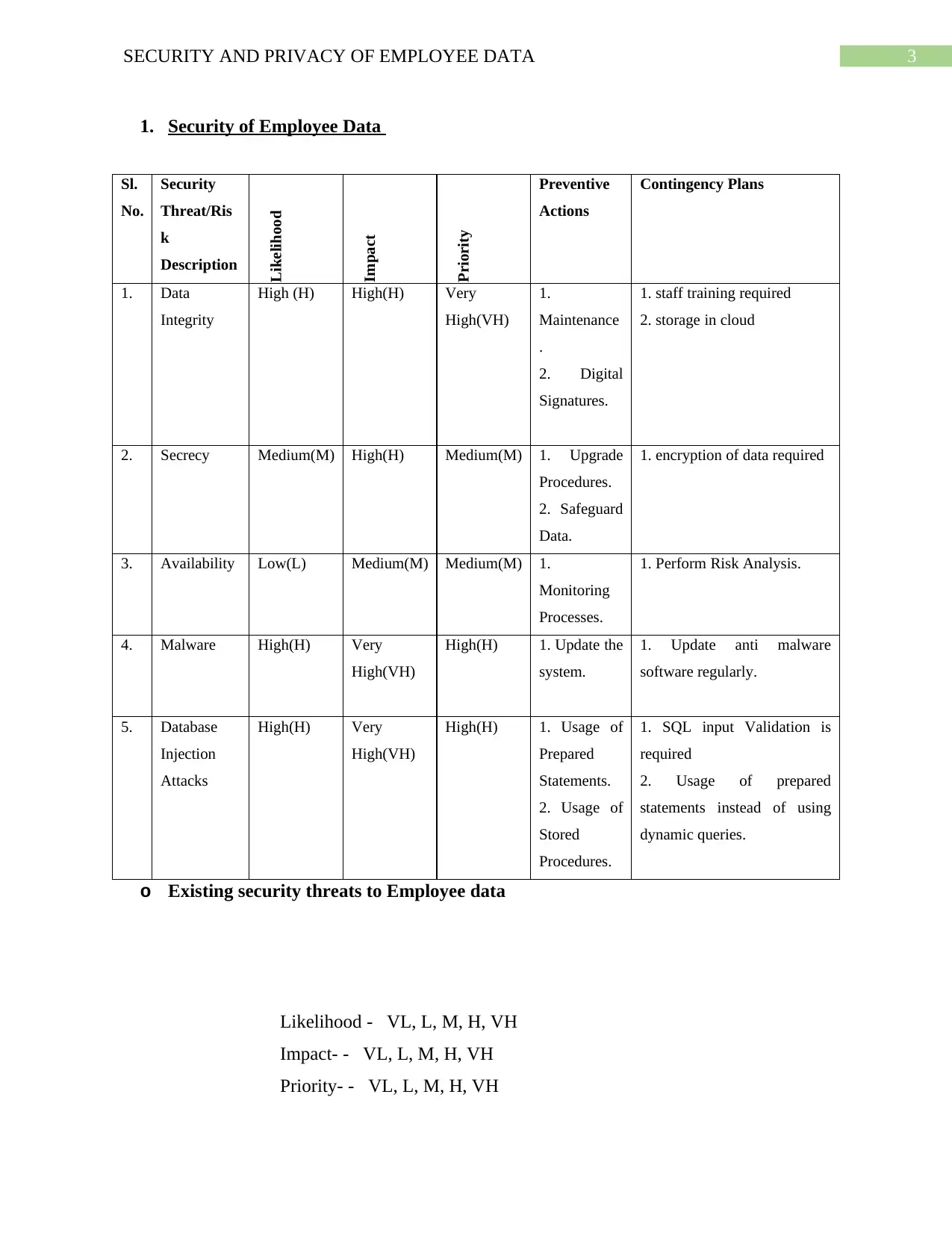
1. Security of Employee Data
Sl.
No.
Security
Threat/Ris
k
Description
Likelihood
Impact
Priority
Preventive
Actions
Contingency Plans
1. Data
Integrity
High (H) High(H) Very
High(VH)
1.
Maintenance
.
2. Digital
Signatures.
1. staff training required
2. storage in cloud
2. Secrecy Medium(M) High(H) Medium(M) 1. Upgrade
Procedures.
2. Safeguard
Data.
1. encryption of data required
3. Availability Low(L) Medium(M) Medium(M) 1.
Monitoring
Processes.
1. Perform Risk Analysis.
4. Malware High(H) Very
High(VH)
High(H) 1. Update the
system.
1. Update anti malware
software regularly.
5. Database
Injection
Attacks
High(H) Very
High(VH)
High(H) 1. Usage of
Prepared
Statements.
2. Usage of
Stored
Procedures.
1. SQL input Validation is
required
2. Usage of prepared
statements instead of using
dynamic queries.
o Existing security threats to Employee data
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
1. Security of Employee Data
Sl.
No.
Security
Threat/Ris
k
Description
Likelihood
Impact
Priority
Preventive
Actions
Contingency Plans
1. Data
Integrity
High (H) High(H) Very
High(VH)
1.
Maintenance
.
2. Digital
Signatures.
1. staff training required
2. storage in cloud
2. Secrecy Medium(M) High(H) Medium(M) 1. Upgrade
Procedures.
2. Safeguard
Data.
1. encryption of data required
3. Availability Low(L) Medium(M) Medium(M) 1.
Monitoring
Processes.
1. Perform Risk Analysis.
4. Malware High(H) Very
High(VH)
High(H) 1. Update the
system.
1. Update anti malware
software regularly.
5. Database
Injection
Attacks
High(H) Very
High(VH)
High(H) 1. Usage of
Prepared
Statements.
2. Usage of
Stored
Procedures.
1. SQL input Validation is
required
2. Usage of prepared
statements instead of using
dynamic queries.
o Existing security threats to Employee data
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4SECURITY AND PRIVACY OF EMPLOYEE DATA
Explain issues
1. Data Integrity: The consistency and accuracy of data is termed as data integrity. Data
integrity provides protection from inappropriate modification of information.
Modification involves insertion, creation, deletion and status change of data.
Maintenance of data integrity is keeping data intact and same throughout the full life
cycle. This consists of data capture, updates, storage, backups and transfers. Whenever
data procession takes place, a risk is always present for data corruption (Kearns, 2016).
Integrity may be lost if unappropriated changes occur with intention or by accidental acts.
Data integrity is essential for quality control and handling OOS results. Data integrity
also introduces the data safety with respect to regulatory compliance. It is maintained by
collection of processes, standards and rules implementation during design phase.
2. Secrecy: The act of information hiding from individuals or from groups is termed as
secrecy. Revealing of data should not take place to users who are not authorized. Secrecy
can be controversial which depends on the nature and content of the secret. Excessive
revealing of information can dispute with morality of confidentiality and privacy (Kearns,
2016). Secrecy exists in different ways such as encryption where technical and
mathematical strategies can be used for hiding messages, true secrecy where participants
are given certain restrictions and obfuscation where data is hidden in plane observation.
3. Availability: Availability is a condition where consumers can access a provided data. So,
with respect to database, data availability refers to if there is a database available, that
data can be accessed by the data users, that is, customers, business and application users.
Any criteria that makes the data inaccessible is the opposite of availability. Another
Explain issues
1. Data Integrity: The consistency and accuracy of data is termed as data integrity. Data
integrity provides protection from inappropriate modification of information.
Modification involves insertion, creation, deletion and status change of data.
Maintenance of data integrity is keeping data intact and same throughout the full life
cycle. This consists of data capture, updates, storage, backups and transfers. Whenever
data procession takes place, a risk is always present for data corruption (Kearns, 2016).
Integrity may be lost if unappropriated changes occur with intention or by accidental acts.
Data integrity is essential for quality control and handling OOS results. Data integrity
also introduces the data safety with respect to regulatory compliance. It is maintained by
collection of processes, standards and rules implementation during design phase.
2. Secrecy: The act of information hiding from individuals or from groups is termed as
secrecy. Revealing of data should not take place to users who are not authorized. Secrecy
can be controversial which depends on the nature and content of the secret. Excessive
revealing of information can dispute with morality of confidentiality and privacy (Kearns,
2016). Secrecy exists in different ways such as encryption where technical and
mathematical strategies can be used for hiding messages, true secrecy where participants
are given certain restrictions and obfuscation where data is hidden in plane observation.
3. Availability: Availability is a condition where consumers can access a provided data. So,
with respect to database, data availability refers to if there is a database available, that
data can be accessed by the data users, that is, customers, business and application users.
Any criteria that makes the data inaccessible is the opposite of availability. Another
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5SECURITY AND PRIVACY OF EMPLOYEE DATA
outlook of availability is the amount of time a system is used for production work (Bosch
& Micevska-Scharf, 2017). The application’s availability will change for different
organizations, for different systems of the organization and even for different users. Data
with poor performance can be accessed, however accessing a database which is
unavailable is not possible. The users cannot perform their respective job if there is
suffering in performance (Beautement, Becker, Parkin, Krol & Sasse, 2016). Availability
consists of four primary components that assures that the systems are up to the mark and
business can be done.
4. Malware: Malware is a software that is designed intentionally for causing damage to a
server, client, network or a computer. Malware causes the damage after its
implementation or implanted to a computer and perform direct executable scripts, codes
and other data. Malware is known as computer worms, viruses, Trojan horses, spyware,
scare ware, random ware and adware in media. Malware contains malicious intent that
acts against computer user’s interest and does not consist of software which creates
unintentional harm that is termed as a bug (Kent, 2016). Programs that are supplied
officially by the companies is considered as malware if they perform secretly against the
computer user’s interest. Sensitive data can be stolen by perennial threat malware through
infected devices.
5. Data Injection Attacks: Two types of data injection attacks are present such as SQL
injection which mark the conventional database systems and NoSQL injection which
target “big data” policy. A SQL injection attack have SQL query’s insertion from client
with input data into application. Sensitive data can be read from database through a
successful SQL injection, database can be modified, administration operations can be
outlook of availability is the amount of time a system is used for production work (Bosch
& Micevska-Scharf, 2017). The application’s availability will change for different
organizations, for different systems of the organization and even for different users. Data
with poor performance can be accessed, however accessing a database which is
unavailable is not possible. The users cannot perform their respective job if there is
suffering in performance (Beautement, Becker, Parkin, Krol & Sasse, 2016). Availability
consists of four primary components that assures that the systems are up to the mark and
business can be done.
4. Malware: Malware is a software that is designed intentionally for causing damage to a
server, client, network or a computer. Malware causes the damage after its
implementation or implanted to a computer and perform direct executable scripts, codes
and other data. Malware is known as computer worms, viruses, Trojan horses, spyware,
scare ware, random ware and adware in media. Malware contains malicious intent that
acts against computer user’s interest and does not consist of software which creates
unintentional harm that is termed as a bug (Kent, 2016). Programs that are supplied
officially by the companies is considered as malware if they perform secretly against the
computer user’s interest. Sensitive data can be stolen by perennial threat malware through
infected devices.
5. Data Injection Attacks: Two types of data injection attacks are present such as SQL
injection which mark the conventional database systems and NoSQL injection which
target “big data” policy. A SQL injection attack have SQL query’s insertion from client
with input data into application. Sensitive data can be read from database through a
successful SQL injection, database can be modified, administration operations can be

6SECURITY AND PRIVACY OF EMPLOYEE DATA
modified in the database, a provided file’s content can be recovered from file system of
database and in few cases commands can be issued to operating system (Malik & Patel,
2016). SQL injection attacks are one kind of injection attack where the predefined SQL
commands are effected by the injection of SQL commands to data-plane input. Identity,
causing repudiation issues like change in balance or transaction void, tempering with data
present can be spoofed by attackers through SQL injection attacks allow revelation of
complete data available in the system, data destruction and making the data unavailable
and becoming database server’s administrators. ASP and PHP applications have SQL
injection as for generality of older interfaces (Kotenko, Levshun, & Chechulin, 2016). As
for the availability of programmatic interfaces, ASP.NET and J2EE applications have
less chance of being exploited by SQL injections.
modified in the database, a provided file’s content can be recovered from file system of
database and in few cases commands can be issued to operating system (Malik & Patel,
2016). SQL injection attacks are one kind of injection attack where the predefined SQL
commands are effected by the injection of SQL commands to data-plane input. Identity,
causing repudiation issues like change in balance or transaction void, tempering with data
present can be spoofed by attackers through SQL injection attacks allow revelation of
complete data available in the system, data destruction and making the data unavailable
and becoming database server’s administrators. ASP and PHP applications have SQL
injection as for generality of older interfaces (Kotenko, Levshun, & Chechulin, 2016). As
for the availability of programmatic interfaces, ASP.NET and J2EE applications have
less chance of being exploited by SQL injections.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7SECURITY AND PRIVACY OF EMPLOYEE DATA
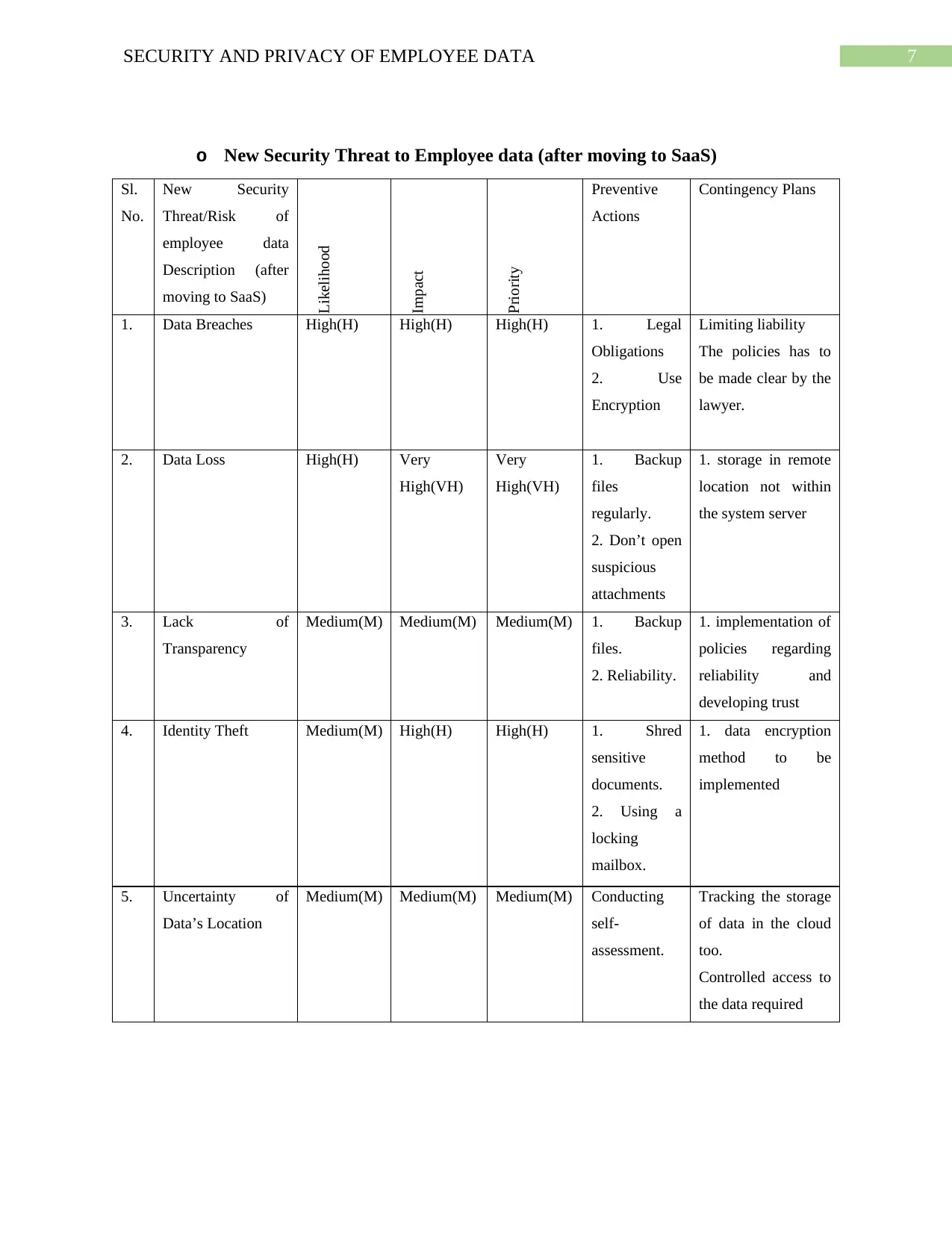
o New Security Threat to Employee data (after moving to SaaS)
Sl.
No.
New Security
Threat/Risk of
employee data
Description (after
moving to SaaS)
Likelihood
Impact
Priority
Preventive
Actions
Contingency Plans
1. Data Breaches High(H) High(H) High(H) 1. Legal
Obligations
2. Use
Encryption
Limiting liability
The policies has to
be made clear by the
lawyer.
2. Data Loss High(H) Very
High(VH)
Very
High(VH)
1. Backup
files
regularly.
2. Don’t open
suspicious
attachments
1. storage in remote
location not within
the system server
3. Lack of
Transparency
Medium(M) Medium(M) Medium(M) 1. Backup
files.
2. Reliability.
1. implementation of
policies regarding
reliability and
developing trust
4. Identity Theft Medium(M) High(H) High(H) 1. Shred
sensitive
documents.
2. Using a
locking
mailbox.
1. data encryption
method to be
implemented
5. Uncertainty of
Data’s Location
Medium(M) Medium(M) Medium(M) Conducting
self-
assessment.
Tracking the storage
of data in the cloud
too.
Controlled access to
the data required
o New Security Threat to Employee data (after moving to SaaS)
Sl.
No.
New Security
Threat/Risk of
employee data
Description (after
moving to SaaS)
Likelihood
Impact
Priority
Preventive
Actions
Contingency Plans
1. Data Breaches High(H) High(H) High(H) 1. Legal
Obligations
2. Use
Encryption
Limiting liability
The policies has to
be made clear by the
lawyer.
2. Data Loss High(H) Very
High(VH)
Very
High(VH)
1. Backup
files
regularly.
2. Don’t open
suspicious
attachments
1. storage in remote
location not within
the system server
3. Lack of
Transparency
Medium(M) Medium(M) Medium(M) 1. Backup
files.
2. Reliability.
1. implementation of
policies regarding
reliability and
developing trust
4. Identity Theft Medium(M) High(H) High(H) 1. Shred
sensitive
documents.
2. Using a
locking
mailbox.
1. data encryption
method to be
implemented
5. Uncertainty of
Data’s Location
Medium(M) Medium(M) Medium(M) Conducting
self-
assessment.
Tracking the storage
of data in the cloud
too.
Controlled access to
the data required
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8SECURITY AND PRIVACY OF EMPLOYEE DATA
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Data Breaches: Though security measures are implemented by cloud storage suppliers,
similar threats which impact storage networks threats the cloud environment as well. Customer
information, trade secrets and intellectual property can be exposed by data breach, which causes
serious consequences. A user can listen to activity from one virtual machine which signals the
encryption key’s arrival on another virtual machine within the same host. This is known as “side
channel timing exposure” which results in falling of organization’s internal data to competitors.
Many security protocols are being placed by the reputed cloud services for protecting the
confidential information (Chang, Kuo & Ramachandran, 2016). The most useful method is using
multi-factor authentication and encryption. If a breach occurs with sensitive data available in
cloud, the breach needs to be disclosed by the company and notifications should be sent to
possible victims.
2. Data Loss: The result of intrusive action and malicious action is the data breach. Data
loss can occur when a hard disk crashes and the owner of the hard disk have not kept a backup.
Data loss occurs when the key of the encrypted data is lost by the owner which unlocks it. Data
loss can occur with intention in case of malicious attack. Though chances of data loss are
minimum in cloud, cloud data centres are hacked by hackers for wiping data and gaining access.
Likelihood - VL, L, M, H, VH
Impact- - VL, L, M, H, VH
Priority- - VL, L, M, H, VH
Explain issues
1. Data Breaches: Though security measures are implemented by cloud storage suppliers,
similar threats which impact storage networks threats the cloud environment as well. Customer
information, trade secrets and intellectual property can be exposed by data breach, which causes
serious consequences. A user can listen to activity from one virtual machine which signals the
encryption key’s arrival on another virtual machine within the same host. This is known as “side
channel timing exposure” which results in falling of organization’s internal data to competitors.
Many security protocols are being placed by the reputed cloud services for protecting the
confidential information (Chang, Kuo & Ramachandran, 2016). The most useful method is using
multi-factor authentication and encryption. If a breach occurs with sensitive data available in
cloud, the breach needs to be disclosed by the company and notifications should be sent to
possible victims.
2. Data Loss: The result of intrusive action and malicious action is the data breach. Data
loss can occur when a hard disk crashes and the owner of the hard disk have not kept a backup.
Data loss occurs when the key of the encrypted data is lost by the owner which unlocks it. Data
loss can occur with intention in case of malicious attack. Though chances of data loss are
minimum in cloud, cloud data centres are hacked by hackers for wiping data and gaining access.

9SECURITY AND PRIVACY OF EMPLOYEE DATA
It’s essential for distributing applications in several areas and keep backup of data through off-
site storage whenever possible (Razak, Othman, Aldolah & Ngadi, 2016). Compliance policies
should also be kept in mind what the limitations are with the collected data. The data will be
protected with these rules in case of data breach.
3. Lack of Transparency: SaaS suppliers are secretive and the clients are assured that the
data is being kept safe. SaaS suppliers guarantee that the data will be more secure and files will
be more proficient with them more than the customers. There are several concerns with lack of
transparency of the supplier on how the overall security protocol is handled. Distrust can be
caused to customers by the lack of transparency. Both the industry analysts and the clients do not
get answers of many security questions (Barona & Anita, 2017). However, the lack of
transparency keeps security of the services provided by the SaaS providers. Information divulge
about data centres can compromise the client’s security.
4. Identity Theft: Payments are always required by SaaS providers and done remotely
with credit cards. It causes some concern few users about possible risk. Such problems are
prevented using several security protocols. Availability of identity management may be in the
LDAP directions of the company, on site of SaaS provider or inside the firewall of the firm. It is
also flawed severely as it is an old process. Identity theft is an important concern which is
prevented using several security tools implying usage of additional software and services
payment which guarantee information of credit card’s safety (Saa et al 2017). It is a concern
which is initiated from access managing and the technology might change in time. This can
create concerns for new users having no idea about the supplier before payment.
It’s essential for distributing applications in several areas and keep backup of data through off-
site storage whenever possible (Razak, Othman, Aldolah & Ngadi, 2016). Compliance policies
should also be kept in mind what the limitations are with the collected data. The data will be
protected with these rules in case of data breach.
3. Lack of Transparency: SaaS suppliers are secretive and the clients are assured that the
data is being kept safe. SaaS suppliers guarantee that the data will be more secure and files will
be more proficient with them more than the customers. There are several concerns with lack of
transparency of the supplier on how the overall security protocol is handled. Distrust can be
caused to customers by the lack of transparency. Both the industry analysts and the clients do not
get answers of many security questions (Barona & Anita, 2017). However, the lack of
transparency keeps security of the services provided by the SaaS providers. Information divulge
about data centres can compromise the client’s security.
4. Identity Theft: Payments are always required by SaaS providers and done remotely
with credit cards. It causes some concern few users about possible risk. Such problems are
prevented using several security protocols. Availability of identity management may be in the
LDAP directions of the company, on site of SaaS provider or inside the firewall of the firm. It is
also flawed severely as it is an old process. Identity theft is an important concern which is
prevented using several security tools implying usage of additional software and services
payment which guarantee information of credit card’s safety (Saa et al 2017). It is a concern
which is initiated from access managing and the technology might change in time. This can
create concerns for new users having no idea about the supplier before payment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10SECURITY AND PRIVACY OF EMPLOYEE DATA
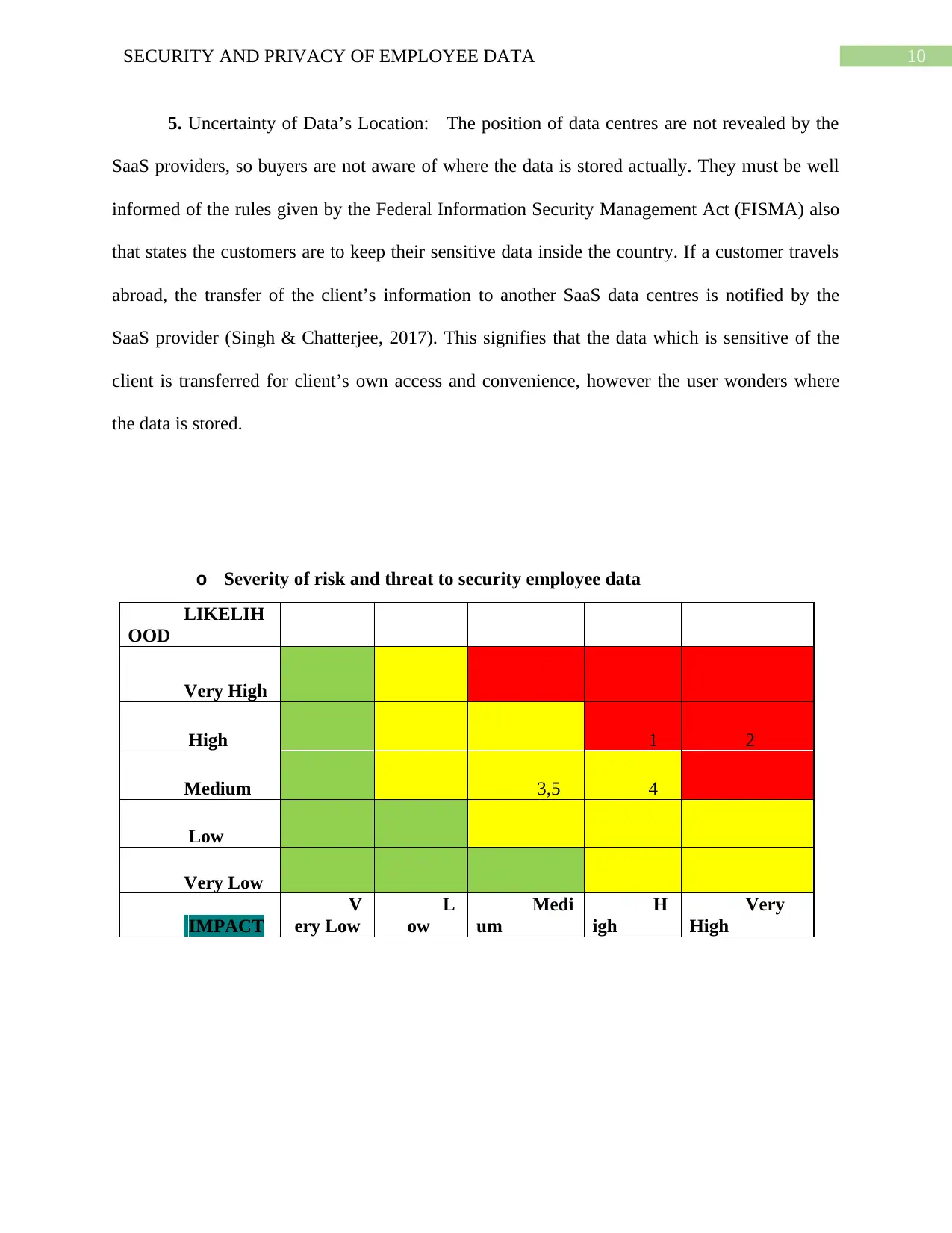
5. Uncertainty of Data’s Location: The position of data centres are not revealed by the
SaaS providers, so buyers are not aware of where the data is stored actually. They must be well
informed of the rules given by the Federal Information Security Management Act (FISMA) also
that states the customers are to keep their sensitive data inside the country. If a customer travels
abroad, the transfer of the client’s information to another SaaS data centres is notified by the
SaaS provider (Singh & Chatterjee, 2017). This signifies that the data which is sensitive of the
client is transferred for client’s own access and convenience, however the user wonders where
the data is stored.
o Severity of risk and threat to security employee data
LIKELIH
OOD
Very High
High 1 2
Medium 3,5 4
Low
Very Low
IMPACT
V
ery Low
L
ow
Medi
um
H
igh
Very
High
5. Uncertainty of Data’s Location: The position of data centres are not revealed by the
SaaS providers, so buyers are not aware of where the data is stored actually. They must be well
informed of the rules given by the Federal Information Security Management Act (FISMA) also
that states the customers are to keep their sensitive data inside the country. If a customer travels
abroad, the transfer of the client’s information to another SaaS data centres is notified by the
SaaS provider (Singh & Chatterjee, 2017). This signifies that the data which is sensitive of the
client is transferred for client’s own access and convenience, however the user wonders where
the data is stored.
o Severity of risk and threat to security employee data
LIKELIH
OOD
Very High
High 1 2
Medium 3,5 4
Low
Very Low
IMPACT
V
ery Low
L
ow
Medi
um
H
igh
Very
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11SECURITY AND PRIVACY OF EMPLOYEE DATA
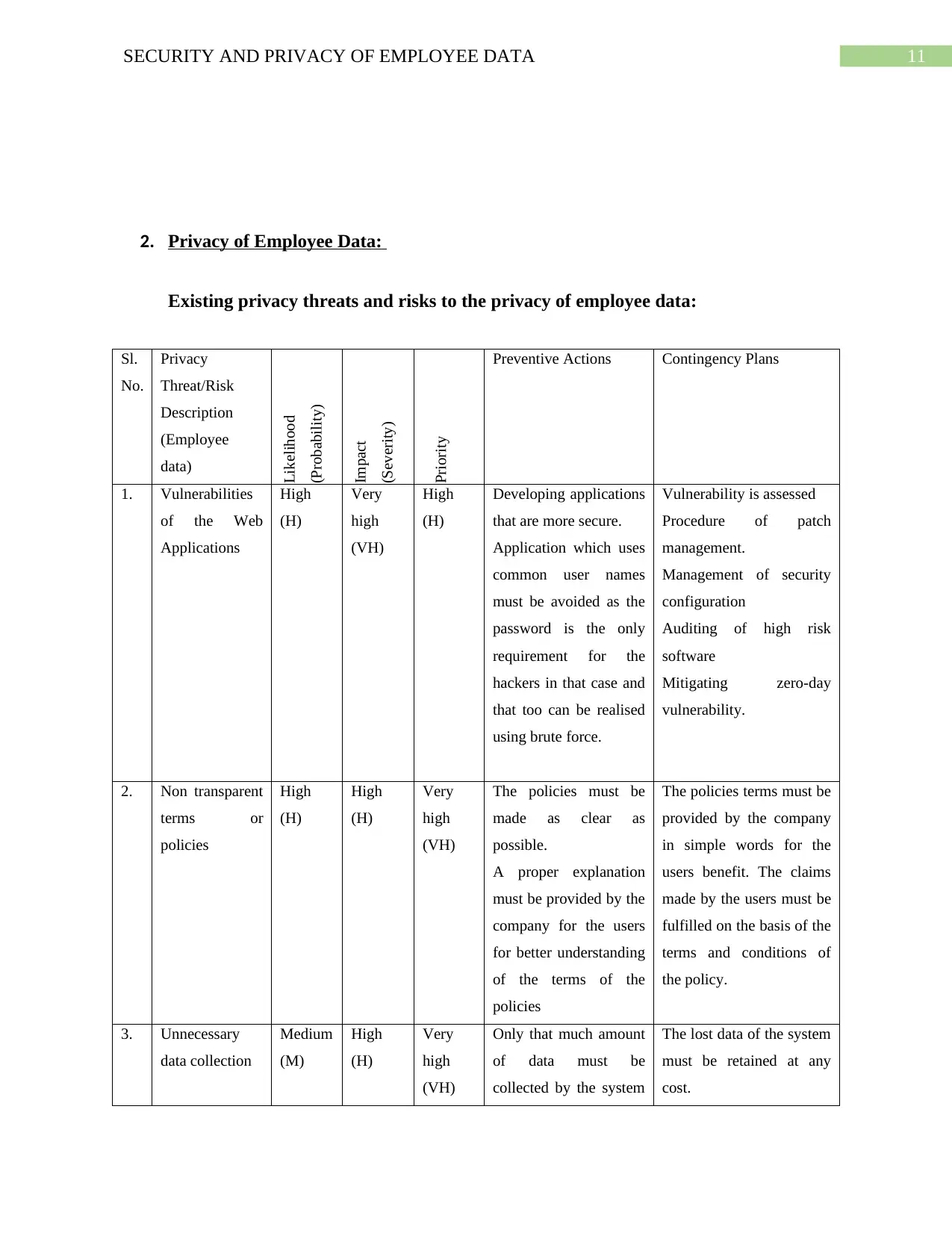
2. Privacy of Employee Data:
Existing privacy threats and risks to the privacy of employee data:
Sl.
No.
Privacy
Threat/Risk
Description
(Employee
data)
Likelihood
(Probability)
Impact
(Severity)
Priority
Preventive Actions Contingency Plans
1. Vulnerabilities
of the Web
Applications
High
(H)
Very
high
(VH)
High
(H)
Developing applications
that are more secure.
Application which uses
common user names
must be avoided as the
password is the only
requirement for the
hackers in that case and
that too can be realised
using brute force.
Vulnerability is assessed
Procedure of patch
management.
Management of security
configuration
Auditing of high risk
software
Mitigating zero-day
vulnerability.
2. Non transparent
terms or
policies
High
(H)
High
(H)
Very
high
(VH)
The policies must be
made as clear as
possible.
A proper explanation
must be provided by the
company for the users
for better understanding
of the terms of the
policies
The policies terms must be
provided by the company
in simple words for the
users benefit. The claims
made by the users must be
fulfilled on the basis of the
terms and conditions of
the policy.
3. Unnecessary
data collection
Medium
(M)
High
(H)
Very
high
(VH)
Only that much amount
of data must be
collected by the system
The lost data of the system
must be retained at any
cost.
2. Privacy of Employee Data:
Existing privacy threats and risks to the privacy of employee data:
Sl.
No.
Privacy
Threat/Risk
Description
(Employee
data)
Likelihood
(Probability)
Impact
(Severity)
Priority
Preventive Actions Contingency Plans
1. Vulnerabilities
of the Web
Applications
High
(H)
Very
high
(VH)
High
(H)
Developing applications
that are more secure.
Application which uses
common user names
must be avoided as the
password is the only
requirement for the
hackers in that case and
that too can be realised
using brute force.
Vulnerability is assessed
Procedure of patch
management.
Management of security
configuration
Auditing of high risk
software
Mitigating zero-day
vulnerability.
2. Non transparent
terms or
policies
High
(H)
High
(H)
Very
high
(VH)
The policies must be
made as clear as
possible.
A proper explanation
must be provided by the
company for the users
for better understanding
of the terms of the
policies
The policies terms must be
provided by the company
in simple words for the
users benefit. The claims
made by the users must be
fulfilled on the basis of the
terms and conditions of
the policy.
3. Unnecessary
data collection
Medium
(M)
High
(H)
Very
high
(VH)
Only that much amount
of data must be
collected by the system
The lost data of the system
must be retained at any
cost.
12SECURITY AND PRIVACY OF EMPLOYEE DATA
which is actually
required for the user’s
interaction to the
system.
The remaining data of the
system is kept secured.
4. Third party
sharing of data
Medium
(M)
High
(H)
Medium
(M)
Third party access of
the data must be
prevented by providing
access control measures
to the system.
Implantation of
biometrics
Implementation of
encrypted data can help.
5. Transferring
data in an
insecure
manner.
Medium
(M)
Very
high
(VH)
High
(H)
The transfer of data
should take place within
end to end encrypted
system.
No third party invasion
must be neglected
Employees must be trained
in a way such that they can
handle issues like this and
prevent this mistake from
repeating.
The risk regarding the old system of data management are discussed below:
1. Vulnerabilities of the web applications: There is one problem that persists in all the
system that guards sensitive data or operates on them; vulnerabilities. Privacy breach
occurs in a system when there is a failure in designing a suitable application or its’ proper
implementation. Failure of problem detection or failure in applying a patch fixation also
results in a privacy breakage.
These vulnerabilities are firstly assessed. Assessment of vulnerability is
mandatory as identification of the cause of the risk is important for mitigating the issue
(Haney et al, 2017). Orchestration, customization and automation of the entire patch
process is necessary. Downloading, testing and deploying the patches automatically to
Mac, Windows, Linux and over as many as 250 third party application at no extra cost,
with a patching module which is integral. Enforcing stronger passwords to the system for
which is actually
required for the user’s
interaction to the
system.
The remaining data of the
system is kept secured.
4. Third party
sharing of data
Medium
(M)
High
(H)
Medium
(M)
Third party access of
the data must be
prevented by providing
access control measures
to the system.
Implantation of
biometrics
Implementation of
encrypted data can help.
5. Transferring
data in an
insecure
manner.
Medium
(M)
Very
high
(VH)
High
(H)
The transfer of data
should take place within
end to end encrypted
system.
No third party invasion
must be neglected
Employees must be trained
in a way such that they can
handle issues like this and
prevent this mistake from
repeating.
The risk regarding the old system of data management are discussed below:
1. Vulnerabilities of the web applications: There is one problem that persists in all the
system that guards sensitive data or operates on them; vulnerabilities. Privacy breach
occurs in a system when there is a failure in designing a suitable application or its’ proper
implementation. Failure of problem detection or failure in applying a patch fixation also
results in a privacy breakage.
These vulnerabilities are firstly assessed. Assessment of vulnerability is
mandatory as identification of the cause of the risk is important for mitigating the issue
(Haney et al, 2017). Orchestration, customization and automation of the entire patch
process is necessary. Downloading, testing and deploying the patches automatically to
Mac, Windows, Linux and over as many as 250 third party application at no extra cost,
with a patching module which is integral. Enforcing stronger passwords to the system for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





