Enterprise Systems Security: Analysis and Case Studies
VerifiedAdded on 2022/08/25
|20
|4603
|27
Project
AI Summary
This project is an e-portfolio created by a student business analyst after completing a short Enterprise Systems course. The project delves into various security issues related to enterprise systems, including data security, cloud computing vulnerabilities, and the importance of IT infrastructure in large organizations. It analyzes these issues, offering a domain analysis model and a security plan to address them. The portfolio also explores relevant considerations for implementing enterprise systems, such as ERP integration, business process optimization, and cloud ERP adoption. Furthermore, it emphasizes the significance of communication skills in dealing with enterprise systems. The project includes case studies focusing on improving financial security in Telstra and analyzing security metrics and risk analysis for enterprise systems, providing insights into advantages, challenges, and solutions, including the Common Vulnerability Scoring System (CVSS). The document aims to provide a comprehensive understanding of enterprise system security for the organization's intranet or knowledge portal.

Running head: SECURITY OF ES
Security of ES
Name of the Student
Name of the University
Author Note
Security of ES
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY OF ES
Table of Contents
1. Introduction............................................................................................................................2
1.1 Background of the system................................................................................................2
1.2 Overall plan of enacting ES.............................................................................................3
2. Analyzing Enterprise System.................................................................................................4
2.1 Deep analysis of the issues...............................................................................................5
3. Larger IT infrastructure of large scale organizations.............................................................6
4. Relevant considerations in the implementation of Enterprise Systems.................................8
5. Communication skills for dealing with Enterprise Systems..................................................9
6. Case study 1: Improvement of financial security in Telstra using ES...................................9
6.1 Advantages.......................................................................................................................9
6.2 Analysis:.........................................................................................................................10
6.2 Case study 2: Security Metrics and Risk Analysis for Enterprise Systems.......................11
6.2.1 Improving cyber security program..........................................................................12
6.2.2 Challenges...............................................................................................................12
6.2.3 Enterprise security management.............................................................................12
6.3.1 Common Vulnerability Scoring System (CVSS)........................................................13
7. Conclusion............................................................................................................................14
8. References............................................................................................................................16
Table of Contents
1. Introduction............................................................................................................................2
1.1 Background of the system................................................................................................2
1.2 Overall plan of enacting ES.............................................................................................3
2. Analyzing Enterprise System.................................................................................................4
2.1 Deep analysis of the issues...............................................................................................5
3. Larger IT infrastructure of large scale organizations.............................................................6
4. Relevant considerations in the implementation of Enterprise Systems.................................8
5. Communication skills for dealing with Enterprise Systems..................................................9
6. Case study 1: Improvement of financial security in Telstra using ES...................................9
6.1 Advantages.......................................................................................................................9
6.2 Analysis:.........................................................................................................................10
6.2 Case study 2: Security Metrics and Risk Analysis for Enterprise Systems.......................11
6.2.1 Improving cyber security program..........................................................................12
6.2.2 Challenges...............................................................................................................12
6.2.3 Enterprise security management.............................................................................12
6.3.1 Common Vulnerability Scoring System (CVSS)........................................................13
7. Conclusion............................................................................................................................14
8. References............................................................................................................................16

2SECURITY OF ES
1. Introduction
There are diverse categories of security issues related with the enterprise systems
which are used in our society as well as in commercial establishments such as the delayed
updates, weighing up the benefits, only one authentication technique, getting the full
access control, numerous unauthorized systems which are related with Enterprise
Software (ES), and inadequate training sessions, failure to comply.
There are other security issues related with the use of ES like the selection of the
exact ES, technical issues of ES, data quality issues, mind shift issues and changes in the
business philosophy (Singhal, 2017). Each of these challenges has to be understood and
addressed in the first place before these systems are considered in a business.
The role of a business analyst is very much significant for the growth and
development of a commercial business as it helps in assisting a business case, monitor and
plan any type of projects, understanding the exact business requirements of the business,
managing the business procedures, managing the communication among the business
stakeholders and requirement analysis. The notable determination of this assignment is to
create an e-portfolio which can reflect the learning of a short enterprise systems course. The
data of the e-portfolio shall be available to each member of the organization where I work as
a business analyst.
1.1 Background of the system
ES can be defined as the type of computer software which is treated as business
oriented tools in commercial business establishments. This tool can be very much useful to
enhance the flexibility of the daily business processes, the productivity of the resources in a
commercial establishment can be enhanced using ES (Tabatabaei & Harris, 2019). The entire
1. Introduction
There are diverse categories of security issues related with the enterprise systems
which are used in our society as well as in commercial establishments such as the delayed
updates, weighing up the benefits, only one authentication technique, getting the full
access control, numerous unauthorized systems which are related with Enterprise
Software (ES), and inadequate training sessions, failure to comply.
There are other security issues related with the use of ES like the selection of the
exact ES, technical issues of ES, data quality issues, mind shift issues and changes in the
business philosophy (Singhal, 2017). Each of these challenges has to be understood and
addressed in the first place before these systems are considered in a business.
The role of a business analyst is very much significant for the growth and
development of a commercial business as it helps in assisting a business case, monitor and
plan any type of projects, understanding the exact business requirements of the business,
managing the business procedures, managing the communication among the business
stakeholders and requirement analysis. The notable determination of this assignment is to
create an e-portfolio which can reflect the learning of a short enterprise systems course. The
data of the e-portfolio shall be available to each member of the organization where I work as
a business analyst.
1.1 Background of the system
ES can be defined as the type of computer software which is treated as business
oriented tools in commercial business establishments. This tool can be very much useful to
enhance the flexibility of the daily business processes, the productivity of the resources in a
commercial establishment can be enhanced using ES (Tabatabaei & Harris, 2019). The entire
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY OF ES
business plan of this organization can be supported using this tool. Clarity in the business
procedure is also maintained with the help of ES. Record keeping ability of the commercial
organization can be enhanced using this tool as well (Simpson & Foltz, 2017). Addressing
the compliance issues is one of the most significant challenges faced in the commercial
organizations which can be addressed in the first place with the help of ES. There are diverse
categories of costs involved in business organizations which can also be reduced with the
help of ES. The detailed plan of incorporating an ES can be understood from the ensuing
segment of this report.
1.2 Overall plan of enacting ES
Understand corporate strategy: Strategic direction of the environment where this
system is going to be installed. The purchasing decisions have to be finalized in the
finalized with the help of the corporate strategy as well.
Business process strategy: New operational strategies have to be selected with the
help of the strategic planners. Shared business service processes have to be
understood using the business process strategy.
Technology: Organizational change initiative has to be introduced as there are
numerous changes regarding the outline of new software.
Strategic KPI: Strategic levels of performance have to be maintained using the help
of the key perform indicators such as the flow efficiency, automation procedures
and code coverage.
Return on investment: The payback period of the project has to be understood in
the first place using cost benefit analysis (Popplewell et al.2019). The yearly return
of investment can be identified with the help of the ROI calculation as well.
business plan of this organization can be supported using this tool. Clarity in the business
procedure is also maintained with the help of ES. Record keeping ability of the commercial
organization can be enhanced using this tool as well (Simpson & Foltz, 2017). Addressing
the compliance issues is one of the most significant challenges faced in the commercial
organizations which can be addressed in the first place with the help of ES. There are diverse
categories of costs involved in business organizations which can also be reduced with the
help of ES. The detailed plan of incorporating an ES can be understood from the ensuing
segment of this report.
1.2 Overall plan of enacting ES
Understand corporate strategy: Strategic direction of the environment where this
system is going to be installed. The purchasing decisions have to be finalized in the
finalized with the help of the corporate strategy as well.
Business process strategy: New operational strategies have to be selected with the
help of the strategic planners. Shared business service processes have to be
understood using the business process strategy.
Technology: Organizational change initiative has to be introduced as there are
numerous changes regarding the outline of new software.
Strategic KPI: Strategic levels of performance have to be maintained using the help
of the key perform indicators such as the flow efficiency, automation procedures
and code coverage.
Return on investment: The payback period of the project has to be understood in
the first place using cost benefit analysis (Popplewell et al.2019). The yearly return
of investment can be identified with the help of the ROI calculation as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY OF ES
On the other hand, as deliberated by Pendleton et al. (2016), the plan of installing a
new software in a business have numerous security challenges which has to be taken care of
and there is no specific plan for enacting a new software such as data integrity, lack of
support from the vendor. The investigator of this journal highlighted the significance of the
software training tools while enacting new software.
The business data of an organization can be enhanced in the first place with the help
of ES, at the same time it can also be said that automation of the customer service be
customized in the first place using the ES. Financial security can be maintained in
commercial establishments using ES, at the same time reliability of IT in a business can also
be enhanced using ES (Panetto et al., 2016). Security of ES can be very much useful in a
business as it is used to secure the customer data as well as the organization data. Real time
access to information is possible of security is maintained by ESs.
2. Analyzing Enterprise System
The role of the senior management team and the IT strategic planners is very much
significant for the successful incorporation of ES. The domain of the enterprise system has to
be analyzed in the first place. Identification of the opportunities is one of the prime aspects
of analyzing the security provided by ES (Nurse et al., 2018). The characteristic features of
the ES depend upon the business requirement of the users of this system. The model of
domain analysis which can be very much beneficial to understand the security provided by an
enterprise system is illustrated below.
On the other hand, as deliberated by Pendleton et al. (2016), the plan of installing a
new software in a business have numerous security challenges which has to be taken care of
and there is no specific plan for enacting a new software such as data integrity, lack of
support from the vendor. The investigator of this journal highlighted the significance of the
software training tools while enacting new software.
The business data of an organization can be enhanced in the first place with the help
of ES, at the same time it can also be said that automation of the customer service be
customized in the first place using the ES. Financial security can be maintained in
commercial establishments using ES, at the same time reliability of IT in a business can also
be enhanced using ES (Panetto et al., 2016). Security of ES can be very much useful in a
business as it is used to secure the customer data as well as the organization data. Real time
access to information is possible of security is maintained by ESs.
2. Analyzing Enterprise System
The role of the senior management team and the IT strategic planners is very much
significant for the successful incorporation of ES. The domain of the enterprise system has to
be analyzed in the first place. Identification of the opportunities is one of the prime aspects
of analyzing the security provided by ES (Nurse et al., 2018). The characteristic features of
the ES depend upon the business requirement of the users of this system. The model of
domain analysis which can be very much beneficial to understand the security provided by an
enterprise system is illustrated below.
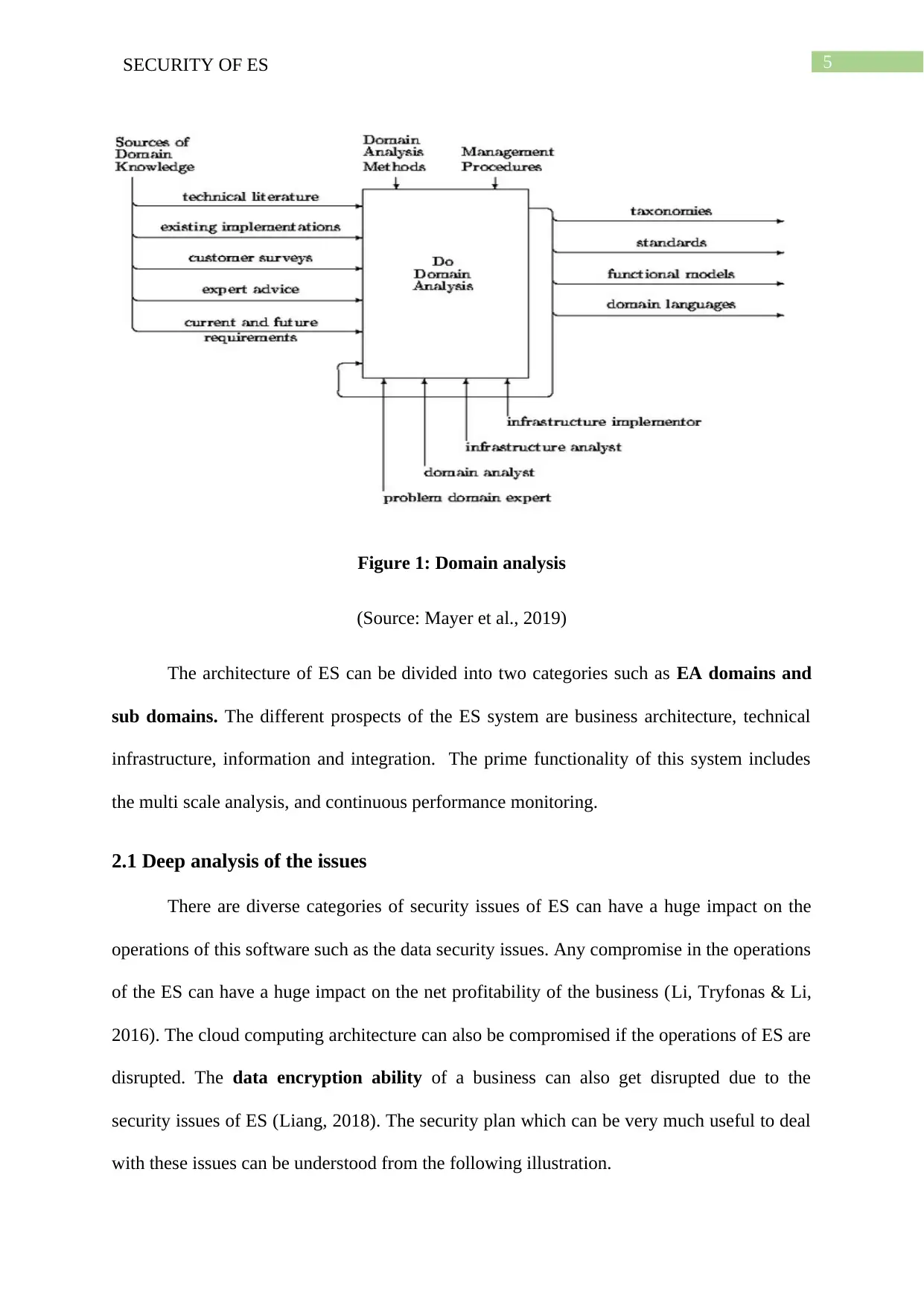
5SECURITY OF ES
Figure 1: Domain analysis
(Source: Mayer et al., 2019)
The architecture of ES can be divided into two categories such as EA domains and
sub domains. The different prospects of the ES system are business architecture, technical
infrastructure, information and integration. The prime functionality of this system includes
the multi scale analysis, and continuous performance monitoring.
2.1 Deep analysis of the issues
There are diverse categories of security issues of ES can have a huge impact on the
operations of this software such as the data security issues. Any compromise in the operations
of the ES can have a huge impact on the net profitability of the business (Li, Tryfonas & Li,
2016). The cloud computing architecture can also be compromised if the operations of ES are
disrupted. The data encryption ability of a business can also get disrupted due to the
security issues of ES (Liang, 2018). The security plan which can be very much useful to deal
with these issues can be understood from the following illustration.
Figure 1: Domain analysis
(Source: Mayer et al., 2019)
The architecture of ES can be divided into two categories such as EA domains and
sub domains. The different prospects of the ES system are business architecture, technical
infrastructure, information and integration. The prime functionality of this system includes
the multi scale analysis, and continuous performance monitoring.
2.1 Deep analysis of the issues
There are diverse categories of security issues of ES can have a huge impact on the
operations of this software such as the data security issues. Any compromise in the operations
of the ES can have a huge impact on the net profitability of the business (Li, Tryfonas & Li,
2016). The cloud computing architecture can also be compromised if the operations of ES are
disrupted. The data encryption ability of a business can also get disrupted due to the
security issues of ES (Liang, 2018). The security plan which can be very much useful to deal
with these issues can be understood from the following illustration.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY OF ES
Figure 2: Security plane to deal with the issues of ES
(Source: Gross & Li 2017)
3. Larger IT infrastructure of large scale organizations
Huge IT infrastructure is maintained in most of the large scale organizations to
optimize business operations such as the transfer of data from one business unit to another.
ES is an integral part of the IT infrastructure of the large scale organizations. ES are
increasingly used across diverse types of industries such as the finance, defense, medical
and intelligence. The current trends in security have to be understood so that the effectiveness
of ES is enjoyed by the business organizations (Gross & Li, 2017). The next generation
security models which can be very much useful to deal with the security issues of ES can be
understood from the following diagram.
Figure 2: Security plane to deal with the issues of ES
(Source: Gross & Li 2017)
3. Larger IT infrastructure of large scale organizations
Huge IT infrastructure is maintained in most of the large scale organizations to
optimize business operations such as the transfer of data from one business unit to another.
ES is an integral part of the IT infrastructure of the large scale organizations. ES are
increasingly used across diverse types of industries such as the finance, defense, medical
and intelligence. The current trends in security have to be understood so that the effectiveness
of ES is enjoyed by the business organizations (Gross & Li, 2017). The next generation
security models which can be very much useful to deal with the security issues of ES can be
understood from the following diagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY OF ES
Figure 3: Next generation security model
(Source: Gao et al. 2019)
According to Gao et al. (2019), CITRIX server can be very much useful to deal with
the security issues of the users and the ES. The role of the database vendors is also very much
useful to deal with the overall security issues of the ES such as the weak configuration of
the end point systems of the legacy operating systems, network devices as well as
applications. The older protocols have to be modified in order to deal with the configuration
issues of ES. Unrestricted cloud storage is the other security challenges related of ES as a
result of the compromising the basic access controls, along with this issue any sort of
unpatched software is the other security concern of ESs (Duffield 2017). There are two types
of user accounts which can be opened in an ES and the use of weaker or smaller passwords
can be very much useful to secure the data centers which are connected with the ES. There
are diverse categories of cyber security attacks related with ES such as the phishing emails
and social engineering attacks.
On the other hand, as elaborated by Dong et al (2017), limited time of incorporating
the software, resistance to change, budget constraints, and network issues are the prime
Figure 3: Next generation security model
(Source: Gao et al. 2019)
According to Gao et al. (2019), CITRIX server can be very much useful to deal with
the security issues of the users and the ES. The role of the database vendors is also very much
useful to deal with the overall security issues of the ES such as the weak configuration of
the end point systems of the legacy operating systems, network devices as well as
applications. The older protocols have to be modified in order to deal with the configuration
issues of ES. Unrestricted cloud storage is the other security challenges related of ES as a
result of the compromising the basic access controls, along with this issue any sort of
unpatched software is the other security concern of ESs (Duffield 2017). There are two types
of user accounts which can be opened in an ES and the use of weaker or smaller passwords
can be very much useful to secure the data centers which are connected with the ES. There
are diverse categories of cyber security attacks related with ES such as the phishing emails
and social engineering attacks.
On the other hand, as elaborated by Dong et al (2017), limited time of incorporating
the software, resistance to change, budget constraints, and network issues are the prime

8SECURITY OF ES
security challenges related with ES. Each of these security threats has to be addressed in the
first place with the help of an effective defensive tools and security solutions. According to
Kawanishi et al., (2019), unwanted interference can be restricted using a firewall with the
help of advanced firewalls as well (Appelbaum et al., 2017). The entire flow of the data can
be managed in the first place using a secure router. The researchers of this data source
provided an in depth discussion about the procedures which can be very much useful to deal
with the security issues of ES such as AV scanning technique, IP reputation awareness
and malware scanning. The considerations of enacting an ES can be understood from the
following section of this report.
4. Relevant considerations in the implementation of Enterprise Systems
The different categories of considerations related with the enactment of ES are as
followings:
Integration of ERP: Clarity of business functions must be there and the business
must be getting a competitive edge after enacting the ES.
Business Process Optimization: The functional capabilities of ES have to be
fulfilling its business requirements. The obsolete processes of the business have to be
minimised along with the redundant processes using the BPO.
Enabling cloud ERP: The overhead cost of enacting ES can be minimised in the first
place if cloud based ERP solutions are hosted.
Mobile adaptation and value addition: In order to get intermission free operations
enterprise mobility must be practised. The planning feature of the ERP software can
also be used to enhance the benefit of the ES.
security challenges related with ES. Each of these security threats has to be addressed in the
first place with the help of an effective defensive tools and security solutions. According to
Kawanishi et al., (2019), unwanted interference can be restricted using a firewall with the
help of advanced firewalls as well (Appelbaum et al., 2017). The entire flow of the data can
be managed in the first place using a secure router. The researchers of this data source
provided an in depth discussion about the procedures which can be very much useful to deal
with the security issues of ES such as AV scanning technique, IP reputation awareness
and malware scanning. The considerations of enacting an ES can be understood from the
following section of this report.
4. Relevant considerations in the implementation of Enterprise Systems
The different categories of considerations related with the enactment of ES are as
followings:
Integration of ERP: Clarity of business functions must be there and the business
must be getting a competitive edge after enacting the ES.
Business Process Optimization: The functional capabilities of ES have to be
fulfilling its business requirements. The obsolete processes of the business have to be
minimised along with the redundant processes using the BPO.
Enabling cloud ERP: The overhead cost of enacting ES can be minimised in the first
place if cloud based ERP solutions are hosted.
Mobile adaptation and value addition: In order to get intermission free operations
enterprise mobility must be practised. The planning feature of the ERP software can
also be used to enhance the benefit of the ES.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY OF ES
5. Communication skills for dealing with Enterprise Systems.
Intragroup communication is very much significant to deal with ES as there are
numerous technical and non-technical challenges of ES. Both the verbal as well as the non-
verbal communication skills are required to deal with ES. The communication skills required
to deal with the challenges of ES are emotional intelligence, cohesion, and empathy
(Alshammari, 2017). Most of the real time interactions can be done with the help of these
communication skills. The collaboration procedure required in each of the business
organization who deals with ES can be optimised with the help of these communication
skills.
6. Case study 1: Improvement of financial security in Telstra using ES
Telstra which is the largest tele-communication industry in Australia has successfully
incorporated a new ES which has helped them to enhance the quality of daily operations. The
entire cloud computing infrastructure was enhanced after ES is introduced in this
organization. There numerous challenges which are faced while incorporating ES in Telstra.
6.1 Advantages
The business operations with the subsidiary organizations of Telstra have improved
after the introduction of ES. The performance of the scalable applications has improved
after the ES successfully incorporated in Telstra. Supervision activities of this business and
the entire IP network of this business are enhanced after this tool is amalgamated in Telstra.
The cutting edge solutions which are provided by this software were also boosted after the
introduction of ES (Enterprise, 2020). The cost of ownership have also enhanced after this
software is installed with the different types of computer systems in this business. The in-
house management of Telstra was improved due to ESs.
5. Communication skills for dealing with Enterprise Systems.
Intragroup communication is very much significant to deal with ES as there are
numerous technical and non-technical challenges of ES. Both the verbal as well as the non-
verbal communication skills are required to deal with ES. The communication skills required
to deal with the challenges of ES are emotional intelligence, cohesion, and empathy
(Alshammari, 2017). Most of the real time interactions can be done with the help of these
communication skills. The collaboration procedure required in each of the business
organization who deals with ES can be optimised with the help of these communication
skills.
6. Case study 1: Improvement of financial security in Telstra using ES
Telstra which is the largest tele-communication industry in Australia has successfully
incorporated a new ES which has helped them to enhance the quality of daily operations. The
entire cloud computing infrastructure was enhanced after ES is introduced in this
organization. There numerous challenges which are faced while incorporating ES in Telstra.
6.1 Advantages
The business operations with the subsidiary organizations of Telstra have improved
after the introduction of ES. The performance of the scalable applications has improved
after the ES successfully incorporated in Telstra. Supervision activities of this business and
the entire IP network of this business are enhanced after this tool is amalgamated in Telstra.
The cutting edge solutions which are provided by this software were also boosted after the
introduction of ES (Enterprise, 2020). The cost of ownership have also enhanced after this
software is installed with the different types of computer systems in this business. The in-
house management of Telstra was improved due to ESs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SECURITY OF ES
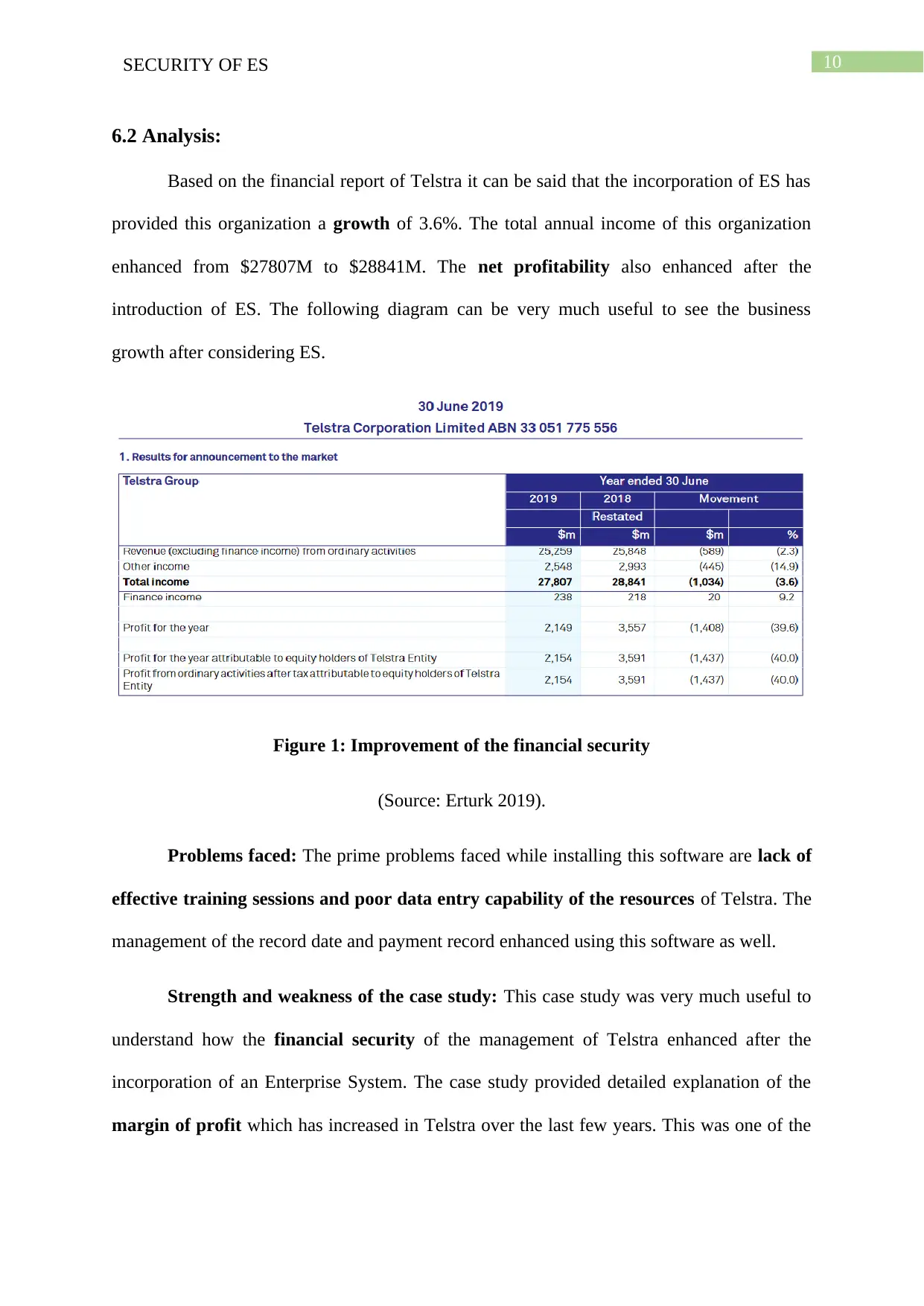
6.2 Analysis:
Based on the financial report of Telstra it can be said that the incorporation of ES has
provided this organization a growth of 3.6%. The total annual income of this organization
enhanced from $27807M to $28841M. The net profitability also enhanced after the
introduction of ES. The following diagram can be very much useful to see the business
growth after considering ES.
Figure 1: Improvement of the financial security
(Source: Erturk 2019).
Problems faced: The prime problems faced while installing this software are lack of
effective training sessions and poor data entry capability of the resources of Telstra. The
management of the record date and payment record enhanced using this software as well.
Strength and weakness of the case study: This case study was very much useful to
understand how the financial security of the management of Telstra enhanced after the
incorporation of an Enterprise System. The case study provided detailed explanation of the
margin of profit which has increased in Telstra over the last few years. This was one of the
6.2 Analysis:
Based on the financial report of Telstra it can be said that the incorporation of ES has
provided this organization a growth of 3.6%. The total annual income of this organization
enhanced from $27807M to $28841M. The net profitability also enhanced after the
introduction of ES. The following diagram can be very much useful to see the business
growth after considering ES.
Figure 1: Improvement of the financial security
(Source: Erturk 2019).
Problems faced: The prime problems faced while installing this software are lack of
effective training sessions and poor data entry capability of the resources of Telstra. The
management of the record date and payment record enhanced using this software as well.
Strength and weakness of the case study: This case study was very much useful to
understand how the financial security of the management of Telstra enhanced after the
incorporation of an Enterprise System. The case study provided detailed explanation of the
margin of profit which has increased in Telstra over the last few years. This was one of the
11SECURITY OF ES
most engaging content of the case study. There are no real limitations in this case study as it
discusses the general problems which were faced while incorporating the software as well.
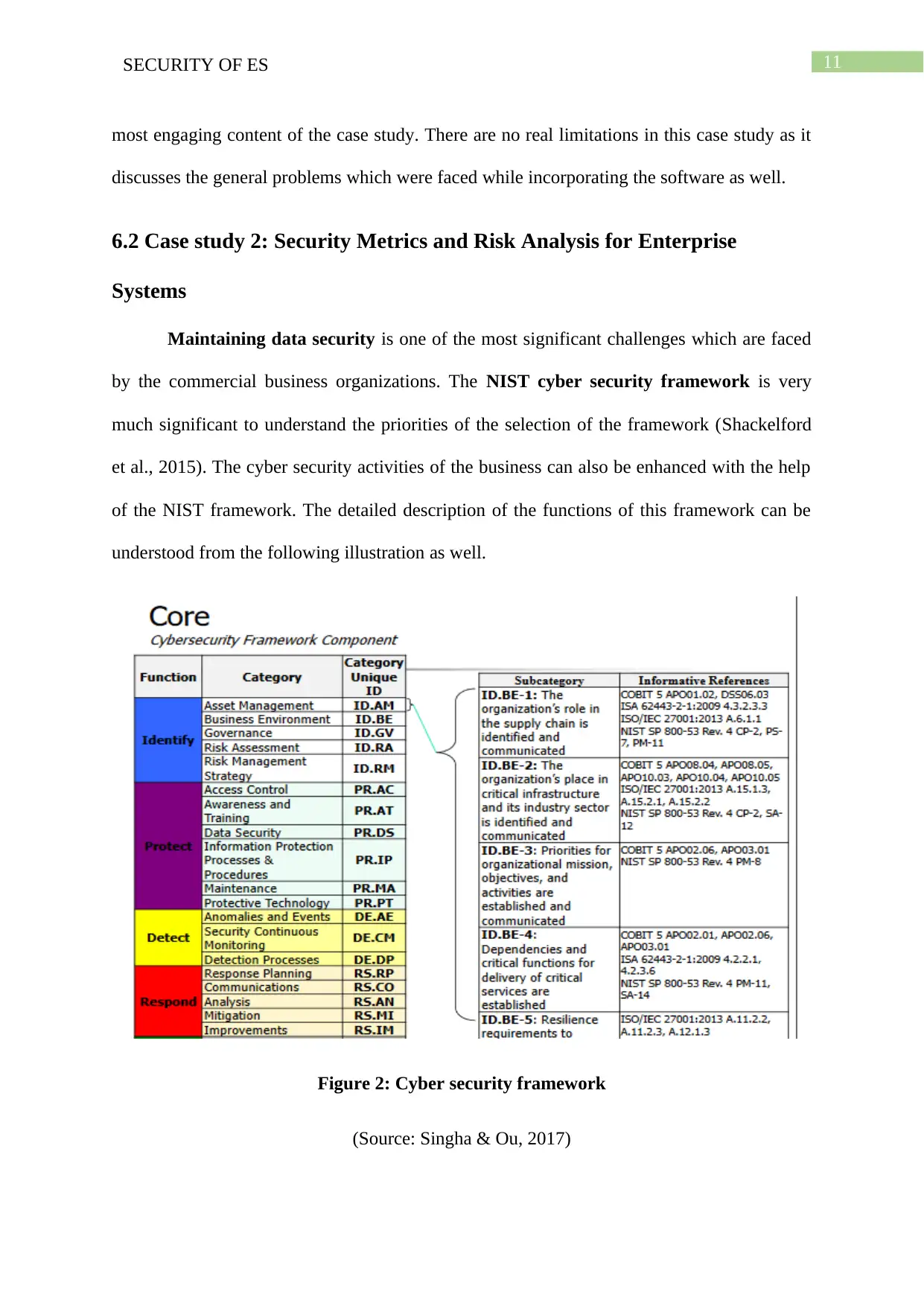
6.2 Case study 2: Security Metrics and Risk Analysis for Enterprise
Systems
Maintaining data security is one of the most significant challenges which are faced
by the commercial business organizations. The NIST cyber security framework is very
much significant to understand the priorities of the selection of the framework (Shackelford
et al., 2015). The cyber security activities of the business can also be enhanced with the help
of the NIST framework. The detailed description of the functions of this framework can be
understood from the following illustration as well.
Figure 2: Cyber security framework
(Source: Singha & Ou, 2017)
most engaging content of the case study. There are no real limitations in this case study as it
discusses the general problems which were faced while incorporating the software as well.
6.2 Case study 2: Security Metrics and Risk Analysis for Enterprise
Systems
Maintaining data security is one of the most significant challenges which are faced
by the commercial business organizations. The NIST cyber security framework is very
much significant to understand the priorities of the selection of the framework (Shackelford
et al., 2015). The cyber security activities of the business can also be enhanced with the help
of the NIST framework. The detailed description of the functions of this framework can be
understood from the following illustration as well.
Figure 2: Cyber security framework
(Source: Singha & Ou, 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





