Analysis of Security Events in Large-Scale Networks: A Report
VerifiedAdded on 2022/08/16
|17
|981
|20
Report
AI Summary
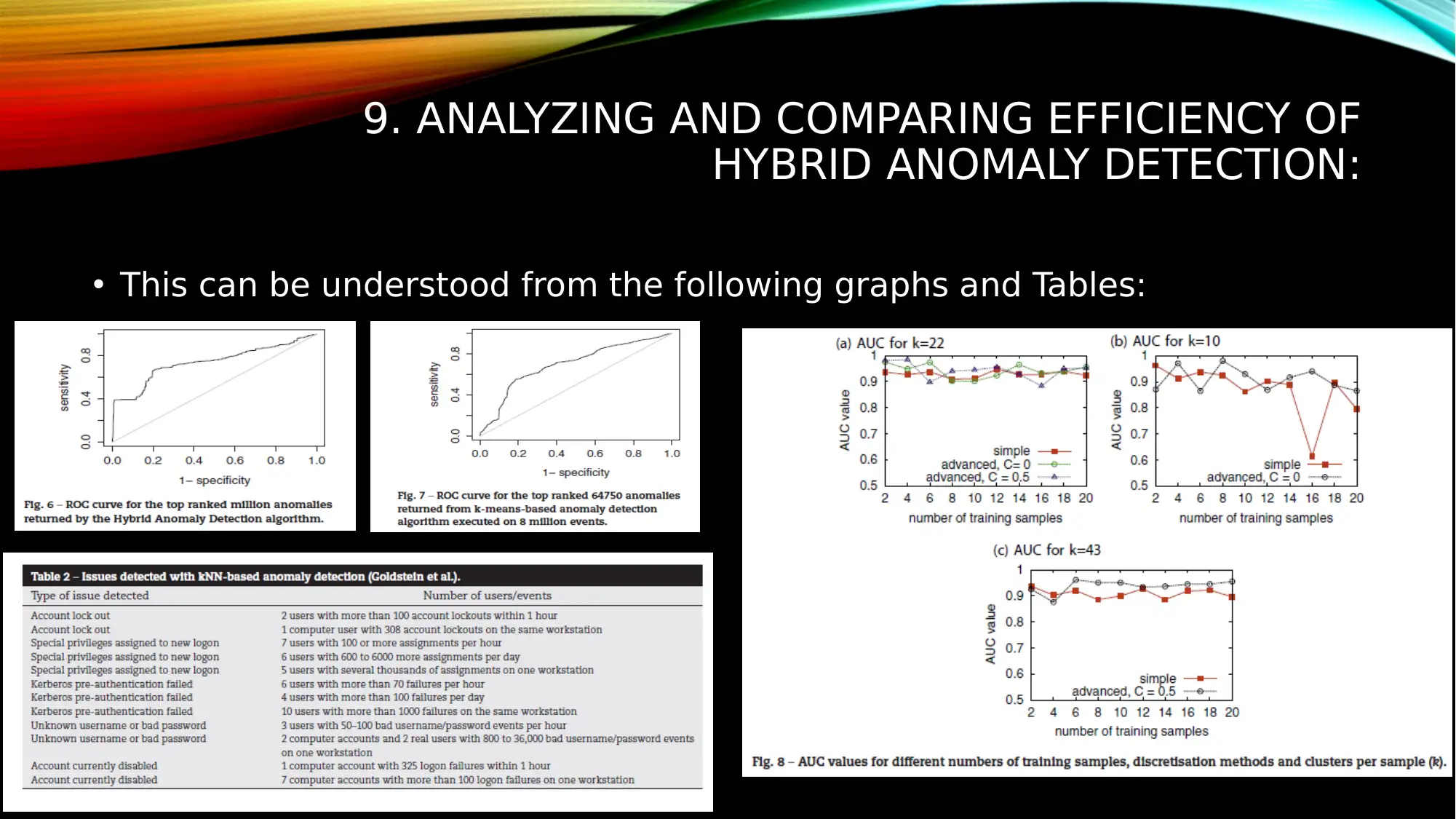
This report analyzes an article that discusses a system for the complex analysis of security events in large-scale networks. The study addresses issues with current SIEM (Security Information and Event Management) systems, such as data normalization problems, false positives, and prolonged processing times, especially in large networks with vast amounts of security events. The report highlights the system's contributions, including converting heterogeneous data to a unique format, employing a hybrid approach for security analytics, and proposing a novel algorithm for unsupervised anomaly detection. The system supports the collection of security events from various sources and utilizes signatures, queries, and anomaly detection to identify suspicious activities. The report also includes the system's testing on real datasets and KDD Cup 1999 data, demonstrating its efficiency and scalability in detecting malicious activities and providing valuable insights for SIEM system operators. The conclusion emphasizes the relevance of the algorithms and architectures used in the SIEM system prototype for analyzing Big Data security and its applicability to large enterprise networks.
1 out of 17


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)