An Empirical Study into Security Exposure of Virtualized Environments
VerifiedAdded on 2020/02/03
|33
|7577
|40
Report
AI Summary
This report presents an empirical study focused on the security exposure of virtualized environments, particularly those running on x86 systems. The research employs a combination of source code auditing and black box random testing to assess vulnerabilities in popular virtual machine implementations. The study explores the potential for security breaches when running hostile or hazardous code within virtual machines, highlighting the increased risks associated with implementation flaws. The report details the testing methodologies, including the use of tools like Crashme and Iofuzz, and the evaluation of various virtual machine emulators like Bochs, QEMU, VMware, and Xen. It also categorizes potential threats, such as total, partial, and abnormal termination compromises, providing an overview of the testing procedures and tools employed. The findings, including specific vulnerabilities identified in QEMU, are presented and analyzed, offering insights into the security landscape of virtualized environments.

An Empirical Study into the Security Exposure to Hosts
of Hostile Virtualized Environments
of Hostile Virtualized Environments
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
As virtual machines become increasingly commonplace as a method of
separating hostile or hazardous code from commodity systems, the potential
security exposure from implementation flaws has increased dramatically. This
report investigates the state of popular virtual machine implementations for x86
systems, employing a combination of source code auditing and black box random
testing to assess the security exposure to the hosts of hostile virtualized
environments.
As virtual machines become increasingly commonplace as a method of
separating hostile or hazardous code from commodity systems, the potential
security exposure from implementation flaws has increased dramatically. This
report investigates the state of popular virtual machine implementations for x86
systems, employing a combination of source code auditing and black box random
testing to assess the security exposure to the hosts of hostile virtualized
environments.

I. INTRODUCTION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Secure isolation comes from virtulization , which is programmed in some limits for virtualized
environment, it gives permission to the hosts that any other action inside the virtual machine will
not interfere with the system and virtual machine immediately change on some situation when hosts
are seperated from a hostile.
When untrusted code and data is displayed or is being loaded so we can prefer virtualized
environment hostile inside the second system of virtual machine. Benefit of virtual machine is
malware analysis is written[22][11].as per the numeric proposals for launching different
applications i.e. honeypots and intrusion detection system.
This data is written to show you that to safely test the asumptions of isolation and for practice is
containment through the survey of popular virtual machine updates or implement for the x86
structure in todays use.its already used cooncept and ferrie alsowrite that a flaw in the VMware
workstation at NAT service that is the final output for compromising the host machine[24] and
some small other research has been published as above area.
I . Virtual machine threats
a) Root secure monitors :
Comodity operating systems can be compromised and privileges escalated[18], it is
absolutely needed when a root secure is used in the virtual machine monitor.it means their's no
privilege to access or interaction any other peoples with the hosts system.
b) Detection :
It is well described by the other researchers[22].Virtual machine analysis should have the
environment that have to be tested on risk changing on emulated code. An emulated code can select
to perfom beingly.i.e, when physical machine is being loaded then it have to be immeadiately
perfom on some malicious actions.
Detection wil not prefer any further in this document, so detect a virtual machine ,or
particularly for the implementation for virtual machine can be prerequisite for the critical attacks
which are tested if any difficulty to determine that how to remove the behaviour of the virtual
machine.
c) Security Threats :
environment, it gives permission to the hosts that any other action inside the virtual machine will
not interfere with the system and virtual machine immediately change on some situation when hosts
are seperated from a hostile.
When untrusted code and data is displayed or is being loaded so we can prefer virtualized
environment hostile inside the second system of virtual machine. Benefit of virtual machine is
malware analysis is written[22][11].as per the numeric proposals for launching different
applications i.e. honeypots and intrusion detection system.
This data is written to show you that to safely test the asumptions of isolation and for practice is
containment through the survey of popular virtual machine updates or implement for the x86
structure in todays use.its already used cooncept and ferrie alsowrite that a flaw in the VMware
workstation at NAT service that is the final output for compromising the host machine[24] and
some small other research has been published as above area.
I . Virtual machine threats
a) Root secure monitors :
Comodity operating systems can be compromised and privileges escalated[18], it is
absolutely needed when a root secure is used in the virtual machine monitor.it means their's no
privilege to access or interaction any other peoples with the hosts system.
b) Detection :
It is well described by the other researchers[22].Virtual machine analysis should have the
environment that have to be tested on risk changing on emulated code. An emulated code can select
to perfom beingly.i.e, when physical machine is being loaded then it have to be immeadiately
perfom on some malicious actions.
Detection wil not prefer any further in this document, so detect a virtual machine ,or
particularly for the implementation for virtual machine can be prerequisite for the critical attacks
which are tested if any difficulty to determine that how to remove the behaviour of the virtual
machine.
c) Security Threats :
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the level of treats are publish by a hostile virtulaized envrionment that can turn in the easy action of
virtual machine is classified as under
=> Total Compromise : the virtual machine is turn whole process to display the arbitrary code
on the hosts with the privileges of the process of vmm.
=> Partial compromise : the hostile process can be interefere with vmm .or vmm can go for to
provide very sesitive info.(for example : grant more resources which are restricted from the admin.)
=>Abnormal termination : the virtual machine monitor can be closed without any expectation or
triggers can be run to the infinite continuity which prevents on host of admin from the interaction of
virtual machine.(i.e., suspending, rolling back , etc.)
=> Overview : other infomation for testing procedure and tools will be defined used in next
stage. Section IV displays the final output of testing and in section X those final outputs are
analyzed . Regarding this all is knows to the author is explained in the section VI , and my
conclusion are shown to you in the section V.
virtual machine is classified as under
=> Total Compromise : the virtual machine is turn whole process to display the arbitrary code
on the hosts with the privileges of the process of vmm.
=> Partial compromise : the hostile process can be interefere with vmm .or vmm can go for to
provide very sesitive info.(for example : grant more resources which are restricted from the admin.)
=>Abnormal termination : the virtual machine monitor can be closed without any expectation or
triggers can be run to the infinite continuity which prevents on host of admin from the interaction of
virtual machine.(i.e., suspending, rolling back , etc.)
=> Overview : other infomation for testing procedure and tools will be defined used in next
stage. Section IV displays the final output of testing and in section X those final outputs are
analyzed . Regarding this all is knows to the author is explained in the section VI , and my
conclusion are shown to you in the section V.

II. TESTING
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

All the three virtual machine imitator which are selected for this particular investigation are open
source software, which are permitting the analysis that is manual analysis of the codes by the
inspection of the particular sections for the error in programming. The leftover software are branded
software products which are distributed without the availability of the source code, therefore an
automated blackbox testing procedure which is based on the fuzz technique innovator by
Miller,fredriksen and so[1] was designed.
By the help of comparison of metrics two new subsystems were identified, that are the most
complex and difficult components of the virtual machine emulators. It was believed that most of the
complex codes are most likely to harbour the subtle bugs that can be exposed through random
testing methods of blackbox which are employed here. The identified subsystems are:
Instructions; that are correctly parsing and trapping privileged instructions, which can
handle unrecognised, illegal and faulting opcodes correctly.
Emulated I/O devices; used to handle invalid, illegal or nonsensical I/O activity.
Different tools were selected and then written to run this code in the exact manner as [1]. The two
main tools which are employed during the investigation were crashme[26], and iofuzz.
A. CRASHME
The testing of hardware and their operating systems robustness to deformed, nonsensical or illegal
instructions has been referenced[27] very well, and those tolls are already a part of the operating
system test suites which is common, such as Linux Test Project. Wood and Katz[16] has been
projected validating cache controllers with very random entry of data as early as 1990. for the only
purpose of this investigation, the easy user mode tool crashme which was by George Carrette was
selected. Crashme which was subjected to the emulated environment to a stress test of handling the
fault by attempting continuously to execute this byte sequence until it encountered the failure.
B. IOFUZZ
The implementation of the accurate emulation of a hardware device into the software device is
beyond question very difficult and challenging task, whether this is correct or not, they are not
bothered about that, only the handling of the illegal and invalid operations. A simple tool was
developed which was modeled on this fuzz to generate some random I/O port activity inside the
virtual machines, and any type of error encountered were listed and analysed.
According to the knowledge of author, no testing has been performed before which is similar
source software, which are permitting the analysis that is manual analysis of the codes by the
inspection of the particular sections for the error in programming. The leftover software are branded
software products which are distributed without the availability of the source code, therefore an
automated blackbox testing procedure which is based on the fuzz technique innovator by
Miller,fredriksen and so[1] was designed.
By the help of comparison of metrics two new subsystems were identified, that are the most
complex and difficult components of the virtual machine emulators. It was believed that most of the
complex codes are most likely to harbour the subtle bugs that can be exposed through random
testing methods of blackbox which are employed here. The identified subsystems are:
Instructions; that are correctly parsing and trapping privileged instructions, which can
handle unrecognised, illegal and faulting opcodes correctly.
Emulated I/O devices; used to handle invalid, illegal or nonsensical I/O activity.
Different tools were selected and then written to run this code in the exact manner as [1]. The two
main tools which are employed during the investigation were crashme[26], and iofuzz.
A. CRASHME
The testing of hardware and their operating systems robustness to deformed, nonsensical or illegal
instructions has been referenced[27] very well, and those tolls are already a part of the operating
system test suites which is common, such as Linux Test Project. Wood and Katz[16] has been
projected validating cache controllers with very random entry of data as early as 1990. for the only
purpose of this investigation, the easy user mode tool crashme which was by George Carrette was
selected. Crashme which was subjected to the emulated environment to a stress test of handling the
fault by attempting continuously to execute this byte sequence until it encountered the failure.
B. IOFUZZ
The implementation of the accurate emulation of a hardware device into the software device is
beyond question very difficult and challenging task, whether this is correct or not, they are not
bothered about that, only the handling of the illegal and invalid operations. A simple tool was
developed which was modeled on this fuzz to generate some random I/O port activity inside the
virtual machines, and any type of error encountered were listed and analysed.
According to the knowledge of author, no testing has been performed before which is similar
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
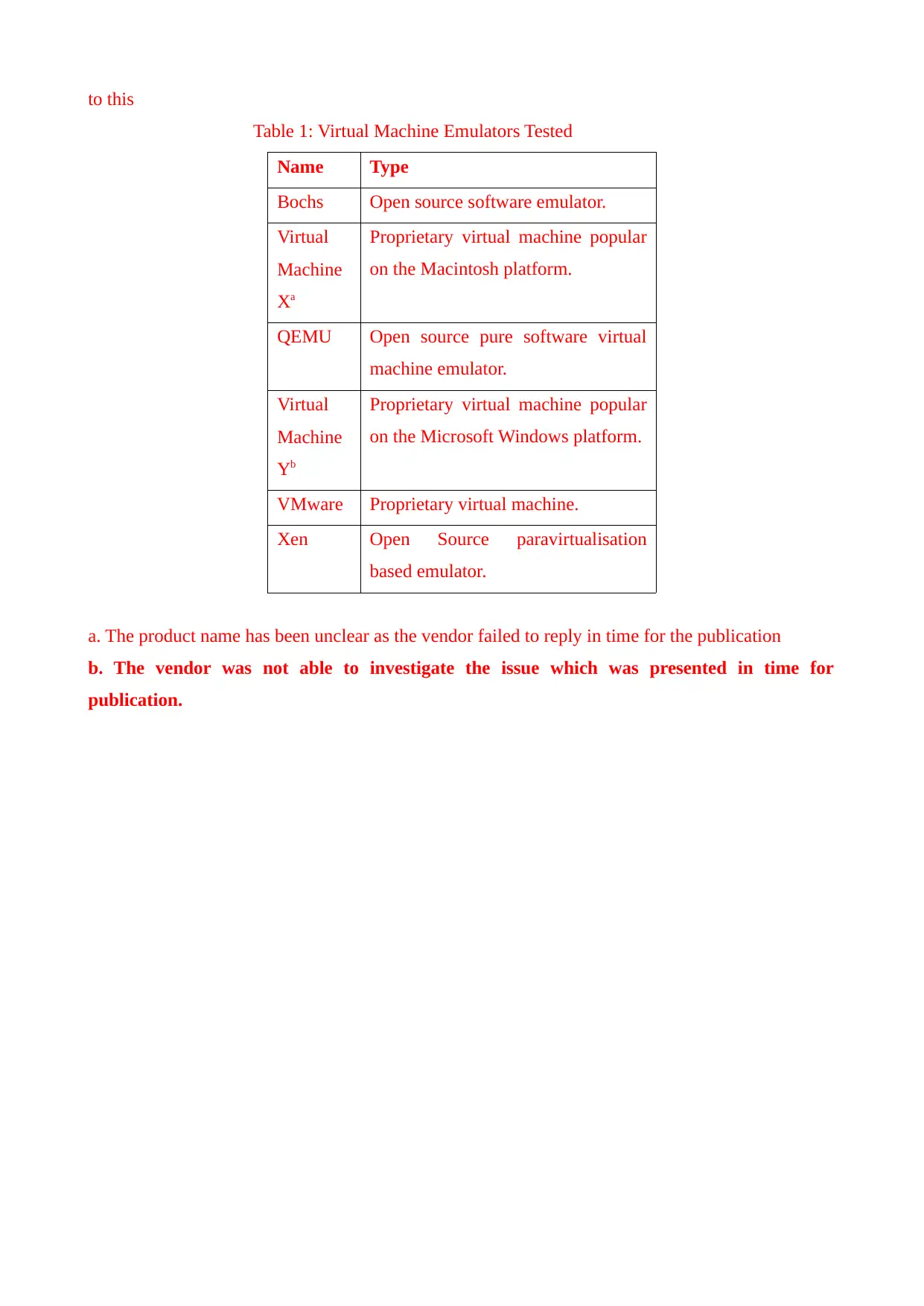
to this
Table 1: Virtual Machine Emulators Tested
Name Type
Bochs Open source software emulator.
Virtual
Machine
Xa
Proprietary virtual machine popular
on the Macintosh platform.
QEMU Open source pure software virtual
machine emulator.
Virtual
Machine
Yb
Proprietary virtual machine popular
on the Microsoft Windows platform.
VMware Proprietary virtual machine.
Xen Open Source paravirtualisation
based emulator.
a. The product name has been unclear as the vendor failed to reply in time for the publication
b. The vendor was not able to investigate the issue which was presented in time for
publication.
Table 1: Virtual Machine Emulators Tested
Name Type
Bochs Open source software emulator.
Virtual
Machine
Xa
Proprietary virtual machine popular
on the Macintosh platform.
QEMU Open source pure software virtual
machine emulator.
Virtual
Machine
Yb
Proprietary virtual machine popular
on the Microsoft Windows platform.
VMware Proprietary virtual machine.
Xen Open Source paravirtualisation
based emulator.
a. The product name has been unclear as the vendor failed to reply in time for the publication
b. The vendor was not able to investigate the issue which was presented in time for
publication.

III. PROCEDUREA. Test platform
In typical commodity system all test were performed (by taking exception of virtual machine
Y which supports only Microsoft Windows hosts) on Pentium IV 3.2GHs running a Linux 2.6 based
operating system. Use the default configuration there were latest version of virtual machine which
were tested and written and than were as default configuration. The option selected which have
been described in relevant sections, when some minimal configuration were required.
To the respective developers were reported the result of investigation from which all flaw were
identified. Patches were provided from the case of open source implementations. At the time of
presenting the report two vendors were unable to respond, so from reminder of the report names of
their product have been obscured.
B. Failure Criteria
if emulated code in the visualization than implementation is considered that automated tests have
failed to perform. For the abnormal exist environment can crash or cause the emulator. Impact
determined of each crash (which is reproduced and investigated) is classified as full, partial or
minor compromise defined as above.
A privileged user may legitimately request the emulated machine is halted in the virtualized
environment, causing the emulator to crash is not necessarily a security law.
From the implication of malware analysis, no effect on physical machine when hostle sample
perform some harmless operations but halts immediately any emulator being used to analysis it.
As per the quality of the code and amount of testing perform this can be considered as a simple
litmus test. A good candidate for further research and unlikely to have seen testing significant
testing is an implementation of continually crashes or aborts. Where the weakest code exist and
where future research may prove to be most fruitful by carefully analyzing any crashes
encountered which may be determined.
C. Testing Procedure
A source code audit is performed to identify as many flaws as possible, where source code is
available. The audit involves a human researcher which is familiar with programming error to
identifying possible code paths that could research in security problems and also it reading source
code manually. Any flaws identified which reproduced in a live environment and documented,
while one the audit has been completed.
Secondly, the virtual machine using the crashme utility which had described in section 1 is
subjected to stress testing. The test continues until run without error, the error is reproduced, and
then analyse and then corrected. The test continues for 24 hours.
In typical commodity system all test were performed (by taking exception of virtual machine
Y which supports only Microsoft Windows hosts) on Pentium IV 3.2GHs running a Linux 2.6 based
operating system. Use the default configuration there were latest version of virtual machine which
were tested and written and than were as default configuration. The option selected which have
been described in relevant sections, when some minimal configuration were required.
To the respective developers were reported the result of investigation from which all flaw were
identified. Patches were provided from the case of open source implementations. At the time of
presenting the report two vendors were unable to respond, so from reminder of the report names of
their product have been obscured.
B. Failure Criteria
if emulated code in the visualization than implementation is considered that automated tests have
failed to perform. For the abnormal exist environment can crash or cause the emulator. Impact
determined of each crash (which is reproduced and investigated) is classified as full, partial or
minor compromise defined as above.
A privileged user may legitimately request the emulated machine is halted in the virtualized
environment, causing the emulator to crash is not necessarily a security law.
From the implication of malware analysis, no effect on physical machine when hostle sample
perform some harmless operations but halts immediately any emulator being used to analysis it.
As per the quality of the code and amount of testing perform this can be considered as a simple
litmus test. A good candidate for further research and unlikely to have seen testing significant
testing is an implementation of continually crashes or aborts. Where the weakest code exist and
where future research may prove to be most fruitful by carefully analyzing any crashes
encountered which may be determined.
C. Testing Procedure
A source code audit is performed to identify as many flaws as possible, where source code is
available. The audit involves a human researcher which is familiar with programming error to
identifying possible code paths that could research in security problems and also it reading source
code manually. Any flaws identified which reproduced in a live environment and documented,
while one the audit has been completed.
Secondly, the virtual machine using the crashme utility which had described in section 1 is
subjected to stress testing. The test continues until run without error, the error is reproduced, and
then analyse and then corrected. The test continues for 24 hours.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

As the results are collected and tabulated and to the minimum serious of peek and pokes any
failures are reduced because of machine subjected to 24 hours iofuzz.
failures are reduced because of machine subjected to 24 hours iofuzz.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table 2: Virtual Machine Failure Impact
Name Full Partial Minor
Bochs • •
Virtual Machine Xa • • •
QEMU•b verified, as the fix would be the same. • •
Virtual Machine Y • •
VMware • • •
Xen •c
a. See “Test platform”.
b.these flaws may impact other implementations derived rom the same code.
c. due to lack of appropriate hardware, these findings were not tested.
A. QEMU
QEMU is based upon the generic and open source machine emulator and visualizer. It can run
oses as well as programs made for one machine on another machine. It achieves very good
translation by dynamic translator. It is distributed under the GPL license. It speeds up many
advance features that offers better performance.
QEMU 0.8.2 is the latest version. It utilizes virtual machine and the life cycle. For testing a
bootable ISO image is prepared within the software. The utility allows to start, to stop and to
migrate VM's between host. QEMU runs a daemon that enforce the policy to run Vms given by a
set of config files.
QEMU Cirrus CLGD-54XX “bitblt ” heap overflow
cirrus VGA extension code uses during video to video copy operations to bound checking at
more than one location. As in the above mention table 4 allows the overwriting of adjacent
buffers through attempting to mark non existent as a dirt. Whereas, the overflowing data is not
controllable. LSB allows the overflow of function pointers.
QEMU NE2000 “mtu ” heap overflow
Ethernet frames has directly written into the device known as NE2000 which is register not to
check against mtu before it has been transferred. As per table 5 it shows large result in
ENO_TCNT overlap of heap buffer in slirp with controllable data from memory bank device.
NIC is the alternate way to emulate through QEMU.
QEMU NE2000 “receive” integer signedness error
An particular device is used to nonsensical values so that they can result in sanit checks. As
above in the table 6 it can be seen that the overflowing a neap buffer data controllable.
QEMU is net socket overflow of heap.
QEMU performance is not adequate by data received through net socket listen. It results in the
overflow of exploitation heap overflow. QEMU process should compromise the traffic who send
or who are local attackers.
QEMU Miscellaneous
Name Full Partial Minor
Bochs • •
Virtual Machine Xa • • •
QEMU•b verified, as the fix would be the same. • •
Virtual Machine Y • •
VMware • • •
Xen •c
a. See “Test platform”.
b.these flaws may impact other implementations derived rom the same code.
c. due to lack of appropriate hardware, these findings were not tested.
A. QEMU
QEMU is based upon the generic and open source machine emulator and visualizer. It can run
oses as well as programs made for one machine on another machine. It achieves very good
translation by dynamic translator. It is distributed under the GPL license. It speeds up many
advance features that offers better performance.
QEMU 0.8.2 is the latest version. It utilizes virtual machine and the life cycle. For testing a
bootable ISO image is prepared within the software. The utility allows to start, to stop and to
migrate VM's between host. QEMU runs a daemon that enforce the policy to run Vms given by a
set of config files.
QEMU Cirrus CLGD-54XX “bitblt ” heap overflow
cirrus VGA extension code uses during video to video copy operations to bound checking at
more than one location. As in the above mention table 4 allows the overwriting of adjacent
buffers through attempting to mark non existent as a dirt. Whereas, the overflowing data is not
controllable. LSB allows the overflow of function pointers.
QEMU NE2000 “mtu ” heap overflow
Ethernet frames has directly written into the device known as NE2000 which is register not to
check against mtu before it has been transferred. As per table 5 it shows large result in
ENO_TCNT overlap of heap buffer in slirp with controllable data from memory bank device.
NIC is the alternate way to emulate through QEMU.
QEMU NE2000 “receive” integer signedness error
An particular device is used to nonsensical values so that they can result in sanit checks. As
above in the table 6 it can be seen that the overflowing a neap buffer data controllable.
QEMU is net socket overflow of heap.
QEMU performance is not adequate by data received through net socket listen. It results in the
overflow of exploitation heap overflow. QEMU process should compromise the traffic who send
or who are local attackers.
QEMU Miscellaneous

• The loop was found in emulated SB16 device.
• Uninitialized function of pointer will deference the DMA code. It will happen only when the
command will be passed or given to the unregistered DMA channel.
• as ain above table 7 undocumented divisor operand will incorrectly handled the instruction .
• unprivileged ‘icebp’ are the 1 instruction which will halt the virtual machine, it cannot be disabled.
See Table 8.
• VGA BIOS use to ignored safely according to the document accompanying Bochs, but it
immediately causes QEMU . Bochs prompts the user to continue or not on encountering a panic.
• BIOS panics can be ignored, but at immediate exist of QEMU.
•signedness errors of Multiple integer exist in the IDE controller, it allows large count to by pass
sanity checks.
Summary
Malware being studied inside QEMU, even in an unprivileged state, can terminate the virtual
machine safely and reliably. Code examples of these flaws are provided in Section X. attacker asses
to QEMU virtualized environment. The virtual machine exicute process. In sextion x the code
example are provided.
B. VMware Workstation and Server
VMware is a family of popular proprietary virtual machine emulators for the x86 platform. The two
VMware Workstation and VMware Server are the major product. major products Workstation and
Server were studied during this investigation. As source code is not freely available for these
programs, the focus was on random testing, followed by the analysis of any anomalies encountered.
The latest version of VMware Workstation available at time of writing was 5.5.3.34685, and
VMware Server was 1.0.1.29996. These were used in as close to the default configuration as
possible.
VMware Security
the security affecting Vulnerabilities the host of a VMware virtual machine have published before.
In 2005 reported a heap overflow in the vmnatd service[24], where a specially crafted EPRT or
PORT FTP command would result in an exploitable heap overflow, it allows hostile virtualized
code to compromise and thus execute code on the host machine.
the guest and host use the commucication to connect., and while officially undocumented, has been
successfully reverse documented by several researchers and is known as the “VMware
Backdoor”[29].
Hence we can say the this channel allow hostile guest to steal clipboard data. The information
about the host can be dangerous operations. Care should be taken to hostile machine.
Attacker access to a QEMU virtualized environment can effectively compromise the process of
virtual machine and emulate with previlegers. Malware
• Uninitialized function of pointer will deference the DMA code. It will happen only when the
command will be passed or given to the unregistered DMA channel.
• as ain above table 7 undocumented divisor operand will incorrectly handled the instruction .
• unprivileged ‘icebp’ are the 1 instruction which will halt the virtual machine, it cannot be disabled.
See Table 8.
• VGA BIOS use to ignored safely according to the document accompanying Bochs, but it
immediately causes QEMU . Bochs prompts the user to continue or not on encountering a panic.
• BIOS panics can be ignored, but at immediate exist of QEMU.
•signedness errors of Multiple integer exist in the IDE controller, it allows large count to by pass
sanity checks.
Summary
Malware being studied inside QEMU, even in an unprivileged state, can terminate the virtual
machine safely and reliably. Code examples of these flaws are provided in Section X. attacker asses
to QEMU virtualized environment. The virtual machine exicute process. In sextion x the code
example are provided.
B. VMware Workstation and Server
VMware is a family of popular proprietary virtual machine emulators for the x86 platform. The two
VMware Workstation and VMware Server are the major product. major products Workstation and
Server were studied during this investigation. As source code is not freely available for these
programs, the focus was on random testing, followed by the analysis of any anomalies encountered.
The latest version of VMware Workstation available at time of writing was 5.5.3.34685, and
VMware Server was 1.0.1.29996. These were used in as close to the default configuration as
possible.
VMware Security
the security affecting Vulnerabilities the host of a VMware virtual machine have published before.
In 2005 reported a heap overflow in the vmnatd service[24], where a specially crafted EPRT or
PORT FTP command would result in an exploitable heap overflow, it allows hostile virtualized
code to compromise and thus execute code on the host machine.
the guest and host use the commucication to connect., and while officially undocumented, has been
successfully reverse documented by several researchers and is known as the “VMware
Backdoor”[29].
Hence we can say the this channel allow hostile guest to steal clipboard data. The information
about the host can be dangerous operations. Care should be taken to hostile machine.
Attacker access to a QEMU virtualized environment can effectively compromise the process of
virtual machine and emulate with previlegers. Malware
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
