Security and Forensics: Software Acquisition, Threats, and Strategy
VerifiedAdded on 2022/12/18
|16
|4363
|457
Report
AI Summary
This report provides a comprehensive analysis of information security practices, addressing software acquisition models, threat assessments, and security strategy development. It begins by comparing and contrasting different software acquisition models, including in-house development, outsourcing, and purchasing off-the-shelf systems, highlighting their respective advantages and disadvantages. The report then evaluates existing security handbooks, identifying missing elements in network activity monitoring policies and discussing potential legal issues. Furthermore, it outlines the information security strategic plan in place and assesses both external and internal threats, proposing a risk assessment methodology with a flowchart-like figure and discussing risk management strategies. The access control strategy is critically analyzed, with recommendations for improvements, and an incident management strategy is proposed. Finally, the report compiles a brief security strategy tailored to business and security requirements.

ahmed choudhary
SECURITY AND FORENSICS
SECURITY AND FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Assignment 1...........................................................................................................................................1
Critically analyse the different types of software acquisition models and try to relate that to
those systems you are using at your workplace.................................................................................. 1
Do you have a handbook that describes the policies, processes, and procedures in place?
Evaluate the security strategy in that handbook for network activity monitoring, for
instance? What are the issues missing in the handbook? You need to discuss the legal issues
raised by this handbook as many companies consider a handbook as part of the contract.......4
What is the information security strategic plan in place and how it is implemented?................5
Analyse the external and internal threats to information systems in your workplace and show
how your security strategy should protect against those threats. Report your risk assessment
methodology in a flowchart-like figure. You can have a look at Stoneburner (2002) work to
understand how you should relate all the activities together. Please do not copy the work from
(Stoneburner, 2002) as you need to compile your own risk assessment methodology as part of
your security strategy plan. You also need to discuss how you are going to manage the
identified risks........................................................................................................................................... 6
Critically analyse the access control strategy? If you are to rewrite that part of your security
plan, what would you change? Why? What sort of a strategy you will use here? proactive or
reactive? Justify your answer................................................................................................................. 8
What do you recommend for a proper incident management strategy? How would you
implement it? Hint: Stakeholders and role responsibilities..............................................................9
Compile a brief security strategy that suits the business requirements as well as the security
requirements of this workplace........................................................................................................... 10
References.............................................................................................................................................14
Assignment 1...........................................................................................................................................1
Critically analyse the different types of software acquisition models and try to relate that to
those systems you are using at your workplace.................................................................................. 1
Do you have a handbook that describes the policies, processes, and procedures in place?
Evaluate the security strategy in that handbook for network activity monitoring, for
instance? What are the issues missing in the handbook? You need to discuss the legal issues
raised by this handbook as many companies consider a handbook as part of the contract.......4
What is the information security strategic plan in place and how it is implemented?................5
Analyse the external and internal threats to information systems in your workplace and show
how your security strategy should protect against those threats. Report your risk assessment
methodology in a flowchart-like figure. You can have a look at Stoneburner (2002) work to
understand how you should relate all the activities together. Please do not copy the work from
(Stoneburner, 2002) as you need to compile your own risk assessment methodology as part of
your security strategy plan. You also need to discuss how you are going to manage the
identified risks........................................................................................................................................... 6
Critically analyse the access control strategy? If you are to rewrite that part of your security
plan, what would you change? Why? What sort of a strategy you will use here? proactive or
reactive? Justify your answer................................................................................................................. 8
What do you recommend for a proper incident management strategy? How would you
implement it? Hint: Stakeholders and role responsibilities..............................................................9
Compile a brief security strategy that suits the business requirements as well as the security
requirements of this workplace........................................................................................................... 10
References.............................................................................................................................................14

Assignment 1
Critically analyse the different types of software acquisition models and try to relate
that to those systems you are using at your workplace.
There is more than one alternative way for organizations to get ISs and IT facilities. It is
becoming increasingly common to buy "canned" software and outsource portions or all of the
corporate IS features. More choices offer more flexibility; however, they make the process of
selection more complex. Each option has distinct pros and cons. The analysis will be done by
comparing and contrasting each of the different acquisition models by listing their pros and
cons. Broadly, there exists three different models. These include the in-house developed
system model, the outsourcing model where the company will outsource it’s requirements
and have an external 3rd party company developed the system for them and thirdly
purchasing a read-made off-the-shelf system (Janert, 2002).
In-house developed system
Advantages
It can be adapted to fulfil the company's precise requirements.
This could be made to suit the particular procedures and organizational culture of an
organization.
It can be intended to operate well with other existing systems.
To keep the system (if you can keep it) you will also have engineers with skills
available.
If competitors don't have access to your technology, there is a potential for strategic
benefit.
It is better compatible with legacy systems that might already be in place.
Disadvantages
The cost of development and maintenance is significant.
Development can take a long time and consume resources that could be spent
elsewhere.
Writing custom applications could make it difficult to use more conventional software
to communicate with other organisations.
Advantages of outsourcing
Critically analyse the different types of software acquisition models and try to relate
that to those systems you are using at your workplace.
There is more than one alternative way for organizations to get ISs and IT facilities. It is
becoming increasingly common to buy "canned" software and outsource portions or all of the
corporate IS features. More choices offer more flexibility; however, they make the process of
selection more complex. Each option has distinct pros and cons. The analysis will be done by
comparing and contrasting each of the different acquisition models by listing their pros and
cons. Broadly, there exists three different models. These include the in-house developed
system model, the outsourcing model where the company will outsource it’s requirements
and have an external 3rd party company developed the system for them and thirdly
purchasing a read-made off-the-shelf system (Janert, 2002).
In-house developed system
Advantages
It can be adapted to fulfil the company's precise requirements.
This could be made to suit the particular procedures and organizational culture of an
organization.
It can be intended to operate well with other existing systems.
To keep the system (if you can keep it) you will also have engineers with skills
available.
If competitors don't have access to your technology, there is a potential for strategic
benefit.
It is better compatible with legacy systems that might already be in place.
Disadvantages
The cost of development and maintenance is significant.
Development can take a long time and consume resources that could be spent
elsewhere.
Writing custom applications could make it difficult to use more conventional software
to communicate with other organisations.
Advantages of outsourcing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Higher level of knowledge of vendor staff could lead in smaller delivery cycles
Access to vendor knowledge and consulting Improved security management owing to
experience
Shorter project development cycles due to vendor knowledge and experience
Fixed IS expenses enable better budgeting for the length of the outsourcing
agreement
Volume discounts agreed by the provider could lead in reduced software costs
The employees of the organization could focus on key areas of the business
IT-related expenses-fixed costs for the seller are distributed over various customers so
that the price per customer is reduced
Risks of outsourcing
Loss of supervisory and control
Loss of skilled employees
Potential loss of competitive edge
The price of subcontracting might be greater than planned, even larger than the
Service Level Agreements (SLAs) of those of in-house developed systems.
The customer must indicate in detail what services are anticipated and the metrics to
be used to evaluate how well the seller provided those facilities.
Purchased (ready-made) applications
Advantages:
Immediately available
Readily available
High-level of Reliability
Low-price support
Disadvantages
May not be a good match for the demands of the organization
Vendor could abandon business
High turnover of vendor staff may nullify any experience benefits
Software licensing may boost total acquisition charges
Access to vendor knowledge and consulting Improved security management owing to
experience
Shorter project development cycles due to vendor knowledge and experience
Fixed IS expenses enable better budgeting for the length of the outsourcing
agreement
Volume discounts agreed by the provider could lead in reduced software costs
The employees of the organization could focus on key areas of the business
IT-related expenses-fixed costs for the seller are distributed over various customers so
that the price per customer is reduced
Risks of outsourcing
Loss of supervisory and control
Loss of skilled employees
Potential loss of competitive edge
The price of subcontracting might be greater than planned, even larger than the
Service Level Agreements (SLAs) of those of in-house developed systems.
The customer must indicate in detail what services are anticipated and the metrics to
be used to evaluate how well the seller provided those facilities.
Purchased (ready-made) applications
Advantages:
Immediately available
Readily available
High-level of Reliability
Low-price support
Disadvantages
May not be a good match for the demands of the organization
Vendor could abandon business
High turnover of vendor staff may nullify any experience benefits
Software licensing may boost total acquisition charges
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As evident from above, each of the models have their own unique strengths and weaknesses
and therefore it entirely depends upon the nature and requirement of the system based on
which the appropriate choice must be made.
Do you have a handbook that describes the policies, processes, and procedures in place?
Evaluate the security strategy in that handbook for network activity monitoring, for
instance? What are the issues missing in the handbook? You need to discuss the legal
issues raised by this handbook as many companies consider a handbook as part of the
contract.
The measures included in the network security policy of the company is appropriately done
for the kind of requirements and the nature of the business. However, given the modern
business environment and the rapid changing state of cyber landscape, there needs to be
additional measures included which would be included. The important elements missing from
the policy are:
Physical safeguards
There is no mention of physical safeguards for the networking hardware and therefore, the
company must take reasonable risk evaluation steps such as fire and water safety, cabinets,
safe shelves, etc. to safeguard networks and communication facilities from accidental harm,
potential abuses, theft or malicious intent. The networking infrastructure should integrate,
wherever feasible, practical and physical resilience elements to reduce the effect of cable and
other networking equipment breakdown or physical harm.
BYOD
Another important piece of policy missing in the network security documentation is the
problem of Bring Your Own Devices. Especially in modern companies, employees are
permitted to carry their own devices and are also allowed to connect to internal servers. This
creates a host of problems from the eyes of security. As a result, there should be a separate
provision in place that handles such cases. As such, such devices must be pre-approved and
should be recognized using a unique ID such as the MAC ID in order to authenticate and
authorize them to the network (Albova, 2017).
and therefore it entirely depends upon the nature and requirement of the system based on
which the appropriate choice must be made.
Do you have a handbook that describes the policies, processes, and procedures in place?
Evaluate the security strategy in that handbook for network activity monitoring, for
instance? What are the issues missing in the handbook? You need to discuss the legal
issues raised by this handbook as many companies consider a handbook as part of the
contract.
The measures included in the network security policy of the company is appropriately done
for the kind of requirements and the nature of the business. However, given the modern
business environment and the rapid changing state of cyber landscape, there needs to be
additional measures included which would be included. The important elements missing from
the policy are:
Physical safeguards
There is no mention of physical safeguards for the networking hardware and therefore, the
company must take reasonable risk evaluation steps such as fire and water safety, cabinets,
safe shelves, etc. to safeguard networks and communication facilities from accidental harm,
potential abuses, theft or malicious intent. The networking infrastructure should integrate,
wherever feasible, practical and physical resilience elements to reduce the effect of cable and
other networking equipment breakdown or physical harm.
BYOD
Another important piece of policy missing in the network security documentation is the
problem of Bring Your Own Devices. Especially in modern companies, employees are
permitted to carry their own devices and are also allowed to connect to internal servers. This
creates a host of problems from the eyes of security. As a result, there should be a separate
provision in place that handles such cases. As such, such devices must be pre-approved and
should be recognized using a unique ID such as the MAC ID in order to authenticate and
authorize them to the network (Albova, 2017).

Remote
There is no mention of networking security for employees or third party remote-connections
such as employees accessing internal servers from remote locations. So, in order to ensure
that there is no harm or abuse over remote connection the company must enable IPSec, SSH
and VPN tunnelling solutions as well as dual-factor authentication to mitigate any
wrongdoings (Salman, 2017).
Apart from the measures missing, the following pieces of measures might create legal issues
for the company:
1. Accessing the user’s information and activity in the information systems when the
user is absent.
2. Accessing the user’s information and activity in the information systems when the
company believes there is a breach of conduct.
3. Accessing the user’s information and activity in the information systems on the
request of legal director.
4. The issue of covert monitoring which is currently undefined as to what level of
monitoring and evidence-extracting activities might be undertaken.
What is the information security strategic plan in place and how it is implemented?
The company has created an information security strategic plan. While there are many
elements in this plan, however it has several essential elements missing from the plan. As a
result of which, the information security strategies would be poorly implemented and the
organization would be at significant risk from internal and external threats as well as
vulnerabilities.
First and foremost, the information security plan begins with classifying the information on
the basis of CIA triad. At the same time, information is also classified on four different levels
starting from publicly freely distributable information right to the secret information which is
absolutely vital and critical to maintain company’s position in the market. The security policy
then highlights the responsibilities of members towards the information they possess and
process and the policy also outlines some of the basics of information protection. The policy
then list downs information labelling and information archiving procedures and measures
There is no mention of networking security for employees or third party remote-connections
such as employees accessing internal servers from remote locations. So, in order to ensure
that there is no harm or abuse over remote connection the company must enable IPSec, SSH
and VPN tunnelling solutions as well as dual-factor authentication to mitigate any
wrongdoings (Salman, 2017).
Apart from the measures missing, the following pieces of measures might create legal issues
for the company:
1. Accessing the user’s information and activity in the information systems when the
user is absent.
2. Accessing the user’s information and activity in the information systems when the
company believes there is a breach of conduct.
3. Accessing the user’s information and activity in the information systems on the
request of legal director.
4. The issue of covert monitoring which is currently undefined as to what level of
monitoring and evidence-extracting activities might be undertaken.
What is the information security strategic plan in place and how it is implemented?
The company has created an information security strategic plan. While there are many
elements in this plan, however it has several essential elements missing from the plan. As a
result of which, the information security strategies would be poorly implemented and the
organization would be at significant risk from internal and external threats as well as
vulnerabilities.
First and foremost, the information security plan begins with classifying the information on
the basis of CIA triad. At the same time, information is also classified on four different levels
starting from publicly freely distributable information right to the secret information which is
absolutely vital and critical to maintain company’s position in the market. The security policy
then highlights the responsibilities of members towards the information they possess and
process and the policy also outlines some of the basics of information protection. The policy
then list downs information labelling and information archiving procedures and measures
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

which nearly concludes the information security policy as a whole. Now, there are many
elements missing in the information security policy and these include the following:
A. The acceptable use of information assets is missing from the policy which
outlines what information owners and employees are allowed or disallowed to
do with information based on the information classification.
B. Another key policy measure missing from the policy statement is the
Information Asset Management Lifecycle (Moon, 2007). This policy measure
describes that all critical assets must be identified, monitored, updated,
upgraded, repaired or discarded on a regular basis.
C. The information security policy also does not include the breach of policy as
to what would happen if people were to breach the policy and for misconduct.
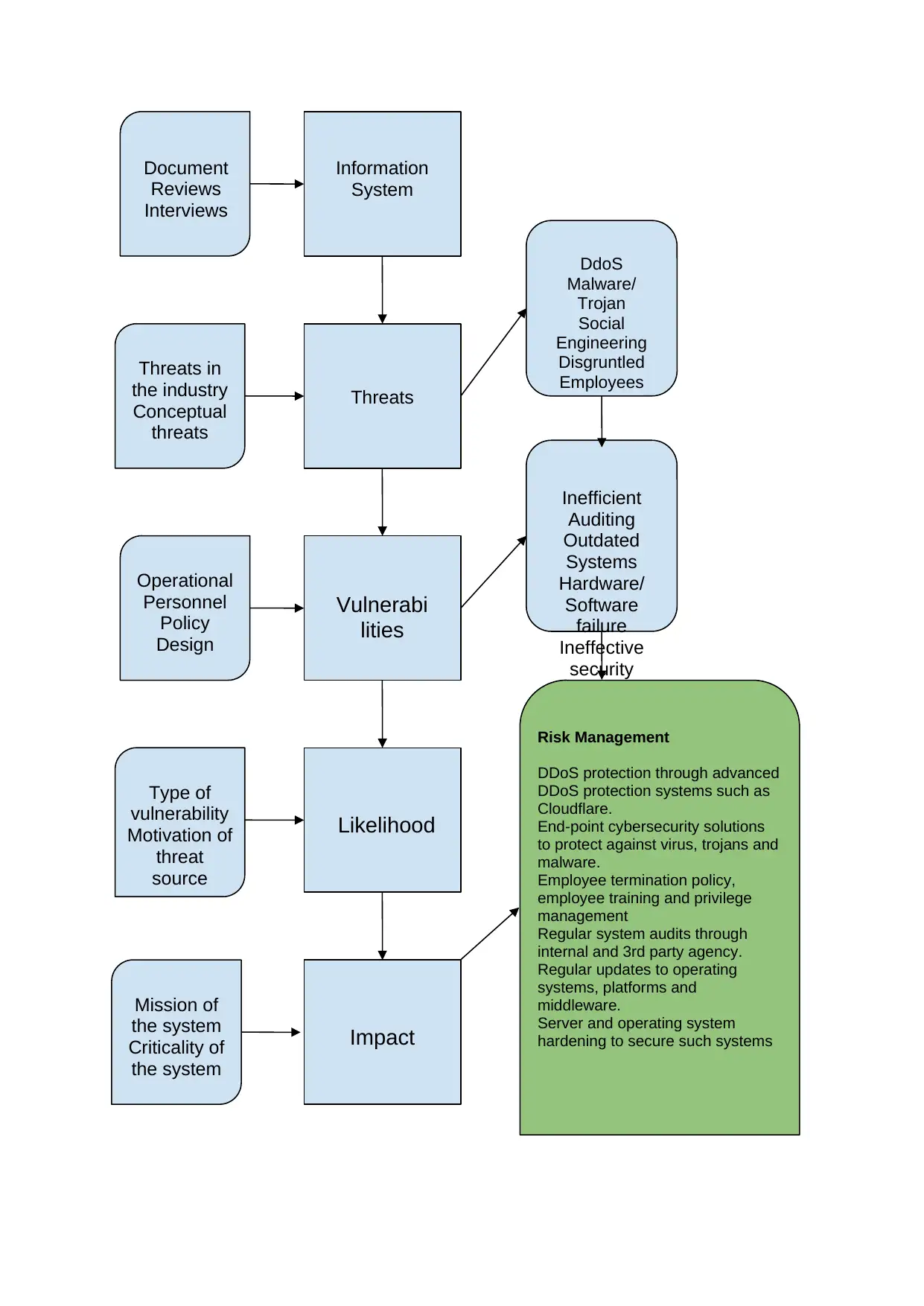
Analyse the external and internal threats to information systems in your workplace and show
how your security strategy should protect against those threats. Report your risk assessment
methodology in a flowchart-like figure. You can have a look at Stoneburner (2002) work to
understand how you should relate all the activities together. Please do not copy the work from
(Stoneburner, 2002) as you need to compile your own risk assessment methodology as part of
your security strategy plan. You also need to discuss how you are going to manage the
identified risks
Internal Threats
Internal risks are the biggest effect on information systems. Inside entities have the right of
access almost all of the organization's resources. As a result, several kinds of harm can be
caused by an employee behavior or failure. These may include current staff, former
employees, contract workers and so on. The type of harm that they can cause could be
anything from deliberate IT infrastructure disruption, to injecting malware into systems, to
helping conduct espionage and so on.
External Threats
The internal threats are caused by groups or individuals operating outside a corporation.
Natural catastrophes are the most existential threats to data systems. External attacks are
triggered by mesh node or physical intrusion. Eg. Calamities, failures caused by man, illegal
users, ransomware, service denial, and so on. These may include DdoS based attacks,
phishing attacks, targeted or random attack from malwares, trojans and viruses and so on.
elements missing in the information security policy and these include the following:
A. The acceptable use of information assets is missing from the policy which
outlines what information owners and employees are allowed or disallowed to
do with information based on the information classification.
B. Another key policy measure missing from the policy statement is the
Information Asset Management Lifecycle (Moon, 2007). This policy measure
describes that all critical assets must be identified, monitored, updated,
upgraded, repaired or discarded on a regular basis.
C. The information security policy also does not include the breach of policy as
to what would happen if people were to breach the policy and for misconduct.
Analyse the external and internal threats to information systems in your workplace and show
how your security strategy should protect against those threats. Report your risk assessment
methodology in a flowchart-like figure. You can have a look at Stoneburner (2002) work to
understand how you should relate all the activities together. Please do not copy the work from
(Stoneburner, 2002) as you need to compile your own risk assessment methodology as part of
your security strategy plan. You also need to discuss how you are going to manage the
identified risks
Internal Threats
Internal risks are the biggest effect on information systems. Inside entities have the right of
access almost all of the organization's resources. As a result, several kinds of harm can be
caused by an employee behavior or failure. These may include current staff, former
employees, contract workers and so on. The type of harm that they can cause could be
anything from deliberate IT infrastructure disruption, to injecting malware into systems, to
helping conduct espionage and so on.
External Threats
The internal threats are caused by groups or individuals operating outside a corporation.
Natural catastrophes are the most existential threats to data systems. External attacks are
triggered by mesh node or physical intrusion. Eg. Calamities, failures caused by man, illegal
users, ransomware, service denial, and so on. These may include DdoS based attacks,
phishing attacks, targeted or random attack from malwares, trojans and viruses and so on.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information
System
Document
Reviews
Interviews
Threats
Vulnerabi
lities
Likelihood
Impact
Threats in
the industry
Conceptual
threats
Operational
Personnel
Policy
Design
Type of
vulnerability
Motivation of
threat
source
Mission of
the system
Criticality of
the system
DdoS
Malware/
Trojan
Social
Engineering
Disgruntled
Employees
Inefficient
Auditing
Outdated
Systems
Hardware/
Software
failure
Ineffective
security
hardening
Risk Management
DDoS protection through advanced
DDoS protection systems such as
Cloudflare.
End-point cybersecurity solutions
to protect against virus, trojans and
malware.
Employee termination policy,
employee training and privilege
management
Regular system audits through
internal and 3rd party agency.
Regular updates to operating
systems, platforms and
middleware.
Server and operating system
hardening to secure such systems
System
Document
Reviews
Interviews
Threats
Vulnerabi
lities
Likelihood
Impact
Threats in
the industry
Conceptual
threats
Operational
Personnel
Policy
Design
Type of
vulnerability
Motivation of
threat
source
Mission of
the system
Criticality of
the system
DdoS
Malware/
Trojan
Social
Engineering
Disgruntled
Employees
Inefficient
Auditing
Outdated
Systems
Hardware/
Software
failure
Ineffective
security
hardening
Risk Management
DDoS protection through advanced
DDoS protection systems such as
Cloudflare.
End-point cybersecurity solutions
to protect against virus, trojans and
malware.
Employee termination policy,
employee training and privilege
management
Regular system audits through
internal and 3rd party agency.
Regular updates to operating
systems, platforms and
middleware.
Server and operating system
hardening to secure such systems
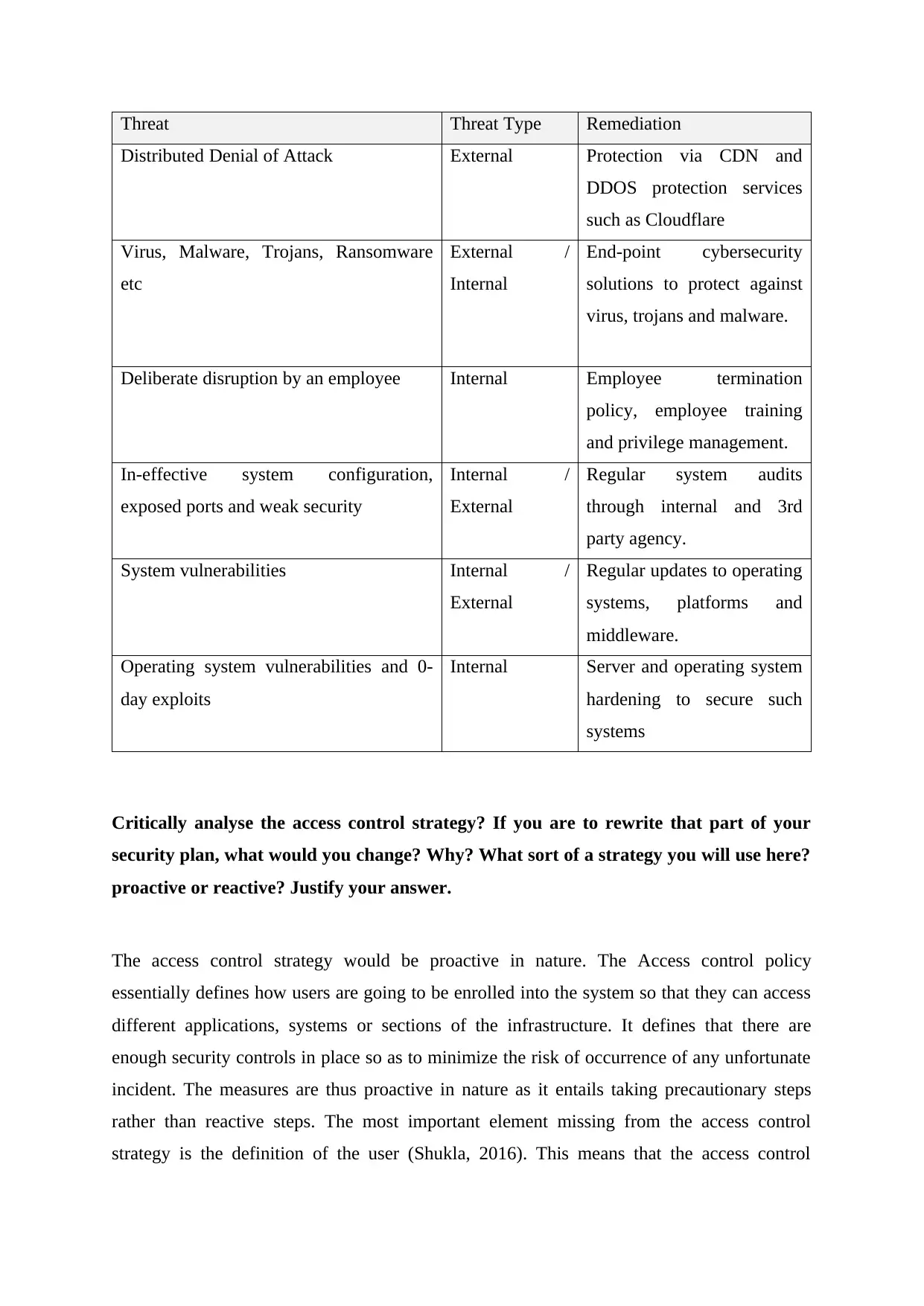
Threat Threat Type Remediation
Distributed Denial of Attack External Protection via CDN and
DDOS protection services
such as Cloudflare
Virus, Malware, Trojans, Ransomware
etc
External /
Internal
End-point cybersecurity
solutions to protect against
virus, trojans and malware.
Deliberate disruption by an employee Internal Employee termination
policy, employee training
and privilege management.
In-effective system configuration,
exposed ports and weak security
Internal /
External
Regular system audits
through internal and 3rd
party agency.
System vulnerabilities Internal /
External
Regular updates to operating
systems, platforms and
middleware.
Operating system vulnerabilities and 0-
day exploits
Internal Server and operating system
hardening to secure such
systems
Critically analyse the access control strategy? If you are to rewrite that part of your
security plan, what would you change? Why? What sort of a strategy you will use here?
proactive or reactive? Justify your answer.
The access control strategy would be proactive in nature. The Access control policy
essentially defines how users are going to be enrolled into the system so that they can access
different applications, systems or sections of the infrastructure. It defines that there are
enough security controls in place so as to minimize the risk of occurrence of any unfortunate
incident. The measures are thus proactive in nature as it entails taking precautionary steps
rather than reactive steps. The most important element missing from the access control
strategy is the definition of the user (Shukla, 2016). This means that the access control
Distributed Denial of Attack External Protection via CDN and
DDOS protection services
such as Cloudflare
Virus, Malware, Trojans, Ransomware
etc
External /
Internal
End-point cybersecurity
solutions to protect against
virus, trojans and malware.
Deliberate disruption by an employee Internal Employee termination
policy, employee training
and privilege management.
In-effective system configuration,
exposed ports and weak security
Internal /
External
Regular system audits
through internal and 3rd
party agency.
System vulnerabilities Internal /
External
Regular updates to operating
systems, platforms and
middleware.
Operating system vulnerabilities and 0-
day exploits
Internal Server and operating system
hardening to secure such
systems
Critically analyse the access control strategy? If you are to rewrite that part of your
security plan, what would you change? Why? What sort of a strategy you will use here?
proactive or reactive? Justify your answer.
The access control strategy would be proactive in nature. The Access control policy
essentially defines how users are going to be enrolled into the system so that they can access
different applications, systems or sections of the infrastructure. It defines that there are
enough security controls in place so as to minimize the risk of occurrence of any unfortunate
incident. The measures are thus proactive in nature as it entails taking precautionary steps
rather than reactive steps. The most important element missing from the access control
strategy is the definition of the user (Shukla, 2016). This means that the access control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

strategy which has cantered it’s entire policy based on the ‘user’, has not defined the user
itself. So, the definition of the user must be made clear in that respect. Apart from that, there
are additional definitions missing from the policy. These include definitions such as the
definition of ‘User Accounts’, the definition of ‘Privileged Accounts’ which have additional
privileges than regular users. These may include super-users or departmental heads.
Furthermore, there needs to be a well-defined ‘Admin account’.
Apart from that, the concept of least privilege is also missing from the access control whereas
the deactivation of user accounts from the system upon employee termination, leave,
suspension etc is also missing. The automated expiry of accounts as well as the automated
password change notifications are also missing from the policy. The document also does not
talk about the process or procedures in place required for user verification authorization.
Automatic session-lock and remote sessions are also missing from access control policy and
they are also an important element of the policy.
Specifically, the following points and measures needs to be amended into the access control
policy:
a. Unique user ID for each of the users.
b. Level of access determined for the user.
c. Revoking of access to the system upon termination.
d. Recovering of IT equipments and assets upon termination.
e. Privileges for each user to be defined on ‘least possible privilege’ and ‘need-to-know’
basis
f. Changes in permission to be followed through a formal procedure and documented
duly.
What do you recommend for a proper incident management strategy? How would you
implement it? Hint: Stakeholders and role responsibilities.
An incident is any event that could lead to damages to an individual or a property. Some
examples may include unauthorized access to data, network, persistent threats, spamming,
spoofing, data exfiltration, unauthorized scanning, hacking and intrusion attempts among
itself. So, the definition of the user must be made clear in that respect. Apart from that, there
are additional definitions missing from the policy. These include definitions such as the
definition of ‘User Accounts’, the definition of ‘Privileged Accounts’ which have additional
privileges than regular users. These may include super-users or departmental heads.
Furthermore, there needs to be a well-defined ‘Admin account’.
Apart from that, the concept of least privilege is also missing from the access control whereas
the deactivation of user accounts from the system upon employee termination, leave,
suspension etc is also missing. The automated expiry of accounts as well as the automated
password change notifications are also missing from the policy. The document also does not
talk about the process or procedures in place required for user verification authorization.
Automatic session-lock and remote sessions are also missing from access control policy and
they are also an important element of the policy.
Specifically, the following points and measures needs to be amended into the access control
policy:
a. Unique user ID for each of the users.
b. Level of access determined for the user.
c. Revoking of access to the system upon termination.
d. Recovering of IT equipments and assets upon termination.
e. Privileges for each user to be defined on ‘least possible privilege’ and ‘need-to-know’
basis
f. Changes in permission to be followed through a formal procedure and documented
duly.
What do you recommend for a proper incident management strategy? How would you
implement it? Hint: Stakeholders and role responsibilities.
An incident is any event that could lead to damages to an individual or a property. Some
examples may include unauthorized access to data, network, persistent threats, spamming,
spoofing, data exfiltration, unauthorized scanning, hacking and intrusion attempts among
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

others. All incident management strategy start with defining what an incident is, and what the
person responsible for detection and management must do in order to contain the activity
(Bhandari, Owen and Trist, 2015).
The most effective way for an incident management strategy to work is to define the rules
and responsibilities of the stakeholders. These would include:
The stakeholders must report any incident to the relevant department whenever they
learn about it.
Stakeholders are required not to hold back, destroy or disprove any information or
data.
Stakeholders would duly collaborate and comply with the organization's advisories as
well as instructions, etc.
Stakeholders would be required to coordinate security incidents with IT Team as and
when requested and provide required details, records, proof and other assistance.
Stakeholders shall make needed adjustments to their hardware, software, database,
applications, services, etc. according to IT department's recommendation to reduce
risk to safety. Upon getting the intervention required.
A comprehensive event report on the event shall be submitted to the IT department by
stakeholders engaged in investigating or mitigating the security event. The report
would be properly reviewed and then sent to the IT department through each project /
division's corresponding HoDs / HoGs.
Stakeholders would need to frequently patch their individual property (hardware,
applications, software... etc) and guarantee that the recent patches on all their
resources are deployed effectively.
Stakeholders would need to guarantee that the suitable anti-virus software is deployed
on all their computer hardware (such as computers, Workstations, tablets, etc.) and
that it is maintained with the recent definitions / signatures for the antivirus solution.
Compile a brief security strategy that suits the business requirements as well as the
security requirements of this workplace.
An indicator of a good security strategy is the ability to respond to a wide variety of security
threats while being dynamic and comprehensive. A good security strategy would entail, first
and foremost the organization, the process, the technology as well as people. Beyond that, it
person responsible for detection and management must do in order to contain the activity
(Bhandari, Owen and Trist, 2015).
The most effective way for an incident management strategy to work is to define the rules
and responsibilities of the stakeholders. These would include:
The stakeholders must report any incident to the relevant department whenever they
learn about it.
Stakeholders are required not to hold back, destroy or disprove any information or
data.
Stakeholders would duly collaborate and comply with the organization's advisories as
well as instructions, etc.
Stakeholders would be required to coordinate security incidents with IT Team as and
when requested and provide required details, records, proof and other assistance.
Stakeholders shall make needed adjustments to their hardware, software, database,
applications, services, etc. according to IT department's recommendation to reduce
risk to safety. Upon getting the intervention required.
A comprehensive event report on the event shall be submitted to the IT department by
stakeholders engaged in investigating or mitigating the security event. The report
would be properly reviewed and then sent to the IT department through each project /
division's corresponding HoDs / HoGs.
Stakeholders would need to frequently patch their individual property (hardware,
applications, software... etc) and guarantee that the recent patches on all their
resources are deployed effectively.
Stakeholders would need to guarantee that the suitable anti-virus software is deployed
on all their computer hardware (such as computers, Workstations, tablets, etc.) and
that it is maintained with the recent definitions / signatures for the antivirus solution.
Compile a brief security strategy that suits the business requirements as well as the
security requirements of this workplace.
An indicator of a good security strategy is the ability to respond to a wide variety of security
threats while being dynamic and comprehensive. A good security strategy would entail, first
and foremost the organization, the process, the technology as well as people. Beyond that, it

will have a good amount of constraints and assumptions drawn into it. Apart from that, a
good security strategy is incomplete without an in-effective risk assessment strategy.
Organization, People, Process And Technology
Understanding the main aspects of the business is the most significant part of creating a
security strategy (Kadam, 2014). Industry policies like COBIT could be used to prepare and
decide on the structure for analysing the IT objectives appropriately aligned while keeping
into consideration variables such as apps, records, networks, knowledge exchange (Zhang
and Fever, 2013). It is necessary to document the roles and duties needed for different I.T and
enterprise positions. Detailed knowledge of the different IT processes, including supply,
capability, expenditure, human resources, performance, training etc needs to be considered
(Oshri, Kotlarsky and Hirsch, 2007). Security and compliance should also be evaluated for
external stakeholders like software development, training, operation, managed services,
hardware suppliers, etc.
Assumptions, constraints and resources
While creating a security strategy, it is important to take into account certain assumptions.
Assumptions are positive or negative factors are that are considered based on estimates. On
the other side, constraints are boundaries or limitations that can deter or diminish the success
or execution of a part or even the whole strategic objective. Resources could be described like
any operation, method, resources, equipment, person, policy, processes, etc. that can be used
to address a void in certain way and therefore help to enforce the security strategy.
Gap analysis and risk assessment
The following processes are generally followed:
Plan:
Understanding enterprise goals, priorities, pertinent risk and success criteria•
Determining legal, regulatory, legislative and statutory relevance
Defining scope as well as limits
Readying a roadmap that contains timetable or timelines, stakeholder data, list
of papers to be checked, required resources and anticipated deliverables.
Recognition of assets–application, repository, sensitive and personal data,
infrastructure systems, facilities, users, etc.
good security strategy is incomplete without an in-effective risk assessment strategy.
Organization, People, Process And Technology
Understanding the main aspects of the business is the most significant part of creating a
security strategy (Kadam, 2014). Industry policies like COBIT could be used to prepare and
decide on the structure for analysing the IT objectives appropriately aligned while keeping
into consideration variables such as apps, records, networks, knowledge exchange (Zhang
and Fever, 2013). It is necessary to document the roles and duties needed for different I.T and
enterprise positions. Detailed knowledge of the different IT processes, including supply,
capability, expenditure, human resources, performance, training etc needs to be considered
(Oshri, Kotlarsky and Hirsch, 2007). Security and compliance should also be evaluated for
external stakeholders like software development, training, operation, managed services,
hardware suppliers, etc.
Assumptions, constraints and resources
While creating a security strategy, it is important to take into account certain assumptions.
Assumptions are positive or negative factors are that are considered based on estimates. On
the other side, constraints are boundaries or limitations that can deter or diminish the success
or execution of a part or even the whole strategic objective. Resources could be described like
any operation, method, resources, equipment, person, policy, processes, etc. that can be used
to address a void in certain way and therefore help to enforce the security strategy.
Gap analysis and risk assessment
The following processes are generally followed:
Plan:
Understanding enterprise goals, priorities, pertinent risk and success criteria•
Determining legal, regulatory, legislative and statutory relevance
Defining scope as well as limits
Readying a roadmap that contains timetable or timelines, stakeholder data, list
of papers to be checked, required resources and anticipated deliverables.
Recognition of assets–application, repository, sensitive and personal data,
infrastructure systems, facilities, users, etc.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
