Security Testing and Implementation: Firewall Vulnerabilities Report
VerifiedAdded on 2022/08/27
|5
|1010
|15
Report
AI Summary
This report focuses on security testing and implementation, specifically addressing firewall vulnerabilities. It begins by defining firewalls and their importance in modern enterprise networks, highlighting three popular firewalls: Barracuda CloudGen Firewall, Cisco Adaptive Security Appliance software, and FortiGate. The report then delves into a critical vulnerability of the Barracuda NextGen firewall, detailing how cross-site scripting can be exploited and the potential impact. Furthermore, it outlines mitigation strategies to address this vulnerability, including input filtering, output encoding, appropriate response headers, and content security policy. The report concludes by summarizing the advantages of the Barracuda NextGen Firewall and includes a bibliography of relevant sources.

Running head: SECURITY TESTING AND IMPLEMENTATION
SECURITY TESTING AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
SECURITY TESTING AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY TESTING AND IMPLEMENTATION
Popular Firewalls Used in Modern Enterprise
A firewall is a system of safety of network that controls and traffic of a network those
are going out and coming in. The firewalls are predefined by the regulations of security.
Generally, a firewall establishes a wall between internal networks those are trusted and an
external network those are not trusted. An example is the internet.
There are various kinds of firewalls that are used by various enterprise in order to
safeguard its network so that the hackers do not enter the network and access the sensitive
information that are important for the company.
The three firewalls that are used by the enterprise are Barracude CloudGen Firewall,
Cisco, Adaptive, security Appliance software and FortiGate. These are used by various
enterprises in order to provide safety to the network.
Barracuda CloudGen Firewall is a family of hardware, virtual appliance that is based
on cloud. It safeguards and upgrades the infrastructure of network those are dispersed. They
distribute great security by tightly combining a comprehensive sequence of technologies of
firewall that are based on generation of cloud.
The family of Cisco of the devices of security that safeguards the networks those are
corporate of all sizes. It offers the users with access to data those are secure using any of the
devices. It provides firewall abilities for the devices of ASA. The ASA software combines
with the other technologies of security in order to deliver proper solutions that meet the
requirements of security.
The FortiGate use processors of security and threat intelligence services of security
from the FortiGuard labs those are powered by AI. The next generation firewalls minimize
complexity and the costs and that encrypts the traffic of the network.
Popular Firewalls Used in Modern Enterprise
A firewall is a system of safety of network that controls and traffic of a network those
are going out and coming in. The firewalls are predefined by the regulations of security.
Generally, a firewall establishes a wall between internal networks those are trusted and an
external network those are not trusted. An example is the internet.
There are various kinds of firewalls that are used by various enterprise in order to
safeguard its network so that the hackers do not enter the network and access the sensitive
information that are important for the company.
The three firewalls that are used by the enterprise are Barracude CloudGen Firewall,
Cisco, Adaptive, security Appliance software and FortiGate. These are used by various
enterprises in order to provide safety to the network.
Barracuda CloudGen Firewall is a family of hardware, virtual appliance that is based
on cloud. It safeguards and upgrades the infrastructure of network those are dispersed. They
distribute great security by tightly combining a comprehensive sequence of technologies of
firewall that are based on generation of cloud.
The family of Cisco of the devices of security that safeguards the networks those are
corporate of all sizes. It offers the users with access to data those are secure using any of the
devices. It provides firewall abilities for the devices of ASA. The ASA software combines
with the other technologies of security in order to deliver proper solutions that meet the
requirements of security.
The FortiGate use processors of security and threat intelligence services of security
from the FortiGuard labs those are powered by AI. The next generation firewalls minimize
complexity and the costs and that encrypts the traffic of the network.

2SECURITY TESTING AND IMPLEMENTATION
Critical Vulnerability of the Firewall
The Barracuda NextGen firewall is a cloud based firewall. The powerful appliance that are
on-premises is optimized in order to do the activities like forwarding of packets, prevention
of intrusion and connectivity of site-to-site. The vulnerabilities include multiple persistence in
put validation web vulnerabilities. The vulnerability permits the attackers those are remote to
inject the scripts those are malicious.
The weakness is located in the menu of the firewall when processing to develop a user object
those are custom with manipulated develop the credentials of the group those are based on
expression of the user. The attackers those are remote can inject harmful codes. The
exploitation of the vulnerability needs user account application those are low privileged and
low interaction of the user. Successful exploitation of the firewall outputs in hijacking of the
session, phishing those are persistent, persistent external redirects and persistent manipulation
of connected or affected context of the module of web.
After the attacker has injected the code, the attacker can save the input through add in order
to run the code those are persistent in the listing of edit. The attackers those are remote are
able to add the persistent context those are injected to the objects module of the custom user.
Mitigation of the Critical vulnerability
The vulnerability of the firewall is cross-site scripting. The vulnerability can be mitigated
using the following process.
Filter input on arrival: At a point at which the input of the user is arriving, the input should
be filtered as strictly as possible that is based on the input those are valid.
Encode data on output: At a point where the information and data those are controlled by
the user is output in the response of HTTP, the output should be encoded in order to avoid it
Critical Vulnerability of the Firewall
The Barracuda NextGen firewall is a cloud based firewall. The powerful appliance that are
on-premises is optimized in order to do the activities like forwarding of packets, prevention
of intrusion and connectivity of site-to-site. The vulnerabilities include multiple persistence in
put validation web vulnerabilities. The vulnerability permits the attackers those are remote to
inject the scripts those are malicious.
The weakness is located in the menu of the firewall when processing to develop a user object
those are custom with manipulated develop the credentials of the group those are based on
expression of the user. The attackers those are remote can inject harmful codes. The
exploitation of the vulnerability needs user account application those are low privileged and
low interaction of the user. Successful exploitation of the firewall outputs in hijacking of the
session, phishing those are persistent, persistent external redirects and persistent manipulation
of connected or affected context of the module of web.
After the attacker has injected the code, the attacker can save the input through add in order
to run the code those are persistent in the listing of edit. The attackers those are remote are
able to add the persistent context those are injected to the objects module of the custom user.
Mitigation of the Critical vulnerability
The vulnerability of the firewall is cross-site scripting. The vulnerability can be mitigated
using the following process.
Filter input on arrival: At a point at which the input of the user is arriving, the input should
be filtered as strictly as possible that is based on the input those are valid.
Encode data on output: At a point where the information and data those are controlled by
the user is output in the response of HTTP, the output should be encoded in order to avoid it
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SECURITY TESTING AND IMPLEMENTATION
from being understood as content those are active. Relying on the context of output, this
might need applying some amalgamation of HTML, UPL, JavaScript and many more.
Use appropriate response headers: In order to avoid the cross side scripting in the
responses of HTTP those are not proposed to include any HTML or JavaScript, the users can
utilise several headers in order to make sure that the browsers understand the replies in the
way that the users aim to.
Content Security Policy: As the last line of defence, the user can use the policy of security
of content in order to minimize the severity of the cross scripting vulnerabilities. The firewall
can be able to mitigate the cross side scripting vulnerability.
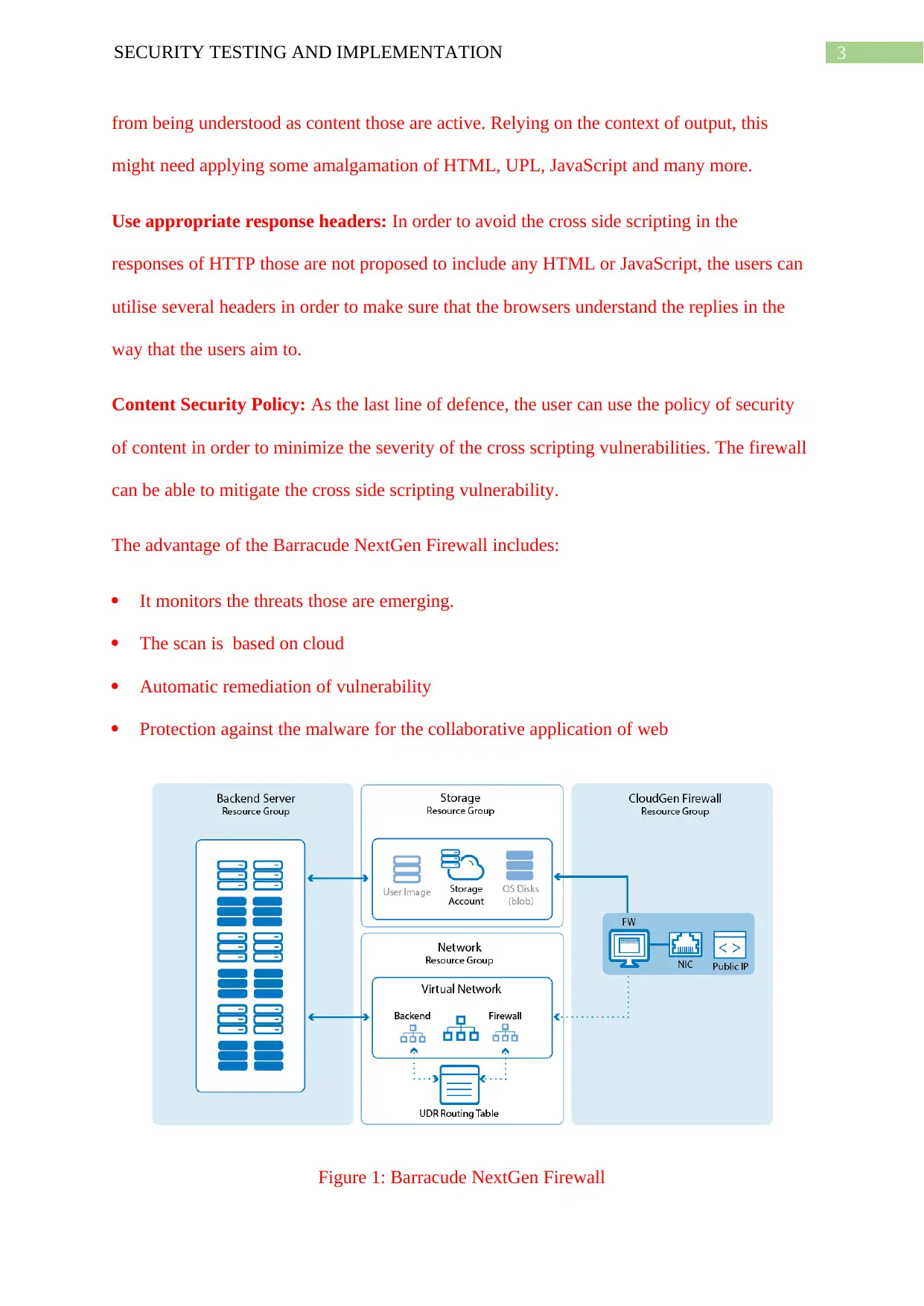
The advantage of the Barracude NextGen Firewall includes:
It monitors the threats those are emerging.
The scan is based on cloud
Automatic remediation of vulnerability
Protection against the malware for the collaborative application of web
Figure 1: Barracude NextGen Firewall
from being understood as content those are active. Relying on the context of output, this
might need applying some amalgamation of HTML, UPL, JavaScript and many more.
Use appropriate response headers: In order to avoid the cross side scripting in the
responses of HTTP those are not proposed to include any HTML or JavaScript, the users can
utilise several headers in order to make sure that the browsers understand the replies in the
way that the users aim to.
Content Security Policy: As the last line of defence, the user can use the policy of security
of content in order to minimize the severity of the cross scripting vulnerabilities. The firewall
can be able to mitigate the cross side scripting vulnerability.
The advantage of the Barracude NextGen Firewall includes:
It monitors the threats those are emerging.
The scan is based on cloud
Automatic remediation of vulnerability
Protection against the malware for the collaborative application of web
Figure 1: Barracude NextGen Firewall
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY TESTING AND IMPLEMENTATION
Bibliography
[1]"Firewall: A Security Point of a Network", International Journal of Science and Research
(IJSR), vol. 4, no. 12, pp. 1568-1570, 2015. Available: 10.21275/v4i12.nov152325.
[2]A. Ali, S. Darwish and S. Guirguis, "An Approach for Improving Performance of a Packet
Filtering Firewall Based on Fuzzy Petri Net", Journal of Advances in Computer Networks,
vol. 3, no. 1, pp. 67-74, 2015. Available: 10.7763/jacn.2015.v3.144.
[3]"Firewall: A Security Point of a Network", International Journal of Science and Research
(IJSR), vol. 4, no. 12, pp. 1568-1570, 2015. Available: 10.21275/v4i12.nov152325.
[4]"Firewall and VPN Technology", International Journal of Science and Research (IJSR),
vol. 6, no. 12, pp. 1762-1765, 2017. Available: 10.21275/art20179139.
Bibliography
[1]"Firewall: A Security Point of a Network", International Journal of Science and Research
(IJSR), vol. 4, no. 12, pp. 1568-1570, 2015. Available: 10.21275/v4i12.nov152325.
[2]A. Ali, S. Darwish and S. Guirguis, "An Approach for Improving Performance of a Packet
Filtering Firewall Based on Fuzzy Petri Net", Journal of Advances in Computer Networks,
vol. 3, no. 1, pp. 67-74, 2015. Available: 10.7763/jacn.2015.v3.144.
[3]"Firewall: A Security Point of a Network", International Journal of Science and Research
(IJSR), vol. 4, no. 12, pp. 1568-1570, 2015. Available: 10.21275/v4i12.nov152325.
[4]"Firewall and VPN Technology", International Journal of Science and Research (IJSR),
vol. 6, no. 12, pp. 1762-1765, 2017. Available: 10.21275/art20179139.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





