An Evaluation of the NIST 800-61 Model for Security Incident Handling
VerifiedAdded on 2023/01/17
|12
|3803
|48
Report
AI Summary
This report provides a comprehensive analysis of the NIST 800-61 model for security incident handling. It begins with an introduction to security incident handling and the importance of a well-defined model, then proposes the NIST 800-61 model for addressing poorly-handled information security incidents. The report details the model's four phases: preparation, detection and analysis, containment, eradication, and recovery, and post-incident activity, using a malicious software incident as an example. It explains each stage, including the resources, tools, and recommended practices for incident prevention and handling. The report further discusses the relationship between incident response and other information security processes, the role of audit in providing assurance, and governance and compliance issues. The report concludes with recommendations for effective incident handling and provides references to support the analysis.

SECURITY, AUDIT AND
COMPLIANCE
COMPLIANCE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
PROPOSED MODEL- MODEL SELECTIO.................................................................................1
PROPOSED MODEL- EXPLANATION.......................................................................................4
EVALUATION AND DISCUSSION.............................................................................................7
Relationship between information security incident response other information security
processes......................................................................................................................................7
Role of audit in providing assurance that the incident handling process is effective..................8
Governance and compliance issues raised and the professional roles involved in managing
them.............................................................................................................................................8
CONCLUSION................................................................................................................................9
Recommendations........................................................................................................................9
REREFENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
PROPOSED MODEL- MODEL SELECTIO.................................................................................1
PROPOSED MODEL- EXPLANATION.......................................................................................4
EVALUATION AND DISCUSSION.............................................................................................7
Relationship between information security incident response other information security
processes......................................................................................................................................7
Role of audit in providing assurance that the incident handling process is effective..................8
Governance and compliance issues raised and the professional roles involved in managing
them.............................................................................................................................................8
CONCLUSION................................................................................................................................9
Recommendations........................................................................................................................9
REREFENCES..............................................................................................................................10

INTRODUCTION
Security incident handling is a continuous process that helps in governing activities
before, during and after a security incident occurs. A proper security incident handling plan or a
model can help an organization to effectively handle security incidents. It has become one of the
most important components which is required to be focused upon by the organizations. there are
various kinds of models that can be used for security information handling by the organization
(Papastergiou, Mouratidis & Kalogeraki, 2019). Some of the most common type of incident
handling model are ISO, NIST, SANS and RSP. This report will aim upon a model for security
incident handling for poorly-handled information security incidents of an organization and ways
in which it can be applied to the organization. For this, NIST 800-61 model has been chosen.
This report will explain, selected model in detail, explanation of selected model, ways in which
information security incident response is related to information security processes.
PROPOSED MODEL- MODEL SELECTIO
There are various kinds of incident response management models that can be used by
organizations for incident security handling. Information security incident response has been one
of the most important components for organizations which is required to be focused upon by
companies. There are various kinds of security information handling models. Some of the most
common models are developed are ISO, NIST, SANS and RSP (Alsmadi, 2019). These models
are further divided into sub-team models. These models are used for responding and evaluation
of an incident so that affect system or information can be restored as soon as possible. Out of all
of these models NIST and ISO models are one of the most common models that are being used
by organizations for handing of security incidents.
NIST Cybersecurity Framework.
NIST model is commonly used because of increasing number of cyber security attacks
because of which information handling of companies is becoming difficult. This model help
companies to enhance their ability to improve their cyber security information handling. This
framework also helps in providing computer security policy framework and guidelines for
private sector organizations so that their ability to detect, prevent and respond to cyber attacks
can be increased. This framework has been translated in many languages and is used by various
organizations. it helps in providing high level of taxonomy of outcomes of cybersecurity as well
as a methodology so that those outcomes can be accessed and managed accordingly. NIST model
1
Security incident handling is a continuous process that helps in governing activities
before, during and after a security incident occurs. A proper security incident handling plan or a
model can help an organization to effectively handle security incidents. It has become one of the
most important components which is required to be focused upon by the organizations. there are
various kinds of models that can be used for security information handling by the organization
(Papastergiou, Mouratidis & Kalogeraki, 2019). Some of the most common type of incident
handling model are ISO, NIST, SANS and RSP. This report will aim upon a model for security
incident handling for poorly-handled information security incidents of an organization and ways
in which it can be applied to the organization. For this, NIST 800-61 model has been chosen.
This report will explain, selected model in detail, explanation of selected model, ways in which
information security incident response is related to information security processes.
PROPOSED MODEL- MODEL SELECTIO
There are various kinds of incident response management models that can be used by
organizations for incident security handling. Information security incident response has been one
of the most important components for organizations which is required to be focused upon by
companies. There are various kinds of security information handling models. Some of the most
common models are developed are ISO, NIST, SANS and RSP (Alsmadi, 2019). These models
are further divided into sub-team models. These models are used for responding and evaluation
of an incident so that affect system or information can be restored as soon as possible. Out of all
of these models NIST and ISO models are one of the most common models that are being used
by organizations for handing of security incidents.
NIST Cybersecurity Framework.
NIST model is commonly used because of increasing number of cyber security attacks
because of which information handling of companies is becoming difficult. This model help
companies to enhance their ability to improve their cyber security information handling. This
framework also helps in providing computer security policy framework and guidelines for
private sector organizations so that their ability to detect, prevent and respond to cyber attacks
can be increased. This framework has been translated in many languages and is used by various
organizations. it helps in providing high level of taxonomy of outcomes of cybersecurity as well
as a methodology so that those outcomes can be accessed and managed accordingly. NIST model
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
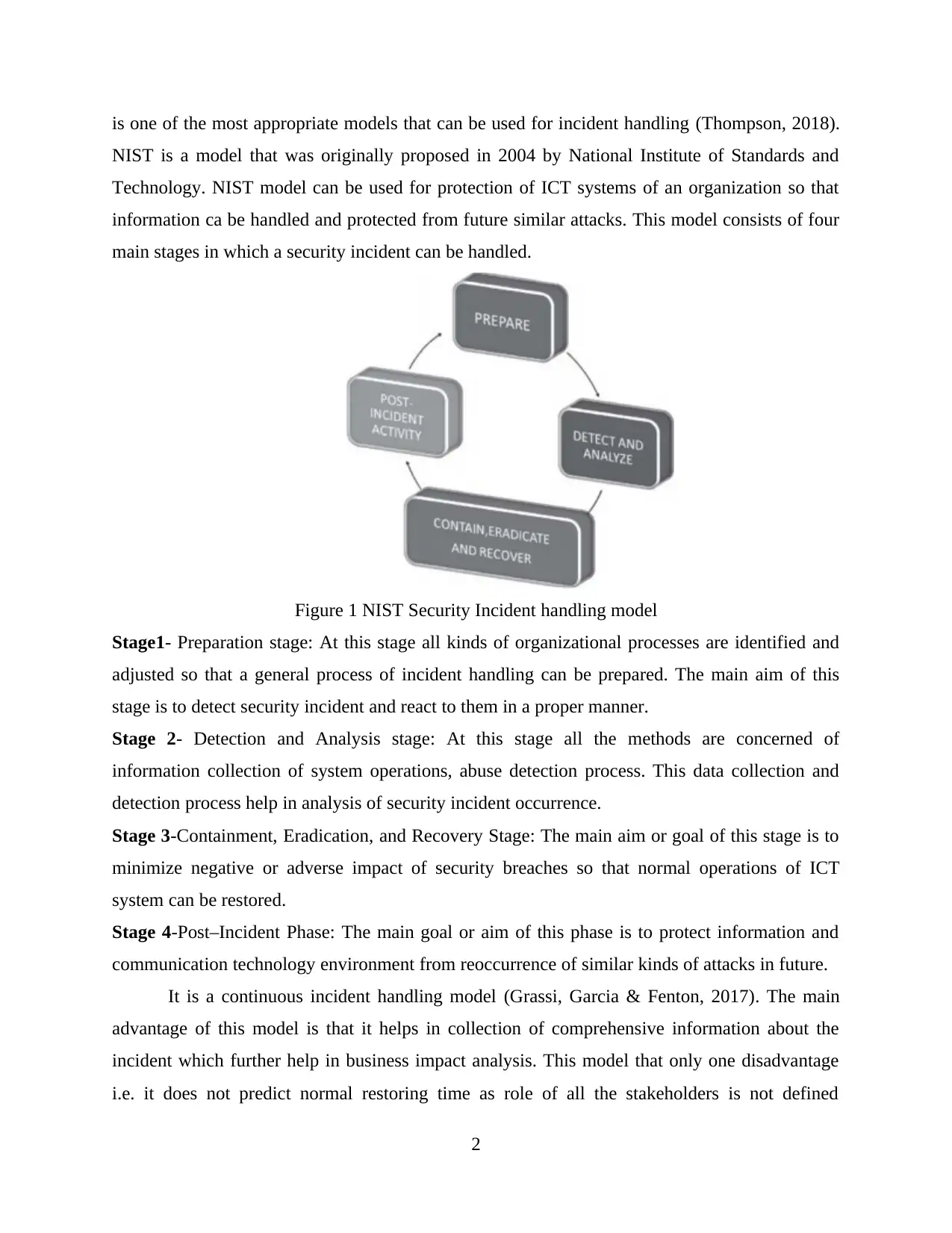
is one of the most appropriate models that can be used for incident handling (Thompson, 2018).
NIST is a model that was originally proposed in 2004 by National Institute of Standards and
Technology. NIST model can be used for protection of ICT systems of an organization so that
information ca be handled and protected from future similar attacks. This model consists of four
main stages in which a security incident can be handled.
Figure 1 NIST Security Incident handling model
Stage1- Preparation stage: At this stage all kinds of organizational processes are identified and
adjusted so that a general process of incident handling can be prepared. The main aim of this
stage is to detect security incident and react to them in a proper manner.
Stage 2- Detection and Analysis stage: At this stage all the methods are concerned of
information collection of system operations, abuse detection process. This data collection and
detection process help in analysis of security incident occurrence.
Stage 3-Containment, Eradication, and Recovery Stage: The main aim or goal of this stage is to
minimize negative or adverse impact of security breaches so that normal operations of ICT
system can be restored.
Stage 4-Post–Incident Phase: The main goal or aim of this phase is to protect information and
communication technology environment from reoccurrence of similar kinds of attacks in future.
It is a continuous incident handling model (Grassi, Garcia & Fenton, 2017). The main
advantage of this model is that it helps in collection of comprehensive information about the
incident which further help in business impact analysis. This model that only one disadvantage
i.e. it does not predict normal restoring time as role of all the stakeholders is not defined
2
NIST is a model that was originally proposed in 2004 by National Institute of Standards and
Technology. NIST model can be used for protection of ICT systems of an organization so that
information ca be handled and protected from future similar attacks. This model consists of four
main stages in which a security incident can be handled.
Figure 1 NIST Security Incident handling model
Stage1- Preparation stage: At this stage all kinds of organizational processes are identified and
adjusted so that a general process of incident handling can be prepared. The main aim of this
stage is to detect security incident and react to them in a proper manner.
Stage 2- Detection and Analysis stage: At this stage all the methods are concerned of
information collection of system operations, abuse detection process. This data collection and
detection process help in analysis of security incident occurrence.
Stage 3-Containment, Eradication, and Recovery Stage: The main aim or goal of this stage is to
minimize negative or adverse impact of security breaches so that normal operations of ICT
system can be restored.
Stage 4-Post–Incident Phase: The main goal or aim of this phase is to protect information and
communication technology environment from reoccurrence of similar kinds of attacks in future.
It is a continuous incident handling model (Grassi, Garcia & Fenton, 2017). The main
advantage of this model is that it helps in collection of comprehensive information about the
incident which further help in business impact analysis. This model that only one disadvantage
i.e. it does not predict normal restoring time as role of all the stakeholders is not defined
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

properly. This model helps in development of security standards and guidelines. It is one of the
most basic information handling models. Today die to increasing security incidents, new types of
security-related incidents are emerging frequently.
NIST 800-61
NIST SP 800-61 is a special publication model that defines an incident a kind of violation
or imminent violation threat of all kinds of computer security policies acceptable use policies and
standard security practices. With time different kinds of changes within this model have been
brought and NIST 800-61 is a special publication model which majorly focuses upon computer
security information handling. This publication of NIST focuses upon providing a guidance to
organizations on ways in which they can operate incident response capacity (Barker & Dang,
2016). This special publication framework provides all kinds of information for development of
procedure for information handling performance and reporting by structuring team, staffing, and
training. This guide is defined in all four phases of incident response life cycle that are:
preparation, detection and analysis, containment eradication and recovery, and post-incident
activity.
This NIST 800-61 model can be selected and used by organization so that they can
prepare themselves for cyber security information handling by working upon ways in which
information handling can be done security of systems can be enhanced and ways in which
company can prepare themselves cybersecurity attacks on system for protection of information.
It also helps in providing high- level guidance to combined security incident response team so
that they can interact with outside team like: coordinating centres, Internet Service Providers,
owners of attacking systems, victims, other CSIRTs, and vendors. This framework primarily
focuses upon developing understanding and relationship between team to team, share
agreements, explanation of role of automation technique in coordination of incident response
handling in a proper and appropriate manner. these are some of the main requirements because of
which this model or framework has been hosen for security incident handling of the
organization. There are other reasons because of this this model has been chosen such as: During
an incident handling an organization is required to communicate with teams within an
organization and parties outside the organization for example: law enforcement, incident
response teams, media and many more. Due to this communication within these teams is
required to be established in a proper manner as communication is required often and quickly
3
most basic information handling models. Today die to increasing security incidents, new types of
security-related incidents are emerging frequently.
NIST 800-61
NIST SP 800-61 is a special publication model that defines an incident a kind of violation
or imminent violation threat of all kinds of computer security policies acceptable use policies and
standard security practices. With time different kinds of changes within this model have been
brought and NIST 800-61 is a special publication model which majorly focuses upon computer
security information handling. This publication of NIST focuses upon providing a guidance to
organizations on ways in which they can operate incident response capacity (Barker & Dang,
2016). This special publication framework provides all kinds of information for development of
procedure for information handling performance and reporting by structuring team, staffing, and
training. This guide is defined in all four phases of incident response life cycle that are:
preparation, detection and analysis, containment eradication and recovery, and post-incident
activity.
This NIST 800-61 model can be selected and used by organization so that they can
prepare themselves for cyber security information handling by working upon ways in which
information handling can be done security of systems can be enhanced and ways in which
company can prepare themselves cybersecurity attacks on system for protection of information.
It also helps in providing high- level guidance to combined security incident response team so
that they can interact with outside team like: coordinating centres, Internet Service Providers,
owners of attacking systems, victims, other CSIRTs, and vendors. This framework primarily
focuses upon developing understanding and relationship between team to team, share
agreements, explanation of role of automation technique in coordination of incident response
handling in a proper and appropriate manner. these are some of the main requirements because of
which this model or framework has been hosen for security incident handling of the
organization. There are other reasons because of this this model has been chosen such as: During
an incident handling an organization is required to communicate with teams within an
organization and parties outside the organization for example: law enforcement, incident
response teams, media and many more. Due to this communication within these teams is
required to be established in a proper manner as communication is required often and quickly
3

(Simmon, 2018). It becomes important for company to pre- determine all the guidelines related
to communication in case of incident handling especially when information is shared with right
parties outside the organization. It is one of the main reason because of this this framework of
model has been chosen for security information handling.
PROPOSED MODEL- EXPLANATION
NIST 800-61 framework helps in provision of high- level guidance for different kinds of
incidents that can occur within an organization such as: attack executed from removable media,
attack in which system is destroyed, attack executed from website or from a web application,
attack though email, violation of acceptable usage, theft of data/information or media and lastly
other kinds of attacks that do not fit within any of these categories. Provision of these high- level
guidance has become important for organization because of increasing number of incidents
because of which security of information is being compromised.
Implementation or adaptation of NIFT model within an organization can be implemented
in several phases. Initial phase of this framework is training and establishment of an incident
response team, acquiring important resources and tools (Zhu & et.al. 2016). Then comes the first
preparation phase in which organization focuses upon attempting to limit number of incidents
that can occur after settings some controls based upon risk identified though risk assessment.
Them comes the second phase of detection and analysis in which all kinds of security breeches
are detected so that organization can be alerted and prepared whenever such kind of incident
occurs so that they can be prepared at that moment. Then comes the Containment, Eradication,
and Recovery phase in which impact of thee risk can be mitigated in order to recover from the
incident or incident can be eradicated. In this phase organization can cycle back to detection and
analysis phase when new incident is about to occur. For example: While eradicating a malicious
software incident, system gets infected by a new infected malware activity. In such case
organization can move ack to previous phase of detection and analysis and only them move
forward to Containment, Eradication, and Recovery phase. After this post- incident handling
activity phase comes into picture. At this phase organization prepare themselves for this incident
if it occurs in future. And move back to preparation phase. Each of these stages or phases can be
explained with the help of a malicious software incident handling example.
Preparation
4
to communication in case of incident handling especially when information is shared with right
parties outside the organization. It is one of the main reason because of this this framework of
model has been chosen for security information handling.
PROPOSED MODEL- EXPLANATION
NIST 800-61 framework helps in provision of high- level guidance for different kinds of
incidents that can occur within an organization such as: attack executed from removable media,
attack in which system is destroyed, attack executed from website or from a web application,
attack though email, violation of acceptable usage, theft of data/information or media and lastly
other kinds of attacks that do not fit within any of these categories. Provision of these high- level
guidance has become important for organization because of increasing number of incidents
because of which security of information is being compromised.
Implementation or adaptation of NIFT model within an organization can be implemented
in several phases. Initial phase of this framework is training and establishment of an incident
response team, acquiring important resources and tools (Zhu & et.al. 2016). Then comes the first
preparation phase in which organization focuses upon attempting to limit number of incidents
that can occur after settings some controls based upon risk identified though risk assessment.
Them comes the second phase of detection and analysis in which all kinds of security breeches
are detected so that organization can be alerted and prepared whenever such kind of incident
occurs so that they can be prepared at that moment. Then comes the Containment, Eradication,
and Recovery phase in which impact of thee risk can be mitigated in order to recover from the
incident or incident can be eradicated. In this phase organization can cycle back to detection and
analysis phase when new incident is about to occur. For example: While eradicating a malicious
software incident, system gets infected by a new infected malware activity. In such case
organization can move ack to previous phase of detection and analysis and only them move
forward to Containment, Eradication, and Recovery phase. After this post- incident handling
activity phase comes into picture. At this phase organization prepare themselves for this incident
if it occurs in future. And move back to preparation phase. Each of these stages or phases can be
explained with the help of a malicious software incident handling example.
Preparation
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

At this phase capability of an incident handling or response is developed so that all the
systems can be prevented from malicious attacks (Ogunyebi, Swar & Aghili, 2018). It is one of
the main success factors of success of incident handling in which it is made sure that systems,
networks, and applications are sufficiently secure. If an organization wants to prepare themselves
from malicious software incident then they need to prepare themselves for the incident handling
and for this two- step can be followed:
Figure 2 NIST 800-61 incident response life- cycle
Preparing to handle incidents: In this step all kinds of resources and tools required for
handling during incident handling. Resources and tools required for malicious software
incident handling are:
Issue tracking system so that incident and its current status can be tacked easily.
Encrypted software so that communication with team members can be done in a
protected manner and malicious software cannot work as a hindrance in communication.
Incident reporting mechanism so that next time whenever this incident occurs again it can
be reported easily.
Backup data so that backup of current organizational data as well as incident data can be
backed up (Bottazzi, Italiano & Rutigliano, 2017).
Spare workstation so that in case of malicious software incident it can be used so that
simultaneously malicious software incident can be talked and work is not hindered.
Preventing incidents: After selecting all the tools and requires required to handle malicious
software incident, assessment is done so that in future occurrence of this incident can be
5
systems can be prevented from malicious attacks (Ogunyebi, Swar & Aghili, 2018). It is one of
the main success factors of success of incident handling in which it is made sure that systems,
networks, and applications are sufficiently secure. If an organization wants to prepare themselves
from malicious software incident then they need to prepare themselves for the incident handling
and for this two- step can be followed:
Figure 2 NIST 800-61 incident response life- cycle
Preparing to handle incidents: In this step all kinds of resources and tools required for
handling during incident handling. Resources and tools required for malicious software
incident handling are:
Issue tracking system so that incident and its current status can be tacked easily.
Encrypted software so that communication with team members can be done in a
protected manner and malicious software cannot work as a hindrance in communication.
Incident reporting mechanism so that next time whenever this incident occurs again it can
be reported easily.
Backup data so that backup of current organizational data as well as incident data can be
backed up (Bottazzi, Italiano & Rutigliano, 2017).
Spare workstation so that in case of malicious software incident it can be used so that
simultaneously malicious software incident can be talked and work is not hindered.
Preventing incidents: After selecting all the tools and requires required to handle malicious
software incident, assessment is done so that in future occurrence of this incident can be
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

prevented. Below explained are some recommended practises that can be used by
organization so that they can handle malicious software incident in future.
Risk assessment: In risk assessment it is identified that want are the main risk associated
with this malicious software incident and what are the threats and vulnerabilities
associated with it. Each of the identified threats and vulnerabilities are then prioritized so
that whenever in future similar incident occurs then as per the priority list it can be
handled either by mitigating, transferring or accepting the risk until it reaches a certain
level.
Host security: All the host should be hardened appropriately. All the host should be
configured according to principles of least privileges. Host should also enable auditing so
that significant security events can be handled accordingly.
Network Security: Network security helps in delaying all the activities whose permission
is not expressed so that threats associated with malicious software cannot further damage
other information or software (Bottazzi, Italiano & Rutigliano, 2017).
Malware prevention: This software should be installed so that malware or malicious
software can be detected and prevented or stopped. This software can be developed at all
the three levels of the system that are host level, application server level and application
client level. This will help in stopping the malicious software to do further damage to the
system.
User Awareness and Training: In this all the users of the system should be provided with
proper training and should be made aware about policies and procedure related to system
or software and lessons from previous incident should be provided to them so that they
can be prepared to handle malicious software incidents if it happens in future.
Detection and Analysis
Incident categories: Malicious software incidents can occur in variety of ways so in this stage
incident is categorised and identified so that it can be handled accordingly such as:
removable media, website and many more.
Sign of an incidents: At this stage sign of incident is identified so that incident response
process can be developed. For this malicious software incidents anti- virus software can be
installed so that it can be detected both manually or automatically and whenever a malicious
6
organization so that they can handle malicious software incident in future.
Risk assessment: In risk assessment it is identified that want are the main risk associated
with this malicious software incident and what are the threats and vulnerabilities
associated with it. Each of the identified threats and vulnerabilities are then prioritized so
that whenever in future similar incident occurs then as per the priority list it can be
handled either by mitigating, transferring or accepting the risk until it reaches a certain
level.
Host security: All the host should be hardened appropriately. All the host should be
configured according to principles of least privileges. Host should also enable auditing so
that significant security events can be handled accordingly.
Network Security: Network security helps in delaying all the activities whose permission
is not expressed so that threats associated with malicious software cannot further damage
other information or software (Bottazzi, Italiano & Rutigliano, 2017).
Malware prevention: This software should be installed so that malware or malicious
software can be detected and prevented or stopped. This software can be developed at all
the three levels of the system that are host level, application server level and application
client level. This will help in stopping the malicious software to do further damage to the
system.
User Awareness and Training: In this all the users of the system should be provided with
proper training and should be made aware about policies and procedure related to system
or software and lessons from previous incident should be provided to them so that they
can be prepared to handle malicious software incidents if it happens in future.
Detection and Analysis
Incident categories: Malicious software incidents can occur in variety of ways so in this stage
incident is categorised and identified so that it can be handled accordingly such as:
removable media, website and many more.
Sign of an incidents: At this stage sign of incident is identified so that incident response
process can be developed. For this malicious software incidents anti- virus software can be
installed so that it can be detected both manually or automatically and whenever a malicious
6

software incident occurs antivirus software can alert when it occurs so that host which is
infected by this software can be detected.
Sources of Precursors and Indicators: in this antivirus software work as a of Precursors and
Indicators in which it helps in detecting malicious software in various forms.
Incident analysis: In this incidents case incident analysis can be done by keeping All Host
Clocks Synchronized. So that it can be identified that which host is infected (Bottazzi,
Italiano & Rutigliano, 2017).
Incident documentation: A case an incident occurs a proper documentation is done in which
summary, indicators, actions taken etc. are documented so that in future it can be used to
handle similar incident.
Containment, Eradication, and Recovery: For this a proper containment strategy is chosen in
which incidents occurrence can be monitored, tracked and handled easily. For this first of all
evidence gathering and handling. For this first of all information related to malicious software
handling is identified, time at which it occurred and location where it occurred is stored. This
will help in handling the incident properly. This will help in eliminating the incidents through
proper eradication and recovery strategy.
Post- Incident Activity: At this phase lessons learned from the incidents is documented,
number od incidents handled is recorded and on the basis of this proper measures are taken so
that in future this incidents ca be handled properly.
EVALUATION AND DISCUSSION
Relationship between information security incident response other information security
processes
Information security incidents handling and information security process has a strong
relationship. NIST 800-61 framework and information security process like risk assessment has
strong relationship. Risk assessment helps in lowering number of incidents, their priorities of
handling and ways in which it can increase vulnerabilities and threats to the system. it further
helps in identifying ways in which identified risk can be mitigated, transferred, or accepted until
and unless risk associated system can be resolved. This risk assessment is used for getting
prepared for incident handling. Results of risk assessment is used by NIST 800-61 framework so
that planning for prevention of incident can be done (Bottazzi, Italiano & Rutigliano, 2017). Risk
assessment is used by incidents response team so that they can identify level of risk, critical
7
infected by this software can be detected.
Sources of Precursors and Indicators: in this antivirus software work as a of Precursors and
Indicators in which it helps in detecting malicious software in various forms.
Incident analysis: In this incidents case incident analysis can be done by keeping All Host
Clocks Synchronized. So that it can be identified that which host is infected (Bottazzi,
Italiano & Rutigliano, 2017).
Incident documentation: A case an incident occurs a proper documentation is done in which
summary, indicators, actions taken etc. are documented so that in future it can be used to
handle similar incident.
Containment, Eradication, and Recovery: For this a proper containment strategy is chosen in
which incidents occurrence can be monitored, tracked and handled easily. For this first of all
evidence gathering and handling. For this first of all information related to malicious software
handling is identified, time at which it occurred and location where it occurred is stored. This
will help in handling the incident properly. This will help in eliminating the incidents through
proper eradication and recovery strategy.
Post- Incident Activity: At this phase lessons learned from the incidents is documented,
number od incidents handled is recorded and on the basis of this proper measures are taken so
that in future this incidents ca be handled properly.
EVALUATION AND DISCUSSION
Relationship between information security incident response other information security
processes
Information security incidents handling and information security process has a strong
relationship. NIST 800-61 framework and information security process like risk assessment has
strong relationship. Risk assessment helps in lowering number of incidents, their priorities of
handling and ways in which it can increase vulnerabilities and threats to the system. it further
helps in identifying ways in which identified risk can be mitigated, transferred, or accepted until
and unless risk associated system can be resolved. This risk assessment is used for getting
prepared for incident handling. Results of risk assessment is used by NIST 800-61 framework so
that planning for prevention of incident can be done (Bottazzi, Italiano & Rutigliano, 2017). Risk
assessment is used by incidents response team so that they can identify level of risk, critical
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

resources that will be used for incident handling so that response activities for preventing
incidents can be handled.
Role of audit in providing assurance that the incident handling process is effective
Audit plays a vital role in incident handling process. Audit can help in identifying
problems and deficiencies within the system that can be corrected. Incident response audit helps
in evaluation of following items against applicable policies, regulations and generally acceptable
practises.
Incident response plan, policy and procedure.
Tools and resources useful for incident response handling
Incident
handler education and training
Incident reports and documentation
Lastly, measuring success factors.
In these ways Audit can help in ensuring success of incident handling process and can
also help in ensuring that the process or procedure developed for incident handling is effective
and can help in handing incident successfully. Not only this it also helps in ensuring that if in
future similar incident occurs then the high- level guidance developed is effective enough to
tackle similar incident in future.
Governance and compliance issues raised and the professional roles involved in managing them.
There are various kinds of Professional roles involved in security incident handling. But some of
the most important processional roles involved in this are:
Legal experts who review incident response procedure, plan and policies for ensuing
compliance with law (NIST SP 800-61, 2012).
Management team for establishment of incident response policy, budget, and staffing.
Information security staff members who play a vital role during stages of information
handling poorly-handled information security incidents in a proper and appropriate manner.
IT technical experts for handing attacked system. they are the one who take important
decision related to attacked system.
There are various kinds of governance and compliance issues associated with incident
handing and management when management of professional team involved in incident handing
comes into picture. If incident review plan, policies and procedures should comply with law and
8
incidents can be handled.
Role of audit in providing assurance that the incident handling process is effective
Audit plays a vital role in incident handling process. Audit can help in identifying
problems and deficiencies within the system that can be corrected. Incident response audit helps
in evaluation of following items against applicable policies, regulations and generally acceptable
practises.
Incident response plan, policy and procedure.
Tools and resources useful for incident response handling
Incident
handler education and training
Incident reports and documentation
Lastly, measuring success factors.
In these ways Audit can help in ensuring success of incident handling process and can
also help in ensuring that the process or procedure developed for incident handling is effective
and can help in handing incident successfully. Not only this it also helps in ensuring that if in
future similar incident occurs then the high- level guidance developed is effective enough to
tackle similar incident in future.
Governance and compliance issues raised and the professional roles involved in managing them.
There are various kinds of Professional roles involved in security incident handling. But some of
the most important processional roles involved in this are:
Legal experts who review incident response procedure, plan and policies for ensuing
compliance with law (NIST SP 800-61, 2012).
Management team for establishment of incident response policy, budget, and staffing.
Information security staff members who play a vital role during stages of information
handling poorly-handled information security incidents in a proper and appropriate manner.
IT technical experts for handing attacked system. they are the one who take important
decision related to attacked system.
There are various kinds of governance and compliance issues associated with incident
handing and management when management of professional team involved in incident handing
comes into picture. If incident review plan, policies and procedures should comply with law and
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

federal guidance in order to adhere right to privacy. Not doing so can create right to privacy
issue. Policy and procedure developed for incident handling should comply with business
process modelling rules so that negative impact of risk can be reduced. NIST framework has its
own compliance which is one of the most important part of essential guidance and requirements.
Not ensuring information procedure compliance with information security requirements can
result in privacy and security issues. Some of the most common governance issue that can be
raised while management of teams involved in incident handling procedure are: issue of
balancing extensive requirements from multiple governing bodies, issues associated with
balancing organization policy and legislation.
CONCLUSION
From the above report it has been identified that NIST 800-61 model has various kinds of
strengths and weaknesses. One of the main strengths of this model is that it helps in continuous
improvement within incident handling procedure. It helps in collecting all kinds of
comprehensive information related to incident and ways in which it can impact the business. But
it has some weaknesses as well such as it does not define role of all the stakeholders properly.
Recommendations
Form this analysis there are various kinds of recommendation that senior management of
the organization can focus upon. Some of the recommendations are as follows:
Organization can focus upon acquiring important and valuable tools and resources that can
be used for different categories of incident handling
Security of network, system and other applications should be reviewed continuously so that
other category incidents can be prevented from occurring.
9
issue. Policy and procedure developed for incident handling should comply with business
process modelling rules so that negative impact of risk can be reduced. NIST framework has its
own compliance which is one of the most important part of essential guidance and requirements.
Not ensuring information procedure compliance with information security requirements can
result in privacy and security issues. Some of the most common governance issue that can be
raised while management of teams involved in incident handling procedure are: issue of
balancing extensive requirements from multiple governing bodies, issues associated with
balancing organization policy and legislation.
CONCLUSION
From the above report it has been identified that NIST 800-61 model has various kinds of
strengths and weaknesses. One of the main strengths of this model is that it helps in continuous
improvement within incident handling procedure. It helps in collecting all kinds of
comprehensive information related to incident and ways in which it can impact the business. But
it has some weaknesses as well such as it does not define role of all the stakeholders properly.
Recommendations
Form this analysis there are various kinds of recommendation that senior management of
the organization can focus upon. Some of the recommendations are as follows:
Organization can focus upon acquiring important and valuable tools and resources that can
be used for different categories of incident handling
Security of network, system and other applications should be reviewed continuously so that
other category incidents can be prevented from occurring.
9

REREFENCES
Books and Journals
Alsmadi, I., (2019). Incident response. In The NICE Cyber Security Framework (pp. 331-346).
Springer, Cham.
Barker, E., & Dang, Q. (2016). Nist special publication 800-57 part 1, revision 4. NIST, Tech.
Rep.
Bottazzi, G., Italiano, G. F., & Rutigliano, G. G. (2017). An Operational Framework for Incident
Handling. In ITASEC (pp. 126-135).
Grassi, P.A., Garcia, M.E. & Fenton, J.L., (2017). DRAFT NIST Special Publication 800-63-3
Digital Identity Guidelines. National Institute of Standards and Technology, Los Altos,
CA.
Ogunyebi, O., Swar, B., & Aghili, S. (2018, March). An Incident Handling Guide for Small
Organizations in the Hospitality Sector. In World Conference on Information Systems
and Technologies (pp. 232-241). Springer, Cham.
Papastergiou, S., Mouratidis, H. & Kalogeraki, E.M., (2019), May. Cyber Security Incident
Handling, Warning and Response System for the European Critical Information
Infrastructures (CyberSANE). In International Conference on Engineering Applications
of Neural Networks (pp. 476-487). Springer, Cham.
Simmon, E. (2018). Evaluation of Cloud Computing Services Based on NIST SP 800-145. NIST
Spec. Publ. 500. 322.
Thompson, E. C. (2018). Incident response frameworks. In Cybersecurity incident response (pp.
17-46). Apress, Berkeley, CA.
Zhu, S., & et.al. (2016, December). More powerful and reliable second-level statistical
randomness tests for NIST SP 800-22. In International Conference on the Theory and
Application of Cryptology and Information Security (pp. 307-329). Springer, Berlin,
Heidelberg.
Online
NIST SP 800-61. 2012. [Online]. Available Through:
<https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf>
10
Books and Journals
Alsmadi, I., (2019). Incident response. In The NICE Cyber Security Framework (pp. 331-346).
Springer, Cham.
Barker, E., & Dang, Q. (2016). Nist special publication 800-57 part 1, revision 4. NIST, Tech.
Rep.
Bottazzi, G., Italiano, G. F., & Rutigliano, G. G. (2017). An Operational Framework for Incident
Handling. In ITASEC (pp. 126-135).
Grassi, P.A., Garcia, M.E. & Fenton, J.L., (2017). DRAFT NIST Special Publication 800-63-3
Digital Identity Guidelines. National Institute of Standards and Technology, Los Altos,
CA.
Ogunyebi, O., Swar, B., & Aghili, S. (2018, March). An Incident Handling Guide for Small
Organizations in the Hospitality Sector. In World Conference on Information Systems
and Technologies (pp. 232-241). Springer, Cham.
Papastergiou, S., Mouratidis, H. & Kalogeraki, E.M., (2019), May. Cyber Security Incident
Handling, Warning and Response System for the European Critical Information
Infrastructures (CyberSANE). In International Conference on Engineering Applications
of Neural Networks (pp. 476-487). Springer, Cham.
Simmon, E. (2018). Evaluation of Cloud Computing Services Based on NIST SP 800-145. NIST
Spec. Publ. 500. 322.
Thompson, E. C. (2018). Incident response frameworks. In Cybersecurity incident response (pp.
17-46). Apress, Berkeley, CA.
Zhu, S., & et.al. (2016, December). More powerful and reliable second-level statistical
randomness tests for NIST SP 800-22. In International Conference on the Theory and
Application of Cryptology and Information Security (pp. 307-329). Springer, Berlin,
Heidelberg.
Online
NIST SP 800-61. 2012. [Online]. Available Through:
<https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf>
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





