Security in the Internet of Things: Threats, Attacks, and Solutions
VerifiedAdded on 2020/02/24
|8
|1638
|41
Report
AI Summary
This report provides a comprehensive overview of security in the Internet of Things (IoT). It begins by introducing the concept of IoT and highlights the associated security risks stemming from the diverse entities involved in IoT applications. The report details various security threats, including physical attacks targeting devices, network attacks like RFID spoofing and man-in-the-middle attacks, software attacks involving malware and DDoS, and encryption attacks. It then explores recommended security measures, such as advanced protection mechanisms for physical devices, network intrusion detection and prevention tools, anti-malware software, and advanced encryption algorithms. Furthermore, the report emphasizes the importance of access controls, security audits, and user awareness to mitigate risks. The conclusion underscores the need for continuous vigilance and proactive security measures to ensure the confidentiality, availability, and integrity of information in IoT environments. The report also includes references to relevant research papers and articles.

Security in Internet of Things (IoT)
8/28/2017
8/28/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security in IoT
Introduction
Security has become a prime topic of research with the emergence of numerous security attacks
and occurrences. Internet of Things (IoT) is a concept that includes a wide variety of services,
devices and networks to achieve a particular objective. There are various different entities that
are involved at the same time in an application that is built using IoT as the base technology. Due
to this reason, it has been observed that there are many security risks and concerns that have
taken place in IoT applications and services.
Descriptions of such occurrences along with the countermeasures that may be used to put a
check on the same have been covered in the report.
IoT Security Risks and Events
Physical Attacks
There are a number of physical security attacks that may be executed in case of the IoT
applications.
These applications involve a number of different devices such as small and large household
appliances, laptops, tablets, Smartphones etc. There may be cases wherein the attackers might
steal or cause damage to these devices which will be threatening from the security point of view.
There are various nodes in the different networks that are used in the IoT applications. Any
damage to these nodes may be done to gain access to the materials and information associated
with a particular node.
There are also attacks that may be launched by the attackers which may lead to quick drainage of
the battery of the devices. This may cause a negative impact on the availability of the services
and the application and may be negative from the security aspect as well (Kumar and Patel,
2014).
Network Attacks
There are a wide variety of network based security attacks that may be executed in association
with an IoT application.
2
Introduction
Security has become a prime topic of research with the emergence of numerous security attacks
and occurrences. Internet of Things (IoT) is a concept that includes a wide variety of services,
devices and networks to achieve a particular objective. There are various different entities that
are involved at the same time in an application that is built using IoT as the base technology. Due
to this reason, it has been observed that there are many security risks and concerns that have
taken place in IoT applications and services.
Descriptions of such occurrences along with the countermeasures that may be used to put a
check on the same have been covered in the report.
IoT Security Risks and Events
Physical Attacks
There are a number of physical security attacks that may be executed in case of the IoT
applications.
These applications involve a number of different devices such as small and large household
appliances, laptops, tablets, Smartphones etc. There may be cases wherein the attackers might
steal or cause damage to these devices which will be threatening from the security point of view.
There are various nodes in the different networks that are used in the IoT applications. Any
damage to these nodes may be done to gain access to the materials and information associated
with a particular node.
There are also attacks that may be launched by the attackers which may lead to quick drainage of
the battery of the devices. This may cause a negative impact on the availability of the services
and the application and may be negative from the security aspect as well (Kumar and Patel,
2014).
Network Attacks
There are a wide variety of network based security attacks that may be executed in association
with an IoT application.
2
Security in IoT
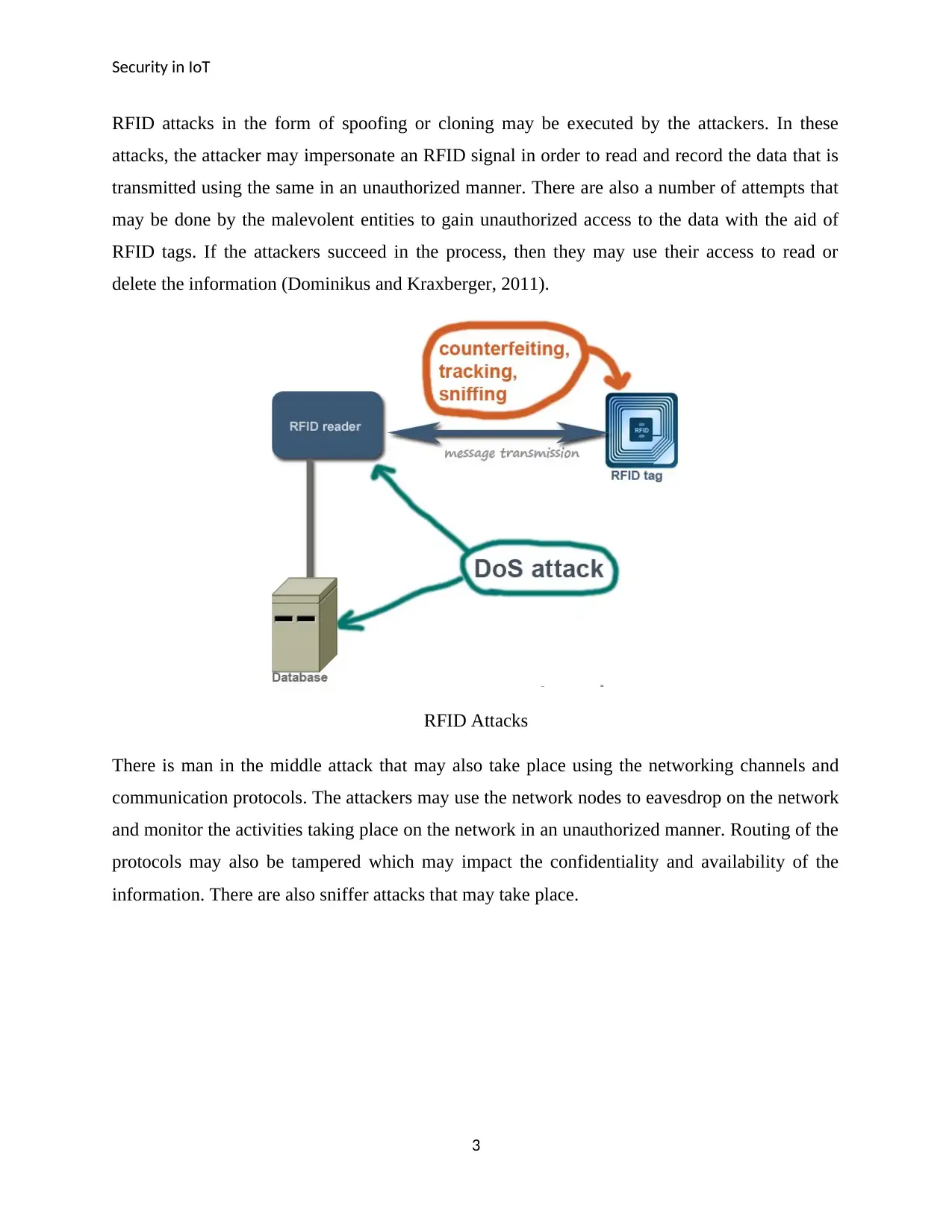
RFID attacks in the form of spoofing or cloning may be executed by the attackers. In these
attacks, the attacker may impersonate an RFID signal in order to read and record the data that is
transmitted using the same in an unauthorized manner. There are also a number of attempts that
may be done by the malevolent entities to gain unauthorized access to the data with the aid of
RFID tags. If the attackers succeed in the process, then they may use their access to read or
delete the information (Dominikus and Kraxberger, 2011).
RFID Attacks
There is man in the middle attack that may also take place using the networking channels and
communication protocols. The attackers may use the network nodes to eavesdrop on the network
and monitor the activities taking place on the network in an unauthorized manner. Routing of the
protocols may also be tampered which may impact the confidentiality and availability of the
information. There are also sniffer attacks that may take place.
3
RFID attacks in the form of spoofing or cloning may be executed by the attackers. In these
attacks, the attacker may impersonate an RFID signal in order to read and record the data that is
transmitted using the same in an unauthorized manner. There are also a number of attempts that
may be done by the malevolent entities to gain unauthorized access to the data with the aid of
RFID tags. If the attackers succeed in the process, then they may use their access to read or
delete the information (Dominikus and Kraxberger, 2011).
RFID Attacks
There is man in the middle attack that may also take place using the networking channels and
communication protocols. The attackers may use the network nodes to eavesdrop on the network
and monitor the activities taking place on the network in an unauthorized manner. Routing of the
protocols may also be tampered which may impact the confidentiality and availability of the
information. There are also sniffer attacks that may take place.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
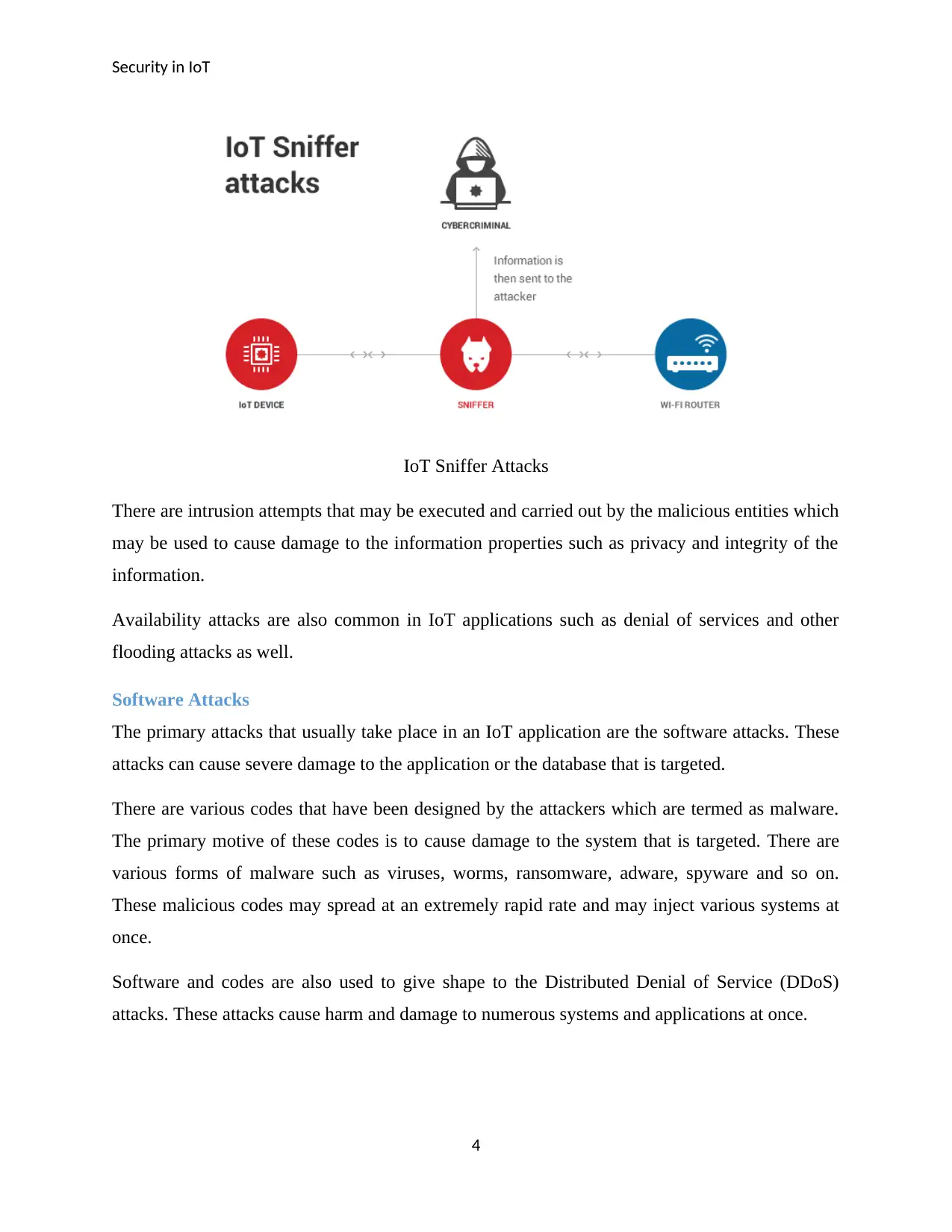
Security in IoT
IoT Sniffer Attacks
There are intrusion attempts that may be executed and carried out by the malicious entities which
may be used to cause damage to the information properties such as privacy and integrity of the
information.
Availability attacks are also common in IoT applications such as denial of services and other
flooding attacks as well.
Software Attacks
The primary attacks that usually take place in an IoT application are the software attacks. These
attacks can cause severe damage to the application or the database that is targeted.
There are various codes that have been designed by the attackers which are termed as malware.
The primary motive of these codes is to cause damage to the system that is targeted. There are
various forms of malware such as viruses, worms, ransomware, adware, spyware and so on.
These malicious codes may spread at an extremely rapid rate and may inject various systems at
once.
Software and codes are also used to give shape to the Distributed Denial of Service (DDoS)
attacks. These attacks cause harm and damage to numerous systems and applications at once.
4
IoT Sniffer Attacks
There are intrusion attempts that may be executed and carried out by the malicious entities which
may be used to cause damage to the information properties such as privacy and integrity of the
information.
Availability attacks are also common in IoT applications such as denial of services and other
flooding attacks as well.
Software Attacks
The primary attacks that usually take place in an IoT application are the software attacks. These
attacks can cause severe damage to the application or the database that is targeted.
There are various codes that have been designed by the attackers which are termed as malware.
The primary motive of these codes is to cause damage to the system that is targeted. There are
various forms of malware such as viruses, worms, ransomware, adware, spyware and so on.
These malicious codes may spread at an extremely rapid rate and may inject various systems at
once.
Software and codes are also used to give shape to the Distributed Denial of Service (DDoS)
attacks. These attacks cause harm and damage to numerous systems and applications at once.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
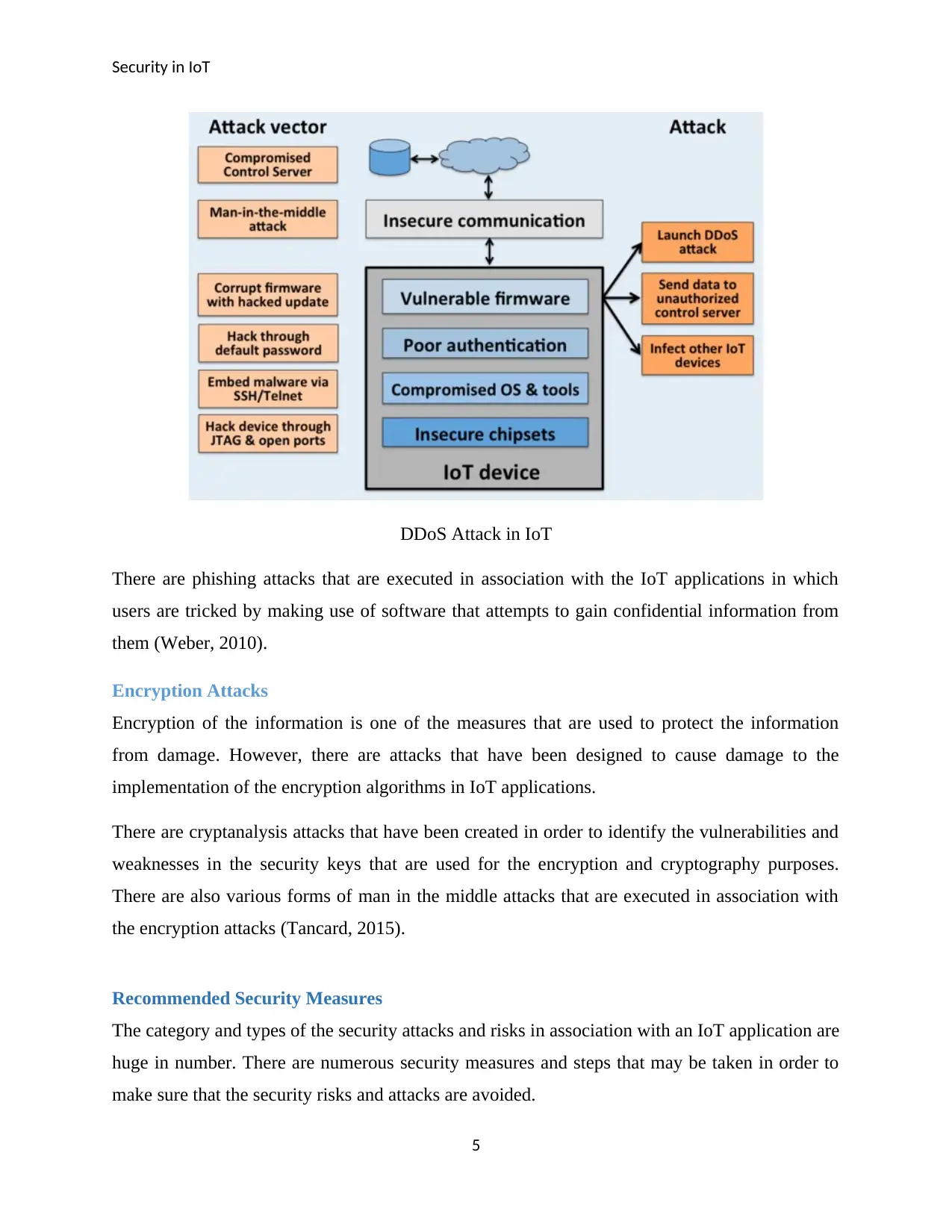
Security in IoT
DDoS Attack in IoT
There are phishing attacks that are executed in association with the IoT applications in which
users are tricked by making use of software that attempts to gain confidential information from
them (Weber, 2010).
Encryption Attacks
Encryption of the information is one of the measures that are used to protect the information
from damage. However, there are attacks that have been designed to cause damage to the
implementation of the encryption algorithms in IoT applications.
There are cryptanalysis attacks that have been created in order to identify the vulnerabilities and
weaknesses in the security keys that are used for the encryption and cryptography purposes.
There are also various forms of man in the middle attacks that are executed in association with
the encryption attacks (Tancard, 2015).
Recommended Security Measures
The category and types of the security attacks and risks in association with an IoT application are
huge in number. There are numerous security measures and steps that may be taken in order to
make sure that the security risks and attacks are avoided.
5
DDoS Attack in IoT
There are phishing attacks that are executed in association with the IoT applications in which
users are tricked by making use of software that attempts to gain confidential information from
them (Weber, 2010).
Encryption Attacks
Encryption of the information is one of the measures that are used to protect the information
from damage. However, there are attacks that have been designed to cause damage to the
implementation of the encryption algorithms in IoT applications.
There are cryptanalysis attacks that have been created in order to identify the vulnerabilities and
weaknesses in the security keys that are used for the encryption and cryptography purposes.
There are also various forms of man in the middle attacks that are executed in association with
the encryption attacks (Tancard, 2015).
Recommended Security Measures
The category and types of the security attacks and risks in association with an IoT application are
huge in number. There are numerous security measures and steps that may be taken in order to
make sure that the security risks and attacks are avoided.
5
Security in IoT
Physical attacks to security can be prevented and controlled by making use of advanced
protection mechanisms for the devices. These mechanisms may use two-fold
authentication processes to protect the device information along with the implementation
of the tracking tools in the devices. In such a manner, the occurrences of device loss and
misuse of the device information will be prohibited (Taylor, 2017).
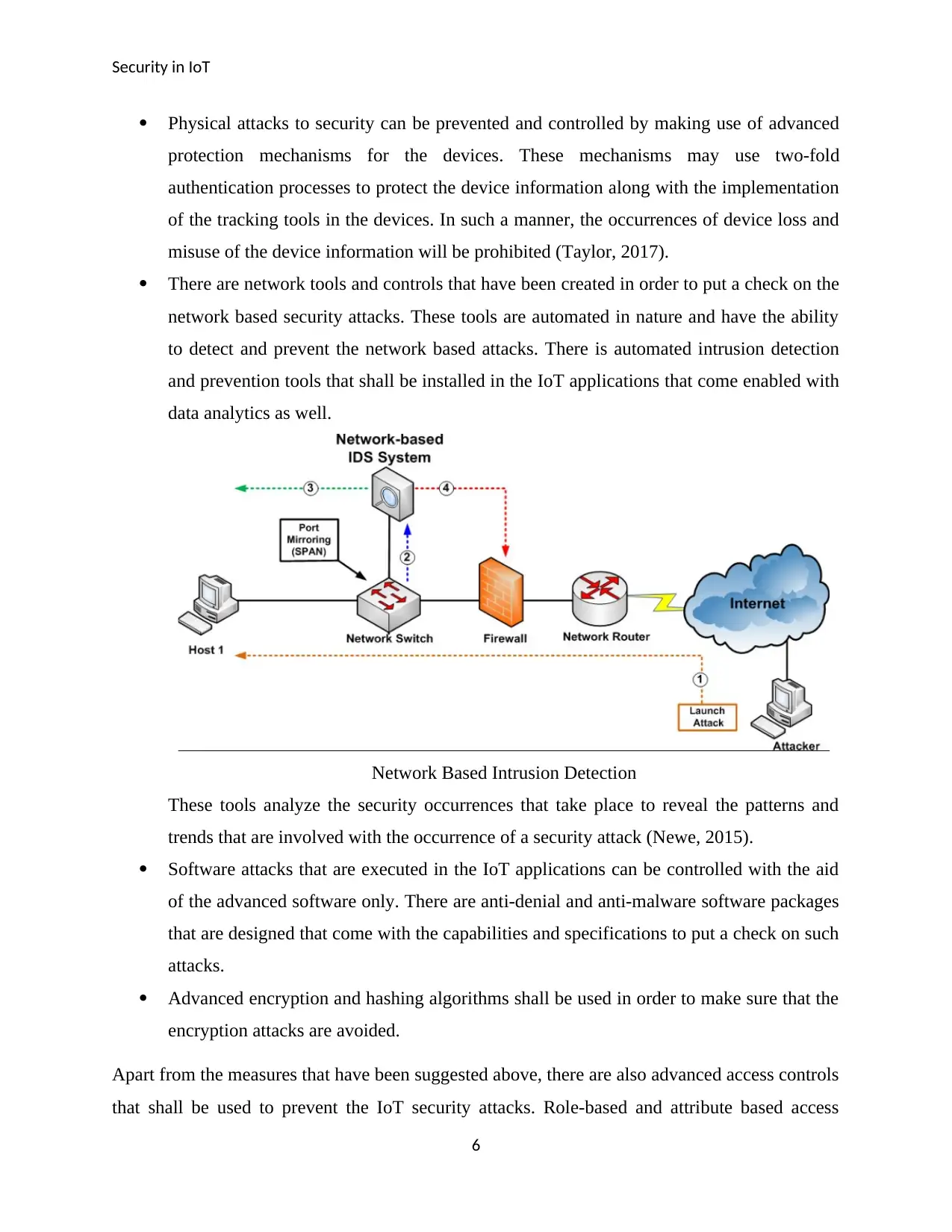
There are network tools and controls that have been created in order to put a check on the
network based security attacks. These tools are automated in nature and have the ability
to detect and prevent the network based attacks. There is automated intrusion detection
and prevention tools that shall be installed in the IoT applications that come enabled with
data analytics as well.
Network Based Intrusion Detection
These tools analyze the security occurrences that take place to reveal the patterns and
trends that are involved with the occurrence of a security attack (Newe, 2015).
Software attacks that are executed in the IoT applications can be controlled with the aid
of the advanced software only. There are anti-denial and anti-malware software packages
that are designed that come with the capabilities and specifications to put a check on such
attacks.
Advanced encryption and hashing algorithms shall be used in order to make sure that the
encryption attacks are avoided.
Apart from the measures that have been suggested above, there are also advanced access controls
that shall be used to prevent the IoT security attacks. Role-based and attribute based access
6
Physical attacks to security can be prevented and controlled by making use of advanced
protection mechanisms for the devices. These mechanisms may use two-fold
authentication processes to protect the device information along with the implementation
of the tracking tools in the devices. In such a manner, the occurrences of device loss and
misuse of the device information will be prohibited (Taylor, 2017).
There are network tools and controls that have been created in order to put a check on the
network based security attacks. These tools are automated in nature and have the ability
to detect and prevent the network based attacks. There is automated intrusion detection
and prevention tools that shall be installed in the IoT applications that come enabled with
data analytics as well.
Network Based Intrusion Detection
These tools analyze the security occurrences that take place to reveal the patterns and
trends that are involved with the occurrence of a security attack (Newe, 2015).
Software attacks that are executed in the IoT applications can be controlled with the aid
of the advanced software only. There are anti-denial and anti-malware software packages
that are designed that come with the capabilities and specifications to put a check on such
attacks.
Advanced encryption and hashing algorithms shall be used in order to make sure that the
encryption attacks are avoided.
Apart from the measures that have been suggested above, there are also advanced access controls
that shall be used to prevent the IoT security attacks. Role-based and attribute based access
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Security in IoT
controls shall be used and implemented to make sure that the security occurrences do not take
place (Cerf, 2015).
There are also administrative steps that the IoT vendors must take place to monitor and control
the security status during the design and development of the application. Security audits and
reviews along with security inspections shall be carried out to ensure that the best security steps
are taken and implemented in the IoT application (Maras, 2015).
Conclusion
IoT is one of the latest technologies that is being used and applied in the present times. There are
various security risks and attacks that may take place in association with the IoT services and
applications. These occurrences may cause damage to the devices and the networks that are
involved in an IoT application and can also be negative for the information properties such as
confidentiality, availability and integrity. There are advanced tools and mechanisms that have
been developed and are available in the market to detect and prevent the security risks and
attacks. Also, the users of the IoT application must be informed and made aware about the
possible risks and threats. The users must take the basic steps towards security such as use of
stronger passwords, protection of their devices etc. to avoid the security attacks from taking
place.
7
controls shall be used and implemented to make sure that the security occurrences do not take
place (Cerf, 2015).
There are also administrative steps that the IoT vendors must take place to monitor and control
the security status during the design and development of the application. Security audits and
reviews along with security inspections shall be carried out to ensure that the best security steps
are taken and implemented in the IoT application (Maras, 2015).
Conclusion
IoT is one of the latest technologies that is being used and applied in the present times. There are
various security risks and attacks that may take place in association with the IoT services and
applications. These occurrences may cause damage to the devices and the networks that are
involved in an IoT application and can also be negative for the information properties such as
confidentiality, availability and integrity. There are advanced tools and mechanisms that have
been developed and are available in the market to detect and prevent the security risks and
attacks. Also, the users of the IoT application must be informed and made aware about the
possible risks and threats. The users must take the basic steps towards security such as use of
stronger passwords, protection of their devices etc. to avoid the security attacks from taking
place.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security in IoT
References
Cerf, V. (2015). Access Control and the Internet of Things. IEEE Internet Computing, 19(5),
pp.96-c3.
Dominikus, S. and Kraxberger, S. (2011). Secure Communication with RFID tags in the Internet
of Things. Security and Communication Networks, 7(12), pp.2639-2653.
Kumar, J. and Patel, D. (2014). A Survey on Internet of Things: Security and Privacy Issues.
International Journal of Computer Applications, 90(11), pp.20-26.
Maras, M. (2015). Internet of Things: security and privacy implications. International Data
Privacy Law, 5(2), pp.99-104.
Newe, G. (2015). Delivering the Internet of Things. Network Security, 2015(3), pp.18-20.
Tankard, C. (2015). The security issues of the Internet of Things. Computer Fraud & Security,
2015(9), pp.11-14.
Taylor, M. (2017). An access control management protocol for Internet of Things devices.
Network Security, 2017(7), pp.11-17.
Weber, R. (2010). Internet of Things – New security and privacy challenges. Computer Law &
Security Review, 26(1), pp.23-30.
8
References
Cerf, V. (2015). Access Control and the Internet of Things. IEEE Internet Computing, 19(5),
pp.96-c3.
Dominikus, S. and Kraxberger, S. (2011). Secure Communication with RFID tags in the Internet
of Things. Security and Communication Networks, 7(12), pp.2639-2653.
Kumar, J. and Patel, D. (2014). A Survey on Internet of Things: Security and Privacy Issues.
International Journal of Computer Applications, 90(11), pp.20-26.
Maras, M. (2015). Internet of Things: security and privacy implications. International Data
Privacy Law, 5(2), pp.99-104.
Newe, G. (2015). Delivering the Internet of Things. Network Security, 2015(3), pp.18-20.
Tankard, C. (2015). The security issues of the Internet of Things. Computer Fraud & Security,
2015(9), pp.11-14.
Taylor, M. (2017). An access control management protocol for Internet of Things devices.
Network Security, 2017(7), pp.11-17.
Weber, R. (2010). Internet of Things – New security and privacy challenges. Computer Law &
Security Review, 26(1), pp.23-30.
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





