Comprehensive Security Management Plan and Analysis
VerifiedAdded on 2022/08/15
|11
|1883
|12
Report
AI Summary
This report details a comprehensive security management plan for a company specializing in physical and personal protection, focusing on cybersecurity. It begins with a hiring matrix for trained personnel, outlining required experience and eligibility criteria, followed by a discussion of company policies governing network services, data security, and incident response. The report identifies potential liability issues, including workplace safety and professional liability, and proposes an operating budget for the coming fiscal year, including cost-benefit analysis. It also outlines a plan for handling internal complaints related to discrimination, harassment, and misconduct, emphasizing employee education and policy enforcement. The conclusion summarizes the key components of the plan, highlighting the importance of compliance and effective management in maintaining a secure and compliant environment. The report provides valuable insights into managing security risks and ensuring operational effectiveness.

Running Head: SECURITY PLAN
Security Management Plan
Name of the Student
Name of the University
Author Note
Security Management Plan
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY PLAN
Table of Contents
Introduction......................................................................................................................................2
Matrix for hiring trained personnel..................................................................................................2
Company Policy...............................................................................................................................3
Liability Issues.................................................................................................................................4
Development of operating budget for the coming Fiscal Year........................................................5
Plan for handling complaints and compliance.................................................................................7
Conclusion.......................................................................................................................................8
Reference.........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................2
Matrix for hiring trained personnel..................................................................................................2
Company Policy...............................................................................................................................3
Liability Issues.................................................................................................................................4
Development of operating budget for the coming Fiscal Year........................................................5
Plan for handling complaints and compliance.................................................................................7
Conclusion.......................................................................................................................................8
Reference.........................................................................................................................................9
2SECURITY PLAN
Introduction
The company deals with providing physical and personal protection in terms of computer
and mobile devices. The security of the assets of the company is also important in the company
(Nielsen, 2015). In order to provide required amount of services to the customers more trained
officers will be required in the company.
In the below report the hiring matrix will be discussed along with company policies,
identification of liability issues, development of operation budget for the coming fiscal year and
procedures to handle the complaints and compliance with harassment, discrimination and
misconduct within the company.
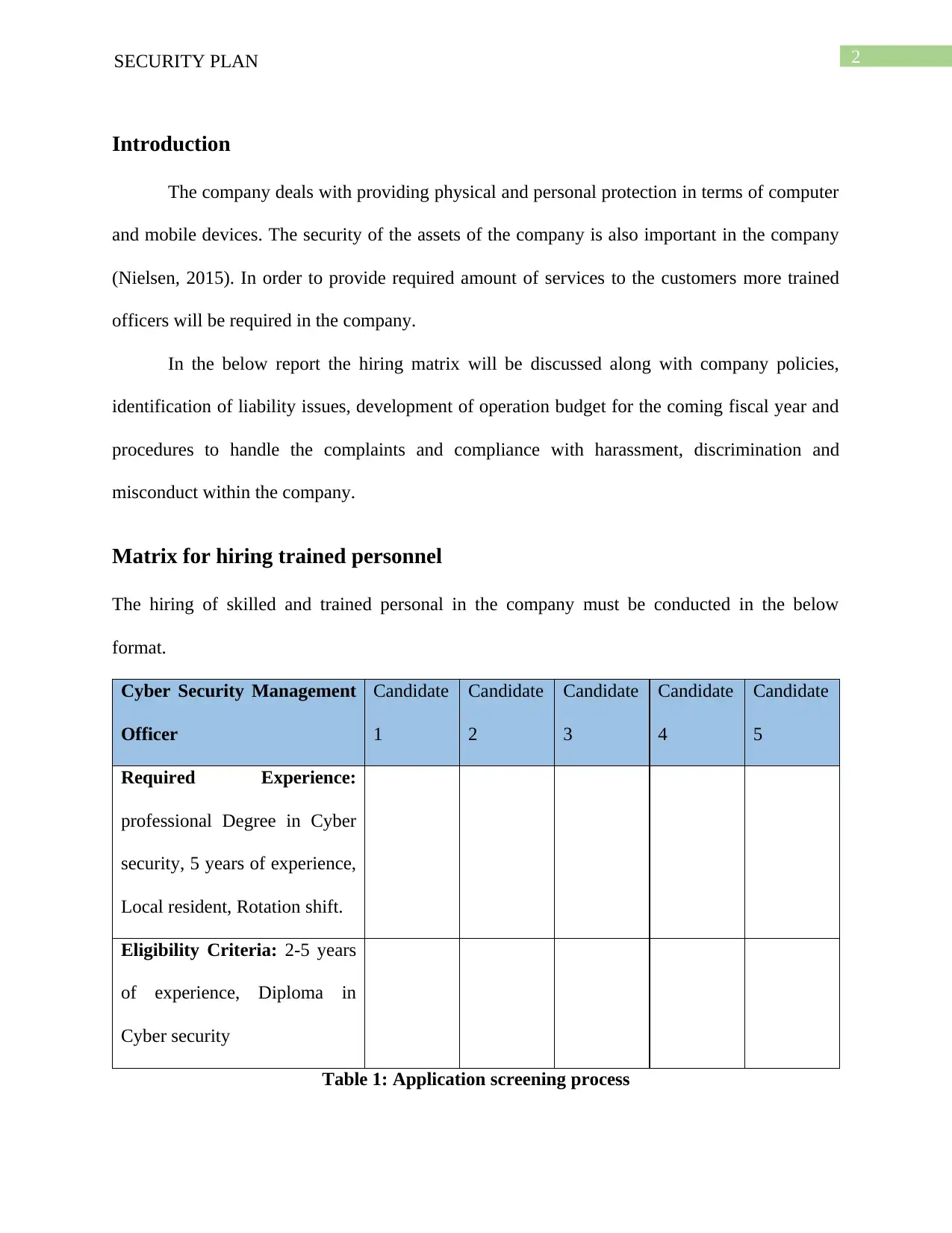
Matrix for hiring trained personnel
The hiring of skilled and trained personal in the company must be conducted in the below
format.
Cyber Security Management
Officer
Candidate
1
Candidate
2
Candidate
3
Candidate
4
Candidate
5
Required Experience:
professional Degree in Cyber
security, 5 years of experience,
Local resident, Rotation shift.
Eligibility Criteria: 2-5 years
of experience, Diploma in
Cyber security
Table 1: Application screening process
Introduction
The company deals with providing physical and personal protection in terms of computer
and mobile devices. The security of the assets of the company is also important in the company
(Nielsen, 2015). In order to provide required amount of services to the customers more trained
officers will be required in the company.
In the below report the hiring matrix will be discussed along with company policies,
identification of liability issues, development of operation budget for the coming fiscal year and
procedures to handle the complaints and compliance with harassment, discrimination and
misconduct within the company.
Matrix for hiring trained personnel
The hiring of skilled and trained personal in the company must be conducted in the below
format.
Cyber Security Management
Officer
Candidate
1
Candidate
2
Candidate
3
Candidate
4
Candidate
5
Required Experience:
professional Degree in Cyber
security, 5 years of experience,
Local resident, Rotation shift.
Eligibility Criteria: 2-5 years
of experience, Diploma in
Cyber security
Table 1: Application screening process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SECURITY PLAN
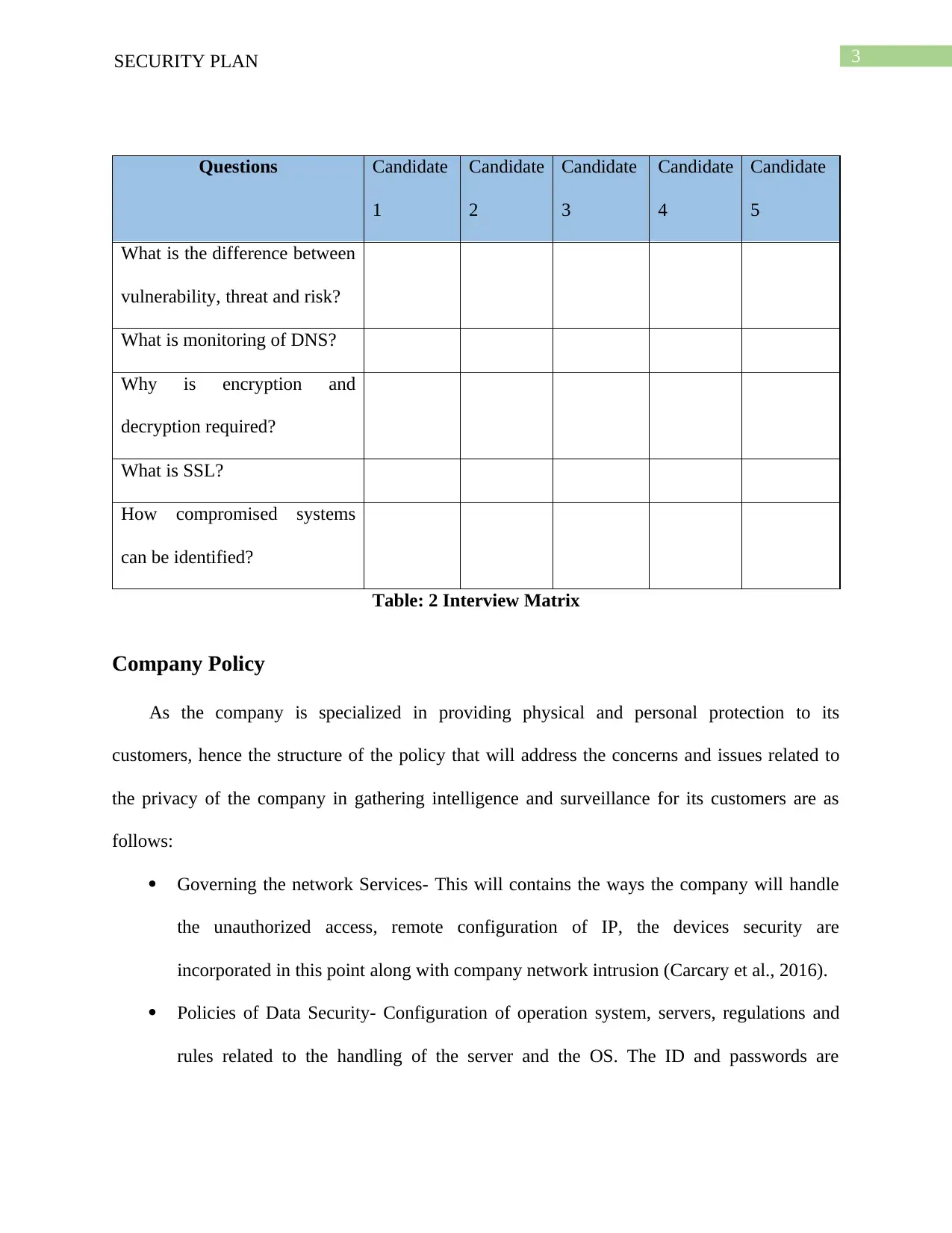
Questions Candidate
1
Candidate
2
Candidate
3
Candidate
4
Candidate
5
What is the difference between
vulnerability, threat and risk?
What is monitoring of DNS?
Why is encryption and
decryption required?
What is SSL?
How compromised systems
can be identified?
Table: 2 Interview Matrix
Company Policy
As the company is specialized in providing physical and personal protection to its
customers, hence the structure of the policy that will address the concerns and issues related to
the privacy of the company in gathering intelligence and surveillance for its customers are as
follows:
Governing the network Services- This will contains the ways the company will handle
the unauthorized access, remote configuration of IP, the devices security are
incorporated in this point along with company network intrusion (Carcary et al., 2016).
Policies of Data Security- Configuration of operation system, servers, regulations and
rules related to the handling of the server and the OS. The ID and passwords are
Questions Candidate
1
Candidate
2
Candidate
3
Candidate
4
Candidate
5
What is the difference between
vulnerability, threat and risk?
What is monitoring of DNS?
Why is encryption and
decryption required?
What is SSL?
How compromised systems
can be identified?
Table: 2 Interview Matrix
Company Policy
As the company is specialized in providing physical and personal protection to its
customers, hence the structure of the policy that will address the concerns and issues related to
the privacy of the company in gathering intelligence and surveillance for its customers are as
follows:
Governing the network Services- This will contains the ways the company will handle
the unauthorized access, remote configuration of IP, the devices security are
incorporated in this point along with company network intrusion (Carcary et al., 2016).
Policies of Data Security- Configuration of operation system, servers, regulations and
rules related to the handling of the server and the OS. The ID and passwords are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY PLAN
managed well. The presence of firewall, antiviruses and safety of database are included
too.
Monitor compliances- Regulatory auditing is done to track the compliance of the
employees with the policies of the company (Zudrags et al., 2015).
Incident response plan- Any data breach or abnormalities are acknowledged at the latest
time and response plans are initiated with a pre-defined team (Soomro, Shah & Ahmed,
2016). This involves reporting of the issues and thorough evaluation of its source and
cause.
Accountability of Data Security- The employees of the company are made aware of
their duties and responsibilities (Ahmad, Maynard & Park, 2014). The confidentiality of
the customer’s information and orders are maintained well.
Patch Management- The vulnerabilities and threats are avoided with proper patch
management, regulatory updates of the system, etc.
Liability Issues
As a company owner the prime concern is to mitigate the risks associated with the company
to provide risk free environment for the employees and provide products and services with best
quality. However, the most concerned situation in security providing company is the liability
issues (Collingwood, 2017). Hence, minimizing the issues is the greatest concern by the proper
liability management plan. The various liability issues are as follows:
Workplace Safety- The proper schedule of duty hours and tasks to maintain safety in the
workplace. The availability of required equipment for the employees. The health of the
employees must be given priority.
managed well. The presence of firewall, antiviruses and safety of database are included
too.
Monitor compliances- Regulatory auditing is done to track the compliance of the
employees with the policies of the company (Zudrags et al., 2015).
Incident response plan- Any data breach or abnormalities are acknowledged at the latest
time and response plans are initiated with a pre-defined team (Soomro, Shah & Ahmed,
2016). This involves reporting of the issues and thorough evaluation of its source and
cause.
Accountability of Data Security- The employees of the company are made aware of
their duties and responsibilities (Ahmad, Maynard & Park, 2014). The confidentiality of
the customer’s information and orders are maintained well.
Patch Management- The vulnerabilities and threats are avoided with proper patch
management, regulatory updates of the system, etc.
Liability Issues
As a company owner the prime concern is to mitigate the risks associated with the company
to provide risk free environment for the employees and provide products and services with best
quality. However, the most concerned situation in security providing company is the liability
issues (Collingwood, 2017). Hence, minimizing the issues is the greatest concern by the proper
liability management plan. The various liability issues are as follows:
Workplace Safety- The proper schedule of duty hours and tasks to maintain safety in the
workplace. The availability of required equipment for the employees. The health of the
employees must be given priority.
5SECURITY PLAN
Professional liability- In the profession setting the rise in obligations, negligence of
practices must be accounted. The damages occurred in the profession field are
incorporated as the professional liabilities.
Product and service Safety- The defects in products or poor quality of services to the
clients are the responsibility of the concerned employee. The laws acts against such
situations. The consumers of the service or product gets benefited from this.
Management Liability- The exposures that received by the officials of management level
from the finances, governance and activities performed by the managers only. It can
occur all throughout the business or till the company runs.
Premises Liability- This depend on the area the company is situated. Any visitor to the
location of the company must be treated well and with proper care (Sundararajan, 2014).
The company may be sued if any accident occurs within the premises of the company.
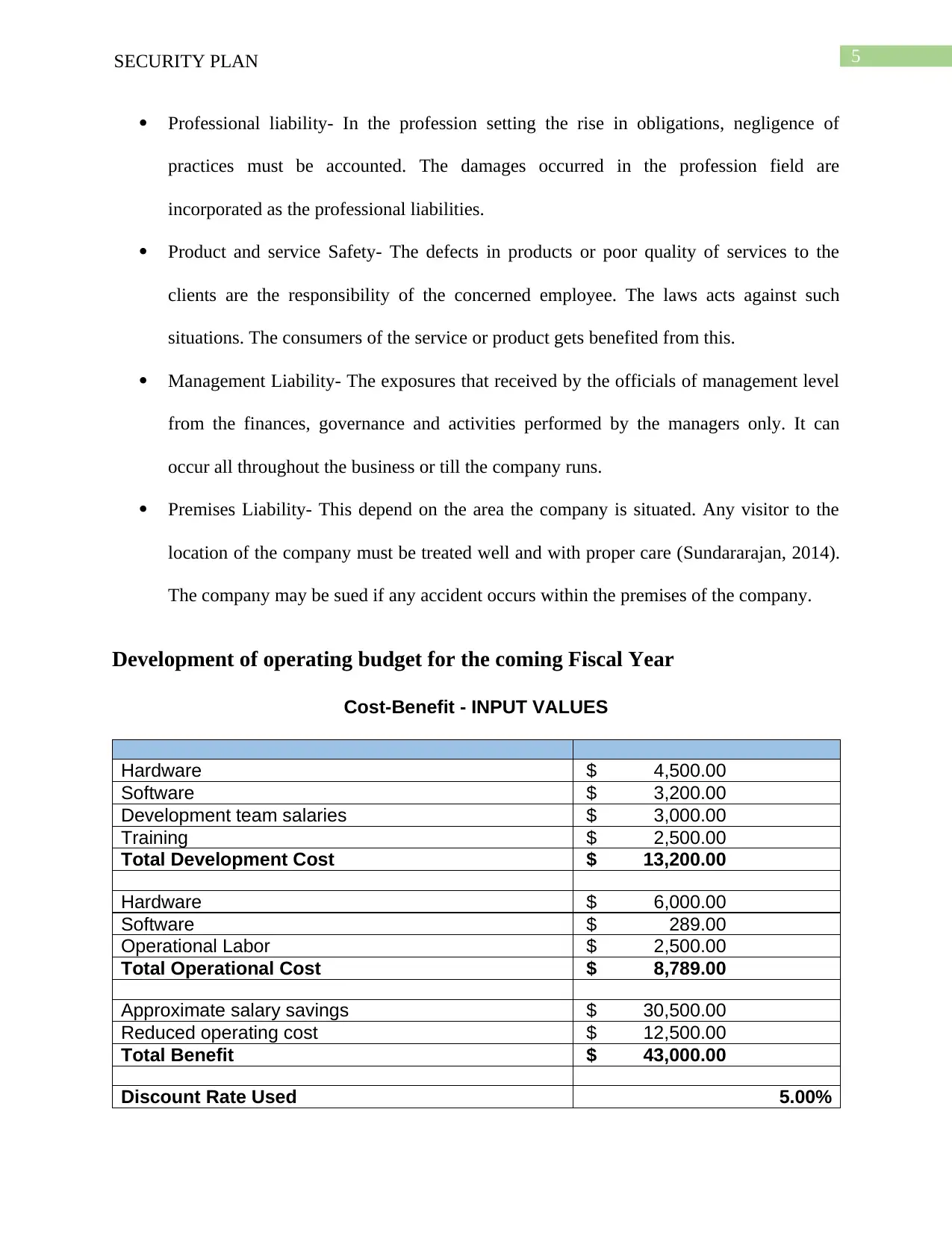
Development of operating budget for the coming Fiscal Year
Cost-Benefit - INPUT VALUES
Hardware $ 4,500.00
Software $ 3,200.00
Development team salaries $ 3,000.00
Training $ 2,500.00
Total Development Cost $ 13,200.00
Hardware $ 6,000.00
Software $ 289.00
Operational Labor $ 2,500.00
Total Operational Cost $ 8,789.00
Approximate salary savings $ 30,500.00
Reduced operating cost $ 12,500.00
Total Benefit $ 43,000.00
Discount Rate Used 5.00%
Professional liability- In the profession setting the rise in obligations, negligence of
practices must be accounted. The damages occurred in the profession field are
incorporated as the professional liabilities.
Product and service Safety- The defects in products or poor quality of services to the
clients are the responsibility of the concerned employee. The laws acts against such
situations. The consumers of the service or product gets benefited from this.
Management Liability- The exposures that received by the officials of management level
from the finances, governance and activities performed by the managers only. It can
occur all throughout the business or till the company runs.
Premises Liability- This depend on the area the company is situated. Any visitor to the
location of the company must be treated well and with proper care (Sundararajan, 2014).
The company may be sued if any accident occurs within the premises of the company.
Development of operating budget for the coming Fiscal Year
Cost-Benefit - INPUT VALUES
Hardware $ 4,500.00
Software $ 3,200.00
Development team salaries $ 3,000.00
Training $ 2,500.00
Total Development Cost $ 13,200.00
Hardware $ 6,000.00
Software $ 289.00
Operational Labor $ 2,500.00
Total Operational Cost $ 8,789.00
Approximate salary savings $ 30,500.00
Reduced operating cost $ 12,500.00
Total Benefit $ 43,000.00
Discount Rate Used 5.00%
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SECURITY PLAN
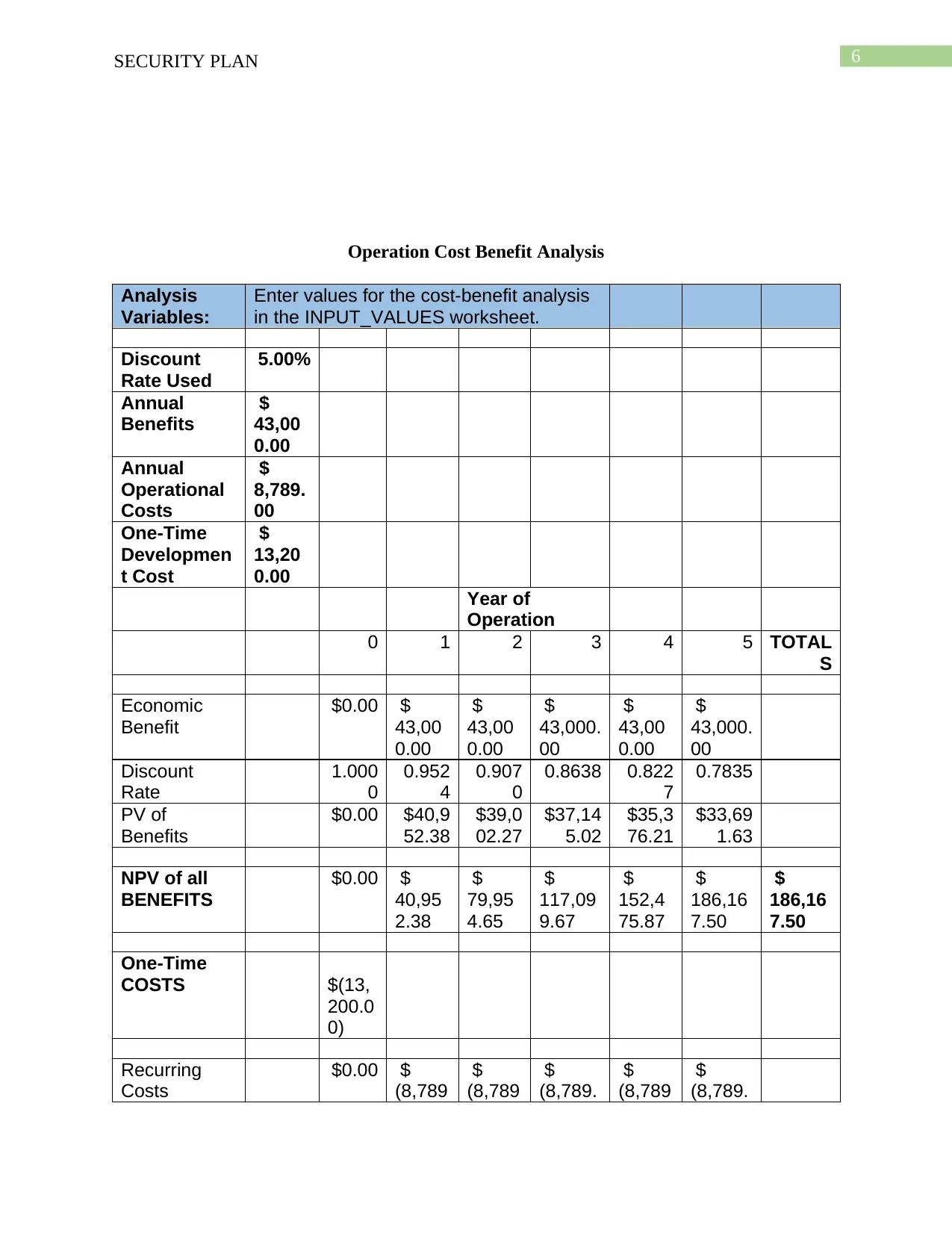
Operation Cost Benefit Analysis
Analysis
Variables:
Enter values for the cost-benefit analysis
in the INPUT_VALUES worksheet.
Discount
Rate Used
5.00%
Annual
Benefits
$
43,00
0.00
Annual
Operational
Costs
$
8,789.
00
One-Time
Developmen
t Cost
$
13,20
0.00
Year of
Operation
0 1 2 3 4 5 TOTAL
S
Economic
Benefit
$0.00 $
43,00
0.00
$
43,00
0.00
$
43,000.
00
$
43,00
0.00
$
43,000.
00
Discount
Rate
1.000
0
0.952
4
0.907
0
0.8638 0.822
7
0.7835
PV of
Benefits
$0.00 $40,9
52.38
$39,0
02.27
$37,14
5.02
$35,3
76.21
$33,69
1.63
NPV of all
BENEFITS
$0.00 $
40,95
2.38
$
79,95
4.65
$
117,09
9.67
$
152,4
75.87
$
186,16
7.50
$
186,16
7.50
One-Time
COSTS $(13,
200.0
0)
Recurring
Costs
$0.00 $
(8,789
$
(8,789
$
(8,789.
$
(8,789
$
(8,789.
Operation Cost Benefit Analysis
Analysis
Variables:
Enter values for the cost-benefit analysis
in the INPUT_VALUES worksheet.
Discount
Rate Used
5.00%
Annual
Benefits
$
43,00
0.00
Annual
Operational
Costs
$
8,789.
00
One-Time
Developmen
t Cost
$
13,20
0.00
Year of
Operation
0 1 2 3 4 5 TOTAL
S
Economic
Benefit
$0.00 $
43,00
0.00
$
43,00
0.00
$
43,000.
00
$
43,00
0.00
$
43,000.
00
Discount
Rate
1.000
0
0.952
4
0.907
0
0.8638 0.822
7
0.7835
PV of
Benefits
$0.00 $40,9
52.38
$39,0
02.27
$37,14
5.02
$35,3
76.21
$33,69
1.63
NPV of all
BENEFITS
$0.00 $
40,95
2.38
$
79,95
4.65
$
117,09
9.67
$
152,4
75.87
$
186,16
7.50
$
186,16
7.50
One-Time
COSTS $(13,
200.0
0)
Recurring
Costs
$0.00 $
(8,789
$
(8,789
$
(8,789.
$
(8,789
$
(8,789.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
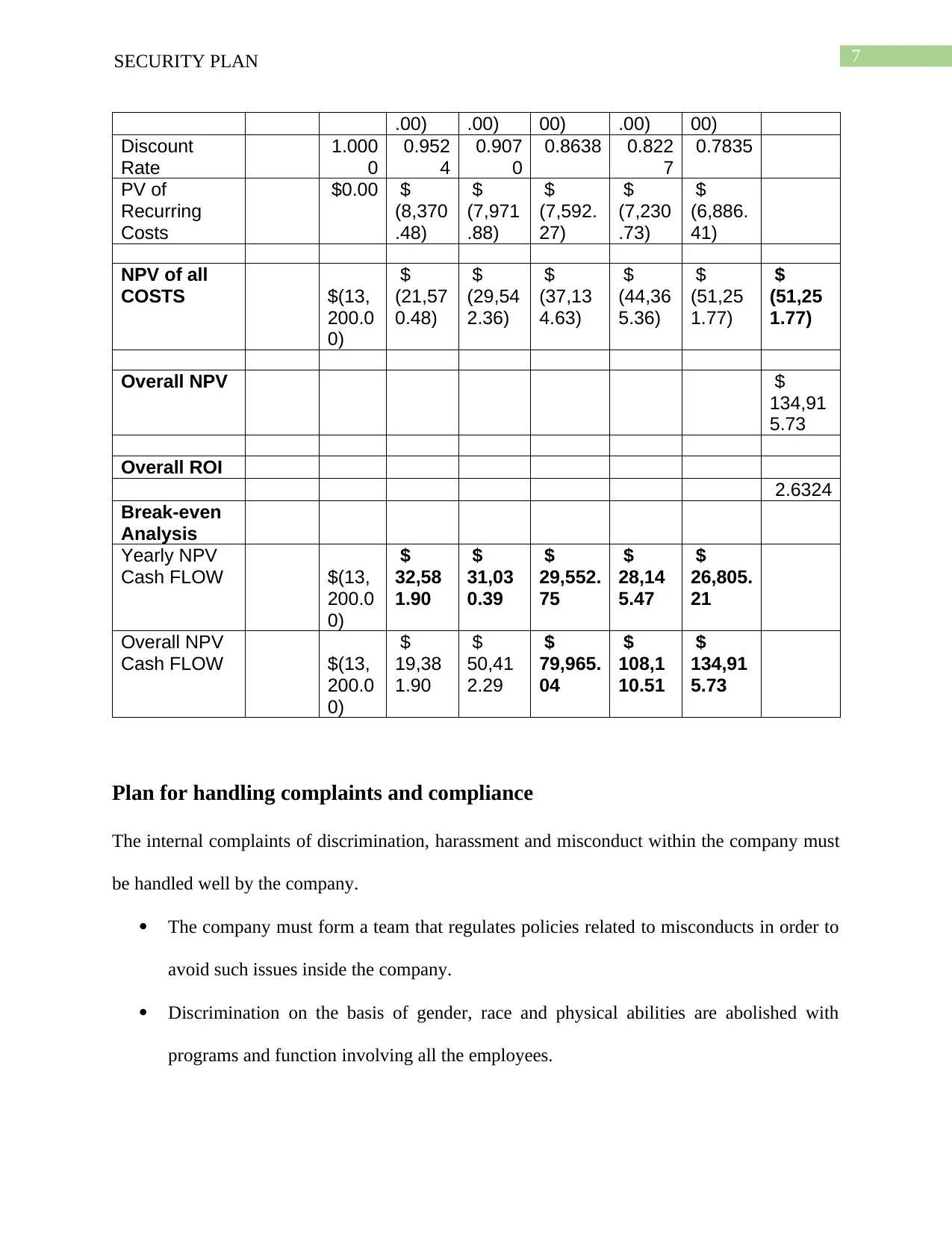
7SECURITY PLAN
.00) .00) 00) .00) 00)
Discount
Rate
1.000
0
0.952
4
0.907
0
0.8638 0.822
7
0.7835
PV of
Recurring
Costs
$0.00 $
(8,370
.48)
$
(7,971
.88)
$
(7,592.
27)
$
(7,230
.73)
$
(6,886.
41)
NPV of all
COSTS $(13,
200.0
0)
$
(21,57
0.48)
$
(29,54
2.36)
$
(37,13
4.63)
$
(44,36
5.36)
$
(51,25
1.77)
$
(51,25
1.77)
Overall NPV $
134,91
5.73
Overall ROI
2.6324
Break-even
Analysis
Yearly NPV
Cash FLOW $(13,
200.0
0)
$
32,58
1.90
$
31,03
0.39
$
29,552.
75
$
28,14
5.47
$
26,805.
21
Overall NPV
Cash FLOW $(13,
200.0
0)
$
19,38
1.90
$
50,41
2.29
$
79,965.
04
$
108,1
10.51
$
134,91
5.73
Plan for handling complaints and compliance
The internal complaints of discrimination, harassment and misconduct within the company must
be handled well by the company.
The company must form a team that regulates policies related to misconducts in order to
avoid such issues inside the company.
Discrimination on the basis of gender, race and physical abilities are abolished with
programs and function involving all the employees.
.00) .00) 00) .00) 00)
Discount
Rate
1.000
0
0.952
4
0.907
0
0.8638 0.822
7
0.7835
PV of
Recurring
Costs
$0.00 $
(8,370
.48)
$
(7,971
.88)
$
(7,592.
27)
$
(7,230
.73)
$
(6,886.
41)
NPV of all
COSTS $(13,
200.0
0)
$
(21,57
0.48)
$
(29,54
2.36)
$
(37,13
4.63)
$
(44,36
5.36)
$
(51,25
1.77)
$
(51,25
1.77)
Overall NPV $
134,91
5.73
Overall ROI
2.6324
Break-even
Analysis
Yearly NPV
Cash FLOW $(13,
200.0
0)
$
32,58
1.90
$
31,03
0.39
$
29,552.
75
$
28,14
5.47
$
26,805.
21
Overall NPV
Cash FLOW $(13,
200.0
0)
$
19,38
1.90
$
50,41
2.29
$
79,965.
04
$
108,1
10.51
$
134,91
5.73
Plan for handling complaints and compliance
The internal complaints of discrimination, harassment and misconduct within the company must
be handled well by the company.
The company must form a team that regulates policies related to misconducts in order to
avoid such issues inside the company.
Discrimination on the basis of gender, race and physical abilities are abolished with
programs and function involving all the employees.

8SECURITY PLAN
Regulation of strict Legal laws against discriminatory activities inside the company
premises.
The creation of hostile environment or harassment for other employees must be treated
with detention from the post and direct complaint to the police authorities.
Any misconduct of activities or behaviors between the employees must be tackled by the
assigned team that regulates the policies of behaviors.
The presence of zero tolerance policy must be applied in the company.
The compliance process that the company may follow is to educate the employees with the
company policies and regulation against the conduction of discrimination, harassment and
general misconduct within the premises of the company (Governatori et al., 2016). The
employees must be engaged in activities, programs where effective communication occurs
between all. The reminder of policy updates should be circulated in the company on yearly basis.
Conclusion
It can be concluded that the company that provides the services of protection, it also need
all type of regulatory operations inside the company that keeps the company on tract about its
security policies and make the employees compliance with them. The company gather
information and intelligence to provide the necessary services to its customer. However, certain
boundaries must be followed by them in order to do so. The hiring procedure of the train
personnel for increasing the productivity and profit of the company is by the above proposed
process will be easier to conduct. The liability issues and internal complaints discussed are
required to mitigate with the effective participation of all the employees. The budget that is
provide is appropriate for operating in the coming fiscal year. The plan for handling the
complaints obtained within the company with respect to harassment, discrimination and
Regulation of strict Legal laws against discriminatory activities inside the company
premises.
The creation of hostile environment or harassment for other employees must be treated
with detention from the post and direct complaint to the police authorities.
Any misconduct of activities or behaviors between the employees must be tackled by the
assigned team that regulates the policies of behaviors.
The presence of zero tolerance policy must be applied in the company.
The compliance process that the company may follow is to educate the employees with the
company policies and regulation against the conduction of discrimination, harassment and
general misconduct within the premises of the company (Governatori et al., 2016). The
employees must be engaged in activities, programs where effective communication occurs
between all. The reminder of policy updates should be circulated in the company on yearly basis.
Conclusion
It can be concluded that the company that provides the services of protection, it also need
all type of regulatory operations inside the company that keeps the company on tract about its
security policies and make the employees compliance with them. The company gather
information and intelligence to provide the necessary services to its customer. However, certain
boundaries must be followed by them in order to do so. The hiring procedure of the train
personnel for increasing the productivity and profit of the company is by the above proposed
process will be easier to conduct. The liability issues and internal complaints discussed are
required to mitigate with the effective participation of all the employees. The budget that is
provide is appropriate for operating in the coming fiscal year. The plan for handling the
complaints obtained within the company with respect to harassment, discrimination and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9SECURITY PLAN
misconduct can be solved by the proposed system. The proper following of company guidelines,
rules and regulations will help in bringing employee compliance with those strategies.
misconduct can be solved by the proposed system. The proper following of company guidelines,
rules and regulations will help in bringing employee compliance with those strategies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY PLAN
Reference
Ahmad, A., Maynard, S. B., & Park, S. (2014). Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2),
357-370.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A framework for information
security governance and management. It Professional, 18(2), 22-30.
Collingwood, L. (2017). Privacy implications and liability issues of autonomous vehicles.
Information & Communications Technology Law, 26(1), 32-45.
Governatori, G., Hashmi, M., Lam, H. P., Villata, S., & Palmirani, M. (2016, November).
Semantic business process regulatory compliance checking using LegalRuleML. In
European Knowledge Acquisition Workshop (pp. 746-761). Springer, Cham.
Nielsen, R. S. (2015). CS651 Computer Systems Security Foundations 3d Imagination Cyber
Security Management Plan (No. LA-UR-15-21507). Los Alamos National Lab.(LANL),
Los Alamos, NM (United States).
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more
holistic approach: A literature review. International Journal of Information Management,
36(2), 215-225.
Sundararajan, A. (2014). Peer-to-peer businesses and the sharing (collaborative) economy:
Overview, economic effects and regulatory issues. Written testimony for the hearing
titled The Power of Connection: Peer to Peer Businesses.
Zudrags, M., Rasikon, S., Ooi, J., & Máthé, L. (2015). Compliance audit and Investigation
report. Bon: Accreditation Services International (ASI).
Reference
Ahmad, A., Maynard, S. B., & Park, S. (2014). Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2),
357-370.
Carcary, M., Renaud, K., McLaughlin, S., & O'Brien, C. (2016). A framework for information
security governance and management. It Professional, 18(2), 22-30.
Collingwood, L. (2017). Privacy implications and liability issues of autonomous vehicles.
Information & Communications Technology Law, 26(1), 32-45.
Governatori, G., Hashmi, M., Lam, H. P., Villata, S., & Palmirani, M. (2016, November).
Semantic business process regulatory compliance checking using LegalRuleML. In
European Knowledge Acquisition Workshop (pp. 746-761). Springer, Cham.
Nielsen, R. S. (2015). CS651 Computer Systems Security Foundations 3d Imagination Cyber
Security Management Plan (No. LA-UR-15-21507). Los Alamos National Lab.(LANL),
Los Alamos, NM (United States).
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more
holistic approach: A literature review. International Journal of Information Management,
36(2), 215-225.
Sundararajan, A. (2014). Peer-to-peer businesses and the sharing (collaborative) economy:
Overview, economic effects and regulatory issues. Written testimony for the hearing
titled The Power of Connection: Peer to Peer Businesses.
Zudrags, M., Rasikon, S., Ooi, J., & Máthé, L. (2015). Compliance audit and Investigation
report. Bon: Accreditation Services International (ASI).
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





