Security Management Plan Report - Complaint Handling and Compliance
VerifiedAdded on 2022/08/15
|13
|703
|16
Report
AI Summary
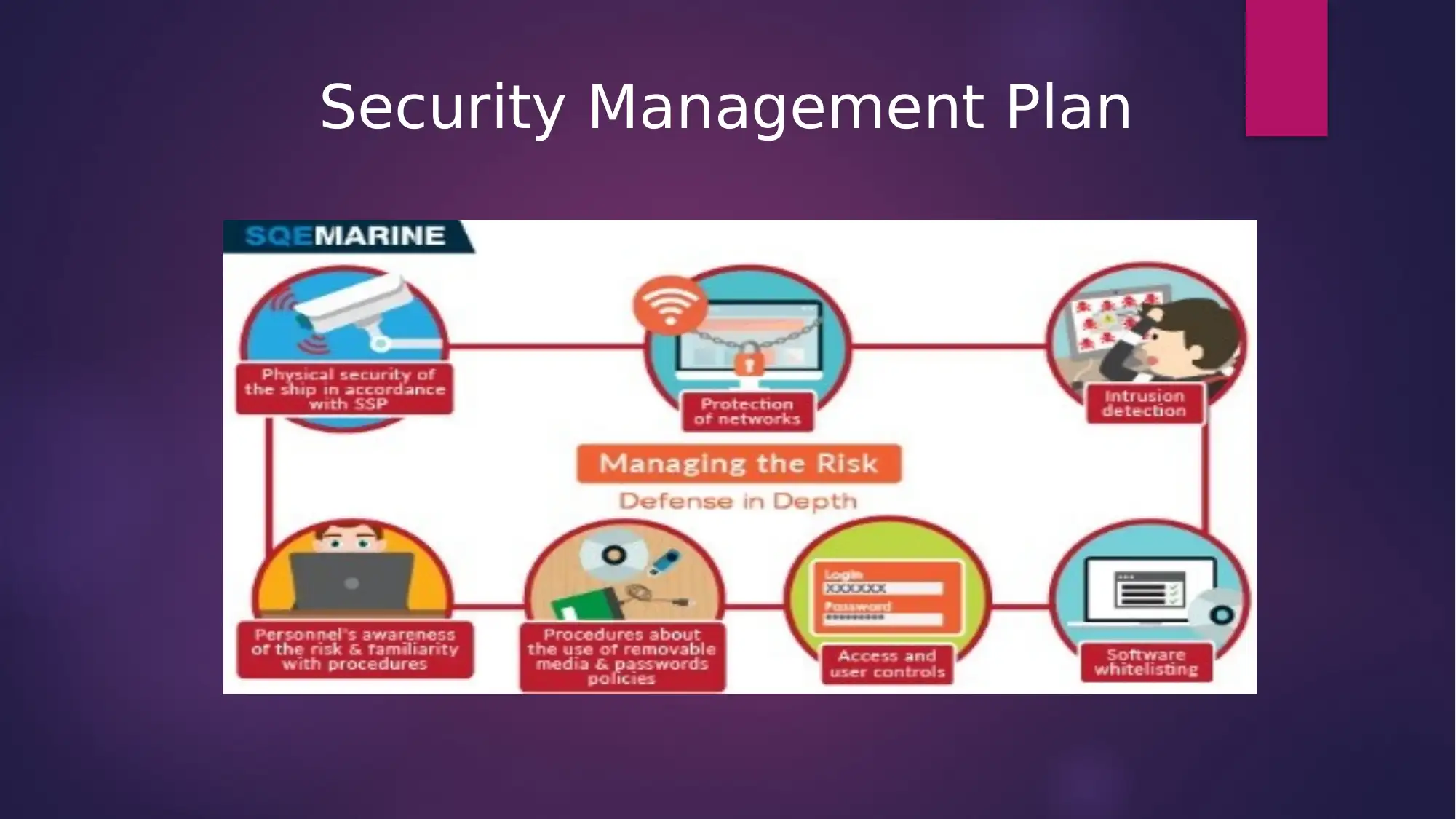
This report presents a security management plan for a company specializing in physical and personal protection services. It outlines the need for increased staffing and the use of a hiring matrix to recruit trained professionals. The plan details company policies related to network and data security, including handling unauthorized access, remote configuration, and data security configurations. It also addresses incident response, data security accountability, and patch management. Furthermore, the report identifies liability issues, workplace safety, and professional, product/service, and management liabilities. An operational budget is developed, including cost considerations, NPV calculations, and ROI analysis. Finally, the plan details the handling of internal complaints, emphasizing a zero-tolerance policy, and ensuring employee compliance with company guidelines and legal regulations. The plan highlights the importance of employee participation in mitigating risks and maintaining a secure environment.
1 out of 13

















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)