Detailed Security Management and Migration Report for Webb's Store
VerifiedAdded on 2020/07/23
|12
|3223
|129
Report
AI Summary
This report analyzes the security management and migration strategies for Webb's Store, focusing on the transition to a cloud-based infrastructure. It begins by examining the security measures provided by AWS and Azure for IAAS instances, highlighting technical safeguards, network security, secure access points, and transmission protection. The report then delves into the risks associated with database migration, including data loss, semantic errors, data corruption, and application stability. Furthermore, it explores the risks associated with IAAS infrastructure migration, such as tracking difficulties, network congestion, and financial implications. The communication between Webb's and its IAAS database in the cloud is also assessed, emphasizing the security challenges like data breaches and the importance of encryption. The report then details the application of cloud services for backup and data repositories, including automated backups, integration, multiple copies, public cloud usage, and disaster recovery (DR) plans. It also discusses the challenges in data storage, such as loss of governance and vendor lock-in, and the issues in data retrieval, including user errors, virus infections, and hardware failures. Finally, the report examines cloud management, addressing IAAS infrastructure, the use of MS SQL Server 2012 R2 cloud instances, and cloud network infrastructure.

Security Management and
Migration
Migration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION ..........................................................................................................................1
1. IAAS instance host by AWS/Azure ............................................................................................1
1.1 Security measures provided by AWS/ Azure for protecting IAAS instance. ..................1
2. Database migration risk...............................................................................................................2
2.1 Database migration risk....................................................................................................2
2.2 IAAS infrastructure migration risk...................................................................................3
2.3 The communication between Webb's and their IAAS database in the cloud...................3
3. Applying Cloud for backup and data repository..........................................................................4
3.1 Backing up data to the cloud............................................................................................4
3.2 Storage of the data in the cloud........................................................................................5
3.3 Retrieval of the data from the cloud................................................................................5
3.4 DR plan of the CSP..........................................................................................................5
4. Cloud management......................................................................................................................6
4.1 Their IAAS infrastructure.................................................................................................6
4.2 Their Ms SQL Server 2012 R2 cloud instance. ...............................................................6
4.3 Their cloud network infrastructure...................................................................................7
4.4 Their cloud backup and restore infrastructure..................................................................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9
INTRODUCTION ..........................................................................................................................1
1. IAAS instance host by AWS/Azure ............................................................................................1
1.1 Security measures provided by AWS/ Azure for protecting IAAS instance. ..................1
2. Database migration risk...............................................................................................................2
2.1 Database migration risk....................................................................................................2
2.2 IAAS infrastructure migration risk...................................................................................3
2.3 The communication between Webb's and their IAAS database in the cloud...................3
3. Applying Cloud for backup and data repository..........................................................................4
3.1 Backing up data to the cloud............................................................................................4
3.2 Storage of the data in the cloud........................................................................................5
3.3 Retrieval of the data from the cloud................................................................................5
3.4 DR plan of the CSP..........................................................................................................5
4. Cloud management......................................................................................................................6
4.1 Their IAAS infrastructure.................................................................................................6
4.2 Their Ms SQL Server 2012 R2 cloud instance. ...............................................................6
4.3 Their cloud network infrastructure...................................................................................7
4.4 Their cloud backup and restore infrastructure..................................................................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9

Illustration Index
Illustration 1: Database migration....................................................................................................2
Illustration 2: Backup and recovery ................................................................................................4
Illustration 1: Database migration....................................................................................................2
Illustration 2: Backup and recovery ................................................................................................4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Security management is a process through which company establishes policies, in order
to manage their sensitive information. In this process cloud computing is producing services
including various layers of safety. Some of them are like networking, transferring, backup,
recovery, etc. Along with this they are offering different platforms as per the requirement of
customers such as SAAS, PAAS and IAAS. Webb's stores is one of the leading retailer of
Australia, they offers wide range of services to their customers like clothing, beauty products,
gifts, hardware, etc. (Almorsy, Grundy and Müller, 2016 ). The organisation is having more than
600 sales staff and 200 for maintaining ware house. The firm is migrating their data on cloud
platform, in order to increase effectiveness of management and operational work. The present
report is based on determining the risk of migration, along with this backups and repositories
process is also discussed.
1. IAAS INSTANCE HOST BY AWS/AZURE
1.1 Security measures provided by AWS/ Azure for protecting IAAS instance.
There are various cloud service providers are available such as Amazon web service and
Azure, in order to safe guard IAAs instance they does not rely on single protection layer. Webb's
will be provided with various security features at IAAS by them. Some of them are following:
1. Technical safeguard: They are giving world class infrastructural network to their
customers. With the help of that users are able to manage, monitor and secure their
instance by selecting various security modes (Barron, Yu and Zhan, 2013).
2. Network security: The communication and monitoring services provided by these
companies are able to manage network traffic and optimise it. Along with this monitoring
process is distributed on the basis of internal and external environment. Through which
user are able to ensure security effectively.
3. Secure access point: In order to maintain competency of the applied security features,
limited access points are provided. It helps in observing the processing of API endpoints
so that only permits and secured HTTP's can enter (Gangwar, Date and Ramaswamy,
2015).
4. Transmission Protection: In order to provide safe data transmission services they are
considering safe access points such as HTTP. Along with this applying Secure Socket
Layers for establishing secure connection.
1
Security management is a process through which company establishes policies, in order
to manage their sensitive information. In this process cloud computing is producing services
including various layers of safety. Some of them are like networking, transferring, backup,
recovery, etc. Along with this they are offering different platforms as per the requirement of
customers such as SAAS, PAAS and IAAS. Webb's stores is one of the leading retailer of
Australia, they offers wide range of services to their customers like clothing, beauty products,
gifts, hardware, etc. (Almorsy, Grundy and Müller, 2016 ). The organisation is having more than
600 sales staff and 200 for maintaining ware house. The firm is migrating their data on cloud
platform, in order to increase effectiveness of management and operational work. The present
report is based on determining the risk of migration, along with this backups and repositories
process is also discussed.
1. IAAS INSTANCE HOST BY AWS/AZURE
1.1 Security measures provided by AWS/ Azure for protecting IAAS instance.
There are various cloud service providers are available such as Amazon web service and
Azure, in order to safe guard IAAs instance they does not rely on single protection layer. Webb's
will be provided with various security features at IAAS by them. Some of them are following:
1. Technical safeguard: They are giving world class infrastructural network to their
customers. With the help of that users are able to manage, monitor and secure their
instance by selecting various security modes (Barron, Yu and Zhan, 2013).
2. Network security: The communication and monitoring services provided by these
companies are able to manage network traffic and optimise it. Along with this monitoring
process is distributed on the basis of internal and external environment. Through which
user are able to ensure security effectively.
3. Secure access point: In order to maintain competency of the applied security features,
limited access points are provided. It helps in observing the processing of API endpoints
so that only permits and secured HTTP's can enter (Gangwar, Date and Ramaswamy,
2015).
4. Transmission Protection: In order to provide safe data transmission services they are
considering safe access points such as HTTP. Along with this applying Secure Socket
Layers for establishing secure connection.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
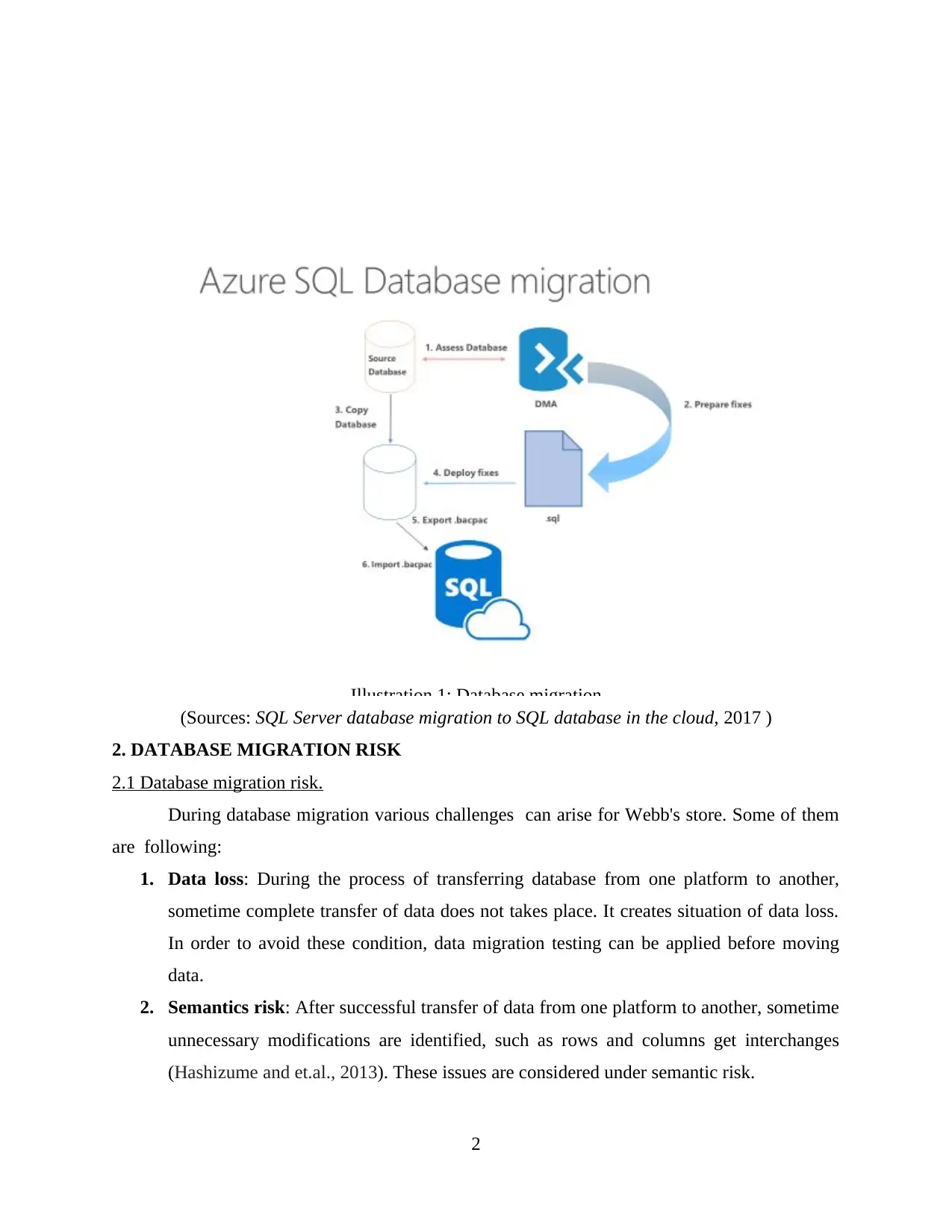
(Sources: SQL Server database migration to SQL database in the cloud, 2017 )
2. DATABASE MIGRATION RISK
2.1 Database migration risk.
During database migration various challenges can arise for Webb's store. Some of them
are following:
1. Data loss: During the process of transferring database from one platform to another,
sometime complete transfer of data does not takes place. It creates situation of data loss.
In order to avoid these condition, data migration testing can be applied before moving
data.
2. Semantics risk: After successful transfer of data from one platform to another, sometime
unnecessary modifications are identified, such as rows and columns get interchanges
(Hashizume and et.al., 2013). These issues are considered under semantic risk.
2
Illustration 1: Database migration
2. DATABASE MIGRATION RISK
2.1 Database migration risk.
During database migration various challenges can arise for Webb's store. Some of them
are following:
1. Data loss: During the process of transferring database from one platform to another,
sometime complete transfer of data does not takes place. It creates situation of data loss.
In order to avoid these condition, data migration testing can be applied before moving
data.
2. Semantics risk: After successful transfer of data from one platform to another, sometime
unnecessary modifications are identified, such as rows and columns get interchanges
(Hashizume and et.al., 2013). These issues are considered under semantic risk.
2
Illustration 1: Database migration

3. Data corruption: Company applies data validation as per their requirement, while
migration process redundant data also migrated, due to which burden is created on the
system and leads situations like data corruption and system crash.
4. Application stability: During migration of database, various challenges can raised due to
ineffective structure of the target platform, improper coding and storage capacity due to
these issues stability of the databases affects.
2.2 IAAS infrastructure migration risk.
During migration of IAAS infrastructure from one to another platform, various risks are
identified. Some of them are following:
1. While migration of infrastructure tracking and monitoring of process and software
become difficult and time consuming due to which failure of process takes place.
2. Through applying IAAS scheduling can be done effectively. It helps in reducing the
traffic congestion, due to migration of the infrastructure networking traffic get increased
due to ineffective scaling and scheduling of resources. It increases the network
congestion and affects the communication process (Kaur,Gobindgarh and Garg, 2015 ).
3. Cloud services and infrastructures are provided at rent, it helps the organisation in
expanding their business at small amount. Due to migration companies are required to
spend large amount on workforce, infrastructure and controlling measures.
4. Data storage is considered as one of the biggest issue, as cloud services are able to handle
big data.
5. Recovery process become complicated, with the help of cloud services backups are
created at regular interval.
2.3 The communication between Webb's and their IAAS database in the cloud.
During the communication process between Webb's and IAAS database in the cloud,
various security challenges arises. Some of them are like data loss, data breach, hacking, etc.
Cloud services are provided by creating virtual environment. In this process security is ensured
with the help of different data encryption and decryption techniques. It the advance approaches
are not applied for data encryption , sensitive information of company can be easily breached by
the hackers (Mishra and et.al., 2013 ). It will create direct impact on the organisation. During the
process of migration if cryptography methods are not effective the chances of data loss
automatically get increased.
3
migration process redundant data also migrated, due to which burden is created on the
system and leads situations like data corruption and system crash.
4. Application stability: During migration of database, various challenges can raised due to
ineffective structure of the target platform, improper coding and storage capacity due to
these issues stability of the databases affects.
2.2 IAAS infrastructure migration risk.
During migration of IAAS infrastructure from one to another platform, various risks are
identified. Some of them are following:
1. While migration of infrastructure tracking and monitoring of process and software
become difficult and time consuming due to which failure of process takes place.
2. Through applying IAAS scheduling can be done effectively. It helps in reducing the
traffic congestion, due to migration of the infrastructure networking traffic get increased
due to ineffective scaling and scheduling of resources. It increases the network
congestion and affects the communication process (Kaur,Gobindgarh and Garg, 2015 ).
3. Cloud services and infrastructures are provided at rent, it helps the organisation in
expanding their business at small amount. Due to migration companies are required to
spend large amount on workforce, infrastructure and controlling measures.
4. Data storage is considered as one of the biggest issue, as cloud services are able to handle
big data.
5. Recovery process become complicated, with the help of cloud services backups are
created at regular interval.
2.3 The communication between Webb's and their IAAS database in the cloud.
During the communication process between Webb's and IAAS database in the cloud,
various security challenges arises. Some of them are like data loss, data breach, hacking, etc.
Cloud services are provided by creating virtual environment. In this process security is ensured
with the help of different data encryption and decryption techniques. It the advance approaches
are not applied for data encryption , sensitive information of company can be easily breached by
the hackers (Mishra and et.al., 2013 ). It will create direct impact on the organisation. During the
process of migration if cryptography methods are not effective the chances of data loss
automatically get increased.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
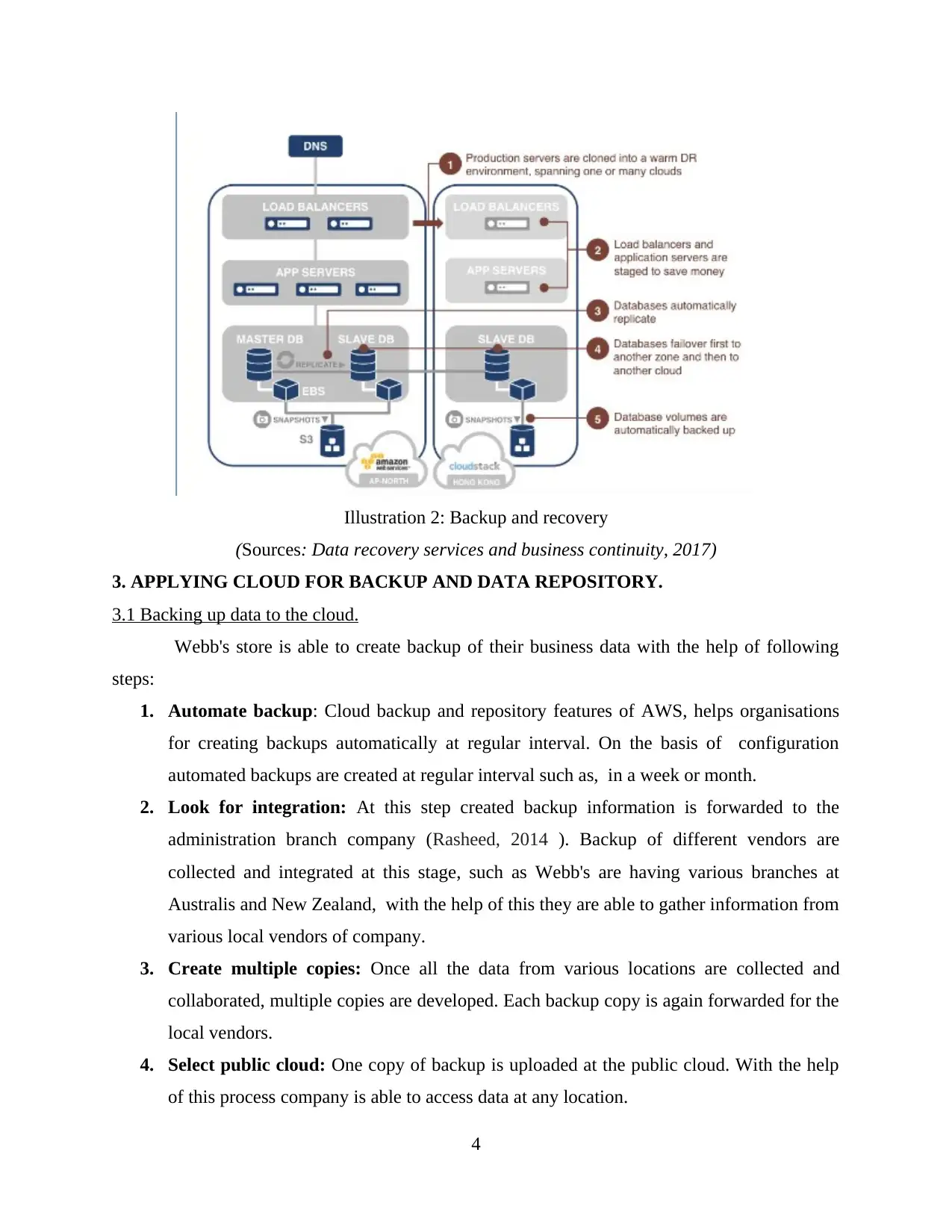
(Sources: Data recovery services and business continuity, 2017)
3. APPLYING CLOUD FOR BACKUP AND DATA REPOSITORY.
3.1 Backing up data to the cloud.
Webb's store is able to create backup of their business data with the help of following
steps:
1. Automate backup: Cloud backup and repository features of AWS, helps organisations
for creating backups automatically at regular interval. On the basis of configuration
automated backups are created at regular interval such as, in a week or month.
2. Look for integration: At this step created backup information is forwarded to the
administration branch company (Rasheed, 2014 ). Backup of different vendors are
collected and integrated at this stage, such as Webb's are having various branches at
Australis and New Zealand, with the help of this they are able to gather information from
various local vendors of company.
3. Create multiple copies: Once all the data from various locations are collected and
collaborated, multiple copies are developed. Each backup copy is again forwarded for the
local vendors.
4. Select public cloud: One copy of backup is uploaded at the public cloud. With the help
of this process company is able to access data at any location.
4
Illustration 2: Backup and recovery
3. APPLYING CLOUD FOR BACKUP AND DATA REPOSITORY.
3.1 Backing up data to the cloud.
Webb's store is able to create backup of their business data with the help of following
steps:
1. Automate backup: Cloud backup and repository features of AWS, helps organisations
for creating backups automatically at regular interval. On the basis of configuration
automated backups are created at regular interval such as, in a week or month.
2. Look for integration: At this step created backup information is forwarded to the
administration branch company (Rasheed, 2014 ). Backup of different vendors are
collected and integrated at this stage, such as Webb's are having various branches at
Australis and New Zealand, with the help of this they are able to gather information from
various local vendors of company.
3. Create multiple copies: Once all the data from various locations are collected and
collaborated, multiple copies are developed. Each backup copy is again forwarded for the
local vendors.
4. Select public cloud: One copy of backup is uploaded at the public cloud. With the help
of this process company is able to access data at any location.
4
Illustration 2: Backup and recovery
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5. Consider analytics to pinpoint backup: Backup process also helps in rectifying and
retrieving data from disaster. Through this process they are able to extract information as
per their requirement by applying respective backup pinpoint.
6. Give it a whirl: In order to make sure that backup data is actually saved, this step is
performed (Rittinghouse and Ransome, 2016). Under this process IT professional of the
company tests the backup and maintains data safety.
3.2 Storage of the data in the cloud.
Cloud computing provides large amount of storage space through which users are able to
manage information easily. However, there are some risks are also associated that can be faced
by Webb's. One of the biggest issues is identified as loss of governance, in this process the
information accessing power is provided to the third party, due to which sensitive information of
company is supplied to the agents, it creates direct impact on the security of the organisation
(Ryan, 2013). Another major issues that is identified as lock in, in this situation users are unable
to access their data and due to frequent logging system get locked. In such condition migration of
information is also not possible, due to which customers becomes helpless.
3.3 Retrieval of the data from the cloud.
During the process of data retrieval various issues are identified that affects the security
of the data. Some of them are like user error, virus infection, backup failure and RAID. User
error is done by the human mistake, in this process wrong recovery instruction are provided to
the system due to which data recovery process get failed. Another problem is virus infection,
under this data corruption occurs, due to presents of trojans, virus, etc (Sadiku, Musa and
Momoh, 2014 ). Redundant array of independent disk (RAID) in this process disk creates
redundant data, due to physical failure of the device recovery failure raise. Therefore, there are
various factors are available that can affects the process of data recovery. In order to overcome
these issues advance recovery applications should be applied by Webb's.
3.4 DR plan of the CSP.
DR instances Backup and restore Replication in cloud
Instance 1. Microsoft
Dynamic CRM
2. Email account.
1. On premises
2. Cloud to cloud
1. On premises
2. Cloud to cloud
5
retrieving data from disaster. Through this process they are able to extract information as
per their requirement by applying respective backup pinpoint.
6. Give it a whirl: In order to make sure that backup data is actually saved, this step is
performed (Rittinghouse and Ransome, 2016). Under this process IT professional of the
company tests the backup and maintains data safety.
3.2 Storage of the data in the cloud.
Cloud computing provides large amount of storage space through which users are able to
manage information easily. However, there are some risks are also associated that can be faced
by Webb's. One of the biggest issues is identified as loss of governance, in this process the
information accessing power is provided to the third party, due to which sensitive information of
company is supplied to the agents, it creates direct impact on the security of the organisation
(Ryan, 2013). Another major issues that is identified as lock in, in this situation users are unable
to access their data and due to frequent logging system get locked. In such condition migration of
information is also not possible, due to which customers becomes helpless.
3.3 Retrieval of the data from the cloud.
During the process of data retrieval various issues are identified that affects the security
of the data. Some of them are like user error, virus infection, backup failure and RAID. User
error is done by the human mistake, in this process wrong recovery instruction are provided to
the system due to which data recovery process get failed. Another problem is virus infection,
under this data corruption occurs, due to presents of trojans, virus, etc (Sadiku, Musa and
Momoh, 2014 ). Redundant array of independent disk (RAID) in this process disk creates
redundant data, due to physical failure of the device recovery failure raise. Therefore, there are
various factors are available that can affects the process of data recovery. In order to overcome
these issues advance recovery applications should be applied by Webb's.
3.4 DR plan of the CSP.
DR instances Backup and restore Replication in cloud
Instance 1. Microsoft
Dynamic CRM
2. Email account.
1. On premises
2. Cloud to cloud
1. On premises
2. Cloud to cloud
5
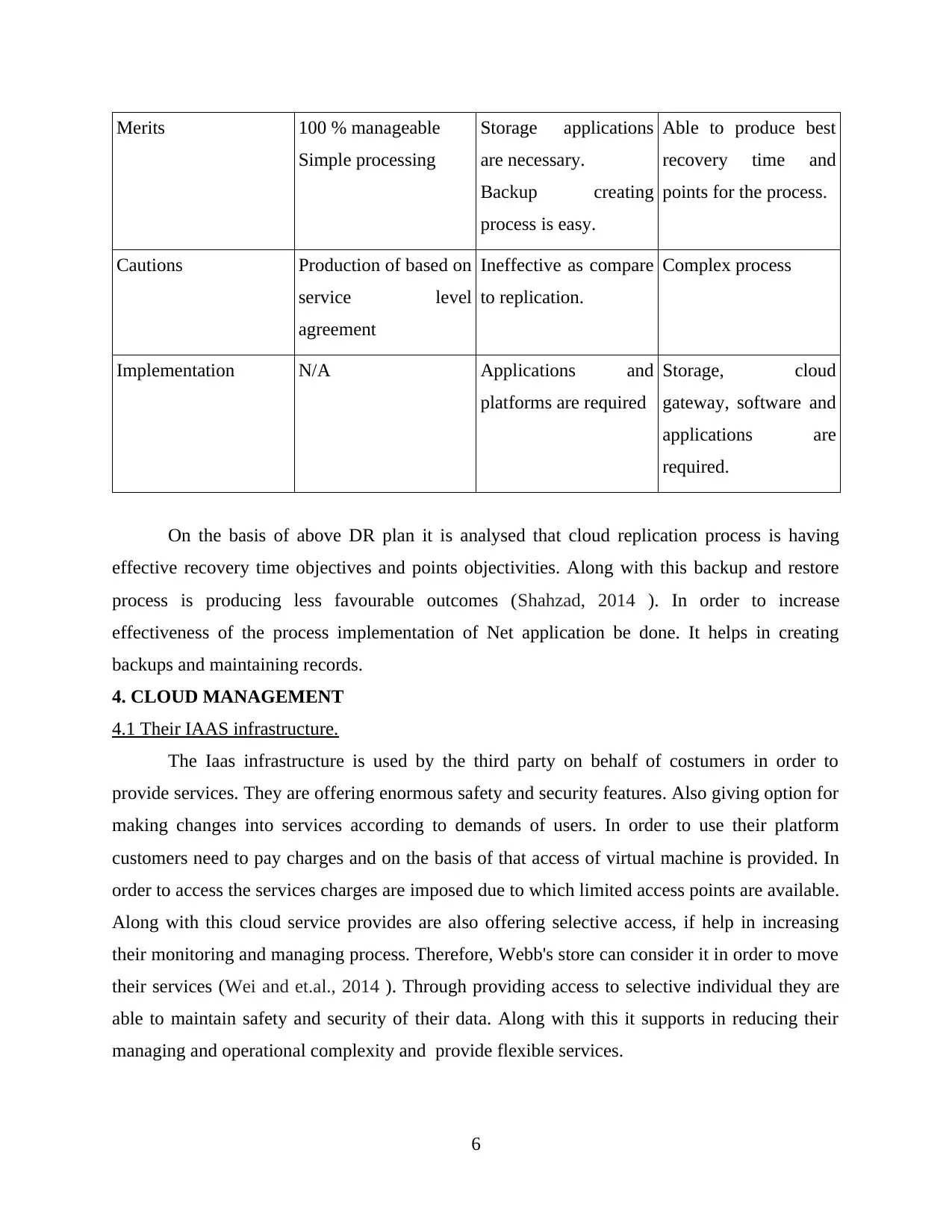
Merits 100 % manageable
Simple processing
Storage applications
are necessary.
Backup creating
process is easy.
Able to produce best
recovery time and
points for the process.
Cautions Production of based on
service level
agreement
Ineffective as compare
to replication.
Complex process
Implementation N/A Applications and
platforms are required
Storage, cloud
gateway, software and
applications are
required.
On the basis of above DR plan it is analysed that cloud replication process is having
effective recovery time objectives and points objectivities. Along with this backup and restore
process is producing less favourable outcomes (Shahzad, 2014 ). In order to increase
effectiveness of the process implementation of Net application be done. It helps in creating
backups and maintaining records.
4. CLOUD MANAGEMENT
4.1 Their IAAS infrastructure.
The Iaas infrastructure is used by the third party on behalf of costumers in order to
provide services. They are offering enormous safety and security features. Also giving option for
making changes into services according to demands of users. In order to use their platform
customers need to pay charges and on the basis of that access of virtual machine is provided. In
order to access the services charges are imposed due to which limited access points are available.
Along with this cloud service provides are also offering selective access, if help in increasing
their monitoring and managing process. Therefore, Webb's store can consider it in order to move
their services (Wei and et.al., 2014 ). Through providing access to selective individual they are
able to maintain safety and security of their data. Along with this it supports in reducing their
managing and operational complexity and provide flexible services.
6
Simple processing
Storage applications
are necessary.
Backup creating
process is easy.
Able to produce best
recovery time and
points for the process.
Cautions Production of based on
service level
agreement
Ineffective as compare
to replication.
Complex process
Implementation N/A Applications and
platforms are required
Storage, cloud
gateway, software and
applications are
required.
On the basis of above DR plan it is analysed that cloud replication process is having
effective recovery time objectives and points objectivities. Along with this backup and restore
process is producing less favourable outcomes (Shahzad, 2014 ). In order to increase
effectiveness of the process implementation of Net application be done. It helps in creating
backups and maintaining records.
4. CLOUD MANAGEMENT
4.1 Their IAAS infrastructure.
The Iaas infrastructure is used by the third party on behalf of costumers in order to
provide services. They are offering enormous safety and security features. Also giving option for
making changes into services according to demands of users. In order to use their platform
customers need to pay charges and on the basis of that access of virtual machine is provided. In
order to access the services charges are imposed due to which limited access points are available.
Along with this cloud service provides are also offering selective access, if help in increasing
their monitoring and managing process. Therefore, Webb's store can consider it in order to move
their services (Wei and et.al., 2014 ). Through providing access to selective individual they are
able to maintain safety and security of their data. Along with this it supports in reducing their
managing and operational complexity and provide flexible services.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4.2 Their Ms SQL Server 2012 R2 cloud instance.
Ms SQL Server 2012 R2 cloud instance is also providing various safety and security
features. The storage capacity of the platform is about 16TB through which organisations are
bale to manage their large amount of data easily. Along with this they are offering various easy
and manageable features such as pre-configurable parameters through selecting them user is able
to directly access SQL server (Zhao, Li and Liu, 2014). Automated software patching, with the
help of that user is able to get automatic updates related to the software. Along with this they are
offering advance encryption techniques thorough which access details remain confidential.
Therefore, with the help of this platform Webb's store is able to secure their access details and
maintain safety of database.
4.3 Their cloud network infrastructure.
Cloud services delivers virtual infrastructure with the help of networking. In this process
cloud users are connected with virtual system. Set of virtual computers are connected with the
network cloud with the help of routers. Through this platform customers are able to
communicate with other and exchanges information. All the safety features that are imposed on
the various infrastructure of the clouds are forwarded to the networks also, due to which it is bale
to control traffic congestion and maintain speed of the process (Data recovery services and
business continuity, 2017 ). Along with this due to huge amount of data base it is able to handle
large number of access at the same time and does not creates situation like system crash.
Therefore, with the help of this platform Webb's store is able to secure their communication
process. Through advance feature of encryption and decryption they are able to protect access on
data.
4.4 Their cloud backup and restore infrastructure.
The cloud backups and restore infrastructures are provided with data protection features.
With the help of this services, user are able to develop effective backups. They are offering
different secure and reliable platforms for creating regular backups, such as different instances,
cloud applications, virtual machines and database (SQL Server database migration to SQL database
in the cloud, 2017 ). With the help of infrastructure user is able to store optimised information. In
this process various application are available such as snapshot, through which copies are created
at fixed interval of time. Snap-restore, it helps in storing copies of recovery and snap- centre
helps in managing data protection of the process. With the help of this application admin is able
7
Ms SQL Server 2012 R2 cloud instance is also providing various safety and security
features. The storage capacity of the platform is about 16TB through which organisations are
bale to manage their large amount of data easily. Along with this they are offering various easy
and manageable features such as pre-configurable parameters through selecting them user is able
to directly access SQL server (Zhao, Li and Liu, 2014). Automated software patching, with the
help of that user is able to get automatic updates related to the software. Along with this they are
offering advance encryption techniques thorough which access details remain confidential.
Therefore, with the help of this platform Webb's store is able to secure their access details and
maintain safety of database.
4.3 Their cloud network infrastructure.
Cloud services delivers virtual infrastructure with the help of networking. In this process
cloud users are connected with virtual system. Set of virtual computers are connected with the
network cloud with the help of routers. Through this platform customers are able to
communicate with other and exchanges information. All the safety features that are imposed on
the various infrastructure of the clouds are forwarded to the networks also, due to which it is bale
to control traffic congestion and maintain speed of the process (Data recovery services and
business continuity, 2017 ). Along with this due to huge amount of data base it is able to handle
large number of access at the same time and does not creates situation like system crash.
Therefore, with the help of this platform Webb's store is able to secure their communication
process. Through advance feature of encryption and decryption they are able to protect access on
data.
4.4 Their cloud backup and restore infrastructure.
The cloud backups and restore infrastructures are provided with data protection features.
With the help of this services, user are able to develop effective backups. They are offering
different secure and reliable platforms for creating regular backups, such as different instances,
cloud applications, virtual machines and database (SQL Server database migration to SQL database
in the cloud, 2017 ). With the help of infrastructure user is able to store optimised information. In
this process various application are available such as snapshot, through which copies are created
at fixed interval of time. Snap-restore, it helps in storing copies of recovery and snap- centre
helps in managing data protection of the process. With the help of this application admin is able
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

to provide role based access, which helps in maintaining access protection. Therefore, Webb's
store is able to implement secure and safe data backups and recovery by providing access to
limited persons.
CONCLUSION
On the basis of above report it is inferred that Webb's i9s able to increase management
and operational process of their organisation with the help of cloud computing. With the help
migrating My SQL database on IAAS they are able to reduce infrastructural cost. Along with this
it helps in increasing there are various problems are also associated with the process such as data
loss, breach, lock in, etc. These issues can be handled with the help of implementing advance
software and tools.
8
store is able to implement secure and safe data backups and recovery by providing access to
limited persons.
CONCLUSION
On the basis of above report it is inferred that Webb's i9s able to increase management
and operational process of their organisation with the help of cloud computing. With the help
migrating My SQL database on IAAS they are able to reduce infrastructural cost. Along with this
it helps in increasing there are various problems are also associated with the process such as data
loss, breach, lock in, etc. These issues can be handled with the help of implementing advance
software and tools.
8

REFERENCES
Books and journals
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Barron, C., Yu, H. and Zhan, J., 2013, July. Cloud computing security case studies and research.
In Proceedings of the world congress on engineering (Vol. 2, No. 1, pp. 1-5).
Gangwar, H., Date, H. and Ramaswamy, R., 2015. Understanding determinants of cloud
computing adoption using an integrated TAM-TOE model. Journal of Enterprise
Information Management.28(1). pp.107-130.
Hashizume, K. and et.al., 2013. An analysis of security issues for cloud computing. Journal of
Internet Services and Applications. 4(1). p.5.
Kaur, J., Gobindgarh, M. and Garg, S., 2015. Survey paper on security in cloud
computing. International Journal in Applied Studies and Production Management.
Mishra, A. and et.al., 2013. Cloud computing security. International Journal on Recent and
Innovation Trends in Computing and Communication.1(1). pp.36-39.
Rasheed, H., 2014. Data and infrastructure security auditing in cloud computing
environments. International Journal of Information Management. 34(3). pp.364-368.
Rittinghouse, J. W. and Ransome, J. F., 2016. Cloud computing: implementation, management,
and security. CRC press.
Ryan, M. D., 2013. Cloud computing security: The scientific challenge, and a survey of
solutions. Journal of Systems and Software.86(9).pp.2263-2268.
Sadiku, M. N., Musa, S. M. and Momoh, O. D., 2014. Cloud computing: opportunities and
challenges. IEEE potentials.33(1). pp.34-36.
Shahzad, F., 2014. State-of-the-art survey on cloud computing security Challenges, approaches
and solutions. Procedia Computer Science. 37. pp.357-362.
Wei, L. and et.al., 2014. Security and privacy for storage and computation in cloud
computing. Information Sciences. 258. pp.371-386.
Zhao, F., Li, C. and Liu, C. F., 2014, February. A cloud computing security solution based on
fully homomorphic encryption. In Advanced Communication Technology (ICACT), 2014
16th International Conference on (pp. 485-488). IEEE.
Online
Data recovery services and business continuity, 2017. [Online]. Available through:
<https://www.datarecovery.net/articles/drs-and-business-continuity.aspx>. [Accessed on
23th September 2017].
SQL Server database migration to SQL database in the cloud, 2017. [Online]. Available
through: <https://docs.microsoft.com/en-us/azure/sql-database/sql-database-cloud-
migrate>. [Accessed on 23th September 2017].
9
Books and journals
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Barron, C., Yu, H. and Zhan, J., 2013, July. Cloud computing security case studies and research.
In Proceedings of the world congress on engineering (Vol. 2, No. 1, pp. 1-5).
Gangwar, H., Date, H. and Ramaswamy, R., 2015. Understanding determinants of cloud
computing adoption using an integrated TAM-TOE model. Journal of Enterprise
Information Management.28(1). pp.107-130.
Hashizume, K. and et.al., 2013. An analysis of security issues for cloud computing. Journal of
Internet Services and Applications. 4(1). p.5.
Kaur, J., Gobindgarh, M. and Garg, S., 2015. Survey paper on security in cloud
computing. International Journal in Applied Studies and Production Management.
Mishra, A. and et.al., 2013. Cloud computing security. International Journal on Recent and
Innovation Trends in Computing and Communication.1(1). pp.36-39.
Rasheed, H., 2014. Data and infrastructure security auditing in cloud computing
environments. International Journal of Information Management. 34(3). pp.364-368.
Rittinghouse, J. W. and Ransome, J. F., 2016. Cloud computing: implementation, management,
and security. CRC press.
Ryan, M. D., 2013. Cloud computing security: The scientific challenge, and a survey of
solutions. Journal of Systems and Software.86(9).pp.2263-2268.
Sadiku, M. N., Musa, S. M. and Momoh, O. D., 2014. Cloud computing: opportunities and
challenges. IEEE potentials.33(1). pp.34-36.
Shahzad, F., 2014. State-of-the-art survey on cloud computing security Challenges, approaches
and solutions. Procedia Computer Science. 37. pp.357-362.
Wei, L. and et.al., 2014. Security and privacy for storage and computation in cloud
computing. Information Sciences. 258. pp.371-386.
Zhao, F., Li, C. and Liu, C. F., 2014, February. A cloud computing security solution based on
fully homomorphic encryption. In Advanced Communication Technology (ICACT), 2014
16th International Conference on (pp. 485-488). IEEE.
Online
Data recovery services and business continuity, 2017. [Online]. Available through:
<https://www.datarecovery.net/articles/drs-and-business-continuity.aspx>. [Accessed on
23th September 2017].
SQL Server database migration to SQL database in the cloud, 2017. [Online]. Available
through: <https://docs.microsoft.com/en-us/azure/sql-database/sql-database-cloud-
migrate>. [Accessed on 23th September 2017].
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





