Security and Network Security Assignment Solution - University
VerifiedAdded on 2020/03/16
|6
|941
|147
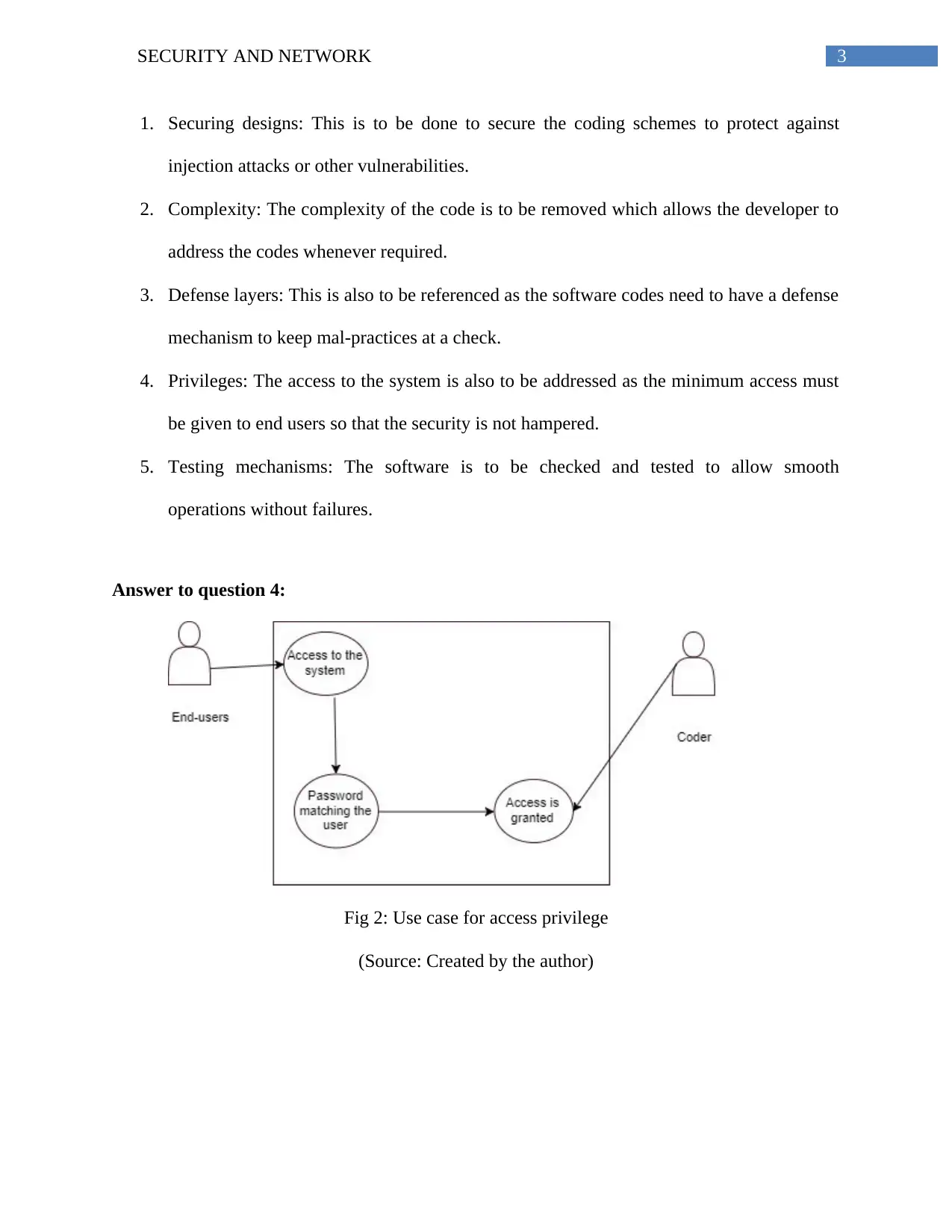
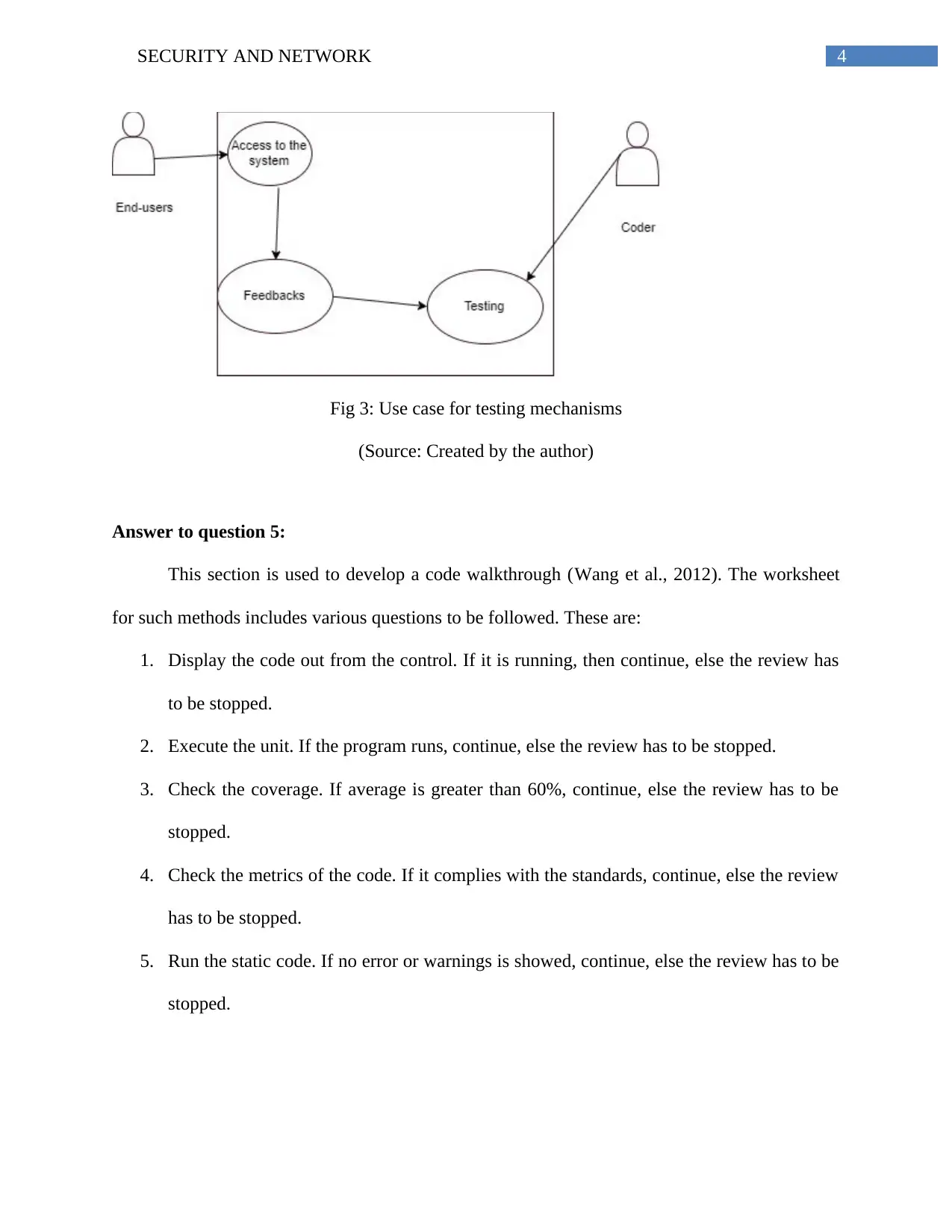
Homework Assignment
AI Summary
This document presents a comprehensive solution to a security and network assignment, addressing key aspects of modern cybersecurity. The solution begins by exploring the security challenges posed by Web 2.0 technologies, including authentication issues, cross-site scripting vulnerabilities, and injection attacks. It then delves into software development processes, outlining the phases of the software development life cycle and emphasizing the importance of secure coding practices. The assignment further highlights five crucial security considerations during coding, such as securing designs, managing complexity, implementing defense layers, controlling privileges, and utilizing robust testing mechanisms. Use case diagrams are provided to illustrate access privileges and testing mechanisms. Finally, the solution includes a detailed code walkthrough, outlining the steps and questions involved in reviewing code for security vulnerabilities. The document references several academic sources to support its findings and provide a well-rounded understanding of the subject matter.
1 out of 6











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)