MyHealth Company: Penetration Testing, BIA, and Ethical Report
VerifiedAdded on 2023/01/05
|13
|2053
|80
Report
AI Summary
This report presents a comprehensive analysis of penetration testing, ethical considerations, and business impact analysis (BIA) within the context of a security assessment for MyHealth Company. The introduction emphasizes the importance of penetration testing in identifying system vulnerabilities and the need for ethical conduct. The report delves into ethical hazards such as client reluctance and legal concerns, alongside ethical issues including information consent and confidentiality. It also includes the values of MTD, RTO, and RPO for various business processes, both before and after implementing controls, along with a BIA policy analysis. The reflective writing section discusses the impact of BIA on business continuity and recovery. The report concludes by highlighting the significance of penetration testing and BIA in risk management and ensuring the security of business operations, supported by relevant references.

[Document Title] 1
Affiliate Information
Affiliate Information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] 2
Table of Contents
Introduction................................................................................................................................................3
Ethical hazards...........................................................................................................................................5
Ethical issues..........................................................................................................................................5
BIA Policies for MyHealth Company....................................................................................................9
Conclusion...........................................................................................................................................11
References............................................................................................................................................12
Table of Contents
Introduction................................................................................................................................................3
Ethical hazards...........................................................................................................................................5
Ethical issues..........................................................................................................................................5
BIA Policies for MyHealth Company....................................................................................................9
Conclusion...........................................................................................................................................11
References............................................................................................................................................12
[Document Title] 3
Introduction
Penetration tester carries out the security tests for a system to ensure that they are not vulnerable to any
type of attacks (Meigh, 2013). The results of the tests are used to secure the system and apply necessary
updates to prevent further attacks. The process of penetration testing requires creativity and technical
knowledge. In case of occurrence of dilemmas during the process, the testers need to have new
approaches to mitigate the problems and carry on with the process.
The results of the tests are analyzed and forwarded to managers to enable them to make decisions to
improve the security issues found in the system. The skills possessed by the test is an aspect that is
considered to ensure delivery of correct results. The type and the number of tests carried determines the
chance and the level of outcomes.
Introduction
Penetration tester carries out the security tests for a system to ensure that they are not vulnerable to any
type of attacks (Meigh, 2013). The results of the tests are used to secure the system and apply necessary
updates to prevent further attacks. The process of penetration testing requires creativity and technical
knowledge. In case of occurrence of dilemmas during the process, the testers need to have new
approaches to mitigate the problems and carry on with the process.
The results of the tests are analyzed and forwarded to managers to enable them to make decisions to
improve the security issues found in the system. The skills possessed by the test is an aspect that is
considered to ensure delivery of correct results. The type and the number of tests carried determines the
chance and the level of outcomes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[Document Title] 4
Importance of penetration testing
Penetration testing is the act of testing a computer system for vulnerabilities that could be exploited.
The main objective of penetration testing is to test weakness in an organization’s system in compliance
with the requirements and the rules of the organization (Halfond, Choudhary & Orso, 2013).
Organizations should perform penetration testing regularly to ensure compliance and consistency with
network security issues. The information about a test is organized and analyzed to provide insightful
decision to secure and provide better mechanisms to defend against any form of attack.
The most preferred time when a penetration test is allowed in a company include :
When applying security patches to the existing systems – patches applied should be checked
and determined if they are compatible with the versions of the existing systems.
During system upgrades – when rolling out new updates for a system, it is important to
determine if they meet the requirements and compliance with the security.
When establishing new offices at other locations - the kind of systems that need be installed in
the new offices should be checked to ensure that they are safe and meet the requirements
criteria for the organization.
During the addition of new infrastructure - the introduction of a new application can be an
entry point for vulnerabilities, these applications need identification to find out if they are
compatible with the existing systems.
Importance of penetration testing
Penetration testing is the act of testing a computer system for vulnerabilities that could be exploited.
The main objective of penetration testing is to test weakness in an organization’s system in compliance
with the requirements and the rules of the organization (Halfond, Choudhary & Orso, 2013).
Organizations should perform penetration testing regularly to ensure compliance and consistency with
network security issues. The information about a test is organized and analyzed to provide insightful
decision to secure and provide better mechanisms to defend against any form of attack.
The most preferred time when a penetration test is allowed in a company include :
When applying security patches to the existing systems – patches applied should be checked
and determined if they are compatible with the versions of the existing systems.
During system upgrades – when rolling out new updates for a system, it is important to
determine if they meet the requirements and compliance with the security.
When establishing new offices at other locations - the kind of systems that need be installed in
the new offices should be checked to ensure that they are safe and meet the requirements
criteria for the organization.
During the addition of new infrastructure - the introduction of a new application can be an
entry point for vulnerabilities, these applications need identification to find out if they are
compatible with the existing systems.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] 5
Ethical hazards
This refers to the unethical behavior in the approach during the actual activity of carrying out the test.
These are actions that are most likely to introduce unwanted behavior in the operation of the task
(Mani, Barua and Whinston, 2010). Some of the hazards include:
Client reluctance – this is a situation in which the clients are defiant to apply the security
patches and now willing to comply with the recommendations from the security experts.
Red versus the Blue teams - this occurs when there are differences between the two teams in
reference to interacting with the clients.
Legal concerns - Uncertainties and disagreements between the agreed rules and regulations.
These are likely to tamper with the operations carried out during the tests.
Ethical issues
An ethical issue is a situation that occurs during which the pen tester has to choose between alternatives
which are evaluated as either right or wrong. The choice of the alternative depends on the motives of
the tester. Ethics can affect the decision making of the tester.
Major ethical issues taken into consideration during the test include:
1. Information consent – this means that a person is able to give consent and access to information in a
clear and voluntary way. Invasion of privacy is a breach and against the rules of any organization.
Personal information should be maintained with dignity and if the information is withheld, the subject
needs to notify.
Ethical hazards
This refers to the unethical behavior in the approach during the actual activity of carrying out the test.
These are actions that are most likely to introduce unwanted behavior in the operation of the task
(Mani, Barua and Whinston, 2010). Some of the hazards include:
Client reluctance – this is a situation in which the clients are defiant to apply the security
patches and now willing to comply with the recommendations from the security experts.
Red versus the Blue teams - this occurs when there are differences between the two teams in
reference to interacting with the clients.
Legal concerns - Uncertainties and disagreements between the agreed rules and regulations.
These are likely to tamper with the operations carried out during the tests.
Ethical issues
An ethical issue is a situation that occurs during which the pen tester has to choose between alternatives
which are evaluated as either right or wrong. The choice of the alternative depends on the motives of
the tester. Ethics can affect the decision making of the tester.
Major ethical issues taken into consideration during the test include:
1. Information consent – this means that a person is able to give consent and access to information in a
clear and voluntary way. Invasion of privacy is a breach and against the rules of any organization.
Personal information should be maintained with dignity and if the information is withheld, the subject
needs to notify.

[Document Title] 6
2. Confidentiality - this refers to the management of private information in order to protect the dignity
and the privacy of the involved subjects. When carrying out the test, the tester must promise the
security of the information and must work according to the given rules and regulations.
3. Skills of the tester - the level of competency for the tester is an important aspect which is used to
determine the success of the outcomes and the results. The testers should possess the necessary skills
and knowledge that is required to perform a successful test. Failure to have these skills might lead to a
problem in the delivery of the results.
2. Confidentiality - this refers to the management of private information in order to protect the dignity
and the privacy of the involved subjects. When carrying out the test, the tester must promise the
security of the information and must work according to the given rules and regulations.
3. Skills of the tester - the level of competency for the tester is an important aspect which is used to
determine the success of the outcomes and the results. The testers should possess the necessary skills
and knowledge that is required to perform a successful test. Failure to have these skills might lead to a
problem in the delivery of the results.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
[Document Title] 7
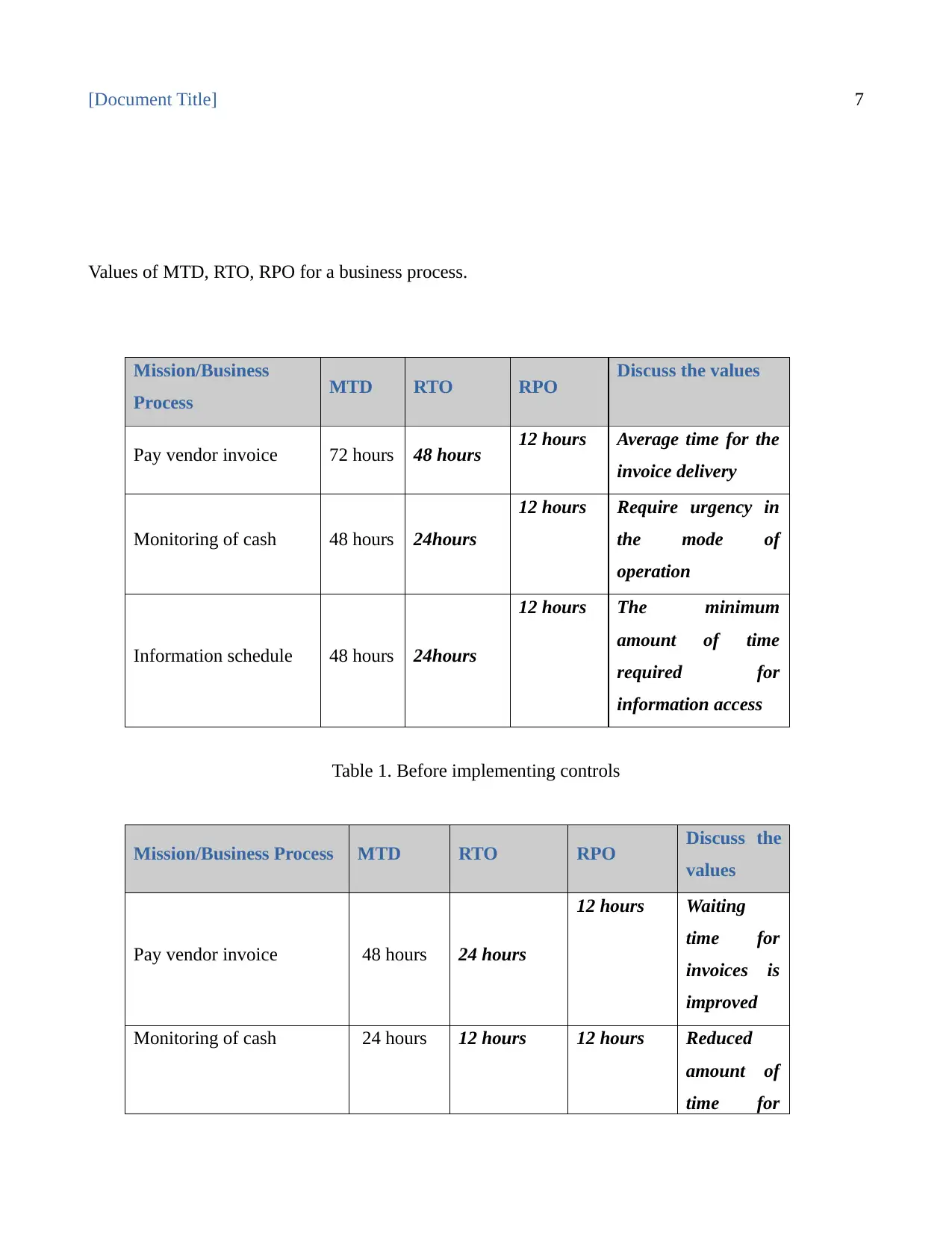
Values of MTD, RTO, RPO for a business process.
Mission/Business
Process MTD RTO RPO Discuss the values
Pay vendor invoice 72 hours 48 hours 12 hours Average time for the
invoice delivery
Monitoring of cash 48 hours 24hours
12 hours Require urgency in
the mode of
operation
Information schedule 48 hours 24hours
12 hours The minimum
amount of time
required for
information access
Table 1. Before implementing controls
Mission/Business Process MTD RTO RPO Discuss the
values
Pay vendor invoice 48 hours 24 hours
12 hours Waiting
time for
invoices is
improved
Monitoring of cash 24 hours 12 hours 12 hours Reduced
amount of
time for
Values of MTD, RTO, RPO for a business process.
Mission/Business
Process MTD RTO RPO Discuss the values
Pay vendor invoice 72 hours 48 hours 12 hours Average time for the
invoice delivery
Monitoring of cash 48 hours 24hours
12 hours Require urgency in
the mode of
operation
Information schedule 48 hours 24hours
12 hours The minimum
amount of time
required for
information access
Table 1. Before implementing controls
Mission/Business Process MTD RTO RPO Discuss the
values
Pay vendor invoice 48 hours 24 hours
12 hours Waiting
time for
invoices is
improved
Monitoring of cash 24 hours 12 hours 12 hours Reduced
amount of
time for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
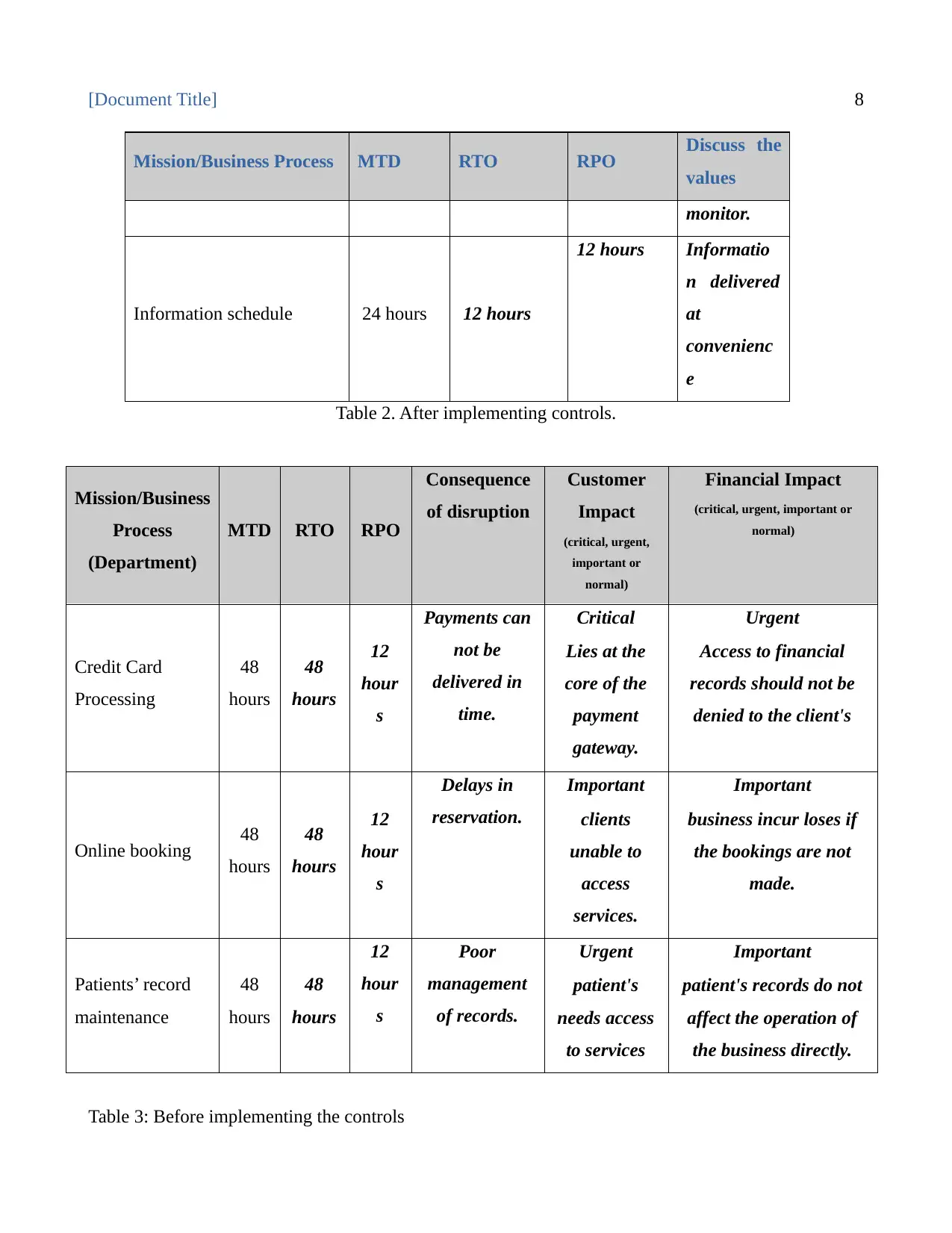
[Document Title] 8
Mission/Business Process MTD RTO RPO Discuss the
values
monitor.
Information schedule 24 hours 12 hours
12 hours Informatio
n delivered
at
convenienc
e
Table 2. After implementing controls.
Mission/Business
Process
(Department)
MTD RTO RPO
Consequence
of disruption
Customer
Impact
(critical, urgent,
important or
normal)
Financial Impact
(critical, urgent, important or
normal)
Credit Card
Processing
48
hours
48
hours
12
hour
s
Payments can
not be
delivered in
time.
Critical
Lies at the
core of the
payment
gateway.
Urgent
Access to financial
records should not be
denied to the client's
Online booking 48
hours
48
hours
12
hour
s
Delays in
reservation.
Important
clients
unable to
access
services.
Important
business incur loses if
the bookings are not
made.
Patients’ record
maintenance
48
hours
48
hours
12
hour
s
Poor
management
of records.
Urgent
patient's
needs access
to services
Important
patient's records do not
affect the operation of
the business directly.
Table 3: Before implementing the controls
Mission/Business Process MTD RTO RPO Discuss the
values
monitor.
Information schedule 24 hours 12 hours
12 hours Informatio
n delivered
at
convenienc
e
Table 2. After implementing controls.
Mission/Business
Process
(Department)
MTD RTO RPO
Consequence
of disruption
Customer
Impact
(critical, urgent,
important or
normal)
Financial Impact
(critical, urgent, important or
normal)
Credit Card
Processing
48
hours
48
hours
12
hour
s
Payments can
not be
delivered in
time.
Critical
Lies at the
core of the
payment
gateway.
Urgent
Access to financial
records should not be
denied to the client's
Online booking 48
hours
48
hours
12
hour
s
Delays in
reservation.
Important
clients
unable to
access
services.
Important
business incur loses if
the bookings are not
made.
Patients’ record
maintenance
48
hours
48
hours
12
hour
s
Poor
management
of records.
Urgent
patient's
needs access
to services
Important
patient's records do not
affect the operation of
the business directly.
Table 3: Before implementing the controls
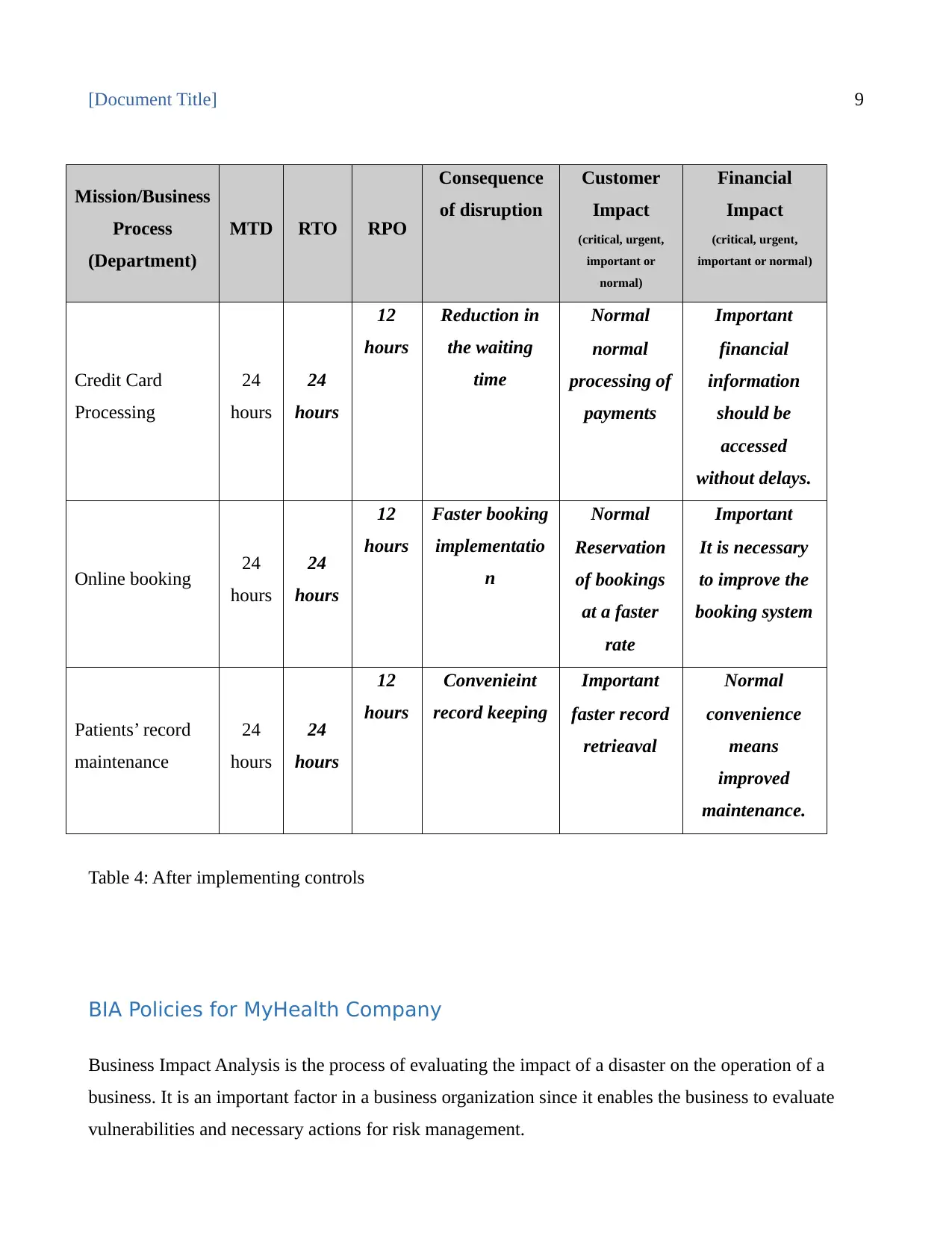
[Document Title] 9
Mission/Business
Process
(Department)
MTD RTO RPO
Consequence
of disruption
Customer
Impact
(critical, urgent,
important or
normal)
Financial
Impact
(critical, urgent,
important or normal)
Credit Card
Processing
24
hours
24
hours
12
hours
Reduction in
the waiting
time
Normal
normal
processing of
payments
Important
financial
information
should be
accessed
without delays.
Online booking 24
hours
24
hours
12
hours
Faster booking
implementatio
n
Normal
Reservation
of bookings
at a faster
rate
Important
It is necessary
to improve the
booking system
Patients’ record
maintenance
24
hours
24
hours
12
hours
Convenieint
record keeping
Important
faster record
retrieaval
Normal
convenience
means
improved
maintenance.
Table 4: After implementing controls
BIA Policies for MyHealth Company
Business Impact Analysis is the process of evaluating the impact of a disaster on the operation of a
business. It is an important factor in a business organization since it enables the business to evaluate
vulnerabilities and necessary actions for risk management.
Mission/Business
Process
(Department)
MTD RTO RPO
Consequence
of disruption
Customer
Impact
(critical, urgent,
important or
normal)
Financial
Impact
(critical, urgent,
important or normal)
Credit Card
Processing
24
hours
24
hours
12
hours
Reduction in
the waiting
time
Normal
normal
processing of
payments
Important
financial
information
should be
accessed
without delays.
Online booking 24
hours
24
hours
12
hours
Faster booking
implementatio
n
Normal
Reservation
of bookings
at a faster
rate
Important
It is necessary
to improve the
booking system
Patients’ record
maintenance
24
hours
24
hours
12
hours
Convenieint
record keeping
Important
faster record
retrieaval
Normal
convenience
means
improved
maintenance.
Table 4: After implementing controls
BIA Policies for MyHealth Company
Business Impact Analysis is the process of evaluating the impact of a disaster on the operation of a
business. It is an important factor in a business organization since it enables the business to evaluate
vulnerabilities and necessary actions for risk management.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

[Document Title] 10
Frequent monitoring of the environment to enhance the detection of faults or a disaster at an
early stage.
Proper maintenance of equipment that can deal with possible threats and disasters in case of an
occurrence.
Abiding by the rules and the legislation set up to ensure that any activity is in accordance with
the rules.
Implementation of procedures and techniques meant to reduce the occurrence of possible
threats.
Reflective writing
The business impact analysis was based on the evaluation of three business units. The main goal of the
analysis was the evaluation of the effectiveness of the use of controls to the business.
BIA is a necessary part of a business evaluation since it focuses on the continuity and the recovery of
the business from a threat (Shrader-Frechette, 2012). The BIA is designed to provide insightful analysis
and prediction of the type of anomalies and the consequences that can affect the business. The analysis
is designed to provide critical recovery techniques.
In the process of data recovery, the amount of time and service used in the restoration must be
determined first before the process commences. Impact assessment is a measure of the impact and is
attributed to the outcome and operations of the project.
The impact of BIA is paramount to a business activity, it enable the business to
recover from possible damages in case of occurrence. The process should be
carried out regularly, to ensure that a business premise is secure from any form
of violation.
BIA enables an organisation to initiate recovery plans that ensure consistency in the business, this
enable the managers and the operators of the organisation to determine and make informed decisions
about the important elements affecting the operations of the business. For instance, with the
advacement and growth in technology a business could migrate its operations to cloud computing. This
results to an improvement in the way usual business is carried out . This is because cloud computing
Frequent monitoring of the environment to enhance the detection of faults or a disaster at an
early stage.
Proper maintenance of equipment that can deal with possible threats and disasters in case of an
occurrence.
Abiding by the rules and the legislation set up to ensure that any activity is in accordance with
the rules.
Implementation of procedures and techniques meant to reduce the occurrence of possible
threats.
Reflective writing
The business impact analysis was based on the evaluation of three business units. The main goal of the
analysis was the evaluation of the effectiveness of the use of controls to the business.
BIA is a necessary part of a business evaluation since it focuses on the continuity and the recovery of
the business from a threat (Shrader-Frechette, 2012). The BIA is designed to provide insightful analysis
and prediction of the type of anomalies and the consequences that can affect the business. The analysis
is designed to provide critical recovery techniques.
In the process of data recovery, the amount of time and service used in the restoration must be
determined first before the process commences. Impact assessment is a measure of the impact and is
attributed to the outcome and operations of the project.
The impact of BIA is paramount to a business activity, it enable the business to
recover from possible damages in case of occurrence. The process should be
carried out regularly, to ensure that a business premise is secure from any form
of violation.
BIA enables an organisation to initiate recovery plans that ensure consistency in the business, this
enable the managers and the operators of the organisation to determine and make informed decisions
about the important elements affecting the operations of the business. For instance, with the
advacement and growth in technology a business could migrate its operations to cloud computing. This
results to an improvement in the way usual business is carried out . This is because cloud computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[Document Title] 11
overs transformation in the way business services are managed, developed and deployed to various
models.
The process and the amount of time taken for a business unit to process and deliver supplies to the
client's is define by the business information analysis.
The analysis gathers the information necessary that can be used to carry out the investigation facing the
business and predict the outcomes. The outcomes are then used to improve the business and recover
from possible threats.
With the increased number of users using the cloud, business models being deployed should make use
of the cloud computing to increase the success of the business.
overs transformation in the way business services are managed, developed and deployed to various
models.
The process and the amount of time taken for a business unit to process and deliver supplies to the
client's is define by the business information analysis.
The analysis gathers the information necessary that can be used to carry out the investigation facing the
business and predict the outcomes. The outcomes are then used to improve the business and recover
from possible threats.
With the increased number of users using the cloud, business models being deployed should make use
of the cloud computing to increase the success of the business.

[Document Title] 12
Conclusion
The impact of the business analysis provides an insight on how the business should be operated and the
effect of applying controls on the business. Different techniques and methodologies are used to
evaluate the effectiveness of the use of controls in the business.
Business impact analysis is used by the management for the purposes of identification and evaluation
of the risks that a business may incur due to a disaster or a threat. If the analysis is performed before the
occurrence of a crisis, the process enables the business to recover efficiently and smoothly from the
disaster.
The analysis gathers the information necessary that can be used to carry out the investigation facing the
business and predict the outcomes. The outcomes are then used to improve the business and recover
from possible threats.
Before a product is deployed, the product is assessed using different criteria and measures to ensure
that it meets the set limits. Impact analysis tells what part of the product needs adjustment and what
needs to be improved. This enables quick recovery of the product from disaster management.
Conclusion
The impact of the business analysis provides an insight on how the business should be operated and the
effect of applying controls on the business. Different techniques and methodologies are used to
evaluate the effectiveness of the use of controls in the business.
Business impact analysis is used by the management for the purposes of identification and evaluation
of the risks that a business may incur due to a disaster or a threat. If the analysis is performed before the
occurrence of a crisis, the process enables the business to recover efficiently and smoothly from the
disaster.
The analysis gathers the information necessary that can be used to carry out the investigation facing the
business and predict the outcomes. The outcomes are then used to improve the business and recover
from possible threats.
Before a product is deployed, the product is assessed using different criteria and measures to ensure
that it meets the set limits. Impact analysis tells what part of the product needs adjustment and what
needs to be improved. This enables quick recovery of the product from disaster management.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





