Assessment 1: Design and Implement ICT Networks Security Perimeter
VerifiedAdded on 2023/01/06
|28
|6020
|52
Report
AI Summary
This report addresses key aspects of designing and implementing a security perimeter for ICT networks. It begins by identifying various network security threats, including computer viruses, software vulnerabilities, hackers, employee negligence, and misuse of user account privileges. The report then delves into network security policies, outlining their purpose, essential considerations for formulation, and the steps involved in their implementation. Furthermore, the report explains penetration testing techniques, their importance, and the concept of network auditing. It examines software and hardware perimeter solutions, detailing their functionalities, advantages, and disadvantages. Finally, the report discusses the importance of log analysis, the infrastructure of knowledge management, and the role of various security tools like anti-malware software, email security, and endpoint security in maintaining a robust network security posture.

Design and Implement a
Security Perimeter for
ICT Networks
Security Perimeter for
ICT Networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Assessment 1
Question 1
1. Computer Viruses
PC infections have been in the news recently for organizational security threats they have posed
this year. These occur in a global range of infectious attacks, but diseases can pose a significant
threat to small groups (Salman, Khalaf, and Abdulsahib, 2019). Diseases can damage your data
and destroy important information, negatively affecting your daily activities. Even under the
most favorable conditions, infections can be eliminated from the hard drive. All in all, it's
important to encourage employees not to open an email or hook up a link they don't see.
2. Software Vulnerabilities Pose Network Security Risks
When a security update comes in the middle of a busy day, it's easy to get out of it and forget to
return it later. However, if your scheduling doesn't update as normally as you should, you could
be putting your organization at risk. It is inevitable that programs can return to an entire
organization where no one can work. It could cause a site to crash and be aware that it is down, it
could lose customers.
3. Hackers
We often think of network security threats as living on our PCs. However, PC programmers can
do terrible damage from anywhere. When programmers break into your framework, they have a
free rein. They can capture records, access specific data, or discover property tactics that your
competitors and the world can see. Programmers can be on the other side of the planet, but with
the chance that they do not value the security of your organization, they should not be deceived.
4. Employees Can Breach Security without Realizing It
In fact, even the most reliable employees can be a safety threat to your organization. It’s not
unintentional, but a lack of training in security best practices can put your organization in a weak
position (Iskandar, Virma and Ahmar, 2019). Make sure your employees see how best to secure
your organization, whether it's through instructions on sharing secure documents or maintaining
a collection of sites they shouldn't visit in the organization aged.
Question 1
1. Computer Viruses
PC infections have been in the news recently for organizational security threats they have posed
this year. These occur in a global range of infectious attacks, but diseases can pose a significant
threat to small groups (Salman, Khalaf, and Abdulsahib, 2019). Diseases can damage your data
and destroy important information, negatively affecting your daily activities. Even under the
most favorable conditions, infections can be eliminated from the hard drive. All in all, it's
important to encourage employees not to open an email or hook up a link they don't see.
2. Software Vulnerabilities Pose Network Security Risks
When a security update comes in the middle of a busy day, it's easy to get out of it and forget to
return it later. However, if your scheduling doesn't update as normally as you should, you could
be putting your organization at risk. It is inevitable that programs can return to an entire
organization where no one can work. It could cause a site to crash and be aware that it is down, it
could lose customers.
3. Hackers
We often think of network security threats as living on our PCs. However, PC programmers can
do terrible damage from anywhere. When programmers break into your framework, they have a
free rein. They can capture records, access specific data, or discover property tactics that your
competitors and the world can see. Programmers can be on the other side of the planet, but with
the chance that they do not value the security of your organization, they should not be deceived.
4. Employees Can Breach Security without Realizing It
In fact, even the most reliable employees can be a safety threat to your organization. It’s not
unintentional, but a lack of training in security best practices can put your organization in a weak
position (Iskandar, Virma and Ahmar, 2019). Make sure your employees see how best to secure
your organization, whether it's through instructions on sharing secure documents or maintaining
a collection of sites they shouldn't visit in the organization aged.

5. Abuse of user account privileges
According to information cited by the Harvard Business Review, for the period of 2016 “60% of
all attacks were carried out by professionals”. Whether it's innocent errors (unintentionally
sending information to an inappropriate email address or losing a working device), intentional
harassment and misuse of registration benefits or fraud wholesale as a result of a phishing
attempt or other social planning attacks that contract user account information, people within
your company are talking about one of the biggest security issues you will have.
Question 2
The primary purpose of a network security policy is to educate delegates and employees about
the needs of securing different resources. These assets require different structures, including
passwords, documents, or even servers (Omar and Abdelaziz, 2020). These policies also
establish rules for acquiring, designing and evaluating PC frameworks and networks. What
organizations should consider when formulating an organization security strategy include; what
do you have in the group that other people need? What circles, information or data structures are
critical to your association? What would prevent your organization from functioning? Responses
to these surveys identify a wide range of network resources. These include basic information
basics, basic applications, individual information, mutual group stock collection, personal email,
and web worker. Organizational security provisions must consider all elements that govern your
organization. The staff, however, the final messengers, and whoever has classified information
about your organizations. Employees are seen as a potential threat in security strategies.
However, these policies must be implemented so that employees remain ready to complete their
duties without undue disruption to safety efforts.
Steps in network security policy:
Identifying risks
Make sure the policy conforms to legal requirements
Level of security should be equal to level of risk
Including staff in policy development
Question 3
A. What do you mean by penetration testing techniques?
According to information cited by the Harvard Business Review, for the period of 2016 “60% of
all attacks were carried out by professionals”. Whether it's innocent errors (unintentionally
sending information to an inappropriate email address or losing a working device), intentional
harassment and misuse of registration benefits or fraud wholesale as a result of a phishing
attempt or other social planning attacks that contract user account information, people within
your company are talking about one of the biggest security issues you will have.
Question 2
The primary purpose of a network security policy is to educate delegates and employees about
the needs of securing different resources. These assets require different structures, including
passwords, documents, or even servers (Omar and Abdelaziz, 2020). These policies also
establish rules for acquiring, designing and evaluating PC frameworks and networks. What
organizations should consider when formulating an organization security strategy include; what
do you have in the group that other people need? What circles, information or data structures are
critical to your association? What would prevent your organization from functioning? Responses
to these surveys identify a wide range of network resources. These include basic information
basics, basic applications, individual information, mutual group stock collection, personal email,
and web worker. Organizational security provisions must consider all elements that govern your
organization. The staff, however, the final messengers, and whoever has classified information
about your organizations. Employees are seen as a potential threat in security strategies.
However, these policies must be implemented so that employees remain ready to complete their
duties without undue disruption to safety efforts.
Steps in network security policy:
Identifying risks
Make sure the policy conforms to legal requirements
Level of security should be equal to level of risk
Including staff in policy development
Question 3
A. What do you mean by penetration testing techniques?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A penetration test, also known as a pen test, is a reconstructed digital attack against your PC
framework to find out for usable vulnerabilities. For web application security, the access test is
usually used to extend a web application firewall (WAF).
Penetration testing is intended to conduct a security check before being attacked by an attacker.
Infiltration test tools generate qualified attack settings to detect and test security holes that may
require acquired records, bargain certificates, authorized innovation, truly identifiable data (PII) ,
cardholder information, personal data, guaranteed welfare, information emancipation or other
harmful business products.
Penetration testing techniques are the methods or ways through which penetration can be
practiced by hackers or backend servers.
B. What is the importance of penetration testing in terms of network security?
Penetration testing is a basic cycle that should be performed regularly in all companies to ensure
the structure of the body. The requirement to conduct an entrance exam changes as directed by
organizations as they all work differently.
One of the most important benefits of a pen testing or penetration testing is that it gives you the
blueprint for working with risk factors in an organized and unique way (Rusere and Ngassam,
2020). In this test, the extent of the weaknesses detected in the target climate and in addition to
the associated risk factors is determined. From the outset, continuity is treated with the highest
risk and then with the lowest risk.
Penetration testing allows security department to think about an organization's current situation
and examine possible current focuses. It gives us a reasonable idea of the whole security
framework and gives us the assurance that the design framework that the leaders followed is
appropriate within the organization.
C. Explain Network Auditing
Networks are dynamic entities; they grow, shrink, change and divide themselves continuously.
Network administrators cannot expect to be fully influenced by this circle. Customers include
tools and sometimes even new equipment for the foundation of the organization. Worse, this is
not the first time a client has installed the programs he needs without contacting the server.
framework to find out for usable vulnerabilities. For web application security, the access test is
usually used to extend a web application firewall (WAF).
Penetration testing is intended to conduct a security check before being attacked by an attacker.
Infiltration test tools generate qualified attack settings to detect and test security holes that may
require acquired records, bargain certificates, authorized innovation, truly identifiable data (PII) ,
cardholder information, personal data, guaranteed welfare, information emancipation or other
harmful business products.
Penetration testing techniques are the methods or ways through which penetration can be
practiced by hackers or backend servers.
B. What is the importance of penetration testing in terms of network security?
Penetration testing is a basic cycle that should be performed regularly in all companies to ensure
the structure of the body. The requirement to conduct an entrance exam changes as directed by
organizations as they all work differently.
One of the most important benefits of a pen testing or penetration testing is that it gives you the
blueprint for working with risk factors in an organized and unique way (Rusere and Ngassam,
2020). In this test, the extent of the weaknesses detected in the target climate and in addition to
the associated risk factors is determined. From the outset, continuity is treated with the highest
risk and then with the lowest risk.
Penetration testing allows security department to think about an organization's current situation
and examine possible current focuses. It gives us a reasonable idea of the whole security
framework and gives us the assurance that the design framework that the leaders followed is
appropriate within the organization.
C. Explain Network Auditing
Networks are dynamic entities; they grow, shrink, change and divide themselves continuously.
Network administrators cannot expect to be fully influenced by this circle. Customers include
tools and sometimes even new equipment for the foundation of the organization. Worse, this is
not the first time a client has installed the programs he needs without contacting the server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

These exercises can have a significant impact on network security. To explain this, a leader
needs to run a custom group that evaluates and screens for any progress to the pre-determined
mark.
Network auditing is a process in which your organization plans for both programming and
equipment. The circle can be awful when done physically, but fortunately some tools can help
mechanize a large part of the circle. The director must identify the tools and equipment
associated with the organization. A routine security check can identify a robbery; some
customers may choose some affordable storage at their workplace that is more likely to be used
at home.
Question 4
A. Software perimeter solution
Software perimeter solution allows IT managers to deploy on-premises or over-the-cloud
deployments by linking remote access of representatives to cloud and on-premises applications
while maintaining sensitive information within the hierarchical group. It has been shown to block
all types of organizational attacks, including DDoS, Man-in-the-Middle, Server Question and
Advanced Persistent Risk.
Implementing Software perimeter solution allows associations to restrict network access and
access to organized frameworks. Accessibility depends on the usability model, which means that
all devices and characters must be checked before being accepted into the group.
A software-defined perimeter (SDP) is a way to hide Internet-connected infrastructure (servers,
routers, etc.) so that it cannot be seen by external groups and attackers, however whether it is
enabled on premises or in the cloud (Ramadan and Hefnawi, 2019). The goal of the SDP
approach is to bring the organization together in terms of programming rather than equipment.
An organization that basically uses SDP hangs a little bit of instability on its staff and another
framework so that no one can see it from an outside perspective; however, approved customers
can now access the platform.
A software-defined perimeter forms a virtual boundary around organizational resources at the
organizational level, not at the application level. This separates it from accessibility-based
controls that limit user benefits but allow access to a large group. Another key difference is that
needs to run a custom group that evaluates and screens for any progress to the pre-determined
mark.
Network auditing is a process in which your organization plans for both programming and
equipment. The circle can be awful when done physically, but fortunately some tools can help
mechanize a large part of the circle. The director must identify the tools and equipment
associated with the organization. A routine security check can identify a robbery; some
customers may choose some affordable storage at their workplace that is more likely to be used
at home.
Question 4
A. Software perimeter solution
Software perimeter solution allows IT managers to deploy on-premises or over-the-cloud
deployments by linking remote access of representatives to cloud and on-premises applications
while maintaining sensitive information within the hierarchical group. It has been shown to block
all types of organizational attacks, including DDoS, Man-in-the-Middle, Server Question and
Advanced Persistent Risk.
Implementing Software perimeter solution allows associations to restrict network access and
access to organized frameworks. Accessibility depends on the usability model, which means that
all devices and characters must be checked before being accepted into the group.
A software-defined perimeter (SDP) is a way to hide Internet-connected infrastructure (servers,
routers, etc.) so that it cannot be seen by external groups and attackers, however whether it is
enabled on premises or in the cloud (Ramadan and Hefnawi, 2019). The goal of the SDP
approach is to bring the organization together in terms of programming rather than equipment.
An organization that basically uses SDP hangs a little bit of instability on its staff and another
framework so that no one can see it from an outside perspective; however, approved customers
can now access the platform.
A software-defined perimeter forms a virtual boundary around organizational resources at the
organizational level, not at the application level. This separates it from accessibility-based
controls that limit user benefits but allow access to a large group. Another key difference is that

SDP identifies devices directly as a user character. The Cloud Security Alliance first came up
with the idea of SDP.
B. Hardware Perimeter solution
Because the drawbacks of software-based perimeters are centered on their inefficient network
position, a hardware solution is the safest alternative. The edges of the equipment are located just
behind the switch, so all information packets from the web must go through your monitor before
you reach internal drivers.
Most of these solutions include far more advanced controls than simple web filtering and basic
data scanning. Like most advances in IT, the latest hardware perimeters is based on “visual”
capabilities that analyze big data to detect malware and cyber attacks that rely on sporadic
exercises instead of spyware. be solely dependent on tactical diseases and aggressive vectors.
Another advantage of hardware perimeters is that they are generally functional. There is no
compelling reason to point out whether the response-enabled workstation collapses after these
devices are running for security all day, every day. The main disadvantage of this type of
accommodation is the level of observation and maintenance it requires. Hardware perimeters are
incredibly incredible, and managing them is no easy task.
Question 5
Computers, networks, and other IT processes create documents that track system operations,
called audit trail reports or logs. The review of these documents is log analysis which is used by
organizations to help manage a range of risks which comply with regulatory regulations.
Network computers, software, operating systems, and configurable or smart devices typically
build records. They consist of several messages that are organized and stored sequentially on a
disc, in folders, or like a log collector in a program.
Analysts need to insure that a full set of communications are comprised of the logs and presented
according to meaning. To prevent misunderstanding to have cohesiveness, log components
should be normalized, using the same language or words. For example, "alert" may be used by
one device while another uses "important." Making sure the terminology and data types are
compatible would help to promote interpretation and minimize error (Angelo, 2019).
with the idea of SDP.
B. Hardware Perimeter solution
Because the drawbacks of software-based perimeters are centered on their inefficient network
position, a hardware solution is the safest alternative. The edges of the equipment are located just
behind the switch, so all information packets from the web must go through your monitor before
you reach internal drivers.
Most of these solutions include far more advanced controls than simple web filtering and basic
data scanning. Like most advances in IT, the latest hardware perimeters is based on “visual”
capabilities that analyze big data to detect malware and cyber attacks that rely on sporadic
exercises instead of spyware. be solely dependent on tactical diseases and aggressive vectors.
Another advantage of hardware perimeters is that they are generally functional. There is no
compelling reason to point out whether the response-enabled workstation collapses after these
devices are running for security all day, every day. The main disadvantage of this type of
accommodation is the level of observation and maintenance it requires. Hardware perimeters are
incredibly incredible, and managing them is no easy task.
Question 5
Computers, networks, and other IT processes create documents that track system operations,
called audit trail reports or logs. The review of these documents is log analysis which is used by
organizations to help manage a range of risks which comply with regulatory regulations.
Network computers, software, operating systems, and configurable or smart devices typically
build records. They consist of several messages that are organized and stored sequentially on a
disc, in folders, or like a log collector in a program.
Analysts need to insure that a full set of communications are comprised of the logs and presented
according to meaning. To prevent misunderstanding to have cohesiveness, log components
should be normalized, using the same language or words. For example, "alert" may be used by
one device while another uses "important." Making sure the terminology and data types are
compatible would help to promote interpretation and minimize error (Angelo, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Normalization also guarantees the significance and consistency of figures and information from
multiple sources.
Question 6
The infrastructure of the knowledge management to tools that enable access, communication,
activity, and management of the network. It usually requires devices, applications, and facilities
for networking (Paul, Kumar and Suman, 2019). If your network is not stable, various threats,
such as denial-of - service, ransom ware, spam, and unauthorized access, are severely vulnerable.
MSPs are facing an ever-present management problem as they work to protect their internet
infrastructure stability, as per security professionals. The challenge is to identify essential
network assets, identify in which these assets are stored by organizations and find the right
balance between powerful, complex defenses and usability and access protection.
Question 7
Anti-malware software- Malware is intended to spread across computer systems and
infiltrate networks in the form of viruses, Trojans, worms, key loggers, spyware, etc.
Anti-malware solutions are a kind of applications for network protection intended to
detect and avoid the dissemination of harmful programmers. Anti-malware and antivirus
applications may also assist in the resolution of malware infections, reducing network
harm.
Email security- Email security is based on shortening human-related security
vulnerabilities, as in DLP. Via spam tactics (often very complicated and compelling),
attackers force receivers of emails to exchange sensitive data via a computer or mobile
device, or accidentally transfer malware to the organization's device. Safety in email
helps recognize unsafe communications and could also be used to block threats and avoid
sensitive data from being exchanged.
Endpoint security- The corporate world is gradually bringing your own gadget (BYOD)
to the point that there is virtually no difference between individual and commercial
computing devices. Regrettably, as consumers rely on them to reach business networks,
multiple sources.
Question 6
The infrastructure of the knowledge management to tools that enable access, communication,
activity, and management of the network. It usually requires devices, applications, and facilities
for networking (Paul, Kumar and Suman, 2019). If your network is not stable, various threats,
such as denial-of - service, ransom ware, spam, and unauthorized access, are severely vulnerable.
MSPs are facing an ever-present management problem as they work to protect their internet
infrastructure stability, as per security professionals. The challenge is to identify essential
network assets, identify in which these assets are stored by organizations and find the right
balance between powerful, complex defenses and usability and access protection.
Question 7
Anti-malware software- Malware is intended to spread across computer systems and
infiltrate networks in the form of viruses, Trojans, worms, key loggers, spyware, etc.
Anti-malware solutions are a kind of applications for network protection intended to
detect and avoid the dissemination of harmful programmers. Anti-malware and antivirus
applications may also assist in the resolution of malware infections, reducing network
harm.
Email security- Email security is based on shortening human-related security
vulnerabilities, as in DLP. Via spam tactics (often very complicated and compelling),
attackers force receivers of emails to exchange sensitive data via a computer or mobile
device, or accidentally transfer malware to the organization's device. Safety in email
helps recognize unsafe communications and could also be used to block threats and avoid
sensitive data from being exchanged.
Endpoint security- The corporate world is gradually bringing your own gadget (BYOD)
to the point that there is virtually no difference between individual and commercial
computing devices. Regrettably, as consumers rely on them to reach business networks,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

electronic devices often become targets. Protection at the endpoint provides a security
layer for remote computers and enterprise networks.
Firewalls- Firewalls operate just like gateways that can be used to protect barriers
between your network and internet. Firewalls are used for channel traffic control,
enabling allowed traffic to pass through and blocking unauthorized traffic entry
(Wetterwald and Seewald, Cisco Technology Inc, 2019).
Virtual private network- VPN software is used to verify contact between such a secure
system and an endpoint computer. Remote access VPNs typically uses IPSec or Safe
Sockets Layer (SSL) for encryption, providing a protected path to prevent certain parties
from snooping.
Question 8
A. Firewall
The failure to deter threats from inside the structure that it is intended to defend.
It can just block the traffic intrusions that really go into them.
It cannot bypass overly designed compliance procedures or bad management standards.
It cannot bypass overly designed compliance procedures or bad management standards.
For example, if an organization has a very poorly knit security plan and over-permissive
rules, then a firewall cannot protect the information or the network.
As long as a contact or operation is enabled, the firewall has no power to protect the
device it against. For example, if a firewall is built to allow email to move through, it
could not identify a virus or a Trojan inside the email.
B. VPN
A VPN service provider who does not take the protection and privacy of the customer
strictly will typically ignore any issues who users are facing. Moreover, this sort of
treatment is typically unstable and cannot provide consumers the online security and
privacy they require (Nichols, 2019).
layer for remote computers and enterprise networks.
Firewalls- Firewalls operate just like gateways that can be used to protect barriers
between your network and internet. Firewalls are used for channel traffic control,
enabling allowed traffic to pass through and blocking unauthorized traffic entry
(Wetterwald and Seewald, Cisco Technology Inc, 2019).
Virtual private network- VPN software is used to verify contact between such a secure
system and an endpoint computer. Remote access VPNs typically uses IPSec or Safe
Sockets Layer (SSL) for encryption, providing a protected path to prevent certain parties
from snooping.
Question 8
A. Firewall
The failure to deter threats from inside the structure that it is intended to defend.
It can just block the traffic intrusions that really go into them.
It cannot bypass overly designed compliance procedures or bad management standards.
It cannot bypass overly designed compliance procedures or bad management standards.
For example, if an organization has a very poorly knit security plan and over-permissive
rules, then a firewall cannot protect the information or the network.
As long as a contact or operation is enabled, the firewall has no power to protect the
device it against. For example, if a firewall is built to allow email to move through, it
could not identify a virus or a Trojan inside the email.
B. VPN
A VPN service provider who does not take the protection and privacy of the customer
strictly will typically ignore any issues who users are facing. Moreover, this sort of
treatment is typically unstable and cannot provide consumers the online security and
privacy they require (Nichols, 2019).

Many VPN providers do use flat sheet encryption to shield their users online.
The trouble with free VPN providers out there is that they only provide the standard
encryption method, which is the kind of authentication that attackers can easily crack.
Not all authentication schemes have the same encryption standard, and the worrying
thing is that many VPN providers out there do use poor safety procedures as their
primary defense mechanism.
Question 9
Regularly Check and Update the Firewall Configuration Settings- Over time , the
organization will actually have a lot of unique configurations for the different firewalls it
uses on the network perimeter, and it may be an issue if these configurations cause
overlapping guidelines.
Use Defense in Depth- While having several firewalls can be a little more difficult to set
up for your system, doing so will help you develop deeper defenses. This, in essence,
slows down some threats that have found their way through a firewall.
Make Sure There Aren’t ANY Modems in Your Internal Network- Here's the tip of the
SANS Institute. As a basic step in testing the configuration of firewalls, it is advised that '
the investigator ensure that neither modems remain within the corporate network
(Chattopadhyay, Lam and Tavva, 2019).
Using Deep Packet Inspection- One of the challenges when using firewalls is that many
malicious programmers use spoofing to fool firewalls to bring heavy traffic in. These
intermediate nodes would have forged arrival and departure codes, enough to circumvent
simplified firewalls.
Don’t Just Rely on Firewalls- Even with the most sophisticated anti-spoofing technology,
best-managed rule setups, but in-depth security technology, firewalls cannot block any
attack under their own.
Question 10
A three-legged firewall solution can be used where it is not possible to have two mechanically
independent firewall systems splitting traffic from multiple network segments. Usually, a new
The trouble with free VPN providers out there is that they only provide the standard
encryption method, which is the kind of authentication that attackers can easily crack.
Not all authentication schemes have the same encryption standard, and the worrying
thing is that many VPN providers out there do use poor safety procedures as their
primary defense mechanism.
Question 9
Regularly Check and Update the Firewall Configuration Settings- Over time , the
organization will actually have a lot of unique configurations for the different firewalls it
uses on the network perimeter, and it may be an issue if these configurations cause
overlapping guidelines.
Use Defense in Depth- While having several firewalls can be a little more difficult to set
up for your system, doing so will help you develop deeper defenses. This, in essence,
slows down some threats that have found their way through a firewall.
Make Sure There Aren’t ANY Modems in Your Internal Network- Here's the tip of the
SANS Institute. As a basic step in testing the configuration of firewalls, it is advised that '
the investigator ensure that neither modems remain within the corporate network
(Chattopadhyay, Lam and Tavva, 2019).
Using Deep Packet Inspection- One of the challenges when using firewalls is that many
malicious programmers use spoofing to fool firewalls to bring heavy traffic in. These
intermediate nodes would have forged arrival and departure codes, enough to circumvent
simplified firewalls.
Don’t Just Rely on Firewalls- Even with the most sophisticated anti-spoofing technology,
best-managed rule setups, but in-depth security technology, firewalls cannot block any
attack under their own.
Question 10
A three-legged firewall solution can be used where it is not possible to have two mechanically
independent firewall systems splitting traffic from multiple network segments. Usually, a new
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
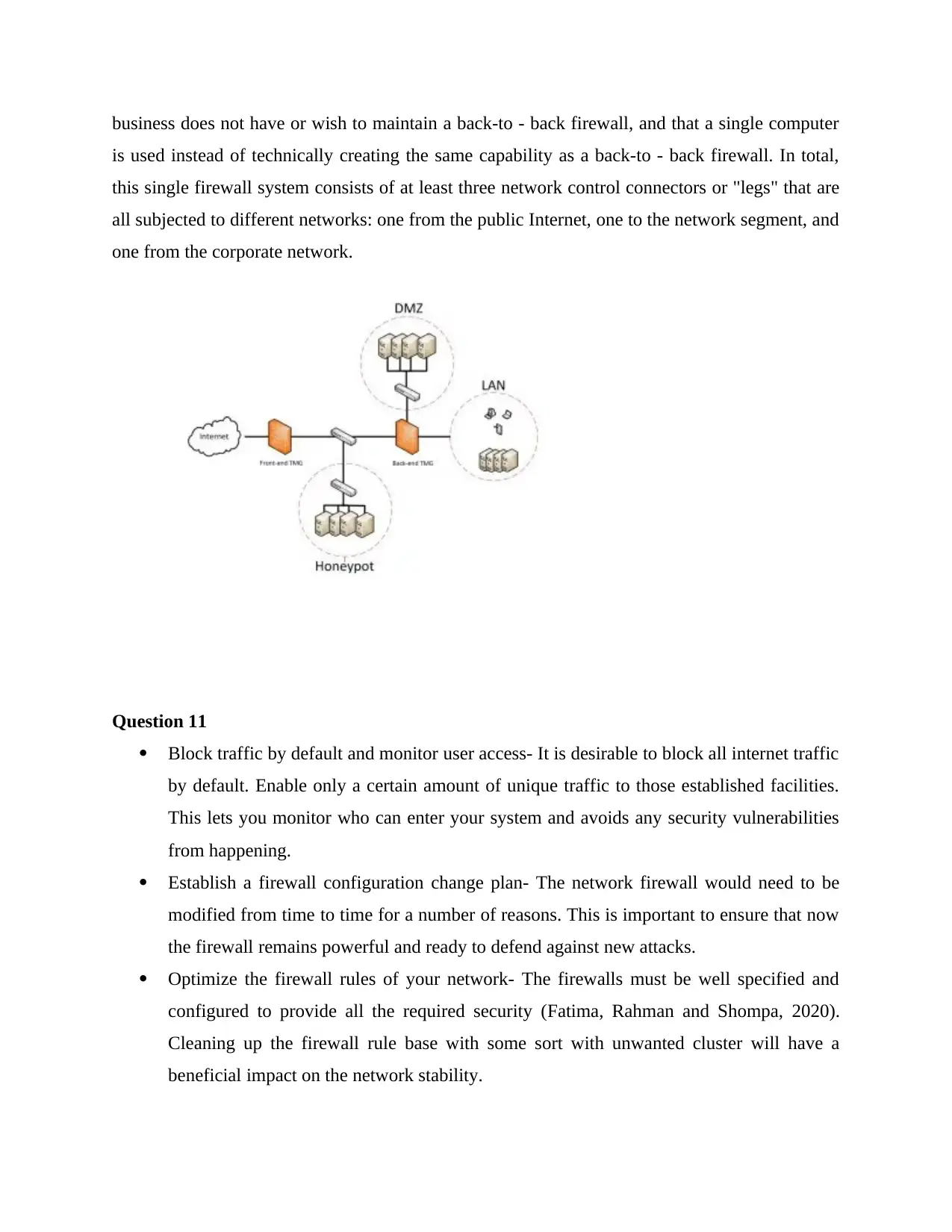
business does not have or wish to maintain a back-to - back firewall, and that a single computer
is used instead of technically creating the same capability as a back-to - back firewall. In total,
this single firewall system consists of at least three network control connectors or "legs" that are
all subjected to different networks: one from the public Internet, one to the network segment, and
one from the corporate network.
Question 11
Block traffic by default and monitor user access- It is desirable to block all internet traffic
by default. Enable only a certain amount of unique traffic to those established facilities.
This lets you monitor who can enter your system and avoids any security vulnerabilities
from happening.
Establish a firewall configuration change plan- The network firewall would need to be
modified from time to time for a number of reasons. This is important to ensure that now
the firewall remains powerful and ready to defend against new attacks.
Optimize the firewall rules of your network- The firewalls must be well specified and
configured to provide all the required security (Fatima, Rahman and Shompa, 2020).
Cleaning up the firewall rule base with some sort with unwanted cluster will have a
beneficial impact on the network stability.
is used instead of technically creating the same capability as a back-to - back firewall. In total,
this single firewall system consists of at least three network control connectors or "legs" that are
all subjected to different networks: one from the public Internet, one to the network segment, and
one from the corporate network.
Question 11
Block traffic by default and monitor user access- It is desirable to block all internet traffic
by default. Enable only a certain amount of unique traffic to those established facilities.
This lets you monitor who can enter your system and avoids any security vulnerabilities
from happening.
Establish a firewall configuration change plan- The network firewall would need to be
modified from time to time for a number of reasons. This is important to ensure that now
the firewall remains powerful and ready to defend against new attacks.
Optimize the firewall rules of your network- The firewalls must be well specified and
configured to provide all the required security (Fatima, Rahman and Shompa, 2020).
Cleaning up the firewall rule base with some sort with unwanted cluster will have a
beneficial impact on the network stability.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Update your firewall software regularly- Firewall vendors typically issue security
upgrades on a daily basis. These upgrades fix any current possible security risks by
allowing small technical improvements.
Question 12
Packet level filtering- The internet protocol uses two names: the origin Id number and the
target IP address for navigate and transmit a data packet through the network.
Circuit level filtering- Circuit level filtering reaches above the filtering at the packet
level. Filters traffic depending on the characteristics of the network layer. The network
layer uses the port number to define the target programmed.
Application level filtering- This is the maximum filtering standard. Filters information
centered on an interface layer interface such as HTTP and FTP. It can also record traffic
for further examination or response.
State full inspection- Hardware file system can be designed to capture and store data
about each packet going through it. This knowledge can be used to philter additional
packets
Question 13
Network backup is a device where chosen data from your backup clients (a single device or a
group of computers) is sent over a channel (such as the Internet) and forwarded to your remote
backup (Dzhalladova, Novotna and Babynyuk, 2019). This database may be privately owned and
operated, or openly maintained by a cloud storage service — as is always the case with many
other small companies. There are several reasons to use network backups for your company.
Managerial backups for various machines and networked systems can be a problem when you
use physical storage media, tape drives, or individually back up each computer individually.
Question 14
Identify the tools and security specifications of the network.
Identify identified risks and how to deal with them.
Operating structures, variants, and software paper (Miloslavskaya, 2019).
Establish the workflow of the company for approved interactions, access privileges
depending on employee responsibilities and user specifications.
upgrades on a daily basis. These upgrades fix any current possible security risks by
allowing small technical improvements.
Question 12
Packet level filtering- The internet protocol uses two names: the origin Id number and the
target IP address for navigate and transmit a data packet through the network.
Circuit level filtering- Circuit level filtering reaches above the filtering at the packet
level. Filters traffic depending on the characteristics of the network layer. The network
layer uses the port number to define the target programmed.
Application level filtering- This is the maximum filtering standard. Filters information
centered on an interface layer interface such as HTTP and FTP. It can also record traffic
for further examination or response.
State full inspection- Hardware file system can be designed to capture and store data
about each packet going through it. This knowledge can be used to philter additional
packets
Question 13
Network backup is a device where chosen data from your backup clients (a single device or a
group of computers) is sent over a channel (such as the Internet) and forwarded to your remote
backup (Dzhalladova, Novotna and Babynyuk, 2019). This database may be privately owned and
operated, or openly maintained by a cloud storage service — as is always the case with many
other small companies. There are several reasons to use network backups for your company.
Managerial backups for various machines and networked systems can be a problem when you
use physical storage media, tape drives, or individually back up each computer individually.
Question 14
Identify the tools and security specifications of the network.
Identify identified risks and how to deal with them.
Operating structures, variants, and software paper (Miloslavskaya, 2019).
Establish the workflow of the company for approved interactions, access privileges
depending on employee responsibilities and user specifications.

Evaluate the firewall: build a firewall to secure the edge (internet-facing), the centre (big
business-facing) or the DMZ (vestige of the first line of defense)
Plan the firewall for convenience.
In order to secure sensitive information on the network, they can first define what
information (e.g. credit card data or patient data) are.
This traffic would be enabled with the use of firewall rules called access control lists
(ACLs) that are added to each application or body and make on the firewall.
Question 15
Step 1- Sign in to the local browser's web-based functionality and select VPN > Site-to-Site.
business-facing) or the DMZ (vestige of the first line of defense)
Plan the firewall for convenience.
In order to secure sensitive information on the network, they can first define what
information (e.g. credit card data or patient data) are.
This traffic would be enabled with the use of firewall rules called access control lists
(ACLs) that are added to each application or body and make on the firewall.
Question 15
Step 1- Sign in to the local browser's web-based functionality and select VPN > Site-to-Site.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





