Security Policy Framework Document: A Comprehensive Overview
VerifiedAdded on 2019/09/22
|14
|2582
|468
Report
AI Summary
This report presents a detailed security policy framework document, essential for organizations to establish robust security measures. It begins with an introduction to the framework, emphasizing its role in mitigating both internal and external threats and ensuring compliance with regulations, especially within the financial industry. The report then outlines an acceptable usage policy, providing guidelines for employee conduct regarding passwords, data sharing, and internet usage. It delves into business continuity planning, including team organization, impact analysis, and incident response protocols, along with disaster recovery planning, which covers risk assessment, impact analysis, and recovery mechanisms. Ethical considerations, such as privacy and copyright, are also addressed. The report further explores security architecture, emphasizing confidentiality, integrity, and availability, along with the application of the Biba Model. Security management practices are discussed in terms of confidentiality, integrity, and availability, with an emphasis on the importance of business continuity planning. Finally, the document concludes with a section on applications, telecommunications, and network security, highlighting the use of VPNs, intrusion detection systems, and firewalls to enhance security.

Security Policy Framework Document
Student Name:
Student ID:
Course Name:
Course ID:
Faculty Name:
University Name:
Student Name:
Student ID:
Course Name:
Course ID:
Faculty Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction................................................................................................................................2
Acceptable Usage Policy............................................................................................................2
Business Continuity Planning....................................................................................................4
Disaster Recovery Planning.......................................................................................................5
Ethics..........................................................................................................................................6
Security Architecture and Models..............................................................................................7
Security Management Practices.................................................................................................7
Applications, Telecommunications and Network Security........................................................8
References................................................................................................................................10
Appendices...............................................................................................................................11
Appendix A: Business Continuity Team Organization Chart..............................................11
Appendix B: Risk Attributes................................................................................................12
Appendix C: Disaster Impact...............................................................................................12
Appendix D: Biba Model.....................................................................................................13
Appendix E: Layers..............................................................................................................13
Appendix F: Security Management Practices......................................................................13
Introduction................................................................................................................................2
Acceptable Usage Policy............................................................................................................2
Business Continuity Planning....................................................................................................4
Disaster Recovery Planning.......................................................................................................5
Ethics..........................................................................................................................................6
Security Architecture and Models..............................................................................................7
Security Management Practices.................................................................................................7
Applications, Telecommunications and Network Security........................................................8
References................................................................................................................................10
Appendices...............................................................................................................................11
Appendix A: Business Continuity Team Organization Chart..............................................11
Appendix B: Risk Attributes................................................................................................12
Appendix C: Disaster Impact...............................................................................................12
Appendix D: Biba Model.....................................................................................................13
Appendix E: Layers..............................................................................................................13
Appendix F: Security Management Practices......................................................................13

Introduction
The Security Policy Framework Document is the set of properly written policies on security.
The security policy framework ensures that the organization has procedures that can be used
at the time of potential threat or challenges (Herath & Rao, 2009). The threat or challenge can
be internal to the organization or it can be external to the organization. Moreover, the
presence of SPFD within the organization keeps it complied with the ever changing rules and
regulation concerning security aspects. SPFD can be used by the organizations that are
oriented towards development of measures that can handle the risks or vulnerabilities
associated with the organization. The risks can be of various forms such as hardware
challenges, software risks, and threat to networks within the organization, challenge from the
human side (specifically the individuals who are working within the organization),
environmental threats, and others.
The SPFD is required in the financial industry as due to the recent development in the
technological aspects has equally increased the level of threat to the information contained
within the organization or within the entire financial industry. The entire economy of a
country relies on the financial industry and any threat to this industry is likely to impact the
functioning of whole economy. Therefore, it has always been suggested that the organizations
operating in a risky environment should consider using security policy framework document.
The current paper discusses various aspects of security policy framework development under
various sections and subsections.
Acceptable Usage Policy
Given below are the acceptable usage policies for the current organization (Gallagher et al,
2015):
The Security Policy Framework Document is the set of properly written policies on security.
The security policy framework ensures that the organization has procedures that can be used
at the time of potential threat or challenges (Herath & Rao, 2009). The threat or challenge can
be internal to the organization or it can be external to the organization. Moreover, the
presence of SPFD within the organization keeps it complied with the ever changing rules and
regulation concerning security aspects. SPFD can be used by the organizations that are
oriented towards development of measures that can handle the risks or vulnerabilities
associated with the organization. The risks can be of various forms such as hardware
challenges, software risks, and threat to networks within the organization, challenge from the
human side (specifically the individuals who are working within the organization),
environmental threats, and others.
The SPFD is required in the financial industry as due to the recent development in the
technological aspects has equally increased the level of threat to the information contained
within the organization or within the entire financial industry. The entire economy of a
country relies on the financial industry and any threat to this industry is likely to impact the
functioning of whole economy. Therefore, it has always been suggested that the organizations
operating in a risky environment should consider using security policy framework document.
The current paper discusses various aspects of security policy framework development under
various sections and subsections.
Acceptable Usage Policy
Given below are the acceptable usage policies for the current organization (Gallagher et al,
2015):
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
- The employees should not allow other members to use their id or password.
- The passwords or other sensitive materials should not be left at publicly accessible
locations. It is suggested to remember the passwords rather than putting them in
physical.
- One employee should not use other employee’s passwords and id.
- The employees should not engage in attempt to access the information for which they
are not authorized.
- Employees should not use external device with the organization’s device.
- Employees are advised not to share any data or information of the organization to the
external parties in any circumstances unless authorized by upper management.
- The email id provided to the each of the employees and the internet is for the business
use and no employees are suggested to use these for personal amusement.
- Every individual will be accountable for whatever action they take while accessing
the internet or the company email systems.
- Employees should not place any company information online that is likely to
compromise the security of the company.
- No employees should engage in sending spam mails to other individual.
- The attachments within the mails, if received from outside, must be passed through
right security check prior to opening them.
- Employees engaging offsite work should abide by the security policy devised by the
company for that purpose.
- The business documents that are out of use must be properly shredded prior to
disposal.
- The passwords or other sensitive materials should not be left at publicly accessible
locations. It is suggested to remember the passwords rather than putting them in
physical.
- One employee should not use other employee’s passwords and id.
- The employees should not engage in attempt to access the information for which they
are not authorized.
- Employees should not use external device with the organization’s device.
- Employees are advised not to share any data or information of the organization to the
external parties in any circumstances unless authorized by upper management.
- The email id provided to the each of the employees and the internet is for the business
use and no employees are suggested to use these for personal amusement.
- Every individual will be accountable for whatever action they take while accessing
the internet or the company email systems.
- Employees should not place any company information online that is likely to
compromise the security of the company.
- No employees should engage in sending spam mails to other individual.
- The attachments within the mails, if received from outside, must be passed through
right security check prior to opening them.
- Employees engaging offsite work should abide by the security policy devised by the
company for that purpose.
- The business documents that are out of use must be properly shredded prior to
disposal.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

- The external devices can be used when there is absence of network connections or
there is alternate option of transferring data. However, it should be done under the
supervision of knowledgeable IT security personnel.
Business Continuity Planning
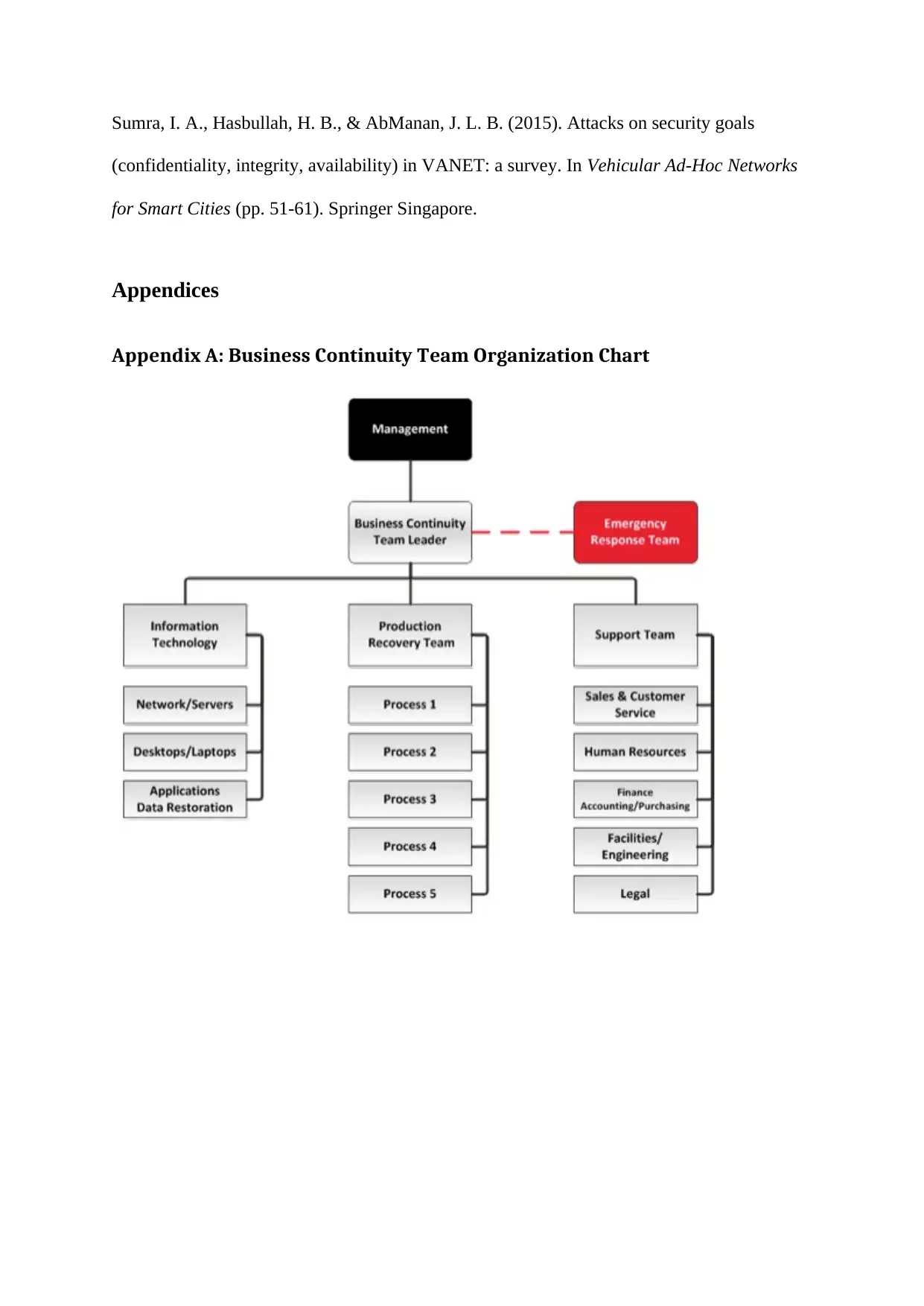
The business continuity planning covers the team organization chart that has been shown in
the Appendix A. A business continuity team is accompanied by the business continuity team
leader. The diagram covers the basic business requirements covering the Information
Technology, Production Recovery Team, and the Support Team (Levy et al, 2016). There are
various aspects that are to be covered within the business continuity planning. The first aspect
is associated with understanding the impact through analysis which will include the recovery
time for business activities and IT. Given below is the plan for the business continuity:
- Actions checklist should be prepared whenever the incident takes place. The actions
associated with the particular incident should always be taken under the consideration
of the senior management. If the scale is low then it can be delegated as required.
- The next step is associated with the development of response checklist that covers the
various responses taken for the incident which will act as the learning guide in the
future similar incidents.
- There are various essential activities within the organization that requires immediate
recovery once the incident occurs. For such incidents, recovery plans should always
be kept on standby.
- The next should be to summarize the equipment or tools that were required to
maintain the operations.
there is alternate option of transferring data. However, it should be done under the
supervision of knowledgeable IT security personnel.
Business Continuity Planning
The business continuity planning covers the team organization chart that has been shown in
the Appendix A. A business continuity team is accompanied by the business continuity team
leader. The diagram covers the basic business requirements covering the Information
Technology, Production Recovery Team, and the Support Team (Levy et al, 2016). There are
various aspects that are to be covered within the business continuity planning. The first aspect
is associated with understanding the impact through analysis which will include the recovery
time for business activities and IT. Given below is the plan for the business continuity:
- Actions checklist should be prepared whenever the incident takes place. The actions
associated with the particular incident should always be taken under the consideration
of the senior management. If the scale is low then it can be delegated as required.
- The next step is associated with the development of response checklist that covers the
various responses taken for the incident which will act as the learning guide in the
future similar incidents.
- There are various essential activities within the organization that requires immediate
recovery once the incident occurs. For such incidents, recovery plans should always
be kept on standby.
- The next should be to summarize the equipment or tools that were required to
maintain the operations.

- There are information systems that are essential for the functioning of the
organization. This covers entire software or hardware that was restored in the case of
incidents.
- The next step is to detail the staff members who are necessary to be present any form
of incident takes place.
- Furthermore, the availability of key contacts is suggested.
- The plan should cover the summary of the entire steps.
Disaster Recovery Planning
Given below is the disaster recovery planning for the organization that allow the information
system infrastructure to recover from the adverse conditions (Sahebjamnia et al, 2015):
- The first step in the disaster recovery planning is to identify and analyse the risks.
There are various attributes of risks. The Appendix B shows different risks attributes
such as predictability, scope, likelihood, impact, and others. Understanding the risks
on these parameters is likely to better plan for the risks.
- There are various weights (attributes) based on which the risks should be classified.
The major aspects for differentiation can be based on external risks, facility risks, data
systems risks, departmental risks, desk-level risks, and others.
- In the next stage, the risks should be assessed by placing values to the attributes from
step 1.
- The next step calls for assessing the impact of the disaster that is likely to be caused
as shown in the Appendix C such as power failure, failure of communication system,
loss of data, and others. This should be followed by understanding the downtime, its
cost and the dependencies of each affected areas on other things.
organization. This covers entire software or hardware that was restored in the case of
incidents.
- The next step is to detail the staff members who are necessary to be present any form
of incident takes place.
- Furthermore, the availability of key contacts is suggested.
- The plan should cover the summary of the entire steps.
Disaster Recovery Planning
Given below is the disaster recovery planning for the organization that allow the information
system infrastructure to recover from the adverse conditions (Sahebjamnia et al, 2015):
- The first step in the disaster recovery planning is to identify and analyse the risks.
There are various attributes of risks. The Appendix B shows different risks attributes
such as predictability, scope, likelihood, impact, and others. Understanding the risks
on these parameters is likely to better plan for the risks.
- There are various weights (attributes) based on which the risks should be classified.
The major aspects for differentiation can be based on external risks, facility risks, data
systems risks, departmental risks, desk-level risks, and others.
- In the next stage, the risks should be assessed by placing values to the attributes from
step 1.
- The next step calls for assessing the impact of the disaster that is likely to be caused
as shown in the Appendix C such as power failure, failure of communication system,
loss of data, and others. This should be followed by understanding the downtime, its
cost and the dependencies of each affected areas on other things.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

- The next step calls for understanding the mechanisms that can be applied to evaluate
the recovery options. The recovery options should be judged based on the cost to
incur, time of recovery, and ease with which the recovery will be complted.
- The final step is associated with constituting the committee that will look after the
disaster recovery from both the ends, that is, before and after the disaster and
implementation of recovery mechanisms.
Ethics
There are various ethical issues surrounding the use of an information system. Given below is
the guidance on some of the ethical issues (Friedman et al, 2013):
- One of the key ethical issues is the privacy challenges. The increased accessibility of
information technology has increased the sharing vast amount of personally
identifiable information from employees to the customers. In such case, it is the
responsibility of the organization that the information of the employees and the
customers are protected at any cost and must not be shared to external parties.
- The nondisclosure of the employee information is necessary to be abide by to ensure
that the faith of the employees’ increase in the organization.
- There should be clear demarcation between the information asset that is directly
related to the employees’ personal life and the organization should have no say in it
and the information that is of the organization and the organization is free to use and
access that information.
- It should be ensured that the organization does not engage in copyright infringement.
The reason is that the easy accessibility of the information generally converts into
copyright infringement if not adequately monitored.
the recovery options. The recovery options should be judged based on the cost to
incur, time of recovery, and ease with which the recovery will be complted.
- The final step is associated with constituting the committee that will look after the
disaster recovery from both the ends, that is, before and after the disaster and
implementation of recovery mechanisms.
Ethics
There are various ethical issues surrounding the use of an information system. Given below is
the guidance on some of the ethical issues (Friedman et al, 2013):
- One of the key ethical issues is the privacy challenges. The increased accessibility of
information technology has increased the sharing vast amount of personally
identifiable information from employees to the customers. In such case, it is the
responsibility of the organization that the information of the employees and the
customers are protected at any cost and must not be shared to external parties.
- The nondisclosure of the employee information is necessary to be abide by to ensure
that the faith of the employees’ increase in the organization.
- There should be clear demarcation between the information asset that is directly
related to the employees’ personal life and the organization should have no say in it
and the information that is of the organization and the organization is free to use and
access that information.
- It should be ensured that the organization does not engage in copyright infringement.
The reason is that the easy accessibility of the information generally converts into
copyright infringement if not adequately monitored.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security Architecture and Models
Security architecture for the information system within an organization is an important aspect
to ensure that the information security policy is successfully implemented or enforced. There
are three aspects of this, namely, confidentiality, integrity, and availability. The
confidentiality refers to ensuring that the users who are not authorized for the system should
not be able to access the data or information. The integrity refers to ensuring that the users
who are not authorized should not be able to temper with the data. The availability refers to
presence of ways that can prevent unauthorized users from preventing legal users from using
the system.
There are various aspects associated with the network protection such as hash tools,
transmission logging, retransmission control, and others that can be utilized. The generic
protection methods for the operating system are user identification and authentication,
complete mediation, audit, mandatory access control, audit log reduction, discretionary
access control, intrusion detection, and others (Nafi et al, 2013). These aspects will be the
part of security architecture. Appendix E shows the various layers within the architecture that
include network, hardware, OS, utilities and application programs. As per the security models
are concerned, Biba Model (Appendix D) will be applied. It shows the layer of secrecy
among the various level of information and data.
Security Management Practices
As briefly discussed earlier, the security management practices consists of three aspects
namely, confidentiality, integrity, and availability. The confidentiality is associated with
privacy aspects and restriction to access the system. This ensures that the important
information is accessible to those individual only who are authorized for the use of such
information. The integrity is associated with the accuracy and the reliability of the
Security architecture for the information system within an organization is an important aspect
to ensure that the information security policy is successfully implemented or enforced. There
are three aspects of this, namely, confidentiality, integrity, and availability. The
confidentiality refers to ensuring that the users who are not authorized for the system should
not be able to access the data or information. The integrity refers to ensuring that the users
who are not authorized should not be able to temper with the data. The availability refers to
presence of ways that can prevent unauthorized users from preventing legal users from using
the system.
There are various aspects associated with the network protection such as hash tools,
transmission logging, retransmission control, and others that can be utilized. The generic
protection methods for the operating system are user identification and authentication,
complete mediation, audit, mandatory access control, audit log reduction, discretionary
access control, intrusion detection, and others (Nafi et al, 2013). These aspects will be the
part of security architecture. Appendix E shows the various layers within the architecture that
include network, hardware, OS, utilities and application programs. As per the security models
are concerned, Biba Model (Appendix D) will be applied. It shows the layer of secrecy
among the various level of information and data.
Security Management Practices
As briefly discussed earlier, the security management practices consists of three aspects
namely, confidentiality, integrity, and availability. The confidentiality is associated with
privacy aspects and restriction to access the system. This ensures that the important
information is accessible to those individual only who are authorized for the use of such
information. The integrity is associated with the accuracy and the reliability of the

information (Sumra et al, 2015). This ensures that the information has not been tempered
with in any form or feature. The availability is associated with the availability of the
information to the concerned stakeholders when needed. The stakeholders can be customers,
suppliers, management, and others.
These three aspects are important as at present the almost all the information whether it is
related to the company asset or new associated business idea, everything is stored in the
electronic or written format. If such information get into the wrong individual, then it is very
likely that the future of the company will be jeopardized. The impact can be severe such as
loss of client, market share, fines from the government, and others.
The business continuity planning play major role in ensuring that the information is available
to the right individual and at the right time. The table in the Appendix F shows the three
aspects, their risks, controls and primary focus for the current organization.
Applications, Telecommunications and Network Security
The focus of this domain is towards the digital communication while considering the various
security aspects. There are various technology level implementations that can be done to
ensure that the security is increased and maintained for the future. Some of them are
mentioned below for the current organization and the sector:
- Virtual Private Networks: Use of virtual private network will nearly remove the
intrusion as it directly connects the remote user to the server using VPN. This method
is secure, reliable, scalable, and manageable (Gallo et al, 2015).
- Intrusion Detection Systems: It will be focused towards detecting and preparing logs
of the activities that are incorrect or different than the normal pattern. These are of
two types, namely, network based IDS and the Host based IDS.
with in any form or feature. The availability is associated with the availability of the
information to the concerned stakeholders when needed. The stakeholders can be customers,
suppliers, management, and others.
These three aspects are important as at present the almost all the information whether it is
related to the company asset or new associated business idea, everything is stored in the
electronic or written format. If such information get into the wrong individual, then it is very
likely that the future of the company will be jeopardized. The impact can be severe such as
loss of client, market share, fines from the government, and others.
The business continuity planning play major role in ensuring that the information is available
to the right individual and at the right time. The table in the Appendix F shows the three
aspects, their risks, controls and primary focus for the current organization.
Applications, Telecommunications and Network Security
The focus of this domain is towards the digital communication while considering the various
security aspects. There are various technology level implementations that can be done to
ensure that the security is increased and maintained for the future. Some of them are
mentioned below for the current organization and the sector:
- Virtual Private Networks: Use of virtual private network will nearly remove the
intrusion as it directly connects the remote user to the server using VPN. This method
is secure, reliable, scalable, and manageable (Gallo et al, 2015).
- Intrusion Detection Systems: It will be focused towards detecting and preparing logs
of the activities that are incorrect or different than the normal pattern. These are of
two types, namely, network based IDS and the Host based IDS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

- Firewalls: Firewall ensures that the flow of the traffic is controlled. Moreover, it
prevents the unauthorized entry into the system either to the network or from the
network.
prevents the unauthorized entry into the system either to the network or from the
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Friedman, B., Kahn Jr, P. H., Borning, A., & Huldtgren, A. (2013). Value sensitive design
and information systems. In Early engagement and new technologies: Opening up the
laboratory (pp. 55-95). Springer Netherlands.
Gallagher, C., McMenemy, D., & Poulter, A. (2015). Management of acceptable use of
computing facilities in the public library: avoiding a panoptic gaze?. Journal of
Documentation, 71(3), 572-590
Gallo, C., De Bonis, M., & Perilli, M. (2015). Virtual Private Networks. In Encyclopedia of
Information Science and Technology, Third Edition (pp. 6347-6356). IGI Global.
Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: a framework for
security policy compliance in organisations. European Journal of Information Systems, 18(2),
106-125.
Levy, J., Yu, P., & Prizzia, R. (2016). Economic Disruptions, Business Continuity Planning
and Disaster Forensic Analysis: The Hawaii Business Recovery Center (HIBRC) Project.
In Disaster Forensics (pp. 315-334). Springer International Publishing.
Nafi, K. W., Kar, T. S., Hoque, S. A., & Hashem, M. M. A. (2013). A newer user
authentication, file encryption and distributed server based cloud computing security
architecture. arXiv preprint arXiv:1303.0598.
Sahebjamnia, N., Torabi, S. A., & Mansouri, S. A. (2015). Integrated business continuity and
disaster recovery planning: Towards organizational resilience. European Journal of
Operational Research, 242(1), 261-273.
Friedman, B., Kahn Jr, P. H., Borning, A., & Huldtgren, A. (2013). Value sensitive design
and information systems. In Early engagement and new technologies: Opening up the
laboratory (pp. 55-95). Springer Netherlands.
Gallagher, C., McMenemy, D., & Poulter, A. (2015). Management of acceptable use of
computing facilities in the public library: avoiding a panoptic gaze?. Journal of
Documentation, 71(3), 572-590
Gallo, C., De Bonis, M., & Perilli, M. (2015). Virtual Private Networks. In Encyclopedia of
Information Science and Technology, Third Edition (pp. 6347-6356). IGI Global.
Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: a framework for
security policy compliance in organisations. European Journal of Information Systems, 18(2),
106-125.
Levy, J., Yu, P., & Prizzia, R. (2016). Economic Disruptions, Business Continuity Planning
and Disaster Forensic Analysis: The Hawaii Business Recovery Center (HIBRC) Project.
In Disaster Forensics (pp. 315-334). Springer International Publishing.
Nafi, K. W., Kar, T. S., Hoque, S. A., & Hashem, M. M. A. (2013). A newer user
authentication, file encryption and distributed server based cloud computing security
architecture. arXiv preprint arXiv:1303.0598.
Sahebjamnia, N., Torabi, S. A., & Mansouri, S. A. (2015). Integrated business continuity and
disaster recovery planning: Towards organizational resilience. European Journal of
Operational Research, 242(1), 261-273.
Sumra, I. A., Hasbullah, H. B., & AbManan, J. L. B. (2015). Attacks on security goals
(confidentiality, integrity, availability) in VANET: a survey. In Vehicular Ad-Hoc Networks
for Smart Cities (pp. 51-61). Springer Singapore.
Appendices
Appendix A: Business Continuity Team Organization Chart
(confidentiality, integrity, availability) in VANET: a survey. In Vehicular Ad-Hoc Networks
for Smart Cities (pp. 51-61). Springer Singapore.
Appendices
Appendix A: Business Continuity Team Organization Chart
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





