Security Policy Development and Management for My Health Record
VerifiedAdded on 2022/10/01
|16
|3468
|25
Report
AI Summary
This report provides a detailed analysis of the My Health Record (MHR) system, focusing on the development and management of its security policies. The report is divided into two parts: the first part discusses the introduction to the MHR system, the importance of security policies, planning for system access, and the development and management of these policies. The second part delves into potential security threats such as computer viruses, social engineering, Distributed Denial of Service (DDoS) attacks, and phishing attacks. The report emphasizes the need for robust cybersecurity measures, including data access controls, risk assessment, and the implementation of international frameworks like COBIT and ISO/IEC 27001. It highlights the critical role of security in protecting sensitive patient data, ensuring system integrity, and maintaining public trust. The report also addresses the challenges and potential risks associated with the MHR system and emphasizes the need for continuous monitoring and adaptation to mitigate these risks effectively.
Running Head: My Health Record Page 0 of 16
My Health Record
Report
Student name
My Health Record
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

My Health Record Page 1 of 16
Table of Contents
Part-I................................................................................................................................................2
Introduction......................................................................................................................................2
Security policy.................................................................................................................................2
Planning of Security Policy for System Access...........................................................................3
Development of Security Policy for System Access..................................................................4
Management of Security Policy for System Access....................................................................5
Conclusion.......................................................................................................................................5
Part-II...............................................................................................................................................7
Computer Viruses........................................................................................................................7
Social engineering........................................................................................................................7
Distributed Denial of Service.......................................................................................................8
Phishing attacks............................................................................................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11
Table of Contents
Part-I................................................................................................................................................2
Introduction......................................................................................................................................2
Security policy.................................................................................................................................2
Planning of Security Policy for System Access...........................................................................3
Development of Security Policy for System Access..................................................................4
Management of Security Policy for System Access....................................................................5
Conclusion.......................................................................................................................................5
Part-II...............................................................................................................................................7
Computer Viruses........................................................................................................................7
Social engineering........................................................................................................................7
Distributed Denial of Service.......................................................................................................8
Phishing attacks............................................................................................................................8
Conclusion.....................................................................................................................................10
References......................................................................................................................................11

My Health Record Page 2 of 16
Part-I
Introduction
The Australian government has decided to delete the personal heath storage system to
avoid data breaches and many bad impacts on patients and other people (Nott, 2018). The
Australian government has implemented centralized system to manage its various works in a
proper manner. In addition, the commonwealth government of Australia has provided various
systems to provide different services to Australians. Now, the commonwealth government will
provide My Health Record (MHR) system to secure all the personal details of a person with their
health records and treatment, which will be used for the treatment of those particular persons.
MHR will provide various benefits to the government as well as the Australians in their
treatment and emergency conditions at anywhere and anytime. This system has accessible by
only limited persons with a high level of security and privacy of data, as personal and health data
is highly sensitive and confidential. There are various advantages of a common health record
system. The commonwealth government wants to improve the security and privacy of the MHR
system using emerging technologies. It is a basic need for the MHR system. In addition, there are
some issues and challenges in the implementation of MHR system.
Security policy
The healthcare sector has adopted various technologies and innovations in their practice
to improve their efficiency and performance (Pai & Huang, 2011). MHR system will store all the
personal records of a patient, which will be related to their treatment and personal things. The
government should create security policies to secure personal and confidential data of people. It
will be a centralized system of the government. There are many security issues with a large
amount of data in the present era. The MHR system will collect different types of data, such as
name, mobile number, email ID, addresses, credit card details, treatment details, medical history,
and many others. Most of the countries have used online health records to improve the treatment
of a patient and other things, such as research, knowledge, and many more (Hsiao & Hing,
2012).
Part-I
Introduction
The Australian government has decided to delete the personal heath storage system to
avoid data breaches and many bad impacts on patients and other people (Nott, 2018). The
Australian government has implemented centralized system to manage its various works in a
proper manner. In addition, the commonwealth government of Australia has provided various
systems to provide different services to Australians. Now, the commonwealth government will
provide My Health Record (MHR) system to secure all the personal details of a person with their
health records and treatment, which will be used for the treatment of those particular persons.
MHR will provide various benefits to the government as well as the Australians in their
treatment and emergency conditions at anywhere and anytime. This system has accessible by
only limited persons with a high level of security and privacy of data, as personal and health data
is highly sensitive and confidential. There are various advantages of a common health record
system. The commonwealth government wants to improve the security and privacy of the MHR
system using emerging technologies. It is a basic need for the MHR system. In addition, there are
some issues and challenges in the implementation of MHR system.
Security policy
The healthcare sector has adopted various technologies and innovations in their practice
to improve their efficiency and performance (Pai & Huang, 2011). MHR system will store all the
personal records of a patient, which will be related to their treatment and personal things. The
government should create security policies to secure personal and confidential data of people. It
will be a centralized system of the government. There are many security issues with a large
amount of data in the present era. The MHR system will collect different types of data, such as
name, mobile number, email ID, addresses, credit card details, treatment details, medical history,
and many others. Most of the countries have used online health records to improve the treatment
of a patient and other things, such as research, knowledge, and many more (Hsiao & Hing,
2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
My Health Record Page 3 of 16
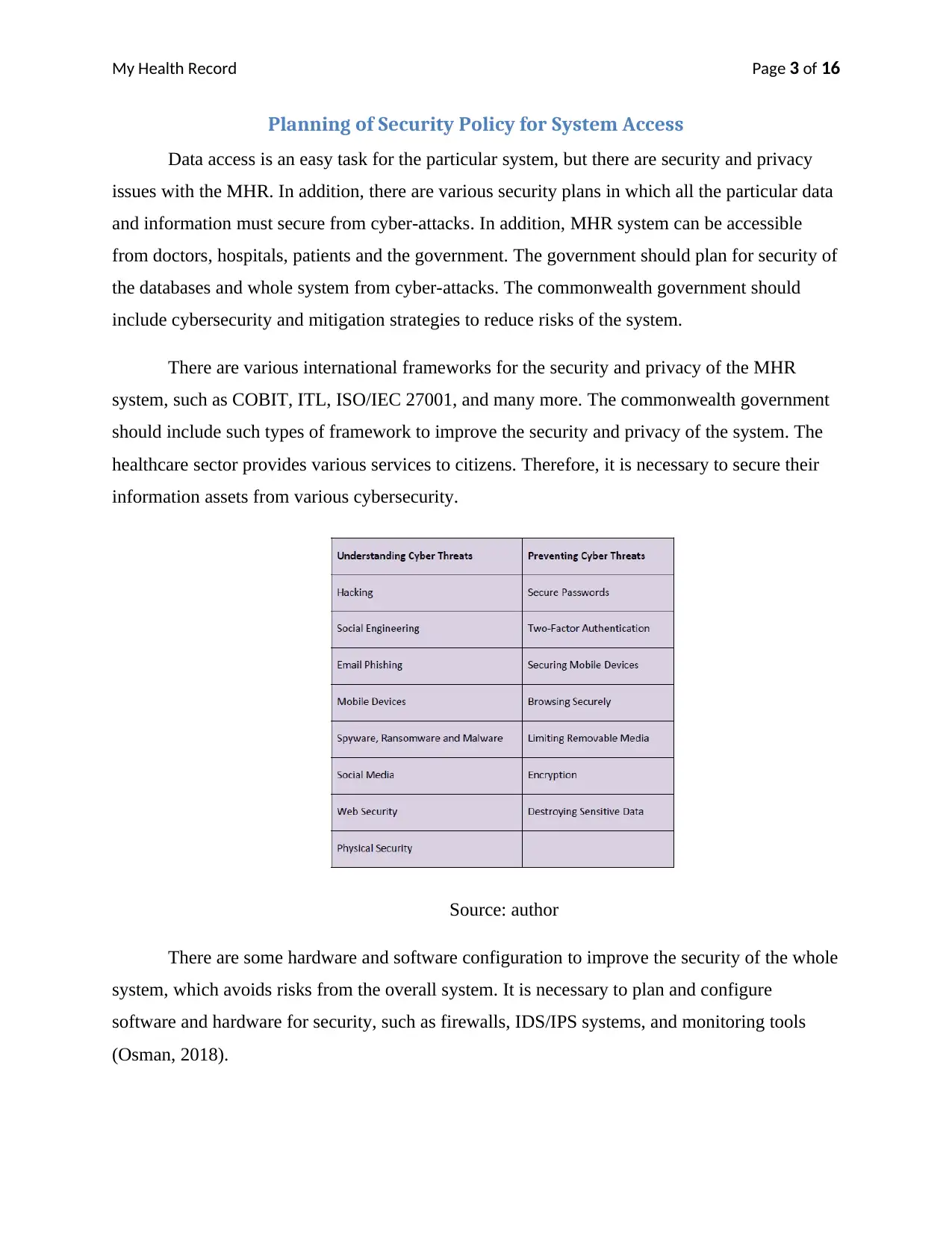
Planning of Security Policy for System Access
Data access is an easy task for the particular system, but there are security and privacy
issues with the MHR. In addition, there are various security plans in which all the particular data
and information must secure from cyber-attacks. In addition, MHR system can be accessible
from doctors, hospitals, patients and the government. The government should plan for security of
the databases and whole system from cyber-attacks. The commonwealth government should
include cybersecurity and mitigation strategies to reduce risks of the system.
There are various international frameworks for the security and privacy of the MHR
system, such as COBIT, ITL, ISO/IEC 27001, and many more. The commonwealth government
should include such types of framework to improve the security and privacy of the system. The
healthcare sector provides various services to citizens. Therefore, it is necessary to secure their
information assets from various cybersecurity.
Source: author
There are some hardware and software configuration to improve the security of the whole
system, which avoids risks from the overall system. It is necessary to plan and configure
software and hardware for security, such as firewalls, IDS/IPS systems, and monitoring tools
(Osman, 2018).
Planning of Security Policy for System Access
Data access is an easy task for the particular system, but there are security and privacy
issues with the MHR. In addition, there are various security plans in which all the particular data
and information must secure from cyber-attacks. In addition, MHR system can be accessible
from doctors, hospitals, patients and the government. The government should plan for security of
the databases and whole system from cyber-attacks. The commonwealth government should
include cybersecurity and mitigation strategies to reduce risks of the system.
There are various international frameworks for the security and privacy of the MHR
system, such as COBIT, ITL, ISO/IEC 27001, and many more. The commonwealth government
should include such types of framework to improve the security and privacy of the system. The
healthcare sector provides various services to citizens. Therefore, it is necessary to secure their
information assets from various cybersecurity.
Source: author
There are some hardware and software configuration to improve the security of the whole
system, which avoids risks from the overall system. It is necessary to plan and configure
software and hardware for security, such as firewalls, IDS/IPS systems, and monitoring tools
(Osman, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

My Health Record Page 4 of 16
In Australia, different companies have provided solutions for the electronic health care
system, which was not properly worked and the Australians have faced privacy and security
issues in the Electronic Health Record (EHR) system (Xu, Gao, Sorwar, & Croll, 2013).
The data access policy should cover all the internal and external risks of the systems and
its consequences on the system. There are some important factors of the data access policy,
which secure the system from unwanted and unauthorized access to the data. In addition, there
are some basic input and output sequences of the system, which can increase the risk of system.
Moreover, there are some basic needs to access control in the network and data centers
of the MHR system. All users have limited access according to their needs. In addition, every
user must secure their personal credentials from others to secure the overall system.
The commonwealth government has included various rules and regulations for the
security of the systems. It will work for all the systems. Security policy makes huge impact on
the IT security policy. In addition, secure assets are more reliable for the system, as those
systems have proper configuration of security and privacy (myhealthrecord.gov.au, 2019). The
secure MHR system is helpful in the various medical processes. An information system is useful
when it secures the data and information from others (Weiskopf & Weng, 2013).
Development of Security Policy for System Access
The data-access security policy must develop for the MHR system to provide security
and privacy for the large amount of data and information of Australians. In addition, there are
some basic needs for security in an online system. A system will face various security issues in
their internal and external processes. Therefore, it is necessary to develop system access security
policy to secure the system form outsides using proper controls and mitigation strategies.
The Australian government has started an electronic health system for storage and access
to the medical history of patients from anywhere and anytime. However, that system has failed
because of low security and privacy of the system (Xu, Gao, Sorwar, & Croll, 2013). It makes
huge impact on the faith of the people that their personal medical data has secured in the system,
which is necessary for each person. A security access security policy must include 3-way
handshake authentication to secure the connection from hackers. In addition, the policy should
include cryptography techniques for securing the internal and external sources of the system.
In Australia, different companies have provided solutions for the electronic health care
system, which was not properly worked and the Australians have faced privacy and security
issues in the Electronic Health Record (EHR) system (Xu, Gao, Sorwar, & Croll, 2013).
The data access policy should cover all the internal and external risks of the systems and
its consequences on the system. There are some important factors of the data access policy,
which secure the system from unwanted and unauthorized access to the data. In addition, there
are some basic input and output sequences of the system, which can increase the risk of system.
Moreover, there are some basic needs to access control in the network and data centers
of the MHR system. All users have limited access according to their needs. In addition, every
user must secure their personal credentials from others to secure the overall system.
The commonwealth government has included various rules and regulations for the
security of the systems. It will work for all the systems. Security policy makes huge impact on
the IT security policy. In addition, secure assets are more reliable for the system, as those
systems have proper configuration of security and privacy (myhealthrecord.gov.au, 2019). The
secure MHR system is helpful in the various medical processes. An information system is useful
when it secures the data and information from others (Weiskopf & Weng, 2013).
Development of Security Policy for System Access
The data-access security policy must develop for the MHR system to provide security
and privacy for the large amount of data and information of Australians. In addition, there are
some basic needs for security in an online system. A system will face various security issues in
their internal and external processes. Therefore, it is necessary to develop system access security
policy to secure the system form outsides using proper controls and mitigation strategies.
The Australian government has started an electronic health system for storage and access
to the medical history of patients from anywhere and anytime. However, that system has failed
because of low security and privacy of the system (Xu, Gao, Sorwar, & Croll, 2013). It makes
huge impact on the faith of the people that their personal medical data has secured in the system,
which is necessary for each person. A security access security policy must include 3-way
handshake authentication to secure the connection from hackers. In addition, the policy should
include cryptography techniques for securing the internal and external sources of the system.

My Health Record Page 5 of 16
Any person can access their personal records from anywhere as well as doctors can use the
history of a patient in their research and treatment.
The policy must include RFID devices and other hardware to secure them in a proper
manner. In addition, all the devices must secure from the cyber-attack and other ways (Wamba,
Anand, & Carter, 2013). In addition, online records have used for the emergency treatment of a
person. Therefore, the MHR system should access by the emergency department of all the
registered hospitals to know about the conditions. It will improve the results of the saving lives
of people in emergency cases (Romano & Stafford, 2011). It was founded that EHR systems
provide help into emergency cases and it has provided huge help to the research as well (Parente
& McCullough, 2009).
Management of Security Policy for System Access
Monitoring and control are necessary for MHR system to reduce various risks form the
internet and other mediums. It will provide many benefits to the organization as well as citizens.
However, lack of security can create some drawbacks because of the system (Menachemi &
Collum, 2011). In addition, MHR system is beneficial for people as well. The Australian Digital
Health Agency (ADHA) has taken responsibility for all the data and the organization has
provided authority to access the MHR system (myhealthrecord.gov.au, 2019).
In addition, the data warehouse has collected large amounts of data, which will provide
help to the research in the research field (Jensen, Jensen, & Brunak, 2012). According to chief
information officer, system access security policy must manage in a proper manner to secure the
online data and sensitive information (Palvia, Lowe, Nemati, & Jacks, 2012). Technology can
include in the system to provide more security, such as AI and machine learning (Pai & Huang,
2011).
Conclusion
It has concluded from the above plan to develop, and manage system access security
policy that MHR system should have security and privacy of the data and information of patients
and other people. Planning is necessary to develop a system access security policy and it
requires high level of management to improve the various things.
Any person can access their personal records from anywhere as well as doctors can use the
history of a patient in their research and treatment.
The policy must include RFID devices and other hardware to secure them in a proper
manner. In addition, all the devices must secure from the cyber-attack and other ways (Wamba,
Anand, & Carter, 2013). In addition, online records have used for the emergency treatment of a
person. Therefore, the MHR system should access by the emergency department of all the
registered hospitals to know about the conditions. It will improve the results of the saving lives
of people in emergency cases (Romano & Stafford, 2011). It was founded that EHR systems
provide help into emergency cases and it has provided huge help to the research as well (Parente
& McCullough, 2009).
Management of Security Policy for System Access
Monitoring and control are necessary for MHR system to reduce various risks form the
internet and other mediums. It will provide many benefits to the organization as well as citizens.
However, lack of security can create some drawbacks because of the system (Menachemi &
Collum, 2011). In addition, MHR system is beneficial for people as well. The Australian Digital
Health Agency (ADHA) has taken responsibility for all the data and the organization has
provided authority to access the MHR system (myhealthrecord.gov.au, 2019).
In addition, the data warehouse has collected large amounts of data, which will provide
help to the research in the research field (Jensen, Jensen, & Brunak, 2012). According to chief
information officer, system access security policy must manage in a proper manner to secure the
online data and sensitive information (Palvia, Lowe, Nemati, & Jacks, 2012). Technology can
include in the system to provide more security, such as AI and machine learning (Pai & Huang,
2011).
Conclusion
It has concluded from the above plan to develop, and manage system access security
policy that MHR system should have security and privacy of the data and information of patients
and other people. Planning is necessary to develop a system access security policy and it
requires high level of management to improve the various things.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

My Health Record Page 6 of 16
This report has provided various things to improve and implement the system access
policy for the MHR system. It will provide various controls for different risks. In addition, the
commonwealth government can include security policy to secure the data and information.
This report has provided various things to improve and implement the system access
policy for the MHR system. It will provide various controls for different risks. In addition, the
commonwealth government can include security policy to secure the data and information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

My Health Record Page 7 of 16
Part-II
HealthVault is a product of Microsoft for managing health records of people. The
Australian government has included various services for managing large amount of data of
people. Microsoft has provided various products and services related to medical fields as well as
other services. In addition, there are some basic need of the system to support security to the data
and information of people.
In addition, data mining has provided various types of advantages to learn more about the
people health records and their consequences (Koh & Tan, 2011). There are some consequences
of the system access risks, which areas:
1. Loss of integrity
2. Loss of data and information
3. Loss of availability
4. Downtime of the systems
5. File transfers
6. Loss of public trust
These are some risks of information assets for the MHR system, which areas:
Computer Viruses
There are various types of computer viruses, which can damage various things of a
system, such as data, images, software, and many others. Therefore, it is necessary to improve
the security of the healthcare systems (Jensen, Jensen, & Brunak, 2012). Viruses can damage a
system, which is using for the accessing the MHR. Thus, it is necessary to know about the
computer viruses and its impacts on the main MHR system.
Social engineering
It is huge risk for the MH system in which someone can take personal credential of a user
of MHR system. They can access the whole system using those credentials. Thus, personal
information must secure from the other people and do not share with others.
Part-II
HealthVault is a product of Microsoft for managing health records of people. The
Australian government has included various services for managing large amount of data of
people. Microsoft has provided various products and services related to medical fields as well as
other services. In addition, there are some basic need of the system to support security to the data
and information of people.
In addition, data mining has provided various types of advantages to learn more about the
people health records and their consequences (Koh & Tan, 2011). There are some consequences
of the system access risks, which areas:
1. Loss of integrity
2. Loss of data and information
3. Loss of availability
4. Downtime of the systems
5. File transfers
6. Loss of public trust
These are some risks of information assets for the MHR system, which areas:
Computer Viruses
There are various types of computer viruses, which can damage various things of a
system, such as data, images, software, and many others. Therefore, it is necessary to improve
the security of the healthcare systems (Jensen, Jensen, & Brunak, 2012). Viruses can damage a
system, which is using for the accessing the MHR. Thus, it is necessary to know about the
computer viruses and its impacts on the main MHR system.
Social engineering
It is huge risk for the MH system in which someone can take personal credential of a user
of MHR system. They can access the whole system using those credentials. Thus, personal
information must secure from the other people and do not share with others.

My Health Record Page 8 of 16
Distributed Denial of Service
It is a common attack in the large-scale data warehouses and systems, as it can stop all
types of connectivity and services of a system. Admin and users could not access the system,
which is a huge risk for the public data (Howard, et al., 2013).
Phishing attacks
There are various impacts of distributed and marge number of email in an account.
Therefore, it is a basic need to know about the spamming and spoofing. In addition, there are
some basic knowledge of accessing and using of online services. Thus, the government must
share basic processes of accessing the MHR system. MHR system should have proper
description of all the steps of using the system (Häyrinen, Saranto, & Nykänen, 2008).
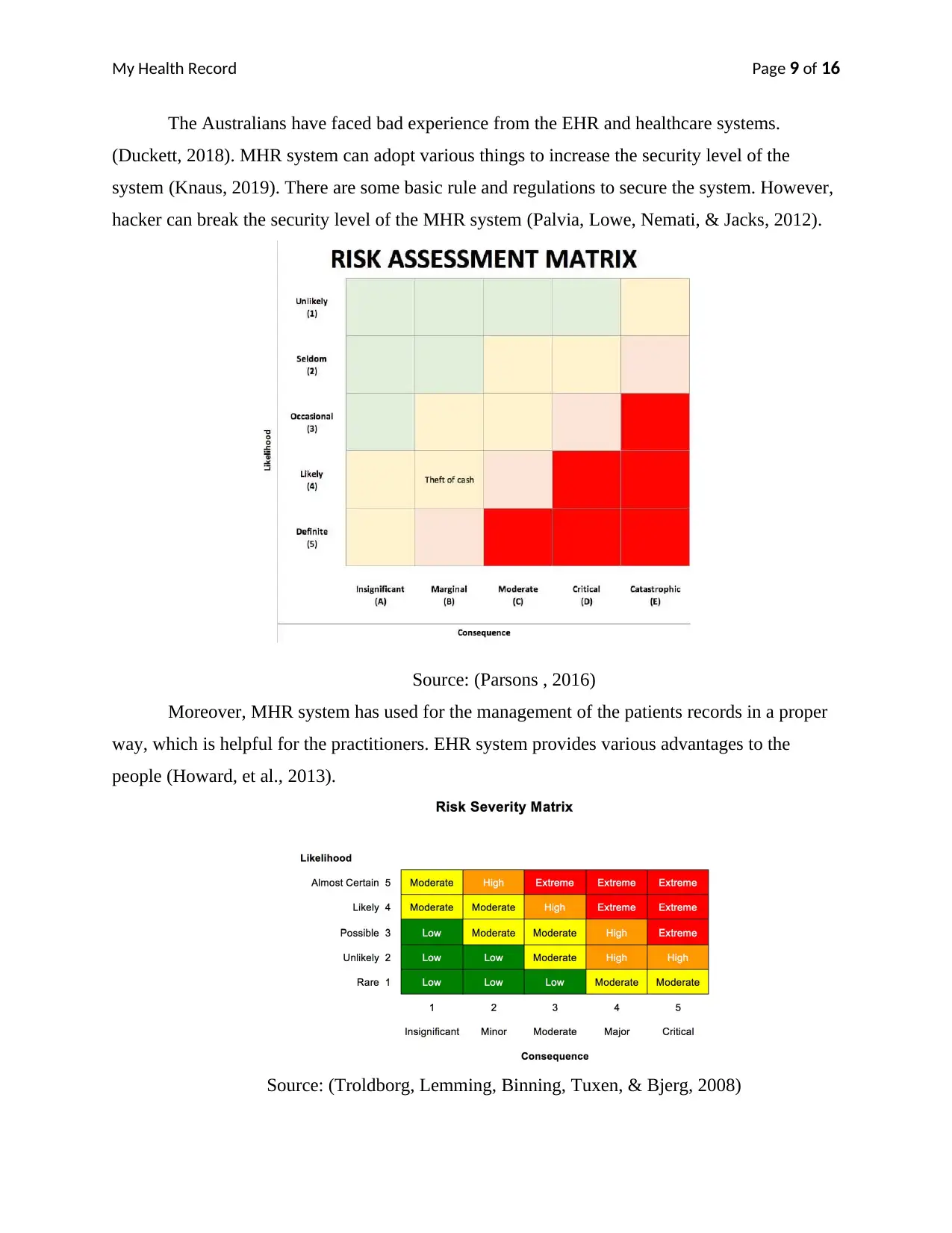
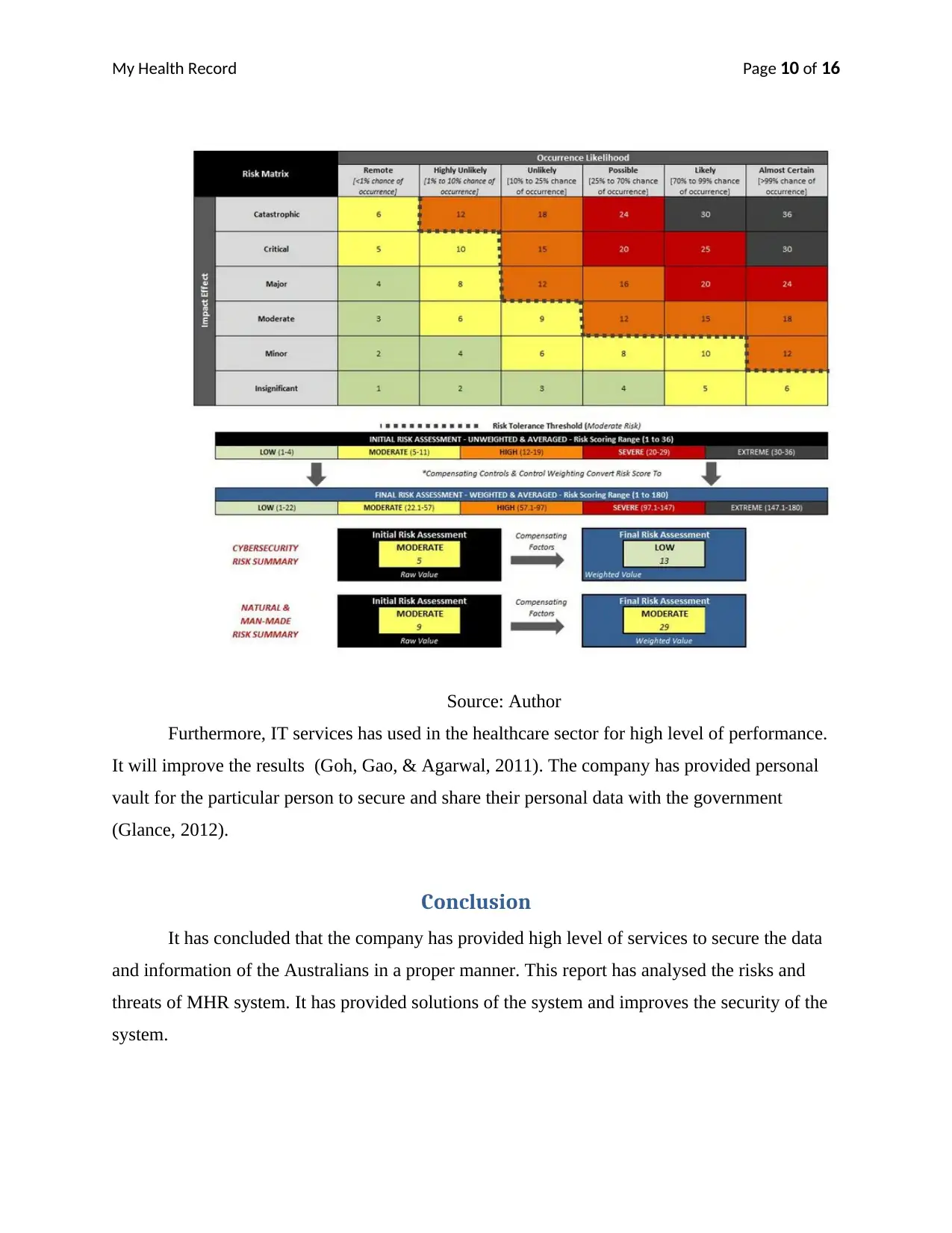
There are various methods for risk assessment, which is necessary for the MHR system.
Therefore, it is necessary to improve the security of the system. The below matrix is an example
of security analysis.
Source: (CERTIFICO, 2014)
Risk severity Matrix has provided the level of the risk. Thus, administrator can set the
controls according to the particular risk. MHR system is a common system for all the Australian.
Therefore, it must have proper security systems and access controls (Angst & Agarwal, 2009).
Electronic Health Records (EHRs) systems has used for the same work and it has failed because
of security reasons (Parente & McCullough, 2009). Thus, MHR system must include
cybersecurity to secure the whole system from cyber-attacks (Bogle, 2019). The Australians have
denied the EHR system because of various consequences, which has related to the security and
privacy (Charette, 2018).
Distributed Denial of Service
It is a common attack in the large-scale data warehouses and systems, as it can stop all
types of connectivity and services of a system. Admin and users could not access the system,
which is a huge risk for the public data (Howard, et al., 2013).
Phishing attacks
There are various impacts of distributed and marge number of email in an account.
Therefore, it is a basic need to know about the spamming and spoofing. In addition, there are
some basic knowledge of accessing and using of online services. Thus, the government must
share basic processes of accessing the MHR system. MHR system should have proper
description of all the steps of using the system (Häyrinen, Saranto, & Nykänen, 2008).
There are various methods for risk assessment, which is necessary for the MHR system.
Therefore, it is necessary to improve the security of the system. The below matrix is an example
of security analysis.
Source: (CERTIFICO, 2014)
Risk severity Matrix has provided the level of the risk. Thus, administrator can set the
controls according to the particular risk. MHR system is a common system for all the Australian.
Therefore, it must have proper security systems and access controls (Angst & Agarwal, 2009).
Electronic Health Records (EHRs) systems has used for the same work and it has failed because
of security reasons (Parente & McCullough, 2009). Thus, MHR system must include
cybersecurity to secure the whole system from cyber-attacks (Bogle, 2019). The Australians have
denied the EHR system because of various consequences, which has related to the security and
privacy (Charette, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
My Health Record Page 9 of 16
The Australians have faced bad experience from the EHR and healthcare systems.
(Duckett, 2018). MHR system can adopt various things to increase the security level of the
system (Knaus, 2019). There are some basic rule and regulations to secure the system. However,
hacker can break the security level of the MHR system (Palvia, Lowe, Nemati, & Jacks, 2012).
Source: (Parsons , 2016)
Moreover, MHR system has used for the management of the patients records in a proper
way, which is helpful for the practitioners. EHR system provides various advantages to the
people (Howard, et al., 2013).
Source: (Troldborg, Lemming, Binning, Tuxen, & Bjerg, 2008)
The Australians have faced bad experience from the EHR and healthcare systems.
(Duckett, 2018). MHR system can adopt various things to increase the security level of the
system (Knaus, 2019). There are some basic rule and regulations to secure the system. However,
hacker can break the security level of the MHR system (Palvia, Lowe, Nemati, & Jacks, 2012).
Source: (Parsons , 2016)
Moreover, MHR system has used for the management of the patients records in a proper
way, which is helpful for the practitioners. EHR system provides various advantages to the
people (Howard, et al., 2013).
Source: (Troldborg, Lemming, Binning, Tuxen, & Bjerg, 2008)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
My Health Record Page 10 of 16
Source: Author
Furthermore, IT services has used in the healthcare sector for high level of performance.
It will improve the results (Goh, Gao, & Agarwal, 2011). The company has provided personal
vault for the particular person to secure and share their personal data with the government
(Glance, 2012).
Conclusion
It has concluded that the company has provided high level of services to secure the data
and information of the Australians in a proper manner. This report has analysed the risks and
threats of MHR system. It has provided solutions of the system and improves the security of the
system.
Source: Author
Furthermore, IT services has used in the healthcare sector for high level of performance.
It will improve the results (Goh, Gao, & Agarwal, 2011). The company has provided personal
vault for the particular person to secure and share their personal data with the government
(Glance, 2012).
Conclusion
It has concluded that the company has provided high level of services to secure the data
and information of the Australians in a proper manner. This report has analysed the risks and
threats of MHR system. It has provided solutions of the system and improves the security of the
system.
My Health Record Page 11 of 16
This report has explained different treats of the MHR systems and its controls for
reducing the risks from the system. In addition, there is some basic system access security policy
to provide security of the system.
This report has explained different treats of the MHR systems and its controls for
reducing the risks from the system. In addition, there is some basic system access security policy
to provide security of the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





