University Security Policy and Risk Management Report - Assessment
VerifiedAdded on 2022/11/25
|14
|2587
|388
Report
AI Summary
This report presents a security policy and risk management analysis, focusing on the Commonwealth Government of Australia's 'My Health Record' system and a hypothetical XYZ software company. Part 1 explores access control for doctors, nurses, and patients, outlining purposes, policies, procedures, and managerial aspects. It emphasizes technological, administrative, and physical controls. Part 2 assesses risks within XYZ, including unauthorized database access, biometric system vulnerabilities, and inventory theft, and proposes mitigation strategies. The report includes a risk register, a risk assessment matrix, and references to support the analysis. The report covers various aspects of security policy, risk assessment, and mitigation techniques within the healthcare and IT sectors. This report provides a comprehensive analysis of security and risk management in different contexts.

Running head: SECURITY POLICY AND RISK MANAGEMENT
SECURITY POLICY AND RISK MANAGEMENT
Name of the Student:
Name of the University:
Author Note:
SECURITY POLICY AND RISK MANAGEMENT
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SECURITY POLICY AND RISK MANAGEMENT
Table of Contents
Assessment Part-1:-....................................................................................................................3
Introduction About the topic..................................................................................................3
Doctor.....................................................................................................................................3
Purpose...............................................................................................................................3
Policy..................................................................................................................................3
Procedure............................................................................................................................4
Managerial..........................................................................................................................4
Nurse......................................................................................................................................4
Purpose...............................................................................................................................4
Policy..................................................................................................................................5
Procedure............................................................................................................................5
Procedure............................................................................................................................5
Managerial..........................................................................................................................5
Patient.....................................................................................................................................6
Purpose...............................................................................................................................6
Policy..................................................................................................................................6
Procedure............................................................................................................................6
Managerial..........................................................................................................................6
Assessment Part-2:-....................................................................................................................7
Introduction of the organization.............................................................................................7
Discussion of Risk..................................................................................................................8
SECURITY POLICY AND RISK MANAGEMENT
Table of Contents
Assessment Part-1:-....................................................................................................................3
Introduction About the topic..................................................................................................3
Doctor.....................................................................................................................................3
Purpose...............................................................................................................................3
Policy..................................................................................................................................3
Procedure............................................................................................................................4
Managerial..........................................................................................................................4
Nurse......................................................................................................................................4
Purpose...............................................................................................................................4
Policy..................................................................................................................................5
Procedure............................................................................................................................5
Procedure............................................................................................................................5
Managerial..........................................................................................................................5
Patient.....................................................................................................................................6
Purpose...............................................................................................................................6
Policy..................................................................................................................................6
Procedure............................................................................................................................6
Managerial..........................................................................................................................6
Assessment Part-2:-....................................................................................................................7
Introduction of the organization.............................................................................................7
Discussion of Risk..................................................................................................................8

2
SECURITY POLICY AND RISK MANAGEMENT
Mitigation of Risk..................................................................................................................8
Residual Risk Assessment and Risk Register........................................................................9
Risk Assessment Matrix.......................................................................................................10
References................................................................................................................................11
SECURITY POLICY AND RISK MANAGEMENT
Mitigation of Risk..................................................................................................................8
Residual Risk Assessment and Risk Register........................................................................9
Risk Assessment Matrix.......................................................................................................10
References................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SECURITY POLICY AND RISK MANAGEMENT
Assessment Part-1:-
Introduction About the topic
Access control specifically refers to that measure of security, which is put in a proper
place to enforce a specific regulation upon the individuals that can view, utilize or have a
special access to that of a restricted environment. Access control carries the primary aim of
protecting a specific place or a restricted area within that of a particular software or in this
case specifically within an information system.
In addition to this, the specific procedure involves the creation or the planning related to that
of an effectively working measure of security within a specific portion within a software or
an information system to protect the data that shall not be visible or should not be made
visible to individual users of the mentioned information system (Nelson & Staggers, 2016).
Commonwealth Government of Australia proposed with the “My health Record” system that
shall have a specific amount of access control being imposed upon all the users of the system
specifically.
Doctor
Purpose
Purpose of the Doctor specifically tends to all of the activities such as the likes of
attending the patients from time to time whenever the patients visit the system for help.
Along with that asking of all the related documents belonging to the medical history of the
patient.
Policy
Every access control policy needs to have an integration of basic three aspects related to that
of the business security of “My Health Record” that has been proposed by the
SECURITY POLICY AND RISK MANAGEMENT
Assessment Part-1:-
Introduction About the topic
Access control specifically refers to that measure of security, which is put in a proper
place to enforce a specific regulation upon the individuals that can view, utilize or have a
special access to that of a restricted environment. Access control carries the primary aim of
protecting a specific place or a restricted area within that of a particular software or in this
case specifically within an information system.
In addition to this, the specific procedure involves the creation or the planning related to that
of an effectively working measure of security within a specific portion within a software or
an information system to protect the data that shall not be visible or should not be made
visible to individual users of the mentioned information system (Nelson & Staggers, 2016).
Commonwealth Government of Australia proposed with the “My health Record” system that
shall have a specific amount of access control being imposed upon all the users of the system
specifically.
Doctor
Purpose
Purpose of the Doctor specifically tends to all of the activities such as the likes of
attending the patients from time to time whenever the patients visit the system for help.
Along with that asking of all the related documents belonging to the medical history of the
patient.
Policy
Every access control policy needs to have an integration of basic three aspects related to that
of the business security of “My Health Record” that has been proposed by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SECURITY POLICY AND RISK MANAGEMENT
Commonwealth Government of Australia in relation to the doctors (Gordon, Fairhall &
Landman, 2017). These three aspects are namely,
Technological
Administrative
Physical control of access
Procedure
However, each of the mentioned aspect carries some or the other implications along with the
inclusion of physically accessible controls that are functional. When the planning for the
creation of the specific access plan is being done for the “My Health Record”, the initial step
shall be considering of all the aspects along with the development of all the areas, which are
vulnerable to that of trespassing instead of kept under the tag of restricted access (Bhuyan et
al., 2017). Considered in this case, some of the already existing information systems carry
alongside far greater risks relying from the areas of internal threats such as the employees of
the organization leading onto leakage of sensitive information belonging to that of the
customers in return for money.
Managerial
A smaller organization however can be relied upon the power from a single existent
source having included all of the doctors present within the working of the system. However,
a bigger company such as the Commonwealth Government of Australia is in dire need of
bigger sources with the provision of bigger amount of energy as a part of creating as well as
planning of the access control policy.
SECURITY POLICY AND RISK MANAGEMENT
Commonwealth Government of Australia in relation to the doctors (Gordon, Fairhall &
Landman, 2017). These three aspects are namely,
Technological
Administrative
Physical control of access
Procedure
However, each of the mentioned aspect carries some or the other implications along with the
inclusion of physically accessible controls that are functional. When the planning for the
creation of the specific access plan is being done for the “My Health Record”, the initial step
shall be considering of all the aspects along with the development of all the areas, which are
vulnerable to that of trespassing instead of kept under the tag of restricted access (Bhuyan et
al., 2017). Considered in this case, some of the already existing information systems carry
alongside far greater risks relying from the areas of internal threats such as the employees of
the organization leading onto leakage of sensitive information belonging to that of the
customers in return for money.
Managerial
A smaller organization however can be relied upon the power from a single existent
source having included all of the doctors present within the working of the system. However,
a bigger company such as the Commonwealth Government of Australia is in dire need of
bigger sources with the provision of bigger amount of energy as a part of creating as well as
planning of the access control policy.

5
SECURITY POLICY AND RISK MANAGEMENT
Nurse
Purpose
Basic purpose of the Nurses present within the Commonwealth Government of
Australia have the basic responsibility of provisioning all the doctors with all of the
information related to all the patients visiting the information system to seek for medical
help. Nurses will maintain all the communication, which takes place between the patient as
well as the doctor.
Policy
Development procedure of the System Access in terms of the security policy shall be done by
taking into consideration all of the existing vulnerabilities related to that of the access points
having a major effect every time any single access point gets barged across (Hassan et al.,
2017). In a single nutshell, having developed an effective Access control point is setting up
the measures related to that of the security at the specifically mentioned critical points, which
carry the major amount of vulnerability in relation to security.
Procedure
Implementation of the security measures to put a control upon the unrestricted flow of work
for the provisioned users as well as to place a prevention upon the unauthorized individual
users from having found a leak within the existing information system of “My Health
Record” belonging to the Commonwealth Government of Australia. Herein, the sources
might be the nurses since they are the bridge of communication between doctors and the
existing patients within the system.
SECURITY POLICY AND RISK MANAGEMENT
Nurse
Purpose
Basic purpose of the Nurses present within the Commonwealth Government of
Australia have the basic responsibility of provisioning all the doctors with all of the
information related to all the patients visiting the information system to seek for medical
help. Nurses will maintain all the communication, which takes place between the patient as
well as the doctor.
Policy
Development procedure of the System Access in terms of the security policy shall be done by
taking into consideration all of the existing vulnerabilities related to that of the access points
having a major effect every time any single access point gets barged across (Hassan et al.,
2017). In a single nutshell, having developed an effective Access control point is setting up
the measures related to that of the security at the specifically mentioned critical points, which
carry the major amount of vulnerability in relation to security.
Procedure
Implementation of the security measures to put a control upon the unrestricted flow of work
for the provisioned users as well as to place a prevention upon the unauthorized individual
users from having found a leak within the existing information system of “My Health
Record” belonging to the Commonwealth Government of Australia. Herein, the sources
might be the nurses since they are the bridge of communication between doctors and the
existing patients within the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SECURITY POLICY AND RISK MANAGEMENT
Procedure
Particular work upon the physical control of access of the nurses has to be
concentrated in relation to the physical protection of the information along with the inclusion
of all the existing patients within the system (Sadgrove, 2016). Physical Control of Access
consists of the primary stage of identifying the specific network along with that of imposing
the control over the access from the networks, which do not have the credentials to access the
specific information system of the Commonwealth Government of Australia given a name,
“My Health Record”.
Managerial
Definition related to that of the data sensitivity levels as well as the assigning of
appropriate clearance of levels to that of the nurses, which consists of the access credentials
lying with them respectively to the patients seeking help from the doctors (Wager, Lee &
Glaser, 2017). Usage of special spaces within the definition of the Access related control plan
puts forward certain criteria for the setting of specific passwords along with the specifying of
certain technical aspects belonging to that of the wiring along with that of the existing routers
as well as the permission to that of the access control belonging to individual users.
Patient
Purpose
Purpose of the patient specifically relies with the fact that of having the primary
motive of seeking with the medical help whenever there arises the situations of emergency in
relation to their health.
Policy
All of the policies in regard to the patients shall be taken into consideration to carry
out a proper management of the software, in turn the information system that has been
SECURITY POLICY AND RISK MANAGEMENT
Procedure
Particular work upon the physical control of access of the nurses has to be
concentrated in relation to the physical protection of the information along with the inclusion
of all the existing patients within the system (Sadgrove, 2016). Physical Control of Access
consists of the primary stage of identifying the specific network along with that of imposing
the control over the access from the networks, which do not have the credentials to access the
specific information system of the Commonwealth Government of Australia given a name,
“My Health Record”.
Managerial
Definition related to that of the data sensitivity levels as well as the assigning of
appropriate clearance of levels to that of the nurses, which consists of the access credentials
lying with them respectively to the patients seeking help from the doctors (Wager, Lee &
Glaser, 2017). Usage of special spaces within the definition of the Access related control plan
puts forward certain criteria for the setting of specific passwords along with the specifying of
certain technical aspects belonging to that of the wiring along with that of the existing routers
as well as the permission to that of the access control belonging to individual users.
Patient
Purpose
Purpose of the patient specifically relies with the fact that of having the primary
motive of seeking with the medical help whenever there arises the situations of emergency in
relation to their health.
Policy
All of the policies in regard to the patients shall be taken into consideration to carry
out a proper management of the software, in turn the information system that has been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SECURITY POLICY AND RISK MANAGEMENT
proposed by the Commonwealth Government of Australia to provision all the patients with a
beneficiary support in maintenance of individual health relating to circumstances of medical
aid (Allen, 2017).
Procedure
Procedures belonging to the working of system in relation to the patients seeking
medical aid from the doctors present as well as associated with the “My Health Record”
system (Kliem & Ludin, 2019). The patients shall approach the information system related to
application following the procedure as mentioned within the guidelines for the patients.
Managerial
Management related to that of the System Access belonging to the policy of security
strictly puts forward the particular procedure of managing all of the activities that has been
taking place within the information system of “My Health Record”, which consists of
vulnerabilities within the field of security as well as leakage of sensitive information of the
patient.
Assessment Part-2:-
Introduction of the organization
XYZ software company is an organization utilizing the presence of information
systems for a very long time, having implemented all of the technology related to that of the
information and technology in every single sector of the activities that are being carried out
within the organization. This company specifically utilizes the role of information systems to
have a faster as well as an accurate reporting towards the management of all the sensitive
information related to that of the customers taking their service (Bengtsson, Borg & Rhinard,
2018). XYZ organization specifically manufactures mobile phones for the people having
installed all the major features along with the inclusion of the latest technology within their
SECURITY POLICY AND RISK MANAGEMENT
proposed by the Commonwealth Government of Australia to provision all the patients with a
beneficiary support in maintenance of individual health relating to circumstances of medical
aid (Allen, 2017).
Procedure
Procedures belonging to the working of system in relation to the patients seeking
medical aid from the doctors present as well as associated with the “My Health Record”
system (Kliem & Ludin, 2019). The patients shall approach the information system related to
application following the procedure as mentioned within the guidelines for the patients.
Managerial
Management related to that of the System Access belonging to the policy of security
strictly puts forward the particular procedure of managing all of the activities that has been
taking place within the information system of “My Health Record”, which consists of
vulnerabilities within the field of security as well as leakage of sensitive information of the
patient.
Assessment Part-2:-
Introduction of the organization
XYZ software company is an organization utilizing the presence of information
systems for a very long time, having implemented all of the technology related to that of the
information and technology in every single sector of the activities that are being carried out
within the organization. This company specifically utilizes the role of information systems to
have a faster as well as an accurate reporting towards the management of all the sensitive
information related to that of the customers taking their service (Bengtsson, Borg & Rhinard,
2018). XYZ organization specifically manufactures mobile phones for the people having
installed all the major features along with the inclusion of the latest technology within their

8
SECURITY POLICY AND RISK MANAGEMENT
products to serve their customers with all of the latest technology having a presence within
the modern world. This company utilizes the information system starting from the start of the
day till the end of the day for all of the employees working within the organization to serve
the customers of the company in the best way that is possible. Starting with the attendance of
the employees going in and coming out of the organization with the help of biometrics to the
maintenance of the digital database with protection and privacy of all the sensitive
information that is linked with the customers of the organization. To handle the inventory
consisting of all the raw materials required for the company in manufacturing the physical
part of the mobiles with the help of information and technology as well as the related security
measures (Yüksel, Küpçü & Özkasap, 2017). Monitoring as well as a keeping a track upon
the orders and the delivery of the orders related to that of the customers is done with the help
of a separate digital database.
Discussion of Risk
The primary risks associated with the IT systems existing within the XYZ
organization are the major risks, which need to be paid severe attention to be eradicated to
avoid circumstances leading to the hampering of the activities being carried out within the
business proceedings of this organization (Martínez-Pérez, De La Torre-Díez & López-
Coronado, 2015). These are,
Unauthorized access within the database of the organization, which contains all the
sensitive information related to the customers of the XYZ Company.
Security issues related to the biometric system of the organization monitoring the
attendance as well as the in and out times of the employees.
Barging in and taking out raw materials, or unordered mobiles from the inventory
despite the presence of the sensors at the gate of the inventory keeping a check upon
the entry as well as the exit of the materials (Peltier, 2016).
SECURITY POLICY AND RISK MANAGEMENT
products to serve their customers with all of the latest technology having a presence within
the modern world. This company utilizes the information system starting from the start of the
day till the end of the day for all of the employees working within the organization to serve
the customers of the company in the best way that is possible. Starting with the attendance of
the employees going in and coming out of the organization with the help of biometrics to the
maintenance of the digital database with protection and privacy of all the sensitive
information that is linked with the customers of the organization. To handle the inventory
consisting of all the raw materials required for the company in manufacturing the physical
part of the mobiles with the help of information and technology as well as the related security
measures (Yüksel, Küpçü & Özkasap, 2017). Monitoring as well as a keeping a track upon
the orders and the delivery of the orders related to that of the customers is done with the help
of a separate digital database.
Discussion of Risk
The primary risks associated with the IT systems existing within the XYZ
organization are the major risks, which need to be paid severe attention to be eradicated to
avoid circumstances leading to the hampering of the activities being carried out within the
business proceedings of this organization (Martínez-Pérez, De La Torre-Díez & López-
Coronado, 2015). These are,
Unauthorized access within the database of the organization, which contains all the
sensitive information related to the customers of the XYZ Company.
Security issues related to the biometric system of the organization monitoring the
attendance as well as the in and out times of the employees.
Barging in and taking out raw materials, or unordered mobiles from the inventory
despite the presence of the sensors at the gate of the inventory keeping a check upon
the entry as well as the exit of the materials (Peltier, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
SECURITY POLICY AND RISK MANAGEMENT
Mitigation of Risk
All of the above-mentioned risk relying within the XYZ Company can be mitigated
by a single procedure of installing a well-built information system within the organization
abiding with all of the methods placed forward by the information and technology systems.
Having a proper security as well as monitoring upon the central database of the organization
containing all of the information related to all the customers of the company (Mehraeen,
Ayatollahi & Ahmadi, 2016). Secondly, maintenance of all the biometric with proper
software that shall be updated on a weekly basis in order to lie with the assurance of no hacks
taking place within the system using which an employee can make its presence marked
instead of being really present inside the office premise (Laudon & Laudon, 2016). Lastly,
stealing of materials from the inventory can be prevented by upgrading the security measures
present at the entry and exit of the inventory warehouse as well as inside the warehouse
premise.
Residual Risk Assessment and Risk Register
No. Risks Description Likelihood Impact Severity Mitigation Technique
1. Unauthorized access
within the central
database.
VH H H Having proper measures
of security control in
relation to the access to
only people having the
credentials.
2. Illegal usage of the
biometric system.
M H M Better usage of software
for the avoidance of
such circumstances
arising, which can be
utilized by the
SECURITY POLICY AND RISK MANAGEMENT
Mitigation of Risk
All of the above-mentioned risk relying within the XYZ Company can be mitigated
by a single procedure of installing a well-built information system within the organization
abiding with all of the methods placed forward by the information and technology systems.
Having a proper security as well as monitoring upon the central database of the organization
containing all of the information related to all the customers of the company (Mehraeen,
Ayatollahi & Ahmadi, 2016). Secondly, maintenance of all the biometric with proper
software that shall be updated on a weekly basis in order to lie with the assurance of no hacks
taking place within the system using which an employee can make its presence marked
instead of being really present inside the office premise (Laudon & Laudon, 2016). Lastly,
stealing of materials from the inventory can be prevented by upgrading the security measures
present at the entry and exit of the inventory warehouse as well as inside the warehouse
premise.
Residual Risk Assessment and Risk Register
No. Risks Description Likelihood Impact Severity Mitigation Technique
1. Unauthorized access
within the central
database.
VH H H Having proper measures
of security control in
relation to the access to
only people having the
credentials.
2. Illegal usage of the
biometric system.
M H M Better usage of software
for the avoidance of
such circumstances
arising, which can be
utilized by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
SECURITY POLICY AND RISK MANAGEMENT
employees to mark their
presence without the
actual present within the
office premise.
3. Barging in and
stealing of goods
from the inventory
warehouse.
M VH H Installation of much
more secure security
measures at the entry as
well as exit of the
warehouse for the
avoidance of getting
stolen or robbed.
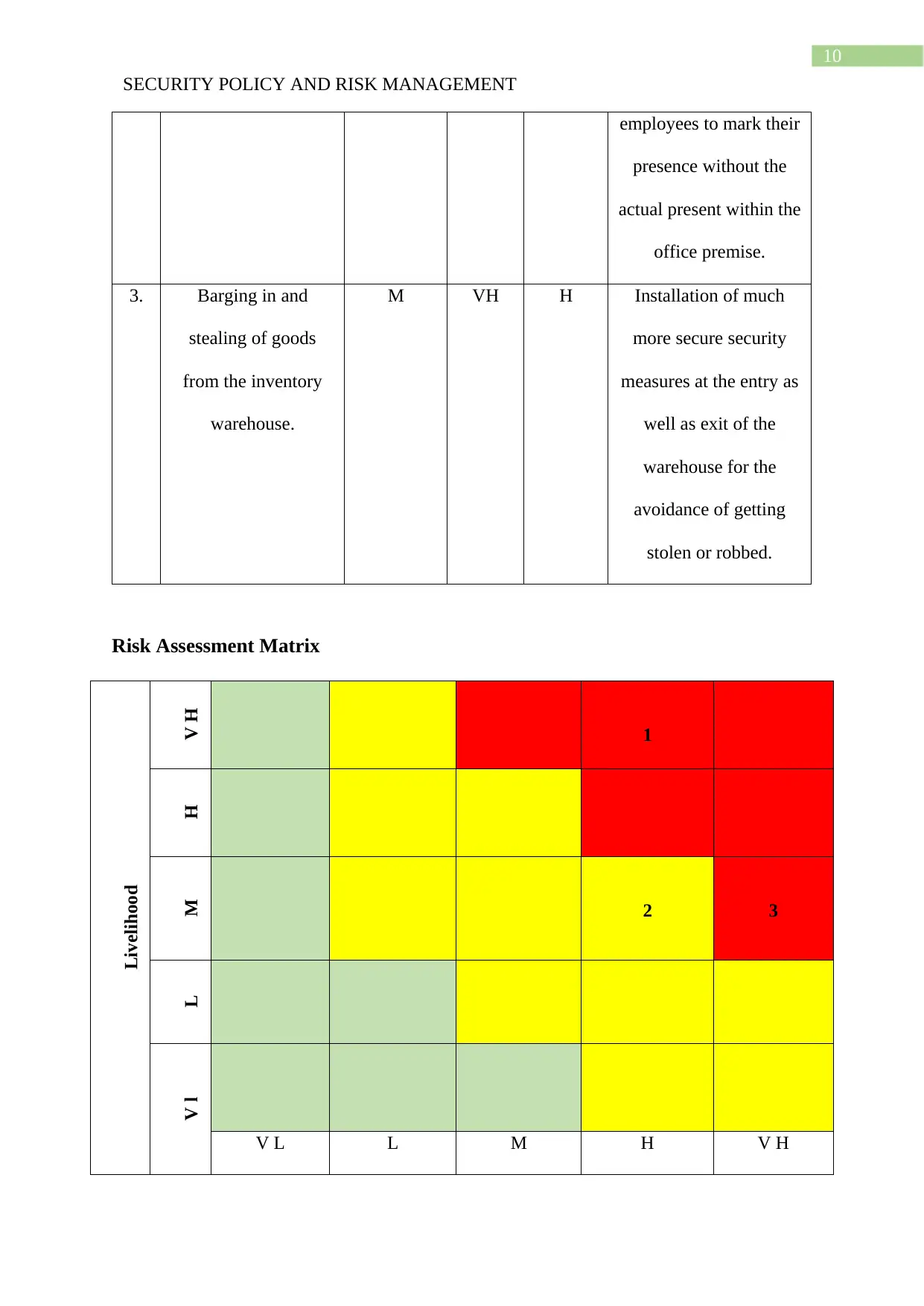
Risk Assessment Matrix
Livelihood
V H
1
HM 2 3
LV l
V L L M H V H
SECURITY POLICY AND RISK MANAGEMENT
employees to mark their
presence without the
actual present within the
office premise.
3. Barging in and
stealing of goods
from the inventory
warehouse.
M VH H Installation of much
more secure security
measures at the entry as
well as exit of the
warehouse for the
avoidance of getting
stolen or robbed.
Risk Assessment Matrix
Livelihood
V H
1
HM 2 3
LV l
V L L M H V H

11
SECURITY POLICY AND RISK MANAGEMENT
Impact
SECURITY POLICY AND RISK MANAGEMENT
Impact
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





