Security and Privacy Issues in Cloud Computing: A Comprehensive Report
VerifiedAdded on 2019/11/08
|11
|2435
|252
Report
AI Summary
This report comprehensively examines the security and privacy challenges associated with cloud computing. It begins by introducing cloud computing technologies like IaaS, SaaS, and PaaS, and then delves into the various challenges organizations face, including service provisioning, control, and transparency. The report highlights critical issues such as data breaches, insider threats, malware injection, user control, and the loss of legal protections. It also discusses the impact of insecure APIs, abuse of cloud services, shared vulnerabilities, and data loss. The report concludes by emphasizing the importance of strong cybersecurity measures for both organizations and cloud service providers to protect sensitive data, and recommends that organizations embrace cloud computing while mitigating security risks. The report is available on Desklib, a platform providing AI-based study tools for students.

Running head: SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Security and Privacy Issues in Cloud Computing
Name of the Student
Name of the University
Author Note
Security and Privacy Issues in Cloud Computing
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Table of Contents
Introduction......................................................................................................................................1
Cloud Computing.............................................................................................................................2
Challenges........................................................................................................................................2
Problems......................................................................................................................................3
Relevant Technologies and Applications....................................................................................3
Issues................................................................................................................................................4
Security Issues.............................................................................................................................4
Privacy Issues..............................................................................................................................5
Important Issues...............................................................................................................................5
Impact of the Issues.........................................................................................................................6
Results..............................................................................................................................................7
Conclusion.......................................................................................................................................7
References:......................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................1
Cloud Computing.............................................................................................................................2
Challenges........................................................................................................................................2
Problems......................................................................................................................................3
Relevant Technologies and Applications....................................................................................3
Issues................................................................................................................................................4
Security Issues.............................................................................................................................4
Privacy Issues..............................................................................................................................5
Important Issues...............................................................................................................................5
Impact of the Issues.........................................................................................................................6
Results..............................................................................................................................................7
Conclusion.......................................................................................................................................7
References:......................................................................................................................................9

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Introduction
The aim of this report is to put emphasis on the privacy and security issues that are
related to the cloud computing adoption. This report focuses on severe privacy and security
issues, including the hidden issues that could seriously affect the organization. This report also
focuses on the technologies of cloud computing and their application in an organization. Cloud
computing is a technique to use cloud based services that are generally offered by the third party.
IaaS, SaaS, and PaaS are the technologies of cloud computing (Zissis & Lekkas, 2012).
Cloud Computing
There are several challenges and problems related to the cloud computing adoption as explained
below:
Challenges
There are several challenges in cloud computing, some major challenges can be stated as:
Efficiency of the service provisioning is the top most challenge in cloud computing that
includes creation of scalable architectures for making this new implementation successful. Usage
of development tools and components, flexibility, and resource management, and availability of
services are the objectives under this challenge (Rong, Nguyen & Jaatun, 2013). Another
challenge in cloud computing is the Effectiveness of Service control and usage, which includes
control over the services by the users (any organization or an individual), liability, and
government and escalation mechanism. The third challenges id the transparency of service
billing and delivery, in which location and data process should be well explained, monitoring
Introduction
The aim of this report is to put emphasis on the privacy and security issues that are
related to the cloud computing adoption. This report focuses on severe privacy and security
issues, including the hidden issues that could seriously affect the organization. This report also
focuses on the technologies of cloud computing and their application in an organization. Cloud
computing is a technique to use cloud based services that are generally offered by the third party.
IaaS, SaaS, and PaaS are the technologies of cloud computing (Zissis & Lekkas, 2012).
Cloud Computing
There are several challenges and problems related to the cloud computing adoption as explained
below:
Challenges
There are several challenges in cloud computing, some major challenges can be stated as:
Efficiency of the service provisioning is the top most challenge in cloud computing that
includes creation of scalable architectures for making this new implementation successful. Usage
of development tools and components, flexibility, and resource management, and availability of
services are the objectives under this challenge (Rong, Nguyen & Jaatun, 2013). Another
challenge in cloud computing is the Effectiveness of Service control and usage, which includes
control over the services by the users (any organization or an individual), liability, and
government and escalation mechanism. The third challenges id the transparency of service
billing and delivery, in which location and data process should be well explained, monitoring
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
SLAs and quality assurance, and license management (Schewe et al., 2012). Information
Security and data privacy is the most concerned challenge for this implementation. Extending
this there are several other challenges like Portability between providers, interoperability within
the system, fair competition and Compliance with the regulatory requirements.
Problems
Lack of standard can be stated as the underlying problem beneath the challenges
explained above. Very less efforts had been made till now, for defining the standards for the
cloud computing. In order to solve these issues about what needs to happen, is service providers,
government, technology companies, and customers should join together and make a concerted
effort in order to adopt and develop industry-wide standards for the Cloud (Chen & Zhao, 2012).
This should also include all the inter-organizational stakeholders.
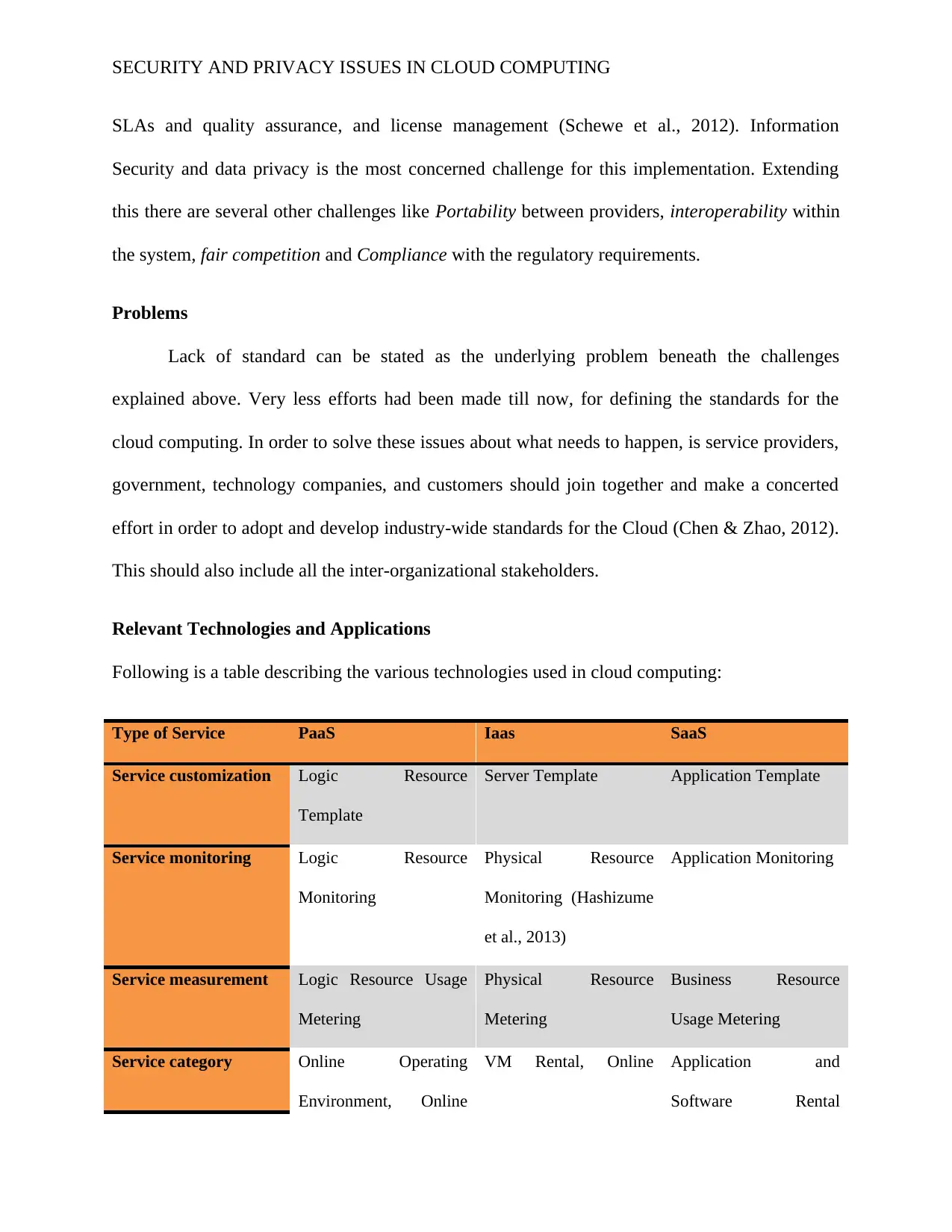
Relevant Technologies and Applications
Following is a table describing the various technologies used in cloud computing:
Type of Service PaaS Iaas SaaS
Service customization Logic Resource
Template
Server Template Application Template
Service monitoring Logic Resource
Monitoring
Physical Resource
Monitoring (Hashizume
et al., 2013)
Application Monitoring
Service measurement Logic Resource Usage
Metering
Physical Resource
Metering
Business Resource
Usage Metering
Service category Online Operating
Environment, Online
VM Rental, Online Application and
Software Rental
SLAs and quality assurance, and license management (Schewe et al., 2012). Information
Security and data privacy is the most concerned challenge for this implementation. Extending
this there are several other challenges like Portability between providers, interoperability within
the system, fair competition and Compliance with the regulatory requirements.
Problems
Lack of standard can be stated as the underlying problem beneath the challenges
explained above. Very less efforts had been made till now, for defining the standards for the
cloud computing. In order to solve these issues about what needs to happen, is service providers,
government, technology companies, and customers should join together and make a concerted
effort in order to adopt and develop industry-wide standards for the Cloud (Chen & Zhao, 2012).
This should also include all the inter-organizational stakeholders.
Relevant Technologies and Applications
Following is a table describing the various technologies used in cloud computing:
Type of Service PaaS Iaas SaaS
Service customization Logic Resource
Template
Server Template Application Template
Service monitoring Logic Resource
Monitoring
Physical Resource
Monitoring (Hashizume
et al., 2013)
Application Monitoring
Service measurement Logic Resource Usage
Metering
Physical Resource
Metering
Business Resource
Usage Metering
Service category Online Operating
Environment, Online
VM Rental, Online Application and
Software Rental
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Database, Online
Message
Storage (Garrison, Kim &
Wakefield, 2012)
Service level
Management
Dynamic Orchestration
of Logic Resources
Dynamic Orchestration
of Physical Resources
Dynamic Orchestration
of Application
Cloud computing is a very new and innovative model for providing IT services and
business. IaaS, PaaS and SaaS are the three levels of cloud computing service that can cover a
wide range of services. Besides the service delivery model and the computing service there are
other applications of cloud computing, which can be listed as: firstly, storage infrastructure,
software application, various models such as data, programming model and many more
(O’Driscoll, Daugelaite & Sleator, 2013).
Issues
There are several issues related to the privacy and security of the information that is migrating
into cloud computing, which can be categorized as:
Security Issues
Data breaches: Data breaches are the one of the most important securities issues in cloud
computing, which raises a question “With sensitive data being stored online rather than on
premise, is the cloud inherently less safe?” As per the findings around half of the security
measures of an organization lacks in security professionals and IT (Hamlen et al., 2012).
Insider threat: threats from the insider attack seem unlikely, but there are possibilities of
inside threats that exist within the system of cloud computing. Employees of the organization
might use their credential for the authorization access to the cloud-based services of the
Database, Online
Message
Storage (Garrison, Kim &
Wakefield, 2012)
Service level
Management
Dynamic Orchestration
of Logic Resources
Dynamic Orchestration
of Physical Resources
Dynamic Orchestration
of Application
Cloud computing is a very new and innovative model for providing IT services and
business. IaaS, PaaS and SaaS are the three levels of cloud computing service that can cover a
wide range of services. Besides the service delivery model and the computing service there are
other applications of cloud computing, which can be listed as: firstly, storage infrastructure,
software application, various models such as data, programming model and many more
(O’Driscoll, Daugelaite & Sleator, 2013).
Issues
There are several issues related to the privacy and security of the information that is migrating
into cloud computing, which can be categorized as:
Security Issues
Data breaches: Data breaches are the one of the most important securities issues in cloud
computing, which raises a question “With sensitive data being stored online rather than on
premise, is the cloud inherently less safe?” As per the findings around half of the security
measures of an organization lacks in security professionals and IT (Hamlen et al., 2012).
Insider threat: threats from the insider attack seem unlikely, but there are possibilities of
inside threats that exist within the system of cloud computing. Employees of the organization
might use their credential for the authorization access to the cloud-based services of the

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
organization and misuse the sensitive information of other employees and can also manipulate or
expose the information related to the organizational operations of the organization, which may
lead a serious loss for the organization.
Malware injection: This is another type of security issue that might affect the
performance and proper workings of the organization. Technically, it is a code or script in the
cloud services that behaves as “valid instances” and run similar to the SaaS cloud servers
(Curran, Carlin & Adams, 2012). This made them undetectable and, which gives it an ability to
be injected into the cloud services and be hidden by behaving as a part of the service or software
that is running with the cloud servers. This could lead intruders’ access to the sensitive
information, which can be misused in various ways.
Privacy Issues
User Control: It could be raised by both the consumers and legal issues. Data control and
visibility becomes limited by implementing cloud services into the system, as the service is being
offered by the third party (Pearson, 2013).
Loss of Legal Protection: Migrating data into the cloud can lead towards the loss of legal
protection of privacy, due the involvement of third party in data accessing (Kshetri, 2013).
Unauthorized usage: The third party, who is providing the services, could take the
benefits of the data that is being saved into their database or the cloud. These data can include
from targeted advertising to the re-sale data.
Important Issues
The issues those have left in the above discussion, which needs concern, are:
organization and misuse the sensitive information of other employees and can also manipulate or
expose the information related to the organizational operations of the organization, which may
lead a serious loss for the organization.
Malware injection: This is another type of security issue that might affect the
performance and proper workings of the organization. Technically, it is a code or script in the
cloud services that behaves as “valid instances” and run similar to the SaaS cloud servers
(Curran, Carlin & Adams, 2012). This made them undetectable and, which gives it an ability to
be injected into the cloud services and be hidden by behaving as a part of the service or software
that is running with the cloud servers. This could lead intruders’ access to the sensitive
information, which can be misused in various ways.
Privacy Issues
User Control: It could be raised by both the consumers and legal issues. Data control and
visibility becomes limited by implementing cloud services into the system, as the service is being
offered by the third party (Pearson, 2013).
Loss of Legal Protection: Migrating data into the cloud can lead towards the loss of legal
protection of privacy, due the involvement of third party in data accessing (Kshetri, 2013).
Unauthorized usage: The third party, who is providing the services, could take the
benefits of the data that is being saved into their database or the cloud. These data can include
from targeted advertising to the re-sale data.
Important Issues
The issues those have left in the above discussion, which needs concern, are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Insecure APIs: Application Programming Interfaces (APIs) provide clients opportunities
in order to customize their cloud experience. However, these APIs can be threat for the
organization’s cloud security due to their very nature. There are the possibilities of vulnerability
of an API that can takes place in the communication between the applications (Srinivasan et al.,
2012). This can help business and programmers in many ways; however they also leave behind
exploitable security risks.
Abuse of Cloud services: An example can make this topic more clearer, privileged users
can be responsible for the indirect or direct increase the security risks, which results infringe on
the terms of use that had been provided by the service provider. These include sharing of pirated
videos, software, books, or music that can result in legal consequences, which can be in the
forms of compensation or fines. An organization or individual can reduce its exposure to risk by
monitoring the usage and setting new guidelines for what the employees can host in the cloud.
Shared Vulnerabilities: Cloud security is a topic of shared responsibility between the clients and
the providers. This can be mitigated if the clients and providers share the responsibilities, and
work together in omitting personal risks can result in securing the organization’s data being
compromised.
Data Loss: Malicious attack can result in the loss of data in cloud, which can be a natural
disaster, or a data wiping by the Cloud service provider. The business that does not have any
recovery plan or backup status, losing vital and sensitive information can be a devastating to the
businesses. Amazon and Google are the examples of such unwanted situation, as both have lost
their data due to natural calamity (Wang et al., 2012).
Insecure APIs: Application Programming Interfaces (APIs) provide clients opportunities
in order to customize their cloud experience. However, these APIs can be threat for the
organization’s cloud security due to their very nature. There are the possibilities of vulnerability
of an API that can takes place in the communication between the applications (Srinivasan et al.,
2012). This can help business and programmers in many ways; however they also leave behind
exploitable security risks.
Abuse of Cloud services: An example can make this topic more clearer, privileged users
can be responsible for the indirect or direct increase the security risks, which results infringe on
the terms of use that had been provided by the service provider. These include sharing of pirated
videos, software, books, or music that can result in legal consequences, which can be in the
forms of compensation or fines. An organization or individual can reduce its exposure to risk by
monitoring the usage and setting new guidelines for what the employees can host in the cloud.
Shared Vulnerabilities: Cloud security is a topic of shared responsibility between the clients and
the providers. This can be mitigated if the clients and providers share the responsibilities, and
work together in omitting personal risks can result in securing the organization’s data being
compromised.
Data Loss: Malicious attack can result in the loss of data in cloud, which can be a natural
disaster, or a data wiping by the Cloud service provider. The business that does not have any
recovery plan or backup status, losing vital and sensitive information can be a devastating to the
businesses. Amazon and Google are the examples of such unwanted situation, as both have lost
their data due to natural calamity (Wang et al., 2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Impact of the Issues
The impact of such issues can be disastrous, based on the type of information and amount
of data that is being saved into the cloud. This could even lead to the closure and ending of an
organization business. These issues can lead to the expose, manipulation, and deletion of data
that are important for the organization. The business runs on the data that is being stored by it,
which includes very sensitive information and data related to the customer, clients, partners and
many more. This can also lead to ransom attack, which could affect the proper functioning and
financially.
Results
Based on the findings made above it can be stated that Cloud computing may help the
organization in transforming the traditional operational activities into digital form but it leads to
several issues that cannot be neglected. These issues can be smaller or vast based on the impact
but, these are matter of concern for any individual or organization practicing it. The technologies
IaaS, SaaS, and PaaS can provide better service like cloud storage, application, data accessibility
anywhere, but cannot mitigate the issues related to the IT infrastructure of the organization and
natural disasters that may affect the data by intruders or unauthorized users. Cyber security
should be strong and well programmed for both organization and cloud service providers, which
can help in protecting the data or information that is being stored in the cloud.
Conclusion
Based on the above report it can be concluded that walking shoulder to shoulder with the
new digital world demands cloud computing into the system. There are uncountable benefits of
this innovative technology and migrating data from personal servers to the cloud can be a
Impact of the Issues
The impact of such issues can be disastrous, based on the type of information and amount
of data that is being saved into the cloud. This could even lead to the closure and ending of an
organization business. These issues can lead to the expose, manipulation, and deletion of data
that are important for the organization. The business runs on the data that is being stored by it,
which includes very sensitive information and data related to the customer, clients, partners and
many more. This can also lead to ransom attack, which could affect the proper functioning and
financially.
Results
Based on the findings made above it can be stated that Cloud computing may help the
organization in transforming the traditional operational activities into digital form but it leads to
several issues that cannot be neglected. These issues can be smaller or vast based on the impact
but, these are matter of concern for any individual or organization practicing it. The technologies
IaaS, SaaS, and PaaS can provide better service like cloud storage, application, data accessibility
anywhere, but cannot mitigate the issues related to the IT infrastructure of the organization and
natural disasters that may affect the data by intruders or unauthorized users. Cyber security
should be strong and well programmed for both organization and cloud service providers, which
can help in protecting the data or information that is being stored in the cloud.
Conclusion
Based on the above report it can be concluded that walking shoulder to shoulder with the
new digital world demands cloud computing into the system. There are uncountable benefits of
this innovative technology and migrating data from personal servers to the cloud can be a

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
beneficial aspect for the organization. However, there are certain issues related with the privacy
and security, which cannot be eliminated but can be diminished in order to keep the information
private and secure. Cloud computing can be helpful for the organization to achieve its scope and
aim in efficient and effective manner.
beneficial aspect for the organization. However, there are certain issues related with the privacy
and security, which cannot be eliminated but can be diminished in order to keep the information
private and secure. Cloud computing can be helpful for the organization to achieve its scope and
aim in efficient and effective manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
References:
Chen, D., & Zhao, H. (2012, March). Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012
International Conference on (Vol. 1, pp. 647-651). IEEE.
Curran, K., Carlin, S., & Adams, M. (2012). Security issues in cloud computing. Cloud
computing for teaching and learning: strategies for design and implementation. IGI
Global, Hershey, Pennsylvania, USA, 200-208.
Garrison, G., Kim, S., & Wakefield, R. L. (2012). Success factors for deploying cloud
computing. Communications of the ACM, 55(9), 62-68.
Hamlen, K., Kantarcioglu, M., Khan, L., & Thuraisingham, B. (2012). Security issues for cloud
computing. Optimizing Information Security and Advancing Privacy Assurance: New
Technologies: New Technologies, 150.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of Internet Services and Applications, 4(1),
5.
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of institutions and
institutional evolution. Telecommunications Policy, 37(4), 372-386.
O’Driscoll, A., Daugelaite, J., & Sleator, R. D. (2013). ‘Big data’, Hadoop and cloud computing
in genomics. Journal of biomedical informatics, 46(5), 774-781.
References:
Chen, D., & Zhao, H. (2012, March). Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012
International Conference on (Vol. 1, pp. 647-651). IEEE.
Curran, K., Carlin, S., & Adams, M. (2012). Security issues in cloud computing. Cloud
computing for teaching and learning: strategies for design and implementation. IGI
Global, Hershey, Pennsylvania, USA, 200-208.
Garrison, G., Kim, S., & Wakefield, R. L. (2012). Success factors for deploying cloud
computing. Communications of the ACM, 55(9), 62-68.
Hamlen, K., Kantarcioglu, M., Khan, L., & Thuraisingham, B. (2012). Security issues for cloud
computing. Optimizing Information Security and Advancing Privacy Assurance: New
Technologies: New Technologies, 150.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of Internet Services and Applications, 4(1),
5.
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of institutions and
institutional evolution. Telecommunications Policy, 37(4), 372-386.
O’Driscoll, A., Daugelaite, J., & Sleator, R. D. (2013). ‘Big data’, Hadoop and cloud computing
in genomics. Journal of biomedical informatics, 46(5), 774-781.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY AND PRIVACY ISSUES IN CLOUD COMPUTING
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and Security for
Cloud Computing (pp. 3-42). Springer London.
Rong, C., Nguyen, S. T., & Jaatun, M. G. (2013). Beyond lightning: A survey on security
challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47-54.
Schewe, K. D., Bosa, K., Lampesberger, H., Ma, J., Rady, M., & Vleju, B. (2012). Challenges in
cloud computing. Scalable Computing: Practice and Experience, 12(4), 385-390.
Schewe, K. D., Bosa, K., Lampesberger, H., Ma, J., Rady, M., & Vleju, B. (2012). Challenges in
cloud computing. Scalable Computing: Practice and Experience, 12(4), 385-390.
Srinivasan, M. K., Sarukesi, K., Rodrigues, P., Manoj, M. S., & Revathy, P. (2012, August).
State-of-the-art cloud computing security taxonomies: a classification of security
challenges in the present cloud computing environment. In Proceedings of the
international conference on advances in computing, communications and
informatics (pp. 470-476). ACM.
Wang, C., Wang, Q., Ren, K., Cao, N., & Lou, W. (2012). Toward secure and dependable
storage services in cloud computing. IEEE transactions on Services Computing, 5(2),
220-232.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Generation
computer systems, 28(3), 583-592.
Pearson, S. (2013). Privacy, security and trust in cloud computing. In Privacy and Security for
Cloud Computing (pp. 3-42). Springer London.
Rong, C., Nguyen, S. T., & Jaatun, M. G. (2013). Beyond lightning: A survey on security
challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47-54.
Schewe, K. D., Bosa, K., Lampesberger, H., Ma, J., Rady, M., & Vleju, B. (2012). Challenges in
cloud computing. Scalable Computing: Practice and Experience, 12(4), 385-390.
Schewe, K. D., Bosa, K., Lampesberger, H., Ma, J., Rady, M., & Vleju, B. (2012). Challenges in
cloud computing. Scalable Computing: Practice and Experience, 12(4), 385-390.
Srinivasan, M. K., Sarukesi, K., Rodrigues, P., Manoj, M. S., & Revathy, P. (2012, August).
State-of-the-art cloud computing security taxonomies: a classification of security
challenges in the present cloud computing environment. In Proceedings of the
international conference on advances in computing, communications and
informatics (pp. 470-476). ACM.
Wang, C., Wang, Q., Ren, K., Cao, N., & Lou, W. (2012). Toward secure and dependable
storage services in cloud computing. IEEE transactions on Services Computing, 5(2),
220-232.
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Generation
computer systems, 28(3), 583-592.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





