NIT6130 Research: Methodology for Security and Privacy in Intelligence
VerifiedAdded on 2024/06/03
|16
|2722
|140
Report
AI Summary
This research report delves into the methodology employed to analyze security and privacy concerns within intelligence assistance, focusing on the development of advanced cybersecurity systems through collaboration between government and private firms. It addresses the research problem of balancing security needs with individual privacy rights in the context of increasing cyber threats and continuous surveillance. The report reviews existing literature, examining the lack of collaboration between government and private entities, and management issues that arise in such partnerships. Both qualitative and quantitative research methods are proposed to enhance data reliability, involving surveys and interviews to gather accurate feedback. The proposed methodology aims to leverage the strengths of both sectors to create a comprehensive defense mechanism, while acknowledging the limitations and challenges associated with collaborative efforts. The framework outlines the steps for data collection, analysis, and interpretation, ultimately contributing to a more secure and privacy-conscious intelligence assistance system. Desklib provides access to this and other solved assignments.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 3 – METHODOLOGY
By
i
ASSIGNMENT 3 – METHODOLOGY
By
i
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Table of Contents...............................................................................................................................ii
List of Figures...................................................................................................................................iii
List of Tables....................................................................................................................................iv
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................1
1.1.1 Research Problem Statement.............................................................................................1
1.1.2 Reorganized Collected Literature......................................................................................3
1.2 Types of Methodology.............................................................................................................4
1.2.1 Qualitative and Quantitative Methodologies.....................................................................4
1.2.2 Type of Chosen Methodology...........................................................................................4
1.3 Review of the Existing Methodologies.....................................................................................5
1.3.1 Selection of sub problem...................................................................................................5
1.3.2 Analysis of the Selected Methodologies............................................................................5
Literature 1: Lack of collaboration between the government and private firms..........................5
Literature 2.................................................................................................................................8
1.3.3 Relevance of the Research Problem..................................................................................9
1.3.4 Summary of the Reviewed Methodologies........................................................................9
1.4 Proposed Methodology.............................................................................................................9
1.4.1 Identification and Justification.........................................................................................10
1.4.2 Benefits and Limitations..................................................................................................10
1.4.3 Framework and Explanation............................................................................................11
List of References............................................................................................................................13
ii
Table of Contents...............................................................................................................................ii
List of Figures...................................................................................................................................iii
List of Tables....................................................................................................................................iv
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................1
1.1.1 Research Problem Statement.............................................................................................1
1.1.2 Reorganized Collected Literature......................................................................................3
1.2 Types of Methodology.............................................................................................................4
1.2.1 Qualitative and Quantitative Methodologies.....................................................................4
1.2.2 Type of Chosen Methodology...........................................................................................4
1.3 Review of the Existing Methodologies.....................................................................................5
1.3.1 Selection of sub problem...................................................................................................5
1.3.2 Analysis of the Selected Methodologies............................................................................5
Literature 1: Lack of collaboration between the government and private firms..........................5
Literature 2.................................................................................................................................8
1.3.3 Relevance of the Research Problem..................................................................................9
1.3.4 Summary of the Reviewed Methodologies........................................................................9
1.4 Proposed Methodology.............................................................................................................9
1.4.1 Identification and Justification.........................................................................................10
1.4.2 Benefits and Limitations..................................................................................................10
1.4.3 Framework and Explanation............................................................................................11
List of References............................................................................................................................13
ii

List of Tables
Table 1: Collection of Literature..........................................................................................................................3
Table 2: Demographic information records – Total participants = 100.............................................................6
Table 3: Responses...............................................................................................................................................7
Table 4: Mean and Standard Deviations (SD), Mean Difference (MD), t-values(t2), and responses for using
advanced technologies for data storage on a scale from 1(low) to(high)............................................................8
Table 5: Relevance of Methodology.....................................................................................................................9
iii
Table 1: Collection of Literature..........................................................................................................................3
Table 2: Demographic information records – Total participants = 100.............................................................6
Table 3: Responses...............................................................................................................................................7
Table 4: Mean and Standard Deviations (SD), Mean Difference (MD), t-values(t2), and responses for using
advanced technologies for data storage on a scale from 1(low) to(high)............................................................8
Table 5: Relevance of Methodology.....................................................................................................................9
iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Chapter 1
Methodology
The research has been conducted to analyse “Security and Privacy in intelligence assistance” and
various journals have been considered for analysing the impact of continuous surveillance. The most
important topic of discussion is the development of an advanced cyber-security system which can be
developed jointly by the government and private firms. The research also contains the possible
hindrances of working in partnership with the government.
The structure that is followed to perform the research is; the research statement is prepared and the
suitable research journals have been selected. After that, the main issues are identified and the possible
results of quantitative analysis have been done. The results have been analysed and the methods that can
be used has been justified by evaluating its benefits and limitations. At the last section, the framework
of the research has been illustrated and suitable explanation has been provided.
1
Methodology
The research has been conducted to analyse “Security and Privacy in intelligence assistance” and
various journals have been considered for analysing the impact of continuous surveillance. The most
important topic of discussion is the development of an advanced cyber-security system which can be
developed jointly by the government and private firms. The research also contains the possible
hindrances of working in partnership with the government.
The structure that is followed to perform the research is; the research statement is prepared and the
suitable research journals have been selected. After that, the main issues are identified and the possible
results of quantitative analysis have been done. The results have been analysed and the methods that can
be used has been justified by evaluating its benefits and limitations. At the last section, the framework
of the research has been illustrated and suitable explanation has been provided.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.1 Research Problem and Reorganized Collected Literature
1.1.1 Research Problem Statement
The research topic that has been selected is “Security and Privacy in intelligence assistance”. The use of
latest technology has enabled the governments and firms for developing surveillance system due to
increasing instances of data breach and data theft. Cyber Security is one of the prime agendas of both
private firms and the government because a high volume of confidential information can be stolen
endangering the security system of the entire region. The use of latest voice-recognised devices is the
potential targets since the hackers will be able to access the server and steal confidential information.
Although the firms and the government implement protective measures, still there is a possibility of
cyber-attacks. Hence, the governments take numerous initiatives for protecting the citizens from these
attacks and they continuously track the activities of an individual. This ensures that the possible threats
can be neutralised at appropriate intervals in order to safeguard the interests of the citizens. This enables
to create a positive environment and the valuable data can be saved protecting the reputation of the firm
(Coaffee and Fussey, 2015).
The continuous surveillance also results in breaching the privacy of the individuals as their personal
files are checked and monitored. This breach of privacy results in the communities getting frustrated as
they feel that they are being targeted which results in creating an unhealthy environment. Hence, in the
previous research, the possible ways of finding the solution to this issue were discussed and it was
suggested that the government and private firms to jointly develop a security system for detecting and
eliminating the possible cyber-attacks. The private firms face the issues related to funding for
developing or upgrading IT infrastructure which can be overcome by borrowing funds from the
government. The government does not have IT expertise and hence, the private companies can be
approached which resolves the issues faced by them and the infrastructure can be developed which aims
at securing the servers. This is a comprehensive solution to the cybersecurity issues faced by the
countries (Iossa and Martimort, 2015).
2
1.1.1 Research Problem Statement
The research topic that has been selected is “Security and Privacy in intelligence assistance”. The use of
latest technology has enabled the governments and firms for developing surveillance system due to
increasing instances of data breach and data theft. Cyber Security is one of the prime agendas of both
private firms and the government because a high volume of confidential information can be stolen
endangering the security system of the entire region. The use of latest voice-recognised devices is the
potential targets since the hackers will be able to access the server and steal confidential information.
Although the firms and the government implement protective measures, still there is a possibility of
cyber-attacks. Hence, the governments take numerous initiatives for protecting the citizens from these
attacks and they continuously track the activities of an individual. This ensures that the possible threats
can be neutralised at appropriate intervals in order to safeguard the interests of the citizens. This enables
to create a positive environment and the valuable data can be saved protecting the reputation of the firm
(Coaffee and Fussey, 2015).
The continuous surveillance also results in breaching the privacy of the individuals as their personal
files are checked and monitored. This breach of privacy results in the communities getting frustrated as
they feel that they are being targeted which results in creating an unhealthy environment. Hence, in the
previous research, the possible ways of finding the solution to this issue were discussed and it was
suggested that the government and private firms to jointly develop a security system for detecting and
eliminating the possible cyber-attacks. The private firms face the issues related to funding for
developing or upgrading IT infrastructure which can be overcome by borrowing funds from the
government. The government does not have IT expertise and hence, the private companies can be
approached which resolves the issues faced by them and the infrastructure can be developed which aims
at securing the servers. This is a comprehensive solution to the cybersecurity issues faced by the
countries (Iossa and Martimort, 2015).
2
1.1.2 Reorganized Collected Literature
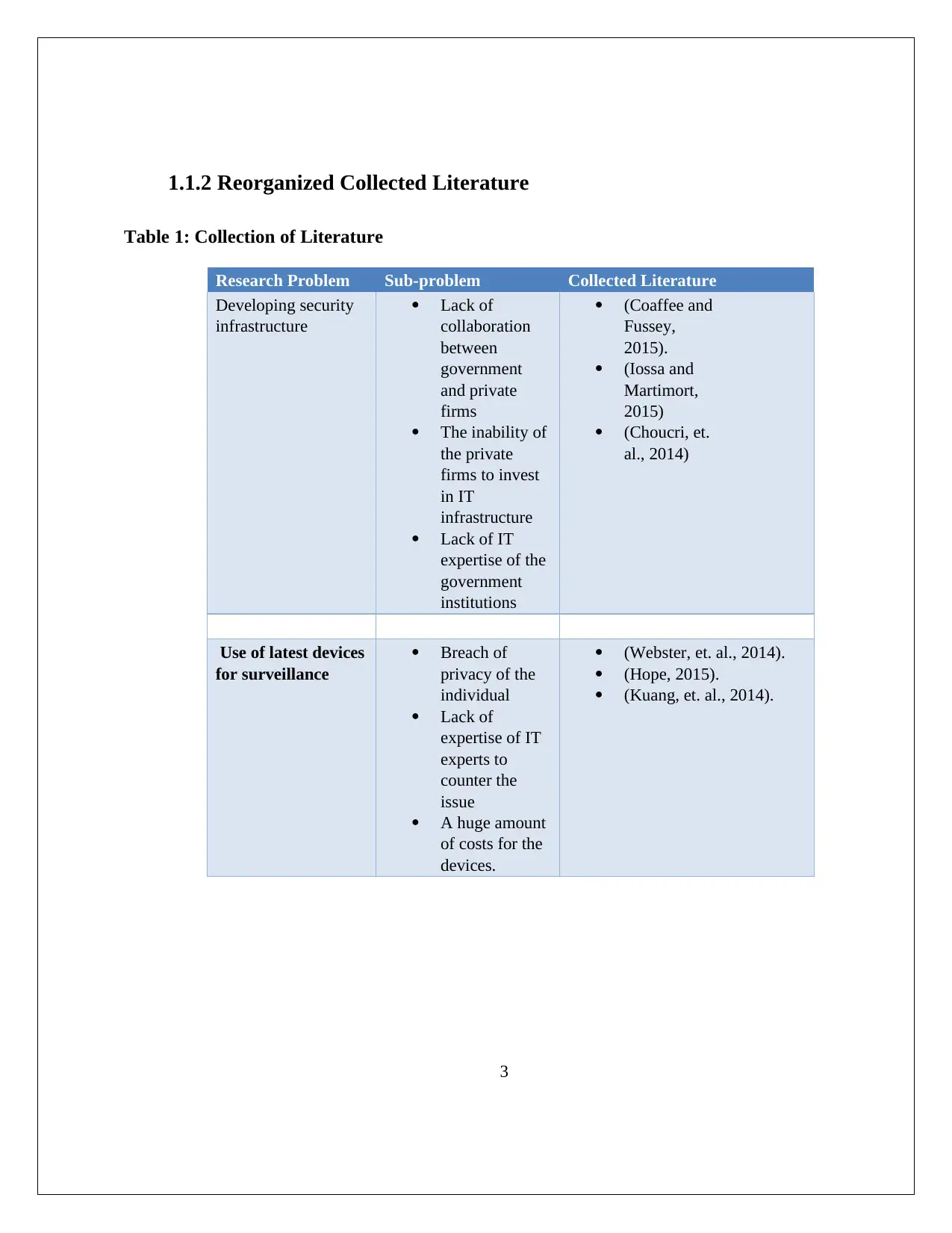
Table 1: Collection of Literature
Research Problem Sub-problem Collected Literature
Developing security
infrastructure
Lack of
collaboration
between
government
and private
firms
The inability of
the private
firms to invest
in IT
infrastructure
Lack of IT
expertise of the
government
institutions
(Coaffee and
Fussey,
2015).
(Iossa and
Martimort,
2015)
(Choucri, et.
al., 2014)
Use of latest devices
for surveillance
Breach of
privacy of the
individual
Lack of
expertise of IT
experts to
counter the
issue
A huge amount
of costs for the
devices.
(Webster, et. al., 2014).
(Hope, 2015).
(Kuang, et. al., 2014).
3
Table 1: Collection of Literature
Research Problem Sub-problem Collected Literature
Developing security
infrastructure
Lack of
collaboration
between
government
and private
firms
The inability of
the private
firms to invest
in IT
infrastructure
Lack of IT
expertise of the
government
institutions
(Coaffee and
Fussey,
2015).
(Iossa and
Martimort,
2015)
(Choucri, et.
al., 2014)
Use of latest devices
for surveillance
Breach of
privacy of the
individual
Lack of
expertise of IT
experts to
counter the
issue
A huge amount
of costs for the
devices.
(Webster, et. al., 2014).
(Hope, 2015).
(Kuang, et. al., 2014).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.2 Types of Methodology
1.2.1 Qualitative and Quantitative Methodologies
Qualitative research is concerned with obtaining a fresh data related to underlying opinions, reasons,
and motivations. It provides accurate information related to the various issues and enables to develop a
hypothesis. The information is directly taken from the targeted audience which makes it reliable and the
data can be used for developing suitable strategies. The data collection methods used in qualitative
methods is; interviews, focus group, and group discussions. The sample size depends on the amount of
information collected and usually, it is smaller and respondents are grouped into smaller groups for
arriving at appropriate results (Bryman, 2017).
Quantitative Research is used for identifying the issues by generating numerical data or data that can be
transformed into statistical data. The defined variables such as views, opinions, and behaviours are
presented by quantifying the information and representing the results in the form of suitable graphs and
diagrams. The sample size is comparatively larger than that of qualitative approach and the data
collection methods are online surveys, mobile surveys, and telephonic interviews.
1.2.2 Type of Chosen Methodology
The research has been conducted by performing both qualitative and quantitative research for enhancing
the reliability of the data. The appropriate questionnaires are prepared for obtaining the accurate
answers and these questions are directly asked the participants. This ensures that the genuine answers
are recorded. The quantitative research method ensures that a large volume of sample size is taken for
analysing the results which enhances the accuracy of the research. The results are indicated by using
graphs and figures so that the results can be easily analysed and appropriate justification can be made.
The reliability of the research is essential for the purpose of the research has to be achieved so that it is
helpful for performing further research.
4
1.2.1 Qualitative and Quantitative Methodologies
Qualitative research is concerned with obtaining a fresh data related to underlying opinions, reasons,
and motivations. It provides accurate information related to the various issues and enables to develop a
hypothesis. The information is directly taken from the targeted audience which makes it reliable and the
data can be used for developing suitable strategies. The data collection methods used in qualitative
methods is; interviews, focus group, and group discussions. The sample size depends on the amount of
information collected and usually, it is smaller and respondents are grouped into smaller groups for
arriving at appropriate results (Bryman, 2017).
Quantitative Research is used for identifying the issues by generating numerical data or data that can be
transformed into statistical data. The defined variables such as views, opinions, and behaviours are
presented by quantifying the information and representing the results in the form of suitable graphs and
diagrams. The sample size is comparatively larger than that of qualitative approach and the data
collection methods are online surveys, mobile surveys, and telephonic interviews.
1.2.2 Type of Chosen Methodology
The research has been conducted by performing both qualitative and quantitative research for enhancing
the reliability of the data. The appropriate questionnaires are prepared for obtaining the accurate
answers and these questions are directly asked the participants. This ensures that the genuine answers
are recorded. The quantitative research method ensures that a large volume of sample size is taken for
analysing the results which enhances the accuracy of the research. The results are indicated by using
graphs and figures so that the results can be easily analysed and appropriate justification can be made.
The reliability of the research is essential for the purpose of the research has to be achieved so that it is
helpful for performing further research.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3 Review of the Existing Methodologies
1.3.1 Selection of sub problem
The issue that has been considered is the lack of collaboration between the government and private
firms for jointly developing cybersecurity systems. Collaboration and partnerships have resolved
various issues faced by the communities and this can also be applied with regard to developing
cybersecurity infrastructure. The government and private firms will benefit since they will be able to
exchange the resources as well as expertise which enables to develop a comprehensive defence
mechanism against possible cyber threats. However, this solution can only work if there is a mutual
understanding among the participating parties as each tries to take more advantage. There may also be
management issues since the government will exert more pressure since it has the responsibility towards
the entire nation when compared to firms who have relatively lower responsibilities (Webster, et. al.,
2014).
1.3.2 Analysis of the Selected Methodologies
Literature 1: Lack of collaboration between the government and private
firms.
The research question is related to the topic of collaboration between the government and private firms
for developing a cyber-security system. However, there are issues related to management and the
amount of benefits that can be obtained by the private firms. These issues have to be resolved before
finalising the type of technology that has to be used.
For performing the research, the participants were divided based on their gender, age, qualification and
type of occupation. The experts were also interviewed who consisted of government officials as well as
other experts in the field. Their views and opinions were taken and were recorded and the data was
stored at the appropriate location. These results were compared with the secondary data obtained from
trustable websites for enhancing the reliability of the data (Hope, 2015). The following data indicates
the number of participants and their demographic information:
5
1.3.1 Selection of sub problem
The issue that has been considered is the lack of collaboration between the government and private
firms for jointly developing cybersecurity systems. Collaboration and partnerships have resolved
various issues faced by the communities and this can also be applied with regard to developing
cybersecurity infrastructure. The government and private firms will benefit since they will be able to
exchange the resources as well as expertise which enables to develop a comprehensive defence
mechanism against possible cyber threats. However, this solution can only work if there is a mutual
understanding among the participating parties as each tries to take more advantage. There may also be
management issues since the government will exert more pressure since it has the responsibility towards
the entire nation when compared to firms who have relatively lower responsibilities (Webster, et. al.,
2014).
1.3.2 Analysis of the Selected Methodologies
Literature 1: Lack of collaboration between the government and private
firms.
The research question is related to the topic of collaboration between the government and private firms
for developing a cyber-security system. However, there are issues related to management and the
amount of benefits that can be obtained by the private firms. These issues have to be resolved before
finalising the type of technology that has to be used.
For performing the research, the participants were divided based on their gender, age, qualification and
type of occupation. The experts were also interviewed who consisted of government officials as well as
other experts in the field. Their views and opinions were taken and were recorded and the data was
stored at the appropriate location. These results were compared with the secondary data obtained from
trustable websites for enhancing the reliability of the data (Hope, 2015). The following data indicates
the number of participants and their demographic information:
5

Table 2: Demographic information records – Total participants = 100
Gender Male
Female
Age Range 20-33
34-57
More Than 57
Education Graduate
Masters
Occupation Experts/government officials
Businessmen
Students
Other professionals
Table 3: Responses
Features Response
Gender
Male 64 (61%)
6
Gender Male
Female
Age Range 20-33
34-57
More Than 57
Education Graduate
Masters
Occupation Experts/government officials
Businessmen
Students
Other professionals
Table 3: Responses
Features Response
Gender
Male 64 (61%)
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
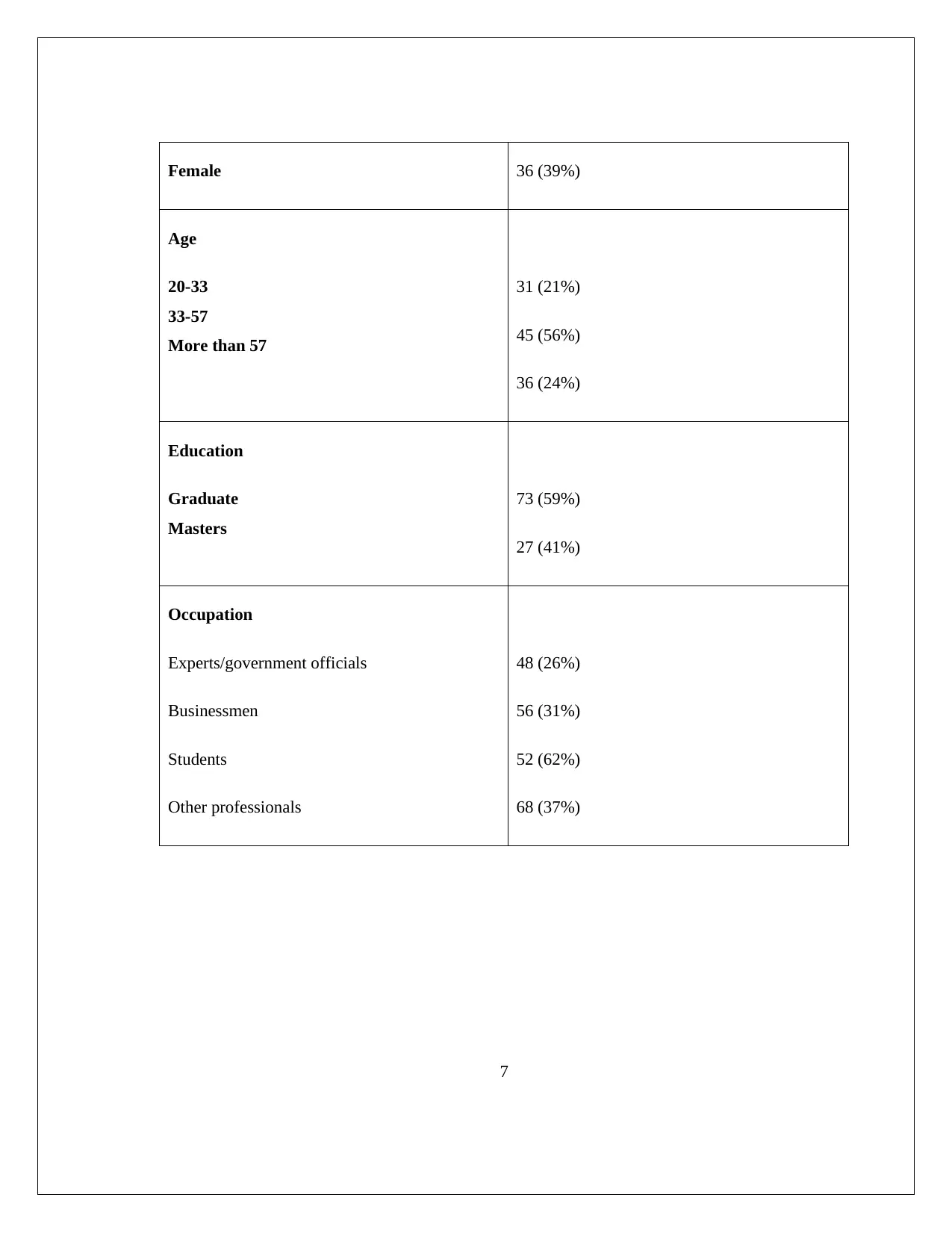
Female 36 (39%)
Age
20-33
33-57
More than 57
31 (21%)
45 (56%)
36 (24%)
Education
Graduate
Masters
73 (59%)
27 (41%)
Occupation
Experts/government officials
Businessmen
Students
Other professionals
48 (26%)
56 (31%)
52 (62%)
68 (37%)
7
Age
20-33
33-57
More than 57
31 (21%)
45 (56%)
36 (24%)
Education
Graduate
Masters
73 (59%)
27 (41%)
Occupation
Experts/government officials
Businessmen
Students
Other professionals
48 (26%)
56 (31%)
52 (62%)
68 (37%)
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Literature 2
Issues related to management
The major concern with regard to forming a partnership is the management of the cybersecurity
apparatus and the amount of control that can be exerted by the government. The private firms always
want a fair share and equal opportunity for utilising the facilities, but the government always consider
taking major portion because of its responsibility towards protecting local communities. This difference
in approach results in lack of coordination among the government and private organisations (Kuang, et.
al., 2014).
Methods used
The qualitative and quantitative methods were used for analysing the results. For this particular analysis,
the interviews were conducted for the government officials and top management executives of large
firms and their feedback is saved for further analysis. Appropriate samples were taken from the different
groups of people for arriving at accurate results.
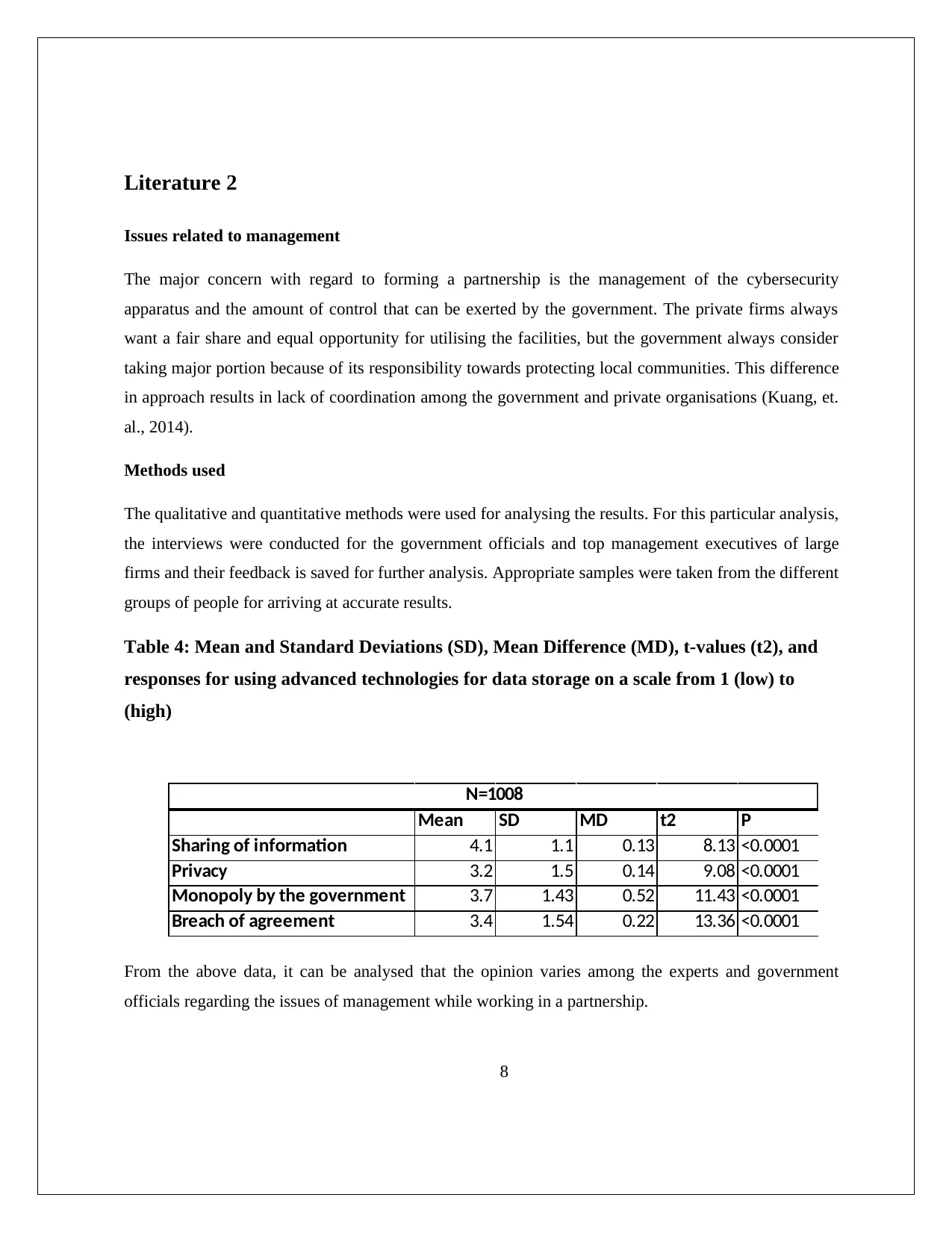
Table 4: Mean and Standard Deviations (SD), Mean Difference (MD), t-values (t2), and
responses for using advanced technologies for data storage on a scale from 1 (low) to
(high)
Mean SD MD t2 P
Sharing of information 4.1 1.1 0.13 8.13 <0.0001
Privacy 3.2 1.5 0.14 9.08 <0.0001
Monopoly by the government 3.7 1.43 0.52 11.43 <0.0001
Breach of agreement 3.4 1.54 0.22 13.36 <0.0001
N=1008
From the above data, it can be analysed that the opinion varies among the experts and government
officials regarding the issues of management while working in a partnership.
8
Issues related to management
The major concern with regard to forming a partnership is the management of the cybersecurity
apparatus and the amount of control that can be exerted by the government. The private firms always
want a fair share and equal opportunity for utilising the facilities, but the government always consider
taking major portion because of its responsibility towards protecting local communities. This difference
in approach results in lack of coordination among the government and private organisations (Kuang, et.
al., 2014).
Methods used
The qualitative and quantitative methods were used for analysing the results. For this particular analysis,
the interviews were conducted for the government officials and top management executives of large
firms and their feedback is saved for further analysis. Appropriate samples were taken from the different
groups of people for arriving at accurate results.
Table 4: Mean and Standard Deviations (SD), Mean Difference (MD), t-values (t2), and
responses for using advanced technologies for data storage on a scale from 1 (low) to
(high)
Mean SD MD t2 P
Sharing of information 4.1 1.1 0.13 8.13 <0.0001
Privacy 3.2 1.5 0.14 9.08 <0.0001
Monopoly by the government 3.7 1.43 0.52 11.43 <0.0001
Breach of agreement 3.4 1.54 0.22 13.36 <0.0001
N=1008
From the above data, it can be analysed that the opinion varies among the experts and government
officials regarding the issues of management while working in a partnership.
8

1.3.3 Relevance of the Research Problem
The literature 1 was the actual issue related to the development of a comprehensive cyber-security
infrastructure. It also analysed the possible ways in which the benefits can be utilised by both the
government and private firms. The literature also explained the various hindrances that can occur while
working in a partnership and the possible reasons for those hindrances.
Literature 2 is a sub problem but it is closely related to the issue mentioned in Literature1. It discusses
the issues related to management of the cyber-security system after its installation.
1.3.4 Summary of the Reviewed Methodologies
Table 5: Relevance of Methodology
Literature # Research Problem Methodology Your Sub-problem Relevance
Literature1 Developing cyber
security
infrastructure by
working in
partnership
Quantitative Issues related to
management
Strongly
relevant
Literature2 Issues related to
management
Quantitative Percentage of
sharing the
authority
Strongly
relevant
1.4 Proposed Methodology
The methodology that can be used is the mixture of qualitative and quantitative methods. As discussed
earlier, by using both qualitative and quantitative methods, the accuracy and reliability of the research
results can be enhanced. This can be used for conducting further research.
9
The literature 1 was the actual issue related to the development of a comprehensive cyber-security
infrastructure. It also analysed the possible ways in which the benefits can be utilised by both the
government and private firms. The literature also explained the various hindrances that can occur while
working in a partnership and the possible reasons for those hindrances.
Literature 2 is a sub problem but it is closely related to the issue mentioned in Literature1. It discusses
the issues related to management of the cyber-security system after its installation.
1.3.4 Summary of the Reviewed Methodologies
Table 5: Relevance of Methodology
Literature # Research Problem Methodology Your Sub-problem Relevance
Literature1 Developing cyber
security
infrastructure by
working in
partnership
Quantitative Issues related to
management
Strongly
relevant
Literature2 Issues related to
management
Quantitative Percentage of
sharing the
authority
Strongly
relevant
1.4 Proposed Methodology
The methodology that can be used is the mixture of qualitative and quantitative methods. As discussed
earlier, by using both qualitative and quantitative methods, the accuracy and reliability of the research
results can be enhanced. This can be used for conducting further research.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





