Analysis of IT Security Risks and Mitigation Strategies for Tesco
VerifiedAdded on 2023/01/19
|21
|5004
|59
Report
AI Summary
This report provides a comprehensive analysis of IT security risks, procedures, and policies, focusing on the case of Tesco. It begins by defining security and identifying various threats such as computer viruses, botnets, spam, worms, hackers, adware, phishing, rootkits, and spyware. The report then details security procedures within an organization, outlining a method for assessing and treating IT security risks. It explores how trusted networks and firewall configurations impact security, as well as the benefits of network monitoring. Furthermore, the report delves into risk assessment procedures, data protection plans, and the methodology of ISO 31000 risk management. It examines the influence of IT security audits on organizational security, the alignment of IT security with organizational policy, and the design of a security policy for a firm. Key elements of a disaster recovery plan and the tools used by an organization are also discussed, culminating in a conclusion and references.

Coursework
Unit 5: Security
Unit 5: Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction ..........................................................................................................................................4
Assessing security risks to organisation................................................................................................5
Computer viruses...........................................................................................................................5
Botnets...........................................................................................................................................5
Spam .............................................................................................................................................6
Worms ..........................................................................................................................................6
Hackers .........................................................................................................................................6
Adware .........................................................................................................................................7
Phishing.........................................................................................................................................7
Rootkits.........................................................................................................................................7
Spyware ........................................................................................................................................7
Security procedures of the Organisation............................................................................................8
A method to assess and treat IT security risks...............................................................................9
Trusted network becomes a part of an IT security how?................................................................9
Incorrect configuration of firewall policies.....................................................................................10
Incorrect configuration of third-party VPNs....................................................................................10
Implementing a DMZ, static IP and NAT ......................................................................................10
Benefits of the Networking monitoring.......................................................................................12
Risk assessment procedures............................................................................................................13
Data protection plan and procedures ..............................................................................................13
Methodology of ISO 31000 risk management.............................................................................14
Influence on the organizational security resulting audit of IT security........................................14
Consider how IT security can be aligned with organisational policy, detailing the security impact
of any misalignment........................................................................................................................15
Design and implement a security policy for a firm.........................................................................15
Key elements of disaster recovery plan...........................................................................................15
Tools that are used by an organization.........................................................................................16
Conclusion ..........................................................................................................................................17
REFERENCES....................................................................................................................................18
Appendix ............................................................................................................................................20
Presentation ....................................................................................................................................20
Introduction ..........................................................................................................................................4
Assessing security risks to organisation................................................................................................5
Computer viruses...........................................................................................................................5
Botnets...........................................................................................................................................5
Spam .............................................................................................................................................6
Worms ..........................................................................................................................................6
Hackers .........................................................................................................................................6
Adware .........................................................................................................................................7
Phishing.........................................................................................................................................7
Rootkits.........................................................................................................................................7
Spyware ........................................................................................................................................7
Security procedures of the Organisation............................................................................................8
A method to assess and treat IT security risks...............................................................................9
Trusted network becomes a part of an IT security how?................................................................9
Incorrect configuration of firewall policies.....................................................................................10
Incorrect configuration of third-party VPNs....................................................................................10
Implementing a DMZ, static IP and NAT ......................................................................................10
Benefits of the Networking monitoring.......................................................................................12
Risk assessment procedures............................................................................................................13
Data protection plan and procedures ..............................................................................................13
Methodology of ISO 31000 risk management.............................................................................14
Influence on the organizational security resulting audit of IT security........................................14
Consider how IT security can be aligned with organisational policy, detailing the security impact
of any misalignment........................................................................................................................15
Design and implement a security policy for a firm.........................................................................15
Key elements of disaster recovery plan...........................................................................................15
Tools that are used by an organization.........................................................................................16
Conclusion ..........................................................................................................................................17
REFERENCES....................................................................................................................................18
Appendix ............................................................................................................................................20
Presentation ....................................................................................................................................20

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

·Introduction
Security can be defined as a way in which resilience against potential harm caused by
others is provided. There are various kinds of security risk that an organization need to be
aware of such as: phishing, malware, data loss, network vulnerabilities, ransomware etc. IT
security is considered as the set of the cyber security strategies that able to prevent the
unauthorized access to the firm assets such as Network, data and computer (Backes, Bugiel
and Derr, 2016). As it maintains the confidentiality as well as integrity of the sensitive
information that blocks the access of hackers. As in today's world, Hackers becomes smarter
day by day, there is a requirement of protection the digital assets as well as networks devices
that is even greater. Present Report lay emphasis on the Tesco that established in London. It
distributes the food across the many town within the country. It focuses on identifying types
of risks, security procedures and also propose a method to treat the I.T security risks, after
that it describes the solution regarding security such as benefits to implement network
systems. It also focuses on the mechanism that control security of Tesco such as risk
assessments data protection process, possible influence to the security of the Tesco.
Furthermore, it also manages the firm's security such as focuses on the main components of
the Organizational disaster as well as implement a security policy plan .It also discusses the
role of the stakeholder's within the firm to apply the security audit recommendations.
Discuss the roles of stakeholders in the organization to implement security audit
recommendations and it highlights on the tools used within an organizational policy.
Security can be defined as a way in which resilience against potential harm caused by
others is provided. There are various kinds of security risk that an organization need to be
aware of such as: phishing, malware, data loss, network vulnerabilities, ransomware etc. IT
security is considered as the set of the cyber security strategies that able to prevent the
unauthorized access to the firm assets such as Network, data and computer (Backes, Bugiel
and Derr, 2016). As it maintains the confidentiality as well as integrity of the sensitive
information that blocks the access of hackers. As in today's world, Hackers becomes smarter
day by day, there is a requirement of protection the digital assets as well as networks devices
that is even greater. Present Report lay emphasis on the Tesco that established in London. It
distributes the food across the many town within the country. It focuses on identifying types
of risks, security procedures and also propose a method to treat the I.T security risks, after
that it describes the solution regarding security such as benefits to implement network
systems. It also focuses on the mechanism that control security of Tesco such as risk
assessments data protection process, possible influence to the security of the Tesco.
Furthermore, it also manages the firm's security such as focuses on the main components of
the Organizational disaster as well as implement a security policy plan .It also discusses the
role of the stakeholder's within the firm to apply the security audit recommendations.
Discuss the roles of stakeholders in the organization to implement security audit
recommendations and it highlights on the tools used within an organizational policy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

·Assessing security risks to organisation
Risk can be defined as a chance or possibility of data loss, damage, unauthorised
access etc. that can be a threat to one’s business, systems or processes. There are many ways
through which risk can be assessed such as: first is to identify any kind of hazard the can be a
threat to business. Then the risk or hazard is assessed and individual, data or processes that
would be affected is identified. Then actions that are required to be taken is accessed or
decided. There are different types of risks that can affect an organization. Some of them have
been explained below.
l壱Computer viruses
Computer viruses are the pieces of the software that able to design so that it can be spread
from one computer to other computer (Bertino and Islam, 2017). As per the statistics 33% of
household computers overelaborate with some kinds of malware, more than half of them are
viruses. They can sent through email attachments or it can download from the various other
specific sites to infect the computer as well as other computers on the list through using
systems regarding network. Viruses are known for sending spam. It corrupts as well as steal
data, disable security settings from an individual's computer including personal information
for example passwords and ever going to delete everything on the hard drive (Brotby and
Hinson, 2016).
l壱Botnets
It can be used regarding anything from targeting the attacks on the servers, so that it able to
run spam email campaigns. Botnets included many computers, as it finds difficult to stop for
many businesses. Usually this computer security can be deployed through a botmaster that
commands a number of the compromised computer number of bots to run the activities that
run malicious activities. Zombie army is often collection of infected computers that carry out
boatmaster of ill intent. If the Tesco's network can be overtaken through a botnet, the system
able to subsequently used to mugging other networks through likes of worms, viruses, Trojan
horses as well as DDoS attacks (Das and Khan, 2016).
Risk can be defined as a chance or possibility of data loss, damage, unauthorised
access etc. that can be a threat to one’s business, systems or processes. There are many ways
through which risk can be assessed such as: first is to identify any kind of hazard the can be a
threat to business. Then the risk or hazard is assessed and individual, data or processes that
would be affected is identified. Then actions that are required to be taken is accessed or
decided. There are different types of risks that can affect an organization. Some of them have
been explained below.
l壱Computer viruses
Computer viruses are the pieces of the software that able to design so that it can be spread
from one computer to other computer (Bertino and Islam, 2017). As per the statistics 33% of
household computers overelaborate with some kinds of malware, more than half of them are
viruses. They can sent through email attachments or it can download from the various other
specific sites to infect the computer as well as other computers on the list through using
systems regarding network. Viruses are known for sending spam. It corrupts as well as steal
data, disable security settings from an individual's computer including personal information
for example passwords and ever going to delete everything on the hard drive (Brotby and
Hinson, 2016).
l壱Botnets
It can be used regarding anything from targeting the attacks on the servers, so that it able to
run spam email campaigns. Botnets included many computers, as it finds difficult to stop for
many businesses. Usually this computer security can be deployed through a botmaster that
commands a number of the compromised computer number of bots to run the activities that
run malicious activities. Zombie army is often collection of infected computers that carry out
boatmaster of ill intent. If the Tesco's network can be overtaken through a botnet, the system
able to subsequently used to mugging other networks through likes of worms, viruses, Trojan
horses as well as DDoS attacks (Das and Khan, 2016).

Figure 1: IT security threats
l壱Spam
Everyone is familiar with the Spam as the junk emails tends to squeeze businesses servers as
well as annoy recipient all across the organization. Spam becomes a threat for the computer
security as it contains harmful links, also overload the mail server as well as distribute
additional spam (Green and Smith, 2016).
l壱Worms
Jiggling is considered as its way into network. It is a worm that is deployed to the self-
replicate from one computer to the another. The only thing makes it differ from the virus is
that it needed no user interaction to get spread. According to this software hat is applied
within large quantities for a short duration of time. It can be considered as wreak havoc on
the network performance as well as it utilize to launch another malicious attacks end-to-end
system (Ingram, 2016).
l壱Hackers
Most of the security breach through the malicious intent of an individual. They are
targeted through hackers regarding financial gain. These are the predators that are seeking
out the opportunities to take advantage on vulnerabilities. It is the reason that why the Tesco
l壱Spam
Everyone is familiar with the Spam as the junk emails tends to squeeze businesses servers as
well as annoy recipient all across the organization. Spam becomes a threat for the computer
security as it contains harmful links, also overload the mail server as well as distribute
additional spam (Green and Smith, 2016).
l壱Worms
Jiggling is considered as its way into network. It is a worm that is deployed to the self-
replicate from one computer to the another. The only thing makes it differ from the virus is
that it needed no user interaction to get spread. According to this software hat is applied
within large quantities for a short duration of time. It can be considered as wreak havoc on
the network performance as well as it utilize to launch another malicious attacks end-to-end
system (Ingram, 2016).
l壱Hackers
Most of the security breach through the malicious intent of an individual. They are
targeted through hackers regarding financial gain. These are the predators that are seeking
out the opportunities to take advantage on vulnerabilities. It is the reason that why the Tesco
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

requires to be on the High alert. To avoid the victimized through hackers, an individual must
stay vigilant as well as employ a security plan ,that involves data management solutions as
well as file sharing to keep the businesses safe. For that employees requires the continual
education as well as Training ways to identified thwarts and threats attacks (Kang, Moon and
Park, 2017).
l壱Adware
When unwanted type of advertisements begins to appeal regarding on the computer. It may
be victimized through adware. While trying for accessing software the staff members of the
Tesco accidentally download adware. They also used the retrieve information without needed
the Knowledge and redirect the user's browsers.
l壱Phishing
Usernames as well as passwords are known as the phishing scam trick an internal used that
provides information that can breach the system. This information seek from the employees
by the email as well as disguised such as legitimate requests. Such as financial institution
asking for the login details to fix an account regarding solving an issue. Over the sensitive
information, the hackers try to gain the access as they require to lockup or steal so that is can
compromise company's critical data (Li and et.al., 2016).
l壱Rootkits
Rootkit is considered as the collection of the software that is implemented to obtain
administrator level access as it is designed to complete. It is imagined form the example if a
cyber-attack gain the complete control all over the computers. A hacker procures this kind of
access by the threats as well as vulnerabilities. For example Phishing scams, weak password
or spyware. It has the capacity to go undetected and also it enables to change the current
software of The Tesco. Also, the security applications ha can employed so that it can protect
computer easily (Nazareth and Choi, 2015).
stay vigilant as well as employ a security plan ,that involves data management solutions as
well as file sharing to keep the businesses safe. For that employees requires the continual
education as well as Training ways to identified thwarts and threats attacks (Kang, Moon and
Park, 2017).
l壱Adware
When unwanted type of advertisements begins to appeal regarding on the computer. It may
be victimized through adware. While trying for accessing software the staff members of the
Tesco accidentally download adware. They also used the retrieve information without needed
the Knowledge and redirect the user's browsers.
l壱Phishing
Usernames as well as passwords are known as the phishing scam trick an internal used that
provides information that can breach the system. This information seek from the employees
by the email as well as disguised such as legitimate requests. Such as financial institution
asking for the login details to fix an account regarding solving an issue. Over the sensitive
information, the hackers try to gain the access as they require to lockup or steal so that is can
compromise company's critical data (Li and et.al., 2016).
l壱Rootkits
Rootkit is considered as the collection of the software that is implemented to obtain
administrator level access as it is designed to complete. It is imagined form the example if a
cyber-attack gain the complete control all over the computers. A hacker procures this kind of
access by the threats as well as vulnerabilities. For example Phishing scams, weak password
or spyware. It has the capacity to go undetected and also it enables to change the current
software of The Tesco. Also, the security applications ha can employed so that it can protect
computer easily (Nazareth and Choi, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

l壱Spyware
This is a malicious software done exactly as per its name suggest. It has the ability to spy on
the user without any need of permission or knowledge. This software is installed on the
computer of the Tesco, the criminal who wanted to execute has the capacity to monitor
activity regarding that device. It collects the information to utilize against the business or use
such as website visits, financial data. Some of them detect redirect web browsers, detect
keystrokes and also alters computer settings or also it installs other programs that are called
as dangerous programs. Thus it is considered as the crucial to out protections within place as
well as update them continuously, so that the spyware attacks are thwarts easily (Pacheco and
Hariri, 2016).
l壱Security procedures of the Organisation
It is considered as the detailed step by step instructions on implementing, security
controls list from the Tesco's security policies. It should cover the hardware as well as
software components that assists the process of the business and security related business
procedures. Such as Onboarding of a new staff member. Security policy also refers to the
well-defined plans, rules as well as regulations systems that access the Tesco's system as well
as information included in it. With the help of the Good policy it protects not only systems
and information and system but also the individuals staff members and the firm as whole
(Safa and et.al., 2015).
Security procedure of an organization has been explained below:
This is a malicious software done exactly as per its name suggest. It has the ability to spy on
the user without any need of permission or knowledge. This software is installed on the
computer of the Tesco, the criminal who wanted to execute has the capacity to monitor
activity regarding that device. It collects the information to utilize against the business or use
such as website visits, financial data. Some of them detect redirect web browsers, detect
keystrokes and also alters computer settings or also it installs other programs that are called
as dangerous programs. Thus it is considered as the crucial to out protections within place as
well as update them continuously, so that the spyware attacks are thwarts easily (Pacheco and
Hariri, 2016).
l壱Security procedures of the Organisation
It is considered as the detailed step by step instructions on implementing, security
controls list from the Tesco's security policies. It should cover the hardware as well as
software components that assists the process of the business and security related business
procedures. Such as Onboarding of a new staff member. Security policy also refers to the
well-defined plans, rules as well as regulations systems that access the Tesco's system as well
as information included in it. With the help of the Good policy it protects not only systems
and information and system but also the individuals staff members and the firm as whole
(Safa and et.al., 2015).
Security procedure of an organization has been explained below:
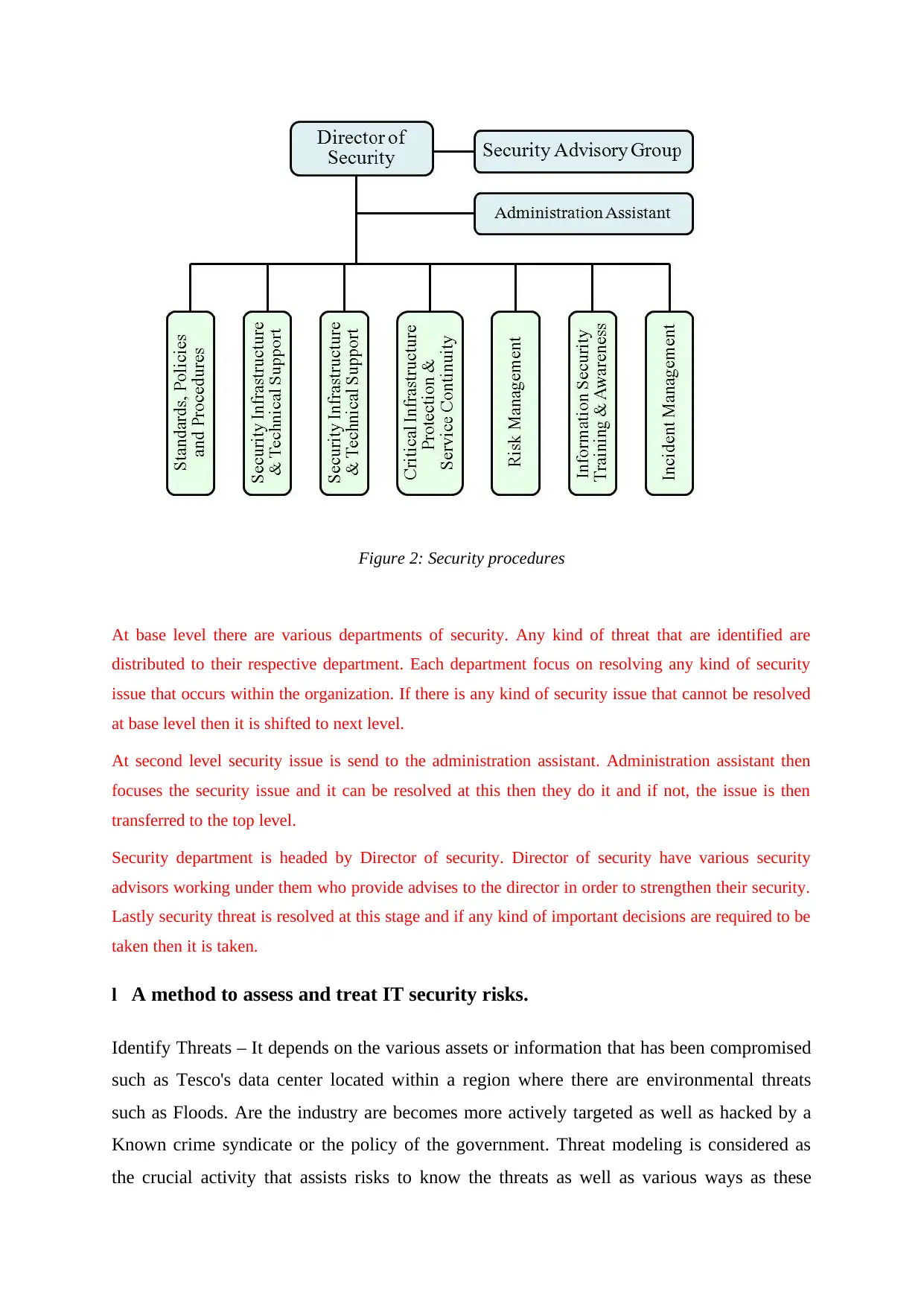
Figure 2: Security procedures
At base level there are various departments of security. Any kind of threat that are identified are
distributed to their respective department. Each department focus on resolving any kind of security
issue that occurs within the organization. If there is any kind of security issue that cannot be resolved
at base level then it is shifted to next level.
At second level security issue is send to the administration assistant. Administration assistant then
focuses the security issue and it can be resolved at this then they do it and if not, the issue is then
transferred to the top level.
Security department is headed by Director of security. Director of security have various security
advisors working under them who provide advises to the director in order to strengthen their security.
Lastly security threat is resolved at this stage and if any kind of important decisions are required to be
taken then it is taken.
l壱A method to assess and treat IT security risks.
Identify Threats – It depends on the various assets or information that has been compromised
such as Tesco's data center located within a region where there are environmental threats
such as Floods. Are the industry are becomes more actively targeted as well as hacked by a
Known crime syndicate or the policy of the government. Threat modeling is considered as
the crucial activity that assists risks to know the threats as well as various ways as these
At base level there are various departments of security. Any kind of threat that are identified are
distributed to their respective department. Each department focus on resolving any kind of security
issue that occurs within the organization. If there is any kind of security issue that cannot be resolved
at base level then it is shifted to next level.
At second level security issue is send to the administration assistant. Administration assistant then
focuses the security issue and it can be resolved at this then they do it and if not, the issue is then
transferred to the top level.
Security department is headed by Director of security. Director of security have various security
advisors working under them who provide advises to the director in order to strengthen their security.
Lastly security threat is resolved at this stage and if any kind of important decisions are required to be
taken then it is taken.
l壱A method to assess and treat IT security risks.
Identify Threats – It depends on the various assets or information that has been compromised
such as Tesco's data center located within a region where there are environmental threats
such as Floods. Are the industry are becomes more actively targeted as well as hacked by a
Known crime syndicate or the policy of the government. Threat modeling is considered as
the crucial activity that assists risks to know the threats as well as various ways as these
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

threats can causes risks so that it causes risk to realize through the exploiting vulnerabilities.
Such as finance risk, it can be managed by making of the budget (Walterbusch, Fietz and
Teuteberg, 2017).
l壱Trusted network becomes a part of an IT security how?
Trusted network such as Mobile security is considers as the top of the worry for the
company. As all the workers of the Tesco frame used the Smartphones, as they also access
corporate data from the mobile phones as well as this means that keep of the sensitive
information into the wrong hands within an intricate puzzle. As it considers higher than ever.
It is easy to focus on the malware of this type as mobile malware infections are becomes
incredible common within the real world Data breaches incidents and many physical attacks
is also done with the threat of the information leaked . Thus, the nature of the malware of
mobile as well as inherent protections build within system called mobile operating systems
(Warkentin and et.al., 2016).
l壱Incorrect configuration of firewall policies
Many times incorrect firewall policies also increases IT security risk for organizations.
Organizations need to focus on Configuring firewall policies and need to narrow down open
firewall policy. If firewall policies are kept broad and open or are configured incorrectly then
it can increase chances of breech and can cause potential damage to the system (Walterbusch,
Fietz and Teuteberg, 2017).
l壱Incorrect configuration of third-party VPNs
Virtual private network helps in ensuring whether secure private connection has been
established or not. Third part VPN have various security weaknesses that can increase IT security risk
for organizations. In fact, third party VPN are weakest network security that can be easily become a
reason for data breech these days. Third party VPN compromises IT security in many ways and also
increases chances of credential theft as it is quite easier for hackers to access default passwords.
Incorrect configuration of VPN of third part can lead to various kinds of security threats such
as: incorrect VPN can increase chances of system hacking where passwords or any kind of
Such as finance risk, it can be managed by making of the budget (Walterbusch, Fietz and
Teuteberg, 2017).
l壱Trusted network becomes a part of an IT security how?
Trusted network such as Mobile security is considers as the top of the worry for the
company. As all the workers of the Tesco frame used the Smartphones, as they also access
corporate data from the mobile phones as well as this means that keep of the sensitive
information into the wrong hands within an intricate puzzle. As it considers higher than ever.
It is easy to focus on the malware of this type as mobile malware infections are becomes
incredible common within the real world Data breaches incidents and many physical attacks
is also done with the threat of the information leaked . Thus, the nature of the malware of
mobile as well as inherent protections build within system called mobile operating systems
(Warkentin and et.al., 2016).
l壱Incorrect configuration of firewall policies
Many times incorrect firewall policies also increases IT security risk for organizations.
Organizations need to focus on Configuring firewall policies and need to narrow down open
firewall policy. If firewall policies are kept broad and open or are configured incorrectly then
it can increase chances of breech and can cause potential damage to the system (Walterbusch,
Fietz and Teuteberg, 2017).
l壱Incorrect configuration of third-party VPNs
Virtual private network helps in ensuring whether secure private connection has been
established or not. Third part VPN have various security weaknesses that can increase IT security risk
for organizations. In fact, third party VPN are weakest network security that can be easily become a
reason for data breech these days. Third party VPN compromises IT security in many ways and also
increases chances of credential theft as it is quite easier for hackers to access default passwords.
Incorrect configuration of VPN of third part can lead to various kinds of security threats such
as: incorrect VPN can increase chances of system hacking where passwords or any kind of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
sensitive information can be easily hacked, chances of unauthorized access on the system can
increase due to this overall security of the system can get compromised.
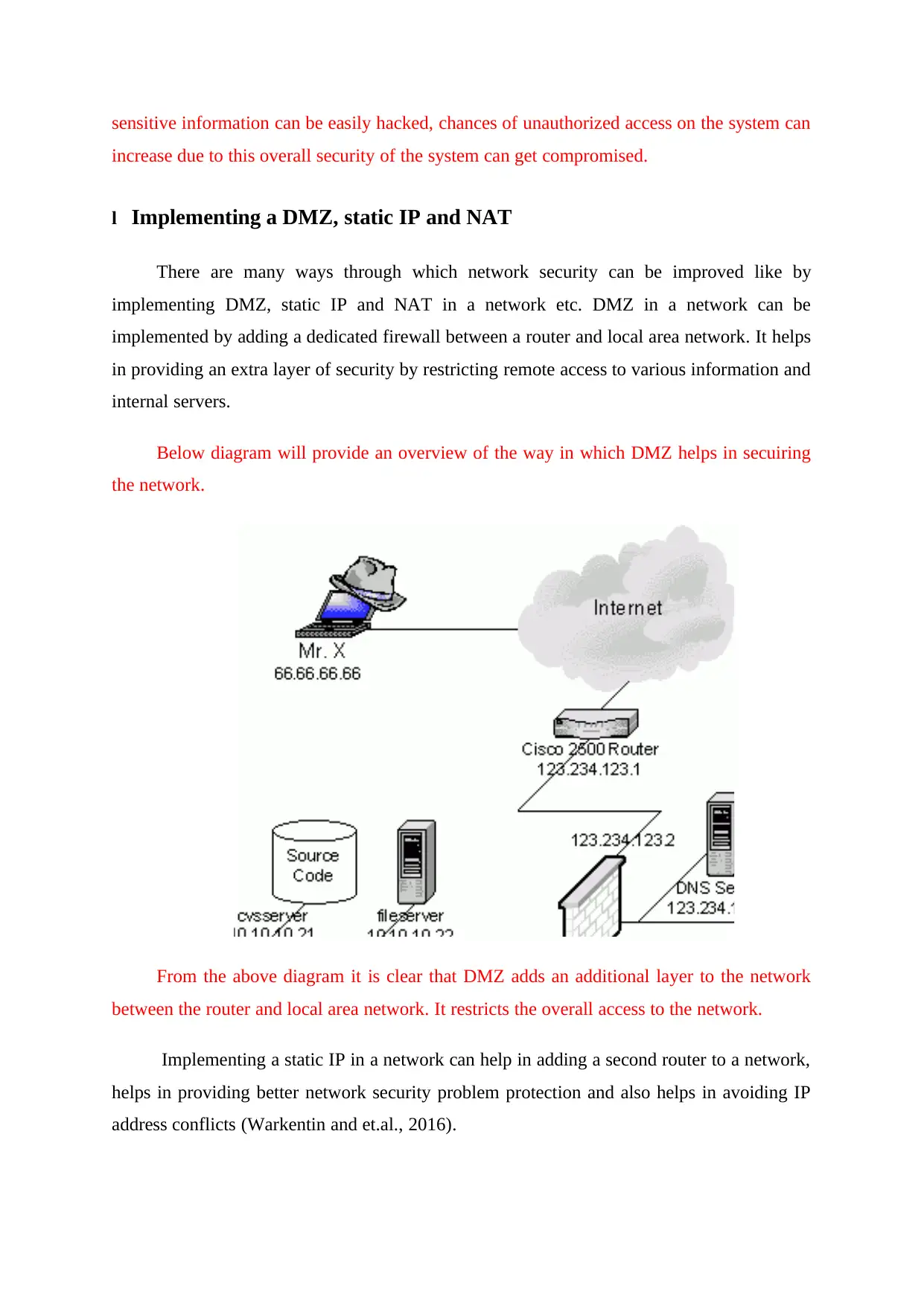
l壱Implementing a DMZ, static IP and NAT
There are many ways through which network security can be improved like by
implementing DMZ, static IP and NAT in a network etc. DMZ in a network can be
implemented by adding a dedicated firewall between a router and local area network. It helps
in providing an extra layer of security by restricting remote access to various information and
internal servers.
Below diagram will provide an overview of the way in which DMZ helps in secuiring
the network.
From the above diagram it is clear that DMZ adds an additional layer to the network
between the router and local area network. It restricts the overall access to the network.
Implementing a static IP in a network can help in adding a second router to a network,
helps in providing better network security problem protection and also helps in avoiding IP
address conflicts (Warkentin and et.al., 2016).
increase due to this overall security of the system can get compromised.
l壱Implementing a DMZ, static IP and NAT
There are many ways through which network security can be improved like by
implementing DMZ, static IP and NAT in a network etc. DMZ in a network can be
implemented by adding a dedicated firewall between a router and local area network. It helps
in providing an extra layer of security by restricting remote access to various information and
internal servers.
Below diagram will provide an overview of the way in which DMZ helps in secuiring
the network.
From the above diagram it is clear that DMZ adds an additional layer to the network
between the router and local area network. It restricts the overall access to the network.
Implementing a static IP in a network can help in adding a second router to a network,
helps in providing better network security problem protection and also helps in avoiding IP
address conflicts (Warkentin and et.al., 2016).
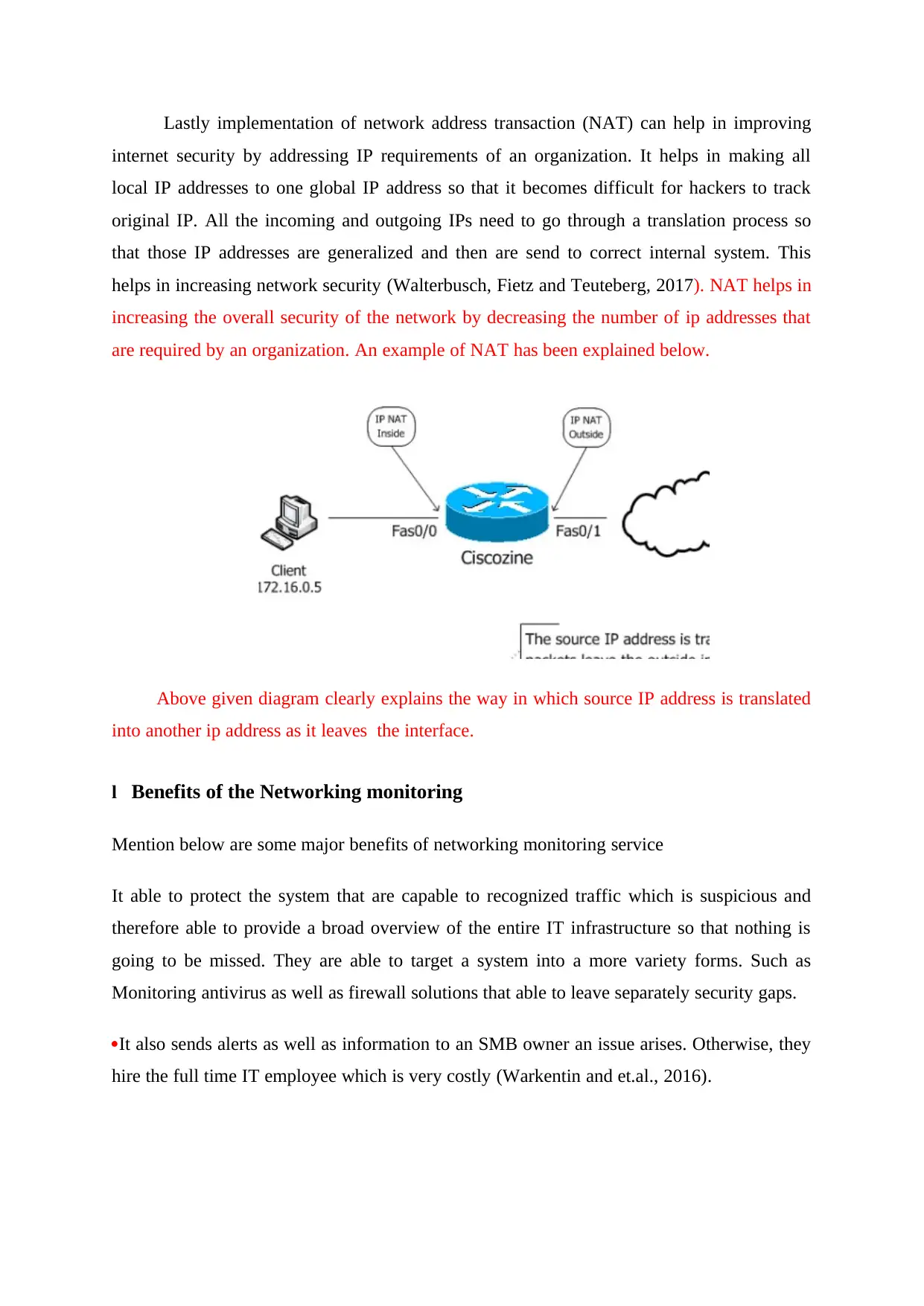
Lastly implementation of network address transaction (NAT) can help in improving
internet security by addressing IP requirements of an organization. It helps in making all
local IP addresses to one global IP address so that it becomes difficult for hackers to track
original IP. All the incoming and outgoing IPs need to go through a translation process so
that those IP addresses are generalized and then are send to correct internal system. This
helps in increasing network security (Walterbusch, Fietz and Teuteberg, 2017). NAT helps in
increasing the overall security of the network by decreasing the number of ip addresses that
are required by an organization. An example of NAT has been explained below.
Above given diagram clearly explains the way in which source IP address is translated
into another ip address as it leaves the interface.
l壱Benefits of the Networking monitoring
Mention below are some major benefits of networking monitoring service
It able to protect the system that are capable to recognized traffic which is suspicious and
therefore able to provide a broad overview of the entire IT infrastructure so that nothing is
going to be missed. They are able to target a system into a more variety forms. Such as
Monitoring antivirus as well as firewall solutions that able to leave separately security gaps.
·It also sends alerts as well as information to an SMB owner an issue arises. Otherwise, they
hire the full time IT employee which is very costly (Warkentin and et.al., 2016).
internet security by addressing IP requirements of an organization. It helps in making all
local IP addresses to one global IP address so that it becomes difficult for hackers to track
original IP. All the incoming and outgoing IPs need to go through a translation process so
that those IP addresses are generalized and then are send to correct internal system. This
helps in increasing network security (Walterbusch, Fietz and Teuteberg, 2017). NAT helps in
increasing the overall security of the network by decreasing the number of ip addresses that
are required by an organization. An example of NAT has been explained below.
Above given diagram clearly explains the way in which source IP address is translated
into another ip address as it leaves the interface.
l壱Benefits of the Networking monitoring
Mention below are some major benefits of networking monitoring service
It able to protect the system that are capable to recognized traffic which is suspicious and
therefore able to provide a broad overview of the entire IT infrastructure so that nothing is
going to be missed. They are able to target a system into a more variety forms. Such as
Monitoring antivirus as well as firewall solutions that able to leave separately security gaps.
·It also sends alerts as well as information to an SMB owner an issue arises. Otherwise, they
hire the full time IT employee which is very costly (Warkentin and et.al., 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





