Advanced Topologies: Evaluating the Security Awareness Program (SAP)
VerifiedAdded on 2022/08/15
|8
|1614
|9
Project
AI Summary
This project report evaluates the effectiveness of a Security Awareness Program (SAP) implemented by Advanced Topologies. The report analyzes the SAP's performance in response to several security breaches, including a virus introduced through an email attachment, a phishing attack, and a physical security breach. The evaluation considers the SAP's strengths and weaknesses in mitigating these threats. The report then proposes security awareness metrics, such as phishing training and a clean desk index, to improve the SAP's effectiveness. It also includes an updated security matrix and outlines training materials, specifying the target audience, delivery method, and frequency. The report concludes by emphasizing the importance of continuous evaluation and improvement of the SAP to protect the company's information assets.

Running head: SECURITY AWARENESS PROGRAM
SECURITY AWARENESS PROGRAM
Name of student
Name of university
Author’s note:
SECURITY AWARENESS PROGRAM
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SECURITY AWARENESS PROGRAM
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Evaluation of SAP......................................................................................................2
Security awareness metrics........................................................................................4
Updated security matrix.............................................................................................5
Training and awareness materials..............................................................................6
References......................................................................................................................7
SECURITY AWARENESS PROGRAM
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Evaluation of SAP......................................................................................................2
Security awareness metrics........................................................................................4
Updated security matrix.............................................................................................5
Training and awareness materials..............................................................................6
References......................................................................................................................7

2
SECURITY AWARENESS PROGRAM
Introduction
The rise of information and technology has led to the development of major sectors in
present business world. The increase in the number of security breaches has increased the
concerns among the companies to implement strong security awareness program. The
Advanced Topologies Company implemented the SAP for ensuring that the security is
provided to all the aspects of the company but still it faced major breaches in Advanced
Topologies company. This report aims to analyse the effectiveness of SAP for various kinds
of data breaches that has led to the loss of significant revenue of the company. Various data
breaches have been discussed in this report.
Discussion
Evaluation of SAP
In the first data breach, where the employees opened the email from an strange source
and exposed the network to the various virus threats, the SAP would be significantly
effective. In this kind of threat, the main issue is that the employees open any email that is
gained from any unverified email address. Any malicious sender could send email to
employees of the company that involves some kind of virus. The SAP in Advanced
Topologies would help in ensuring that no employees open emails in the workplace other
than the verified users. It would include the guidelines that emails would only be opened
from employees of the organisation and the clients of the organisation. No other email from
other users would be accessed in the company systems. This protocol would ensure that no
email has been accessed using the company resources.
Phishing is the kind of attempting fraud for gaining various kinds of critical
information ranging from the passwords, usernames as well as the details of credit cards by
effectively disguising anyone as trustworthy entity in any electronic communication. It is
SECURITY AWARENESS PROGRAM
Introduction
The rise of information and technology has led to the development of major sectors in
present business world. The increase in the number of security breaches has increased the
concerns among the companies to implement strong security awareness program. The
Advanced Topologies Company implemented the SAP for ensuring that the security is
provided to all the aspects of the company but still it faced major breaches in Advanced
Topologies company. This report aims to analyse the effectiveness of SAP for various kinds
of data breaches that has led to the loss of significant revenue of the company. Various data
breaches have been discussed in this report.
Discussion
Evaluation of SAP
In the first data breach, where the employees opened the email from an strange source
and exposed the network to the various virus threats, the SAP would be significantly
effective. In this kind of threat, the main issue is that the employees open any email that is
gained from any unverified email address. Any malicious sender could send email to
employees of the company that involves some kind of virus. The SAP in Advanced
Topologies would help in ensuring that no employees open emails in the workplace other
than the verified users. It would include the guidelines that emails would only be opened
from employees of the organisation and the clients of the organisation. No other email from
other users would be accessed in the company systems. This protocol would ensure that no
email has been accessed using the company resources.
Phishing is the kind of attempting fraud for gaining various kinds of critical
information ranging from the passwords, usernames as well as the details of credit cards by
effectively disguising anyone as trustworthy entity in any electronic communication. It is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SECURITY AWARENESS PROGRAM
commonly executed with the help of instant messaging or email spoofing and it frequently
directs the users in entering the personal information within any fake website that matches
look as well as the feel of legitimate site. Attacks of phishing could be described as the
example of social engineering method that is being utilised for deceiving the users. The users
are frequently lured by the communications claiming in being from any trusted sender, for
example from the social websites, auction sites, the banks, online payment processors or the
IT administrators. In the situation of Advanced Topologies, it could be observed that the
employees of the organisation has accessed the email from the unverified users and opened
an email that comprised of viruses. When this email was opened, it asked for sensitive
information and the employees gave the critical information without verifying the validity of
the email. With the help of SAP in the company, this kind of threat could also be avoided
efficiently. The SAP would include the guideline of not opening any email from unverified
users and if any email asks for some kind of critical information regarding the company and
ask for any login details to websites, then it should not be provided. The company or its
clients would not ask for sensitive information over the emails and any other person asking
for credentials should not be provided with the sensitive information.
In the third situation where an unknown visitor entered the premises of the company
and stole the valuable belongings of the company employees, the implementation of SAP
would be beneficial for ensuring that no unauthorised person has entered the company
premises. The SAP implemented in the company would ensure that all the visitors in the
company should be provided with a visitor card that would enter the time and date at which
the visitors entered the premises. Any person without the visitor card would not be allowed to
enter. The SAP would ensure that the use of any kind of smartphone would not be done in the
company working hours and the laptop of the company would be tagged with RFID tags. If
any employee or any other person is trying to go out of the company premises with the
SECURITY AWARENESS PROGRAM
commonly executed with the help of instant messaging or email spoofing and it frequently
directs the users in entering the personal information within any fake website that matches
look as well as the feel of legitimate site. Attacks of phishing could be described as the
example of social engineering method that is being utilised for deceiving the users. The users
are frequently lured by the communications claiming in being from any trusted sender, for
example from the social websites, auction sites, the banks, online payment processors or the
IT administrators. In the situation of Advanced Topologies, it could be observed that the
employees of the organisation has accessed the email from the unverified users and opened
an email that comprised of viruses. When this email was opened, it asked for sensitive
information and the employees gave the critical information without verifying the validity of
the email. With the help of SAP in the company, this kind of threat could also be avoided
efficiently. The SAP would include the guideline of not opening any email from unverified
users and if any email asks for some kind of critical information regarding the company and
ask for any login details to websites, then it should not be provided. The company or its
clients would not ask for sensitive information over the emails and any other person asking
for credentials should not be provided with the sensitive information.
In the third situation where an unknown visitor entered the premises of the company
and stole the valuable belongings of the company employees, the implementation of SAP
would be beneficial for ensuring that no unauthorised person has entered the company
premises. The SAP implemented in the company would ensure that all the visitors in the
company should be provided with a visitor card that would enter the time and date at which
the visitors entered the premises. Any person without the visitor card would not be allowed to
enter. The SAP would ensure that the use of any kind of smartphone would not be done in the
company working hours and the laptop of the company would be tagged with RFID tags. If
any employee or any other person is trying to go out of the company premises with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SECURITY AWARENESS PROGRAM
resources of the company, proper approval should be taken from the top management and the
same would be relayed to the security officials at the gate. Only the verified systems and
personal resources would be allowed to pass through the gate and no unverified devices
would be allowed to pass. It would ensure that no resources of the company is taken outside
the premises without proper approval from the management of the company.
Security awareness metrics
The security awareness metrics that are required to be implemented in the company
SAP are as follows:
Phishing training: The phishing training could be considered as relatively easy
method of gaining the metrics (Peltier, 2016). Prior the training is done, the baseline is
required to be implemented by the recording of number of employees who falls into the trap
of social engineering attacks and the number of file reports on the suspicious emails. After
the training has been done, test campaign has to be executed with the help of the phony
emails of phishing (Banfield, 2016). It has to be considered to monitor the extent to which the
employees have been able to gain benefits from the training, and therefore it is required to
vary the times as well as the tactics of any fake emails. By the comparison of the behaviour
of employees prior and after conducting the training, the effectiveness could be measured
(Bogale, Lessa & Negash, 2019).
Clean desk index: Keeping the track of the applicability of the team of Clean Desk
Principle is considered as the key. It denotes to the knowledge of the number of employees of
the organisation who leave their screens on without proper password protection, keeping the
data on who has forgotten to properly shred the sensitive documents prior putting them in the
trash (Bogale, Lessa & Negash, 2019).
SECURITY AWARENESS PROGRAM
resources of the company, proper approval should be taken from the top management and the
same would be relayed to the security officials at the gate. Only the verified systems and
personal resources would be allowed to pass through the gate and no unverified devices
would be allowed to pass. It would ensure that no resources of the company is taken outside
the premises without proper approval from the management of the company.
Security awareness metrics
The security awareness metrics that are required to be implemented in the company
SAP are as follows:
Phishing training: The phishing training could be considered as relatively easy
method of gaining the metrics (Peltier, 2016). Prior the training is done, the baseline is
required to be implemented by the recording of number of employees who falls into the trap
of social engineering attacks and the number of file reports on the suspicious emails. After
the training has been done, test campaign has to be executed with the help of the phony
emails of phishing (Banfield, 2016). It has to be considered to monitor the extent to which the
employees have been able to gain benefits from the training, and therefore it is required to
vary the times as well as the tactics of any fake emails. By the comparison of the behaviour
of employees prior and after conducting the training, the effectiveness could be measured
(Bogale, Lessa & Negash, 2019).
Clean desk index: Keeping the track of the applicability of the team of Clean Desk
Principle is considered as the key. It denotes to the knowledge of the number of employees of
the organisation who leave their screens on without proper password protection, keeping the
data on who has forgotten to properly shred the sensitive documents prior putting them in the
trash (Bogale, Lessa & Negash, 2019).
5
SECURITY AWARENESS PROGRAM
The reason for selecting these metrics is to ensure that the two most frequent threats
to the company is tackled and all the information regarding the threats have been conveyed to
the employees of the company.
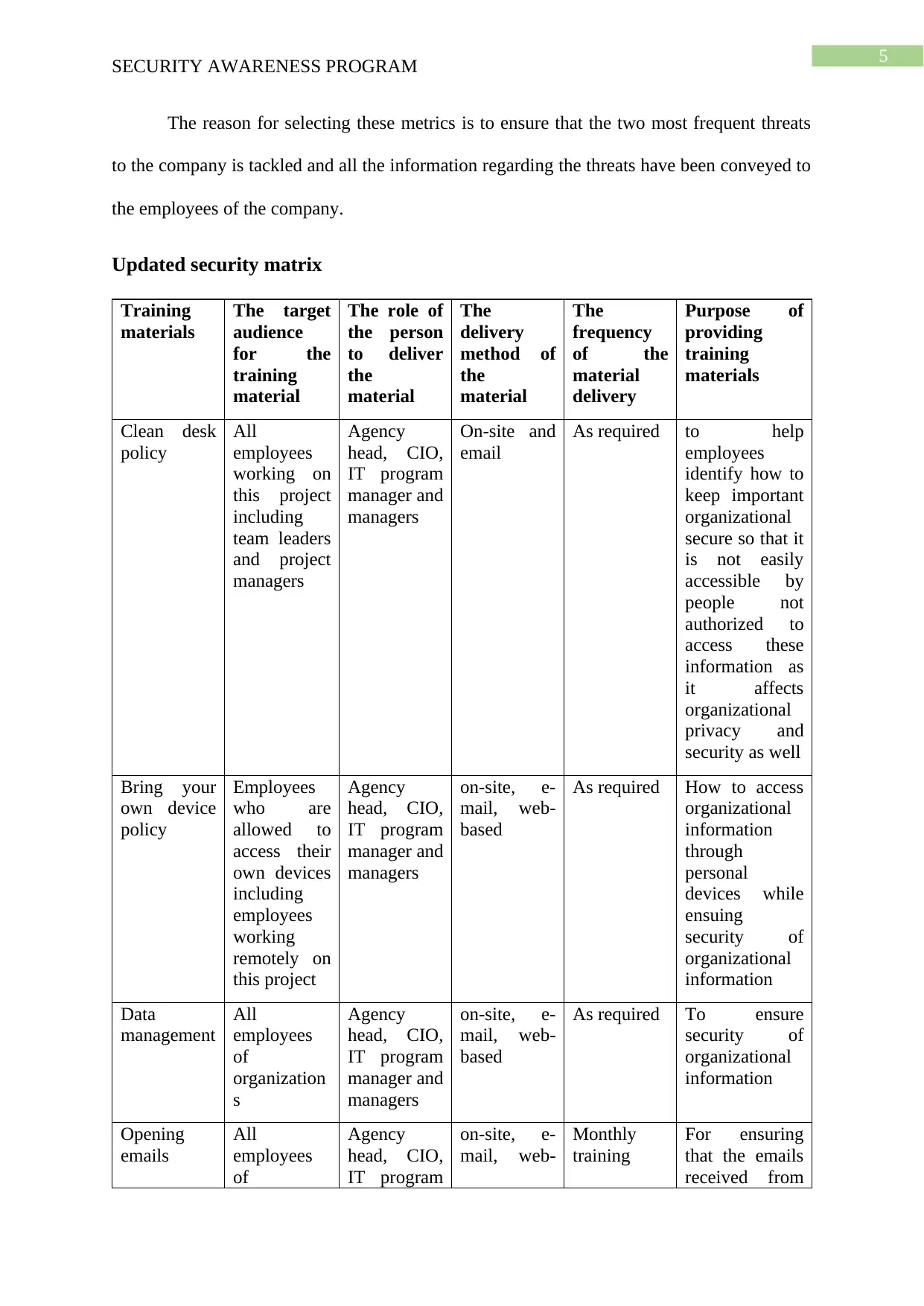
Updated security matrix
Training
materials
The target
audience
for the
training
material
The role of
the person
to deliver
the
material
The
delivery
method of
the
material
The
frequency
of the
material
delivery
Purpose of
providing
training
materials
Clean desk
policy
All
employees
working on
this project
including
team leaders
and project
managers
Agency
head, CIO,
IT program
manager and
managers
On-site and
email
As required to help
employees
identify how to
keep important
organizational
secure so that it
is not easily
accessible by
people not
authorized to
access these
information as
it affects
organizational
privacy and
security as well
Bring your
own device
policy
Employees
who are
allowed to
access their
own devices
including
employees
working
remotely on
this project
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required How to access
organizational
information
through
personal
devices while
ensuing
security of
organizational
information
Data
management
All
employees
of
organization
s
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required To ensure
security of
organizational
information
Opening
emails
All
employees
of
Agency
head, CIO,
IT program
on-site, e-
mail, web-
Monthly
training
For ensuring
that the emails
received from
SECURITY AWARENESS PROGRAM
The reason for selecting these metrics is to ensure that the two most frequent threats
to the company is tackled and all the information regarding the threats have been conveyed to
the employees of the company.
Updated security matrix
Training
materials
The target
audience
for the
training
material
The role of
the person
to deliver
the
material
The
delivery
method of
the
material
The
frequency
of the
material
delivery
Purpose of
providing
training
materials
Clean desk
policy
All
employees
working on
this project
including
team leaders
and project
managers
Agency
head, CIO,
IT program
manager and
managers
On-site and
As required to help
employees
identify how to
keep important
organizational
secure so that it
is not easily
accessible by
people not
authorized to
access these
information as
it affects
organizational
privacy and
security as well
Bring your
own device
policy
Employees
who are
allowed to
access their
own devices
including
employees
working
remotely on
this project
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required How to access
organizational
information
through
personal
devices while
ensuing
security of
organizational
information
Data
management
All
employees
of
organization
s
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required To ensure
security of
organizational
information
Opening
emails
All
employees
of
Agency
head, CIO,
IT program
on-site, e-
mail, web-
Monthly
training
For ensuring
that the emails
received from
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
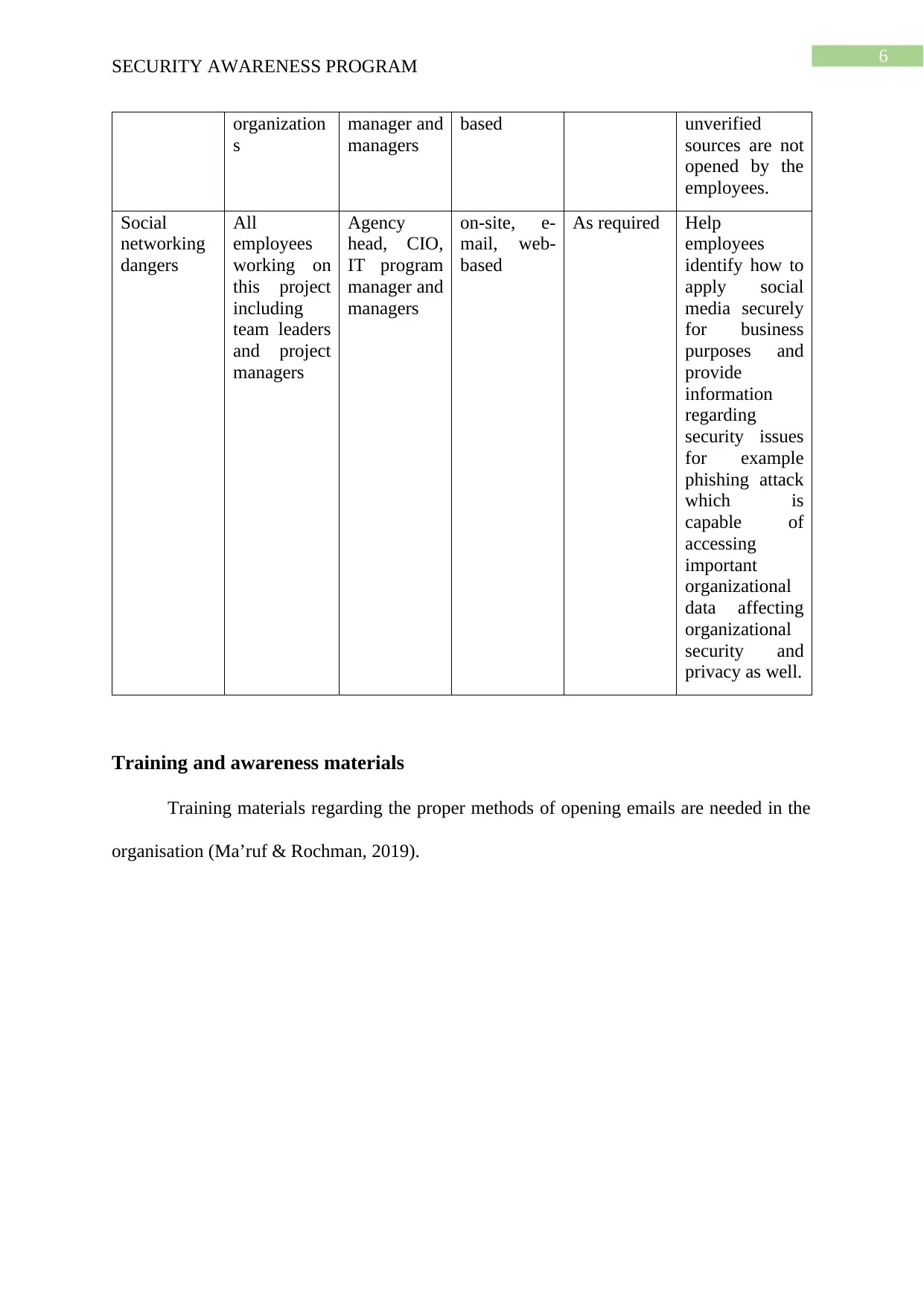
6
SECURITY AWARENESS PROGRAM
organization
s
manager and
managers
based unverified
sources are not
opened by the
employees.
Social
networking
dangers
All
employees
working on
this project
including
team leaders
and project
managers
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required Help
employees
identify how to
apply social
media securely
for business
purposes and
provide
information
regarding
security issues
for example
phishing attack
which is
capable of
accessing
important
organizational
data affecting
organizational
security and
privacy as well.
Training and awareness materials
Training materials regarding the proper methods of opening emails are needed in the
organisation (Ma’ruf & Rochman, 2019).
SECURITY AWARENESS PROGRAM
organization
s
manager and
managers
based unverified
sources are not
opened by the
employees.
Social
networking
dangers
All
employees
working on
this project
including
team leaders
and project
managers
Agency
head, CIO,
IT program
manager and
managers
on-site, e-
mail, web-
based
As required Help
employees
identify how to
apply social
media securely
for business
purposes and
provide
information
regarding
security issues
for example
phishing attack
which is
capable of
accessing
important
organizational
data affecting
organizational
security and
privacy as well.
Training and awareness materials
Training materials regarding the proper methods of opening emails are needed in the
organisation (Ma’ruf & Rochman, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SECURITY AWARENESS PROGRAM
References
Banfield, J. M. (2016). A study of information security awareness program effectiveness in
predicting end-user security behavior.
Bogale, M., Lessa, L., & Negash, S. (2019). Building an Information Security Awareness
Program for a Bank: Case from Ethiopia.
Ma’ruf, K. F., & Rochman, M. M. (2019). GUIDELINES FOR DEVELOPING
INFORMATION SECURITY TRAINING AND AWARENESS PROGRAMS IN
GOVERNMENT AGENCY: THE PERSPECTIVE OF ADDIE INSTRUCTIONAL
DESIGN MODELS (A CASE STUDY IN INDONESIAN GOVERNMENT
AGENCY). PEOPLE: International Journal of Social Sciences, 5(2).
Peltier, T. R. (2016). Security awareness program. In Information Security Policies,
Procedures, and Standards (pp. 163-174). Auerbach Publications.
Schroeder, J. (2017). Advanced Persistent Training: Take Your Security Awareness Program
to the Next Level. Apress.
SECURITY AWARENESS PROGRAM
References
Banfield, J. M. (2016). A study of information security awareness program effectiveness in
predicting end-user security behavior.
Bogale, M., Lessa, L., & Negash, S. (2019). Building an Information Security Awareness
Program for a Bank: Case from Ethiopia.
Ma’ruf, K. F., & Rochman, M. M. (2019). GUIDELINES FOR DEVELOPING
INFORMATION SECURITY TRAINING AND AWARENESS PROGRAMS IN
GOVERNMENT AGENCY: THE PERSPECTIVE OF ADDIE INSTRUCTIONAL
DESIGN MODELS (A CASE STUDY IN INDONESIAN GOVERNMENT
AGENCY). PEOPLE: International Journal of Social Sciences, 5(2).
Peltier, T. R. (2016). Security awareness program. In Information Security Policies,
Procedures, and Standards (pp. 163-174). Auerbach Publications.
Schroeder, J. (2017). Advanced Persistent Training: Take Your Security Awareness Program
to the Next Level. Apress.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





