Comprehensive Information Security Report: Algorithms and Methods
VerifiedAdded on 2021/05/31
|14
|2481
|157
Report
AI Summary
This report provides a comprehensive overview of information security, covering key aspects such as antiviruses, hash algorithms, key management, and load balancing algorithms. The report begins by discussing various antivirus software, their features, and comparisons, including Windows Defender, Bid-defender, Smadav, and Norton antivirus. It then delves into hash algorithms, explaining Message Digest, Secure Hash Algorithm (SHA), Whirlpool, and RIPEMD, along with a comparison of their properties. Furthermore, the report explores the key management lifecycle, detailing the processes of creation, deployment, and monitoring. Finally, it examines load balancing algorithms, including Round Robin, Weighted Round Robin, Source IP Hash, URL Hash, Least Connections, and Server algorithms, providing their advantages and disadvantages. The report aims to provide a detailed understanding of these critical elements in information security.

INFORMATION SECURITY
Name
Course
Date of Submission
1
Name
Course
Date of Submission
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
CHAPTER FOUR...........................................................................................................................4
Introduction..................................................................................................................................4
Antiviruses...................................................................................................................................4
Windows Defender......................................................................................................................4
Bid-defender.................................................................................................................................4
Smadav.........................................................................................................................................4
Norton antivirus..........................................................................................................................4
Antiviruses Features and Comparison.........................................................................................5
Recommendation.............................................................................................................................5
CHAPTER FIVE.............................................................................................................................6
HASH ALGORITHMS................................................................................................................6
Introduction..................................................................................................................................6
Message Digest............................................................................................................................6
Secure hash algorithm..................................................................................................................6
Whirpool......................................................................................................................................6
RIMED ........................................................................................................................................6
Comparison between Hashcodes.................................................................................................7
CHAPTER SIX................................................................................................................................8
Key management life cycle..........................................................................................................8
Creation....................................................................................................................................9
Deployment..............................................................................................................................9
Monitoring..............................................................................................................................10
CHAPTER SEVEN.......................................................................................................................11
LOAD BALANCING ALGORITHMS.....................................................................................11
References......................................................................................................................................14
2
CHAPTER FOUR...........................................................................................................................4
Introduction..................................................................................................................................4
Antiviruses...................................................................................................................................4
Windows Defender......................................................................................................................4
Bid-defender.................................................................................................................................4
Smadav.........................................................................................................................................4
Norton antivirus..........................................................................................................................4
Antiviruses Features and Comparison.........................................................................................5
Recommendation.............................................................................................................................5
CHAPTER FIVE.............................................................................................................................6
HASH ALGORITHMS................................................................................................................6
Introduction..................................................................................................................................6
Message Digest............................................................................................................................6
Secure hash algorithm..................................................................................................................6
Whirpool......................................................................................................................................6
RIMED ........................................................................................................................................6
Comparison between Hashcodes.................................................................................................7
CHAPTER SIX................................................................................................................................8
Key management life cycle..........................................................................................................8
Creation....................................................................................................................................9
Deployment..............................................................................................................................9
Monitoring..............................................................................................................................10
CHAPTER SEVEN.......................................................................................................................11
LOAD BALANCING ALGORITHMS.....................................................................................11
References......................................................................................................................................14
2

3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CHAPTER FOUR
Introduction.
Antiviruses are the software’s that are specifically designed to protect computers against
malicious software or codes by detecting them and removing them hence disinfecting the
computer. There are many types of viruses that can attack the computer this includes Trojans,
worms and droppers each affect computers in different ways. Different antiviruses are designed
to remove malwares from computers .Below is a description and comparison of some antiviruses
and how they are used to remove some malwares in attacked devices (SERGEEVICH,2015).
Antiviruses softwares.
This are software that are specifically designed to protect computers from malware attack. There
are different types of viruses each with different types of features. Some antiviruses are free
products from companies while others are commercialized. Windows defender is free product
from Microsoft windows while others like Kaspersky, smadav, Notan and bid-defender are
commercialized. Each different type of this have different functioning hence differing in their
characteristics. The following outlines the comparison and the description of the above
mentioned antiviruses (ZHENG, 2010).
Windows Defender.
This is a malware software that is in-built in Microsoft operating system. It runs in the
background of the operating system. It a notifies the user if there is any malware attack and
quick scan the system if prompted to do the same to remove some attacks. This is mostly used by
many computers since it comes with the windows operating system as a background application
(Hayash, 2013).
Bid-defender
This is multi-layer commercialized software that defends computers against ransomware
attack .It uses threat detection technique to protect attacks.
Smadav
Specialized in protecting flash disks from attacks.
Norton antivirus.
This protects our pc from internet malwares. There some malwares that are installed to our
computers when we are accessing the internet Norton detects them and remove them.
4
Introduction.
Antiviruses are the software’s that are specifically designed to protect computers against
malicious software or codes by detecting them and removing them hence disinfecting the
computer. There are many types of viruses that can attack the computer this includes Trojans,
worms and droppers each affect computers in different ways. Different antiviruses are designed
to remove malwares from computers .Below is a description and comparison of some antiviruses
and how they are used to remove some malwares in attacked devices (SERGEEVICH,2015).
Antiviruses softwares.
This are software that are specifically designed to protect computers from malware attack. There
are different types of viruses each with different types of features. Some antiviruses are free
products from companies while others are commercialized. Windows defender is free product
from Microsoft windows while others like Kaspersky, smadav, Notan and bid-defender are
commercialized. Each different type of this have different functioning hence differing in their
characteristics. The following outlines the comparison and the description of the above
mentioned antiviruses (ZHENG, 2010).
Windows Defender.
This is a malware software that is in-built in Microsoft operating system. It runs in the
background of the operating system. It a notifies the user if there is any malware attack and
quick scan the system if prompted to do the same to remove some attacks. This is mostly used by
many computers since it comes with the windows operating system as a background application
(Hayash, 2013).
Bid-defender
This is multi-layer commercialized software that defends computers against ransomware
attack .It uses threat detection technique to protect attacks.
Smadav
Specialized in protecting flash disks from attacks.
Norton antivirus.
This protects our pc from internet malwares. There some malwares that are installed to our
computers when we are accessing the internet Norton detects them and remove them.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
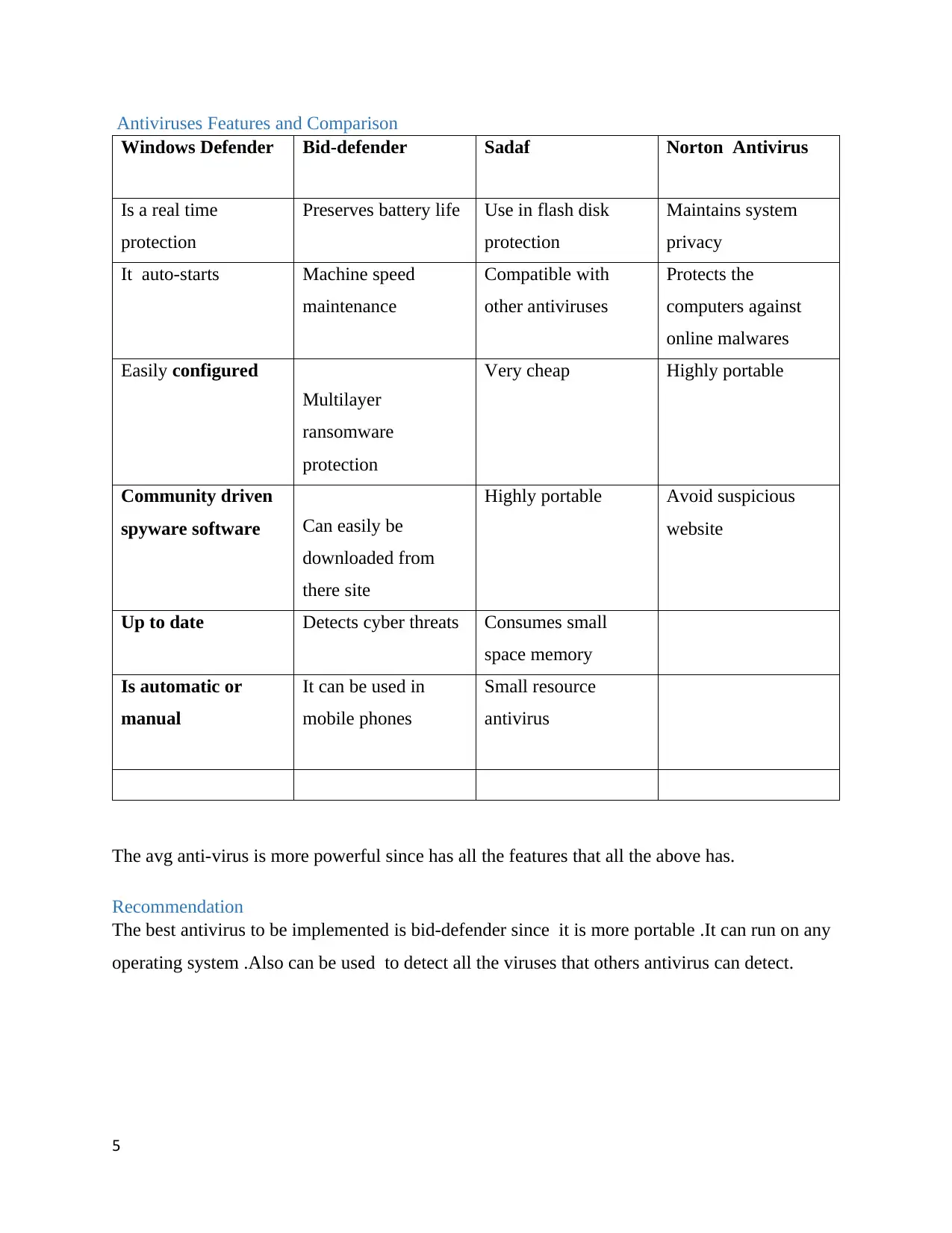
Antiviruses Features and Comparison
Windows Defender Bid-defender Sadaf Norton Antivirus
Is a real time
protection
Preserves battery life Use in flash disk
protection
Maintains system
privacy
It auto-starts Machine speed
maintenance
Compatible with
other antiviruses
Protects the
computers against
online malwares
Easily configured
Multilayer
ransomware
protection
Very cheap Highly portable
Community driven
spyware software Can easily be
downloaded from
there site
Highly portable Avoid suspicious
website
Up to date Detects cyber threats Consumes small
space memory
Is automatic or
manual
It can be used in
mobile phones
Small resource
antivirus
The avg anti-virus is more powerful since has all the features that all the above has.
Recommendation
The best antivirus to be implemented is bid-defender since it is more portable .It can run on any
operating system .Also can be used to detect all the viruses that others antivirus can detect.
5
Windows Defender Bid-defender Sadaf Norton Antivirus
Is a real time
protection
Preserves battery life Use in flash disk
protection
Maintains system
privacy
It auto-starts Machine speed
maintenance
Compatible with
other antiviruses
Protects the
computers against
online malwares
Easily configured
Multilayer
ransomware
protection
Very cheap Highly portable
Community driven
spyware software Can easily be
downloaded from
there site
Highly portable Avoid suspicious
website
Up to date Detects cyber threats Consumes small
space memory
Is automatic or
manual
It can be used in
mobile phones
Small resource
antivirus
The avg anti-virus is more powerful since has all the features that all the above has.
Recommendation
The best antivirus to be implemented is bid-defender since it is more portable .It can run on any
operating system .Also can be used to detect all the viruses that others antivirus can detect.
5
CHAPTER FIVE
HASH ALGORITHMS
Introduction
The Internet is wide with millions of users leading to terabytes of data. According reports, the
amount of content on the internet doubles every six months. With this sort of development, it is
difficult to miss anything in the web, so more information structures and calculations for putting
away and getting to information. So what isn't right with customary information structures like
Arrays and Linked Lists? Assume we have an expansive informational collection put away in a
cluster. The measure of time required to look into a component in the exhibit is either O(log n) or
O( n) in view of whether the cluster is arranged or not. On chance that the cluster is arranged
then a strategy, for example, paired hunt can be utilized to look through the exhibit. Something
else, the cluster must be looked. Due to this many algorithms have been created this include
message digest, secure hash algorithms and whirlpool have been invented.
Message Digest
Is a cryptographic hash work made up of a series of digits from restricted hashing equation?
Message digests are anticipated to provide security to bits of information by recognizing any
change to information or media provided.
Secure hash algorithm
This is an algorithm which takes an input ad produces a 160 bit hash value which is referred to as
a message digest.
Whirlpool
Is a cryptographic hash work. It was outlined by Vincent Ragmen (co-maker of the Advanced
Encryption Standard) and Paulo S. L. M. Barret, who initially depicted it in 2000. The hash has
been prescribed by the NESSIE venture.
RIMEPD.
This mean is a member of the hash function group developed by Leuven and Belgium.
6
HASH ALGORITHMS
Introduction
The Internet is wide with millions of users leading to terabytes of data. According reports, the
amount of content on the internet doubles every six months. With this sort of development, it is
difficult to miss anything in the web, so more information structures and calculations for putting
away and getting to information. So what isn't right with customary information structures like
Arrays and Linked Lists? Assume we have an expansive informational collection put away in a
cluster. The measure of time required to look into a component in the exhibit is either O(log n) or
O( n) in view of whether the cluster is arranged or not. On chance that the cluster is arranged
then a strategy, for example, paired hunt can be utilized to look through the exhibit. Something
else, the cluster must be looked. Due to this many algorithms have been created this include
message digest, secure hash algorithms and whirlpool have been invented.
Message Digest
Is a cryptographic hash work made up of a series of digits from restricted hashing equation?
Message digests are anticipated to provide security to bits of information by recognizing any
change to information or media provided.
Secure hash algorithm
This is an algorithm which takes an input ad produces a 160 bit hash value which is referred to as
a message digest.
Whirlpool
Is a cryptographic hash work. It was outlined by Vincent Ragmen (co-maker of the Advanced
Encryption Standard) and Paulo S. L. M. Barret, who initially depicted it in 2000. The hash has
been prescribed by the NESSIE venture.
RIMEPD.
This mean is a member of the hash function group developed by Leuven and Belgium.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
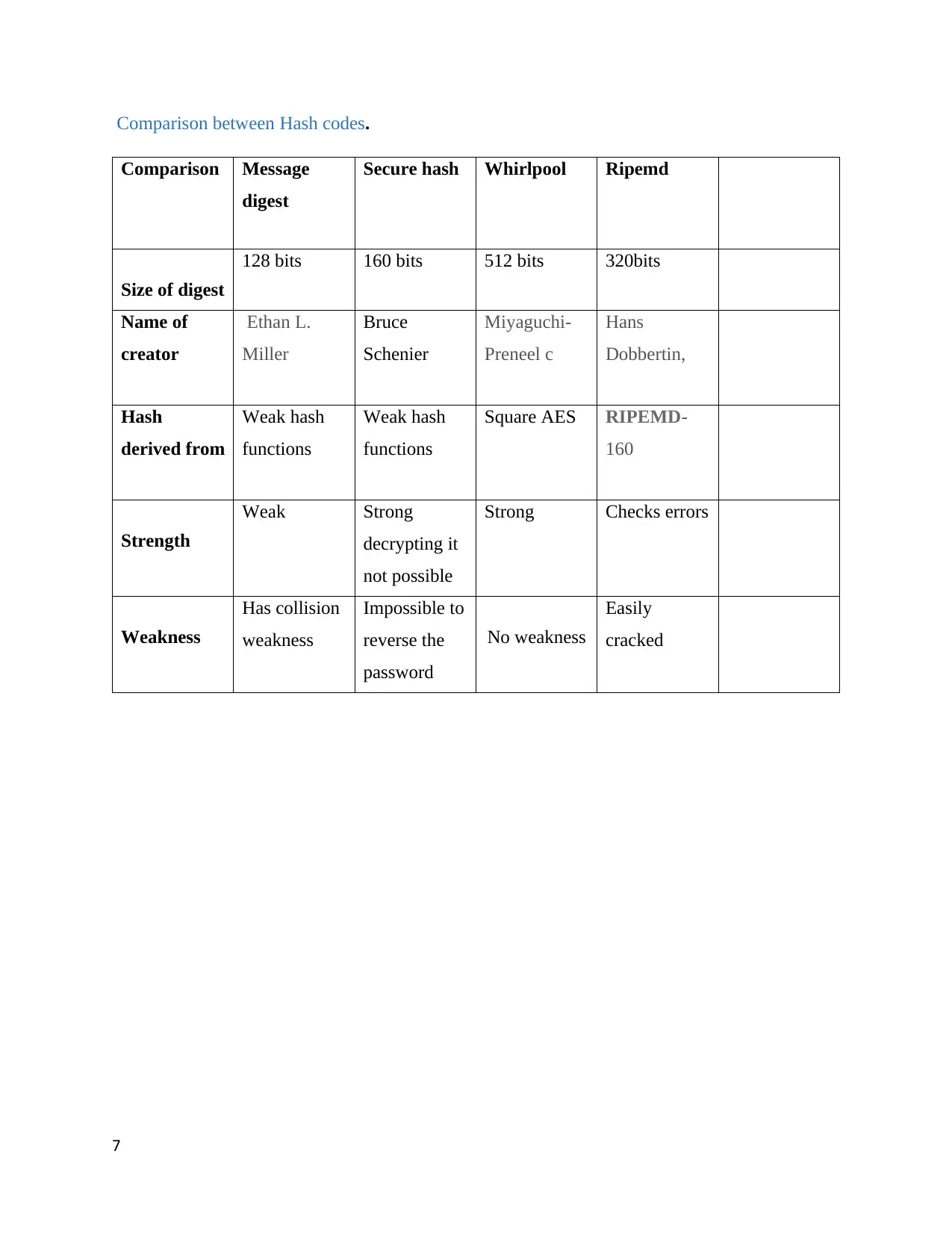
Comparison between Hash codes.
Comparison Message
digest
Secure hash Whirlpool Ripemd
Size of digest
128 bits 160 bits 512 bits 320bits
Name of
creator
Ethan L.
Miller
Bruce
Schenier
Miyaguchi-
Preneel c
Hans
Dobbertin,
Hash
derived from
Weak hash
functions
Weak hash
functions
Square AES RIPEMD-
160
Strength
Weak Strong
decrypting it
not possible
Strong Checks errors
Weakness
Has collision
weakness
Impossible to
reverse the
password
No weakness
Easily
cracked
7
Comparison Message
digest
Secure hash Whirlpool Ripemd
Size of digest
128 bits 160 bits 512 bits 320bits
Name of
creator
Ethan L.
Miller
Bruce
Schenier
Miyaguchi-
Preneel c
Hans
Dobbertin,
Hash
derived from
Weak hash
functions
Weak hash
functions
Square AES RIPEMD-
160
Strength
Weak Strong
decrypting it
not possible
Strong Checks errors
Weakness
Has collision
weakness
Impossible to
reverse the
password
No weakness
Easily
cracked
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
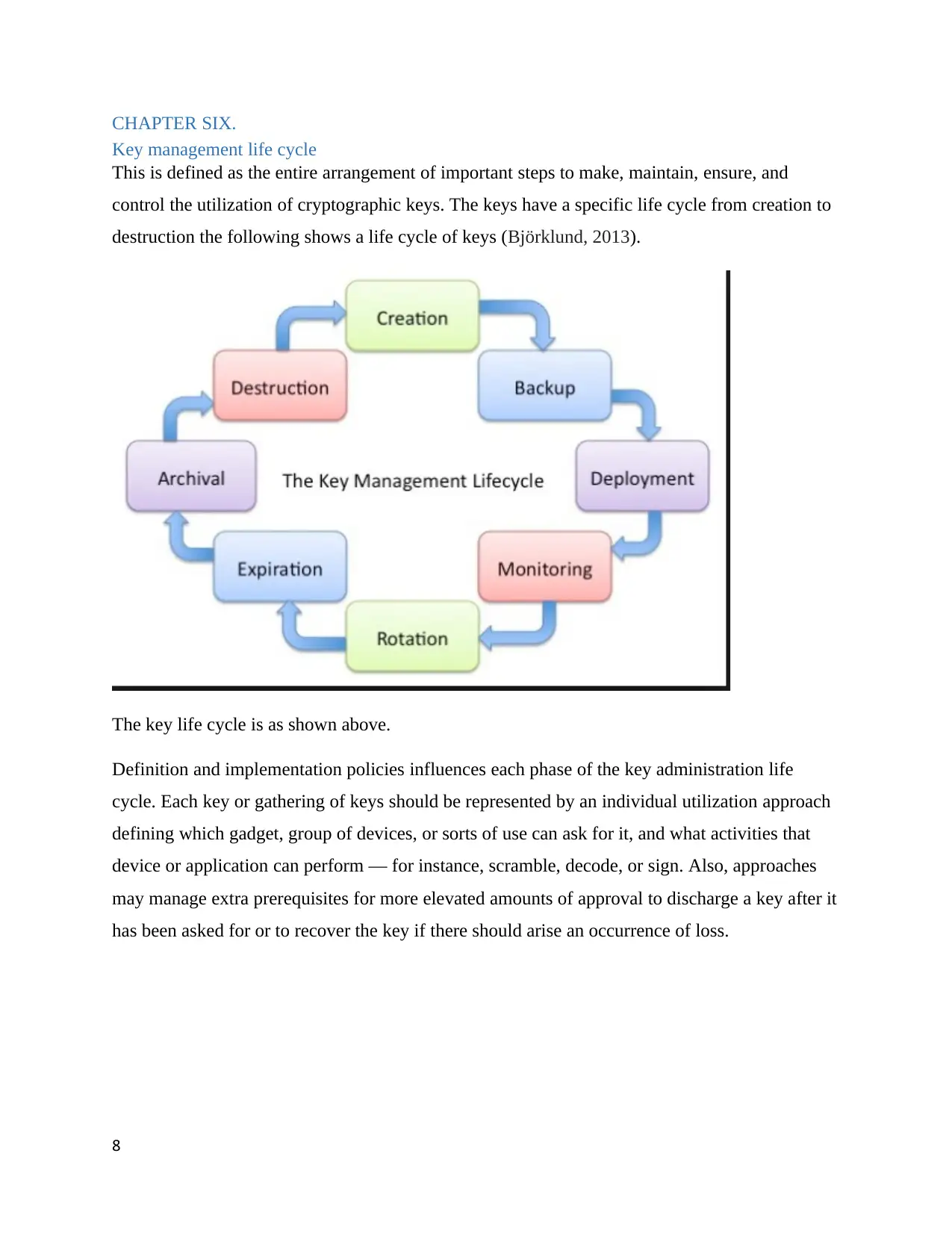
CHAPTER SIX.
Key management life cycle
This is defined as the entire arrangement of important steps to make, maintain, ensure, and
control the utilization of cryptographic keys. The keys have a specific life cycle from creation to
destruction the following shows a life cycle of keys (Björklund, 2013).
The key life cycle is as shown above.
Definition and implementation policies influences each phase of the key administration life
cycle. Each key or gathering of keys should be represented by an individual utilization approach
defining which gadget, group of devices, or sorts of use can ask for it, and what activities that
device or application can perform — for instance, scramble, decode, or sign. Also, approaches
may manage extra prerequisites for more elevated amounts of approval to discharge a key after it
has been asked for or to recover the key if there should arise an occurrence of loss.
8
Key management life cycle
This is defined as the entire arrangement of important steps to make, maintain, ensure, and
control the utilization of cryptographic keys. The keys have a specific life cycle from creation to
destruction the following shows a life cycle of keys (Björklund, 2013).
The key life cycle is as shown above.
Definition and implementation policies influences each phase of the key administration life
cycle. Each key or gathering of keys should be represented by an individual utilization approach
defining which gadget, group of devices, or sorts of use can ask for it, and what activities that
device or application can perform — for instance, scramble, decode, or sign. Also, approaches
may manage extra prerequisites for more elevated amounts of approval to discharge a key after it
has been asked for or to recover the key if there should arise an occurrence of loss.
8

Creation.
Is the underlying stage in the key administration lifecycle. A safe environment should be used in
key creation, this might consolidate the need to fulfill the requirements for separation of duties.
Mostly, the key made will be a symmetric key. The key developed should be of high quality and
reliable mainly developed from series of random numbers. Key value (should assessed in number
of bits) is routinely in perspective of the assignment real era of the information being guaranteed,
joined with the intervals it takes to break (by methods for savage constraining) keys within the
given crypto system. For example, if you have information that is real for long time, by then
brute keys that can withstand attacks for longer than 5 years are required. Instead of picking a
fitting key excellent quality, one should in like manner attempt to choose an encryption count
that has been exposed to peer study and scholarly investigation. Arbitrary encryption designs
should be abstained from, educing the mantra "if figuring is required to be kept secret, by then it
apparently suggests that it can't tolerate analysis and is thusly an awful technique.
Backup
Before creation of another key, it is preferred that key reinforcement to be made. The
reinforcement could basically involve coming up with the way to store in outer media (e.g., CD,
DVD, USB drive) and setting away it in a somatic vault. Or on the other hand, it might be
valuable to back it up using a current conventional reinforcement arrangement (nearby or
organized)
Deployment
Currently it is significantly recommended that a new encryption key be encoded by an open key
before approval by the association. This idea gives a method to parcel of obligations in an area
where key business practices are not by any means confined inside a lone system. Many controls
system may need this segment of assurances to confirm that no single substance can influence a
key, to pass on a key, and after that self-emphatically get to and translate information without
countersignature (Fuller, 2010).
Monitoring
Observing may be its own development stage as it could essentially be a region of duty that is
corresponding to the entire key association lifecycle. There are three key practices that should be
watched out in an oraganization. This incorporate (Stark, 2015)
It is basic to monitor unauthorized managerial access to crypto configurations to ensure
that unauthorized key association assignments are not performed. Any sort of
9
Is the underlying stage in the key administration lifecycle. A safe environment should be used in
key creation, this might consolidate the need to fulfill the requirements for separation of duties.
Mostly, the key made will be a symmetric key. The key developed should be of high quality and
reliable mainly developed from series of random numbers. Key value (should assessed in number
of bits) is routinely in perspective of the assignment real era of the information being guaranteed,
joined with the intervals it takes to break (by methods for savage constraining) keys within the
given crypto system. For example, if you have information that is real for long time, by then
brute keys that can withstand attacks for longer than 5 years are required. Instead of picking a
fitting key excellent quality, one should in like manner attempt to choose an encryption count
that has been exposed to peer study and scholarly investigation. Arbitrary encryption designs
should be abstained from, educing the mantra "if figuring is required to be kept secret, by then it
apparently suggests that it can't tolerate analysis and is thusly an awful technique.
Backup
Before creation of another key, it is preferred that key reinforcement to be made. The
reinforcement could basically involve coming up with the way to store in outer media (e.g., CD,
DVD, USB drive) and setting away it in a somatic vault. Or on the other hand, it might be
valuable to back it up using a current conventional reinforcement arrangement (nearby or
organized)
Deployment
Currently it is significantly recommended that a new encryption key be encoded by an open key
before approval by the association. This idea gives a method to parcel of obligations in an area
where key business practices are not by any means confined inside a lone system. Many controls
system may need this segment of assurances to confirm that no single substance can influence a
key, to pass on a key, and after that self-emphatically get to and translate information without
countersignature (Fuller, 2010).
Monitoring
Observing may be its own development stage as it could essentially be a region of duty that is
corresponding to the entire key association lifecycle. There are three key practices that should be
watched out in an oraganization. This incorporate (Stark, 2015)
It is basic to monitor unauthorized managerial access to crypto configurations to ensure
that unauthorized key association assignments are not performed. Any sort of
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

unauthorized movement could be have been authentic tonice results for your structure,
and for your data
Checking the key in progress is in likewise fundamental to confirm that the key has been
created and sent truly. In case a tainted key is passed on too quickly without honest to
goodness checking, the results could be discouraging. Correspondingly, if a fault in the
crypto structure happens, by then the results could moreover encroach upon advantage,
with a negative impact to the business.
The managers should be responsible for the key being used.
Rotation.
Keys rotation is the same as key deployment. The aim of this process is to bring a new
key by replacing the old one. The process is very hectic unless all the other processes a
have been carried out in well-known criteria. Then this can be focused on the key
exchange criteria without going through the other stages. This can only happen if no data
in the system is still encrypted by the old key if this happens then the all process fails .
Expiration
The choice of the lifespan of key determines the validity time of data encrypted by the
same key. The minimum lifespan of key to expire is one year and much greater for keys
protecting sensitive data. The maximum time key should exists is 5 years. The following
steps are involved changing the key.
Recovering of data with archived keys
Ensuring that the archived key has been well secured.
Include the archived keys as part of routing procedures
After all the data has been decrypted then the key can now be replaced so that it can
encrypt the available data in the system.
10
and for your data
Checking the key in progress is in likewise fundamental to confirm that the key has been
created and sent truly. In case a tainted key is passed on too quickly without honest to
goodness checking, the results could be discouraging. Correspondingly, if a fault in the
crypto structure happens, by then the results could moreover encroach upon advantage,
with a negative impact to the business.
The managers should be responsible for the key being used.
Rotation.
Keys rotation is the same as key deployment. The aim of this process is to bring a new
key by replacing the old one. The process is very hectic unless all the other processes a
have been carried out in well-known criteria. Then this can be focused on the key
exchange criteria without going through the other stages. This can only happen if no data
in the system is still encrypted by the old key if this happens then the all process fails .
Expiration
The choice of the lifespan of key determines the validity time of data encrypted by the
same key. The minimum lifespan of key to expire is one year and much greater for keys
protecting sensitive data. The maximum time key should exists is 5 years. The following
steps are involved changing the key.
Recovering of data with archived keys
Ensuring that the archived key has been well secured.
Include the archived keys as part of routing procedures
After all the data has been decrypted then the key can now be replaced so that it can
encrypt the available data in the system.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CHAPTER SEVEN
LOAD BALANCING ALGORITHMS.
Powerful load balancers shrewdly figure out which gadget inside a given server cultivate is best
ready to process an approaching information bundle. Doing as such requires calculations
customized to disseminate stacks particularly. The following are of the algorithms that help the
servers accomplish their tasks. The following shows there advantages and disadvantages
(Randles, 2010).
LOAD
BALANCERS
ALGORITHM
Advantages Disadvantages
Roundbin
All the processes are given the
same priority
Starvation does not occur in
the processes
Specific time given for each
process to execute
Long processes given time to
complete executing
Short processes
have to wait for a
long time.
Processes run until
it finishes.
Does not give
priority to more
important tasks.
Frustrates those
with medium
length tasks
Weighed roundbin It is very first Complex
11
LOAD BALANCING ALGORITHMS.
Powerful load balancers shrewdly figure out which gadget inside a given server cultivate is best
ready to process an approaching information bundle. Doing as such requires calculations
customized to disseminate stacks particularly. The following are of the algorithms that help the
servers accomplish their tasks. The following shows there advantages and disadvantages
(Randles, 2010).
LOAD
BALANCERS
ALGORITHM
Advantages Disadvantages
Roundbin
All the processes are given the
same priority
Starvation does not occur in
the processes
Specific time given for each
process to execute
Long processes given time to
complete executing
Short processes
have to wait for a
long time.
Processes run until
it finishes.
Does not give
priority to more
important tasks.
Frustrates those
with medium
length tasks
Weighed roundbin It is very first Complex
11
Identifies if the server is
loaded
Improves the efficient of the
server
Compressive reporting and full
integration
Less expensive it requires no
cost to be installed
calculations can
lead to errors
Requires high
maintenance.
Source IP hash It gets the ip address of the
client.
Locates the client to a
particular server.
Calculates hash values hence
encrypted
A single virtual
NIC cannot use
more than a single
physical NIC's
bandwidth
URL hash
Improves situations where
single virtual machine can
communicate with multiple
machines.
Has network adapter
redundancy
Requires
physically ports to
be configured
manually.
Requires only a
single connection.
Does not support
IP hash
It only supports
standard switches.
Least Connections Has a best response
Has best response time.
Does not manage
client catch.
12
loaded
Improves the efficient of the
server
Compressive reporting and full
integration
Less expensive it requires no
cost to be installed
calculations can
lead to errors
Requires high
maintenance.
Source IP hash It gets the ip address of the
client.
Locates the client to a
particular server.
Calculates hash values hence
encrypted
A single virtual
NIC cannot use
more than a single
physical NIC's
bandwidth
URL hash
Improves situations where
single virtual machine can
communicate with multiple
machines.
Has network adapter
redundancy
Requires
physically ports to
be configured
manually.
Requires only a
single connection.
Does not support
IP hash
It only supports
standard switches.
Least Connections Has a best response
Has best response time.
Does not manage
client catch.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
