Security Risk Management Plan: Analysis for East Marine Supplies (EMS)
VerifiedAdded on 2022/10/03
|12
|3200
|35
Report
AI Summary
This report presents a comprehensive security risk management plan tailored for East Marine Supplies (EMS), a firm specializing in maritime equipment supply and installation. It begins with an introduction outlining the importance of proactive risk management in identifying, monitoring, and managing potential security threats, including those related to cybercrime and technological advancements. The report details the benefits of a risk management plan for EMS, such as the identification of apparent security risks, support for the board of directors, compliance with regulatory agencies, and reduction of business liability. It then outlines the security risk management process, including hazard identification, risk assessment, control measures, and review. Furthermore, the report details the steps of a risk management plan, encompassing risk assessment and analysis, risk evaluation, and risk treatment. It also analyzes specific security risks related to ICT systems, such as password protection, and provides risk control measures, including safe system design, employee screening, and training. The report includes asset priority and TVA tables for a structured risk analysis, emphasizing the importance of ongoing reviews and policy development to maintain the security of information technology systems. The conclusion stresses the importance of a proactive and adaptable approach to security risk management to safeguard EMS's operations and assets.

Running Head: SECURITY RISK MANAGEMENT PLAN 1
Security Risk Management Plan
Name:
University affiliation:
Security Risk Management Plan
Name:
University affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY RISK MANAGEMENT PLAN 2
Introduction
A security risk management plan helps to identify, monitor and manage security
problems that are potential before they can occur; this helps in the planning of risk handling
activities that can be put in place to counter the upcoming risks. (Pritchard & PMP 2014). To
successfully achieve the set objectives of a project a risk management plan must be drafted
(Kliem & Ludin 2019). A security risk management plan will enlighten the potential security
threats that can affect the operations of a project; these security risks can be associated with
suspected criminal activities, developing crime patterns or technological advancement that
can harm the systems of the organization. This paper contains a detailed security risk
management report for East Marine Supplies (EMS) that will project the purpose and
importance of conducting a security risk management plan, the process and steps to an
effective risk management plan and how it is related to the success of EMS. There have been
new developments in the security sector that have been driven by technological developments
in crime patterns. It’s therefore important that a security risk management plan is drafted to
bring to copy the possible threats that might interfere with the normalcy of operations in a
business (Aven, 2012).
Contingency plan for EMS
EMS is one of the leading firms in the supply and installation of equipment for
maritime vessels, one of the methods used in sales in the use of an online platform created to
enable the customers to make their orders and pay for the services. As a firm that has
endorsed technological advancement in service delivery, the systems must be well maintained
and protected from harm caused by hackers and thieves. A security risk management plan
will assist to enlighten the management of the possible security threats and the risks that they
Introduction
A security risk management plan helps to identify, monitor and manage security
problems that are potential before they can occur; this helps in the planning of risk handling
activities that can be put in place to counter the upcoming risks. (Pritchard & PMP 2014). To
successfully achieve the set objectives of a project a risk management plan must be drafted
(Kliem & Ludin 2019). A security risk management plan will enlighten the potential security
threats that can affect the operations of a project; these security risks can be associated with
suspected criminal activities, developing crime patterns or technological advancement that
can harm the systems of the organization. This paper contains a detailed security risk
management report for East Marine Supplies (EMS) that will project the purpose and
importance of conducting a security risk management plan, the process and steps to an
effective risk management plan and how it is related to the success of EMS. There have been
new developments in the security sector that have been driven by technological developments
in crime patterns. It’s therefore important that a security risk management plan is drafted to
bring to copy the possible threats that might interfere with the normalcy of operations in a
business (Aven, 2012).
Contingency plan for EMS
EMS is one of the leading firms in the supply and installation of equipment for
maritime vessels, one of the methods used in sales in the use of an online platform created to
enable the customers to make their orders and pay for the services. As a firm that has
endorsed technological advancement in service delivery, the systems must be well maintained
and protected from harm caused by hackers and thieves. A security risk management plan
will assist to enlighten the management of the possible security threats and the risks that they

SECURITY RISK MANAGEMENT PLAN 3
impose on the firm. Risk management will assist in the early detection and management of
such risks. EMS being a firm with quite several employees it becomes important to ensure
that both the employees and the systems they operate are secure from harm.
As a measure of protecting property and employees, physical security should be
adhered to, all the access points and the perimeter walls of the stores should be properly
manned and surveyed. Risks that can cause harm to either the employees or the system will
affect the productivity of the firm; therefore a security risk management plan must be
generated to ensure safety.
Benefits of a risk a management plan to EMS
A business that has long term goals must prioritize the drafting of a risk management
plan to achieve the following reasons; assist in the identification of security risks that are
not apparent; this provides a platform for providing a deeper understanding of all types of
security risks comprehensively (Hopkin, P. (2018). This plan helps to provide insight and
support to the board of directors in identifying potential security risks that are outside their
areas of experience. This will provide an advisory platform to the board members and its
committees. The security risk management plan will assist the organization to get credit for
the corporation from regulatory agencies who want to see measures in place to curb potential
risks. The plan will also assist in building a better defense of class actions by showing the
risk mitigation plans that have been in place to minimize the risks. This is usually during
plaintiffs in class actions in defending the fact that there was no negligence.
This plan also assists to reduce business liability by reducing the litigation risk
upfront to win the trust of investors and attract more. This enables the organization to prevent
any liability that might come forth. (Grace et al. 2015). The plan also assists to frame the
impose on the firm. Risk management will assist in the early detection and management of
such risks. EMS being a firm with quite several employees it becomes important to ensure
that both the employees and the systems they operate are secure from harm.
As a measure of protecting property and employees, physical security should be
adhered to, all the access points and the perimeter walls of the stores should be properly
manned and surveyed. Risks that can cause harm to either the employees or the system will
affect the productivity of the firm; therefore a security risk management plan must be
generated to ensure safety.
Benefits of a risk a management plan to EMS
A business that has long term goals must prioritize the drafting of a risk management
plan to achieve the following reasons; assist in the identification of security risks that are
not apparent; this provides a platform for providing a deeper understanding of all types of
security risks comprehensively (Hopkin, P. (2018). This plan helps to provide insight and
support to the board of directors in identifying potential security risks that are outside their
areas of experience. This will provide an advisory platform to the board members and its
committees. The security risk management plan will assist the organization to get credit for
the corporation from regulatory agencies who want to see measures in place to curb potential
risks. The plan will also assist in building a better defense of class actions by showing the
risk mitigation plans that have been in place to minimize the risks. This is usually during
plaintiffs in class actions in defending the fact that there was no negligence.
This plan also assists to reduce business liability by reducing the litigation risk
upfront to win the trust of investors and attract more. This enables the organization to prevent
any liability that might come forth. (Grace et al. 2015). The plan also assists to frame the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY RISK MANAGEMENT PLAN 4
available regulatory issues by providing more insight on insurance and liability issues to get
more focused.
Security Risk management process
The first process in security risk management is identifying the hazards that will
lead to the projected risk. During the identification of the hazards, an inspection of the
workplace will be done to understand the operations involved in the organization, emphasis
will be laid on the physical work environment, the equipment, and materials used in the
organization, work tasks and how they are performed, work design and management. When
identifying the hazards both the existing and suspected hazards are included in the
documentation of hazards. It's also important to engage the workers to identify their
discomforts and potential hazards and then review the available data that has been
enlightened.
The next process of security risk management plan is to assess the available risks,
after the identifications of a risk an assessment of the risk follows. In this process, the
characteristics of the hazardous risks and their relationship to productivity will create a
deeper understanding of the potential risks and their cause (Hopkin, P. (2018).
The next process involves controlling the risk from the highest level of protection to
the lowest. In this process the risk can be eliminated if there are avenues of immediate
elimination, the risk can be substituted and replaced by factors that have a lighter impact on
production or the risk can be isolated by proving full independence from the risk factors. The
risks can be engineered by adopting technical solutions. The risk can also be altered
administratively by the adoption of new policies to curb the effects of the risk and lastly
personal protection equipment can be adapted to control the effect of the risk at hand.
available regulatory issues by providing more insight on insurance and liability issues to get
more focused.
Security Risk management process
The first process in security risk management is identifying the hazards that will
lead to the projected risk. During the identification of the hazards, an inspection of the
workplace will be done to understand the operations involved in the organization, emphasis
will be laid on the physical work environment, the equipment, and materials used in the
organization, work tasks and how they are performed, work design and management. When
identifying the hazards both the existing and suspected hazards are included in the
documentation of hazards. It's also important to engage the workers to identify their
discomforts and potential hazards and then review the available data that has been
enlightened.
The next process of security risk management plan is to assess the available risks,
after the identifications of a risk an assessment of the risk follows. In this process, the
characteristics of the hazardous risks and their relationship to productivity will create a
deeper understanding of the potential risks and their cause (Hopkin, P. (2018).
The next process involves controlling the risk from the highest level of protection to
the lowest. In this process the risk can be eliminated if there are avenues of immediate
elimination, the risk can be substituted and replaced by factors that have a lighter impact on
production or the risk can be isolated by proving full independence from the risk factors. The
risks can be engineered by adopting technical solutions. The risk can also be altered
administratively by the adoption of new policies to curb the effects of the risk and lastly
personal protection equipment can be adapted to control the effect of the risk at hand.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY RISK MANAGEMENT PLAN 5
The last process involves the review of the risk control that involves the review of the
adopted measure used to curb the risk; this assists the organization to measure the progress on
the risk eradication method. The review will assist identify if the measures placed are not
effective or slow and to identify the new hazards in place.
Steps of risk management plan
The process of risk management plan consists of three main steps; the first step involves risk
assessment and analysis which evaluates the exposure of an organization to uncertain events
that could impact the normalcy then estimates the damages that could be caused by the events
analyzed. It also checks on the impact to the organization's revenue and reputation to the
public. This helps to protect the assets, improve the decision-making process and improves
the efficiency of operations within the organization (Yilmaz & Flouris 2010).
The next step in the process is to evaluate the risks by comparing the estimated risks
against the risk criteria that have already been established by the organization. The criterion
involves the associated cost and benefits of the organization, the social-economic factors and
legal requirements of the organization. The final step in the process is the treatment of the
risk and response by implementing the policies and procedures that will minimize the risks.
The process of risk management should be ongoing so that upcoming risks can be identified
and mitigated, to achieve this, it's important to review the risk management plan yearly.
Analysis of security risk management plan
Technology has advanced with time and helped create solutions to improve service delivery
in most organizations, most of the firms that have adopted technological aspects of service
delivery have bulks of information technology that needs protection from threats that might
be intending to cause harm to the information data. (McManus, 2012). In the quest to address
the risks involved in the ICT systems, it's important to note that hazards that are associated
The last process involves the review of the risk control that involves the review of the
adopted measure used to curb the risk; this assists the organization to measure the progress on
the risk eradication method. The review will assist identify if the measures placed are not
effective or slow and to identify the new hazards in place.
Steps of risk management plan
The process of risk management plan consists of three main steps; the first step involves risk
assessment and analysis which evaluates the exposure of an organization to uncertain events
that could impact the normalcy then estimates the damages that could be caused by the events
analyzed. It also checks on the impact to the organization's revenue and reputation to the
public. This helps to protect the assets, improve the decision-making process and improves
the efficiency of operations within the organization (Yilmaz & Flouris 2010).
The next step in the process is to evaluate the risks by comparing the estimated risks
against the risk criteria that have already been established by the organization. The criterion
involves the associated cost and benefits of the organization, the social-economic factors and
legal requirements of the organization. The final step in the process is the treatment of the
risk and response by implementing the policies and procedures that will minimize the risks.
The process of risk management should be ongoing so that upcoming risks can be identified
and mitigated, to achieve this, it's important to review the risk management plan yearly.
Analysis of security risk management plan
Technology has advanced with time and helped create solutions to improve service delivery
in most organizations, most of the firms that have adopted technological aspects of service
delivery have bulks of information technology that needs protection from threats that might
be intending to cause harm to the information data. (McManus, 2012). In the quest to address
the risks involved in the ICT systems, it's important to note that hazards that are associated

SECURITY RISK MANAGEMENT PLAN 6
with the system such as password protection, most cyberattacks have been succeeded due to
the availability of weak passwords that can be easily cracked. Password is a very essential
necessity in accessing all equipments that are protected, wireless networks and data.
About password protection, all the risks that are related to password breach must be
analyzed and addressed. Password is a key aspect of security should be prioritized at all time
and any risks that may be involved with it should be addressed as soon as possible. The
strongest passwords should contain numbers, letters and symbols to make the password
unique. It's important that during risk assessment the risks related to weak passwords are
identified. All the passwords should be assessed to ensure that they conform to the
requirements of a stronger password that can't be cracked by hackers.
As part of the risk management plan, it's important to control the risk after assessing
the possible risks to the security information systems. As a method of risk control, it's
important to design safe systems that will reduce the exposure of the company system to
hackers and thieves intending to harm the system. By designing a safe system you will be
reducing the points if failure by limiting the access to hardware and software. This means that
the system will limit and restrict individual user and system privilege only to the needed
equipment and programs. In adopting this model the potential damages are minimized by
using unique sets of email addresses, logins, servers and domain names for each user
involved in the system operations.
As processes of risk management plan, it's important to conduct screening and
background checks to identify unwanted intrusions that have occurred to the firewalls. In
handling, this risk assessment will focus on screening all prospective employees from the
mailroom to the executive team.
with the system such as password protection, most cyberattacks have been succeeded due to
the availability of weak passwords that can be easily cracked. Password is a very essential
necessity in accessing all equipments that are protected, wireless networks and data.
About password protection, all the risks that are related to password breach must be
analyzed and addressed. Password is a key aspect of security should be prioritized at all time
and any risks that may be involved with it should be addressed as soon as possible. The
strongest passwords should contain numbers, letters and symbols to make the password
unique. It's important that during risk assessment the risks related to weak passwords are
identified. All the passwords should be assessed to ensure that they conform to the
requirements of a stronger password that can't be cracked by hackers.
As part of the risk management plan, it's important to control the risk after assessing
the possible risks to the security information systems. As a method of risk control, it's
important to design safe systems that will reduce the exposure of the company system to
hackers and thieves intending to harm the system. By designing a safe system you will be
reducing the points if failure by limiting the access to hardware and software. This means that
the system will limit and restrict individual user and system privilege only to the needed
equipment and programs. In adopting this model the potential damages are minimized by
using unique sets of email addresses, logins, servers and domain names for each user
involved in the system operations.
As processes of risk management plan, it's important to conduct screening and
background checks to identify unwanted intrusions that have occurred to the firewalls. In
handling, this risk assessment will focus on screening all prospective employees from the
mailroom to the executive team.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY RISK MANAGEMENT PLAN 7
As part of the security risk management, it's important to involve all the employees to
advanced training that is basic to the provision of security to the system. This training
will assist the organization in creating a culture that will emphasize computer technology by
introducing training on programs that will create warning alerts on risks of sloppy passwords
and the careless use involving the network.
In risk management, it's important to review the risks that have been brought up for
attention and assess the control measures that have been put in place to ensure that they are
progressive and applicable in risk management. It is important to identify the measures that
do not add value in risk management and replacing them with the alternatives that can
deliver.
A company must create policies that are directed to maintaining security of the
information technology. The systems used in service delivery should be up to date with the
current updates and the virus scanners; this will assist in ensuring that the security systems
are up to date. It's also important to keep sensitive data out of the cloud, cloud computing has
been used diversely in ensuring business benefits and cost-saving. This service exposes the
system to threats since most of the data are housed on servers that are remote which are
operated by third parties who may be faced with security problems.
Risk analysis
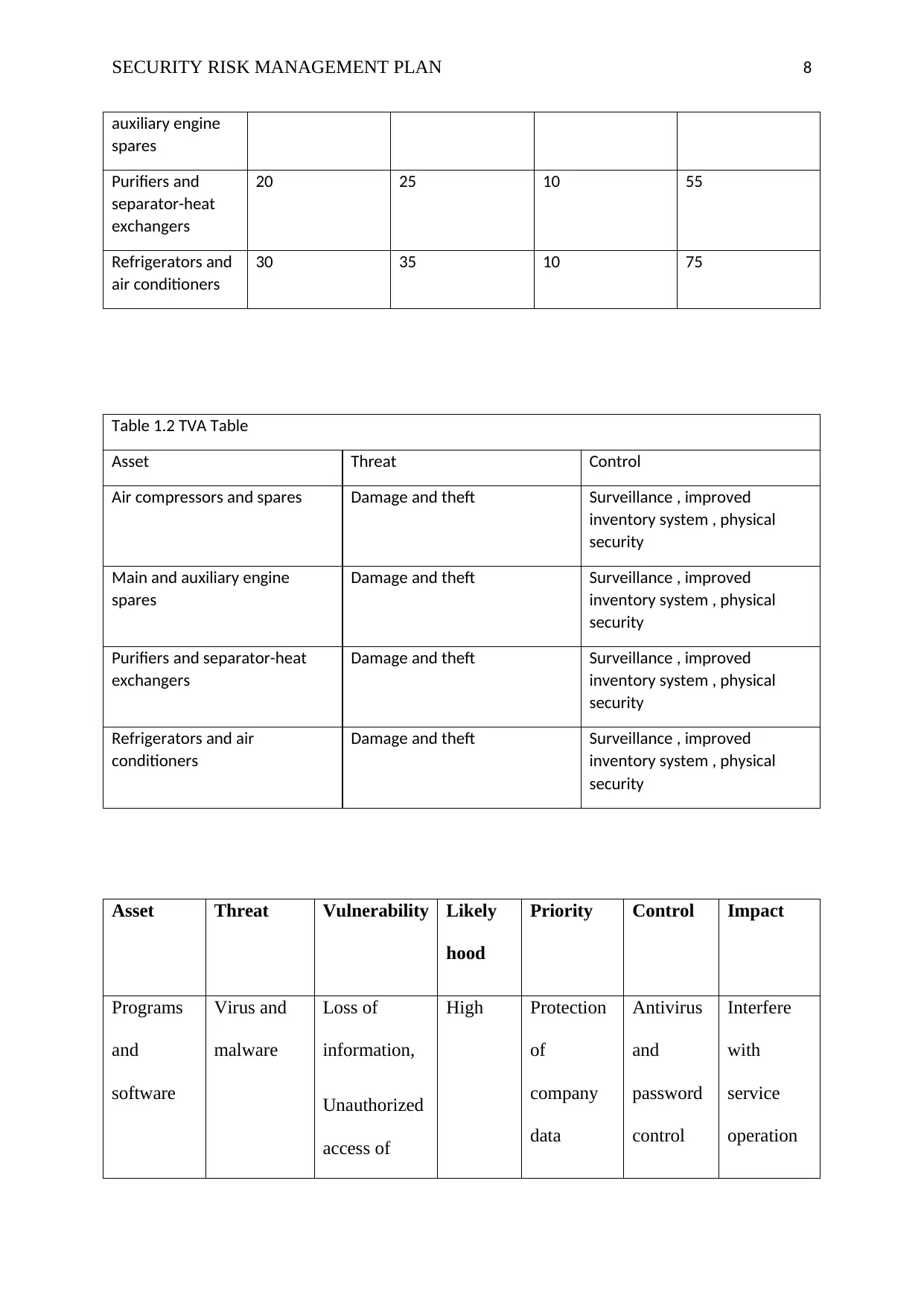
Table 1:1 Asset priority table
Asset Revenue impact Profitability
impact
Public image Priority score
(asset impact )
Air compressors
and spares
20 30 10 60
Main and 25 40 10 75
As part of the security risk management, it's important to involve all the employees to
advanced training that is basic to the provision of security to the system. This training
will assist the organization in creating a culture that will emphasize computer technology by
introducing training on programs that will create warning alerts on risks of sloppy passwords
and the careless use involving the network.
In risk management, it's important to review the risks that have been brought up for
attention and assess the control measures that have been put in place to ensure that they are
progressive and applicable in risk management. It is important to identify the measures that
do not add value in risk management and replacing them with the alternatives that can
deliver.
A company must create policies that are directed to maintaining security of the
information technology. The systems used in service delivery should be up to date with the
current updates and the virus scanners; this will assist in ensuring that the security systems
are up to date. It's also important to keep sensitive data out of the cloud, cloud computing has
been used diversely in ensuring business benefits and cost-saving. This service exposes the
system to threats since most of the data are housed on servers that are remote which are
operated by third parties who may be faced with security problems.
Risk analysis
Table 1:1 Asset priority table
Asset Revenue impact Profitability
impact
Public image Priority score
(asset impact )
Air compressors
and spares
20 30 10 60
Main and 25 40 10 75
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
SECURITY RISK MANAGEMENT PLAN 8
auxiliary engine
spares
Purifiers and
separator-heat
exchangers
20 25 10 55
Refrigerators and
air conditioners
30 35 10 75
Table 1.2 TVA Table
Asset Threat Control
Air compressors and spares Damage and theft Surveillance , improved
inventory system , physical
security
Main and auxiliary engine
spares
Damage and theft Surveillance , improved
inventory system , physical
security
Purifiers and separator-heat
exchangers
Damage and theft Surveillance , improved
inventory system , physical
security
Refrigerators and air
conditioners
Damage and theft Surveillance , improved
inventory system , physical
security
Asset Threat Vulnerability Likely
hood
Priority Control Impact
Programs
and
software
Virus and
malware
Loss of
information,
Unauthorized
access of
High Protection
of
company
data
Antivirus
and
password
control
Interfere
with
service
operation
auxiliary engine
spares
Purifiers and
separator-heat
exchangers
20 25 10 55
Refrigerators and
air conditioners
30 35 10 75
Table 1.2 TVA Table
Asset Threat Control
Air compressors and spares Damage and theft Surveillance , improved
inventory system , physical
security
Main and auxiliary engine
spares
Damage and theft Surveillance , improved
inventory system , physical
security
Purifiers and separator-heat
exchangers
Damage and theft Surveillance , improved
inventory system , physical
security
Refrigerators and air
conditioners
Damage and theft Surveillance , improved
inventory system , physical
security
Asset Threat Vulnerability Likely
hood
Priority Control Impact
Programs
and
software
Virus and
malware
Loss of
information,
Unauthorized
access of
High Protection
of
company
data
Antivirus
and
password
control
Interfere
with
service
operation
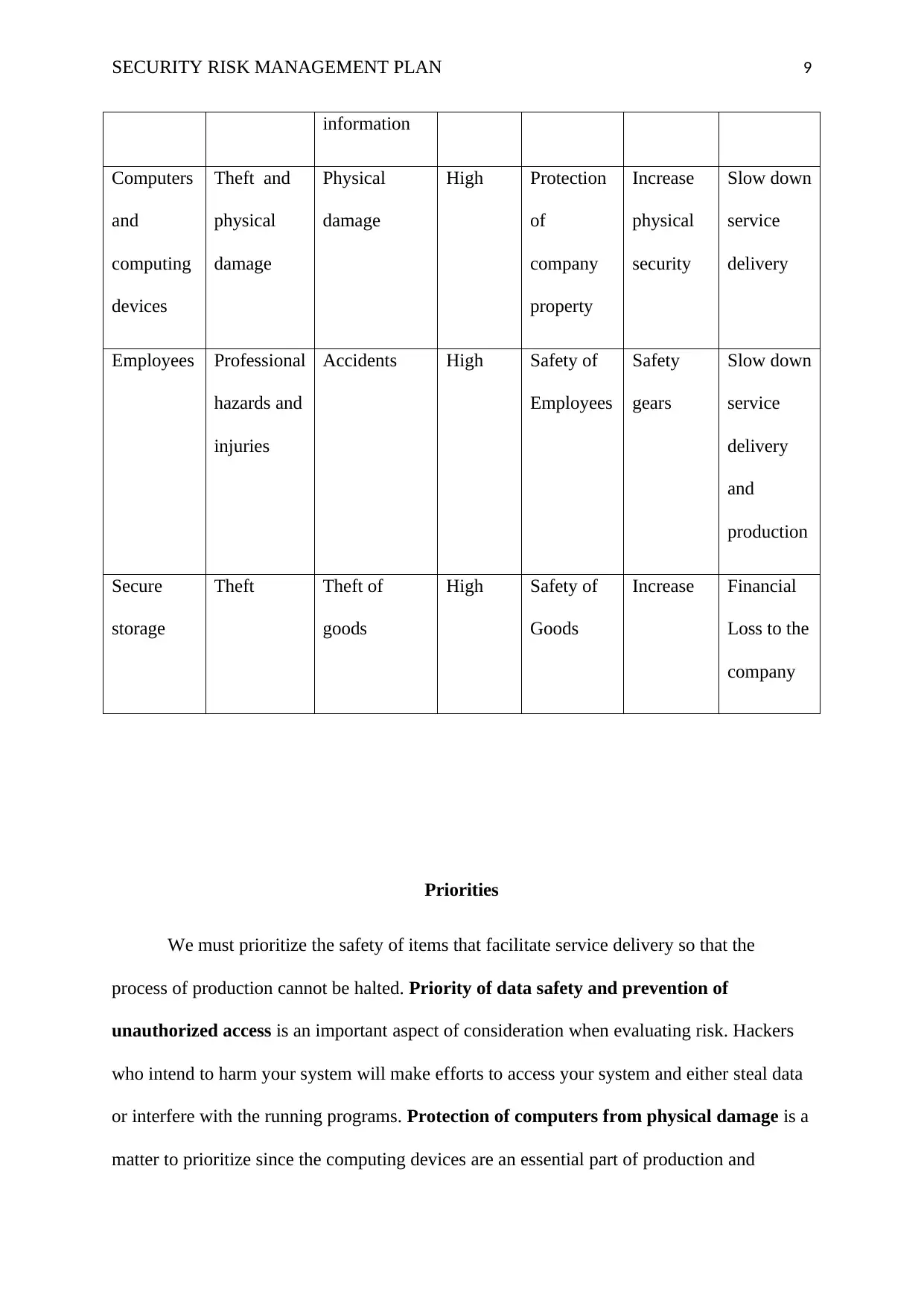
SECURITY RISK MANAGEMENT PLAN 9
information
Computers
and
computing
devices
Theft and
physical
damage
Physical
damage
High Protection
of
company
property
Increase
physical
security
Slow down
service
delivery
Employees Professional
hazards and
injuries
Accidents High Safety of
Employees
Safety
gears
Slow down
service
delivery
and
production
Secure
storage
Theft Theft of
goods
High Safety of
Goods
Increase Financial
Loss to the
company
Priorities
We must prioritize the safety of items that facilitate service delivery so that the
process of production cannot be halted. Priority of data safety and prevention of
unauthorized access is an important aspect of consideration when evaluating risk. Hackers
who intend to harm your system will make efforts to access your system and either steal data
or interfere with the running programs. Protection of computers from physical damage is a
matter to prioritize since the computing devices are an essential part of production and
information
Computers
and
computing
devices
Theft and
physical
damage
Physical
damage
High Protection
of
company
property
Increase
physical
security
Slow down
service
delivery
Employees Professional
hazards and
injuries
Accidents High Safety of
Employees
Safety
gears
Slow down
service
delivery
and
production
Secure
storage
Theft Theft of
goods
High Safety of
Goods
Increase Financial
Loss to the
company
Priorities
We must prioritize the safety of items that facilitate service delivery so that the
process of production cannot be halted. Priority of data safety and prevention of
unauthorized access is an important aspect of consideration when evaluating risk. Hackers
who intend to harm your system will make efforts to access your system and either steal data
or interfere with the running programs. Protection of computers from physical damage is a
matter to prioritize since the computing devices are an essential part of production and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY RISK MANAGEMENT PLAN 10
service delivery, it is, therefore, important that we protect the computing devices from any
physical damages that might be caused by persons with ill motives of slowing down the
operations of the company.
Secure storage is one of the services offered by the company to ensure that they store
their client's goods in a safe storage facility, it is therefore important that this storage facilities
are manned and protected from intruders who might want to steal the goods. Surveillance
must be enhanced as well as increased patrol by the physical guards.Safety of employees is
an important factor to prioritize in achieving smooth service delivery. Employees being part
of the team that does production and ensures the effective running of the company operations
must be protected from physical harm when performing their duties. It's therefore important
to ensure that they are introduced to safety gear to protect them. When an employee is
injured, it slows down service delivery.
Risk checks and controls
EMS is a firm that has its operations based on online interactions creates room for
attacks by hackers who would want to access the data and steal by corrupting the system. A
major threat to its online operations is hacking that is commonly done due to access to weak
passwords created by the access systems. By hacking and corrupting the system it disrupts
the normal operations on the online platform. It's therefore important that the passwords are
assessed and made to conform to the strength of a perfect password.
The hackers can introduce a virus to corrupt the system and allow easy access into the
system through easy hacking of the system data. To prevent this system should adopt a strong
antivirus that will detect and block any forms of viruses that the system will be exposed to.
The system will need regular system updates to ensure that the software conforms to the
developments required to provide security.
service delivery, it is, therefore, important that we protect the computing devices from any
physical damages that might be caused by persons with ill motives of slowing down the
operations of the company.
Secure storage is one of the services offered by the company to ensure that they store
their client's goods in a safe storage facility, it is therefore important that this storage facilities
are manned and protected from intruders who might want to steal the goods. Surveillance
must be enhanced as well as increased patrol by the physical guards.Safety of employees is
an important factor to prioritize in achieving smooth service delivery. Employees being part
of the team that does production and ensures the effective running of the company operations
must be protected from physical harm when performing their duties. It's therefore important
to ensure that they are introduced to safety gear to protect them. When an employee is
injured, it slows down service delivery.
Risk checks and controls
EMS is a firm that has its operations based on online interactions creates room for
attacks by hackers who would want to access the data and steal by corrupting the system. A
major threat to its online operations is hacking that is commonly done due to access to weak
passwords created by the access systems. By hacking and corrupting the system it disrupts
the normal operations on the online platform. It's therefore important that the passwords are
assessed and made to conform to the strength of a perfect password.
The hackers can introduce a virus to corrupt the system and allow easy access into the
system through easy hacking of the system data. To prevent this system should adopt a strong
antivirus that will detect and block any forms of viruses that the system will be exposed to.
The system will need regular system updates to ensure that the software conforms to the
developments required to provide security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY RISK MANAGEMENT PLAN 11
EMS handles equipment that are expensive and valued by many; this exposes the
products to threat of theft either from external thieves or through collusion from the staff. It's
therefore important to limit the chances of exposure to theft. By this surveillance should be
improved through surveillance equipment like CCTV cameras that will monitor the
movements. There should be physical guards to control access to all the stores and maintain
the record of inventory.
As a measure of security, all the access points should be well managed and the
perimeter walls of the entire store properly manned. This will enhance physical security and
ensure the safety of the property. Enough guards should be deployed to Mann the properties
at all times.
Conclusion
Security is a basic requirement in the success of any business, the safety of both the
employees and the work systems contributes to the success of a business. (Varela-Vaca,
Gasca & Jimenez-Ramirez 2011, May). Security threats are known to be evolving with time
and a contingency plan must be created to curb such risks. A security risk management plan
will greatly assist in the early detection of future risks that a business is exposed to and timely
solutions to the problem.
The development of risks requires that a risk management plan is reviewed and
updated frequently to assist the business be in a copy of the developments in the risks it faces.
To effectively manage risk, the prompt process must be followed to ensure that the risk is
contained.
For effective production and progress if a business, it’s important that the welfare and safety
of the employees are prioritized to ensure that they are motivated to work. Risks can lead to
injuries to employees that will slow down production (Probst, & Estrada 2010)
EMS handles equipment that are expensive and valued by many; this exposes the
products to threat of theft either from external thieves or through collusion from the staff. It's
therefore important to limit the chances of exposure to theft. By this surveillance should be
improved through surveillance equipment like CCTV cameras that will monitor the
movements. There should be physical guards to control access to all the stores and maintain
the record of inventory.
As a measure of security, all the access points should be well managed and the
perimeter walls of the entire store properly manned. This will enhance physical security and
ensure the safety of the property. Enough guards should be deployed to Mann the properties
at all times.
Conclusion
Security is a basic requirement in the success of any business, the safety of both the
employees and the work systems contributes to the success of a business. (Varela-Vaca,
Gasca & Jimenez-Ramirez 2011, May). Security threats are known to be evolving with time
and a contingency plan must be created to curb such risks. A security risk management plan
will greatly assist in the early detection of future risks that a business is exposed to and timely
solutions to the problem.
The development of risks requires that a risk management plan is reviewed and
updated frequently to assist the business be in a copy of the developments in the risks it faces.
To effectively manage risk, the prompt process must be followed to ensure that the risk is
contained.
For effective production and progress if a business, it’s important that the welfare and safety
of the employees are prioritized to ensure that they are motivated to work. Risks can lead to
injuries to employees that will slow down production (Probst, & Estrada 2010)

SECURITY RISK MANAGEMENT PLAN 12
References
Aven, T. (2012). Foundations of risk analysis. John Wiley & Sons.
Grace, M. F., Leverty, J. T., Phillips, R. D., & Shimpi, P. (2015). The value of investing in
enterprise risk management. Journal of Risk and Insurance, 82(2), 289-316.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Kliem, R. L., & Ludin, I. S. (2019). Reducing project risk. Routledge.
McManus, J. (2012). Risk management in software development projects. Routledge
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. Auerbach
Publications.
Yilmaz, A. K., & Flouris, T. (2010). Managing corporate sustainability: Risk management
process-based perspective. African journal of business management, 4(2), 162-171.
Varela-Vaca, A. J., Gasca, R. M., & Jimenez-Ramirez, A. (2011, May). A model-driven
engineering approach with diagnosis of non-conformance of security objectives in
business process models. In 2011 FIFTH INTERNATIONAL CONFERENCE ON
RESEARCH CHALLENGES IN INFORMATION SCIENCE (pp. 1-6). IEEE.
Probst, T. M., & Estrada, A. X. (2010). Accident under-reporting among employees: Testing
the moderating influence of psychological safety climate and supervisor enforcement
of safety practices. Accident Analysis & Prevention, 42(5), 1438-1444.
References
Aven, T. (2012). Foundations of risk analysis. John Wiley & Sons.
Grace, M. F., Leverty, J. T., Phillips, R. D., & Shimpi, P. (2015). The value of investing in
enterprise risk management. Journal of Risk and Insurance, 82(2), 289-316.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Kliem, R. L., & Ludin, I. S. (2019). Reducing project risk. Routledge.
McManus, J. (2012). Risk management in software development projects. Routledge
Pritchard, C. L., & PMP, P. R. (2014). Risk management: concepts and guidance. Auerbach
Publications.
Yilmaz, A. K., & Flouris, T. (2010). Managing corporate sustainability: Risk management
process-based perspective. African journal of business management, 4(2), 162-171.
Varela-Vaca, A. J., Gasca, R. M., & Jimenez-Ramirez, A. (2011, May). A model-driven
engineering approach with diagnosis of non-conformance of security objectives in
business process models. In 2011 FIFTH INTERNATIONAL CONFERENCE ON
RESEARCH CHALLENGES IN INFORMATION SCIENCE (pp. 1-6). IEEE.
Probst, T. M., & Estrada, A. X. (2010). Accident under-reporting among employees: Testing
the moderating influence of psychological safety climate and supervisor enforcement
of safety practices. Accident Analysis & Prevention, 42(5), 1438-1444.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





